Patents
Literature
42 results about "Bootstrapping Server Function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
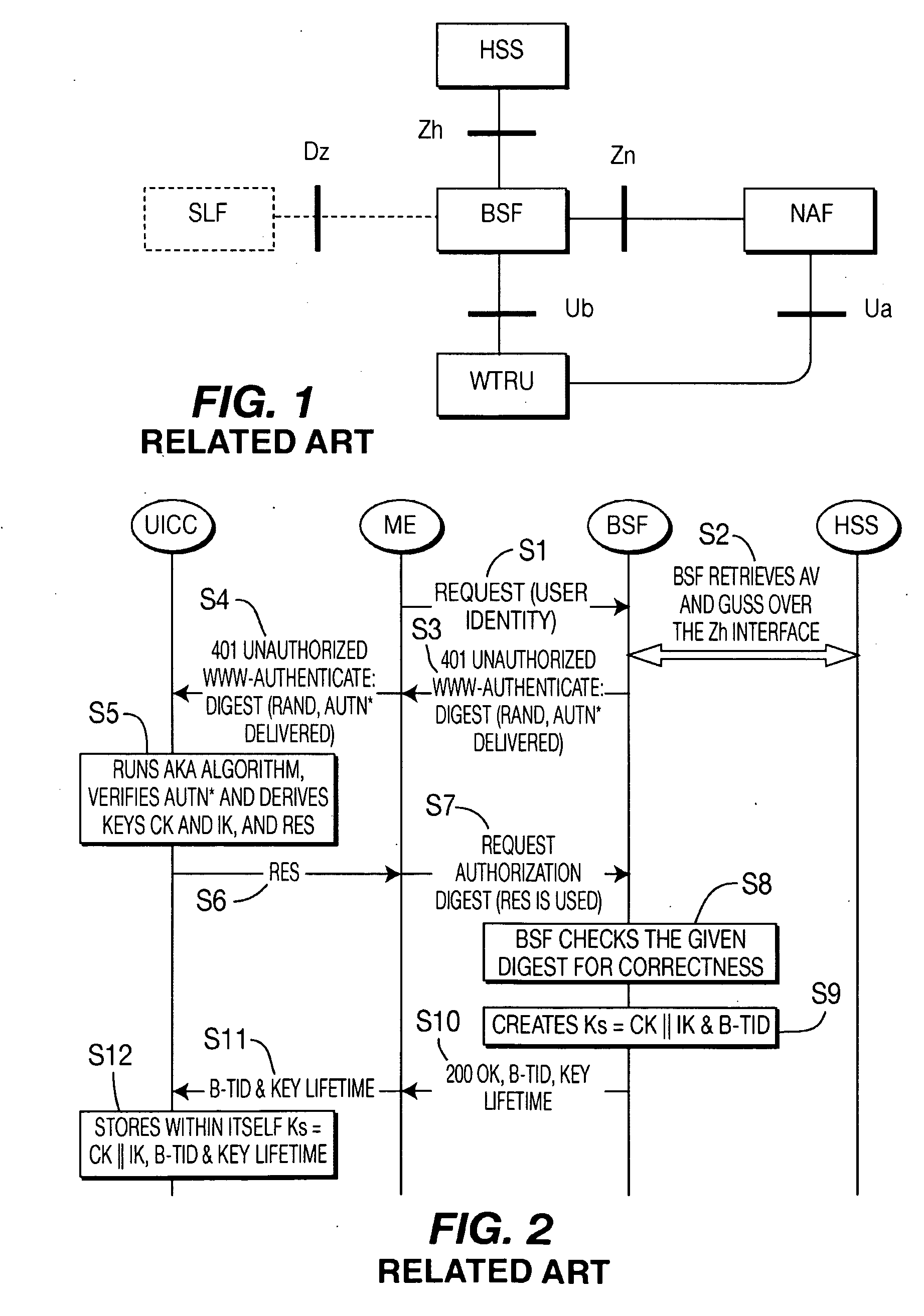
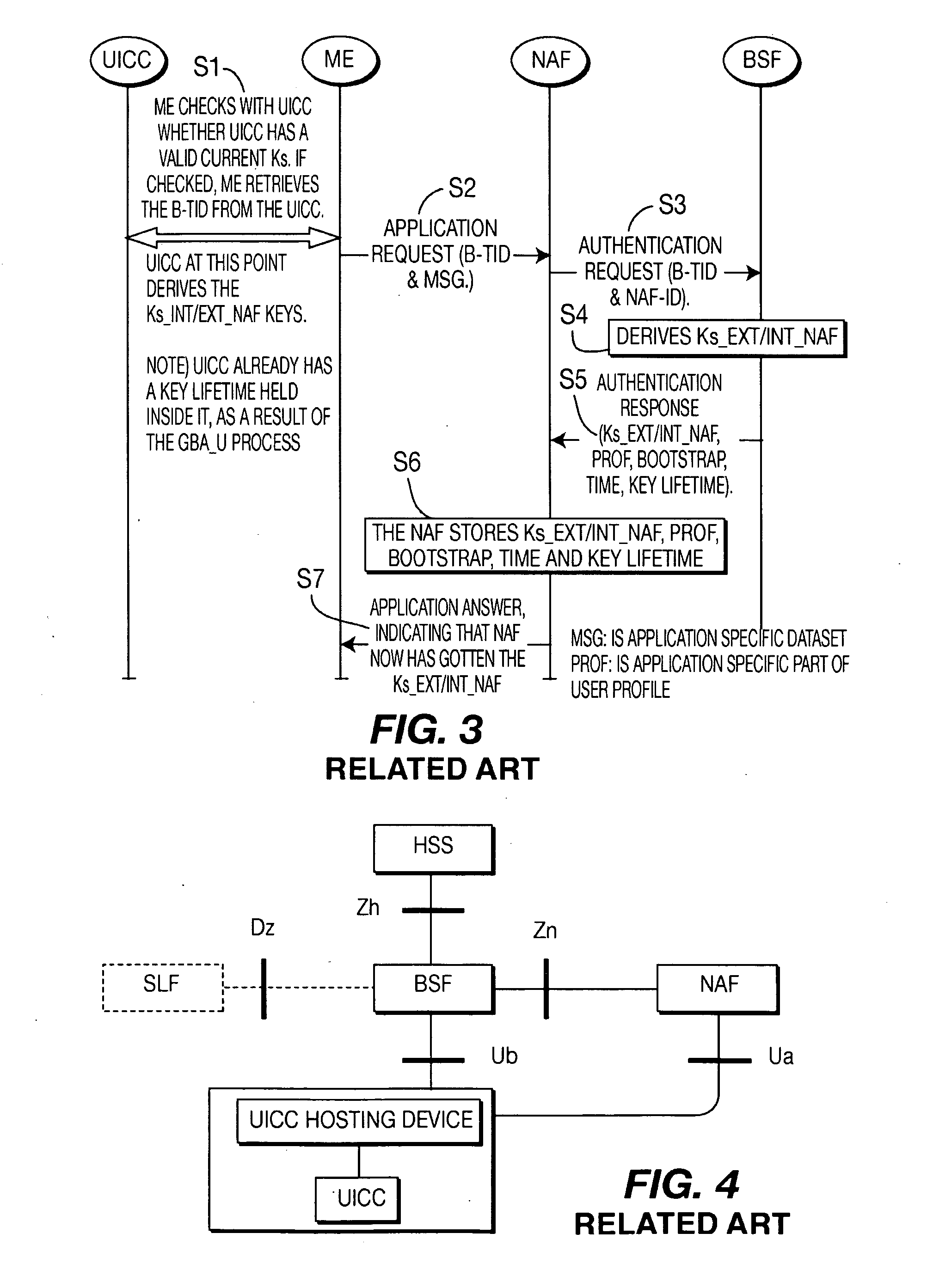
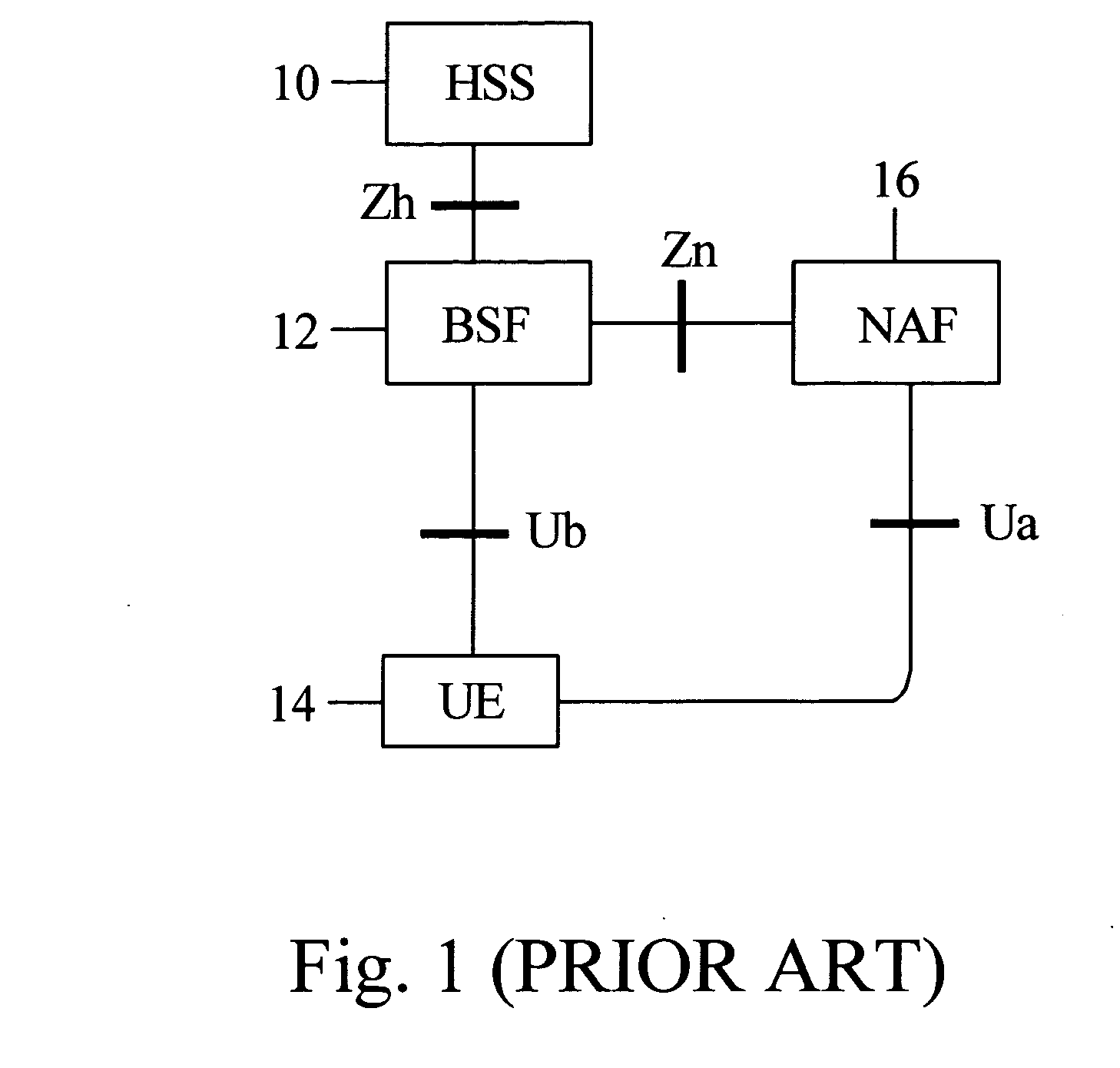
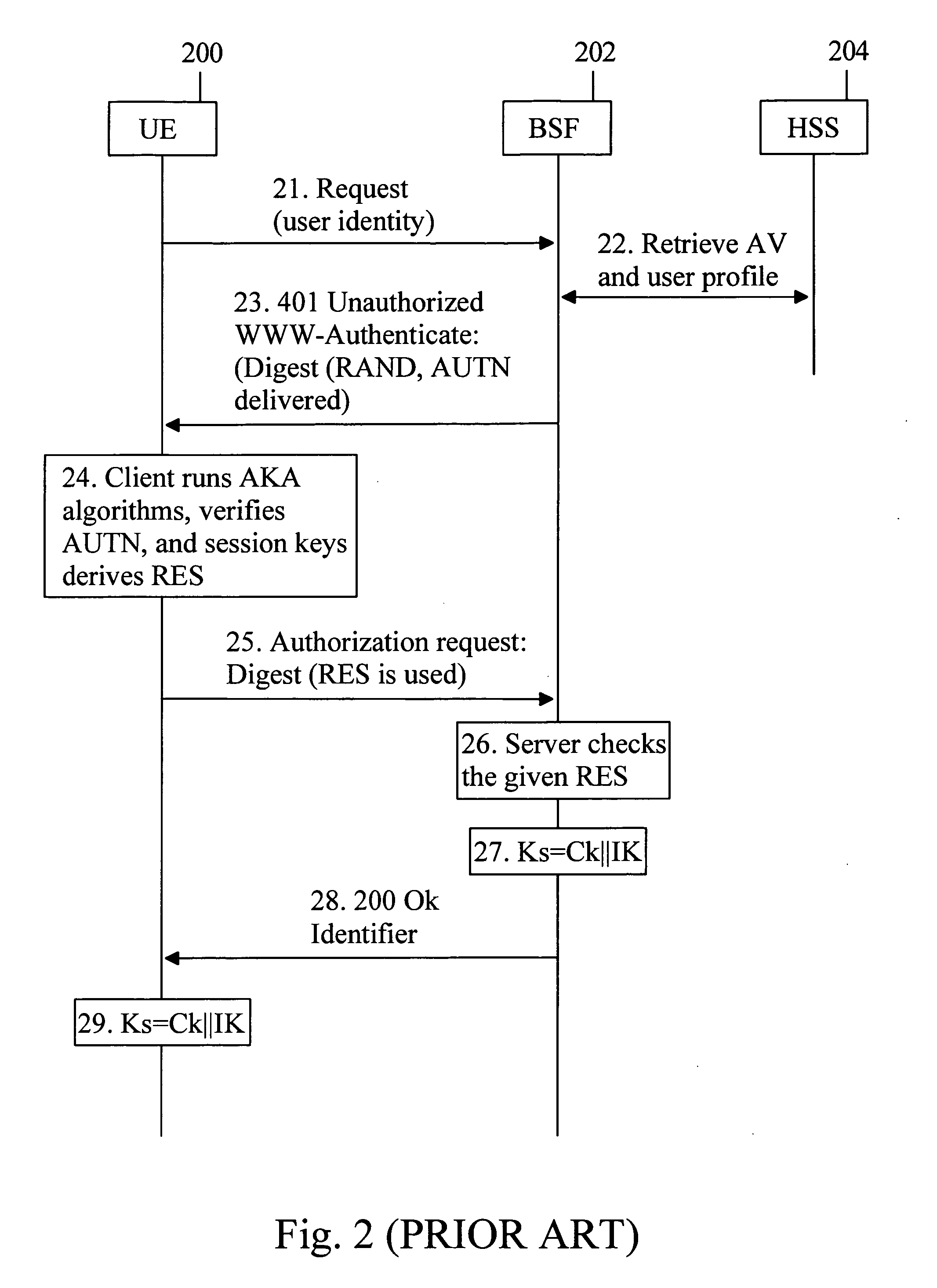
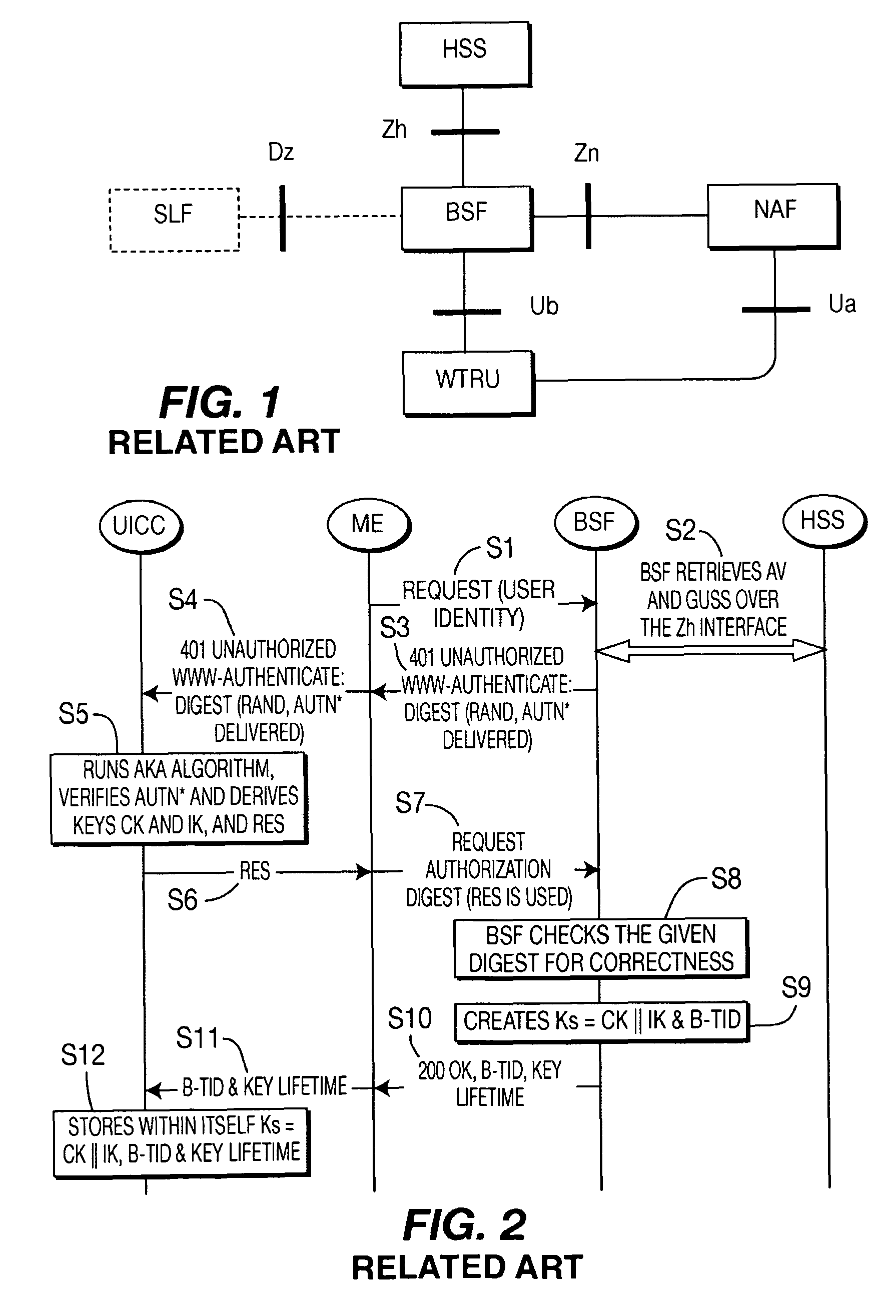
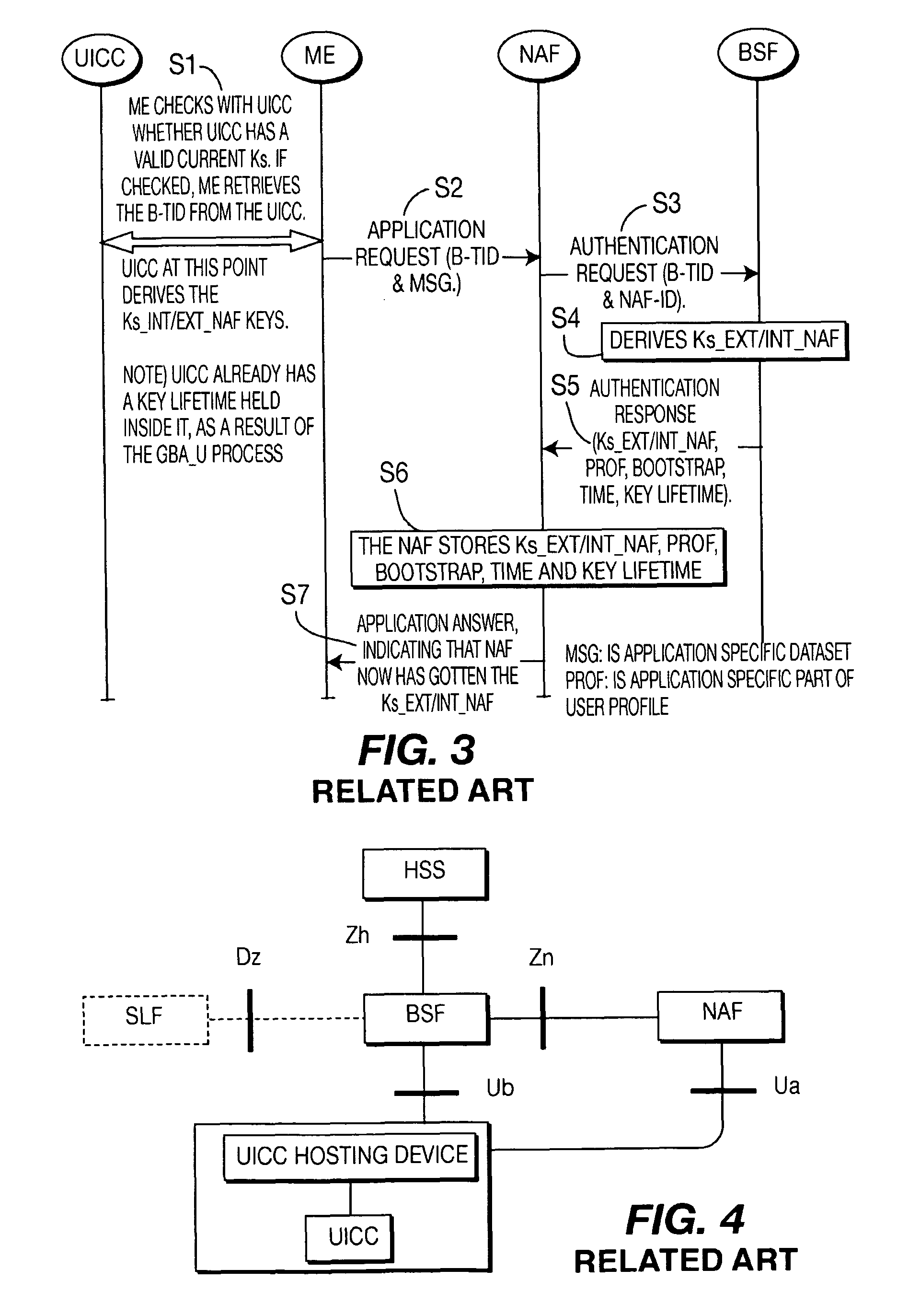
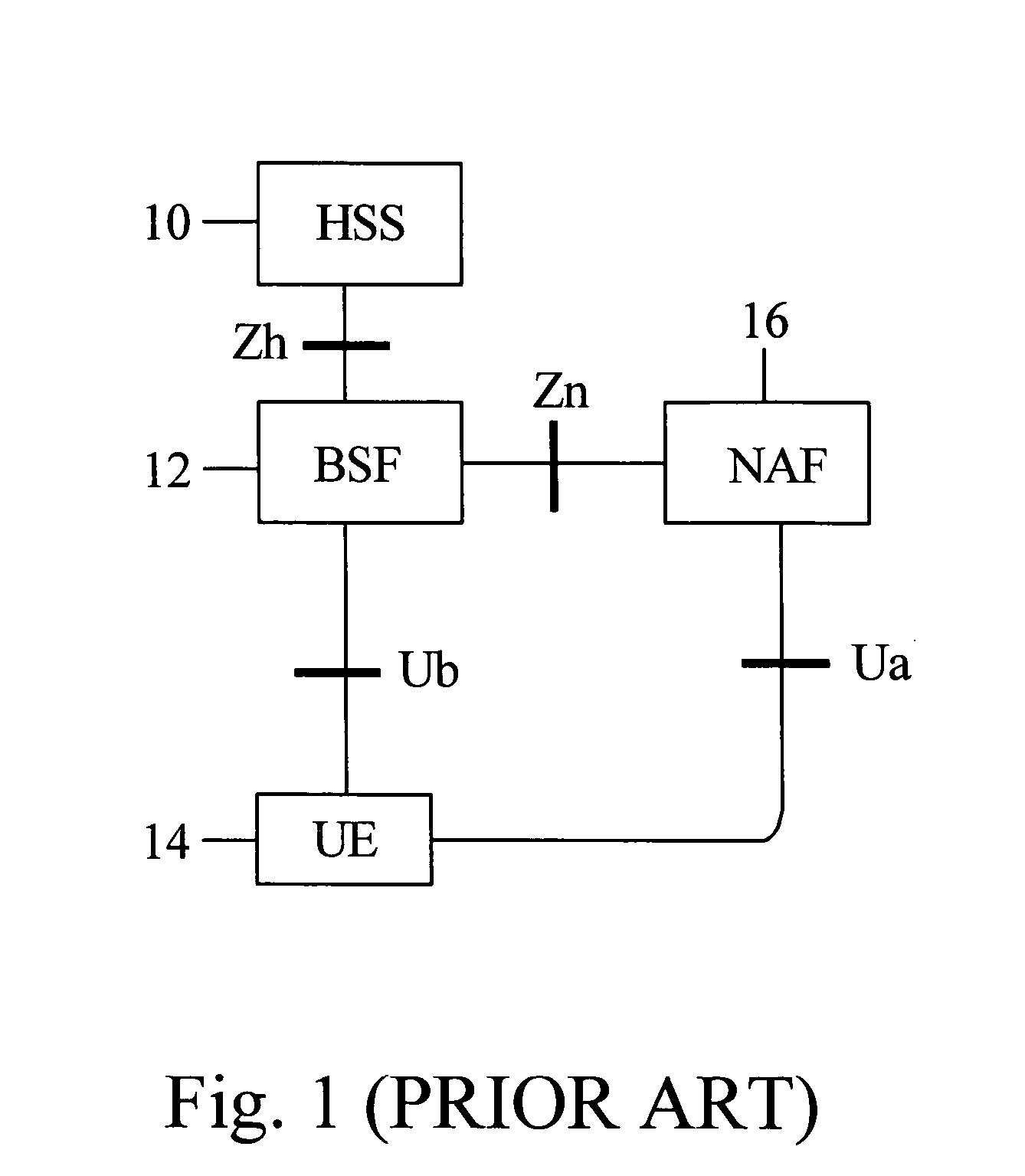
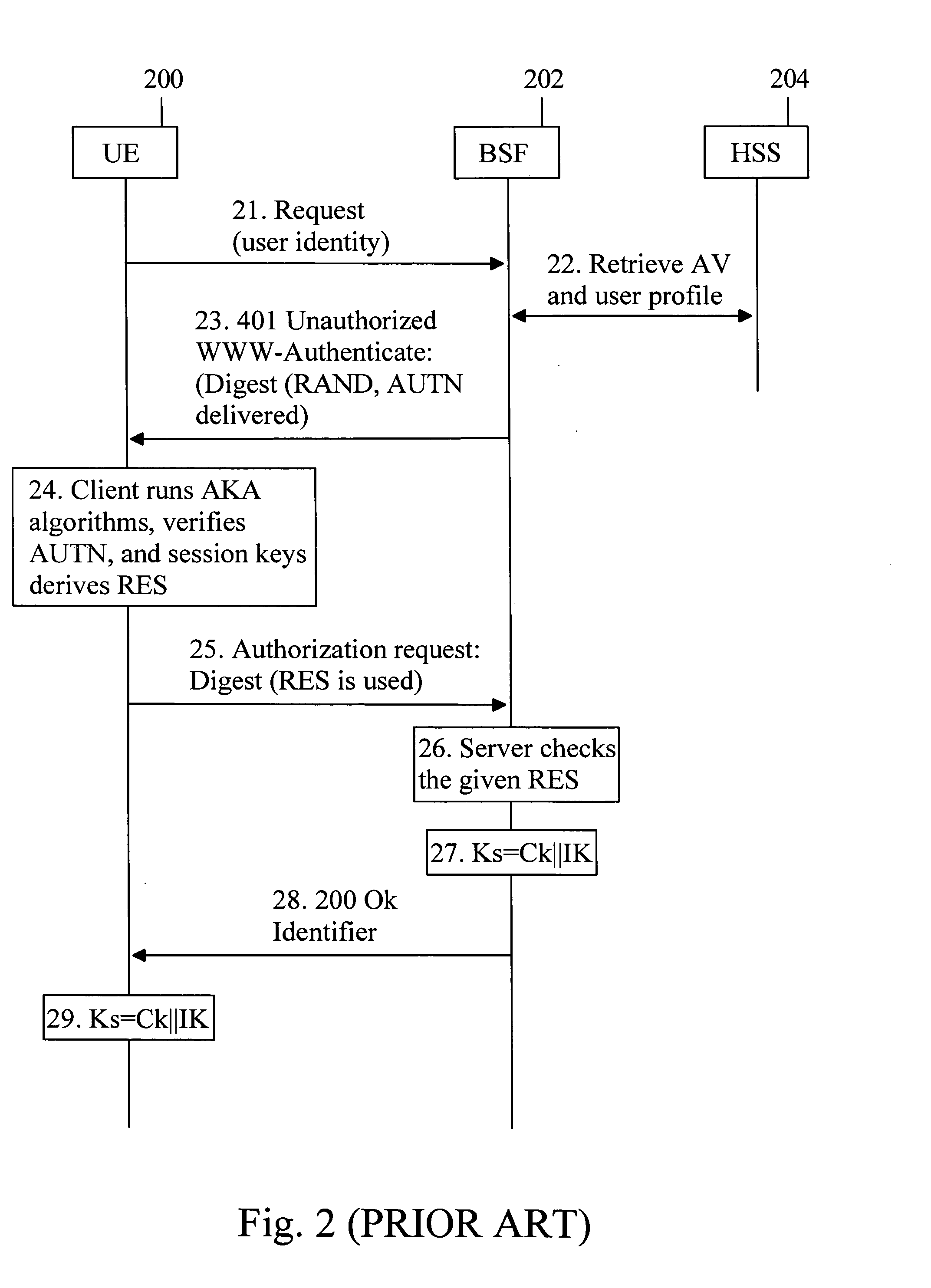
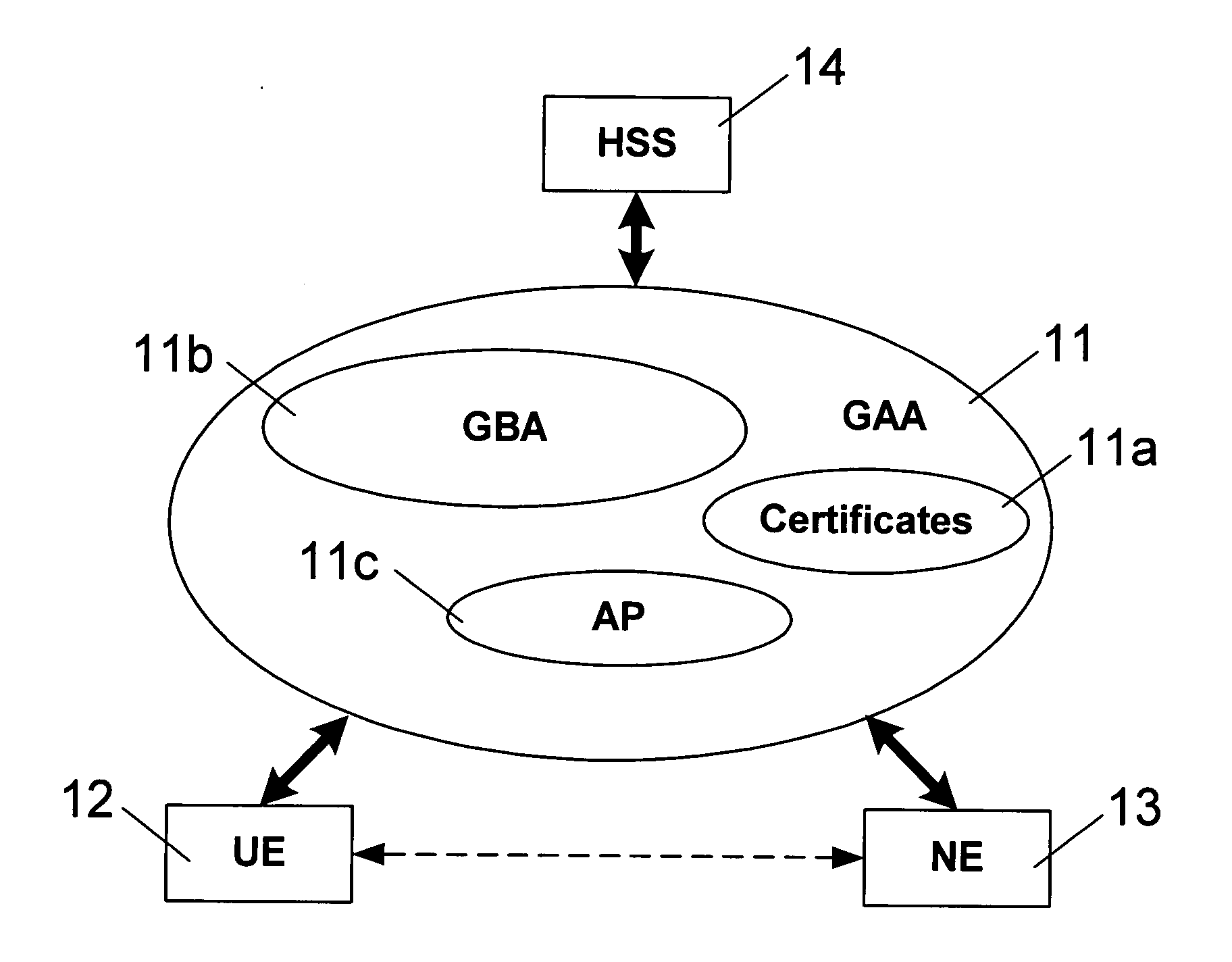
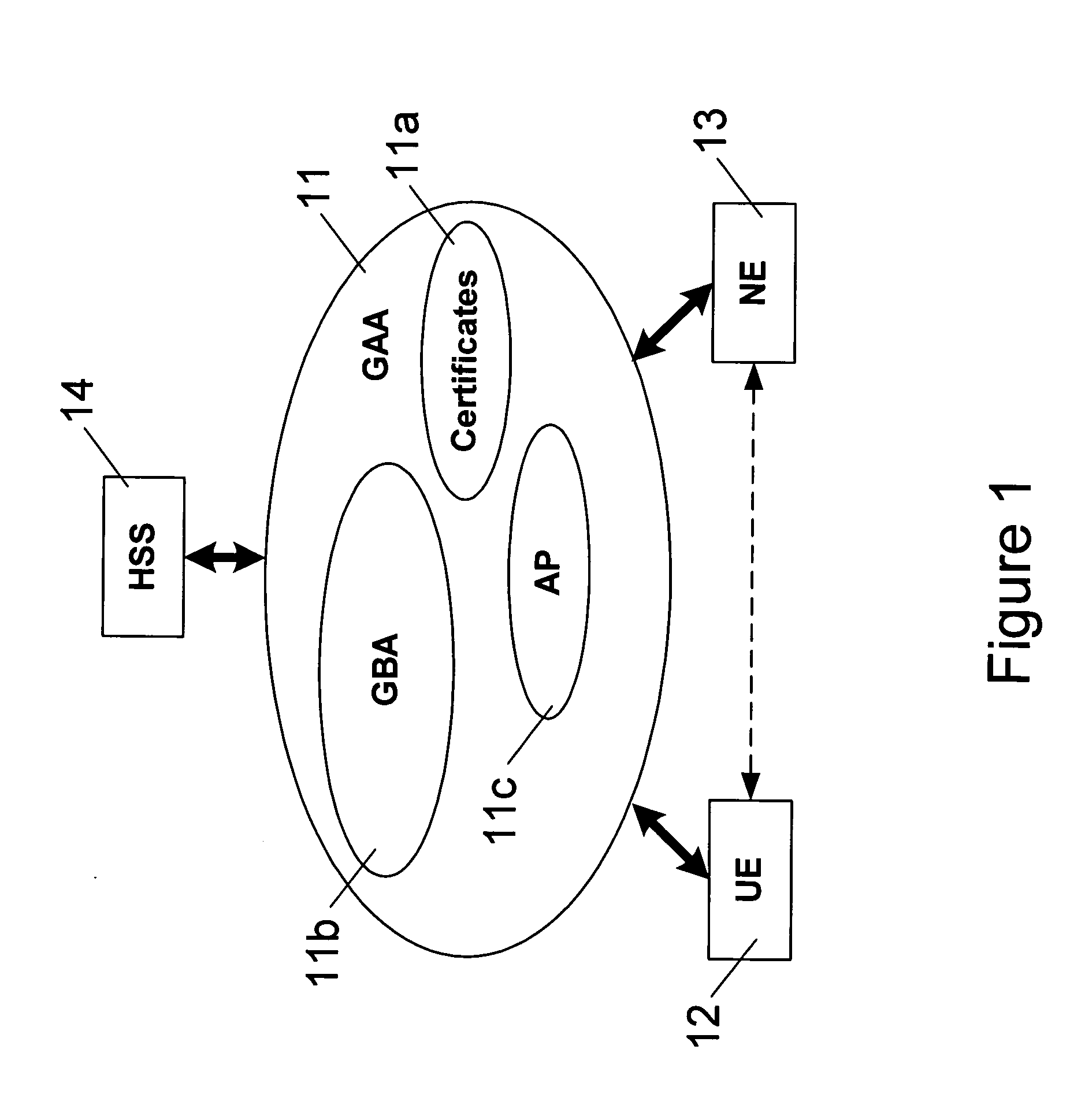
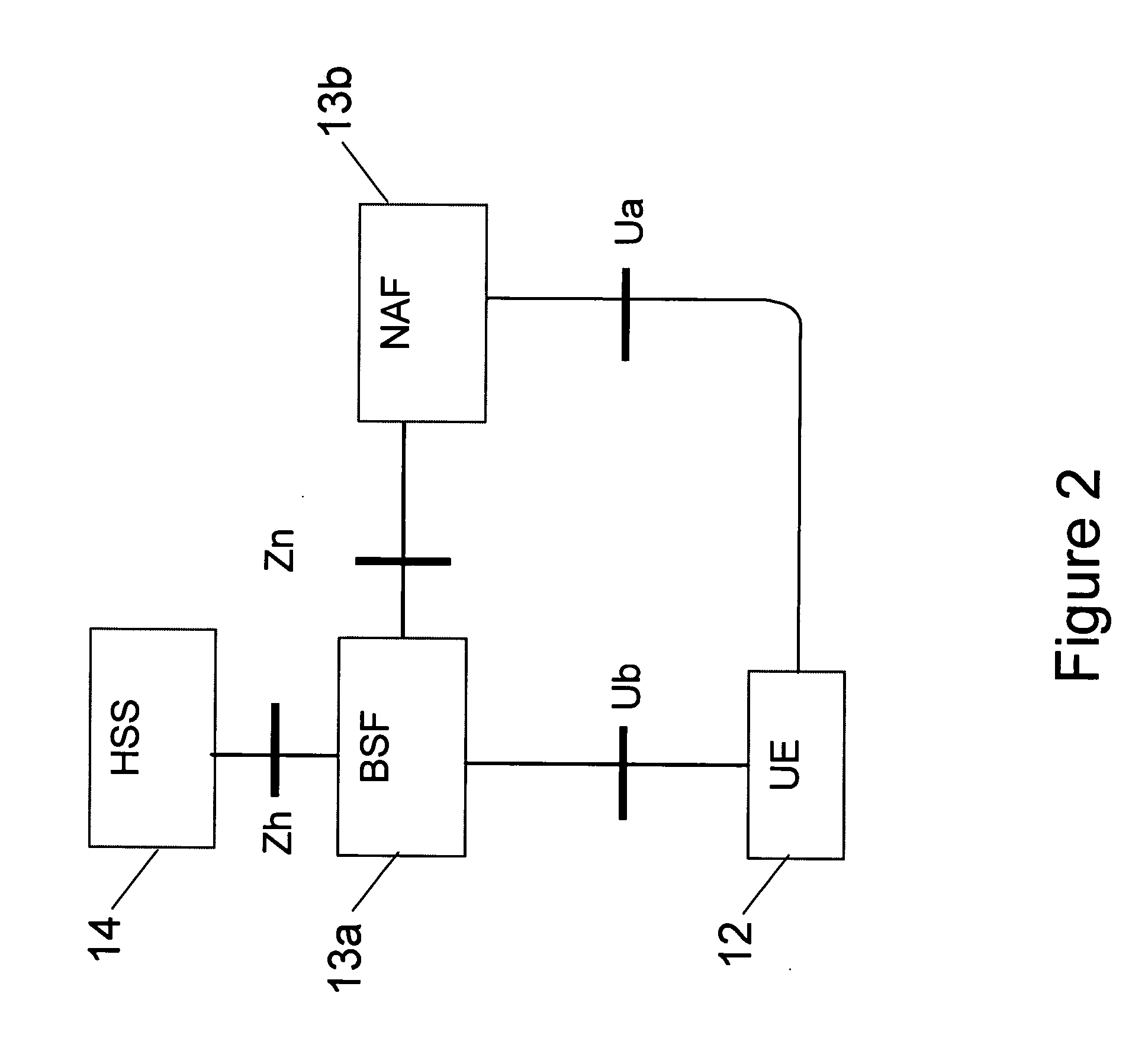
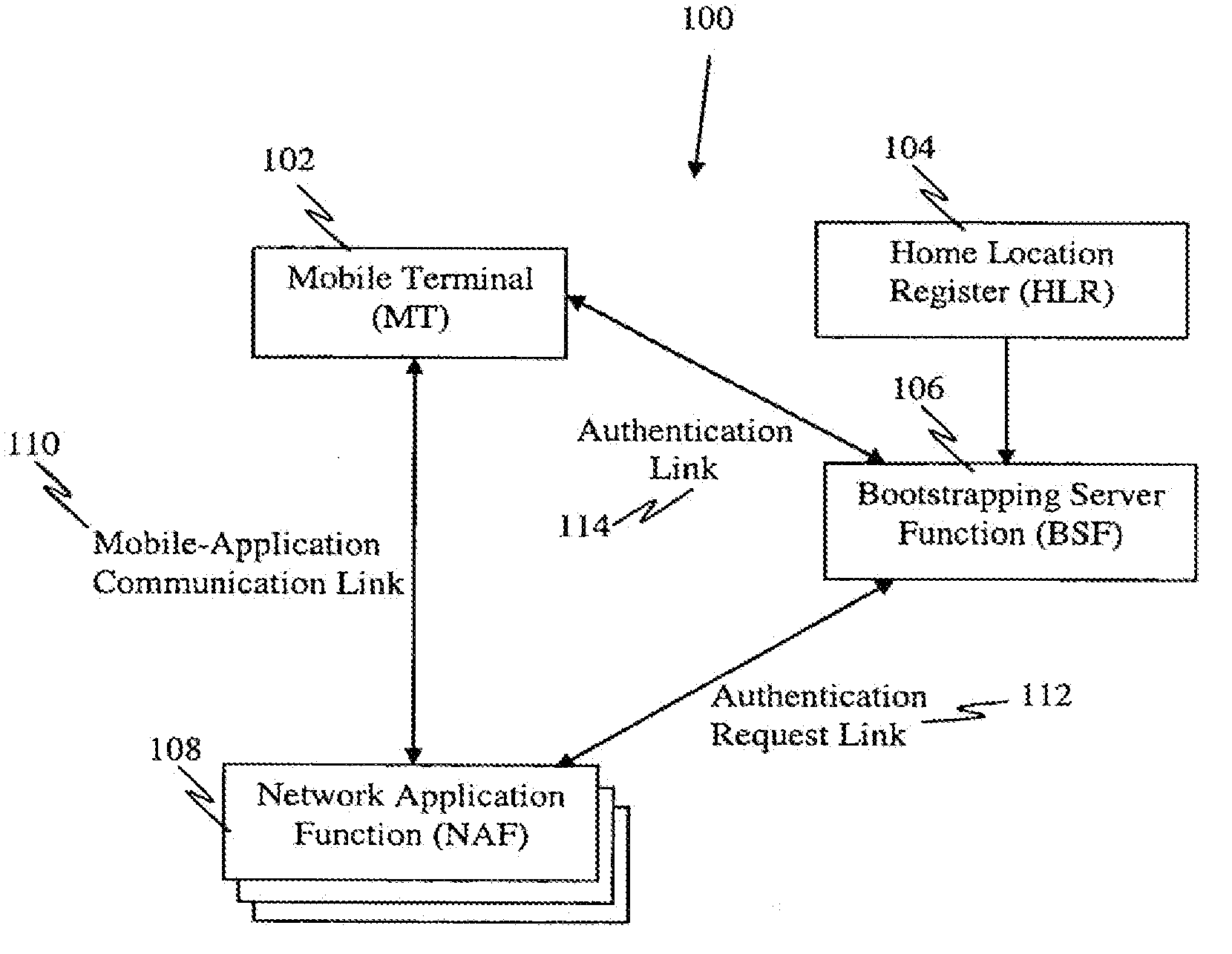
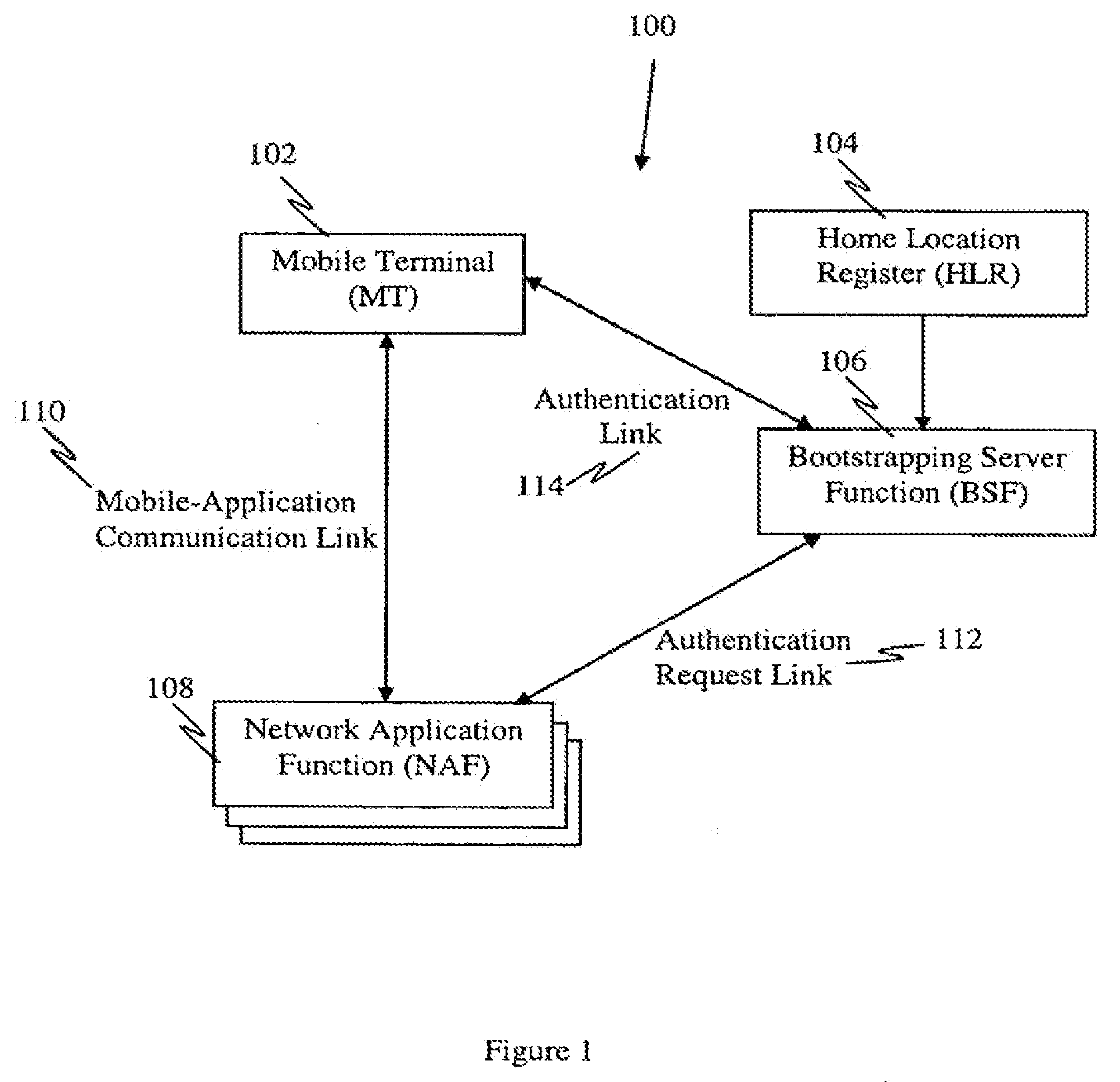
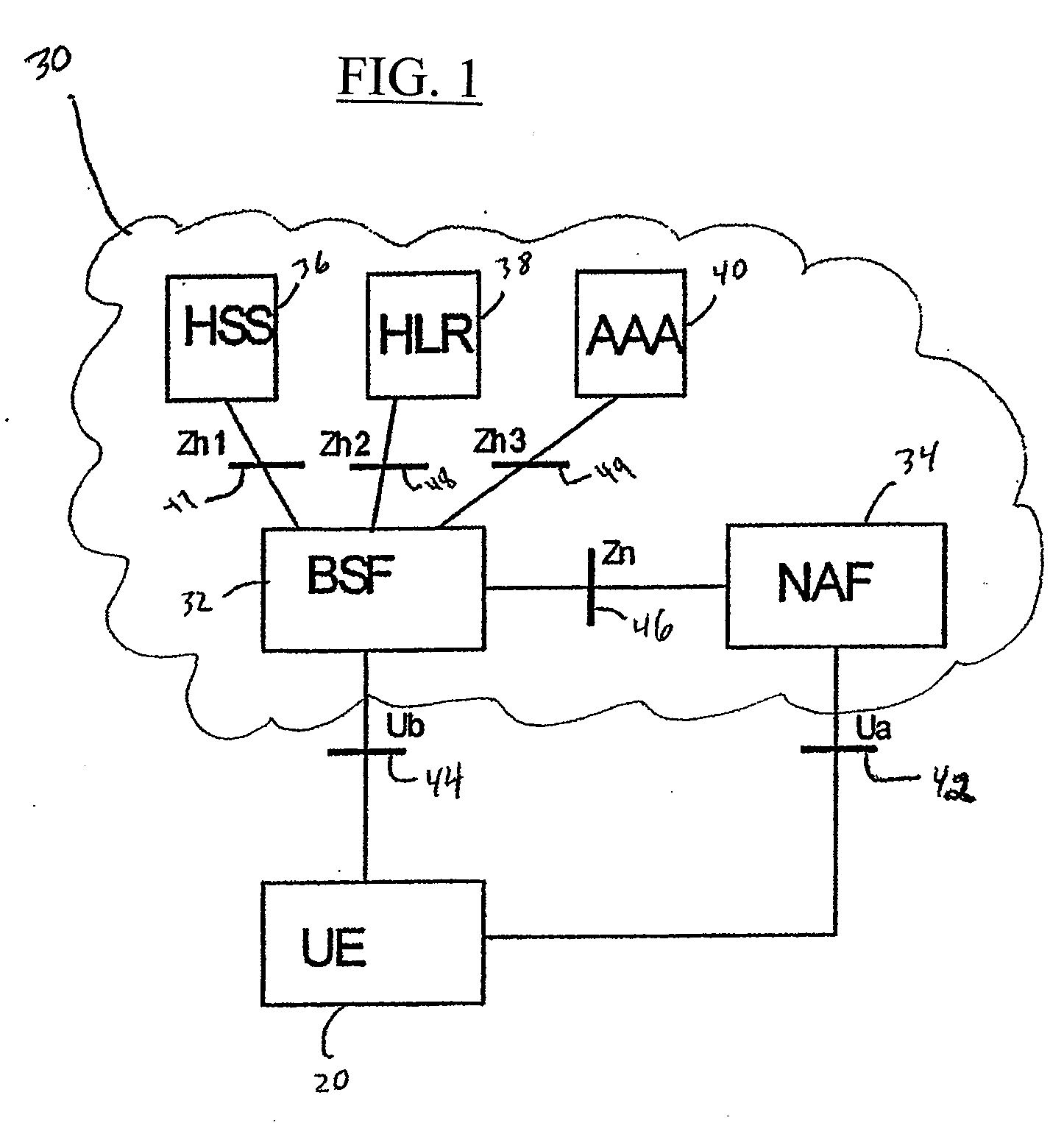
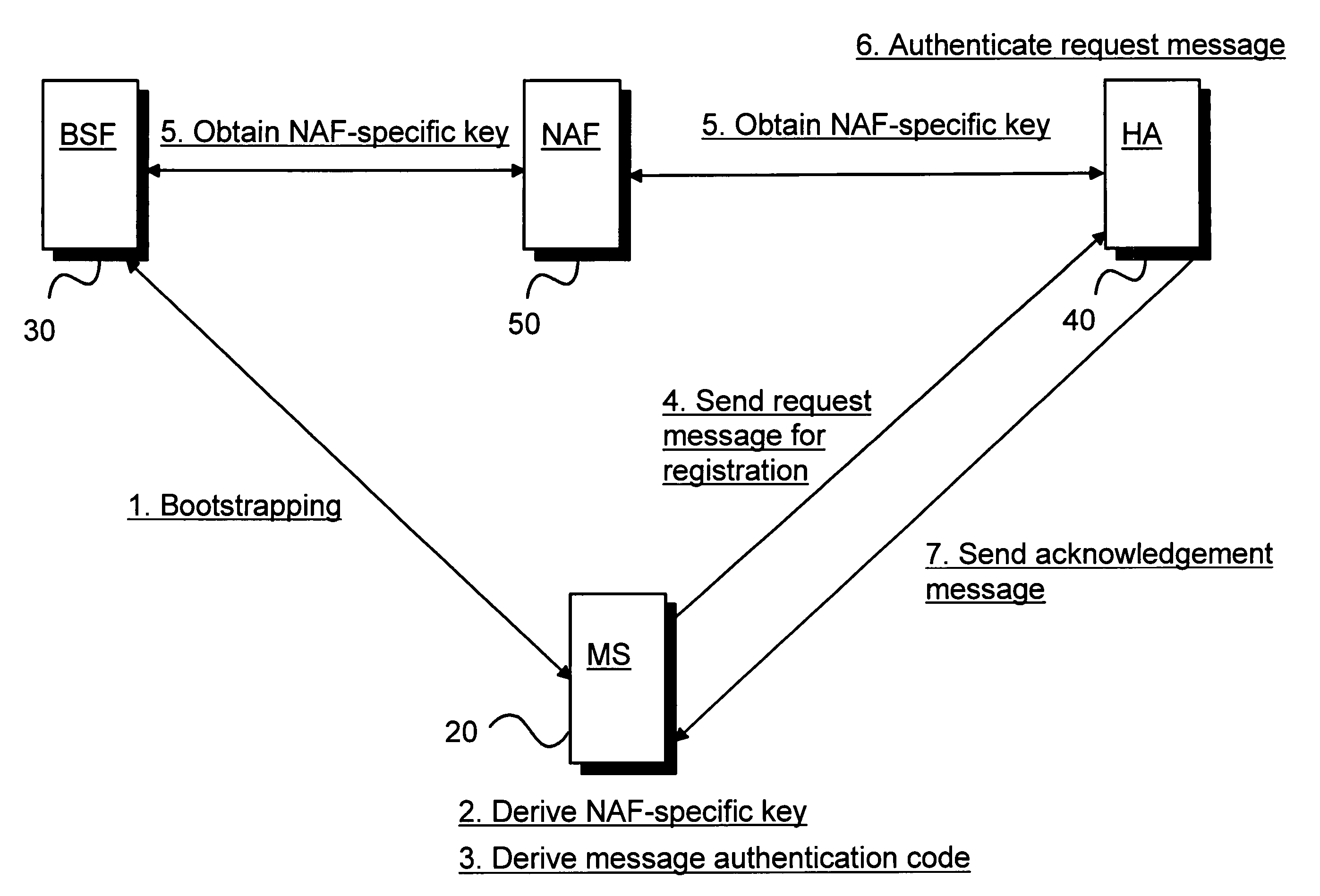
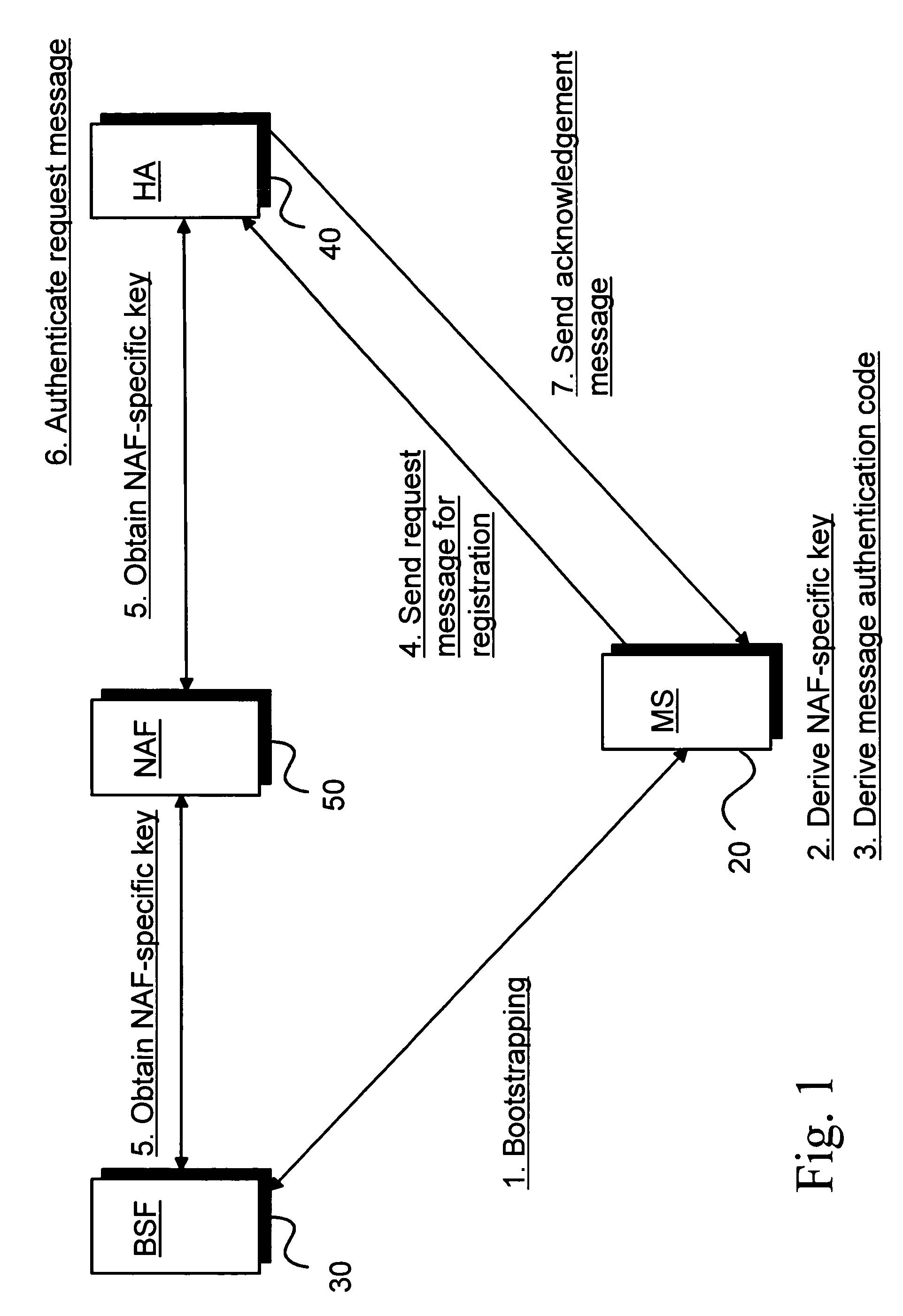
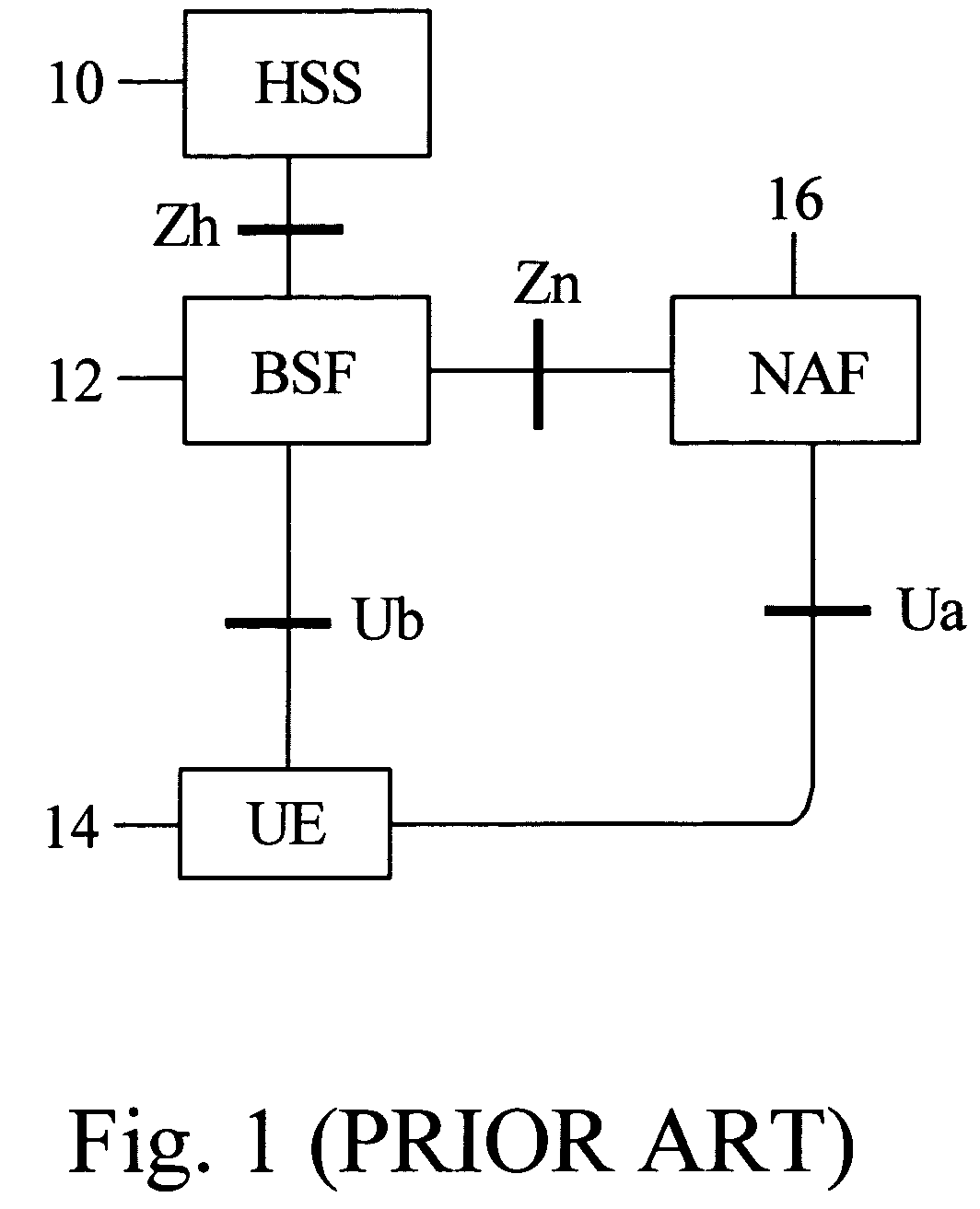
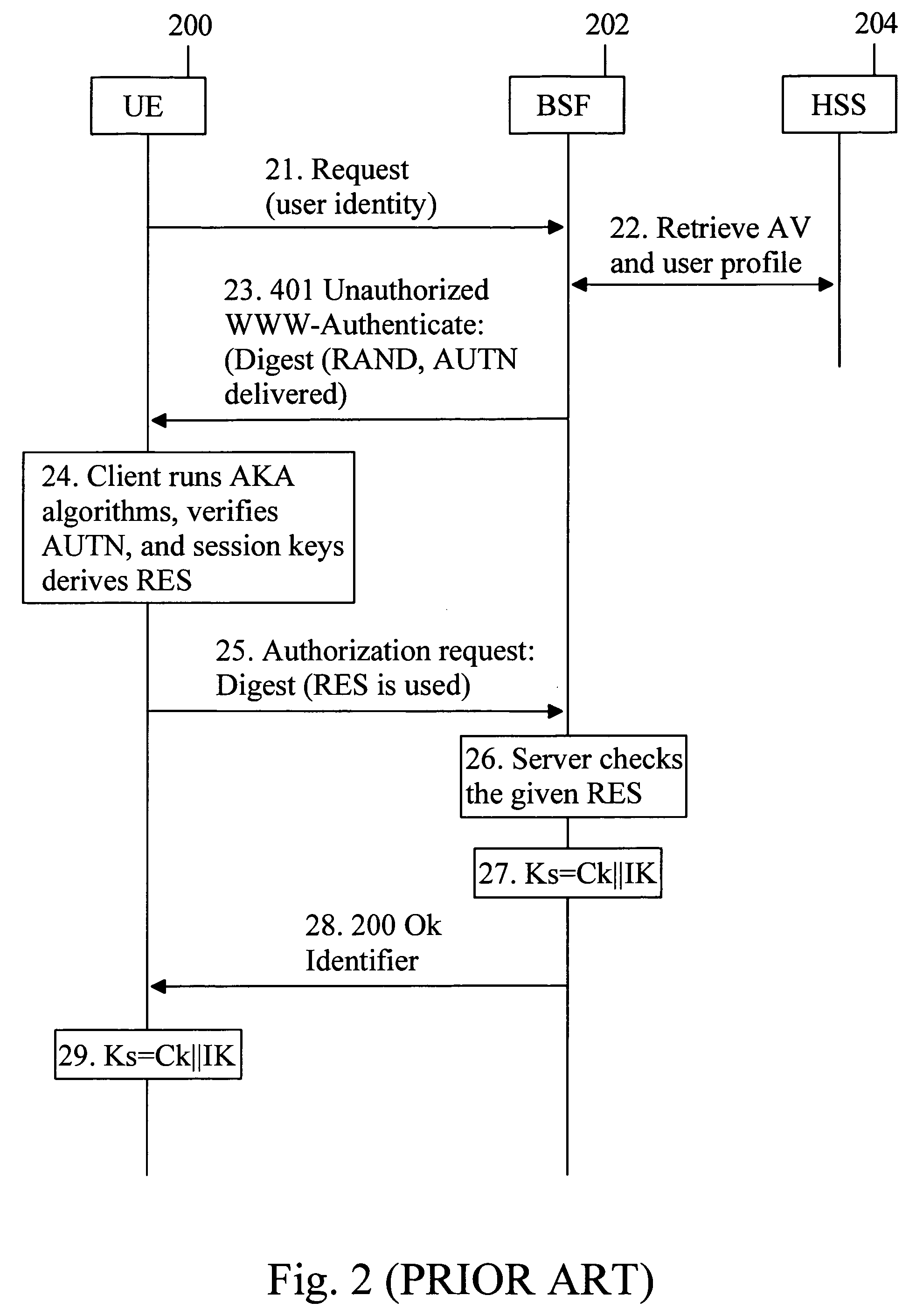
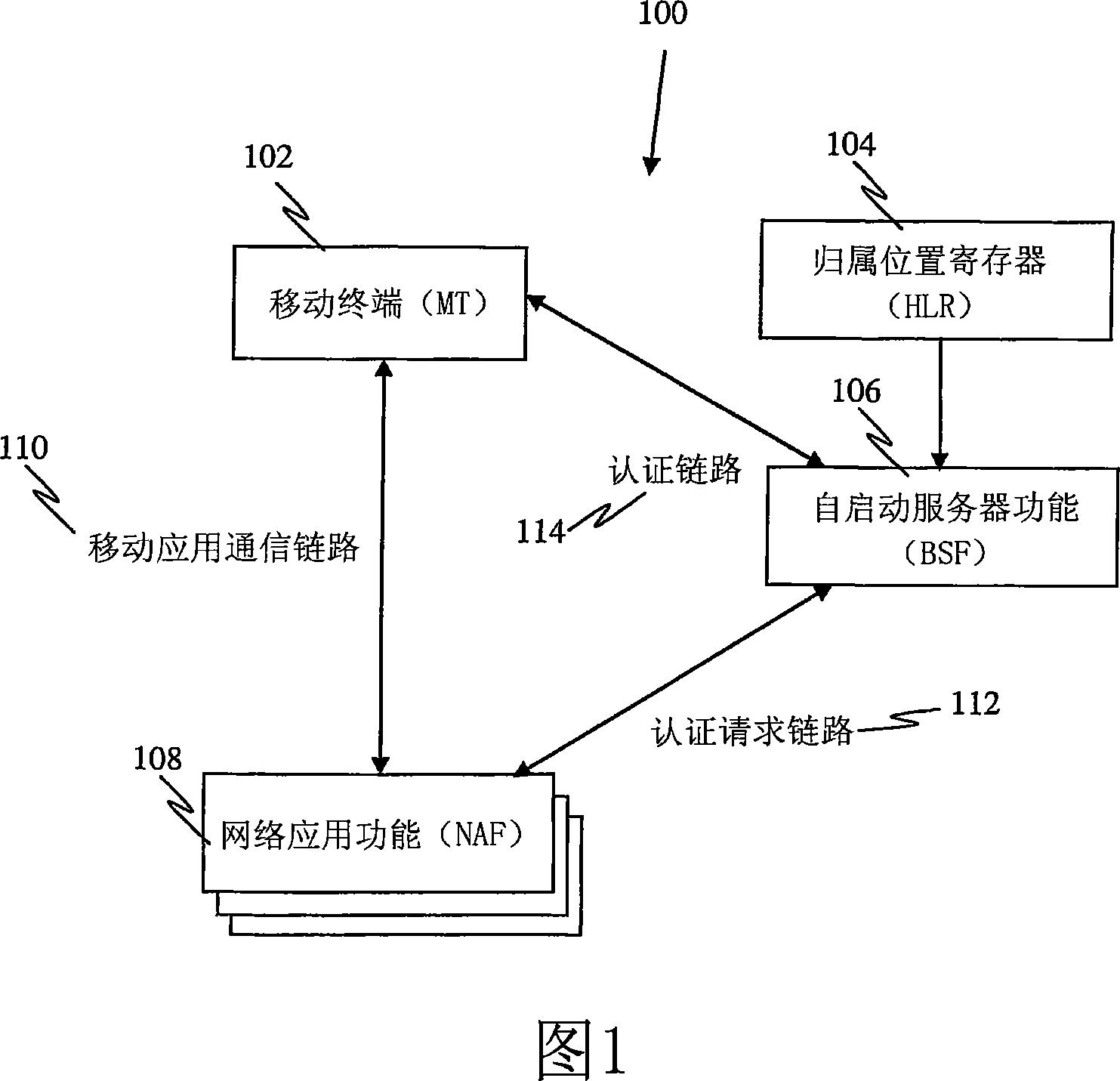
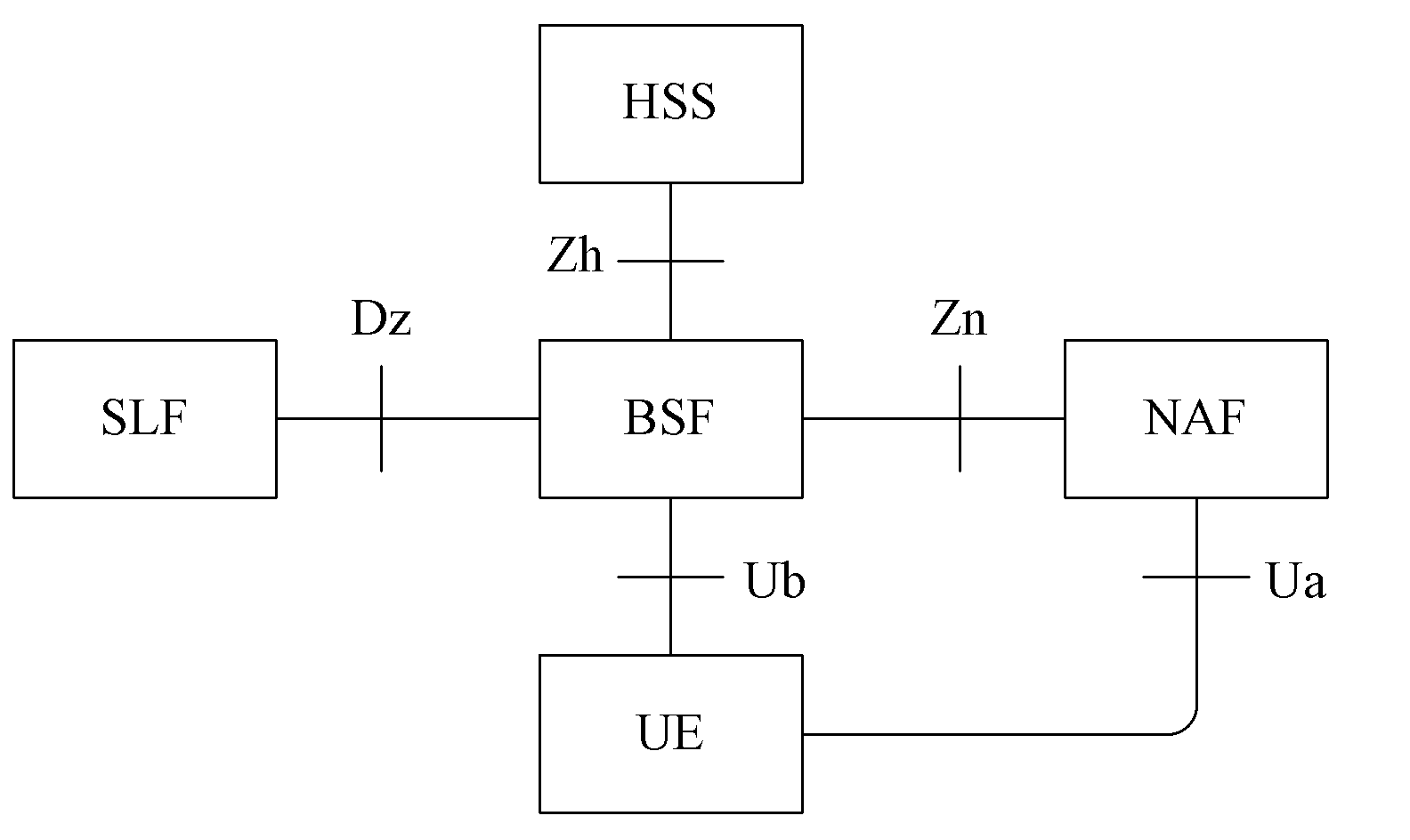
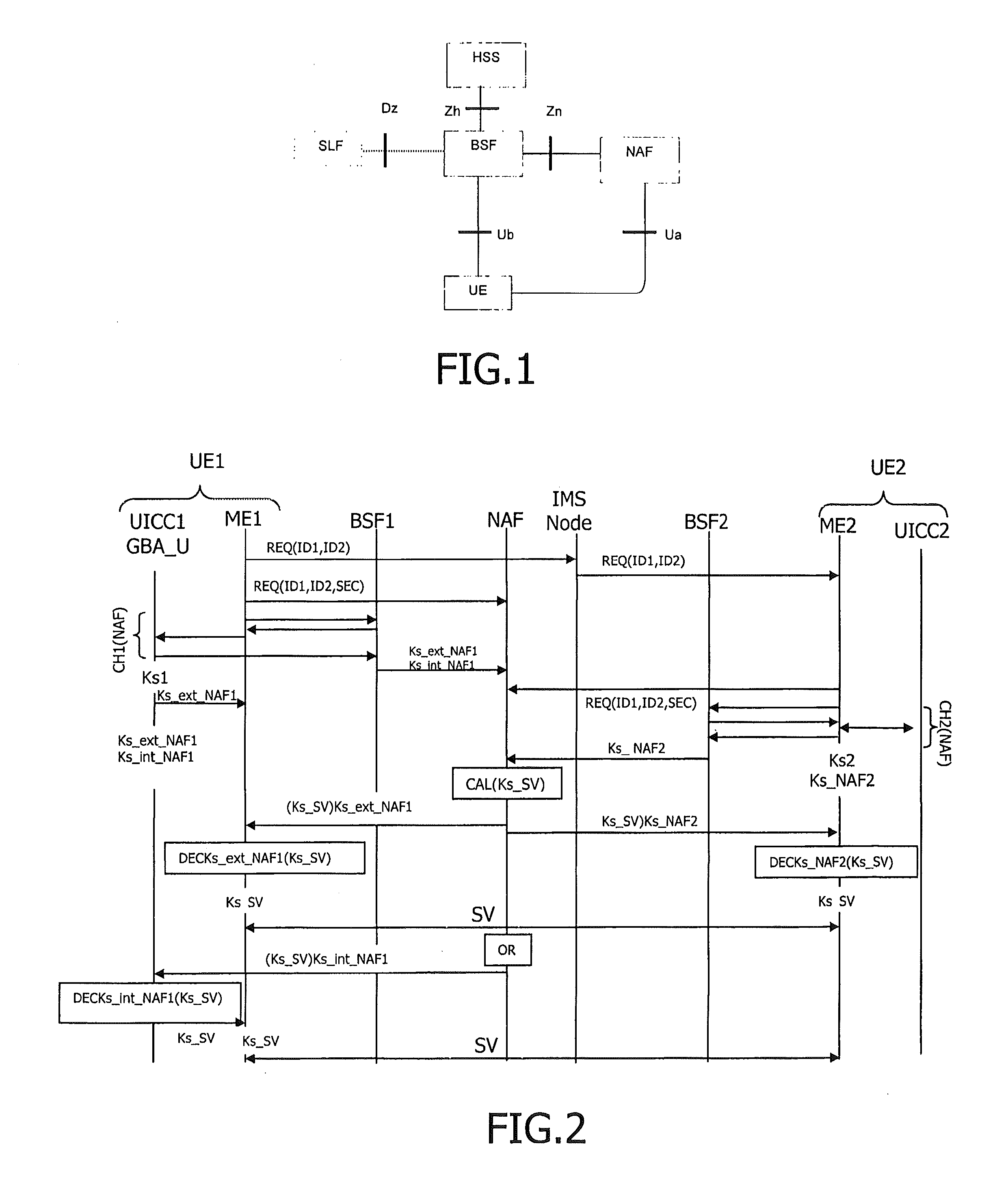
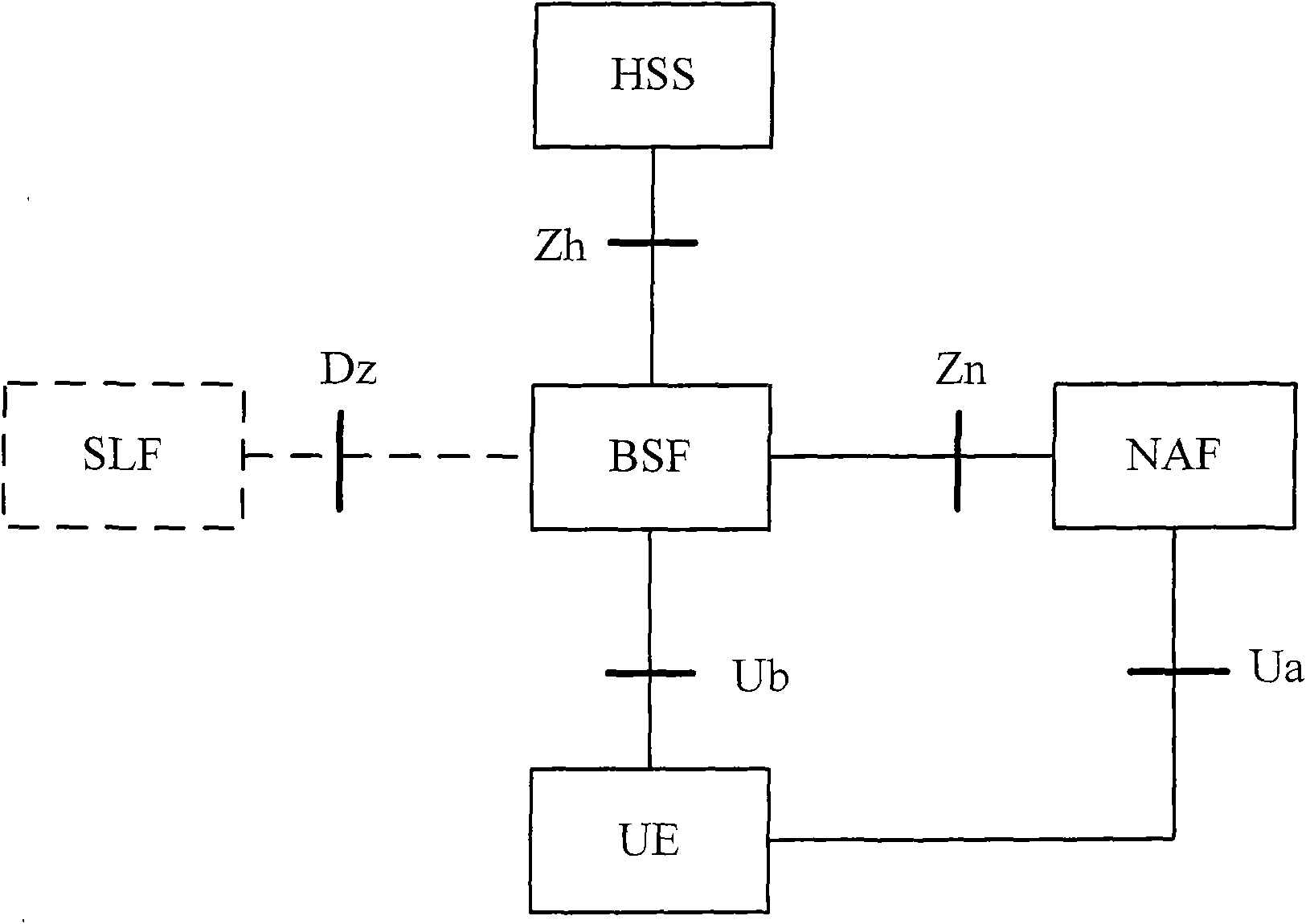
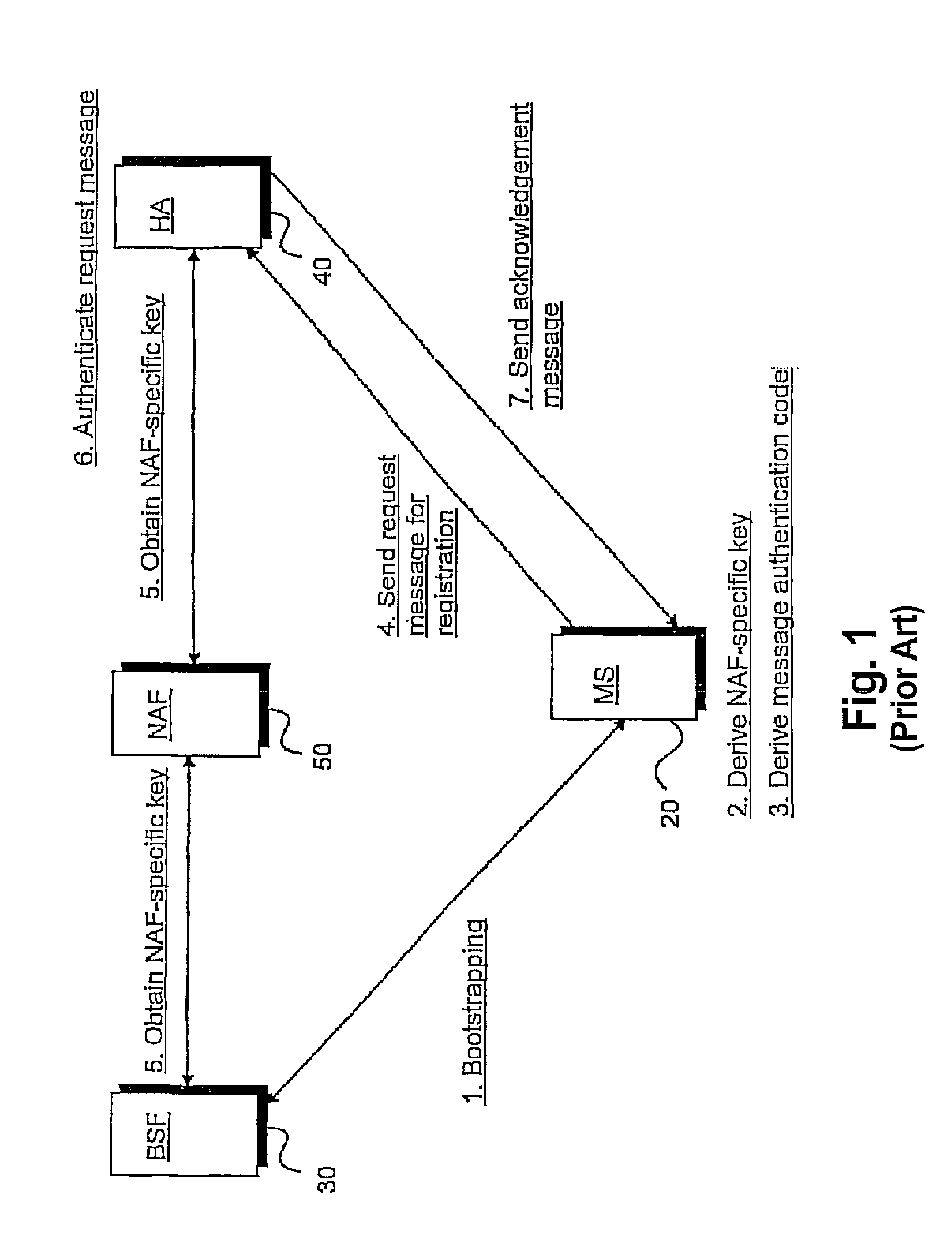
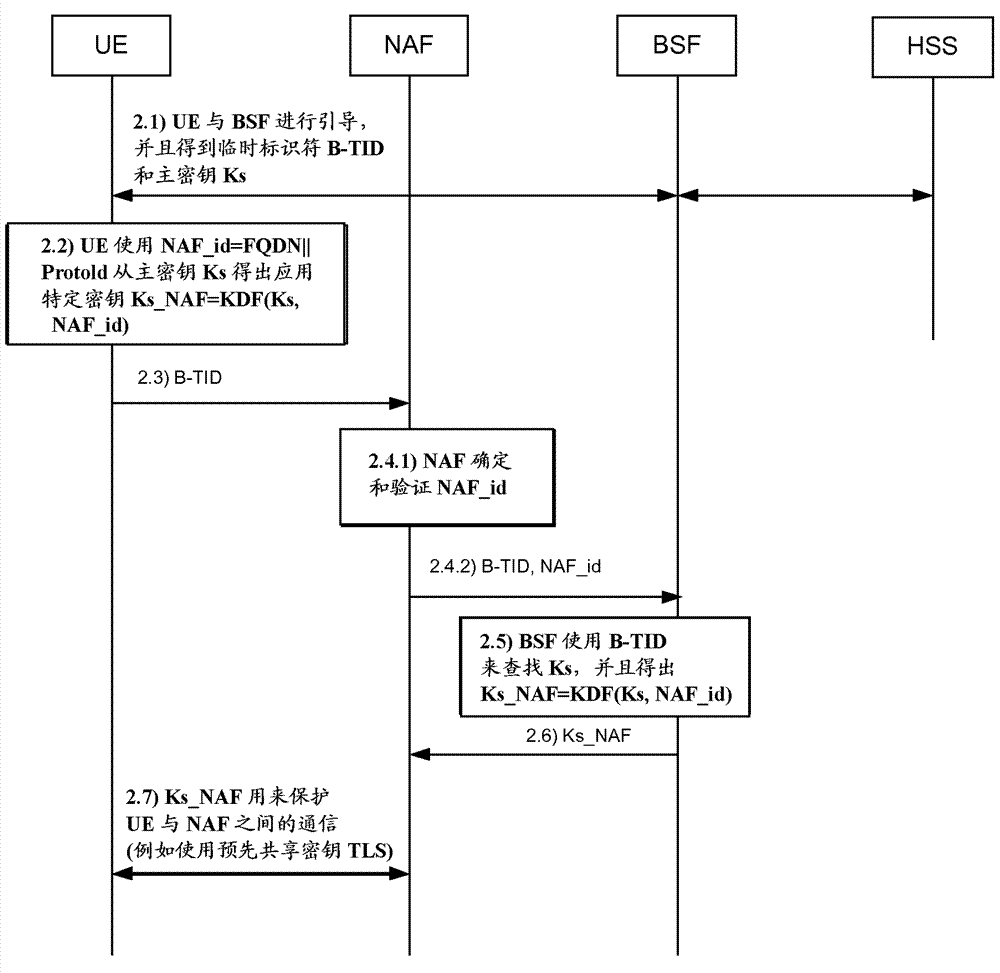
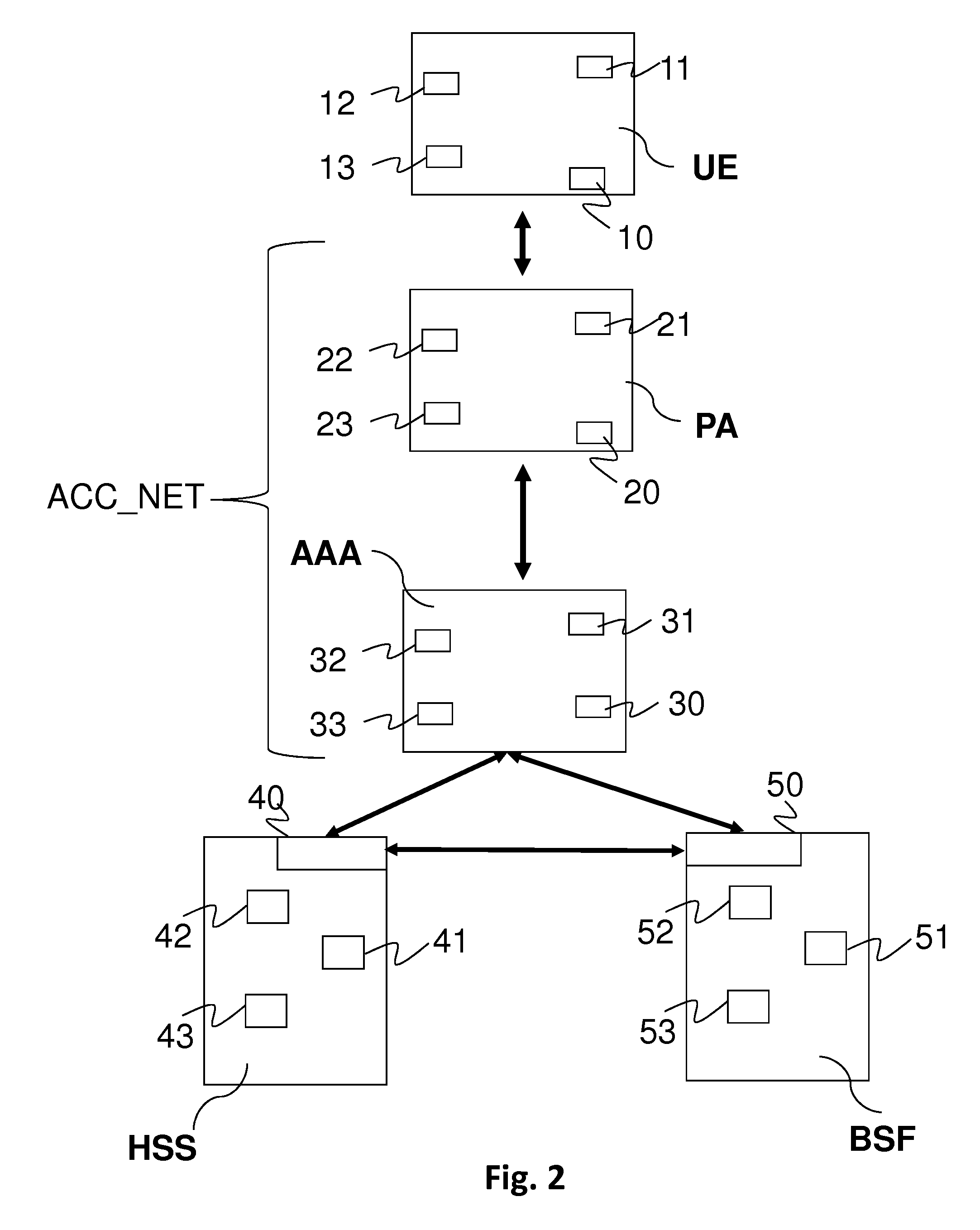
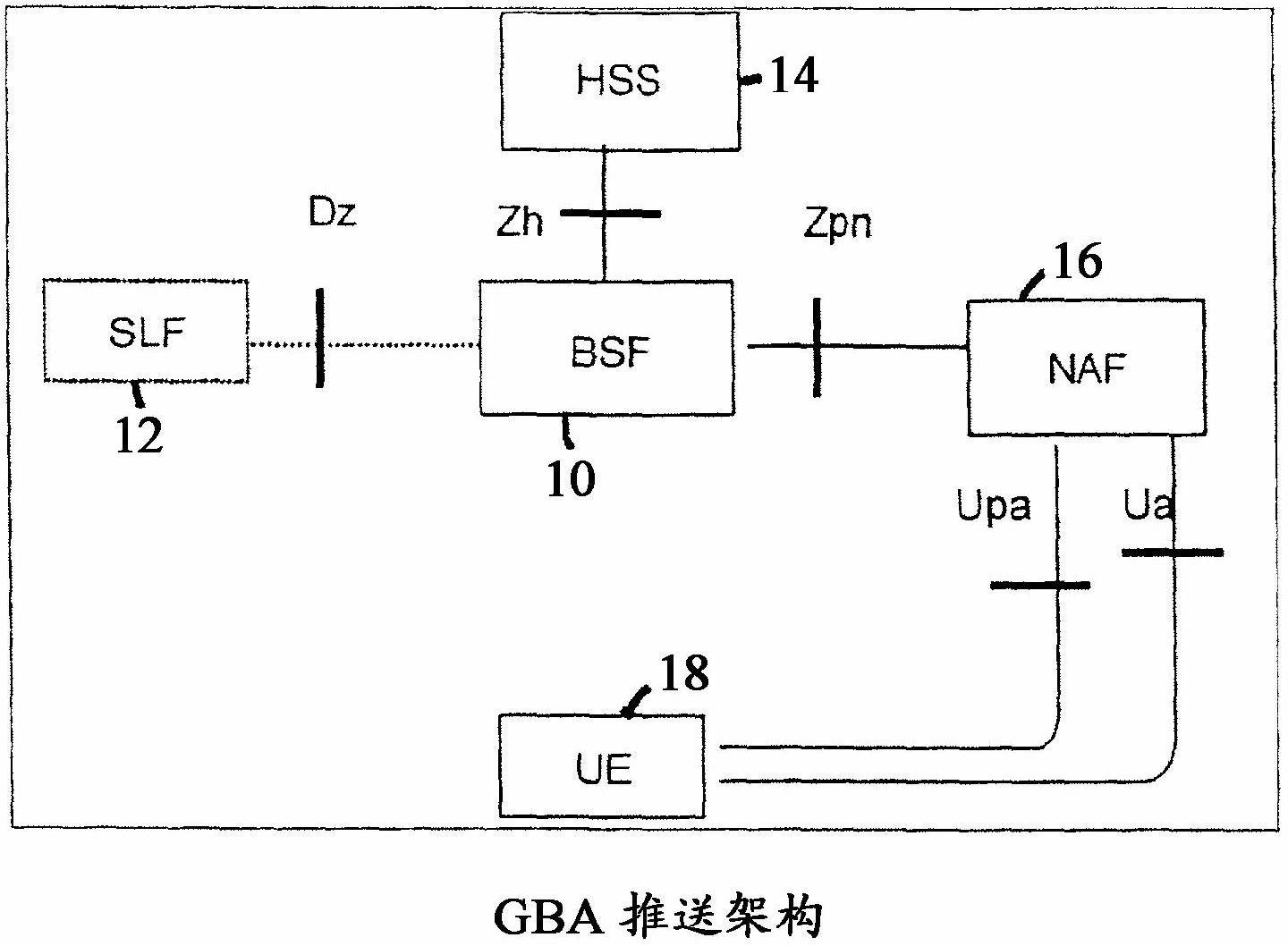
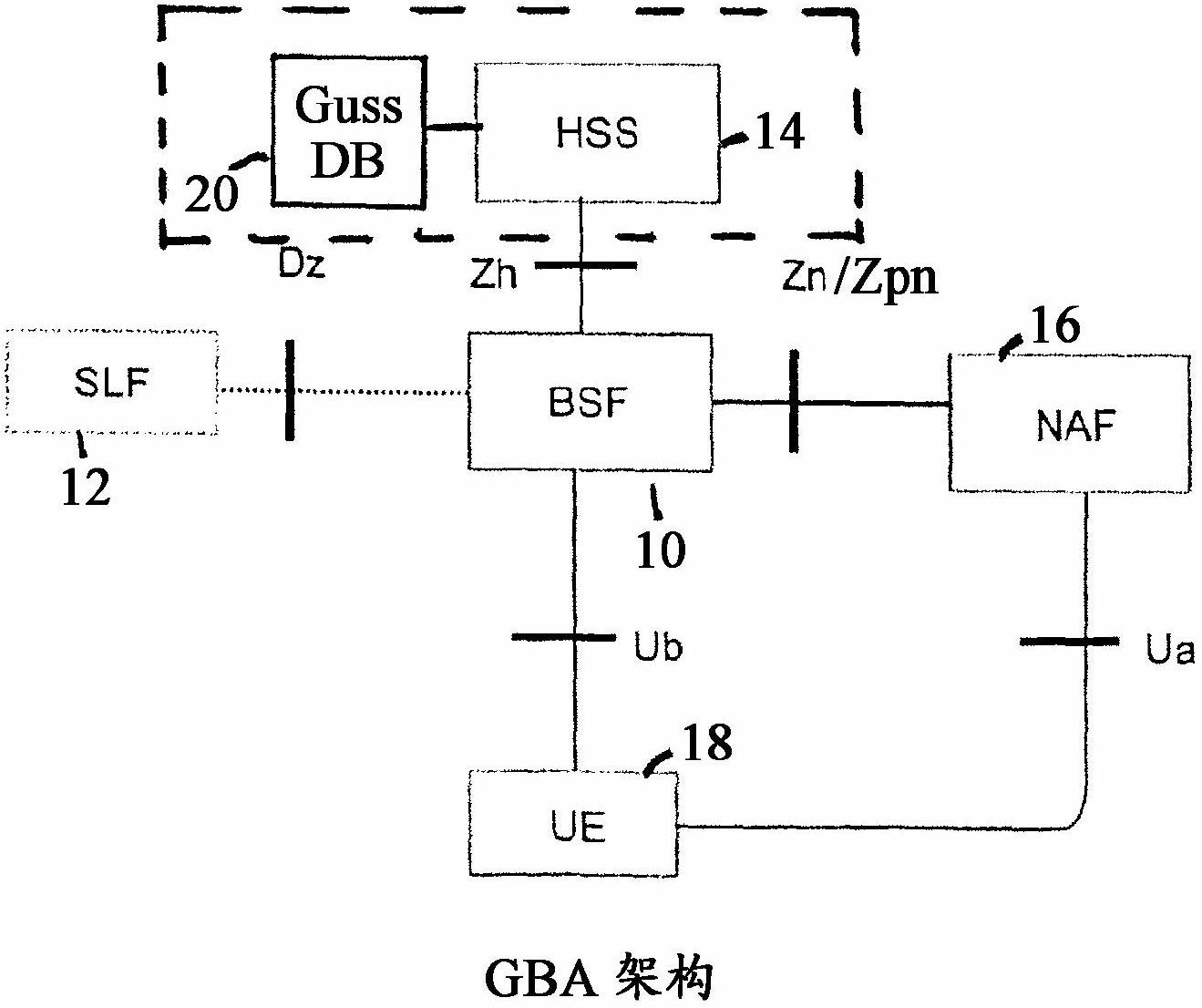
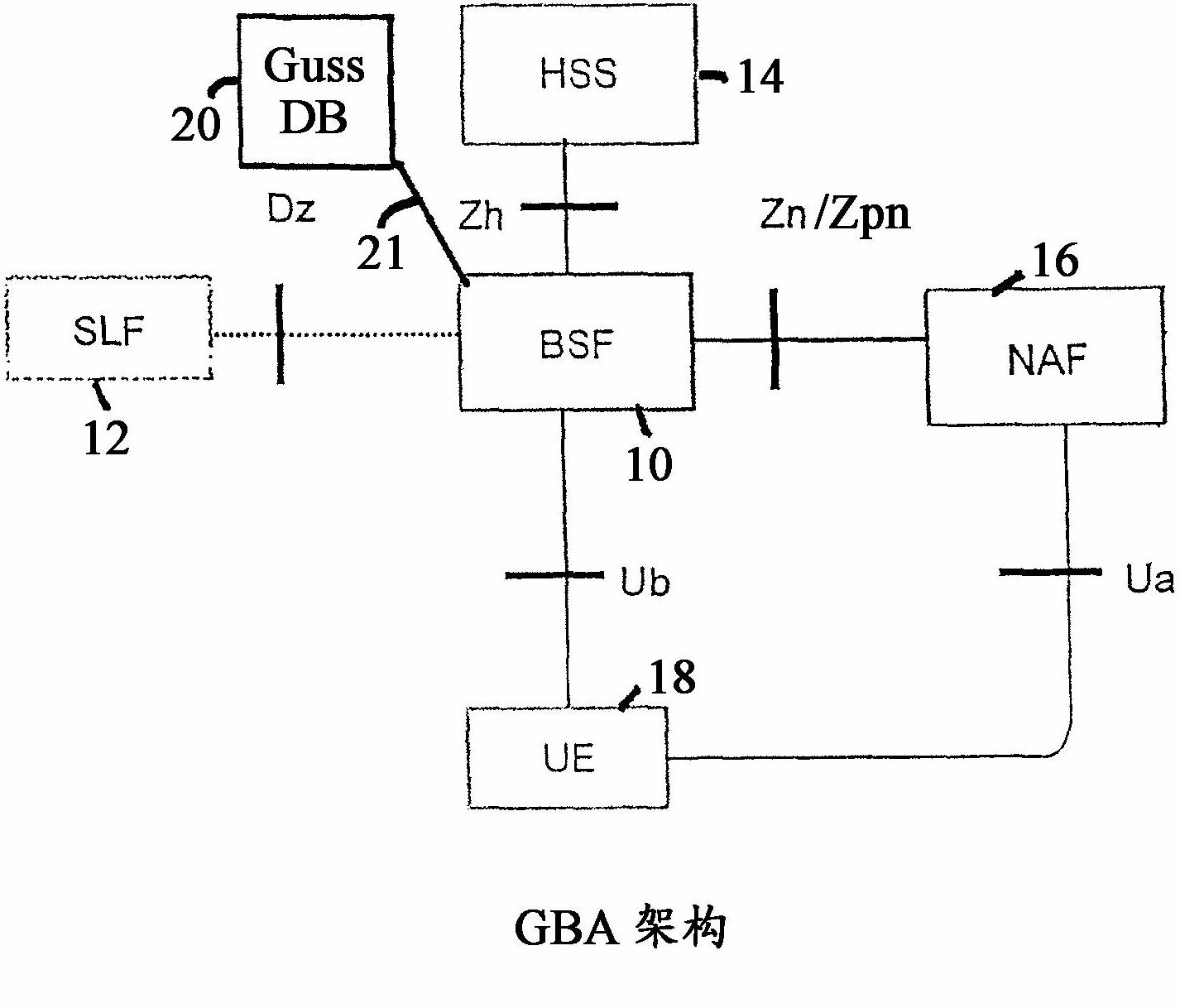
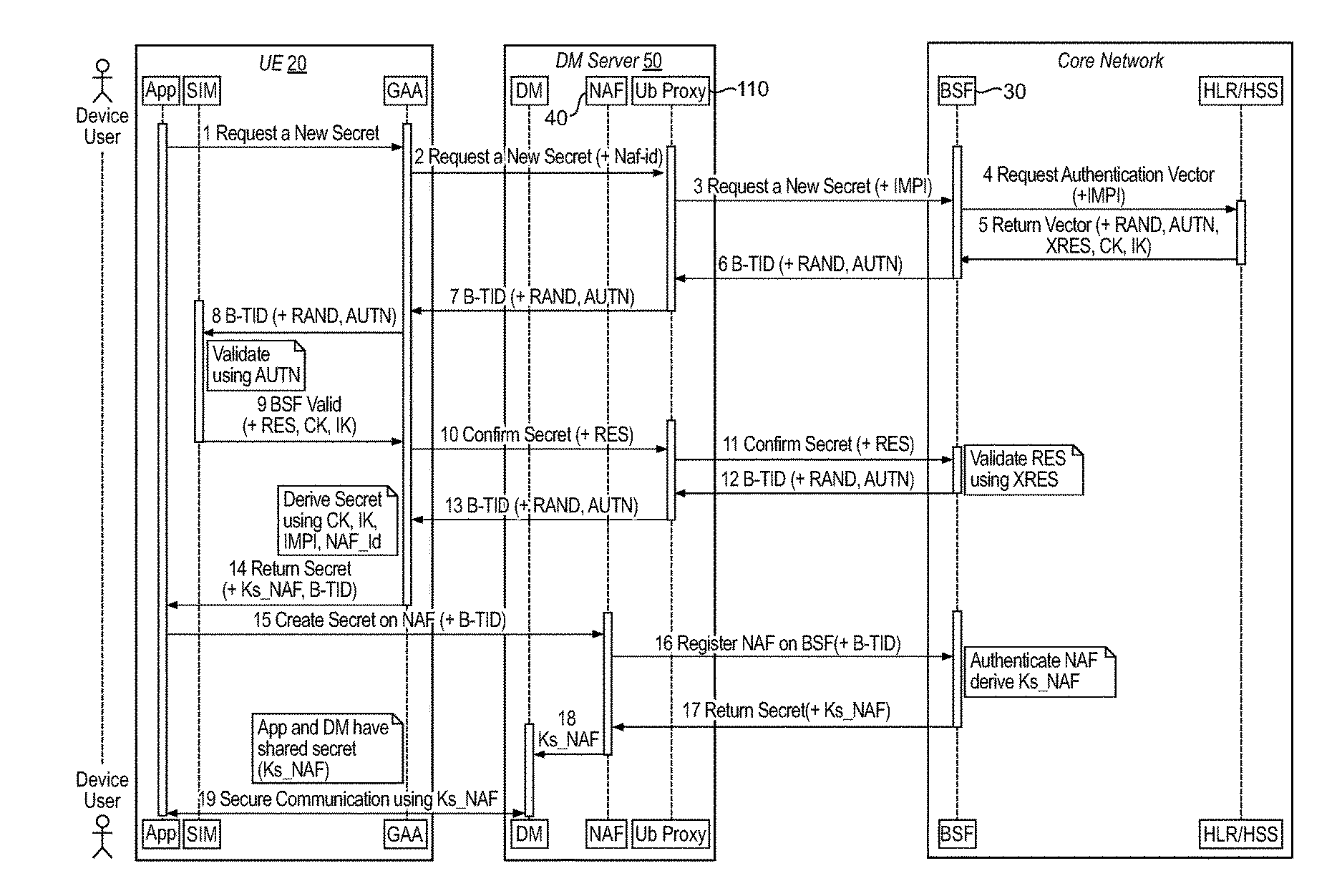
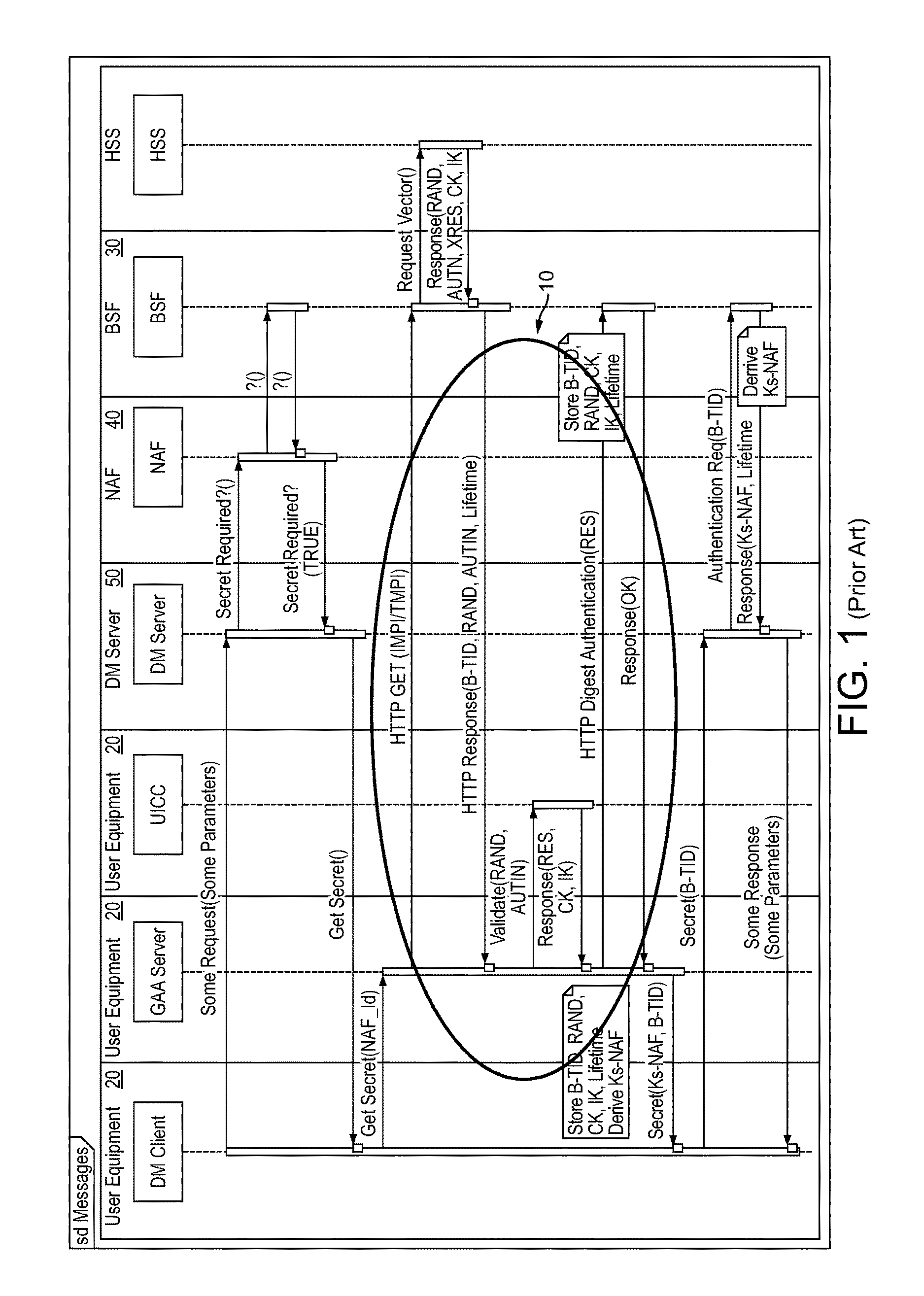
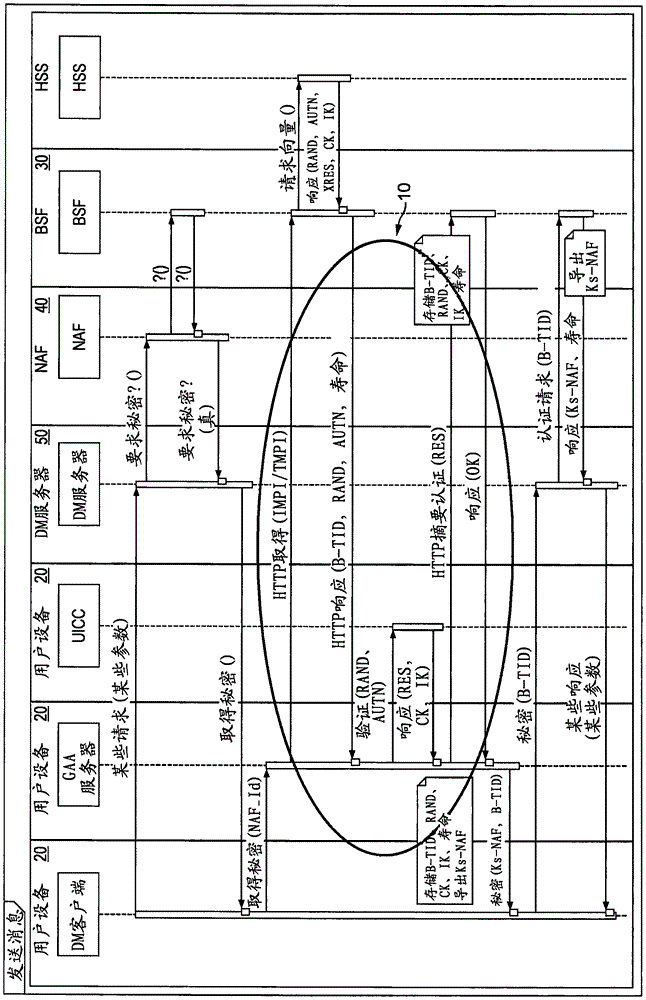
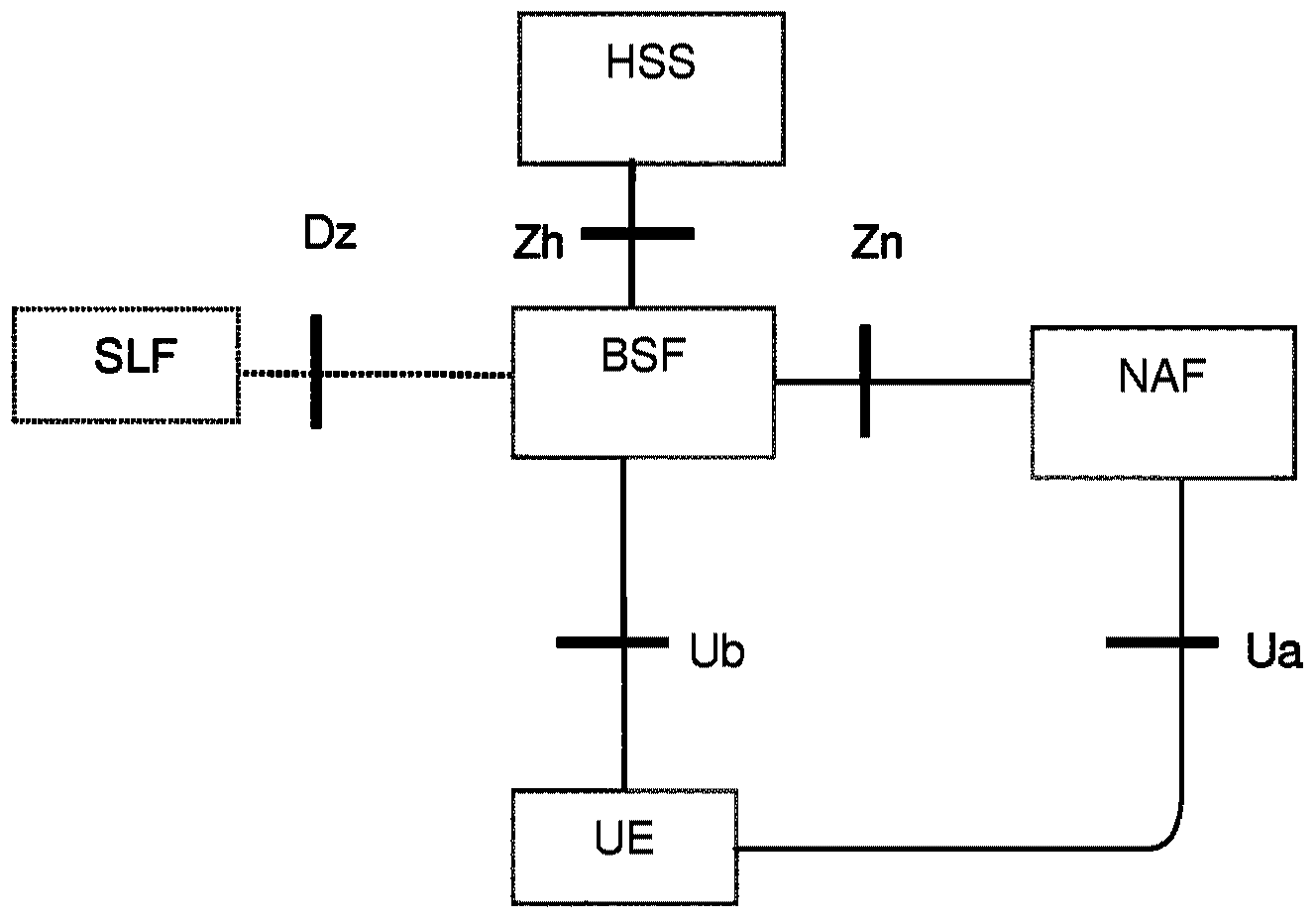
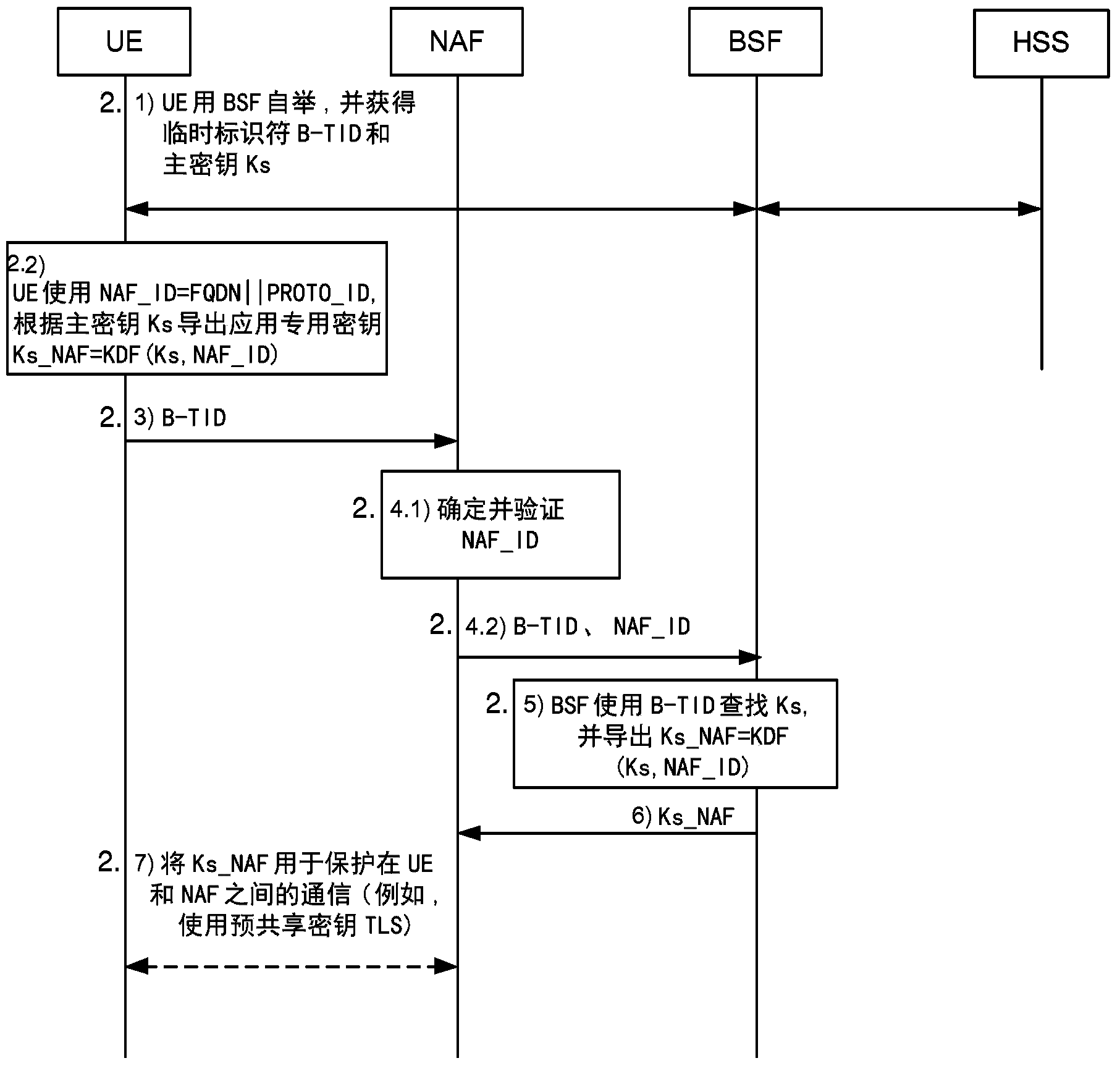
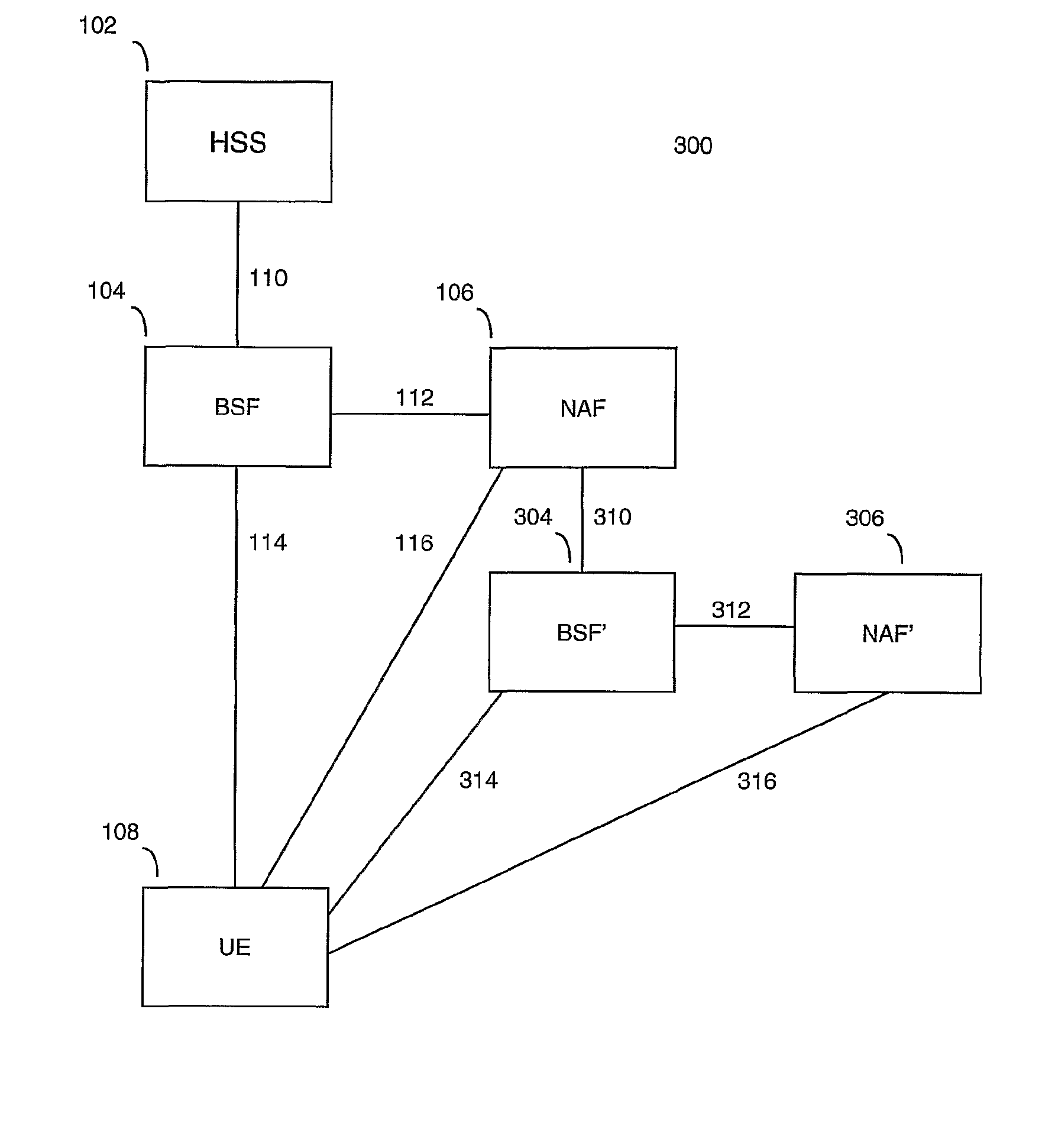
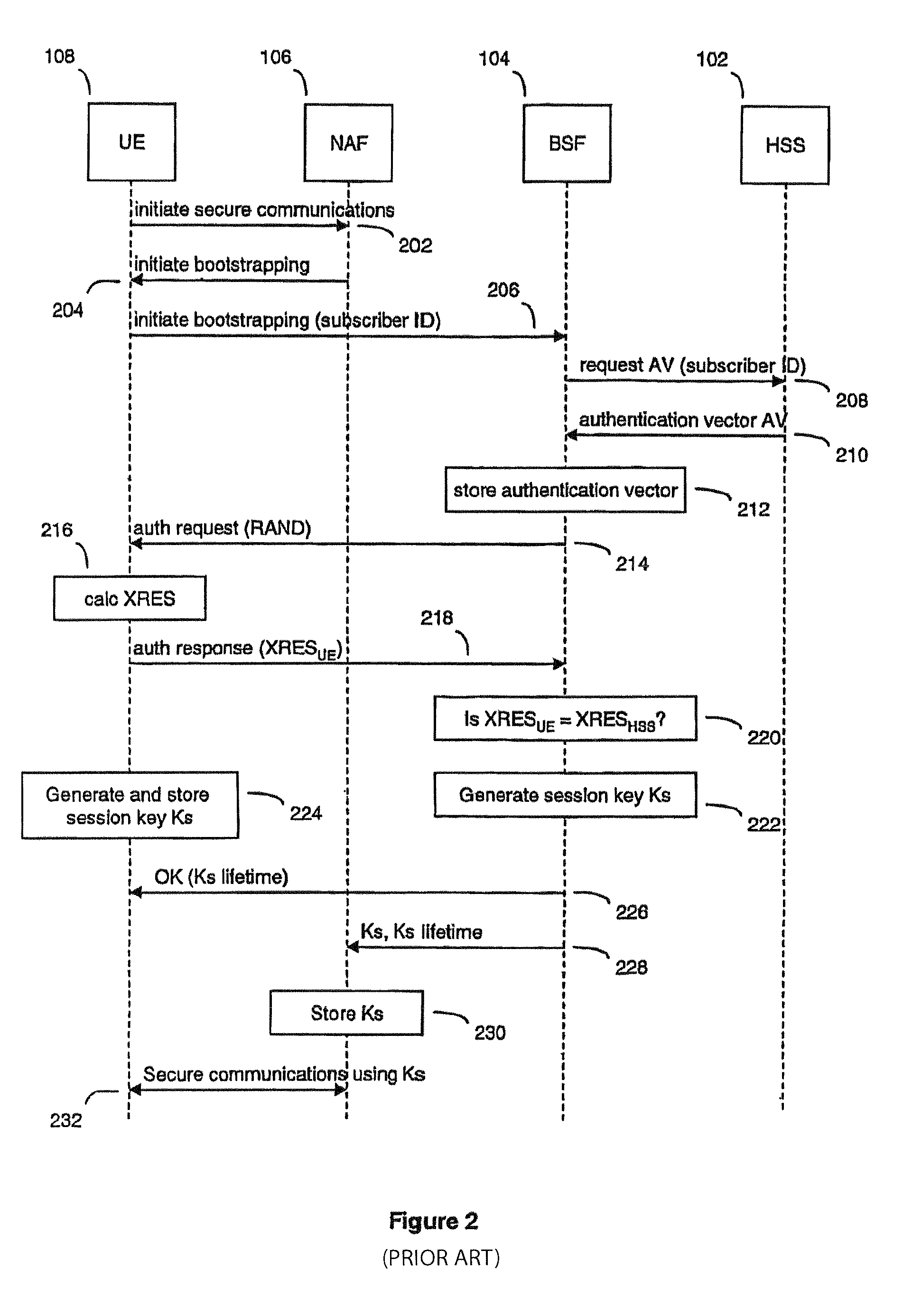
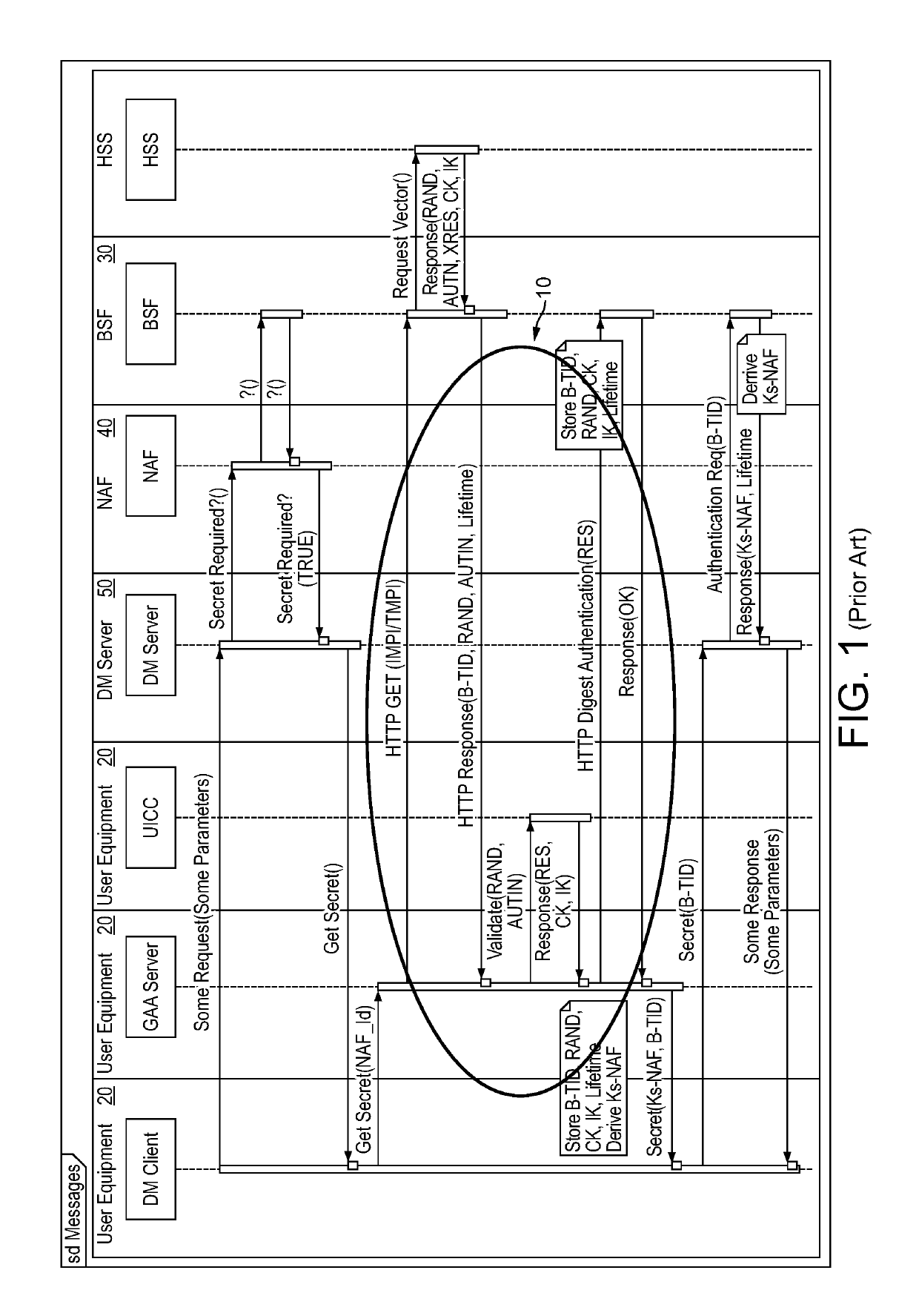
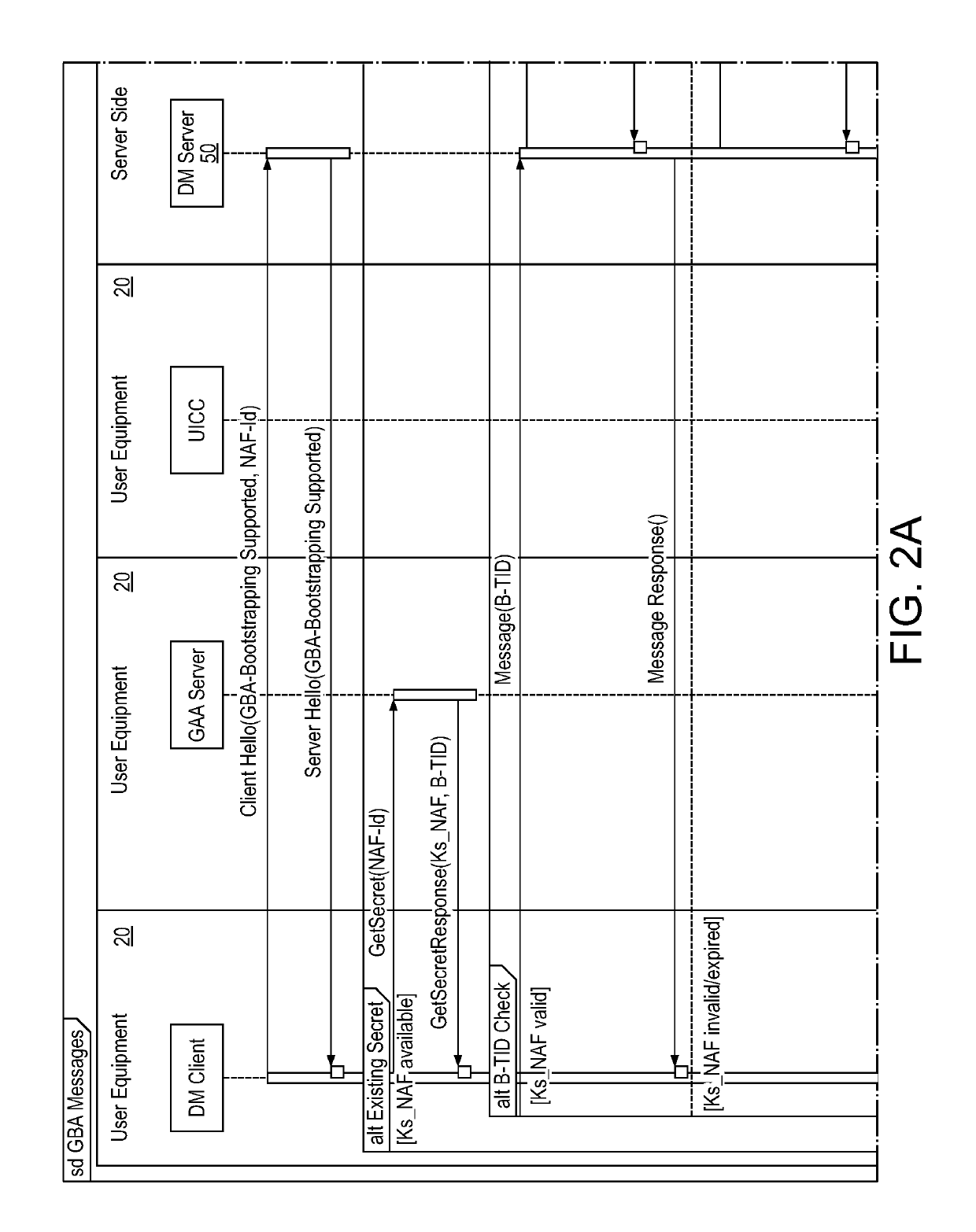
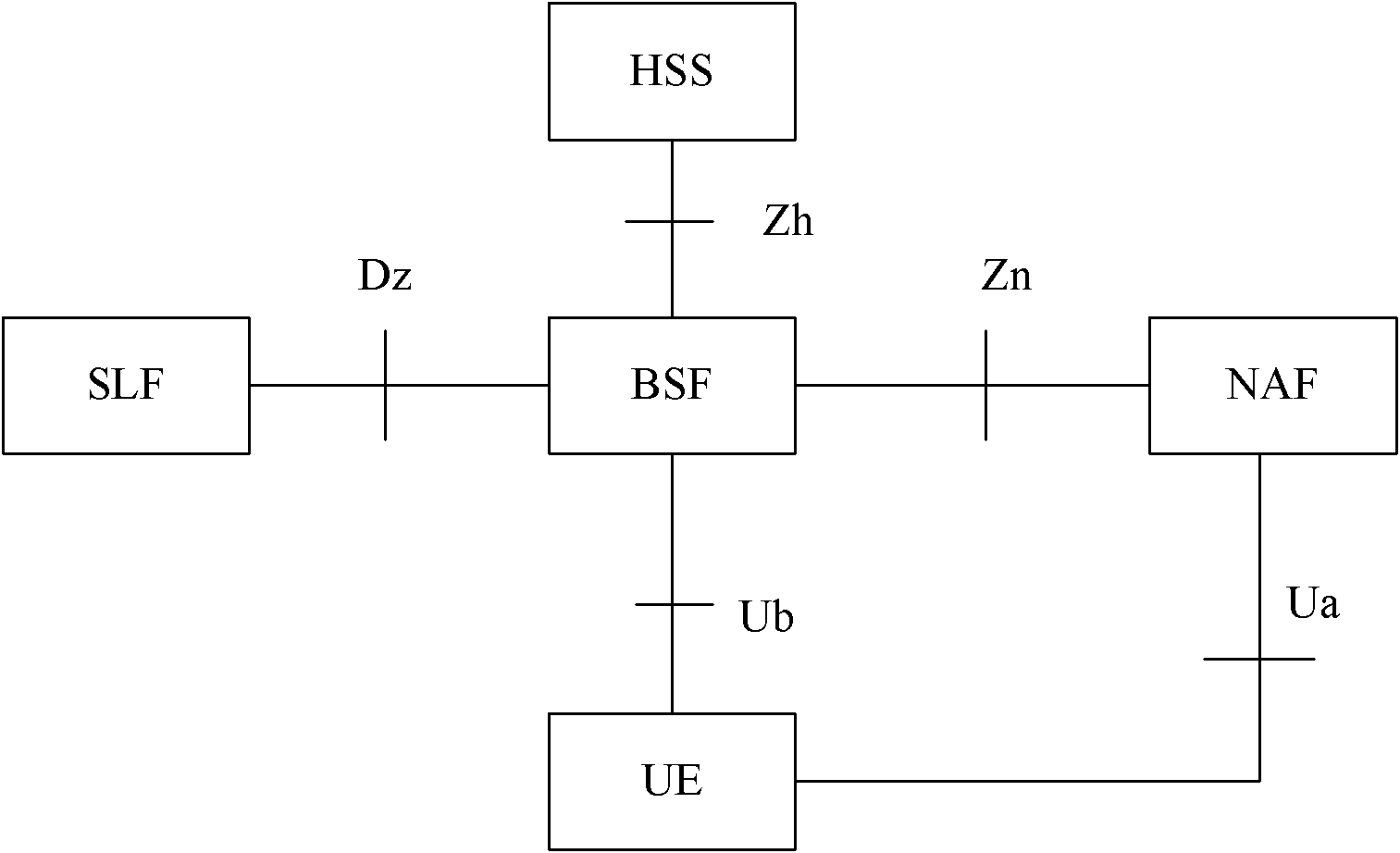
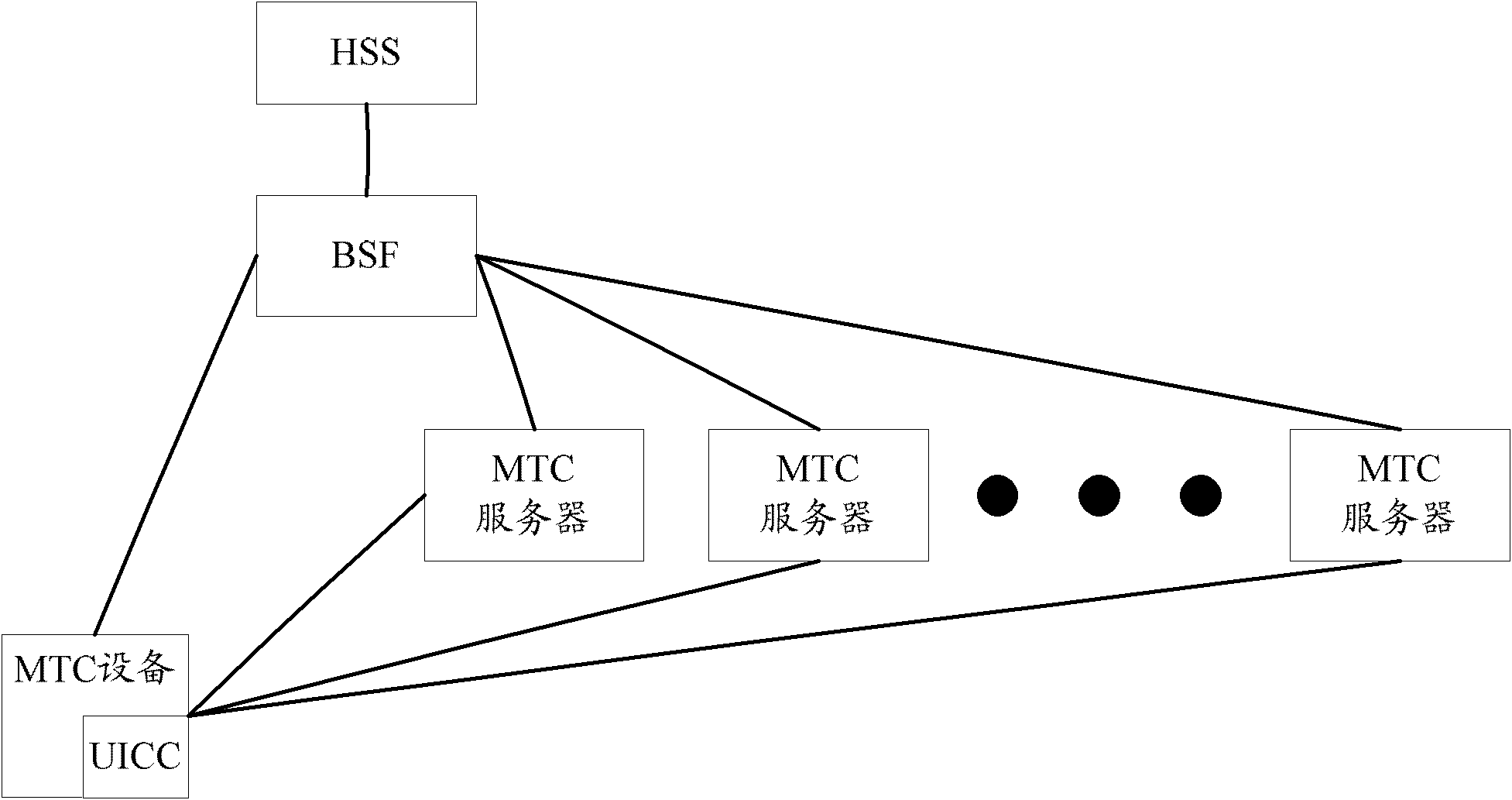
A Bootstrapping Server Function (BSF) is an intermediary element in Cellular networks which provides application independent functions for mutual authentication of user equipment and servers unknown to each other and for 'bootstrapping' the exchange of secret session keys afterwards. This allows the use of additional services like Mobile TV and PKI, which need authentication and secured communication.
Techniques for secure channelization between uicc and a terminal
InactiveUS20090209232A1Improve integrityReduce needUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemThird generation
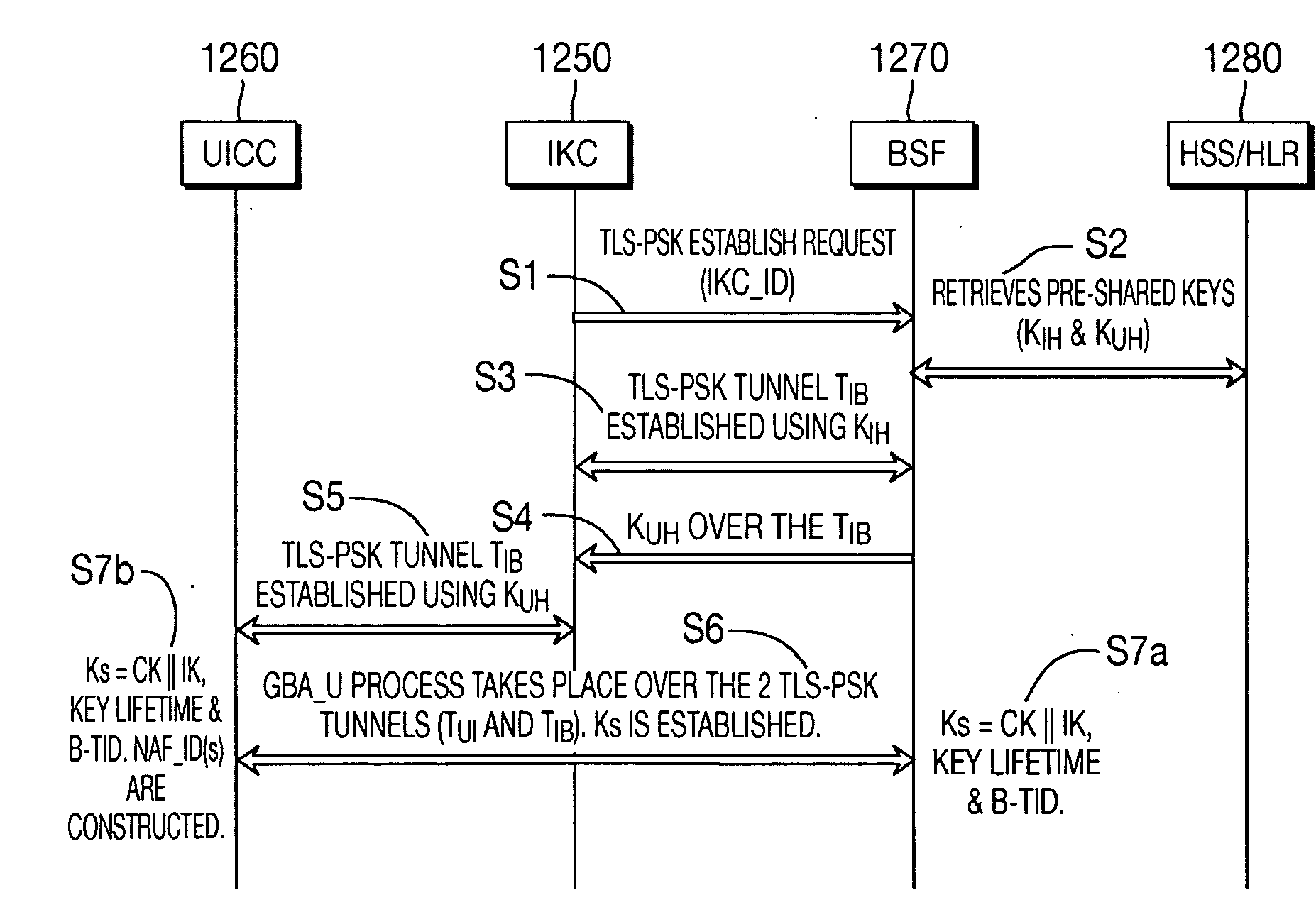
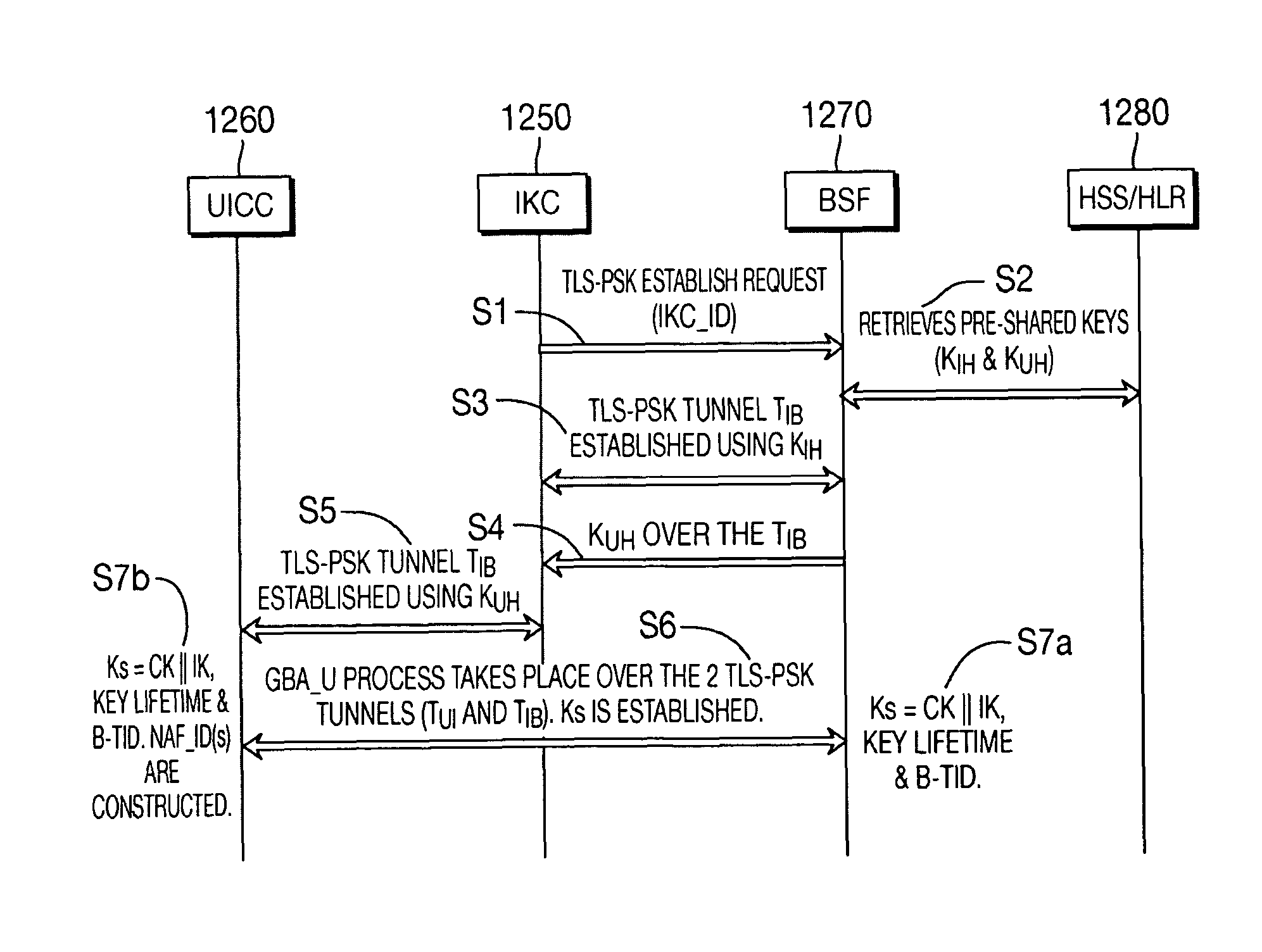
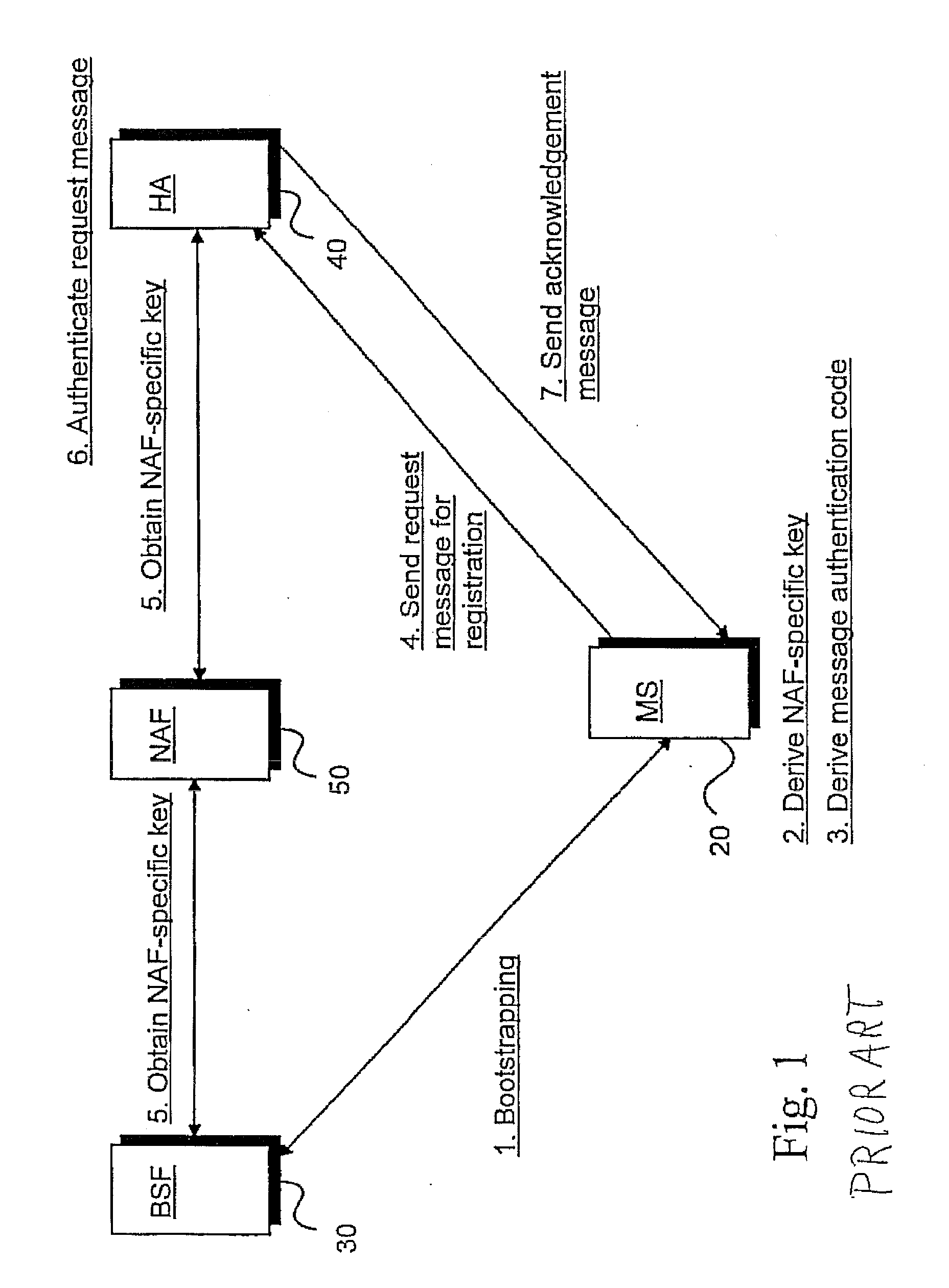
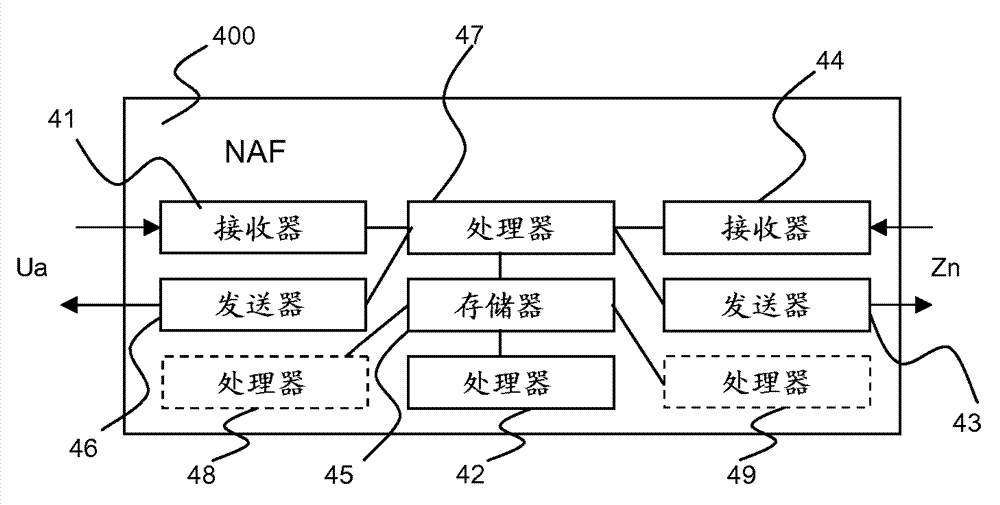
The present invention is related to a wireless communication system. 3G UMTS mobile phone systems rely on a protected smart card called the UMTS integrated circuit card (UICC) that provides UMTS subscriber identity module (USIM) applications as a basis or root of various security measures protecting the communication path between the 3G mobile terminal and the UMTS wireless network (or UTRAN). Disclosed is a method by which the UICC exchanges information with a terminal, such as an Internal Key Center (IKC 1250) and a Bootstrapping Server Function (BSF 1270) enables a procedure where multiple local keys specific to applications and Network Application Functions (NAFs) (Ks_local) are used for authentication and to encrypt and decrypt messages.
Owner:INTERDIGITAL TECH CORP
Authenticating an application
ActiveUS20070234041A1Easy to moveOption very attractiveKey distribution for secure communicationUser identity/authority verificationOperating systemNetwork application
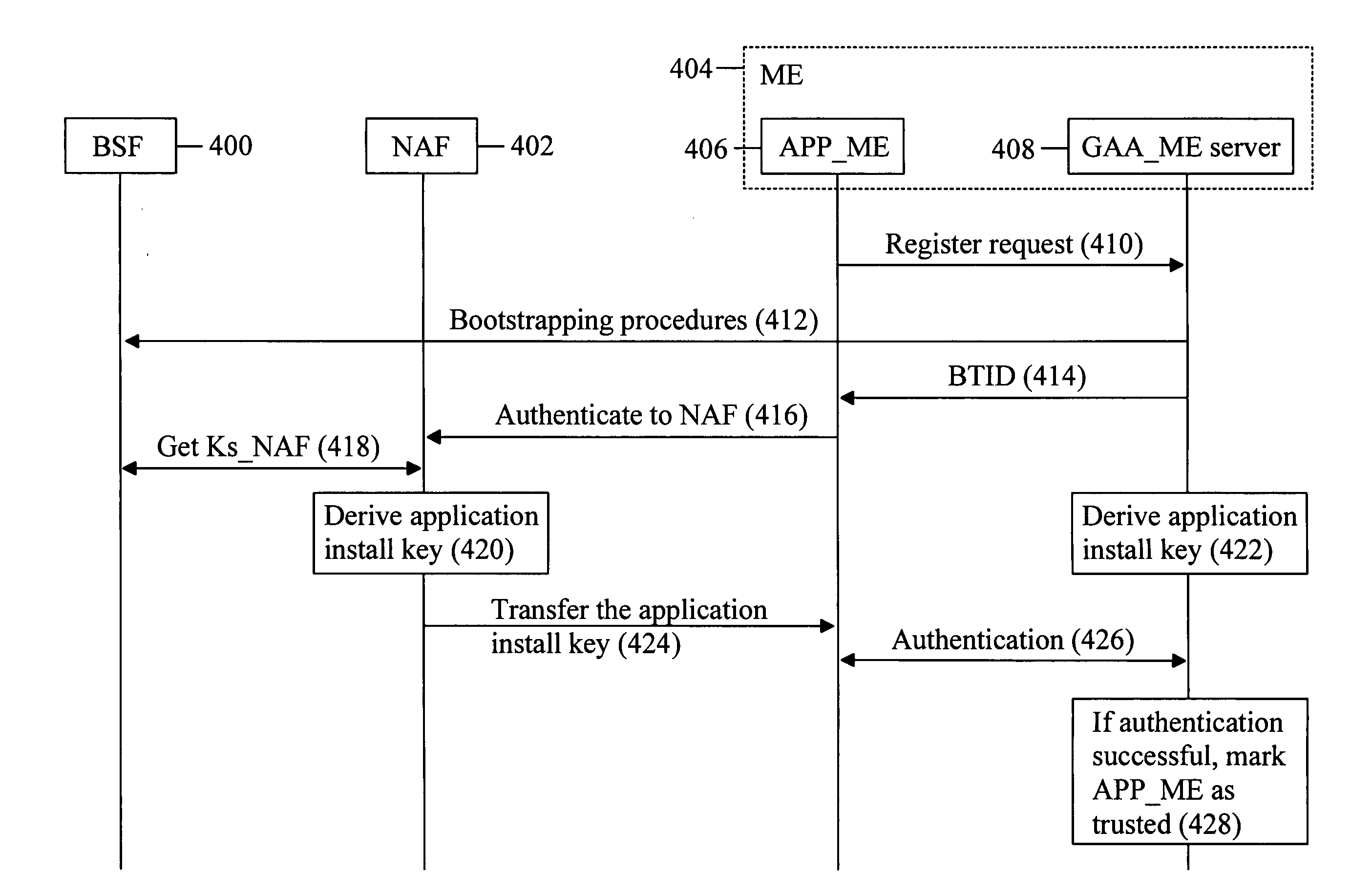
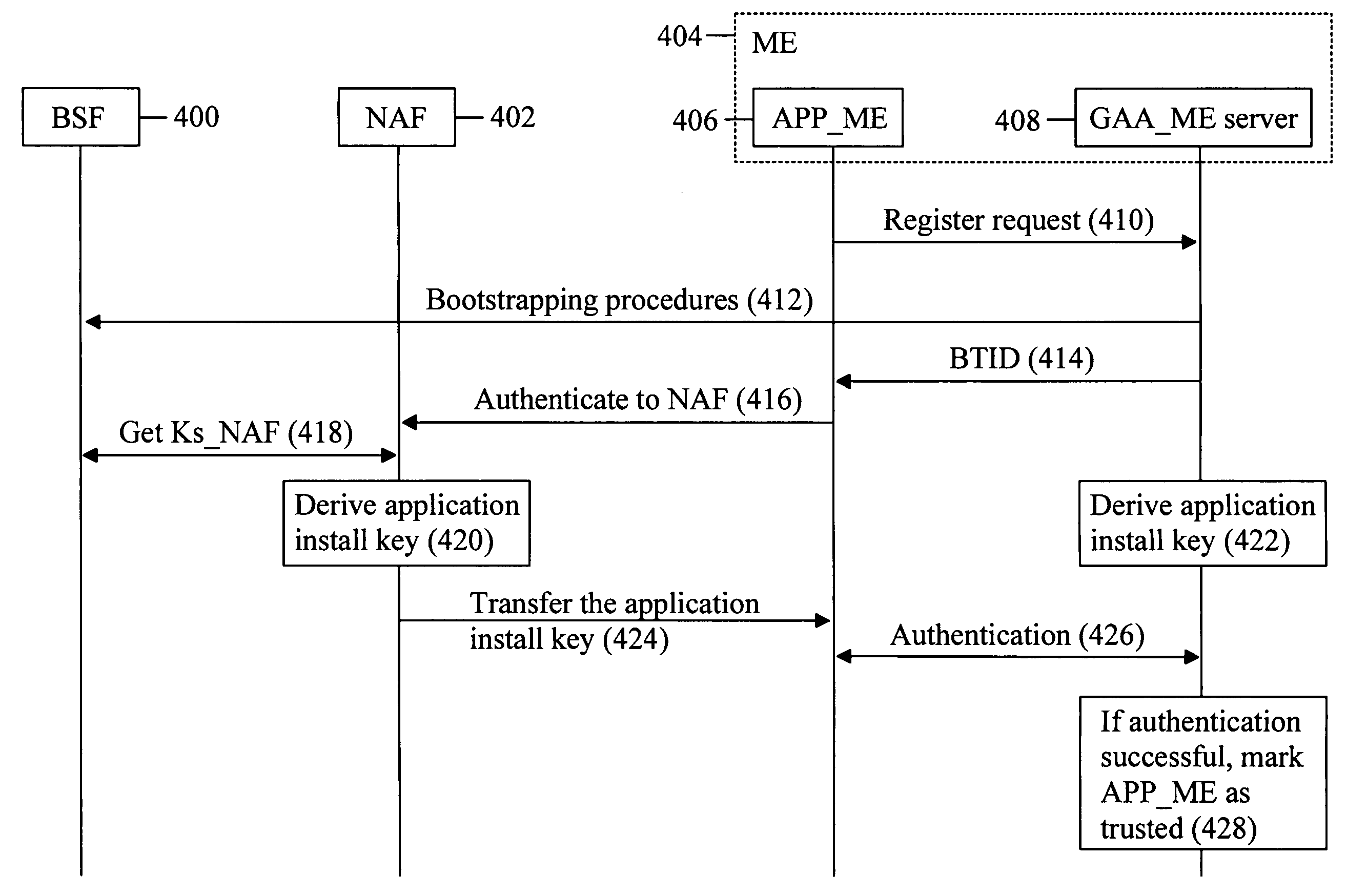
One aspect of the invention discloses a method of authenticating an application. The method comprising performing, with a server application, bootstrapping procedures between the server application and a bootstrapping server function; deriving a shared key based on at least a key received from the bootstrapping server function server during the bootstrapping procedures and a network application function identifier; providing an application with a bootstrapping transaction identifier, the bootstrapping transaction identifier being received from the bootstrapping server function server during the bootstrapping procedures; receiving a response from the application; and authenticating the application by validating the response with the shared key.
Owner:NOKIA TECHNOLOGLES OY
Techniques for secure channelization between UICC and a terminal
InactiveUS8503376B2Reduce needUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemSecurity Measure
The present invention is related to a wireless communication system. 3G UMTS mobile phone systems rely on a protected smart card called the UMTS integrated circuit card (UICC) that provides UMTS subscriber identity module (USIM) applications as a basis or root of various security measures protecting the communication path between the 3G mobile terminal and the UMTS wireless network (or UTRAN). Disclosed is a method by which the UICC exchanges information with a terminal, such as an Internal Key Center (IKC 1250) and a Bootstrapping Server Function (BSF 1270) enables a procedure where multiple local keys specific to applications and Network Application Functions (NAFs) (Ks_local) are used for authentication and to encrypt and decrypt messages.
Owner:INTERDIGITAL TECH CORP
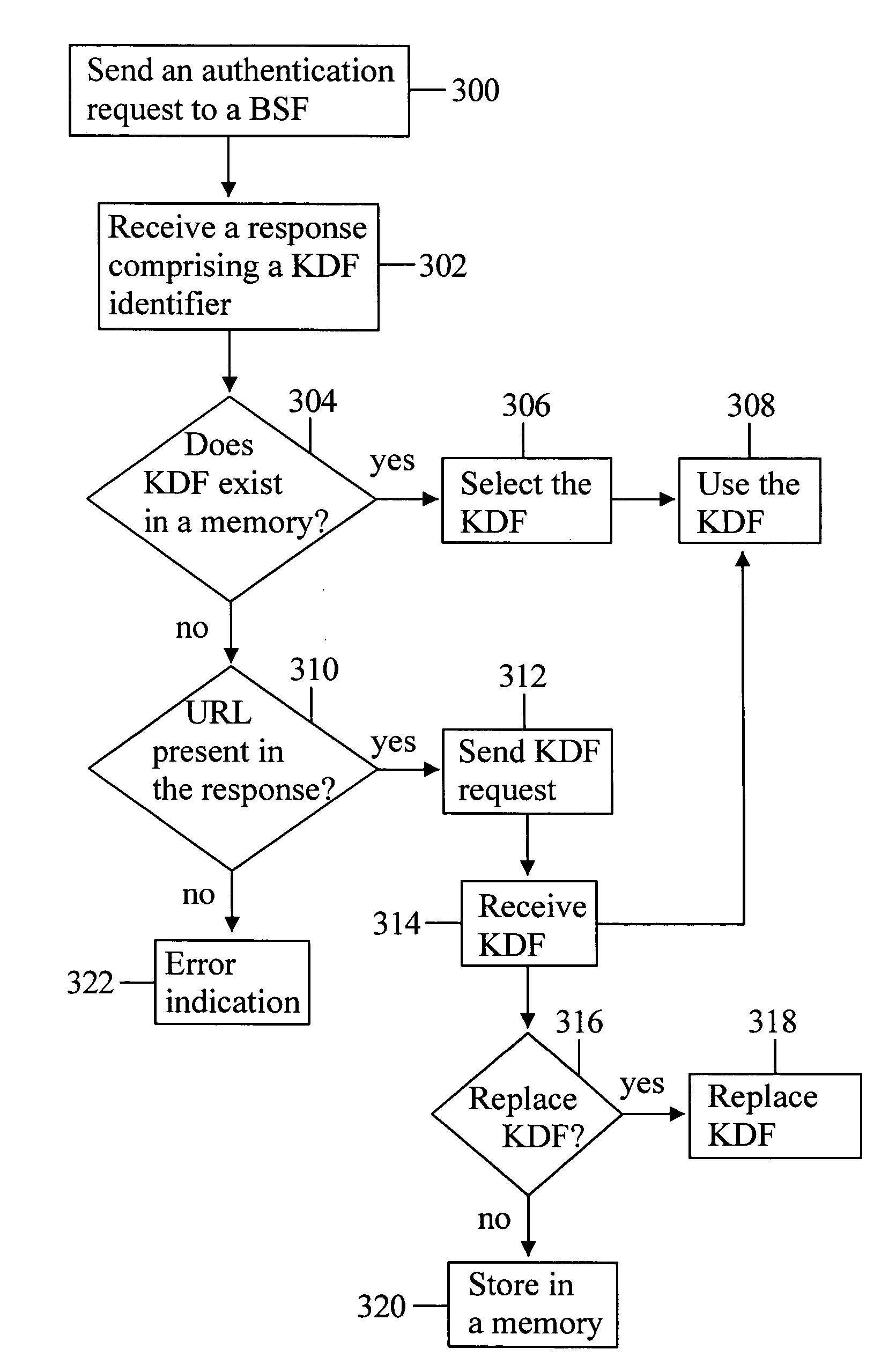
Determining a key derivation function
InactiveUS20060101270A1Easy to switchKey distribution for secure communicationUser identity/authority verificationKey derivation functionUser equipment
Owner:NOKIA CORP
Authentication using GAA functionality for unidirectional network connections
ActiveUS20060174117A1Broaden applicationUser identity/authority verificationSecurity arrangementClient-sideUnidirectional network
Methods, a client entity, network entities, a system, and a computer program product perform authentication between a client entity and a network. The network includes at least a bootstrapping server function entity and a network application function entity. The client entity is not able to communicate with both of the network entities in a bidirectional manner. The 3GPP standard Ub reference point between the client entity and the bootstrapping server function entity is not utilized for authentication purposes, such as authentication using GAA functionality for unidirectional network connections.
Owner:NOKIA TECHNOLOGLES OY
Secure bootstrapping for wireless communications
ActiveUS7966000B2Unauthorised/fraudulent call preventionMultiple keys/algorithms usageKey exchangeChallenge response
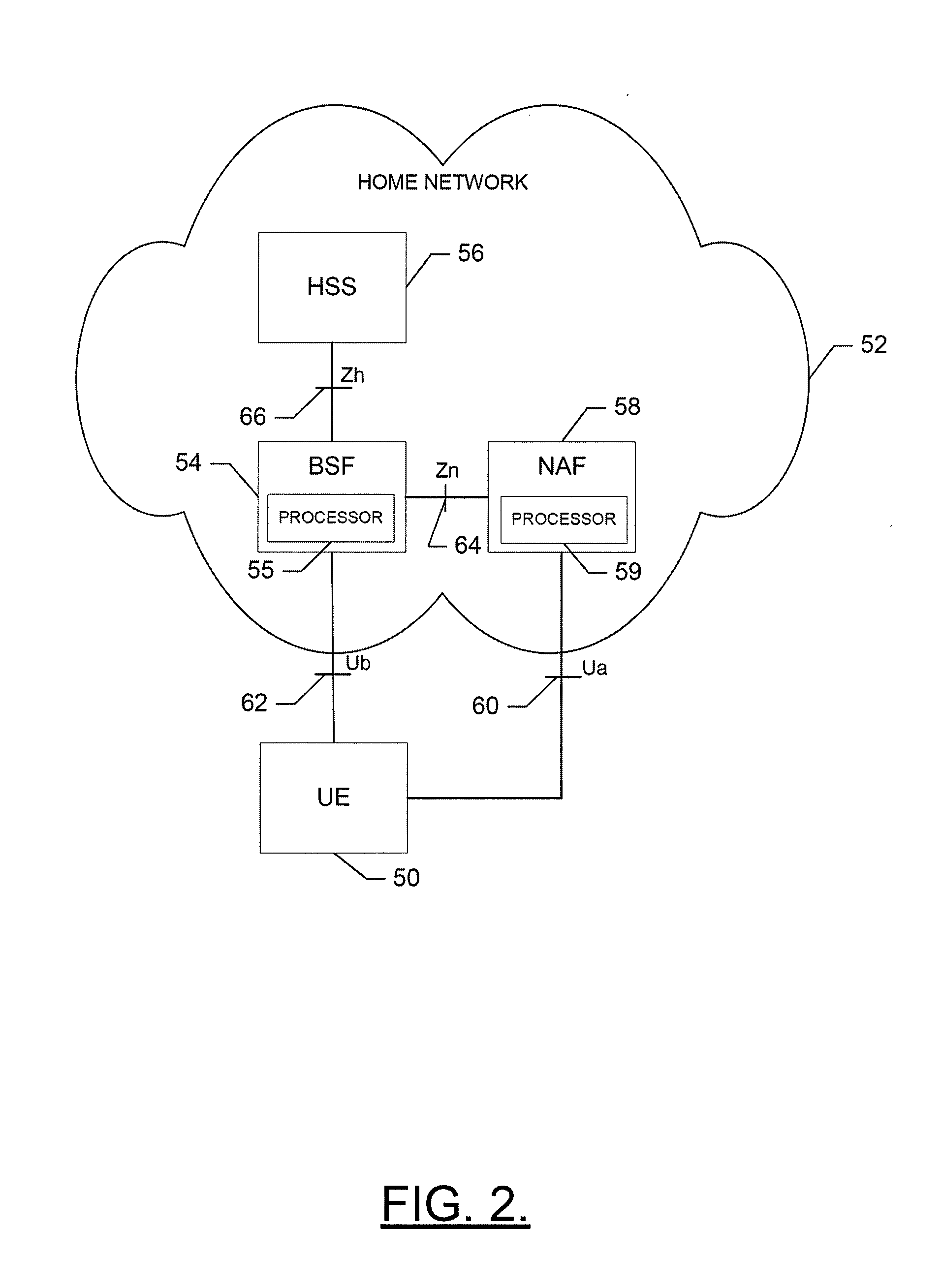
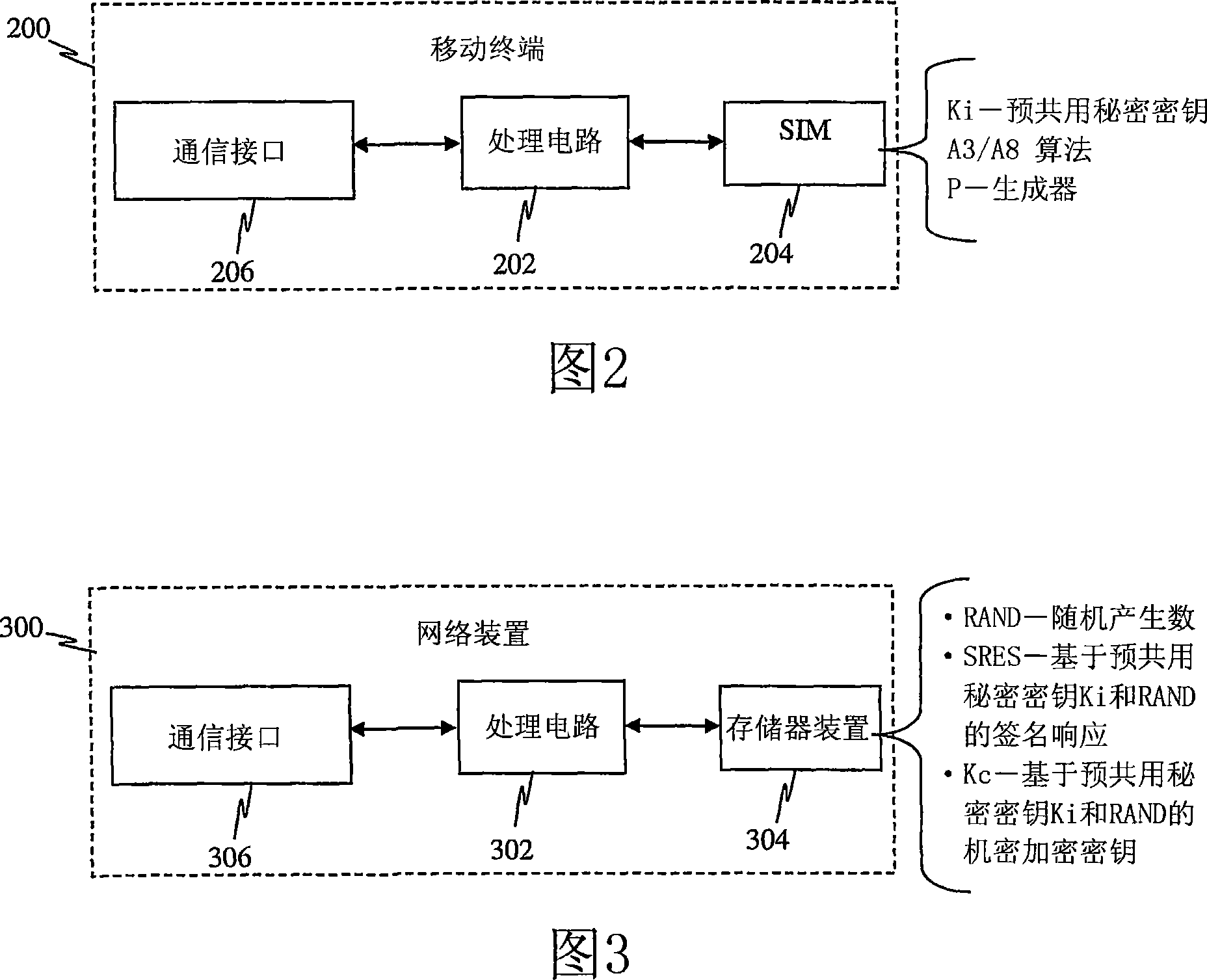
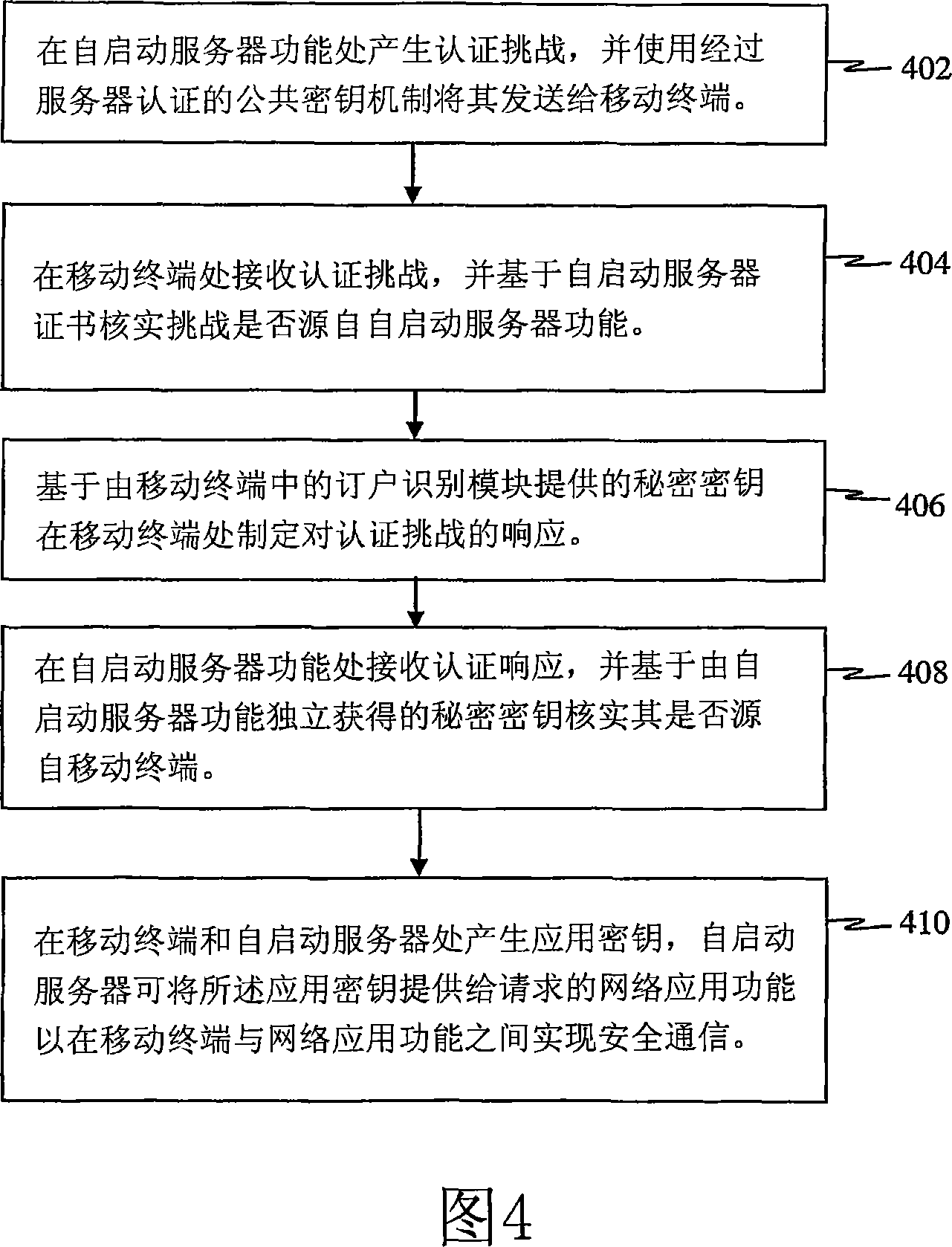
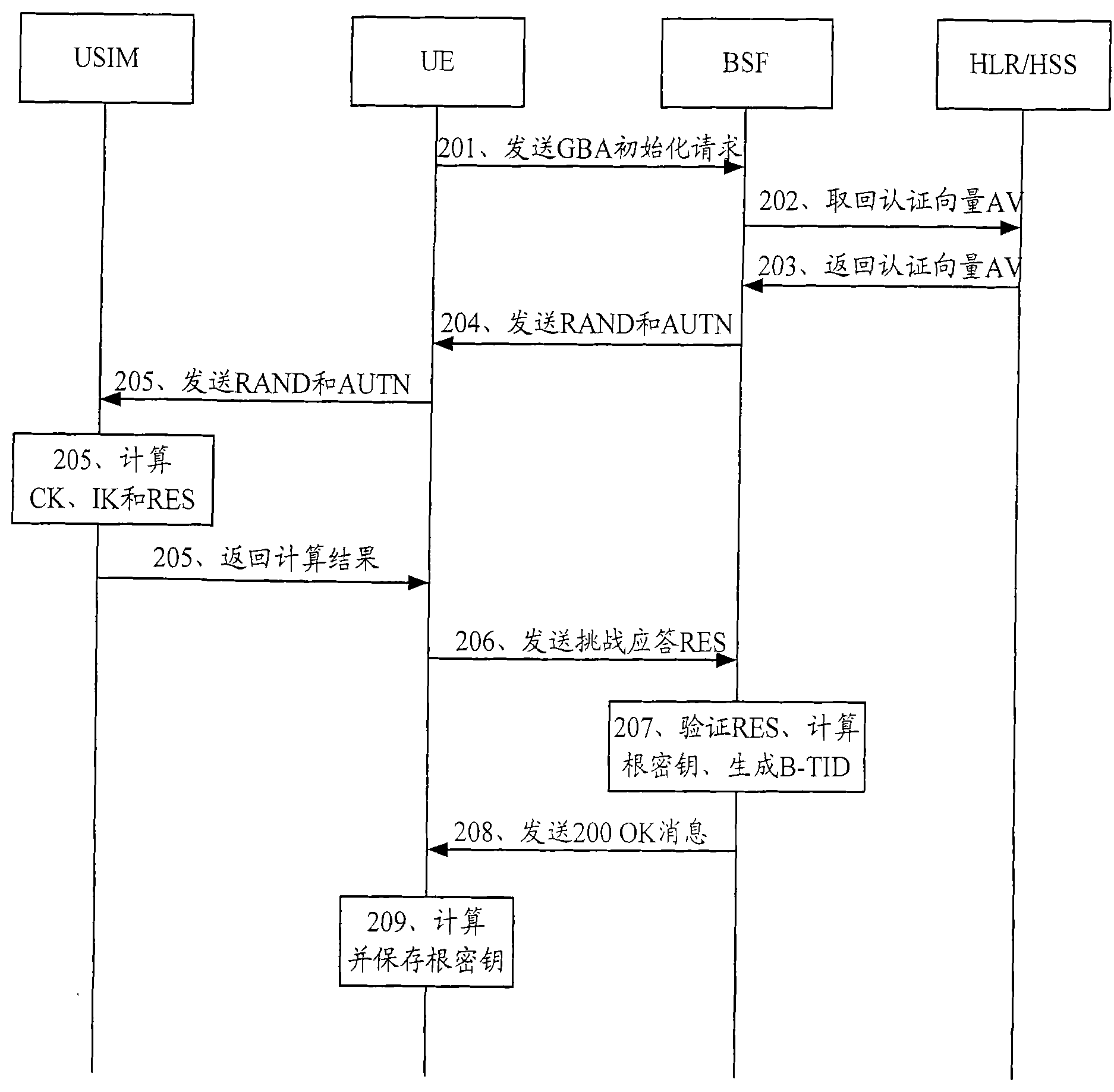
A mutual authentication method is provided for securely agreeing application-security keys with mobile terminals supporting legacy Subscriber Identity Modules (e.g., GSM SIM and CDMA2000 R-UIM, which do not support 3G AKA mechanisms). A challenge-response key exchange is implemented between a bootstrapping server function (BSF) and mobile terminal (MT). The BSF generates an authentication challenge and sends it to the MT under a server-authenticated public key mechanism. The MT receives the challenge and determines whether it originates from the BSF based on a bootstrapping server certificate. The MT formulates a response to the authentication challenge based on keys derived from the authentication challenge and a pre-shared secret key. The BSF receives the authentication response and verifies whether it originates from the MT. Once verified, the BSF and MT independently calculate an application security key that the BSF sends to a requesting network application function to establish secure communications with the MT.
Owner:QUALCOMM INC
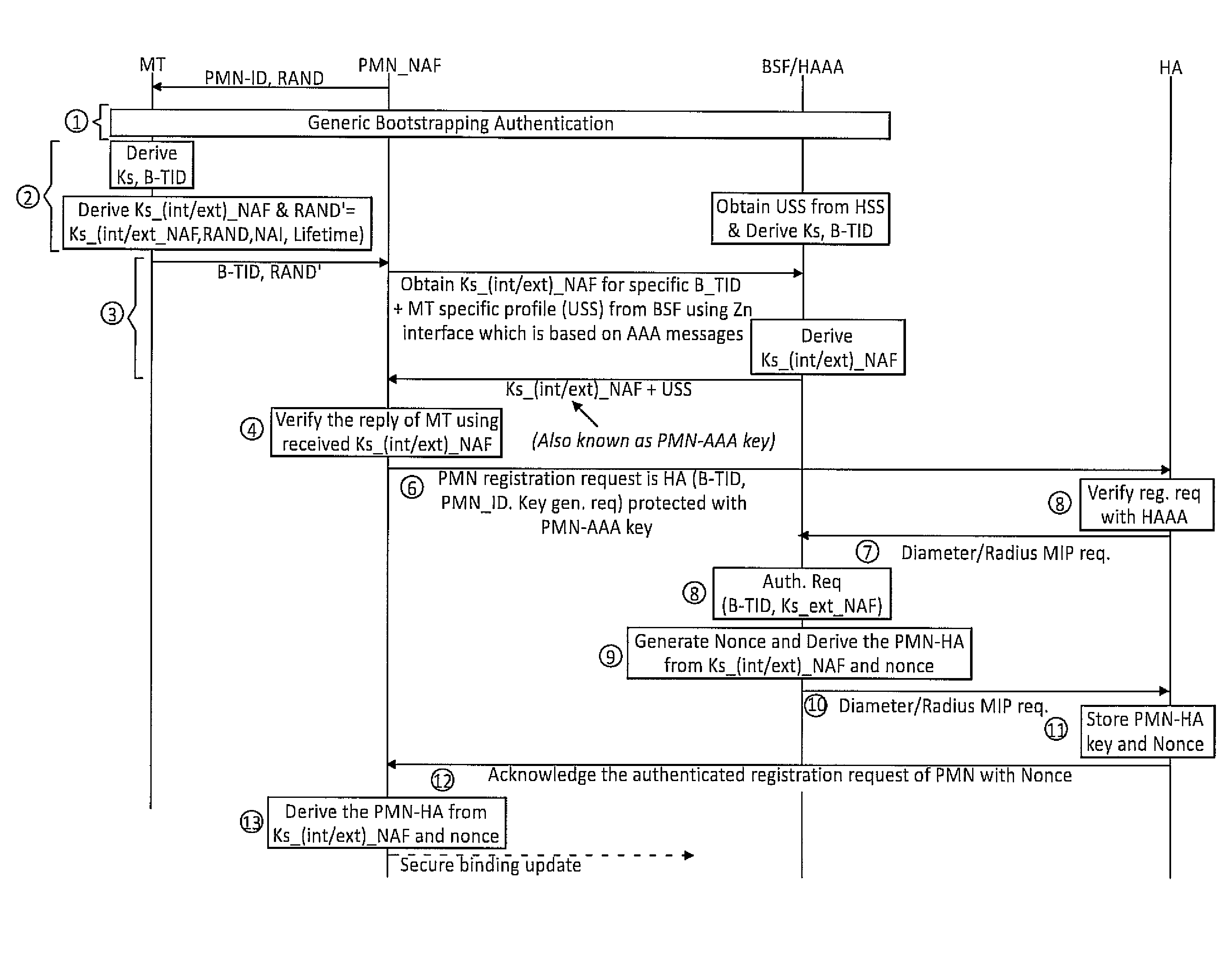
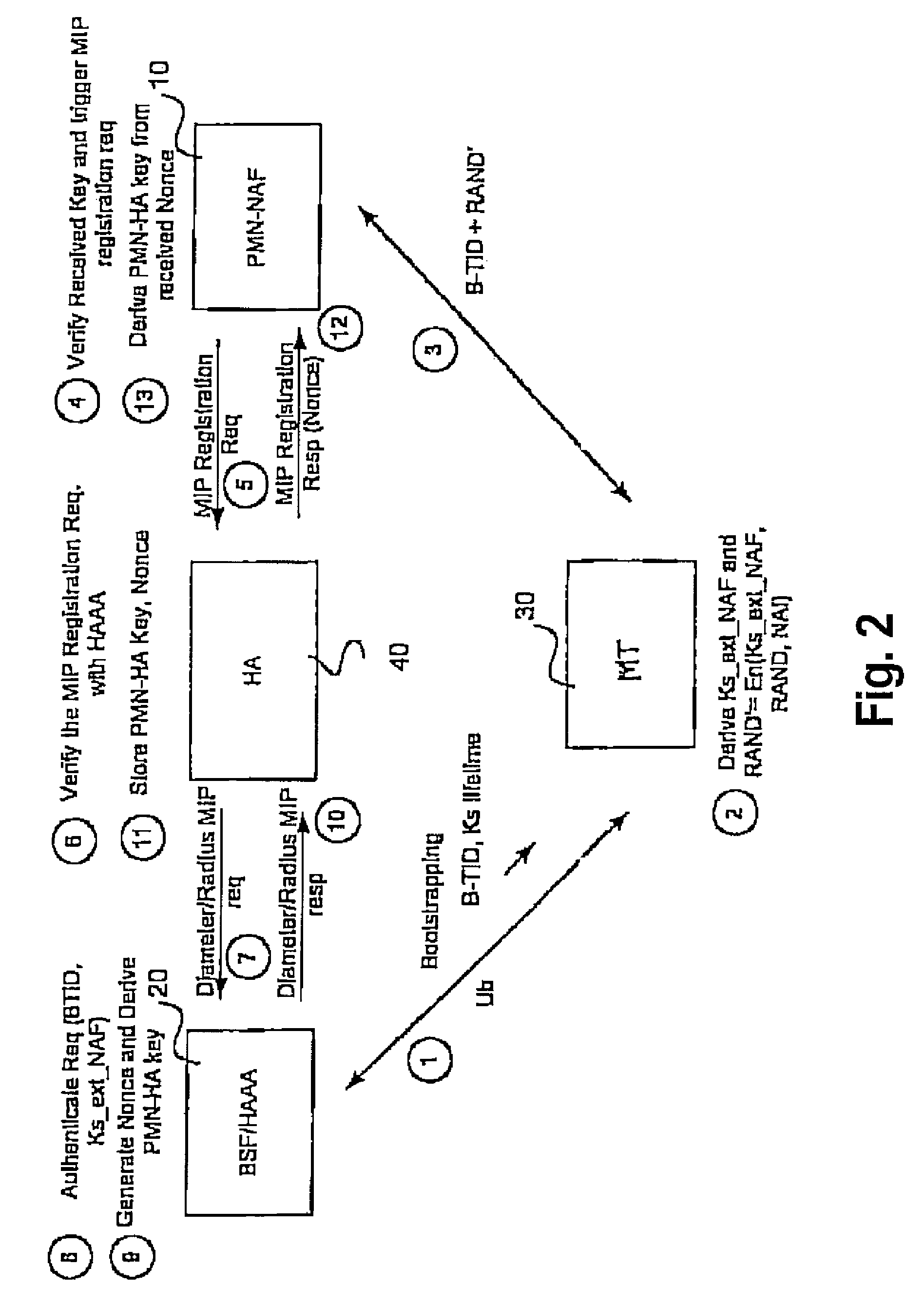
Using gaa to derive and distribute proxy mobile node home agent keys
InactiveUS20090138955A1Digital data processing detailsUser identity/authority verificationSurrogate keyMessage authentication code
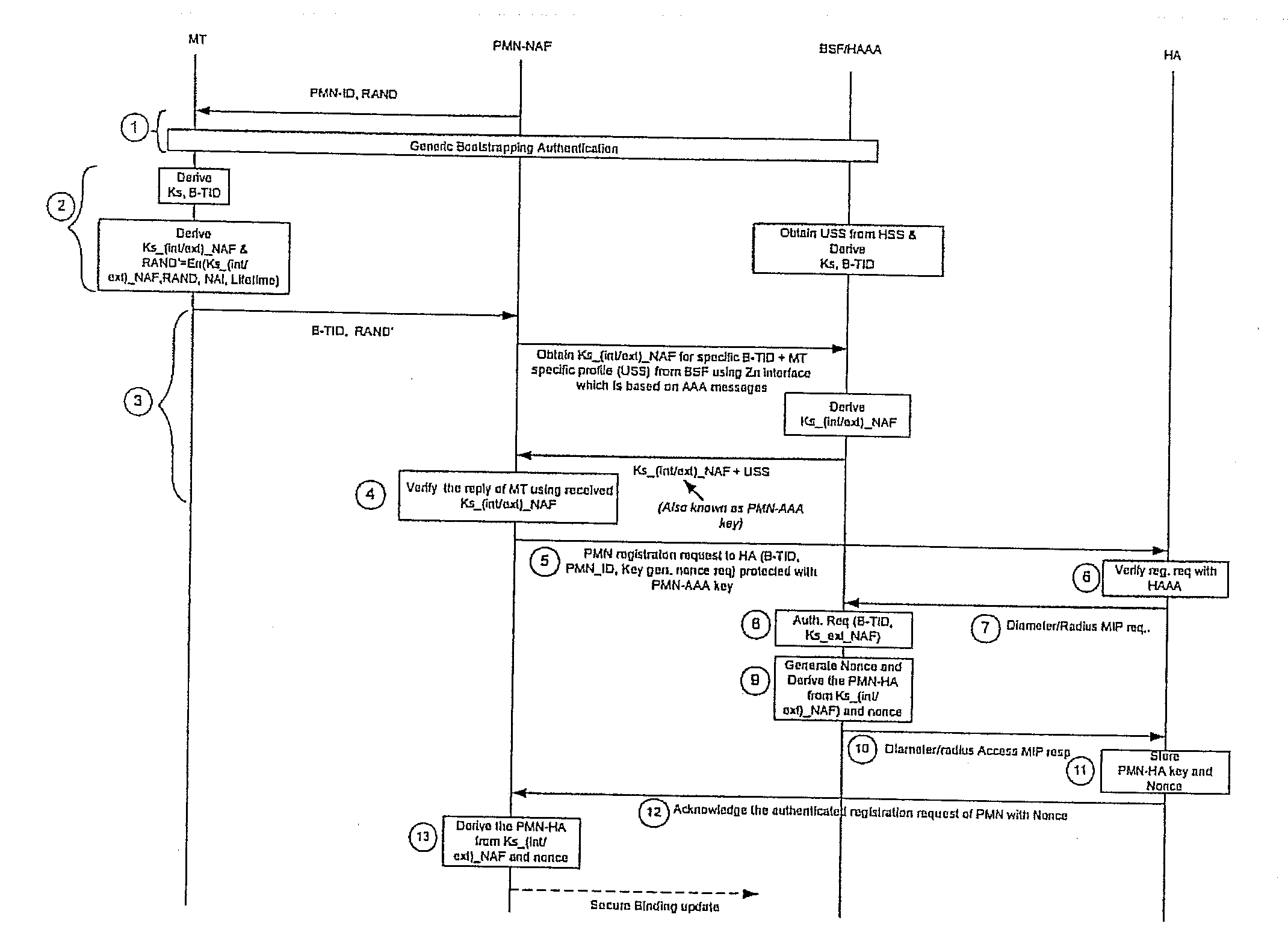
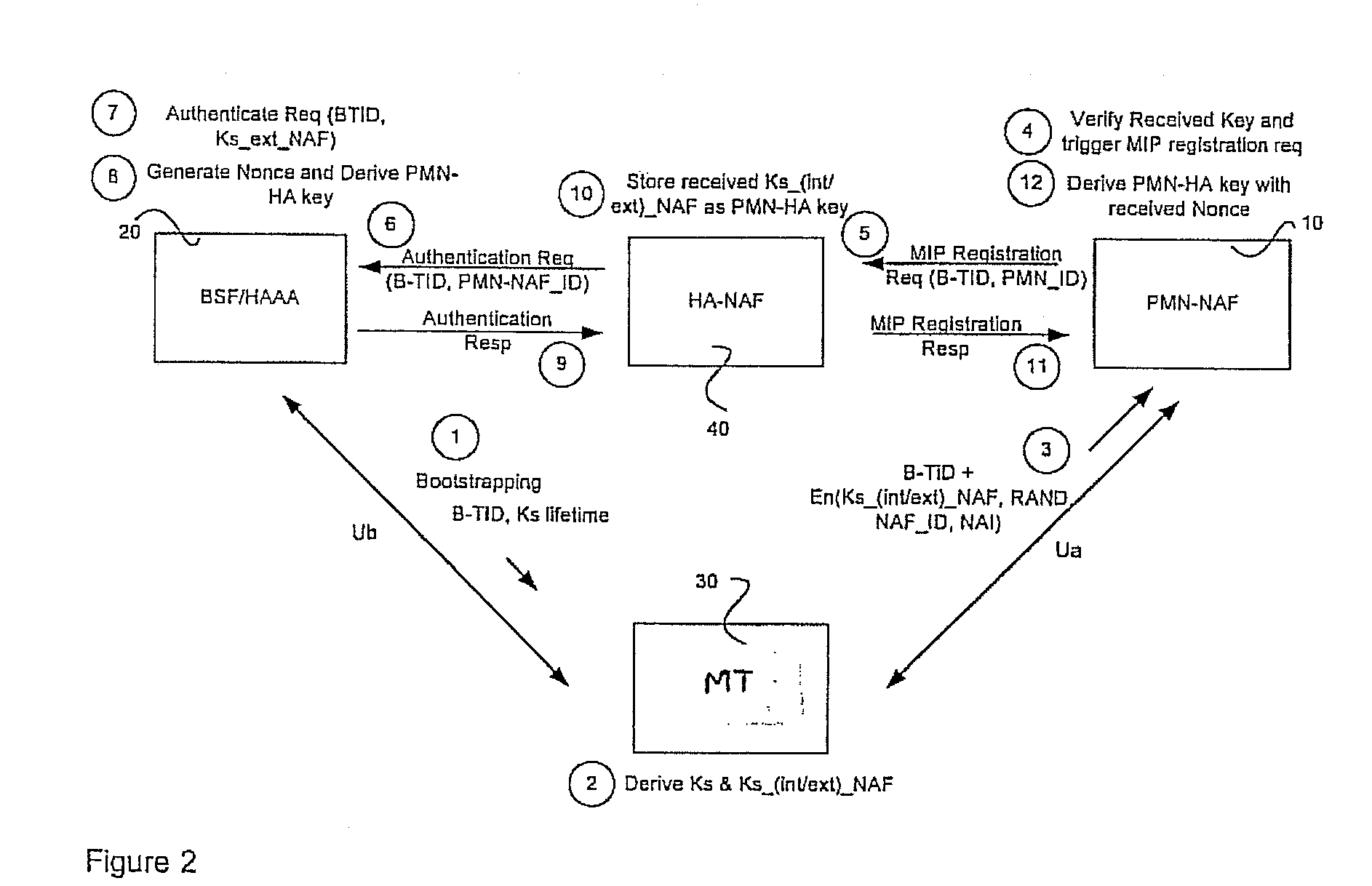
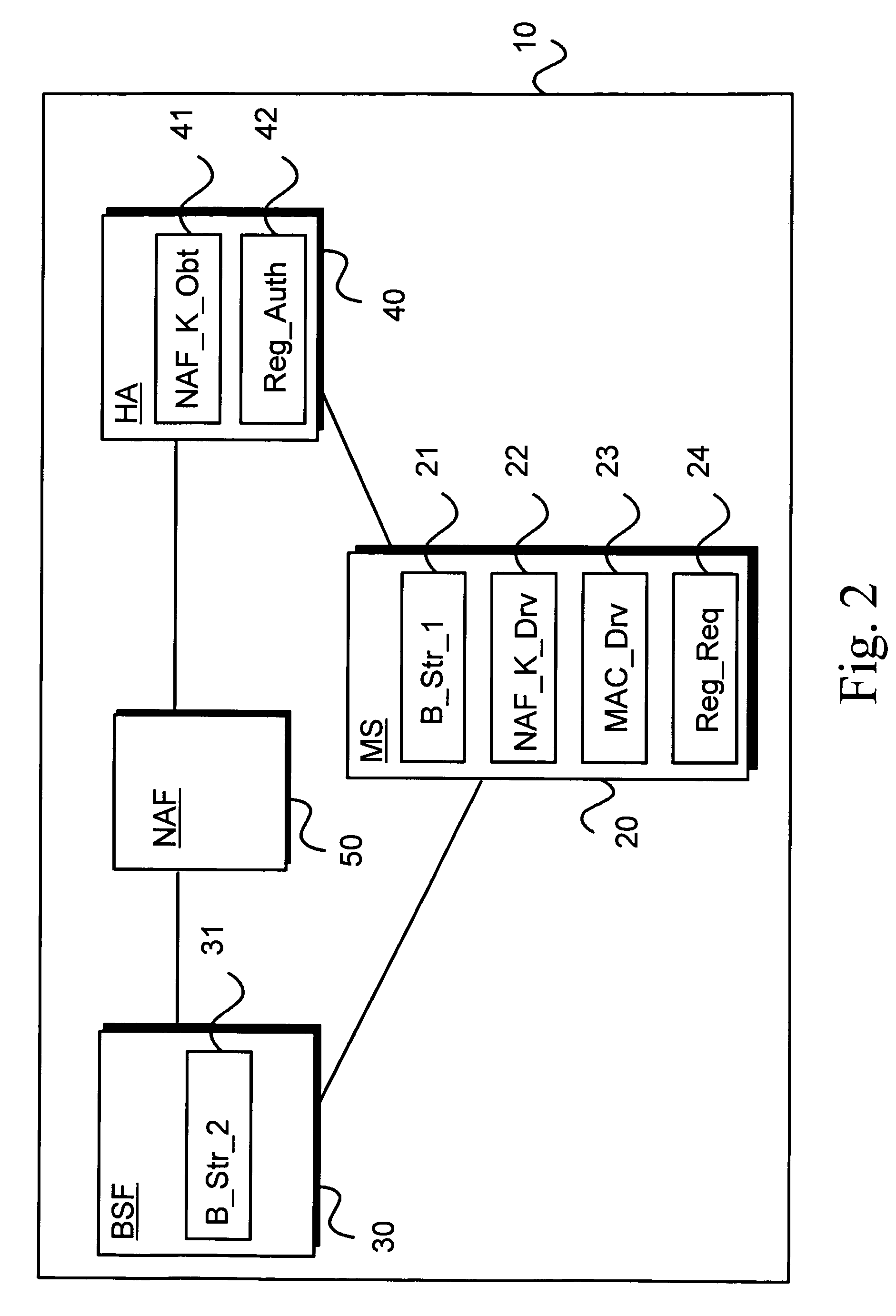
A Generic Authentication Architecture bootstrapping procedure is performed between a mobile terminal and a bootstrapping server function resulting in the mobile terminal and the bootstrapping server function each acquiring at least a bootstrapping transaction Identifier associated with the mobile terminal and a corresponding shared key. The mobile terminal derives a network application function specific key based on at least the acquired shared key and an identifier of said network application function. The bootstrapping transaction identifier and the network application function specific key are sent from the mobile terminal to the proxy mobile node. A request message for Mobile Internet Protocol registration is sent from the proxy mobile node to a home agent on behalf of the mobile terminal, the request message including the bootstrapping transaction identifier and an identifier of the proxy mobile node. The registration message is verified in the home agent with the use of a network application function specific key obtained from the bootstrapping server function or a network application function. The request message for Mobile Internet Protocol registration is authenticated with the proxy mobile node acting on behalf of the mobile terminal by verifying the message authentication code with the obtained network application function specific key.
Owner:WSOU INVESTMENTS LLC
Re-Keying in a Generic Bootstrapping Architecture Following Handover of a Mobile Terminal
InactiveUS20070124587A1User identity/authority verificationSecurity arrangementGeneric Bootstrapping ArchitectureRe keying
An apparatus for re-keying a mobile terminal in a foreign network includes a processor. The processor is configured to receive, at the apparatus which is physically located in the foreign network, a request for re-keying from the mobile terminal in the foreign network. The processor is also configured to translate the request for transmission to a home network of the mobile terminal and to transmit the translated request to a bootstrapping server function of the home network.
Owner:NOKIA CORP
Utilizing generic authentication architecture for mobile internet protocol key distribution
The invention allows utilizing Generic Authentication Architecture for Mobile Internet Protocol key distribution. A Generic Authentication Architecture bootstrapping is performed between a mobile terminal device and a Bootstrapping Server Function. In an embodiment a resulting Bootstrapping Transaction Identifier is sent to a Home Agent which uses it to obtain a Home Agent specific key to be used in authenticating a Mobile Internet Protocol Registration Request.
Owner:WSOU INVESTMENTS LLC
Authenticating an application
ActiveUS8522025B2Easy to moveOption very attractiveKey distribution for secure communicationUser identity/authority verificationNetwork applicationOperating system
Owner:NOKIA TECH OY
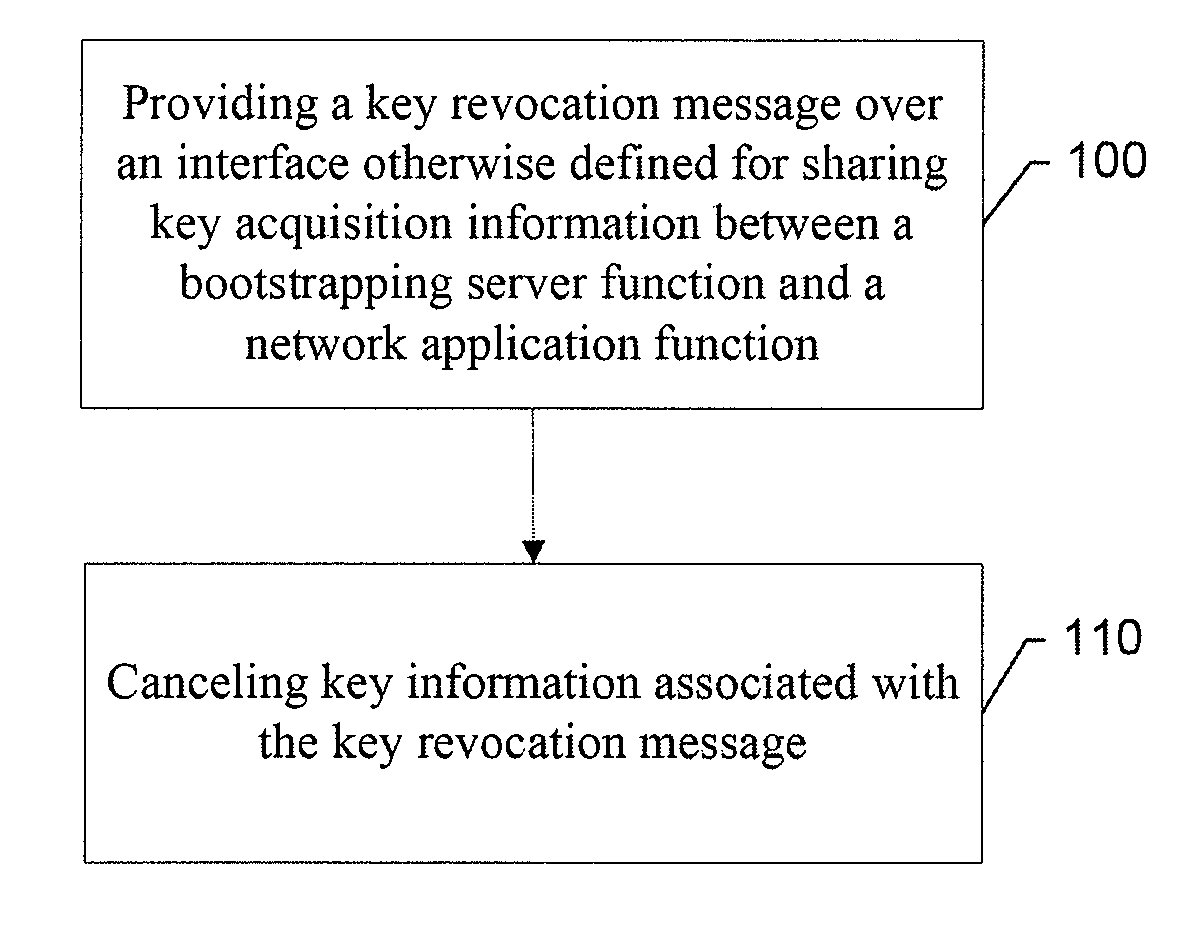
Method, Apparatus and Computer Program Product for Providing Key Management for a Mobile Authentication Architecture
InactiveUS20090232310A1Improve securityEncryption apparatus with shift registers/memoriesMultiple digital computer combinationsMobile authenticationComputer science
An apparatus for providing key management for a mobile authentication architecture may include a processor. The processor may be configured to provide a request for key revocation over an interface otherwise defined for sharing key acquisition information between a bootstrapping server function and a network application function, and cancel key information associated with the request for key revocation.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Secure bootstrapping for wireless communications
Owner:QUALCOMM INC
Method and system for managing machine type communication (MTC) equipment based on generic bootstrapping architecture (GBA) in grouping manner
InactiveCN102469455AWireless commuication servicesTransmissionGeneric Bootstrapping ArchitectureCommunication device
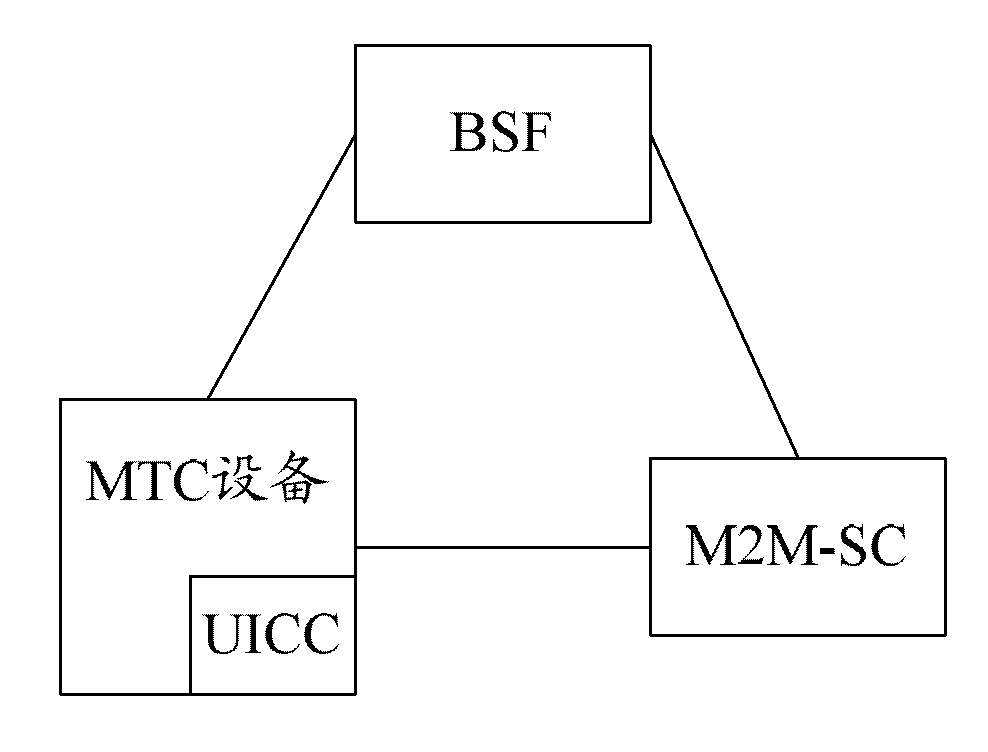
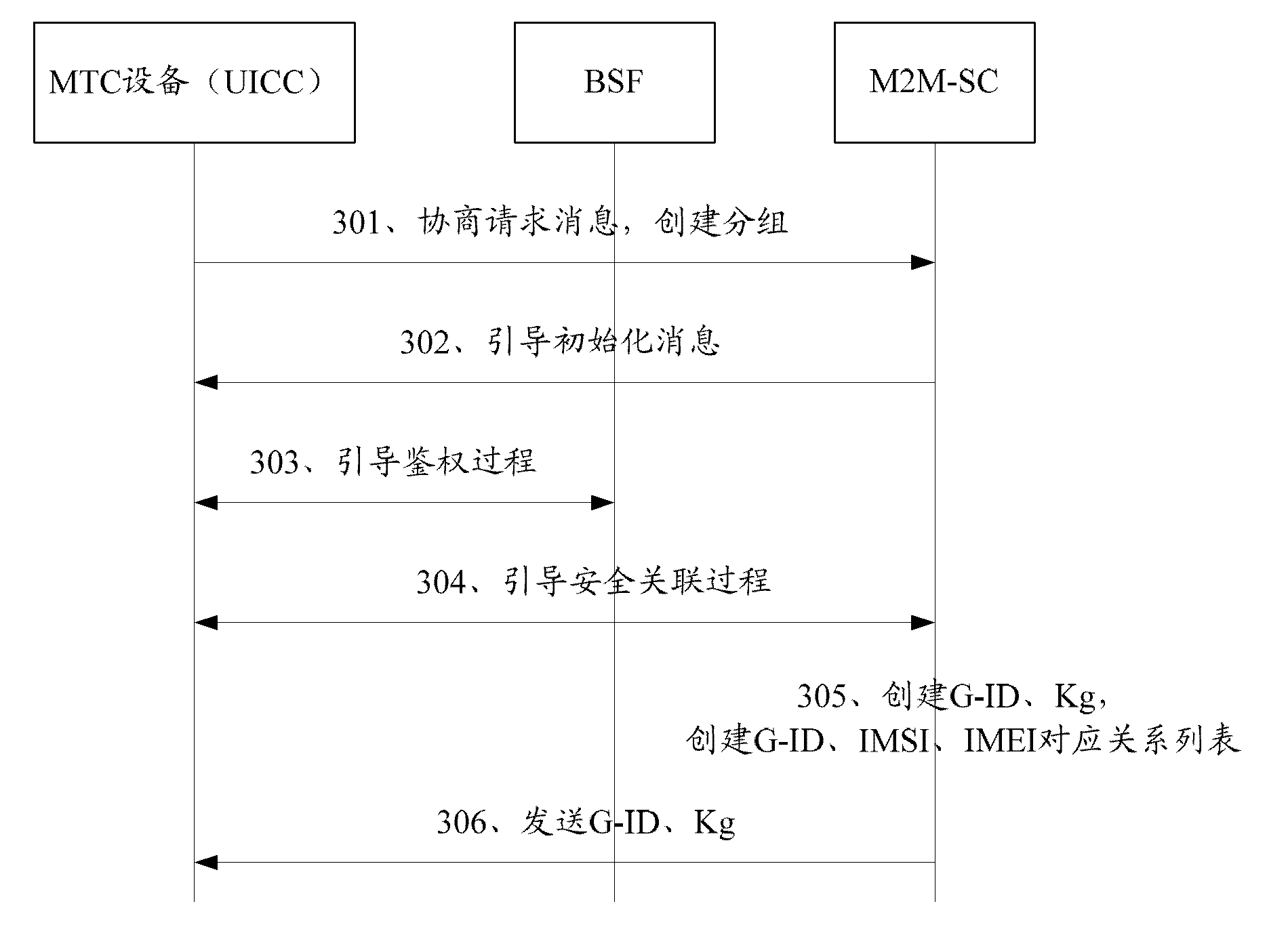
The invention discloses a method for managing machine type communication (MTC) equipment based on a generic bootstrapping architecture (GBA) in a grouping manner. The method is applied to a system which comprises the MTC equipment, a bootstrapping server function (BSF) and a machine to machine service center (M2M-SC), and comprises the following steps that: when the MTC equipment which is determined to be added with a group identifier (G-ID) through the negotiation between first MTC equipment and the M2M-SC is grouped, the first MTC equipment, the BSF and the M2M-SC establish a first session key between the first MTC equipment and the M2M-SC in a first GBA process, and the M2M-SC encrypts the G-ID and a group key Kg which are grouped by the MTC equipment through the first session key and then transmits the encrypted G-ID and group key Kg to the first MTC equipment. By the method, group members in the grouped MTC equipment can be safely managed.
Owner:ZTE CORP
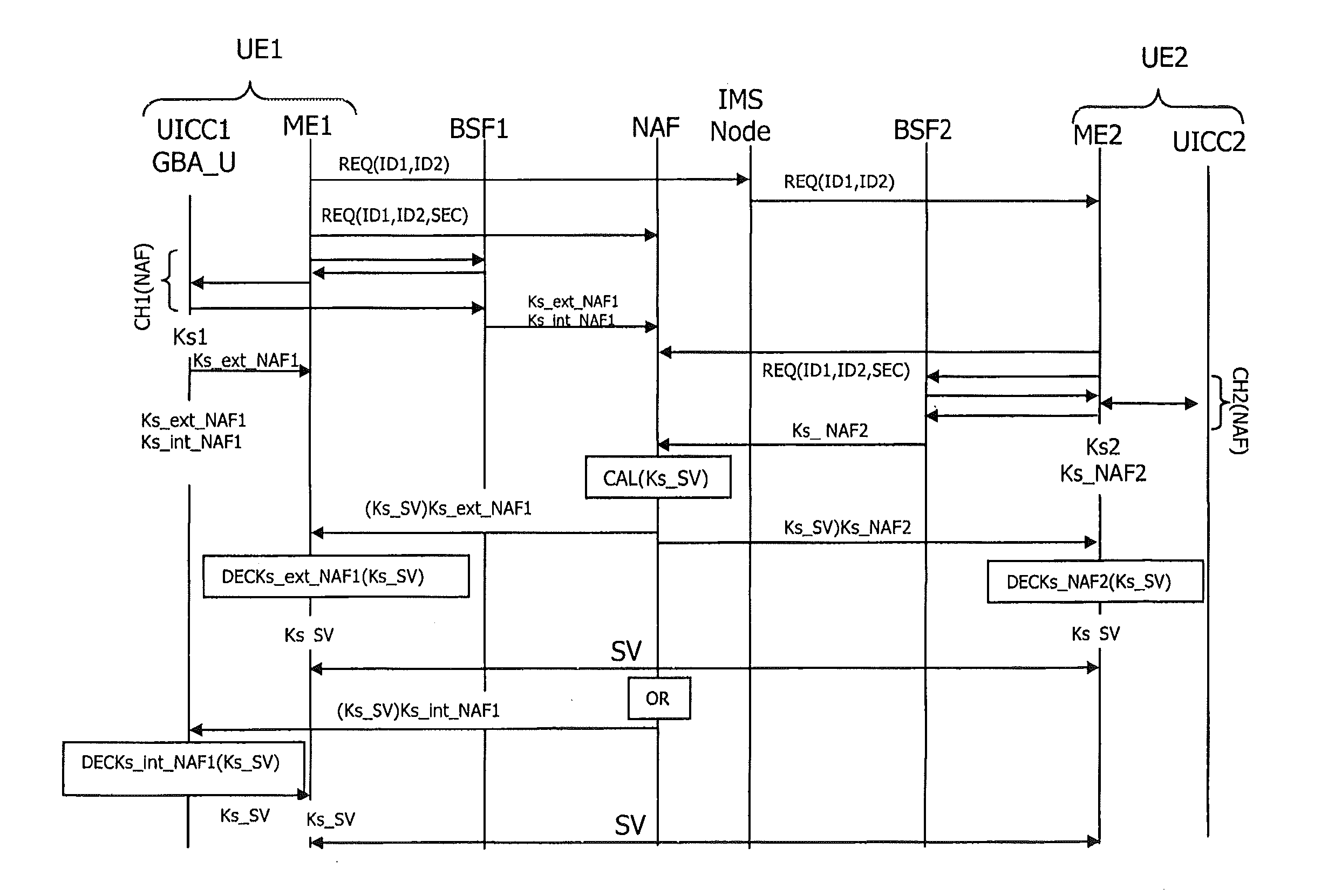
Method to establish a secure voice communication using generic bootstrapping architecture
InactiveUS20160044505A1Improve securityKnown materialSecret communicationTransmissionVoice communicationGeneric Bootstrapping Architecture
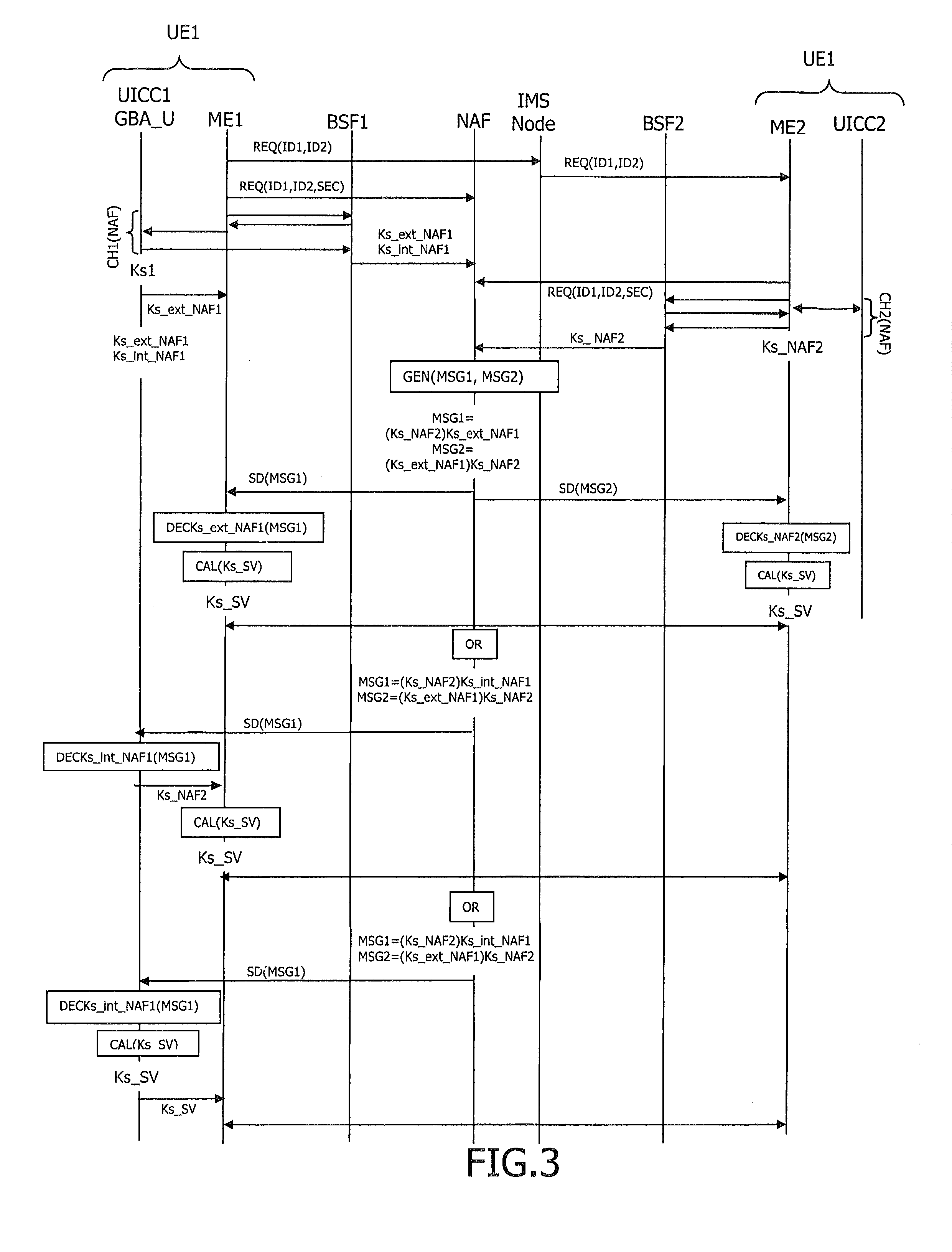
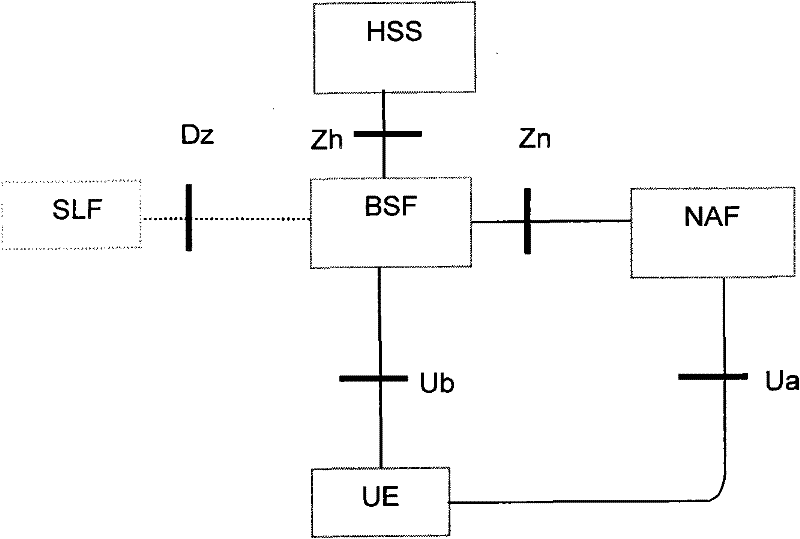
The present invention relates to a method to establish a secure voice communication session between two user equipments with the help of a dedicated Network Application Function (NAF) and at least one Bootstrapping Server Function. A session key is calculated from bootstrapping service derived external or internal NAF keys of the first and the second user equipments. A secured voice communication is established using the calculated session key.
Owner:GEMPLU
Method, device and system for updating key of general guide architecture
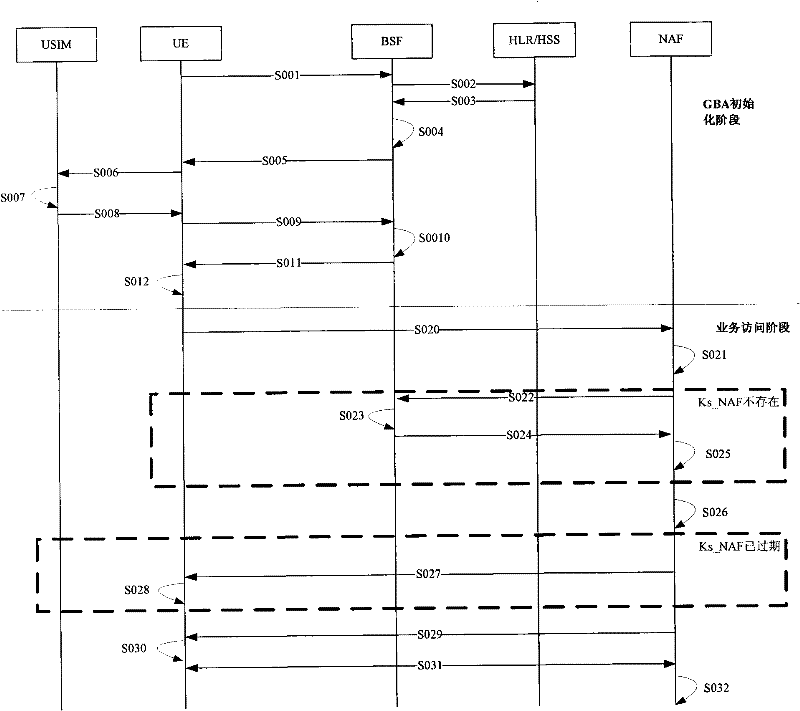
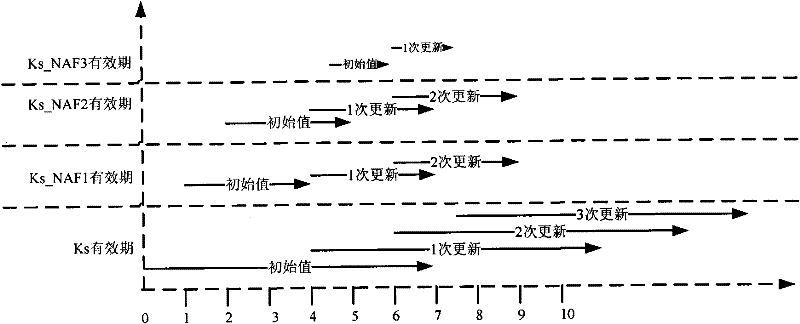
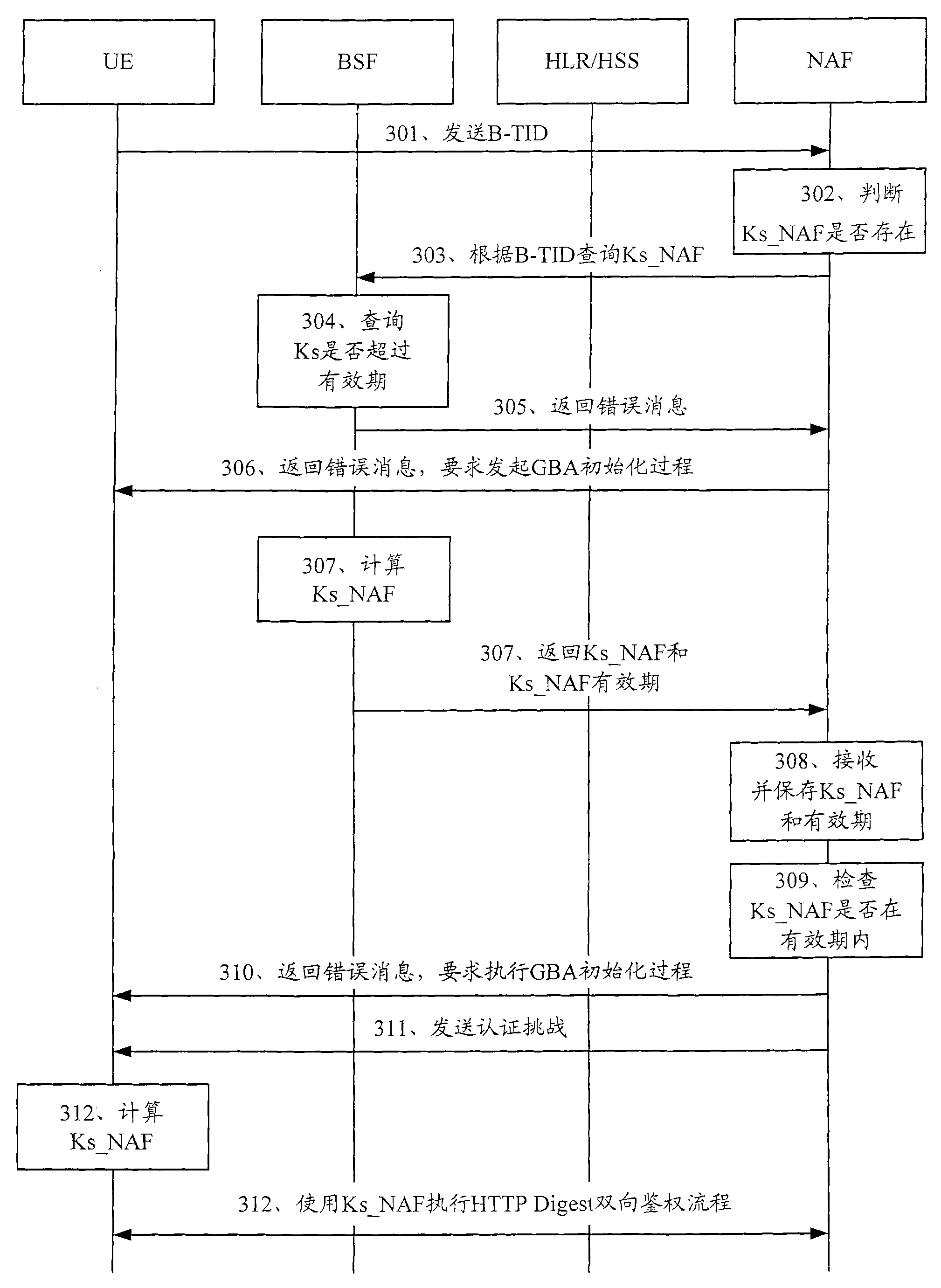
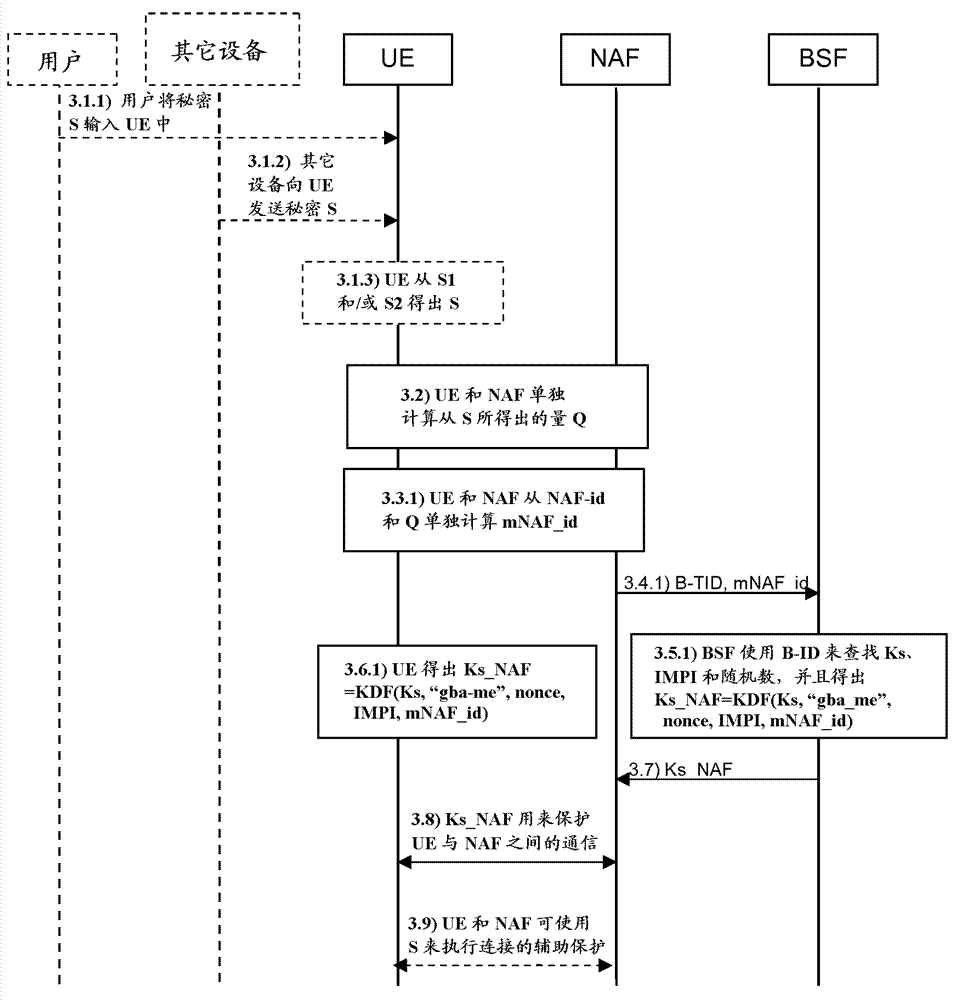
The invention discloses a method, device and system for updating the key of a general guide architecture. The method for updating the key of the general guide architecture comprises the following steps of: receiving a Ks_NAF (Network Application Function) acquisition request with a BSF (Bootstrapping Server Function); obtaining a key parameter, and generating a Ks_NAF according to the formula that Ks_NAF=KDF(Ks, a preset character string, RAND: random, IMPI:IP Multimedia Private Identity, NAF_ID and the key parameter); storing and returning the Ks_NAF and the key parameter. When the method for updating the key of the general guide architecture disclosed by the invention is used for updating a GBA (Genetic Bootstrapping Architecture) key, frequent updating of Ks which is not out of date is avoided, and the key updating load of the BSF and a service platform is reduced.
Owner:CHINA MOBILE COMM GRP CO LTD
Method, device and system for updating key
ActiveCN102065421AReduce update loadAvoid frequent updatesSecurity arrangementComputer hardwareGeneric Bootstrapping Architecture
The embodiment of the invention discloses a method for updating a key. The method comprises the following steps: receiving a bootstrapping service identifier from network application function (NAF) and inquiring whether a root key is in the valid period according to the bootstrapping service identifier; if the root key is not in the valid period, returning the error message to user equipment (UE) by NAF and ensuring NAF to initiate generic bootstrapping architecture (GBA) with the UE; and if the root key is in the valid period, generating a random number, obtaining a service key according to the random number, sending the service key, the valid period of the service key and the random number to NAF and ensuring NAF to carry out two-way authentication with the UE according to the service key and the random number. The embodiment of the invention reduces the load of bootstrapping server function (BSF) and the load of a service server. The embodiment of the invention also discloses a device and system applying the method.
Owner:CHINA MOBILE COMM GRP CO LTD
Using GAA to derive and distribute proxy mobile node home agent keys
InactiveUS7984486B2Digital data processing detailsUser identity/authority verificationMessage authentication codeProtocol for Carrying Authentication for Network Access
A Generic Authentication Architecture bootstrapping procedure is performed between a mobile terminal and a bootstrapping server function resulting in the mobile terminal and the bootstrapping server function each acquiring at least a bootstrapping transaction Identifier associated with the mobile terminal and a corresponding shared key. The mobile terminal derives a network application function specific key based on at least the acquired shared key and an identifier of said network application function. The bootstrapping transaction identifier and the network application function specific key are sent from the mobile terminal to the proxy mobile node. A request message for Mobile Internet Protocol registration is sent from the proxy mobile node to a home agent on behalf of the mobile terminal, the request message including the bootstrapping transaction identifier and an identifier of the proxy mobile node. The registration message is verified in the home agent with the use of a network application function specific key obtained from the bootstrapping server function or a network application function. The request message for Mobile Internet Protocol registration is authenticated with the proxy mobile node acting on behalf of the mobile terminal by verifying the message authentication code with the obtained network application function specific key.
Owner:WSOU INVESTMENTS LLC
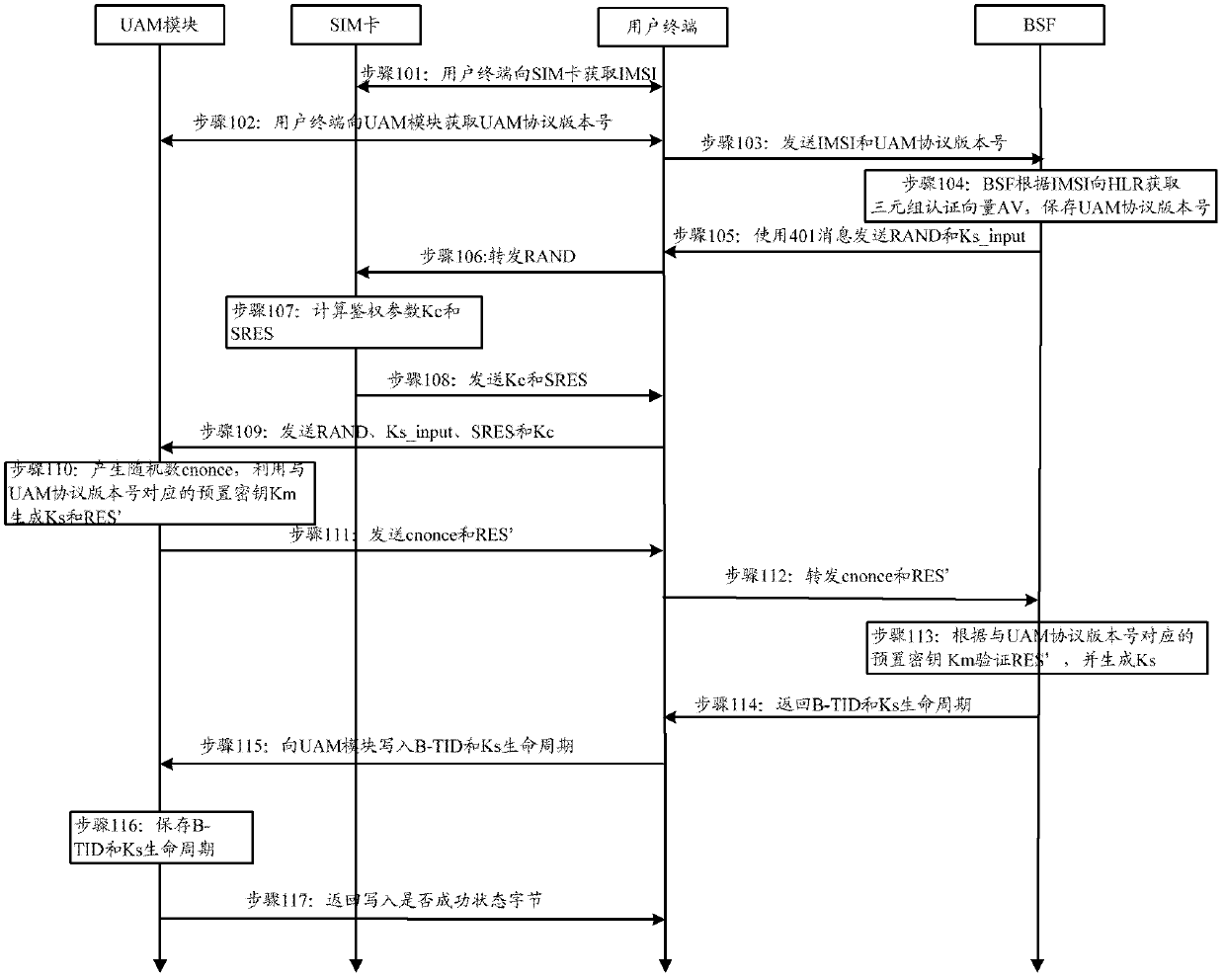
Authentication method and device based on generic bootstrapping architecture (GBA)
ActiveCN103313244AAvoid security risksRealize "One UAM One Password"Security arrangementBootstrapping Server FunctionUser authentication
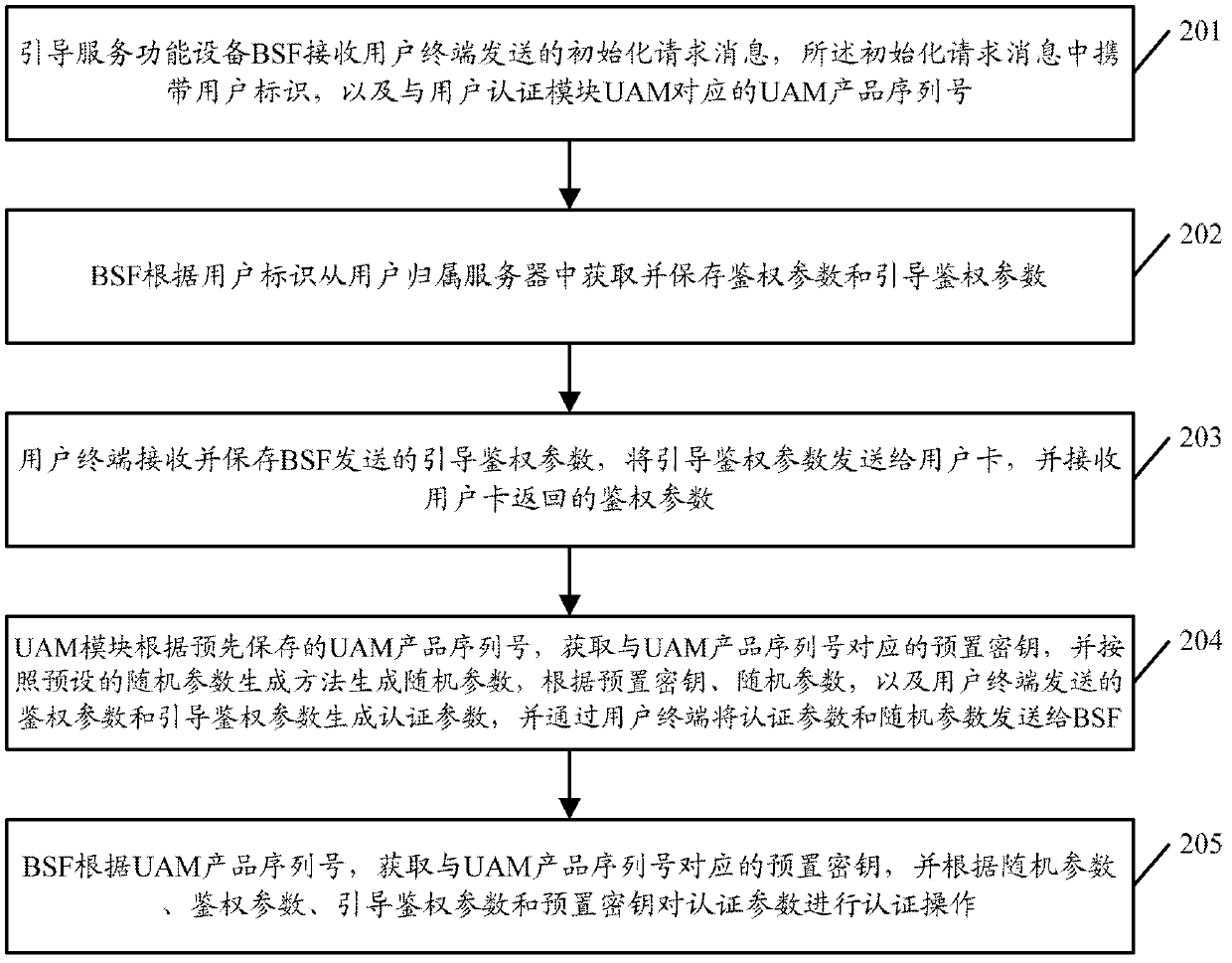
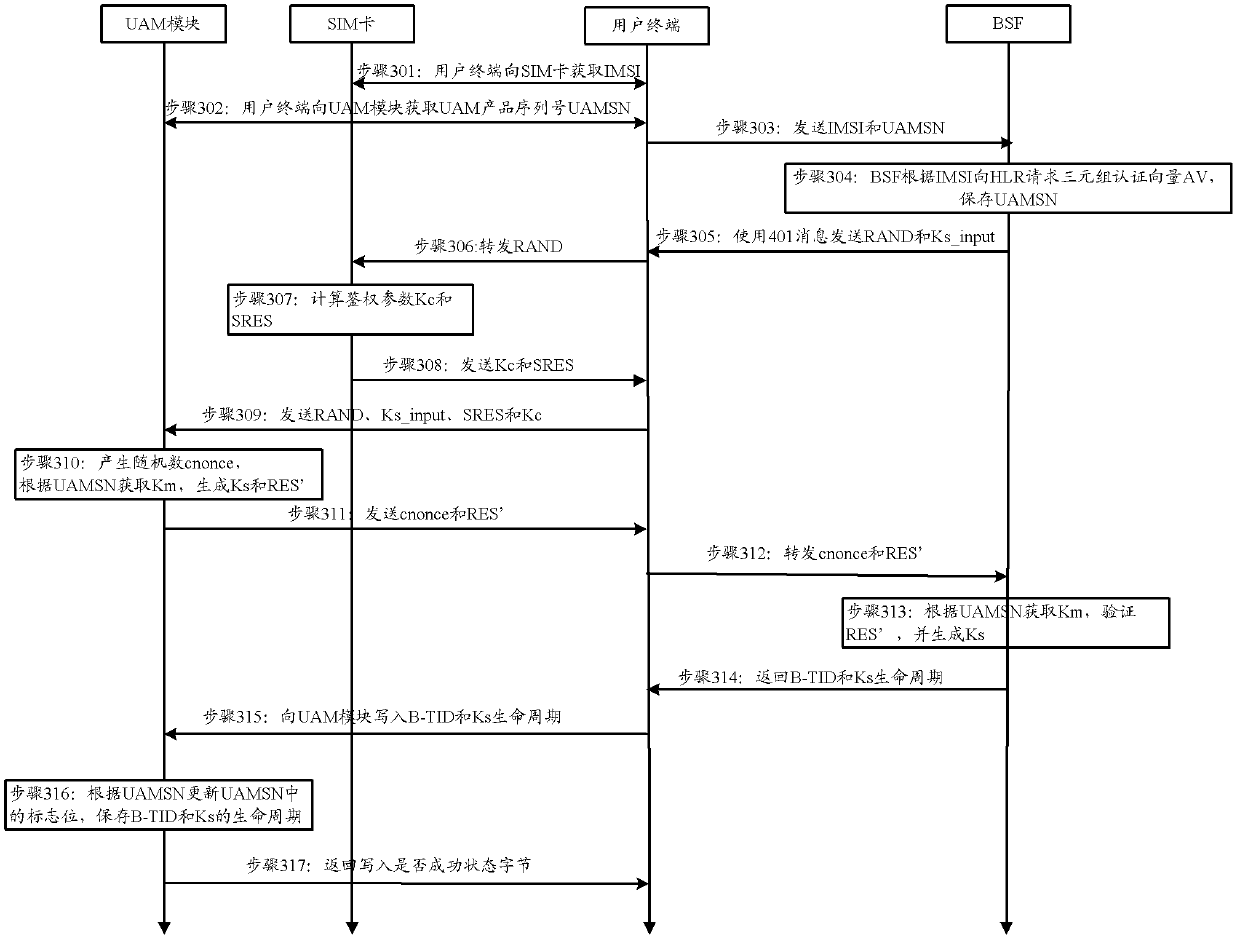
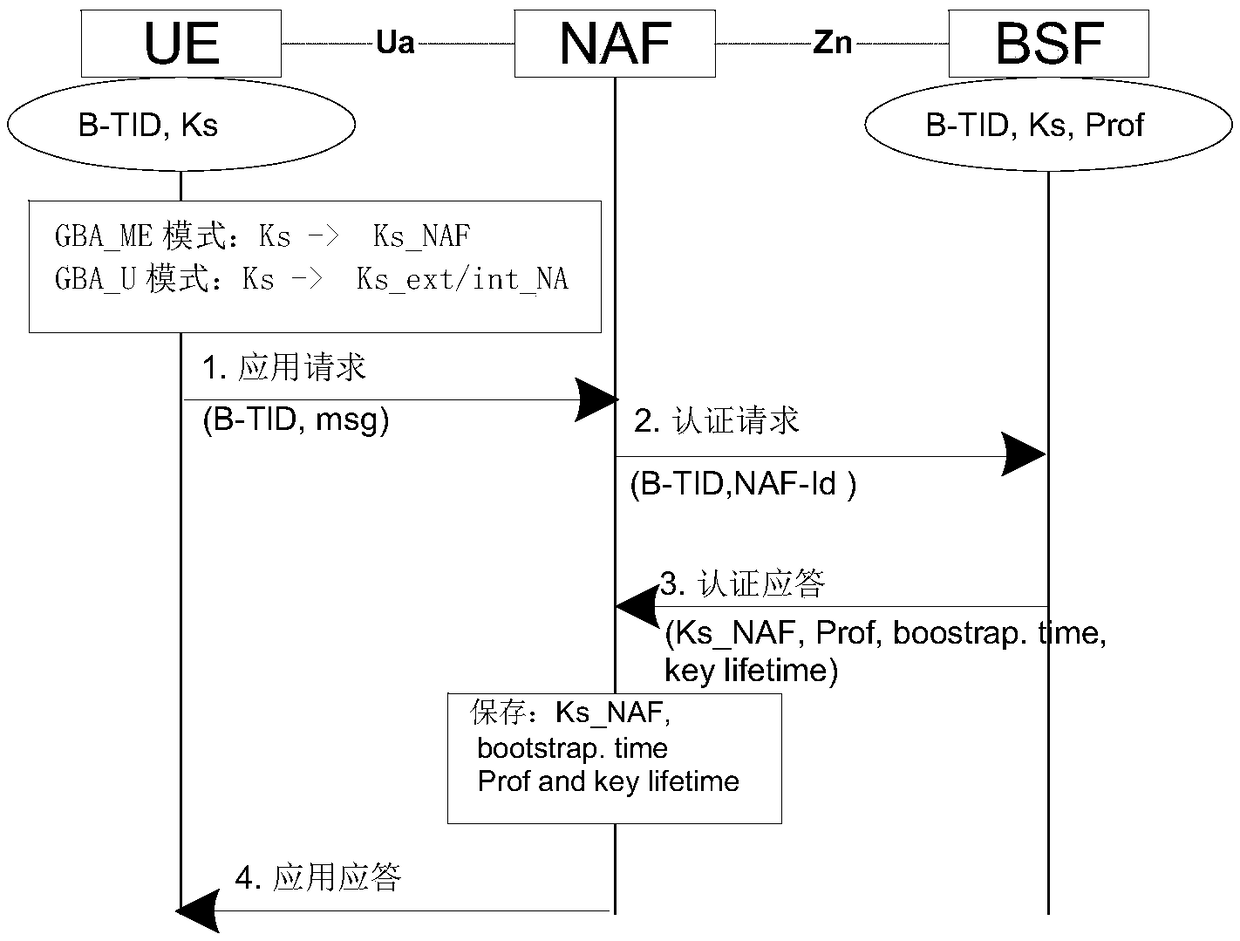
The invention discloses an authentication method and device based on a generic bootstrapping architecture (GBA). The method comprises the steps of: receiving an initial request message which is sent from a user terminal through a bootstrapping server function (BSF), and obtaining and storing authentication parameters and guide authentication parameters from a user attribution server according to a user identification which is carried in the message; receiving and storing the guide authentication parameters which are sent from the BSF through utilizing the user terminal, transmitting the guide authentication parameters to a user card, and receiving the authentication parameters which are set back from the user card; obtaining the corresponding preset secret keys of user authentication module (UAM) product serial numbers through a UAM module, generating random parameters, and generating certification parameters according to the preset secret keys, the random parameters and the authentication parameters and the guide authentication parameters which are set by the user terminal; obtaining the corresponding preset secret key through the BSF according to the UAM product serial numbers carried in the initial request message, and authenticating the certification parameters according to the random parameters, the authentication parameters, the guide authentication parameters and the preset secret keys. Compared with the prior art, the safety of a GBA initial process can be improved.
Owner:CHINA MOBILE COMM GRP CO LTD
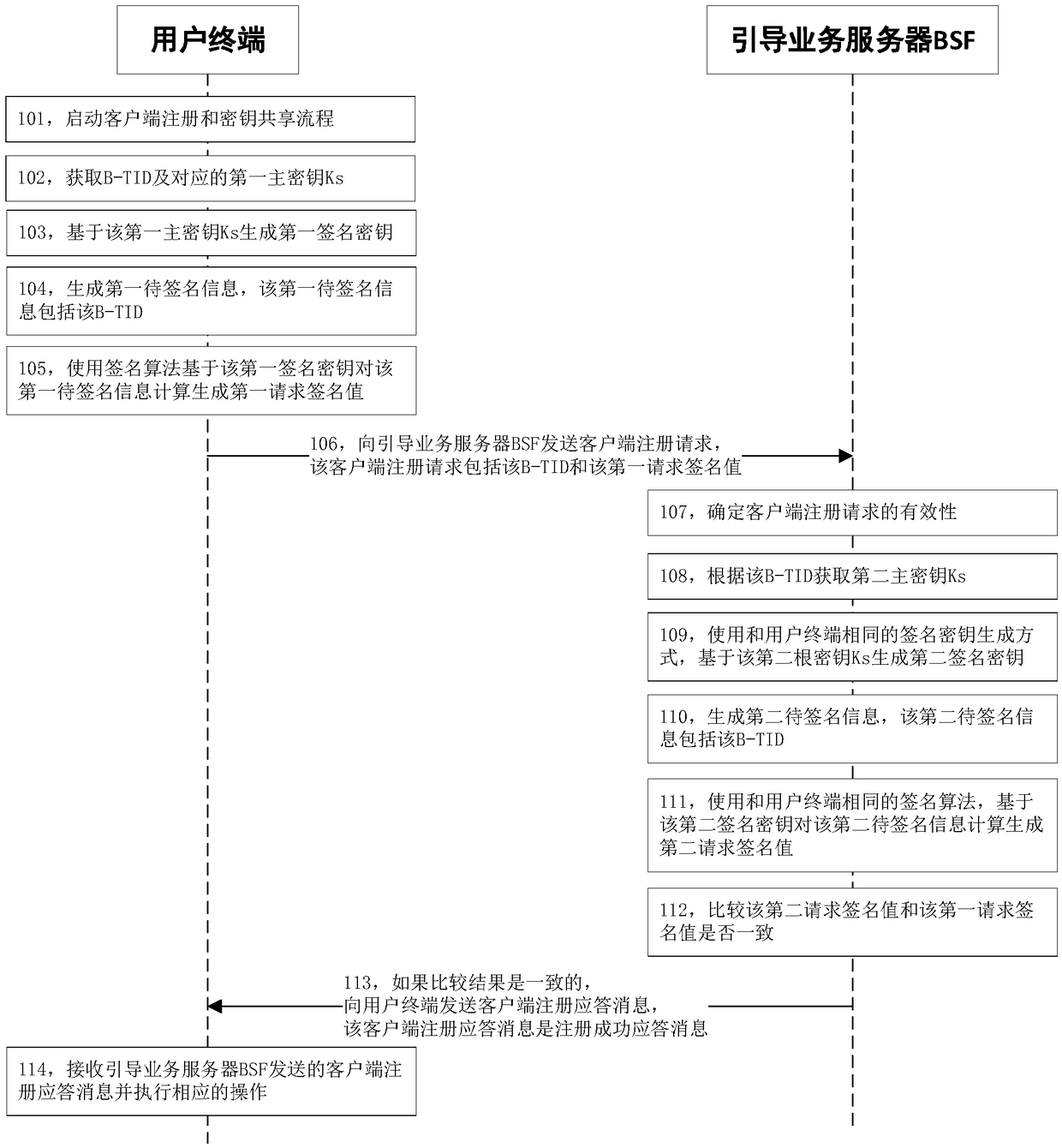
Client registration and secret key sharing method, device and system based on GBA
InactiveCN109121135AOvercoming technical deficienciesSecurity arrangementSecuring communicationThird partyGeneric Bootstrapping Architecture
The present invention discloses a client registration and secret key sharing method, device and system based on GBA (Generic Bootstrapping Architecture). The method comprises the steps of: operating auser terminal with a third-party application client to send a client registration request to a guidance business server BSF (Bootstrapping Server Function), wherein the client registration request comprises a B-TID (Bootstrapping Transaction Identifier) and a first request signature value; and verifying the validness of the first request signature value in the client registration terminal according to the B-TID and the corresponding secret key, and after the verification is valid, providing safe registration information and service for the third-party application client after, and generatingan application secret key for the third-party application client.
Owner:刘高峰
Method and apparatus for direct communication key establishment
InactiveCN108141755AService provisioningNetwork topologiesAir interfaceGeneric Bootstrapping Architecture
A method, performed by a User Equipment device (UE), for obtaining a key for direct communication with a device over an air interface, wherein the UE has previously acquired a transaction identifier received from a Bootstrapping Server Function (BSF), in a Generic Bootstrapping Architecture (GBA), procedure, is provided. The method comprises storing the transaction identifier, sending the transaction identifier to the device and requesting key generation for direct communication with the device. If the transaction identifier is invalid, the method further comprises receiving from the device adevice identifier and key generation information, deriving a session shared key from at least the key generation information, and deriving a direct communication key from at least the session shared key and the device identifier.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and apparatus for securing a connection in a communications network
ActiveCN104756458ASecurity arrangementSecuring communicationSecure communicationGeneric Bootstrapping Architecture
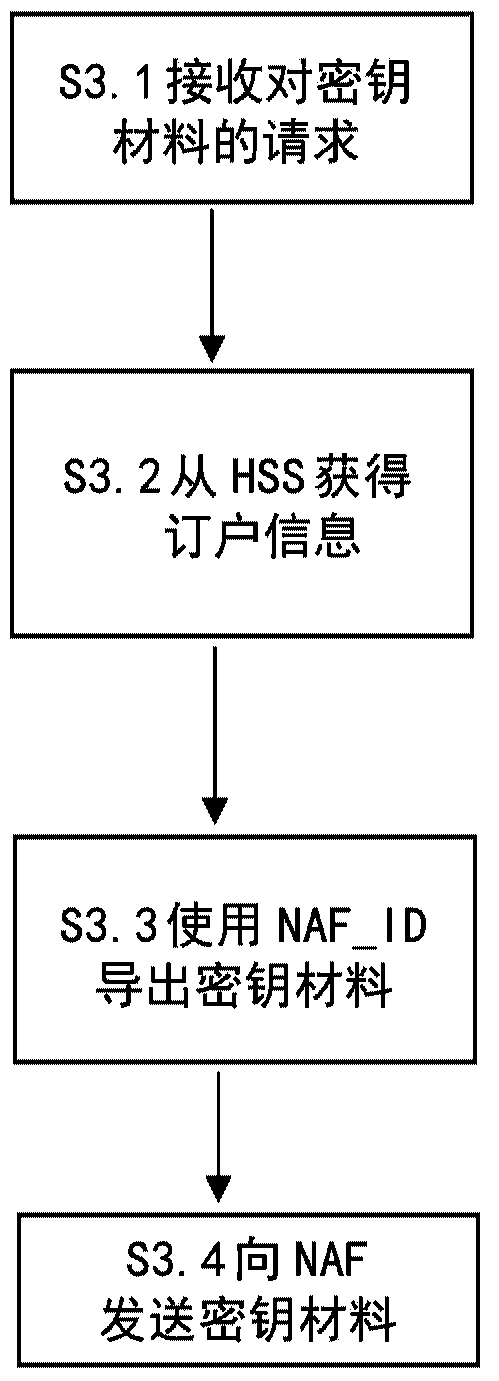
A method of securing a session between a Network Application Function, NAF, and a User Equipment, UE, connected to a network. The NAF is assigned a NAF identifier, NAF_id, using the Generic Bootstrapping Architecture, GBA, or a similar architecture and a shared secret is established between the UE and the NAF (S7.1). An application request containing a bootstrapping transaction identifier is sent to the NAF from the UE (S7.2) and an authentication request comprising the bootstrapping transaction identifier, the NAF_id, and information derived from the shared secret is sent to a Bootstrapping Server Function, BSF, from the NAF (S7.4).The BSF and the UE determine a NAF key, Ks_NAF, by using a modified parameter in place of or in addition to an original parameter in a key derivation function, the modified parameter being derived from the shared secret and the original parameter of the key derivation function (S7.5). This NAF key is transmitted from the BSF to the NAF (S7.6) and used to secure communications between the NAF and the UE (S7.7). Also provided are apparatus to act as a NAF, UE, and BSF in the method above.
Owner:TELEFON AB LM ERICSSON (PUBL)
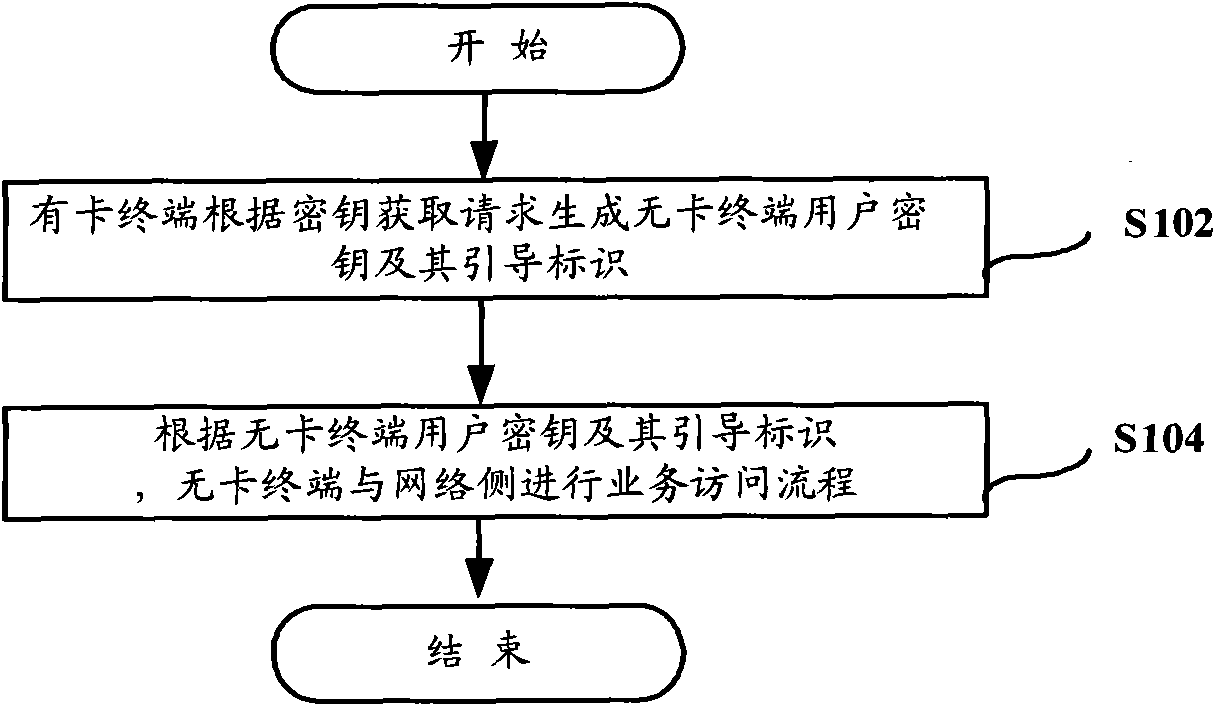
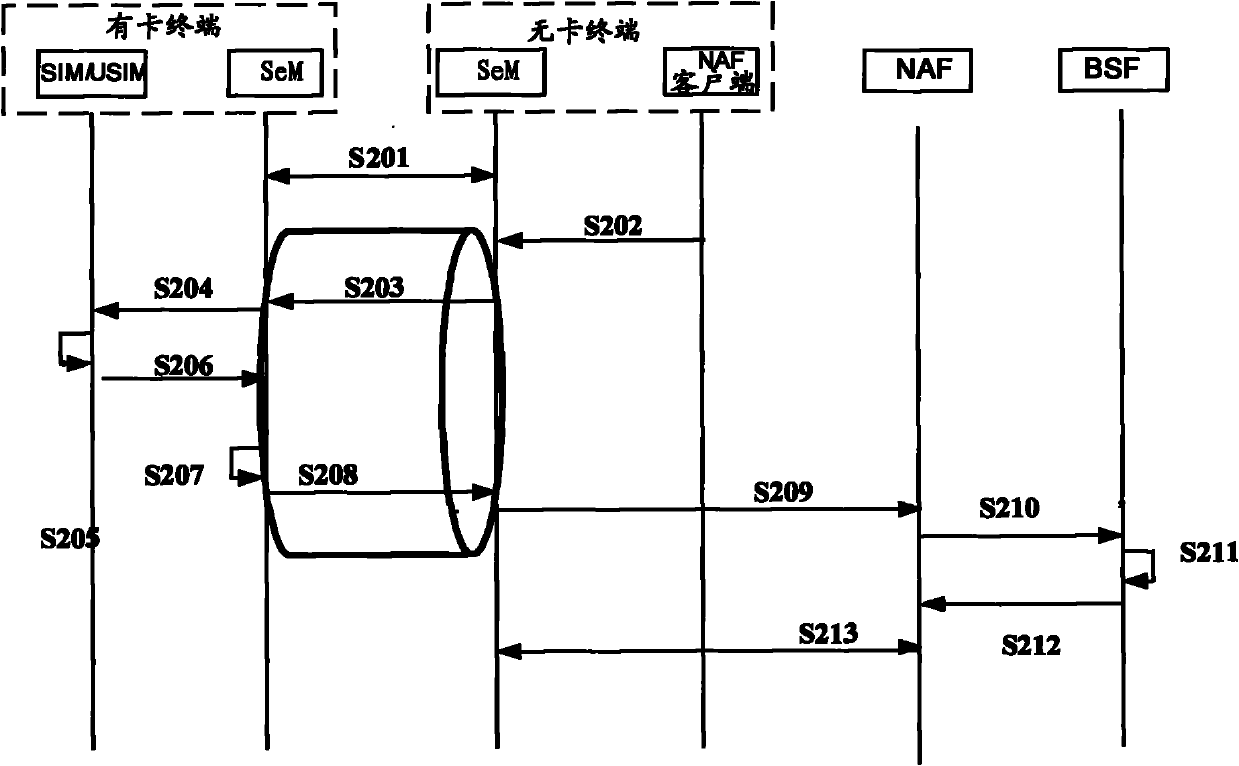
Card-free terminal, service access method and system thereof, terminal with card and bootstrapping server function (BSF)
The invention provides a card-free terminal, a service access method for the card-free terminal, a service access system for the card-free terminal, a terminal with a card, and a bootstrapping server function (BSF). The method comprises that: when receiving a key acquisition request from the card-free terminal, the terminal with the card generates a card-free terminal user key and a pilot identifier used for identifying the card-free terminal user key according to the key acquisition request; and the card-free terminal performs a service access flow with a network side according to the card-free terminal user key and the pilot identifier. By the card-free terminal, the method, the system, the terminal with the card and the BSF, the card-free terminal can acquire the key from the terminal with the card for service access.
Owner:CHINA MOBILE COMM GRP CO LTD
Implementing a Security Association During the Attachment of a Terminal to an Access Network
ActiveUS20150189507A1Reduce signalingMinimize the numberDigital data processing detailsNetwork topologiesAccess networkSecurity association
A method is provided for implementing a security association for a terminal being attached to an access network. The method includes the following steps, carried out by an authentication server of the access network, after receiving a request coming from the terminal for attachment to the network: receiving a first message containing at least one security association parameter from a bootstrapping server function; authenticating the terminal by using at least one first authentication parameter provided by a home subscriber server of the terminal; and sending a security association message containing the at least one security association parameter to the authenticated terminal.
Owner:ORANGE SA (FR)
Smart card security feature profile in home subscriber server
In accordance with the exemplary embodiments of the invention there is at least a method, an executable computer program, and an apparatus to determine at a network application function a list of desired user equipment security features to be used, the security features of the list ordered by preference of the network application function, send the list to a database of user security settings via a bootstrapping server function, and receive by the network application function, via the bootstrapping server function, a security features response including a security key,derived from information stored in the database, corresponding to a desired security feature contained in the list, thereby informing the network application function of the availability of at least one of the desired security features in the user equipment.
Owner:NOKIA TECHNOLOGLES OY
Generic bootstrapping architecture protocol
ActiveUS20170041785A1Improve securityReduce the numberMessaging/mailboxes/announcementsSecurity arrangementGeneric Bootstrapping ArchitectureProxy server
Method and system for communicating securely with a user equipment, UE, using generic bootstrapping architecture, GBA, the system comprising a bootstrapping server function, BSF. A proxy server configured to receive messages from a user equipment, UE, in a first format. Convert the received messages from the first format to a second format. Transmit the received UE messages to a bootstrapping server function, BSF, in the second format. Receive messages from the BSF, in a third format. Convert the messages received from the BSF from the third format to a fourth format. Transmit the received BSF messages to the UE in the fourth format.
Owner:VODAFONE IP LICENSING
Generic bootstrapping architecture protocol
ActiveCN106714154AMessaging/mailboxes/announcementsSecurity arrangementGeneric Bootstrapping ArchitectureSchema for Object-Oriented XML
Owner:VODAFONE IP LICENSING
Network application function authorisation in a generic bootstrapping architecture
InactiveCN104247485AComputer security arrangementsSecurity arrangementTelecommunicationsGeneric Bootstrapping Architecture
There is provided a method of authorising a subscriber user equipment to access a Network Application Function, NAF, in a Generic Bootstrapping Architecture, GBA. The method comprises, at a Bootstrapping Server Function, BSF, receiving a request for key material for the subscriber user equipment from the NAF, wherein the NAF is associated with one or more NAF identifiers, NAF_IDs, obtaining subscriber information from a Home Subscriber System, HSS, the information including one or more NAF_IDs that are valid for the subscriber, authorising the subscriber user equipment on the basis of the identity of said NAF and the NAF_ID(s) included within the subscriber information. In the event that the subscriber user equipment is authorised, key material is derived using a NAF_ID that is contained within said subscriber information; and the key material is sent to said NAF.
Owner:TELEFON AB LM ERICSSON (PUBL)
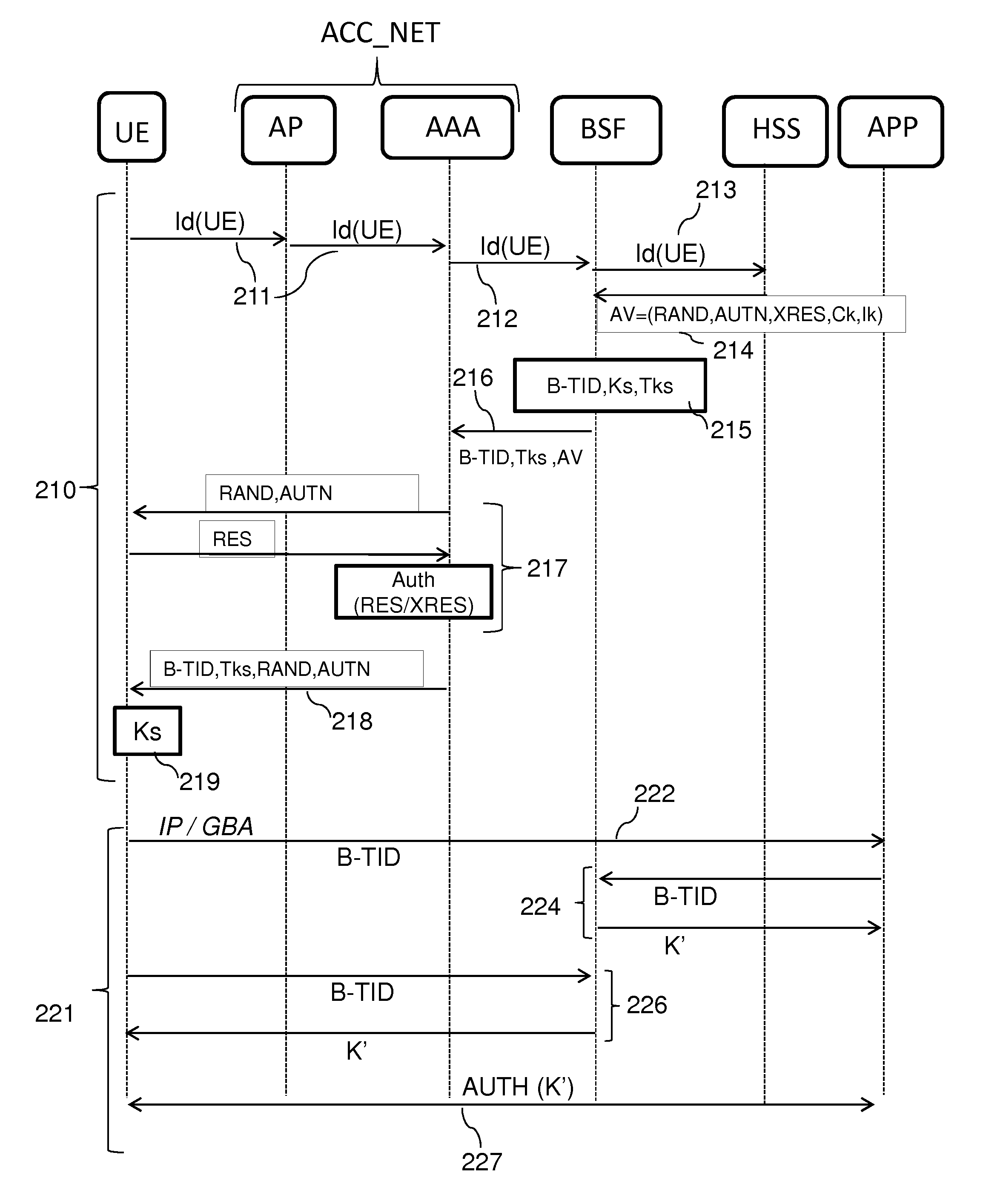
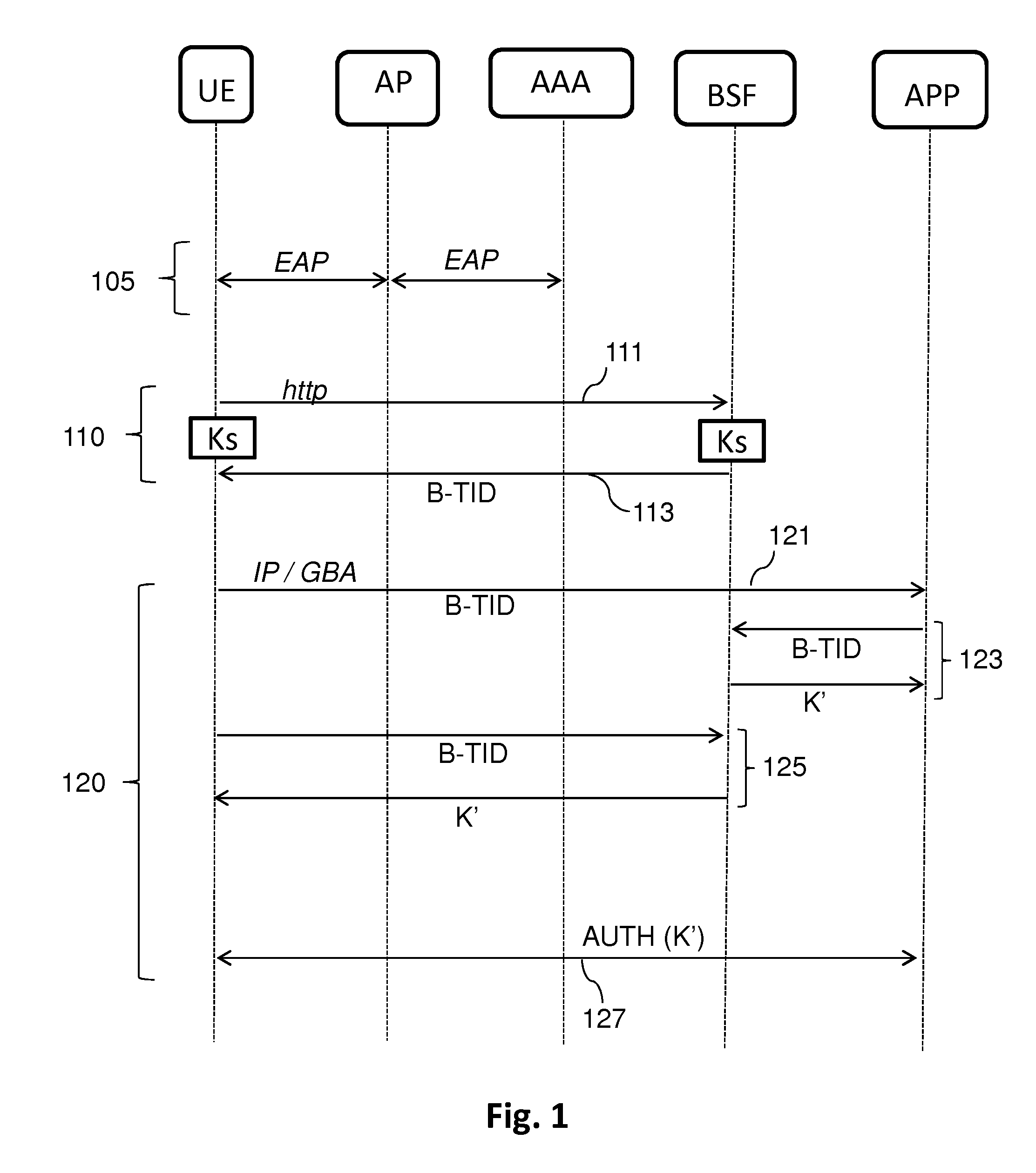
Method and system for recursive authentication in a mobile network
ActiveUS8165565B2Avoid authenticationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird generationMobile ad hoc network
Under a system referred to as GAA in the 3G protocol, authentication of devices in a network that is usually performed by a home subscriber server can be transferred to a third party element known as a bootstrapping server function. However, the use of a bootstrapping server function does not completely address the problem of reducing authentication traffic at the home subscriber server. Such a problem is alleviated by utilizing the original session key generated under GAA and using that key in a recursive process to authenticate and generate further session keys at other network elements. This generation of further keys can be performed independently of the home subscriber server, and thus reduces traffic at the home subscriber server.
Owner:BRITISH TELECOMM PLC
Generic bootstrapping architecture protocol
ActiveUS10484869B2Improve securityReduce the numberKey distribution for secure communicationMessaging/mailboxes/announcementsGeneric Bootstrapping ArchitectureProxy server
Method and system for communicating securely with a user equipment, UE, using generic bootstrapping architecture, GBA, the system comprising a bootstrapping server function, BSF. A proxy server configured to receive messages from a user equipment, UE, in a first format. Convert the received messages from the first format to a second format. Transmit the received UE messages to a bootstrapping server function, BSF, in the second format. Receive messages from the BSF, in a third format. Convert the messages received from the BSF from the third format to a fourth format. Transmit the received BSF messages to the UE in the fourth format.
Owner:VODAFONE IP LICENSING
Method and system for MTC (Machine Type Communication) servers to share key
InactiveCN102595389AImprove efficiencyService provisioningSecurity arrangementSecure communicationGeneric Bootstrapping Architecture
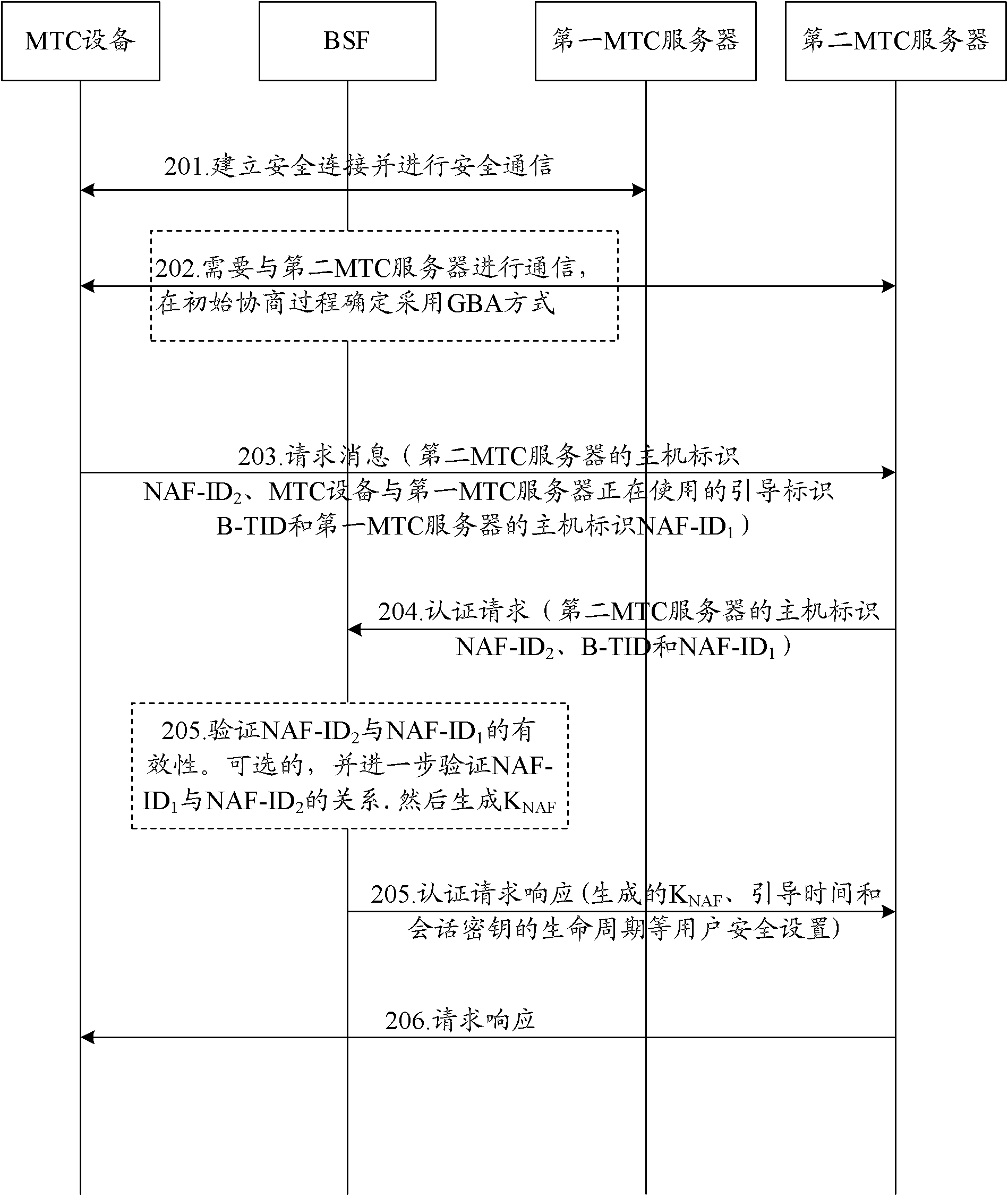
The invention discloses a method for MTC (Machine Type Communication) servers to share a key. The method comprises the following steps of: sending request information, which comprises a boot identity B-TID used by an MTC device and a first MTC server right now and a host identity NAF (Network Application Function)-ID1 of the first MTC server, to a second MTC server when security connection is established and security communication is carried out by the MTC device and the first MTC server through a GBA (Generic Bootstrapping Architecture) process; sending an authentication request, which comprises a host identity NAF-ID2, the B-TID and the NAF-ID1 of the second MTC server, to a BSF (Bootstrapping Server Function) by the second MTC server; and generating a session key KNAF according to the B-TID and the NAF-ID1 after the NAF-ID2 and the NAF-ID1 are verified to be effective by the BSF, and sending the session key KNAF to the second MTC server. The invention also correspondingly discloses a system for the MTC servers to share the key. According to the method and the system which are disclosed by the invention, the security communication between the MTC device and multiple MTC servers can be carried out simultaneously, and the use rate of a network resource can be increased.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com