Method and apparatus for securing a connection in a communications network
A device and network technology, applied in the field of two-factor authentication, can solve problems such as undesirable, slow down the authentication process, and time-consuming for users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
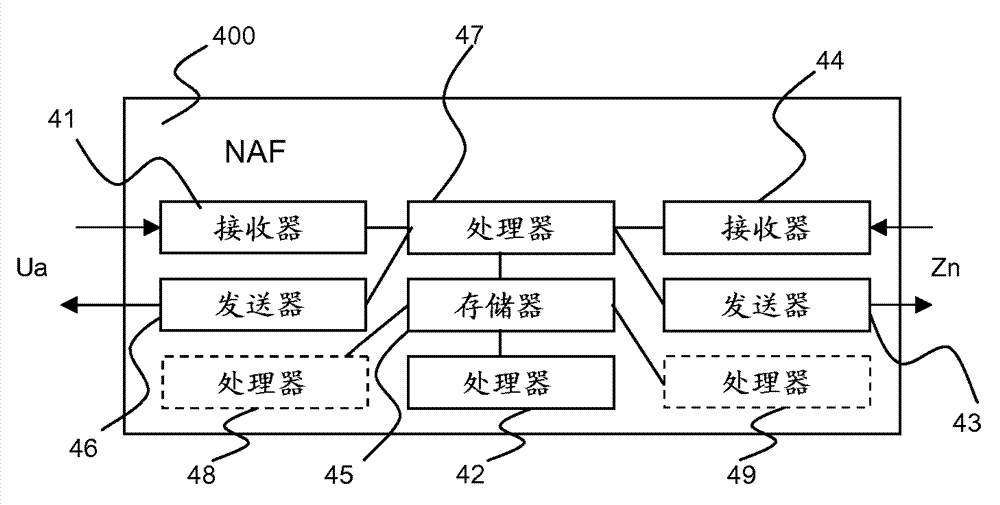
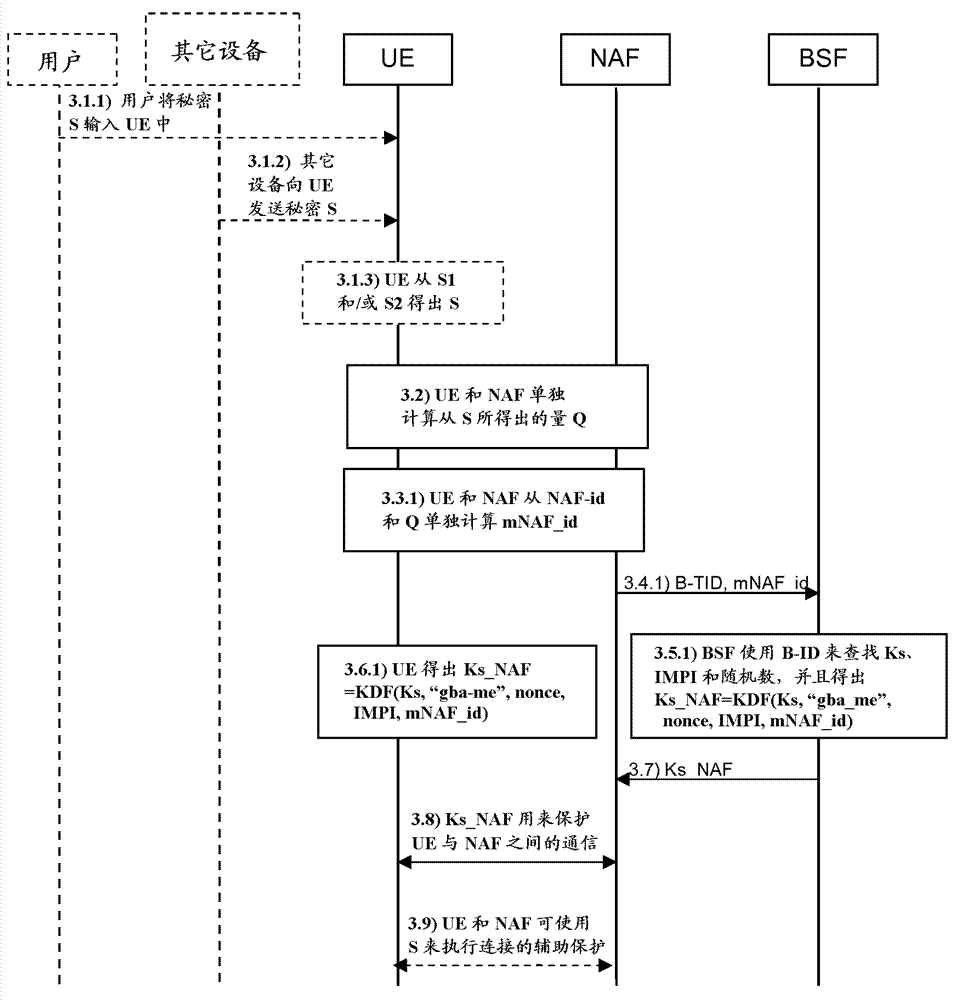
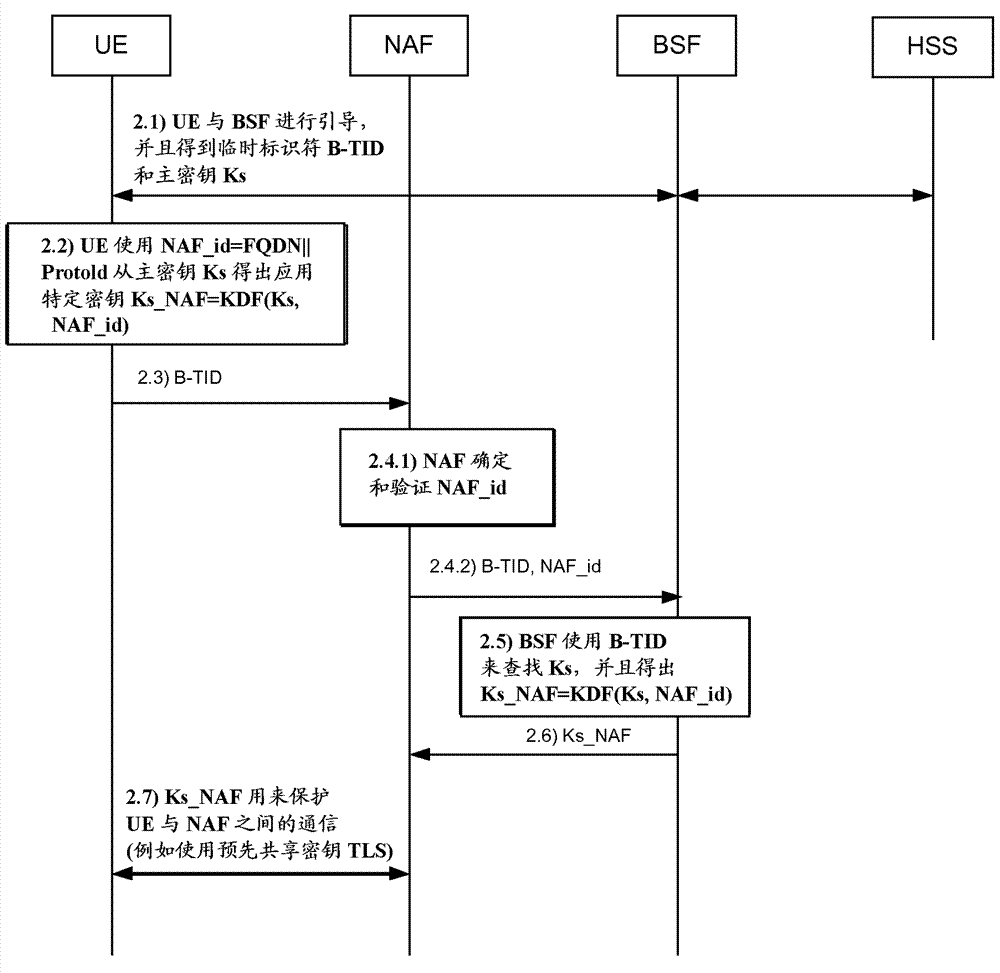
[0043] The Generic Bootstrapping Architecture (GBA) defined in 3GPP Technical Specification TS 33.220 provides a mechanism whereby a client terminal (UE) can be authenticated to a network application function (NAF) and a secure session key can be derived for communication between the UE and the NAF use. Such as figure 2 As shown, the GBA provides a mechanism whereby the UE bootstraps with the Bootstrap Server Function (BSF) such that the UE is authenticated to the BSF and a master key Ks and a Bootstrap Transaction Identifier (B-TID) are obtained. The UE then derives the application specific key Ks_NAF through a Key Derivation Function (KDF) defined as KDF(Ks, "gba-me", nonce, IMPI, NAF_id). Ks is the previously defined master key; "gba-me" is a fixed value; nonce is a random number used to generate Ks; IMPI is the Internet Protocol Multimedia Private Identity of the UE; and NAF_id is the NAF identifier of the NAF. The NAF_ID is formed by concatenating the Fully Qualified D...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com