Method, device and system for updating key
A technology for updating keys and keys, applied in the field of communications, can solve the problems of increasing BSF load and service server load, etc., to reduce the key update load and avoid frequent updates.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
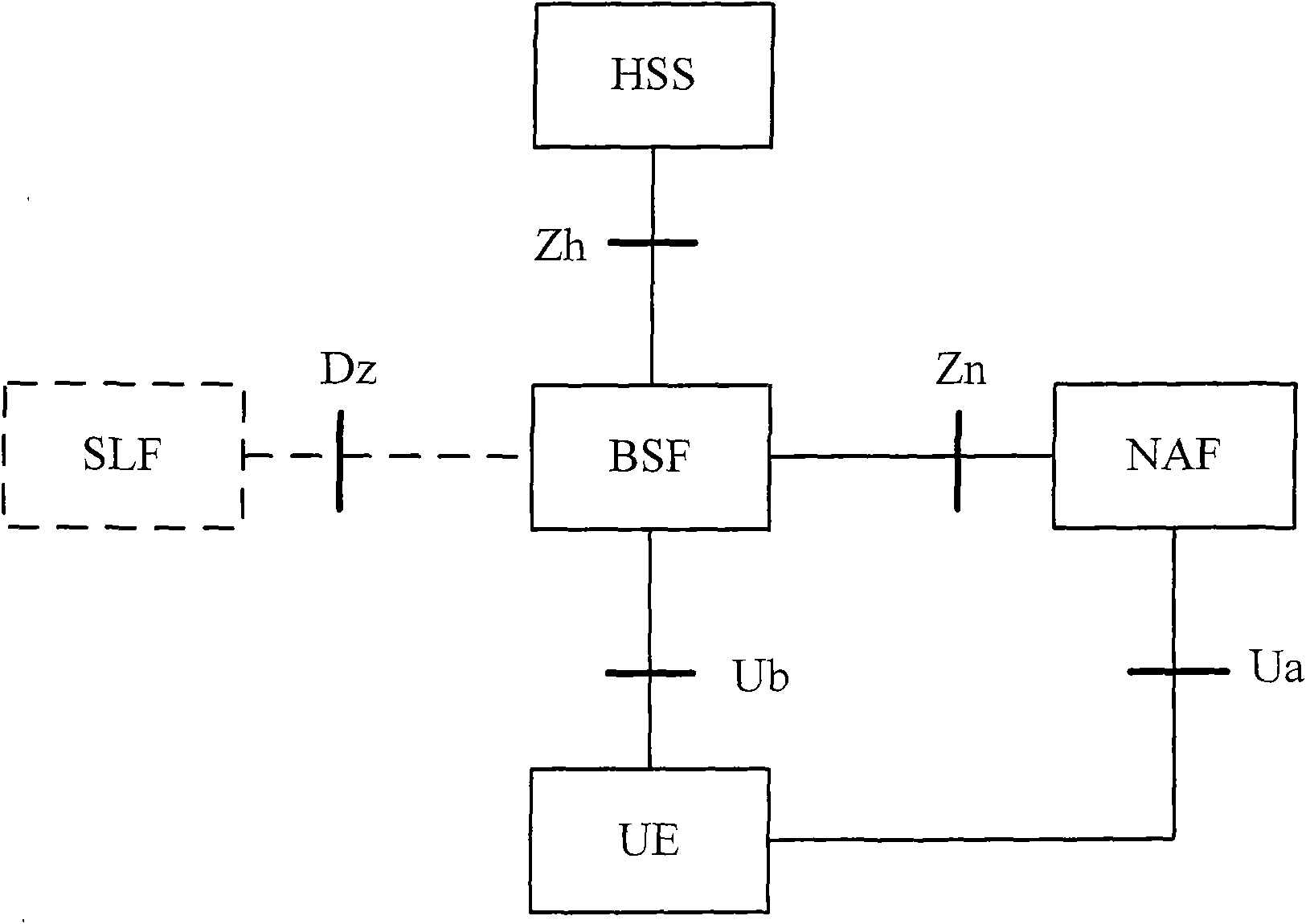
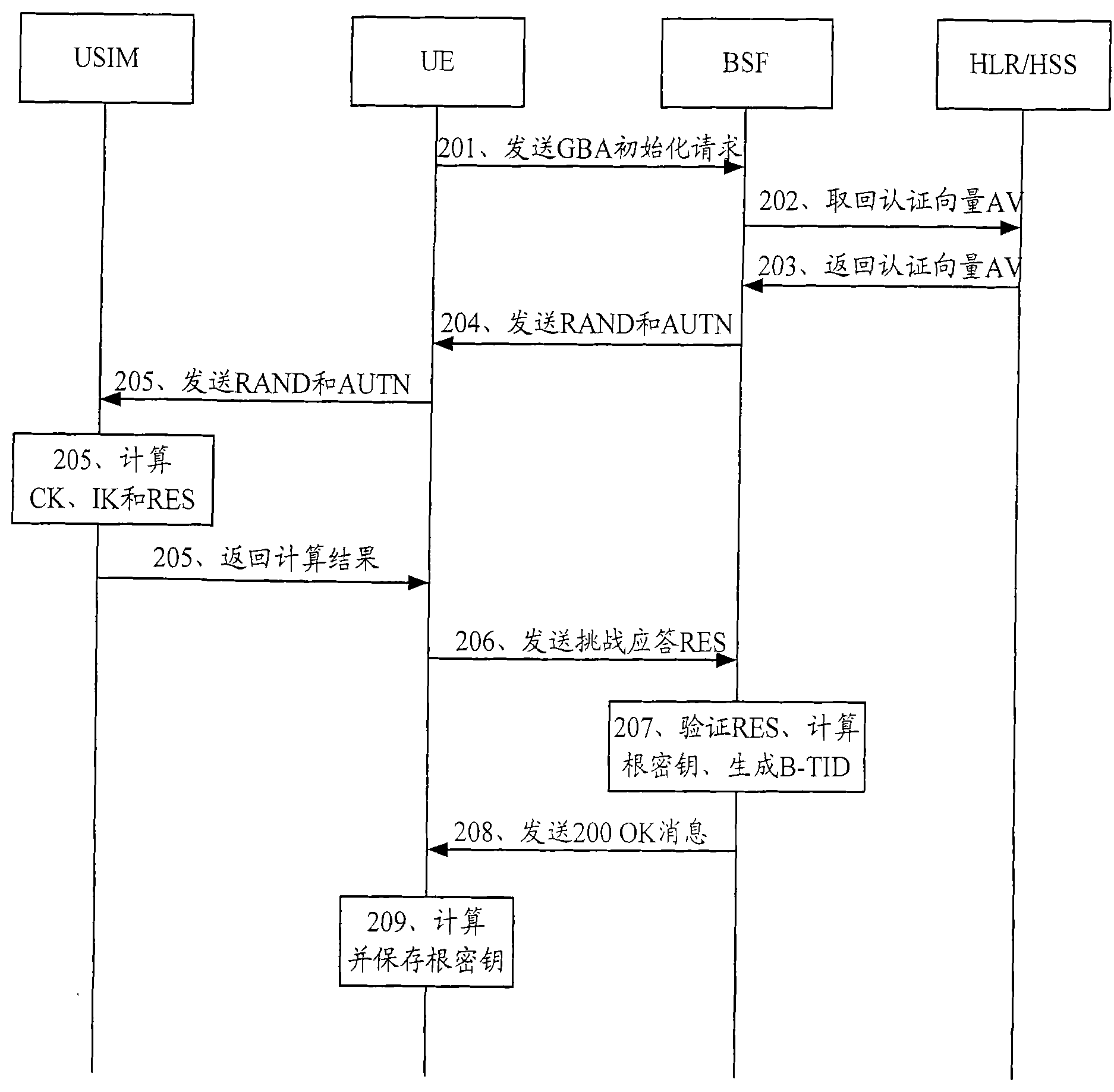
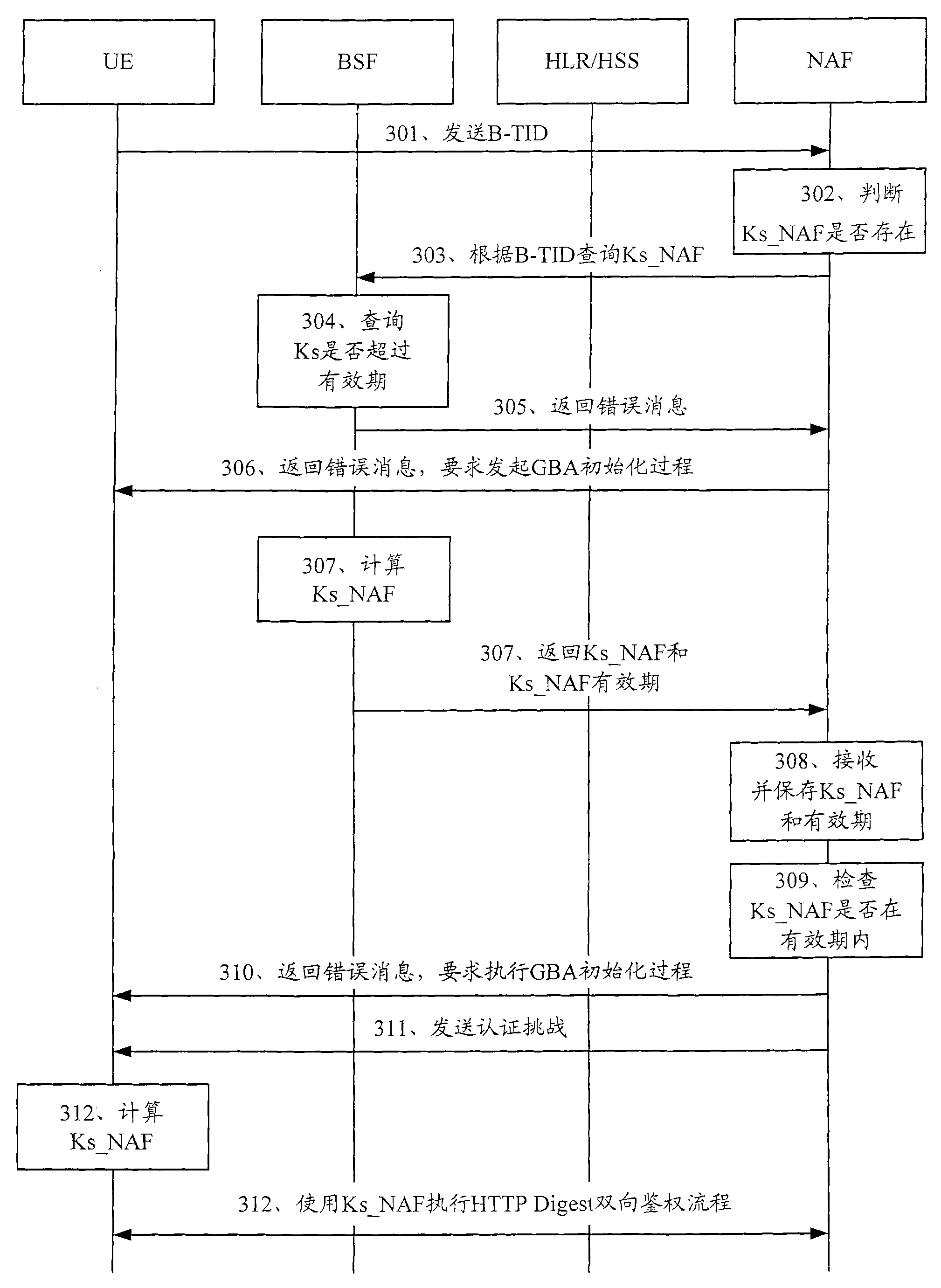
[0072] In the technical solution provided by the embodiment of the present invention, the core idea is that the NAF receives the guided service identifier from the user equipment, and when it finds that there is no service key locally or the service key is not within the validity period according to the guided service identifier, it queries the BSF for the root key. The BSF receives the guidance service identifier from the NAF, and queries whether the root key is within the validity period according to the guidance service identification; if the root key is not within the validity period, returns an error message to the user equipment, and performs common guidance with the user equipment Architecture GBA initialization; if the root key is within the validity period, generate a random number, obtain a service key according to the random number, and send the service key, the validity period of the service key and the random number For the NAF, make the NAF perform two-way authen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com