Patents
Literature
52 results about "Re keying" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
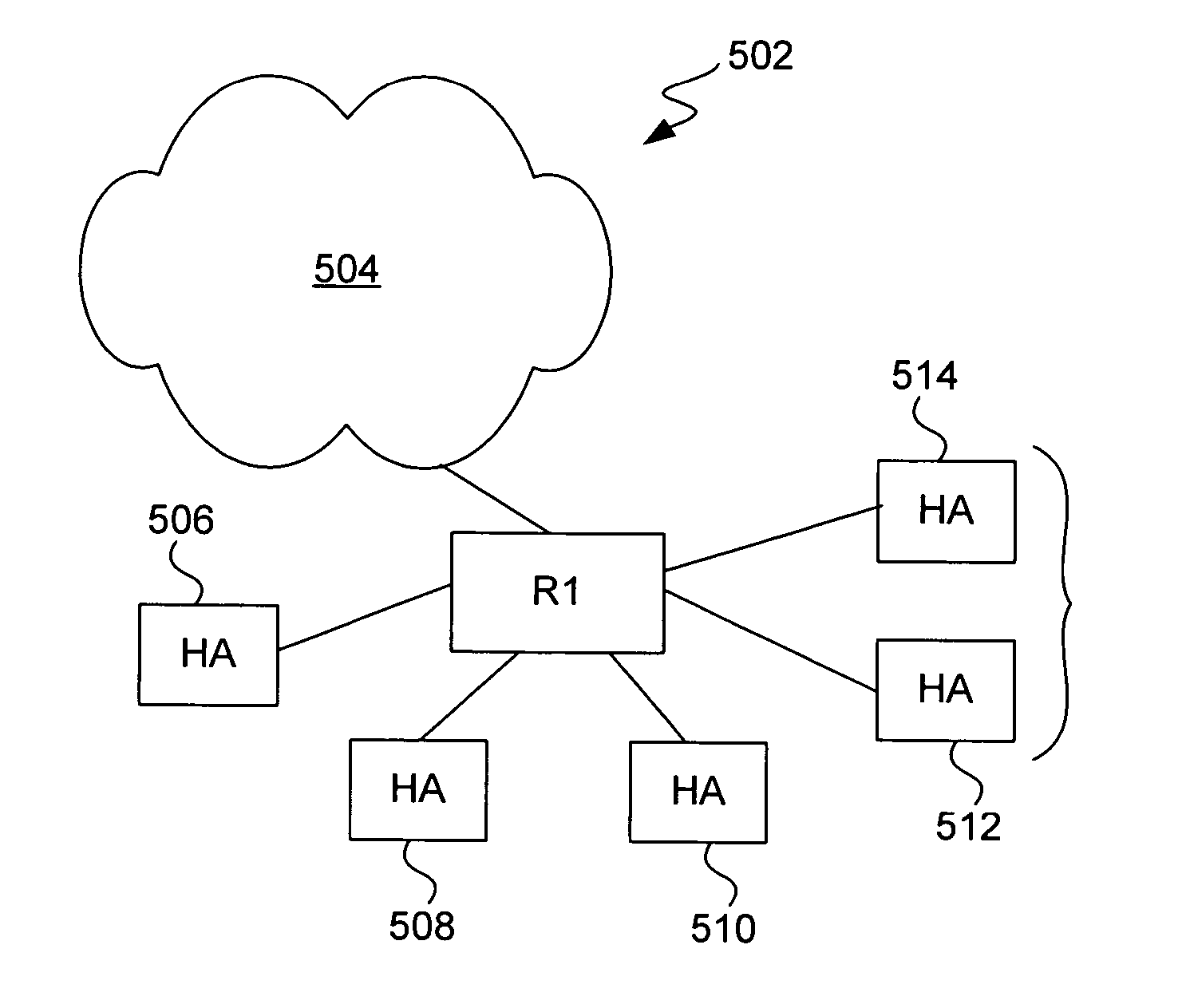
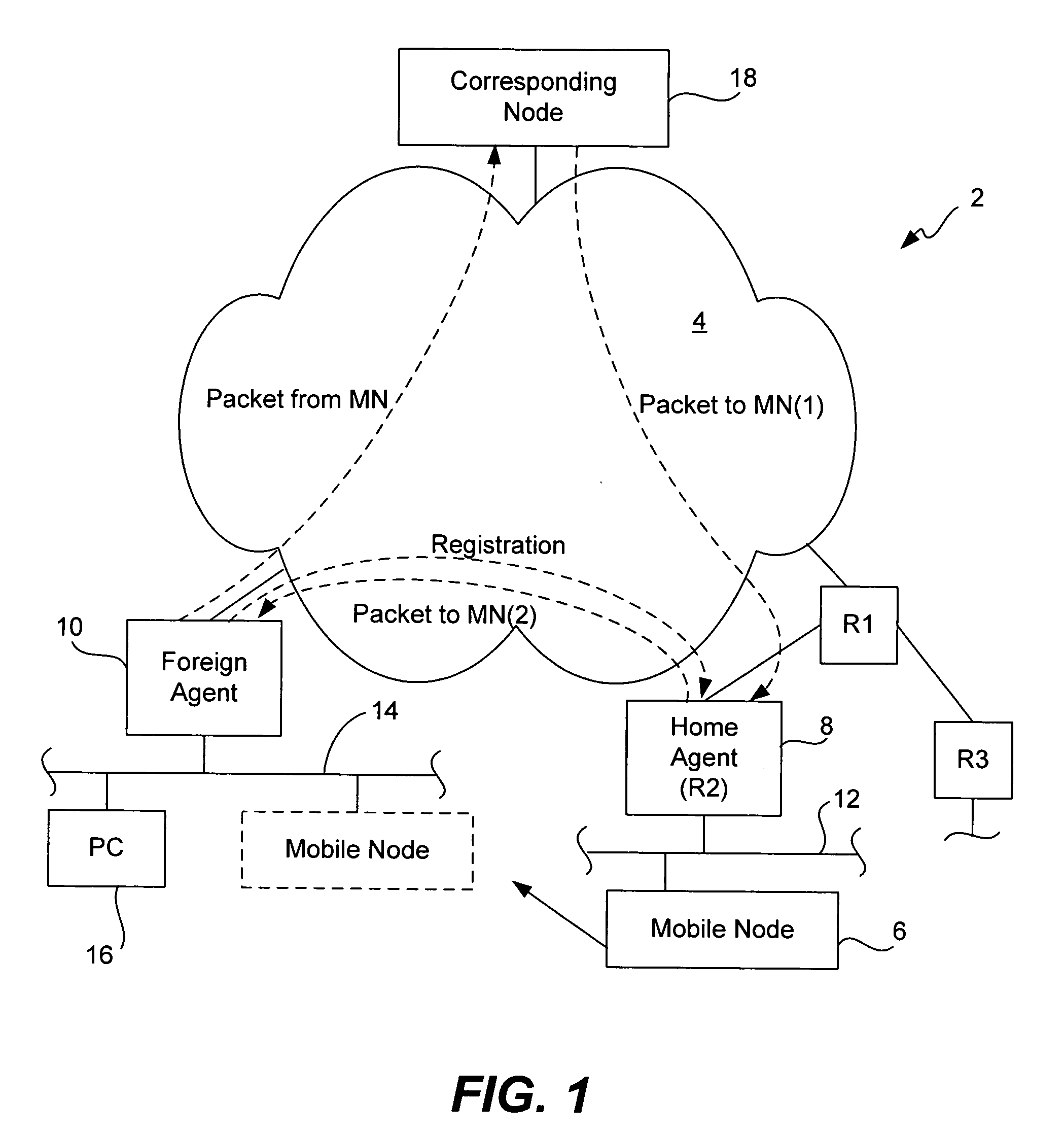
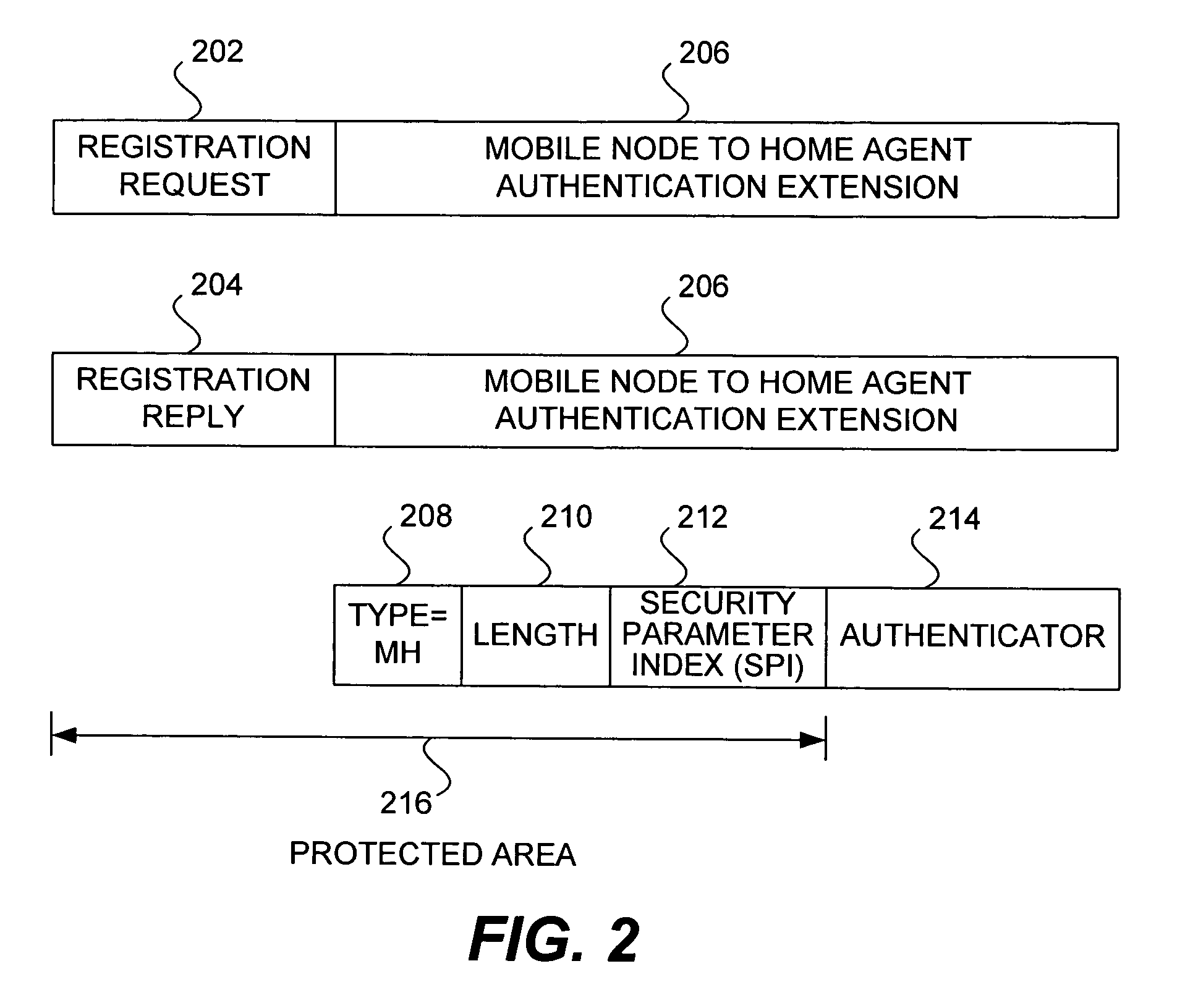
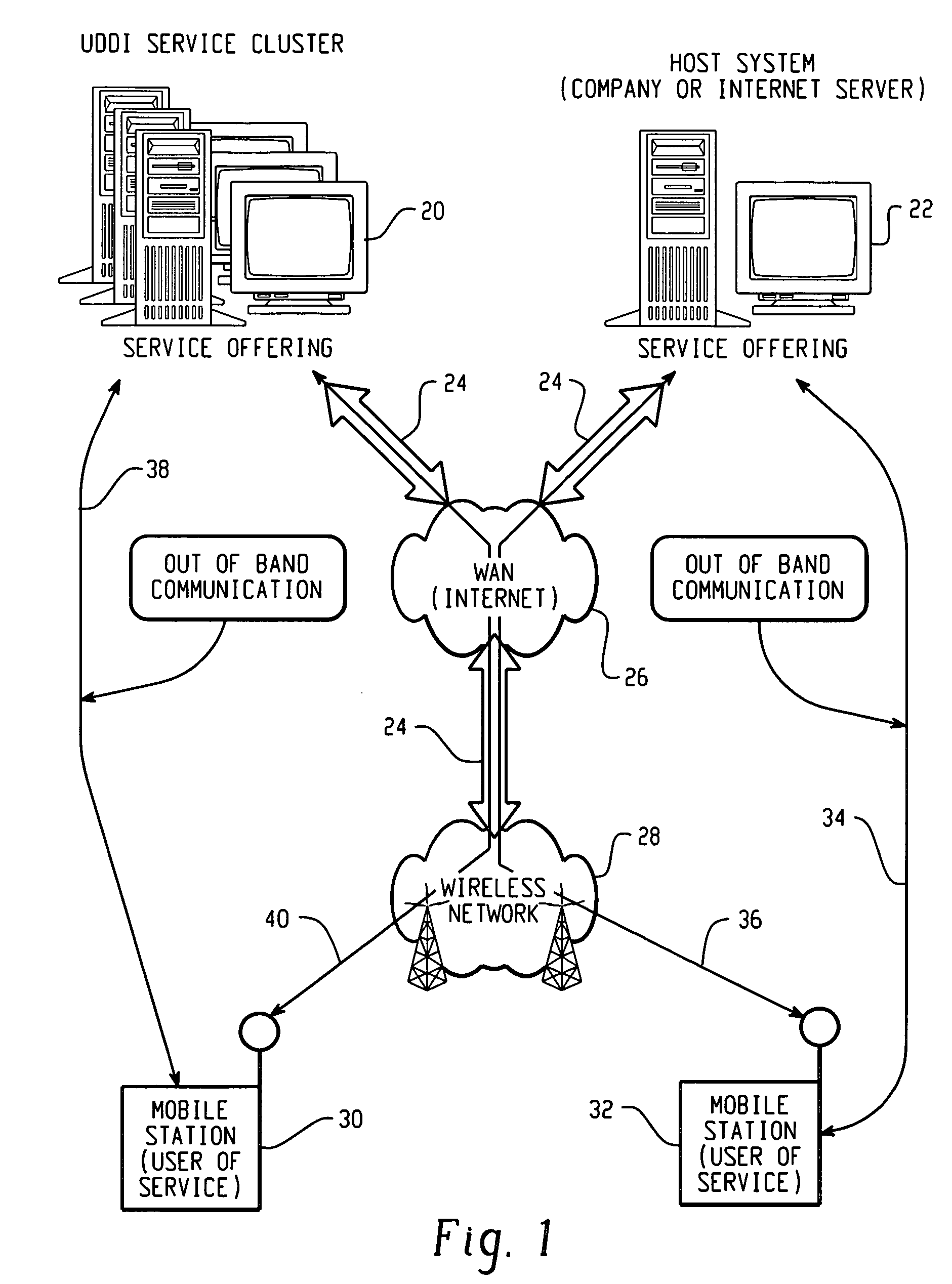
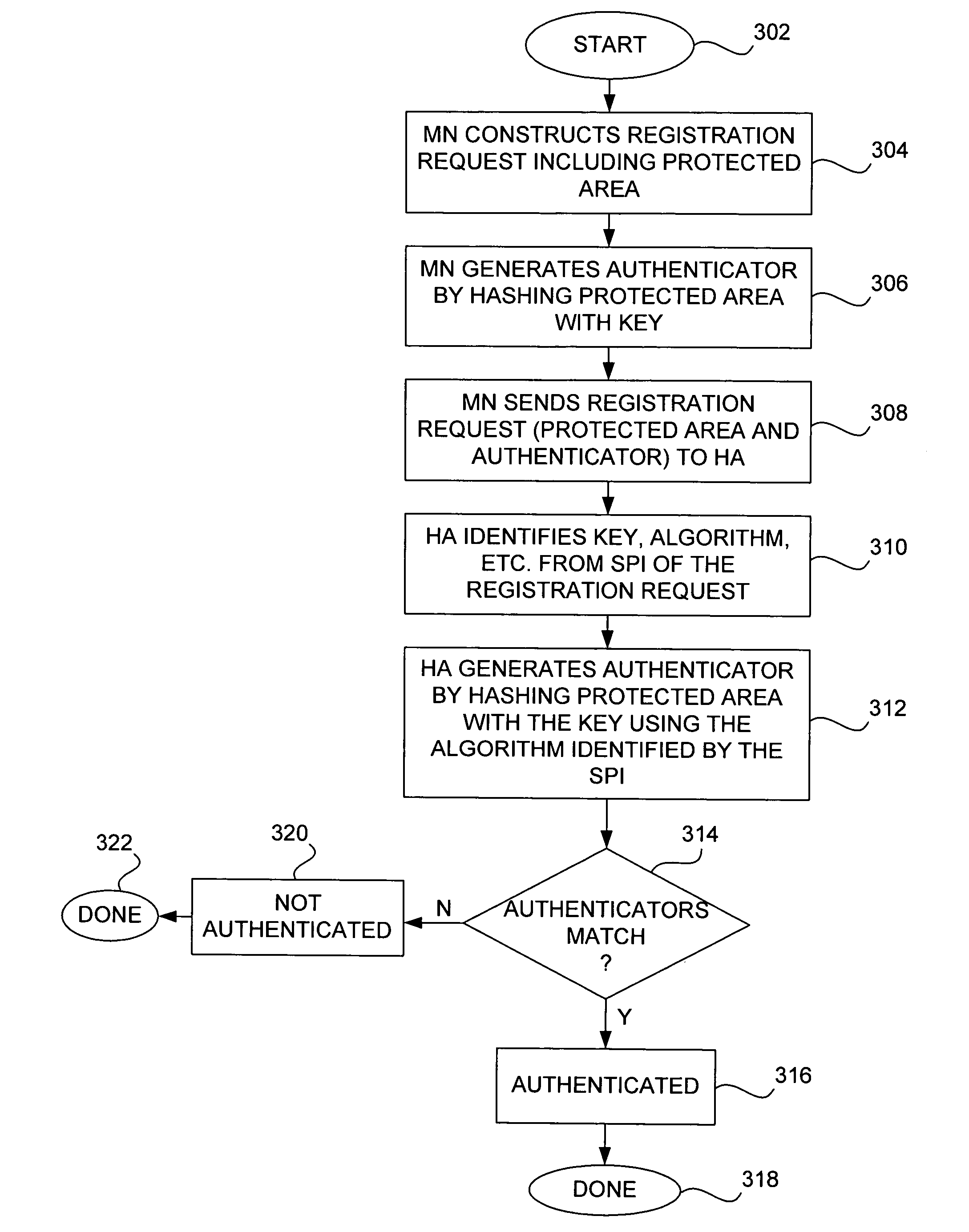
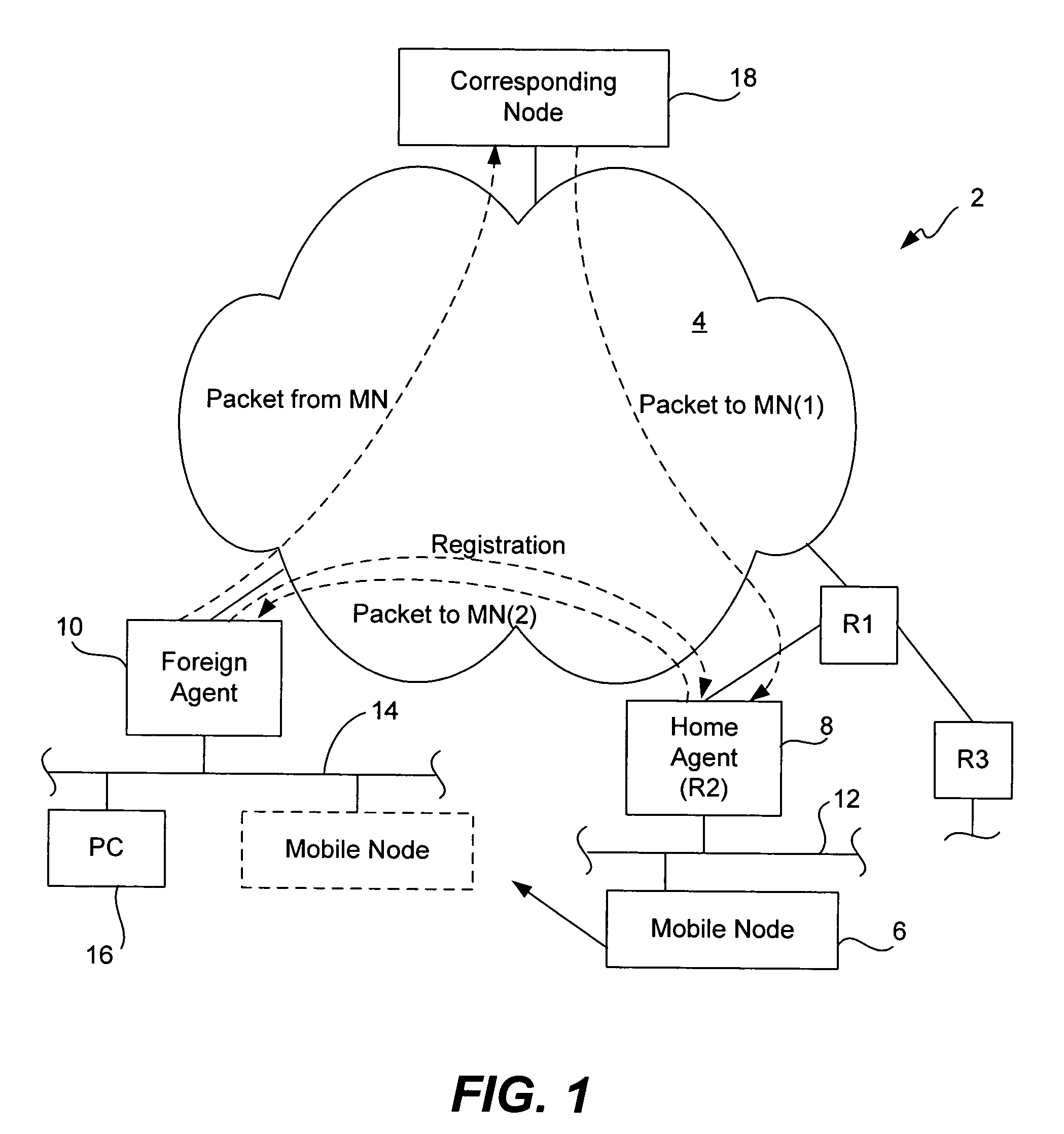
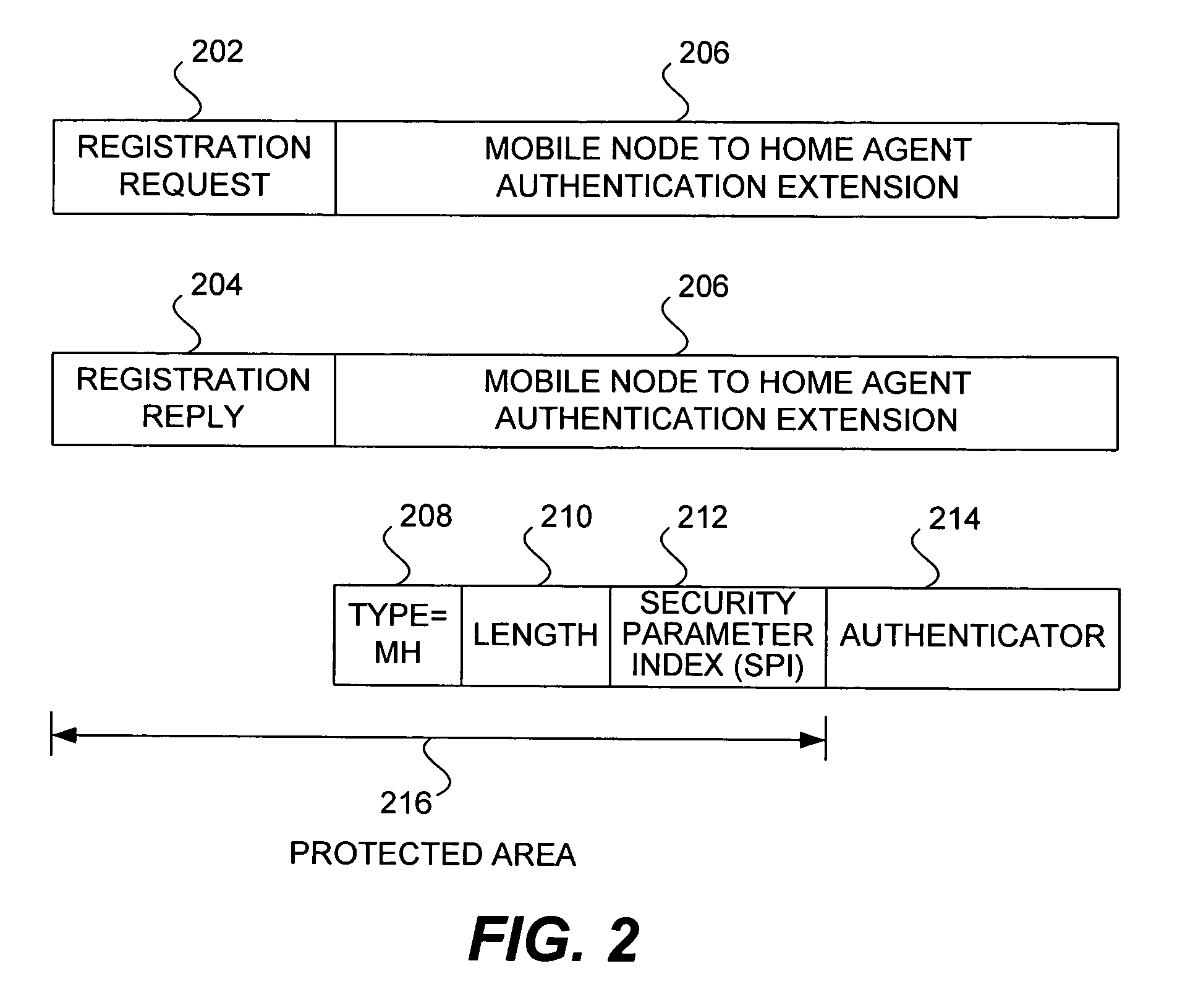
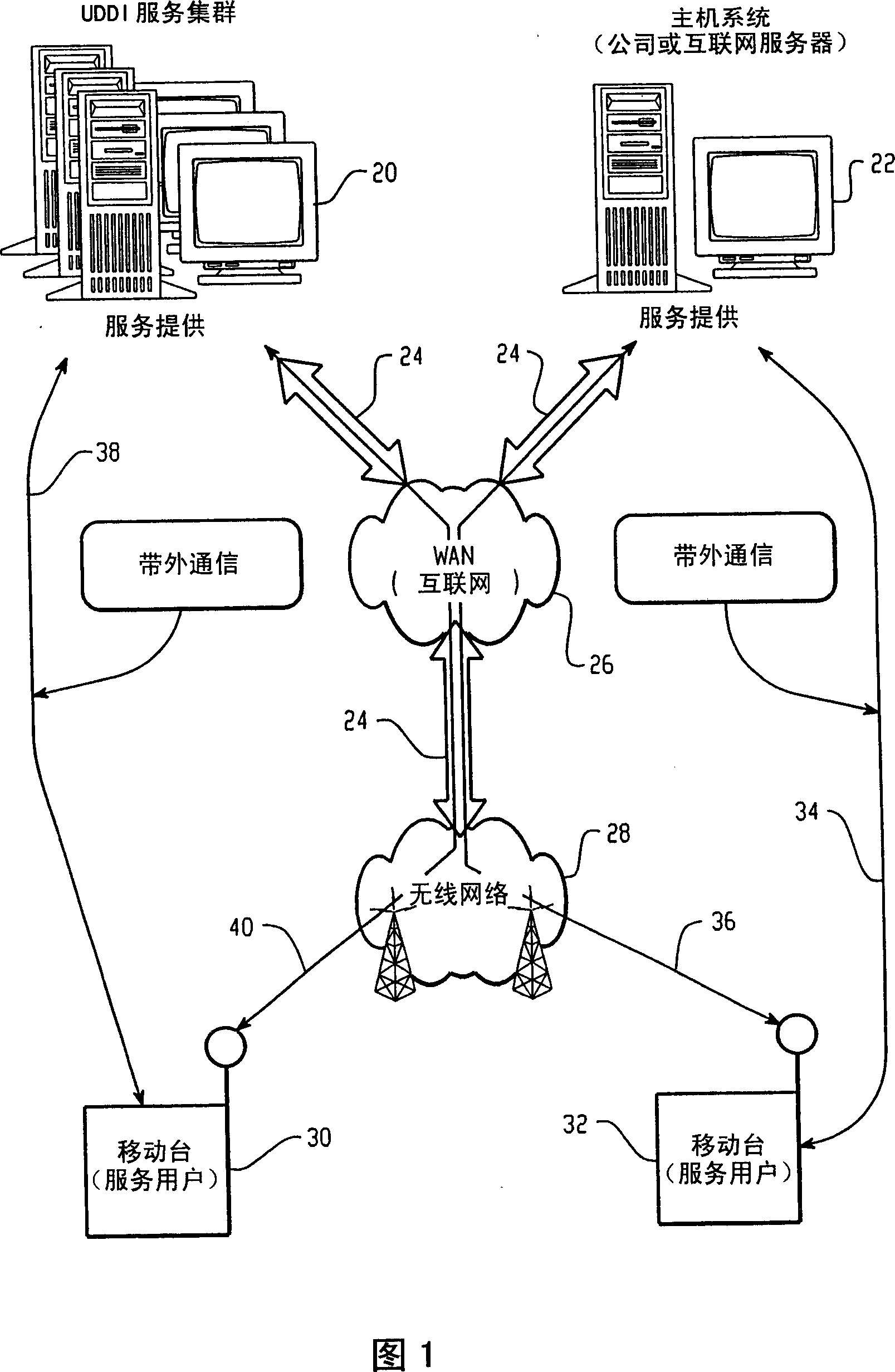
Methods and apparatus for dynamic session key generation and rekeying in mobile IP
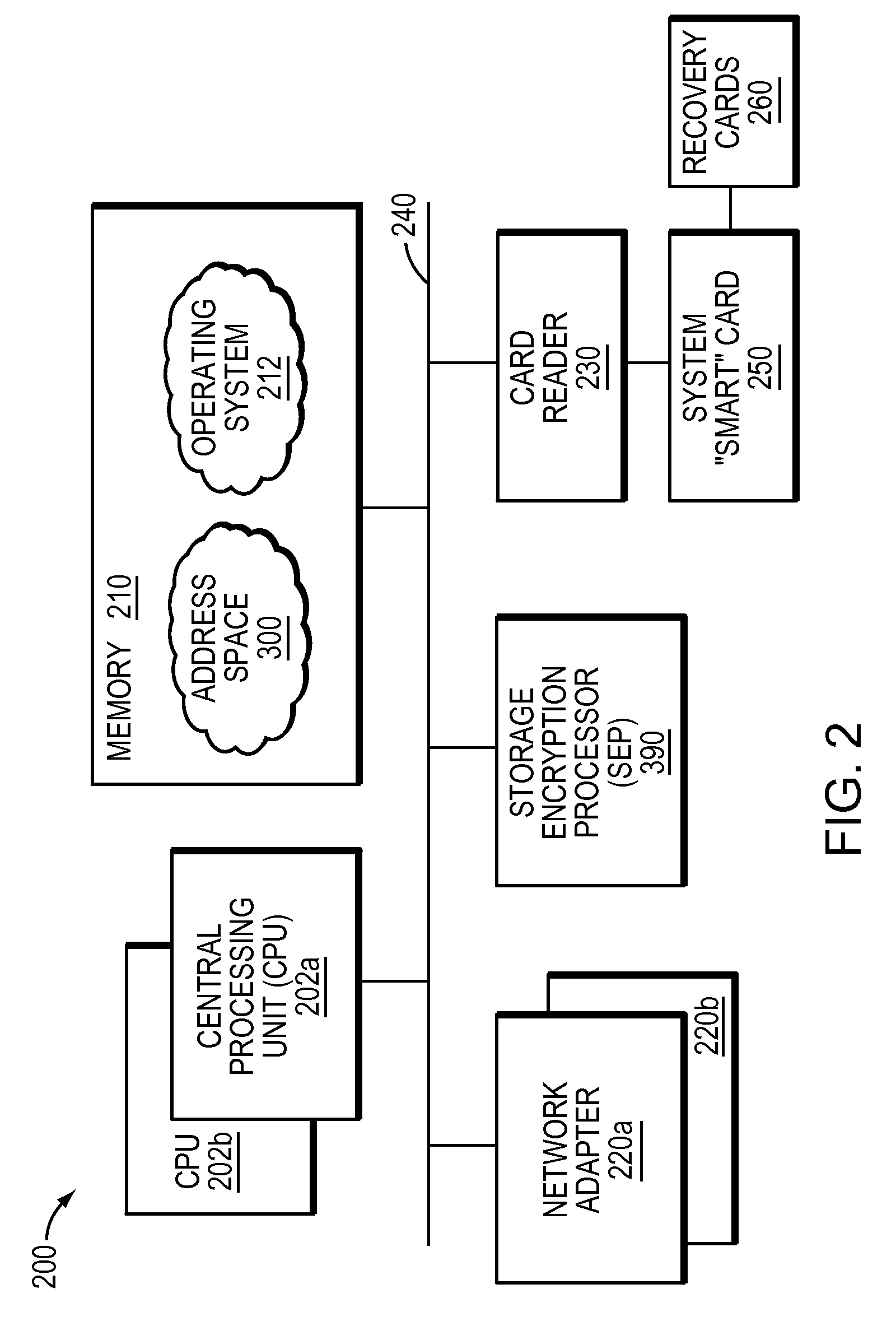
ActiveUS20050025091A1Eliminate needDigital data processing detailsUser identity/authority verificationPasswordRe keying
Methods and apparatus for providing a centralized source of session keys to be shared by a Home Agent and a Mobile Node are disclosed. In accordance with one aspect of the invention, a Mobile Node registers with a Home Agent supporting Mobile IP by sending a registration request to the Home Agent. The Home Agent sends a request message (e.g., access-request message) to a AAA server, the request message identifying the Mobile Node. The AAA server then derives key information from a key or password associated with the Mobile Node. The AAA server then sends a reply message (e.g., access-reply message) to the Home Agent, the reply message including the key information associated with the Mobile Node, thereby enabling the Home Agent to derive a shared key to be shared between the Mobile Node and the Home Agent from the key information. The Home Agent derives a key from the key information, the key being a shared key between the Mobile Node and the Home Agent. A registration reply is then sent to the Mobile Node. When the Mobile Node receives a registration reply from the Home Agent, the registration reply indicates that the Mobile Node is to derive a key to be shared between the Mobile Node and the Home Agent. The Mobile Node then derives a key to be shared between the Mobile Node and the Home Agent from key information stored at the Mobile Node. The Mobile Node may initiate “re-keying” by sending a subsequent registration request to the Home Agent.
Owner:CISCO TECH INC
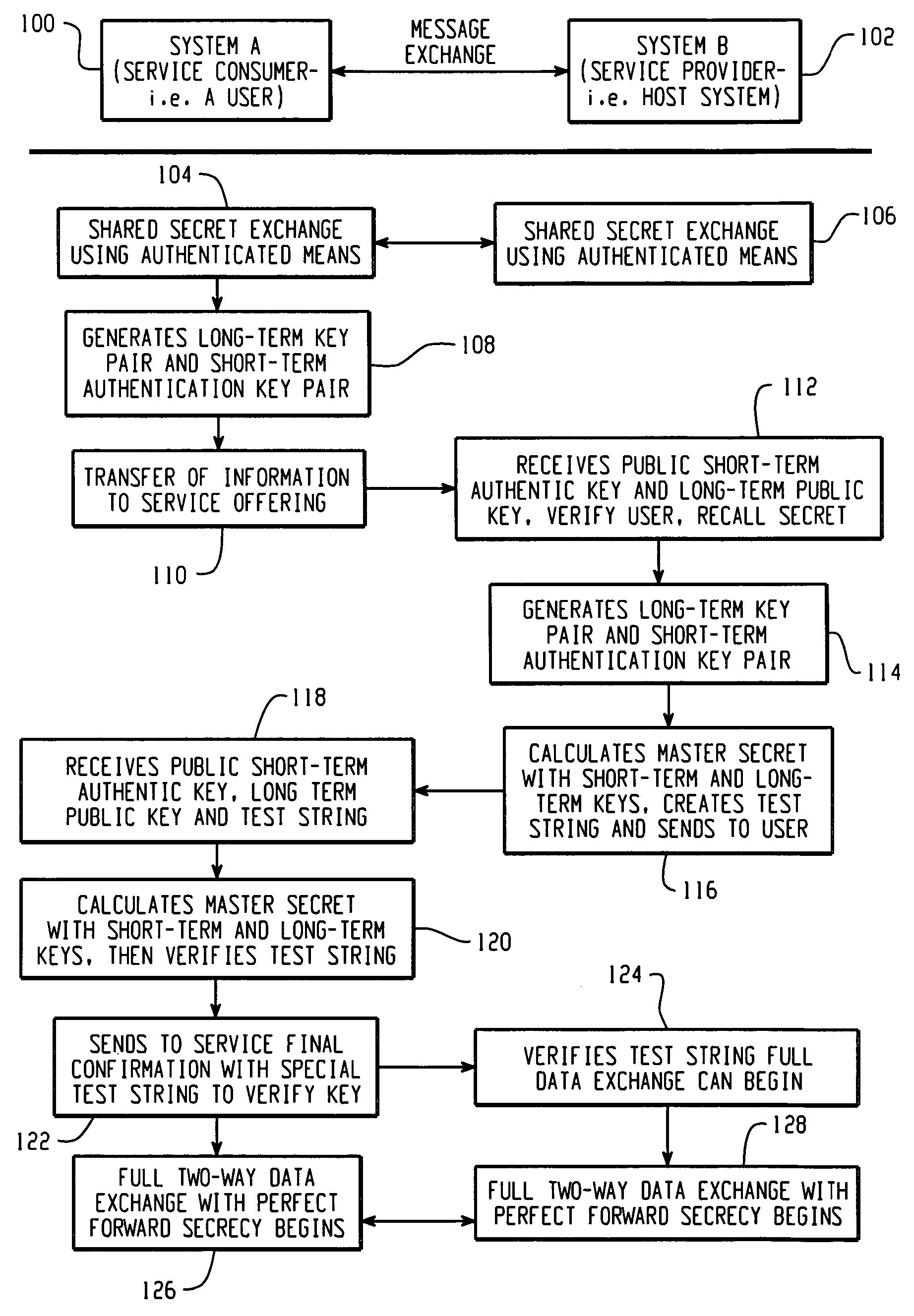
Systems and methods to securely generate shared keys
ActiveUS20050251680A1Key distribution for secure communicationPublic key for secure communicationMaster keyRe keying
A method for secure bidirectional communication between two systems is described. A first key pair and a second key pair are generated, the latter including a second public key that is generated based upon a shared secret. First and second public keys are sent to a second system, and third and fourth public keys are received from the second system. The fourth public key is generated based upon the shared secret. A master key for encrypting messages is calculated based upon a first private key, a second private key, the third public key and the fourth public key. For re-keying, a new second key pair having a new second public key and a new second private key is generated, and a new fourth public key is received. A new master key is calculated using elliptic curve calculations using the new second private key and the new fourth public key.
Owner:MALIKIE INNOVATIONS LTD
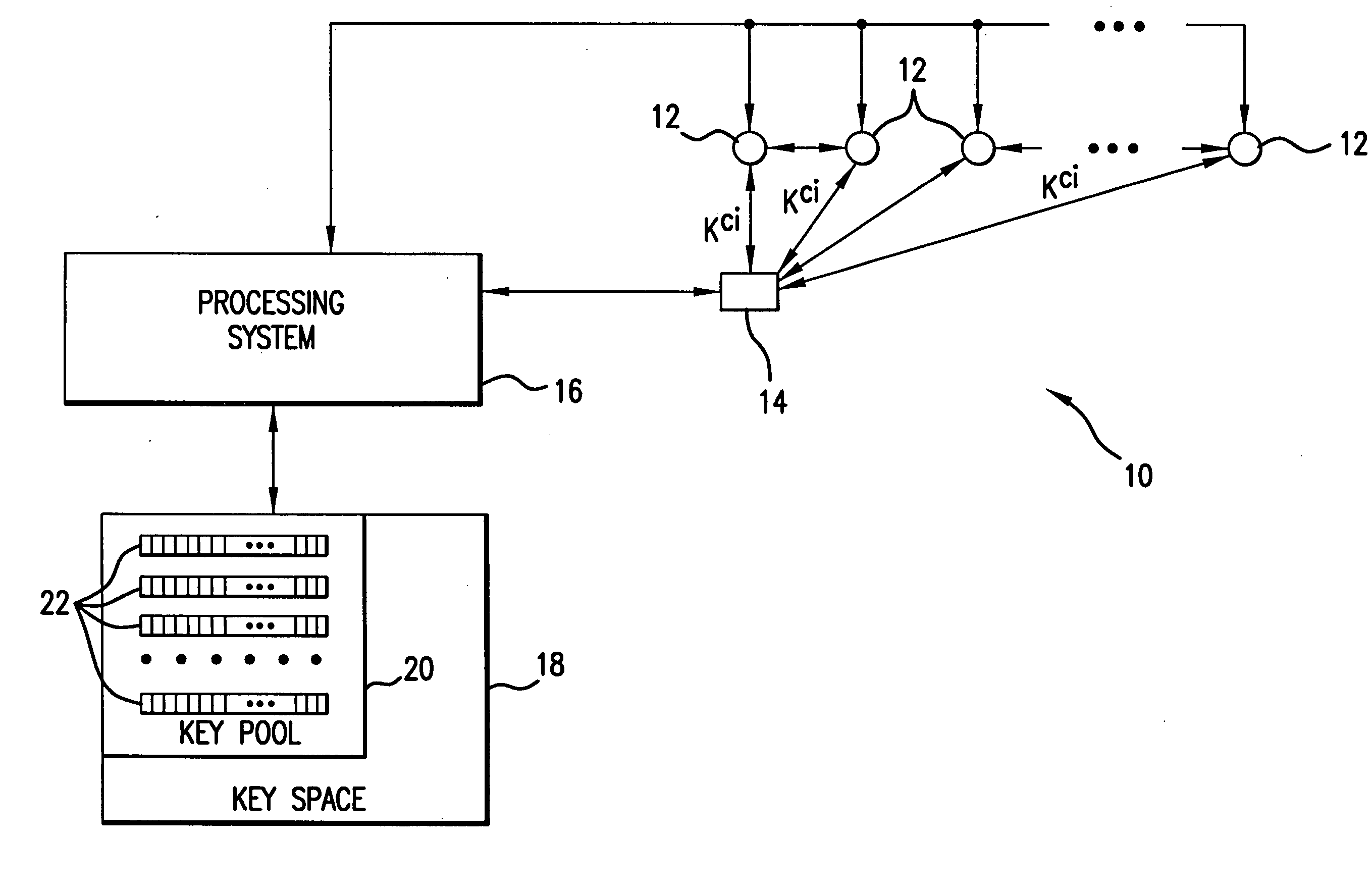
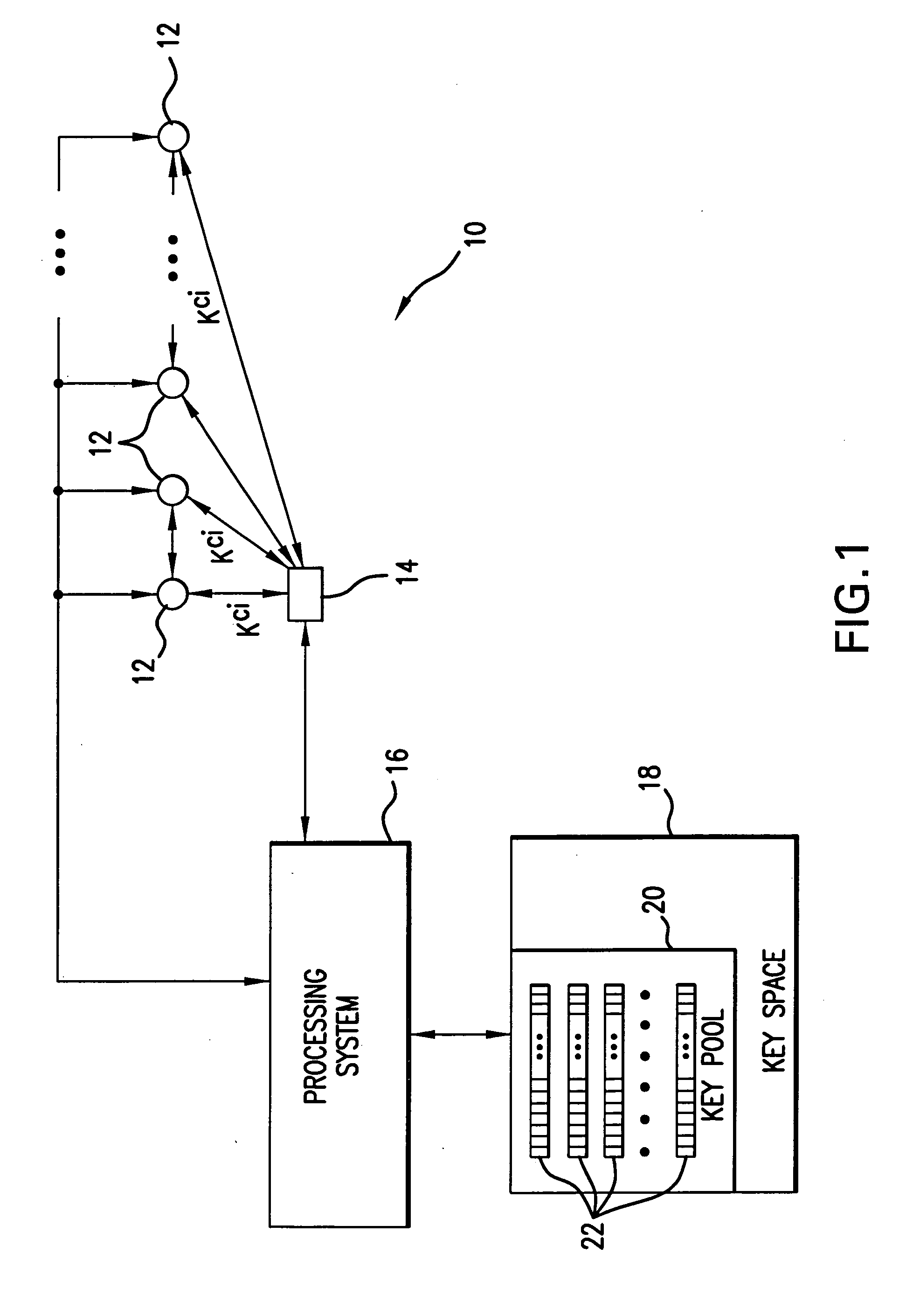
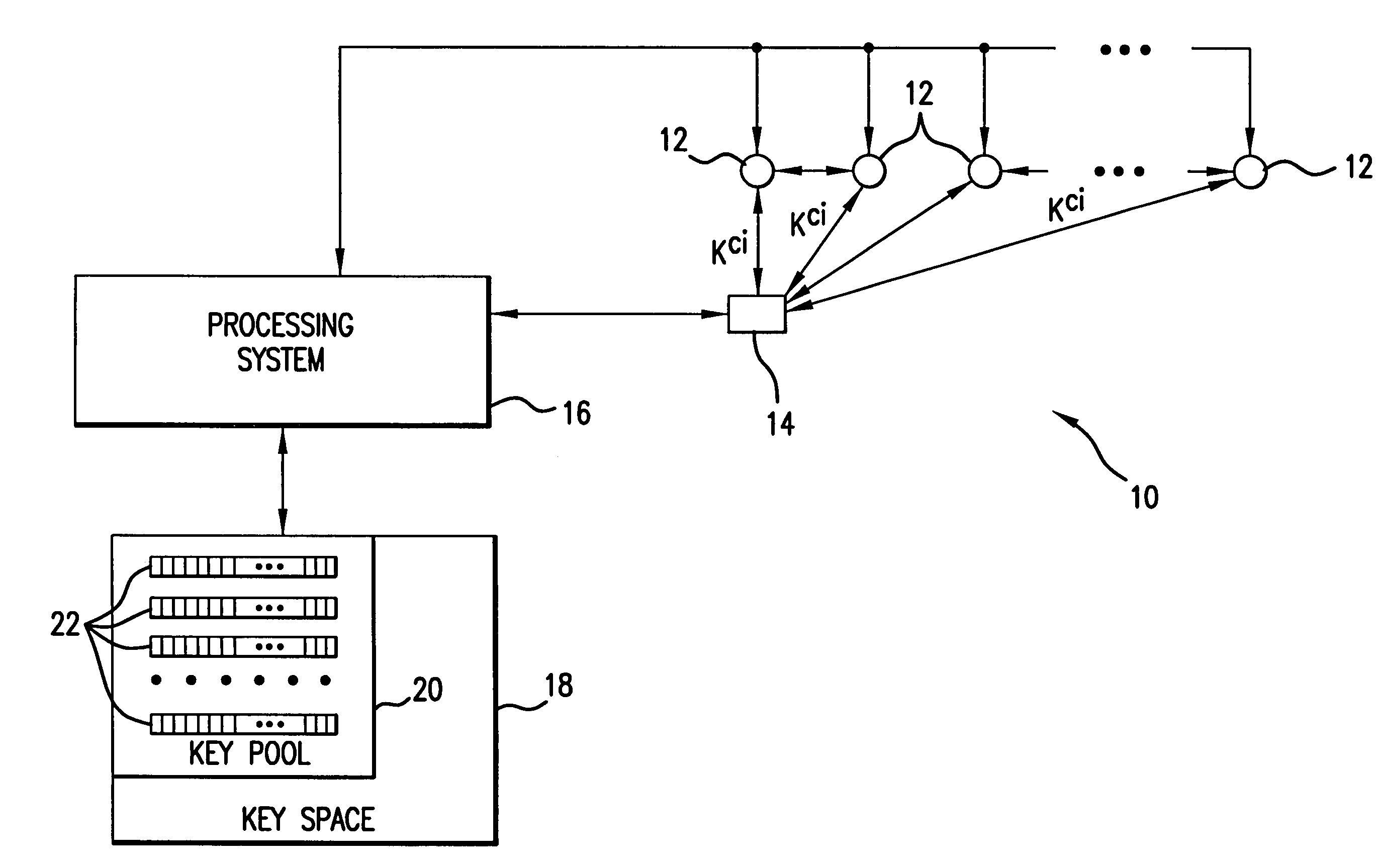
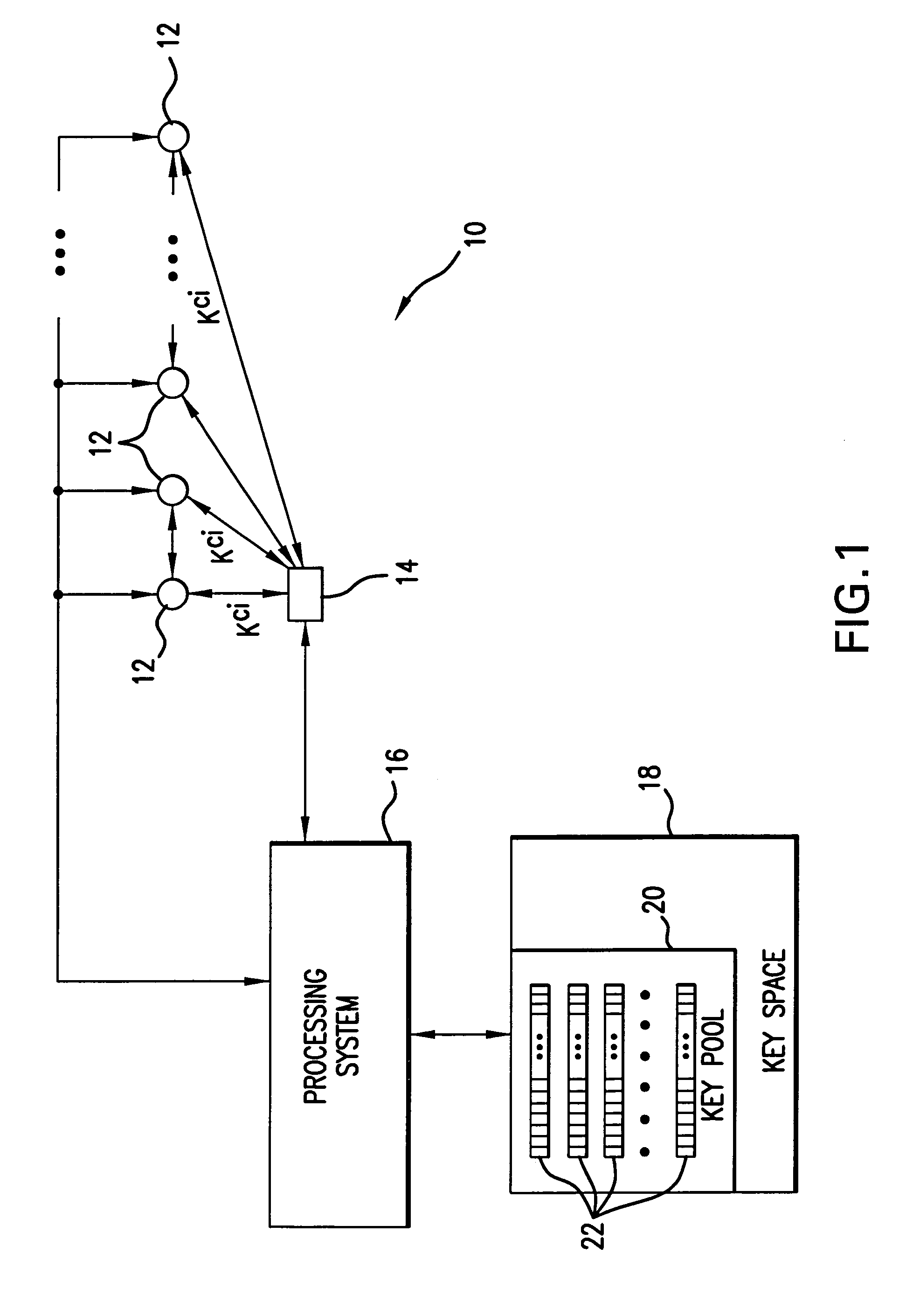
Method and apparatus for key management in distributed sensor networks
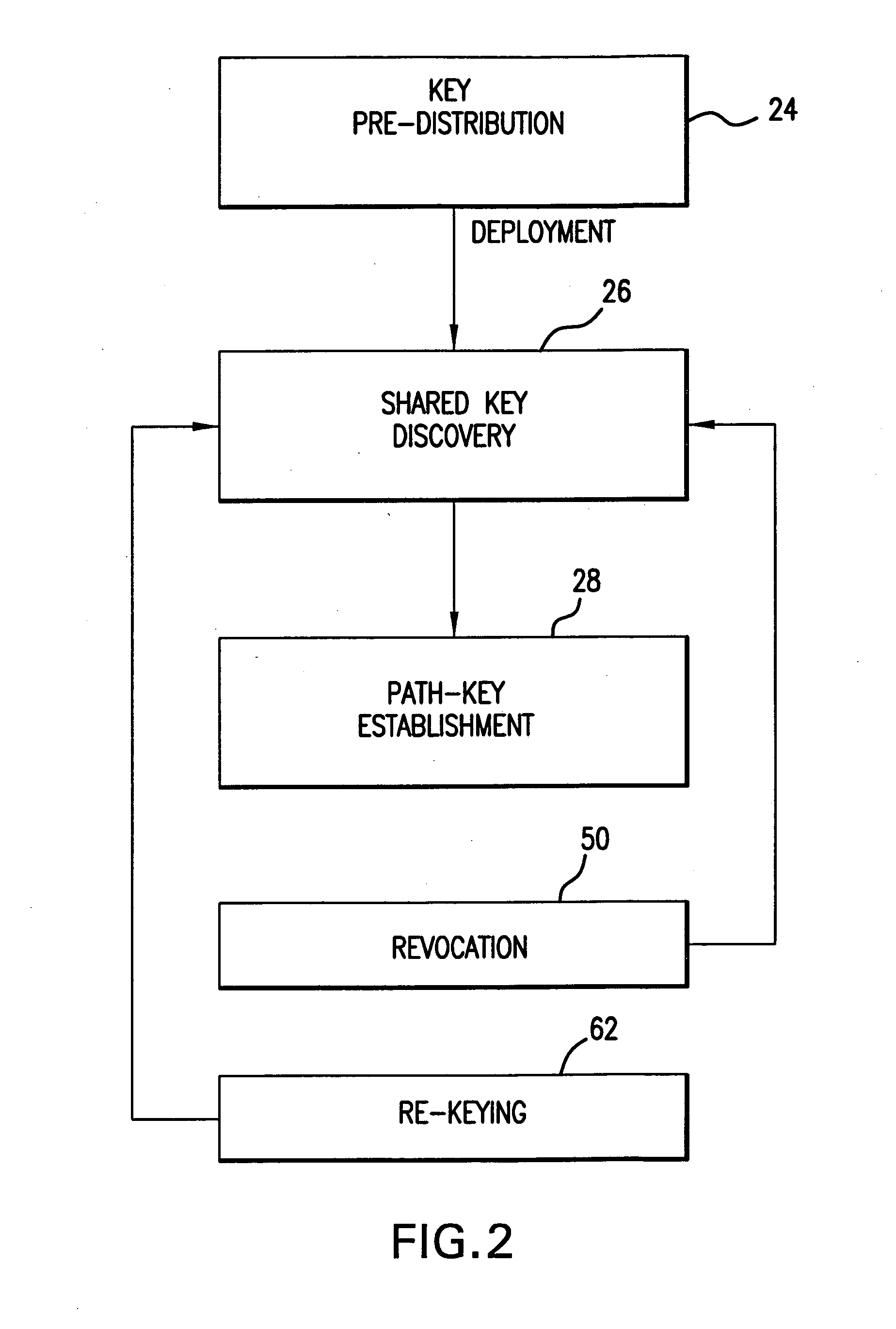
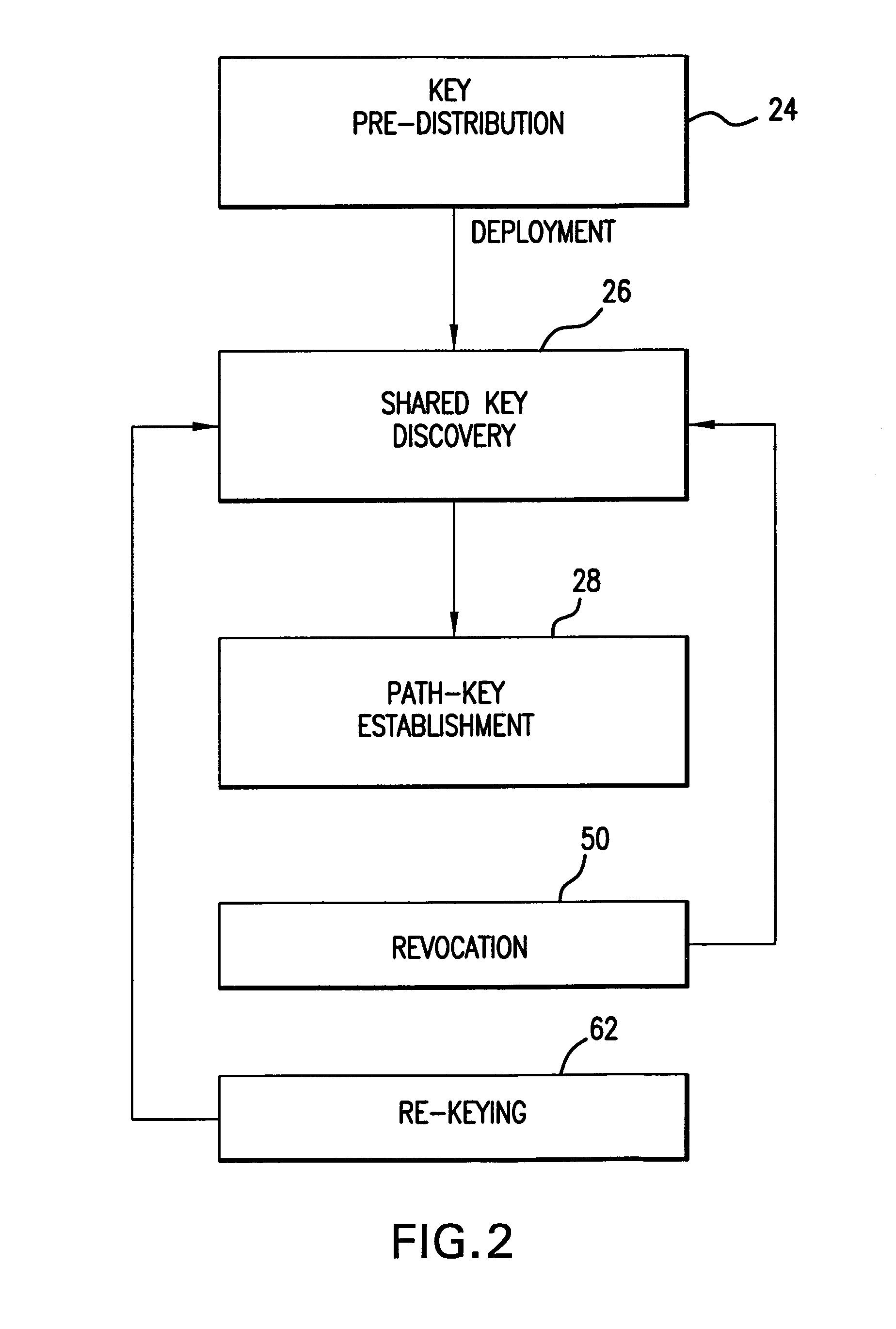
InactiveUS20050140964A1Key distribution for secure communicationOptical rangefindersRe keyingRevocation
In a distributed sensor network, a method of key management is carried out in several phases, particularly key pre-distribution phase, shared key discovery phase, and as needed, a path key establishment phase. In the key pre-distribution phase, prior to DSN deployment, a ring of keys is distributed to each sensor node, each key ring consisting of randomly chosen keys from a large pool of keys which is generated off-line. A shared key exists between each two key rings with a predetermined probability. In the shared key discovery phase, which takes place upon deployment of the DSN, every sensor node discovers its neighbors in wireless communication range with which it shares keys, and the topology of the sensor array is established by forming secure communication links between respective sensor nodes. The path key establishment phase assigns a path key to selected pairs of sensor nodes in wireless communication range that do not share a key but are connected by two or more links at the end of the shared key discovery phase. The key management scheme also assumes a revocation phase for removal of the key ring of the compromised sensor node from the network. Also, re-keying phase is assumed for removal of those keys with the expired lifetime.
Owner:MARYLAND UNIV OF
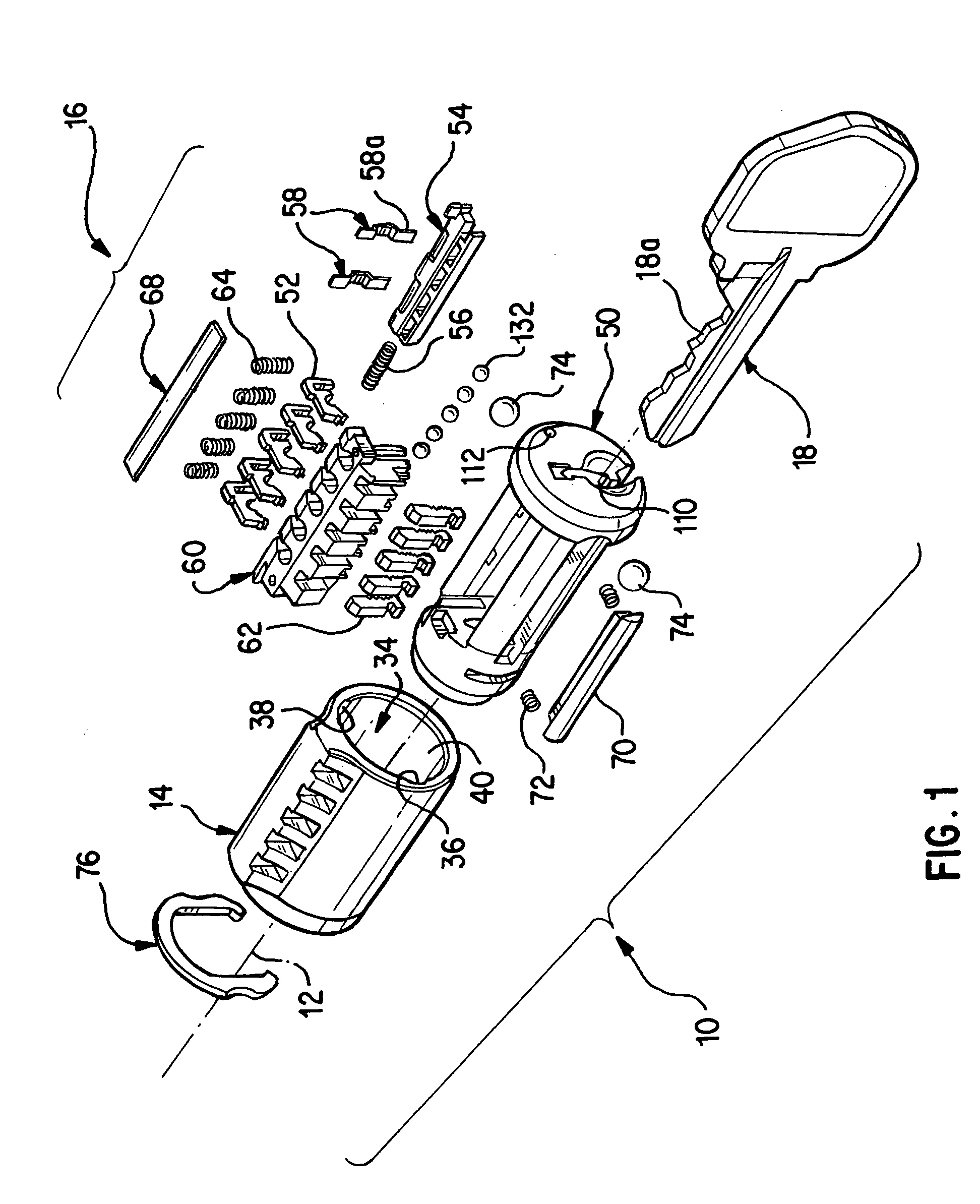
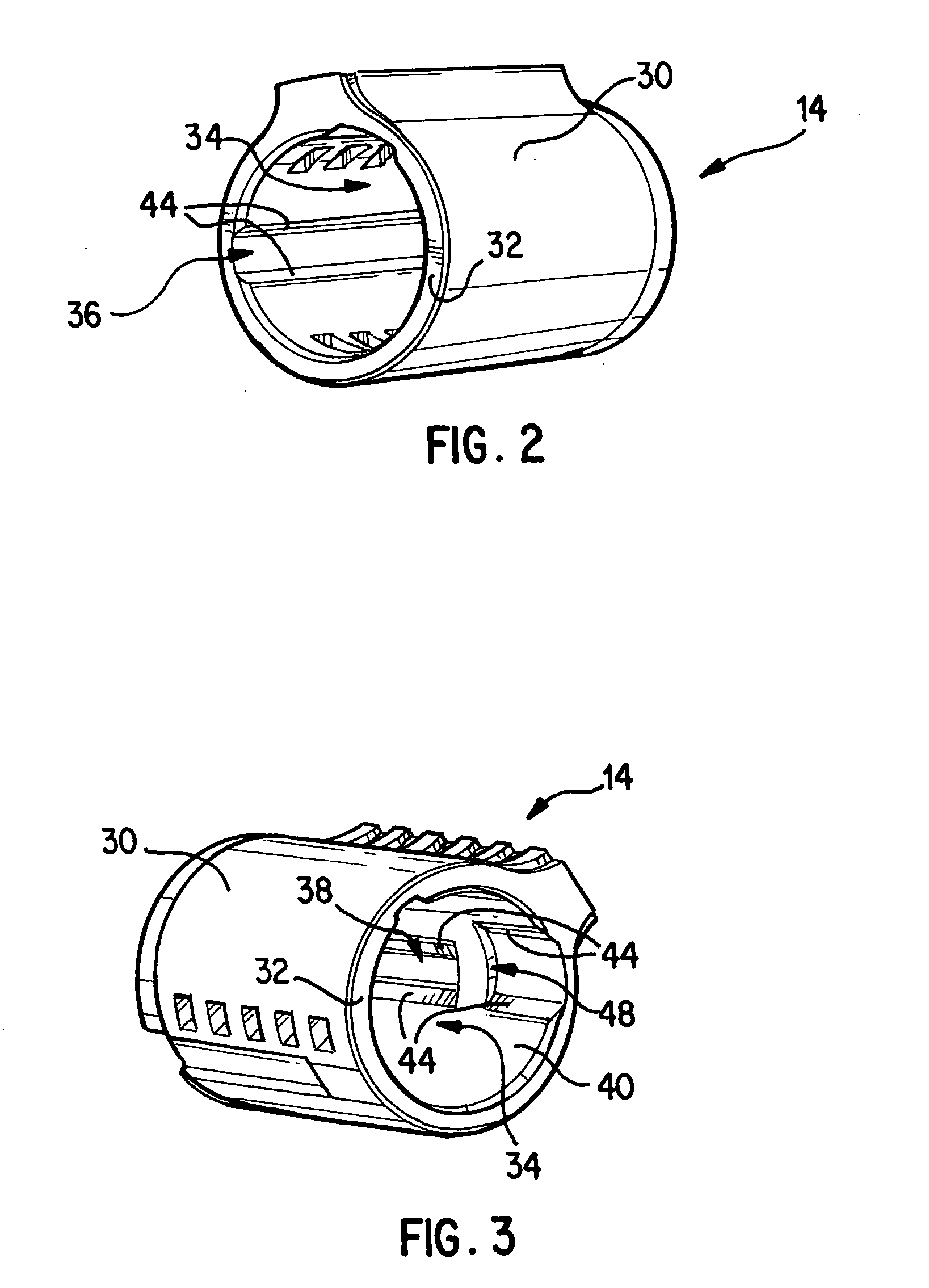
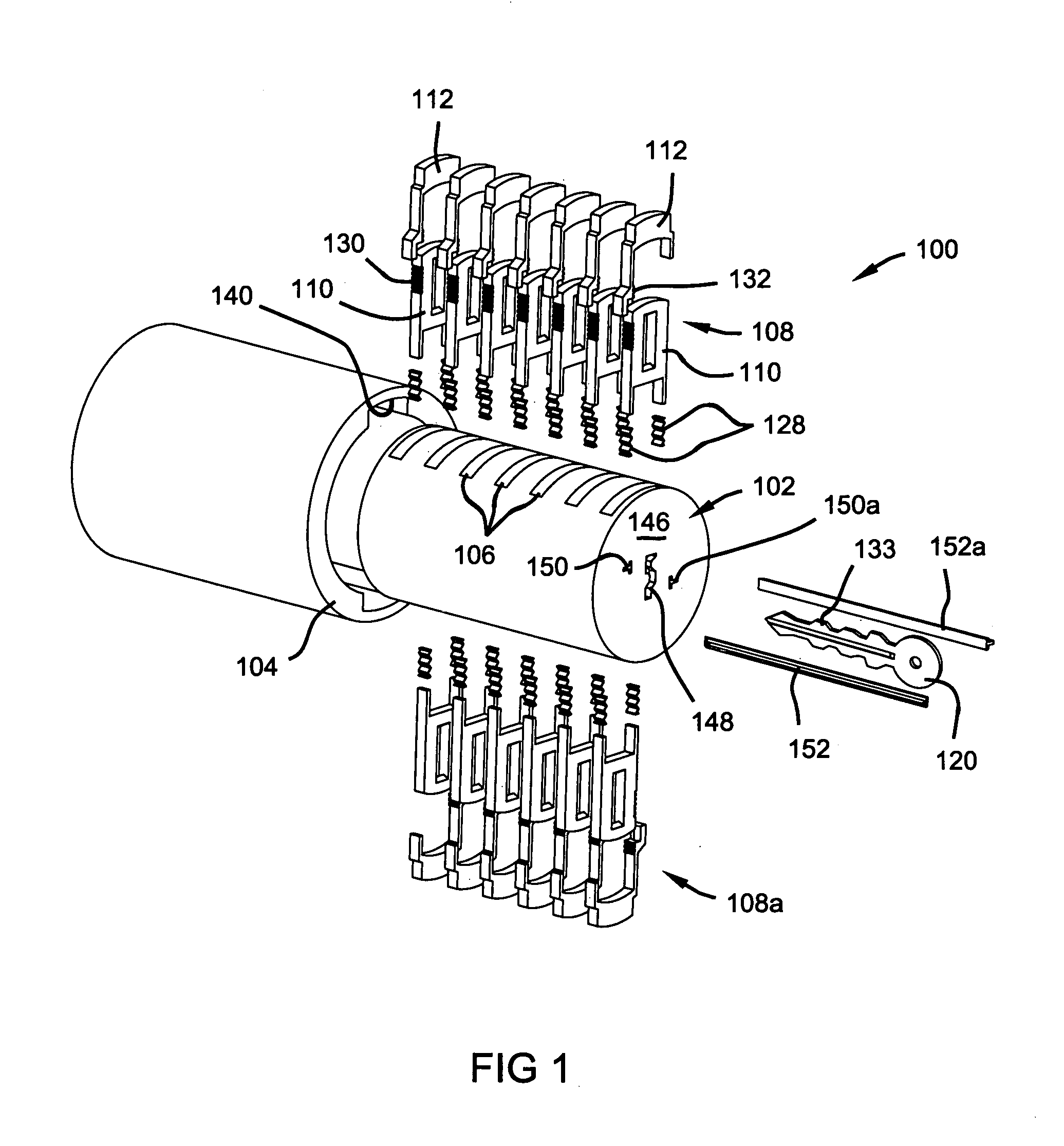
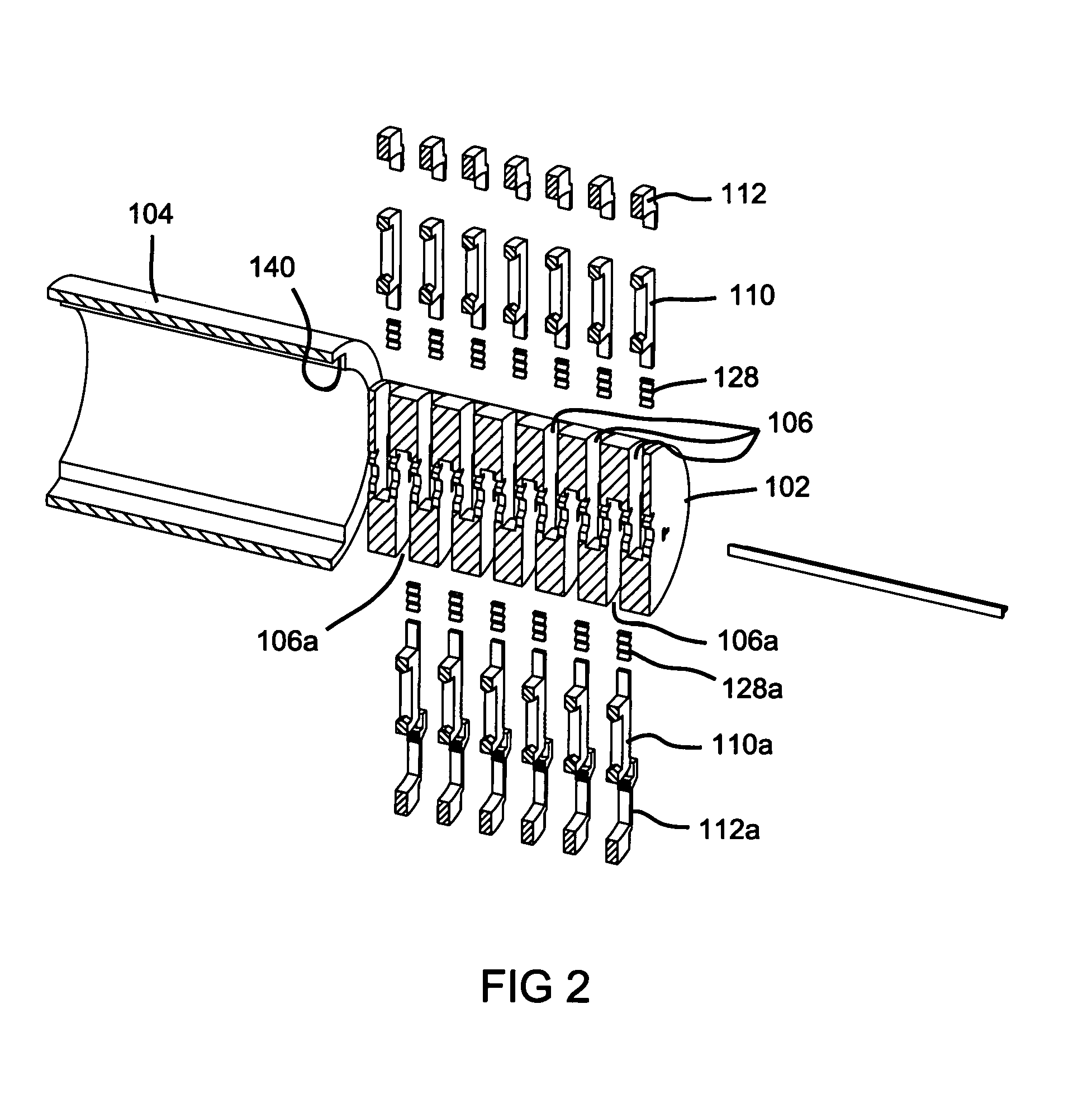
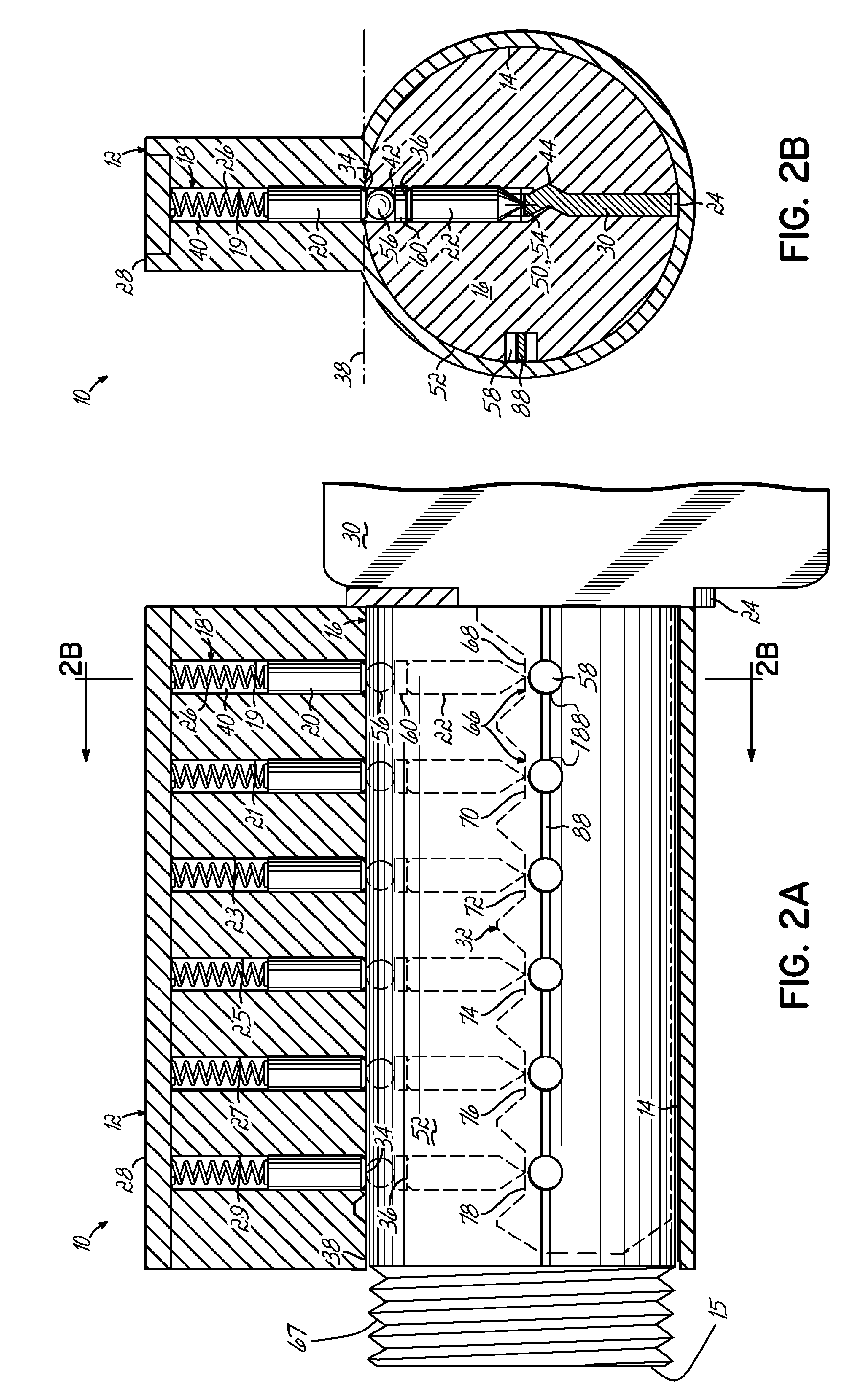
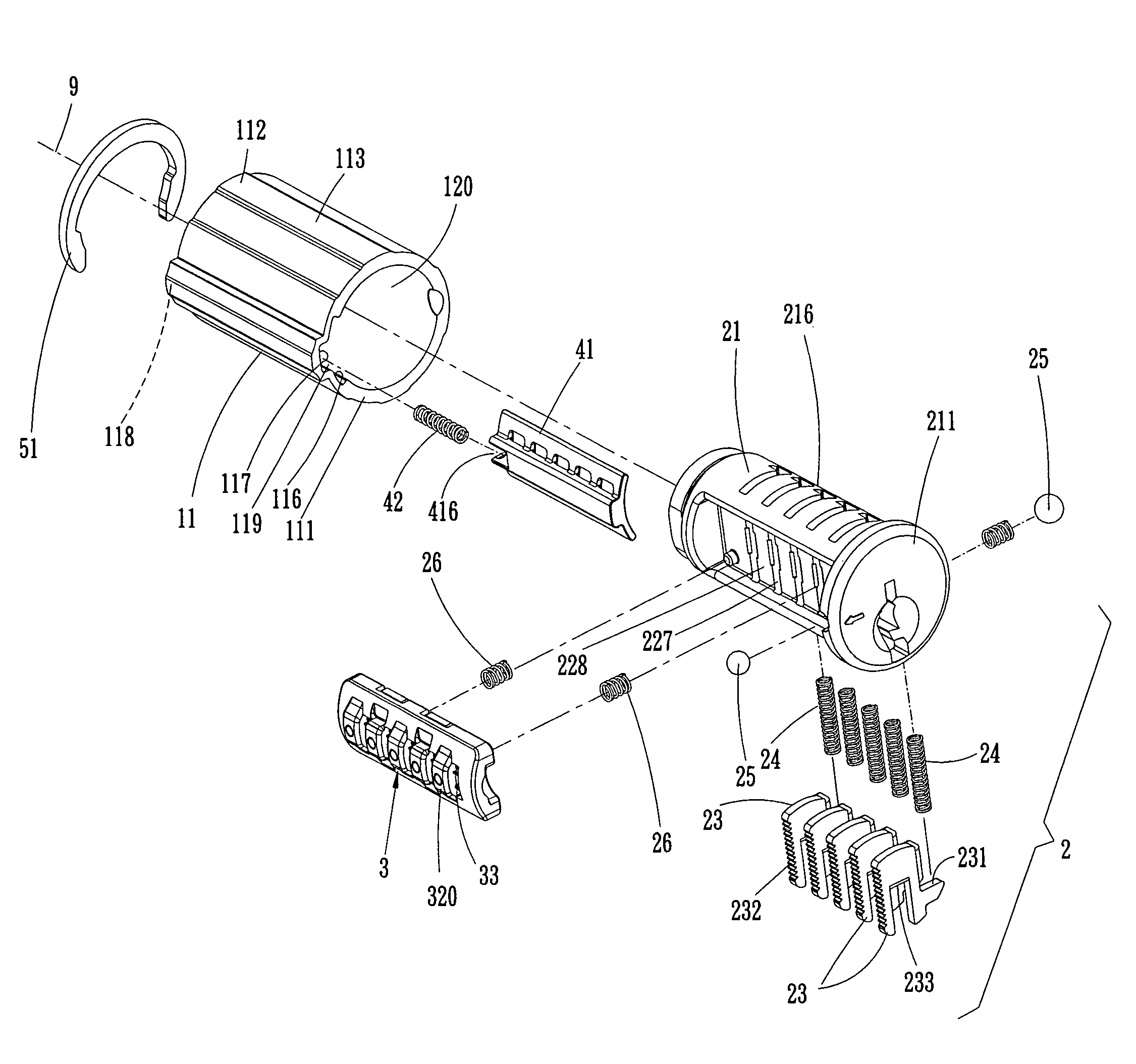
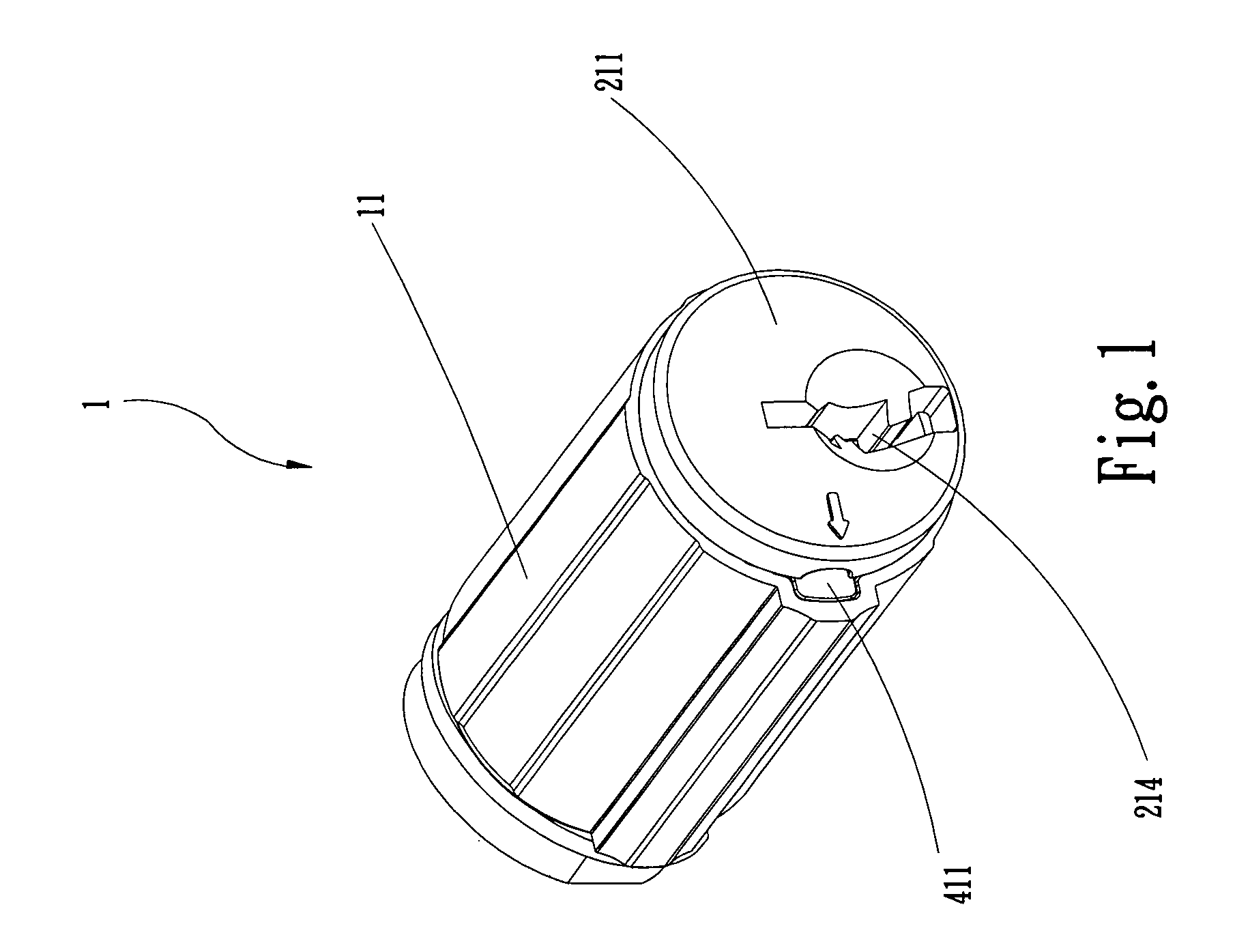
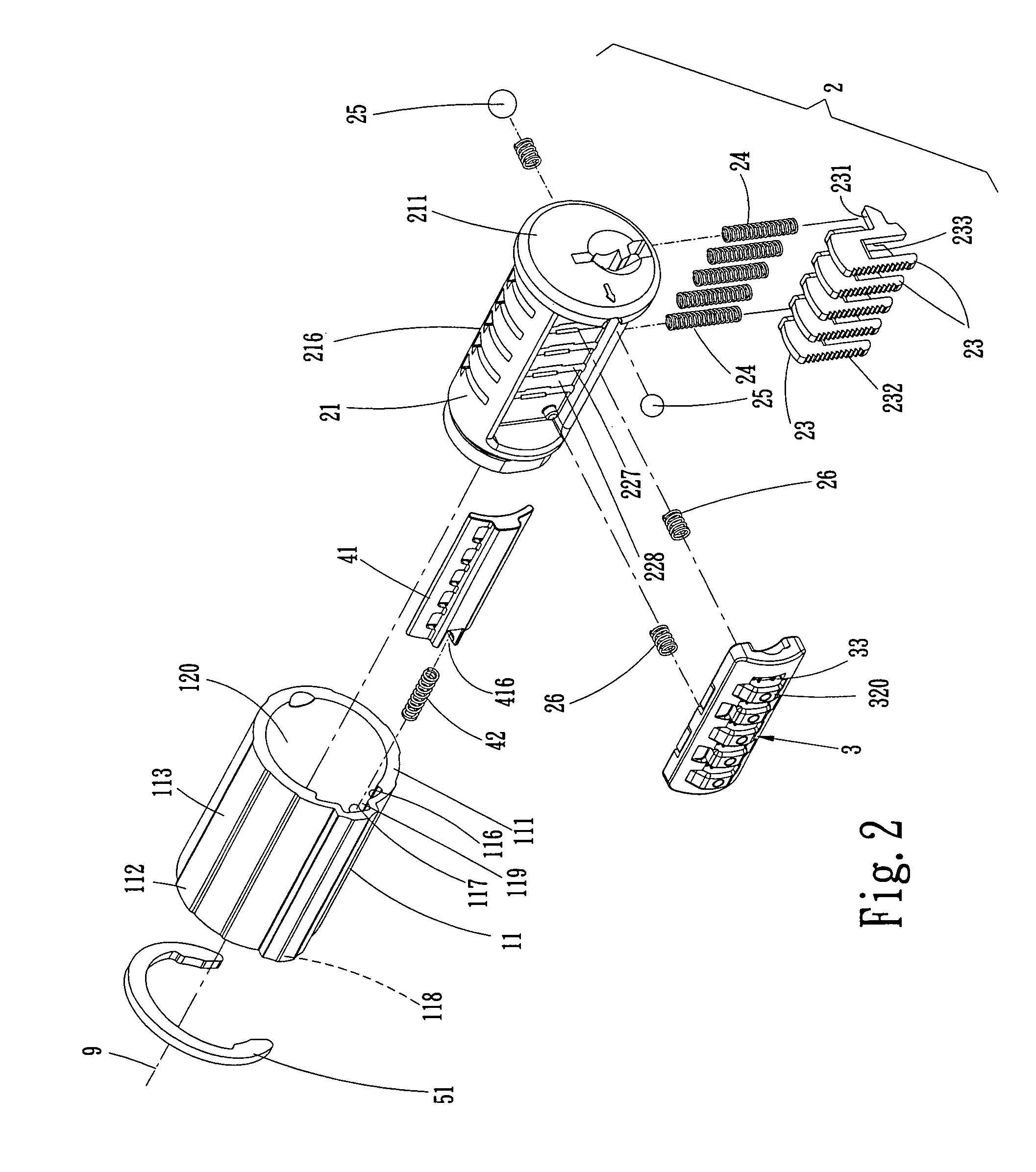
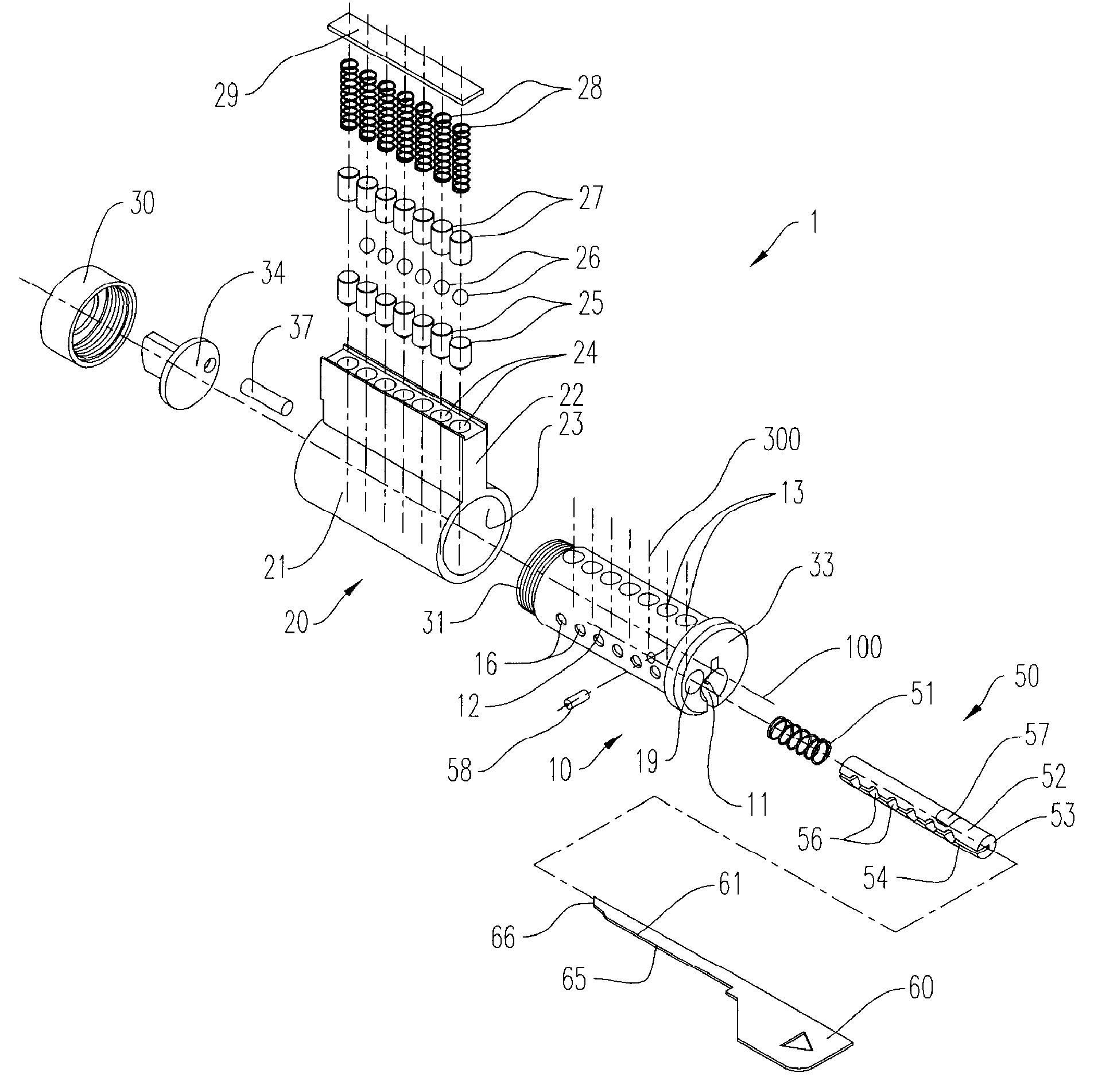
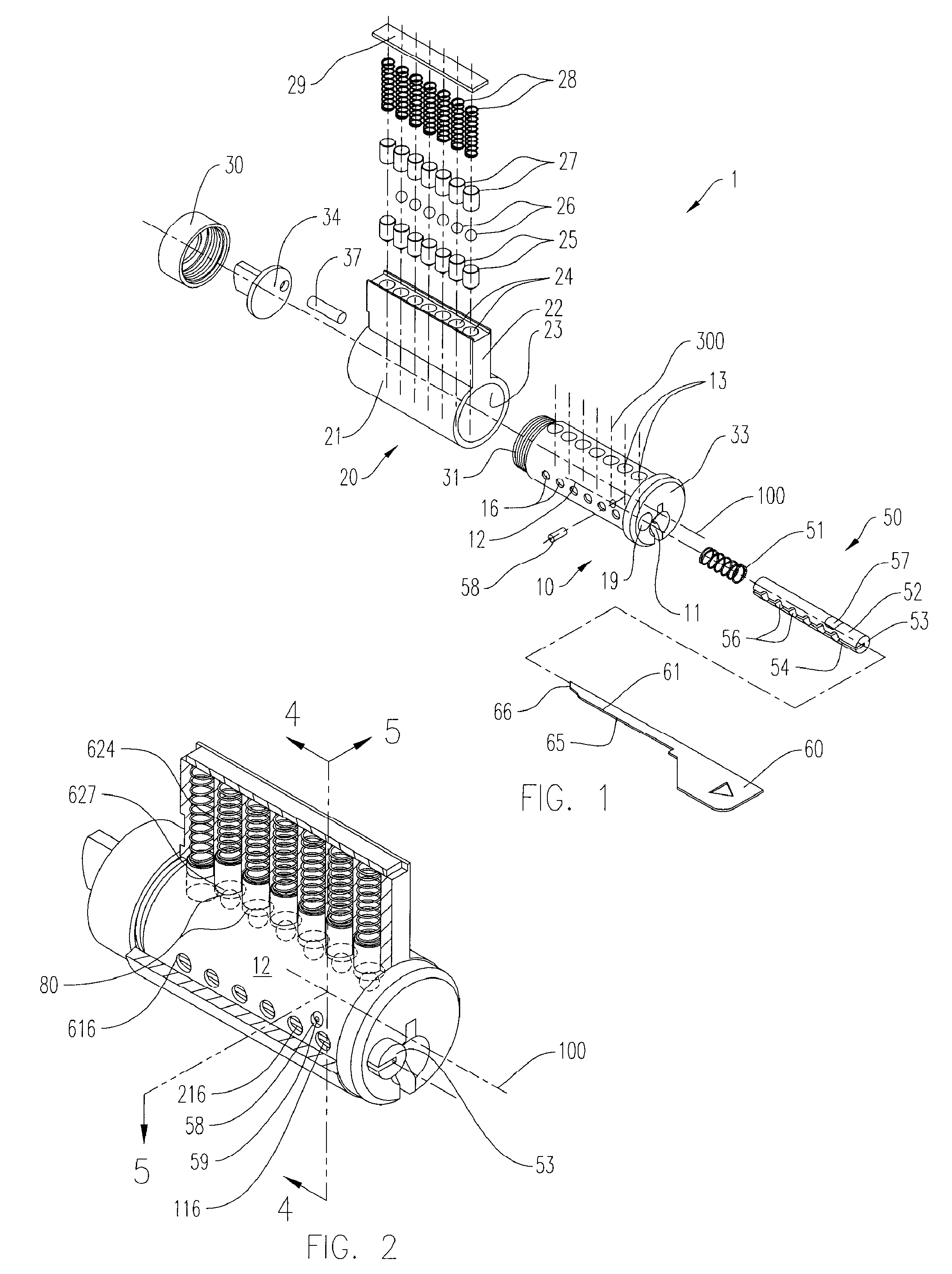
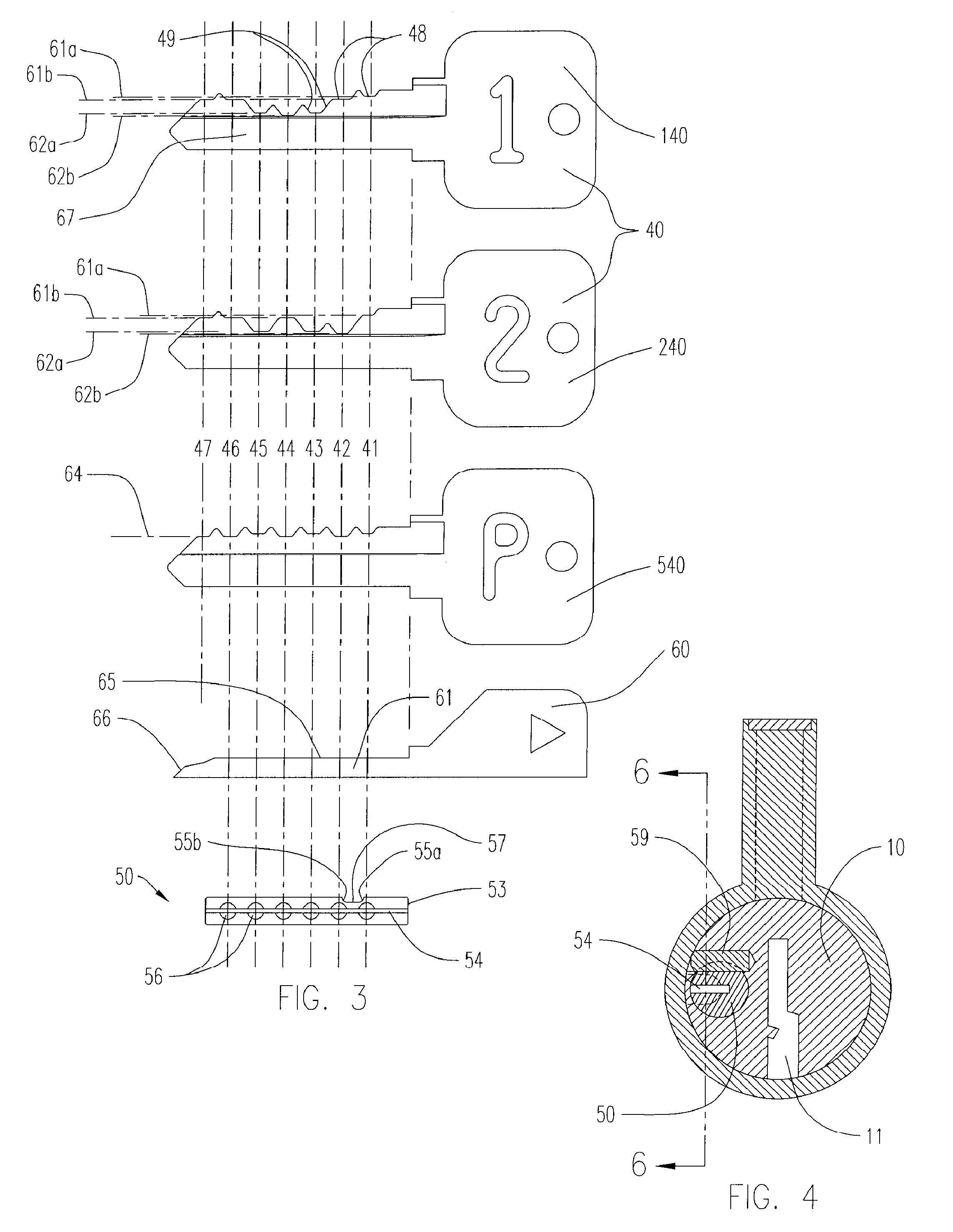
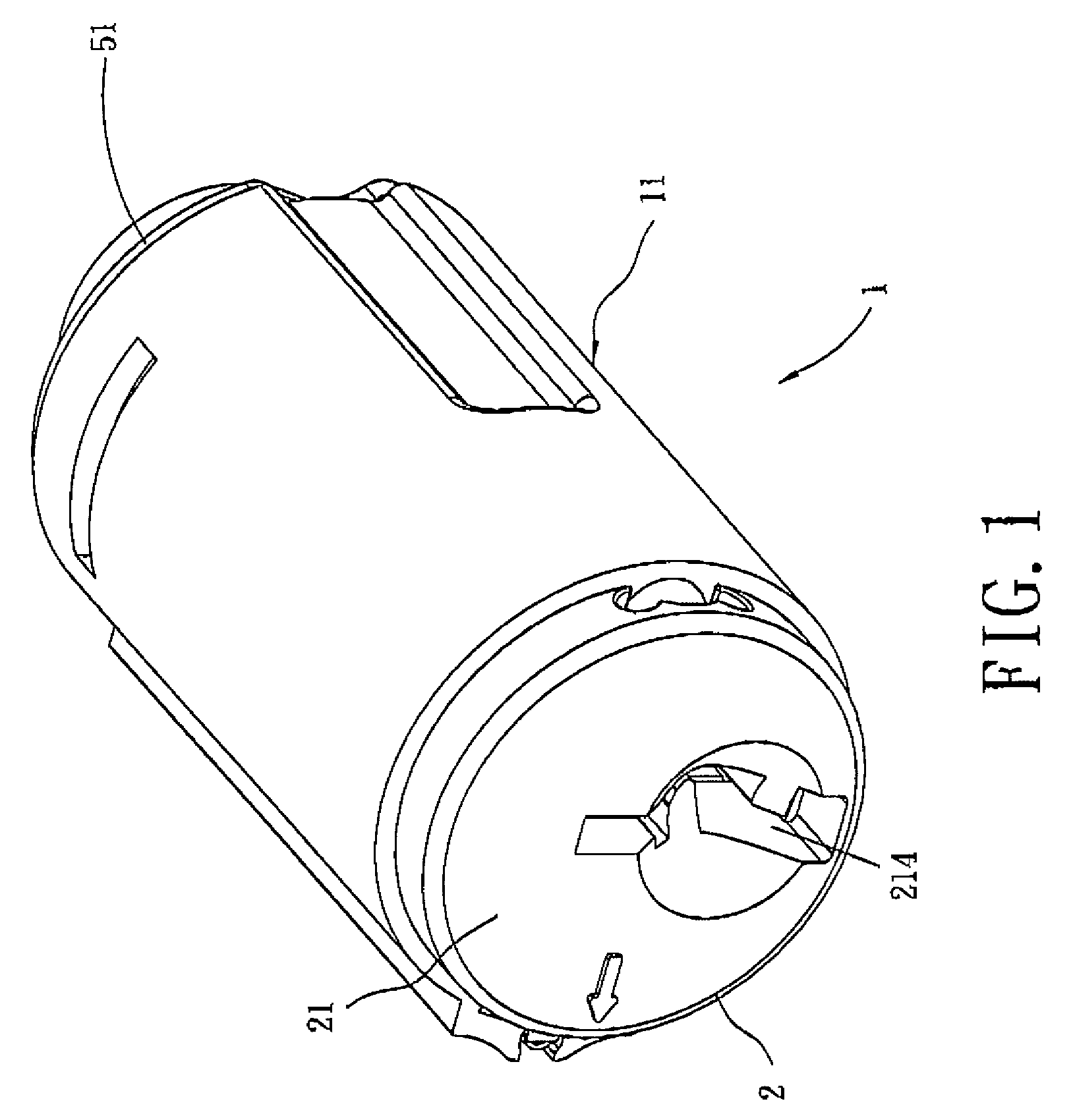
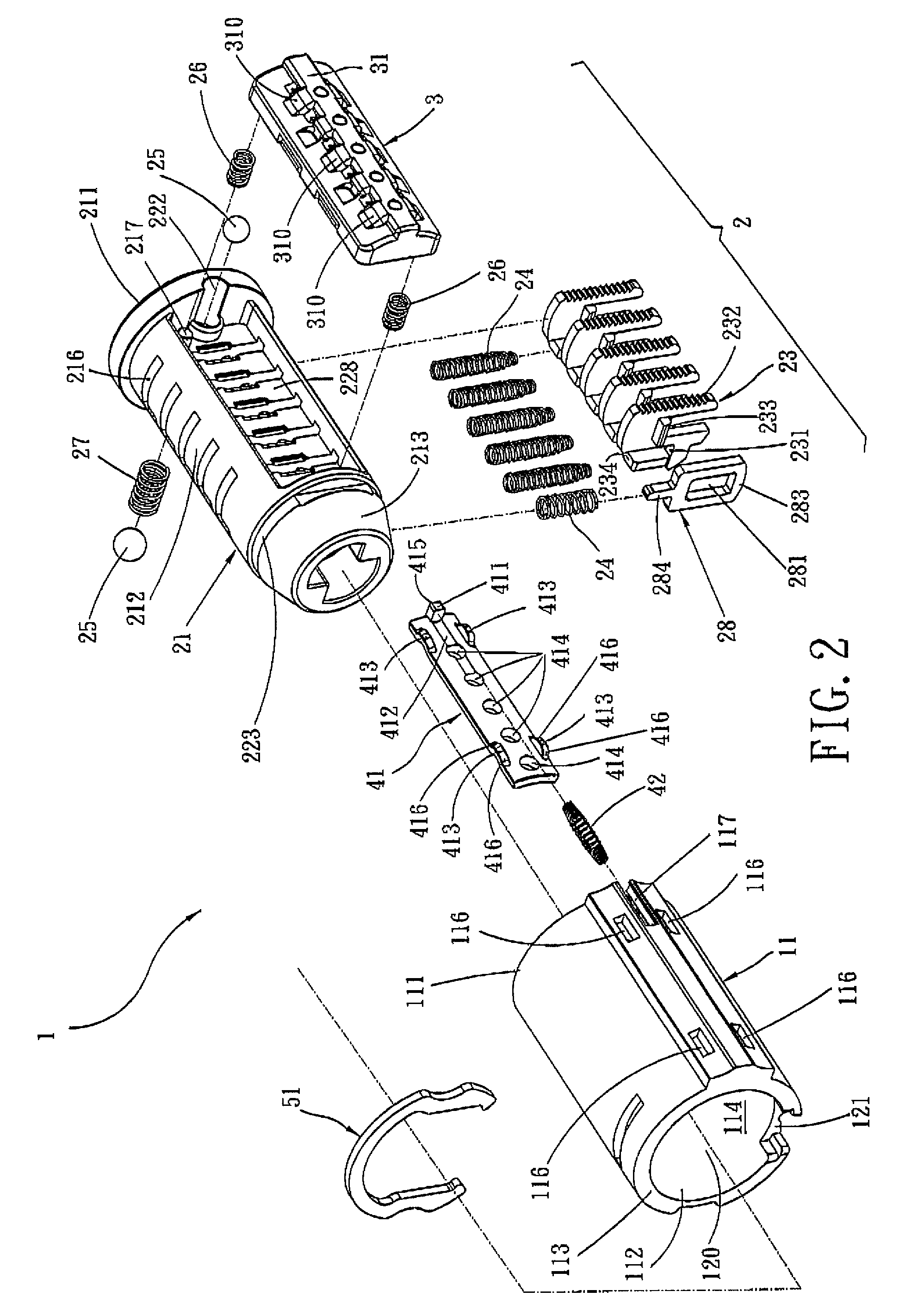
Re-keyable lock cylinder
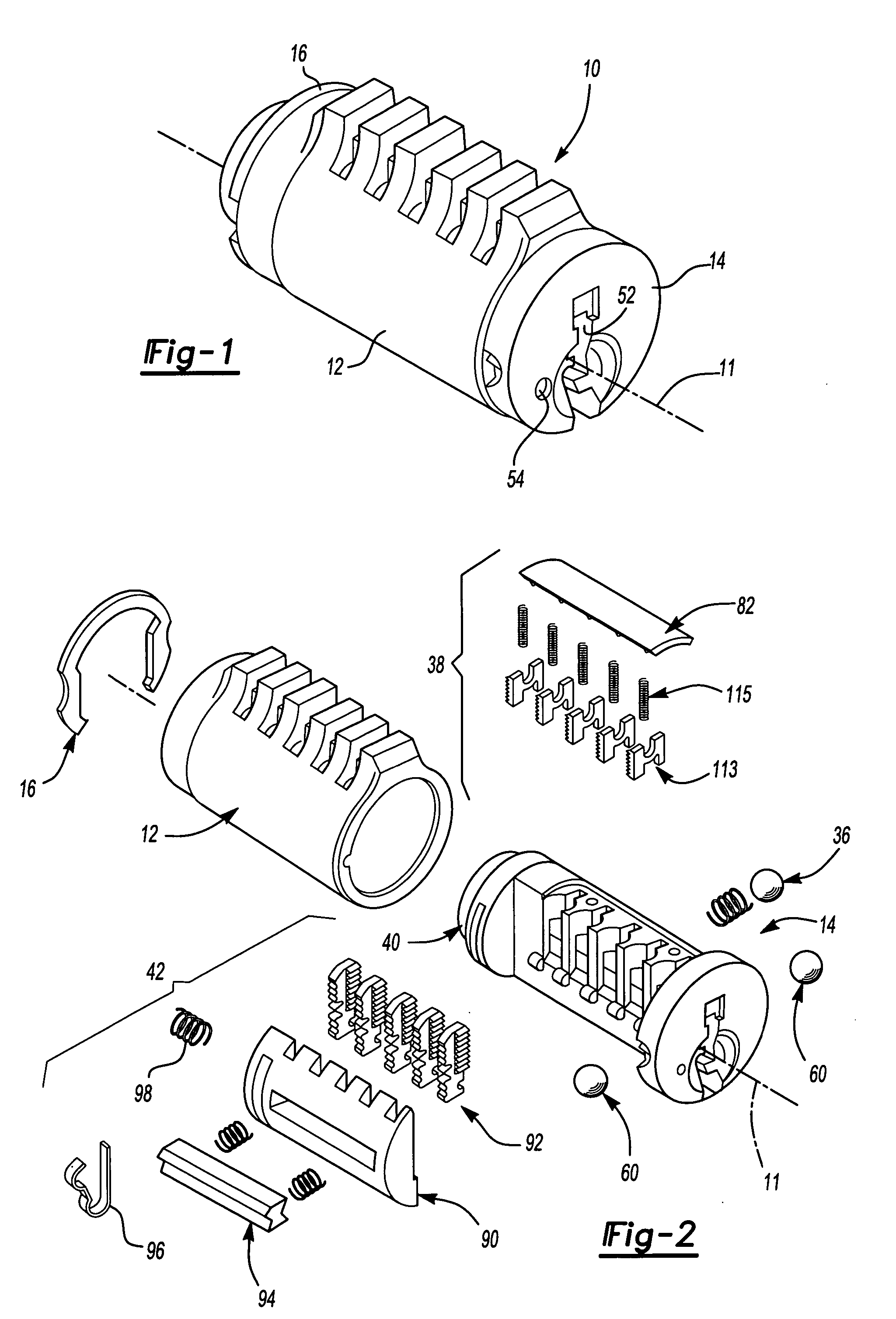
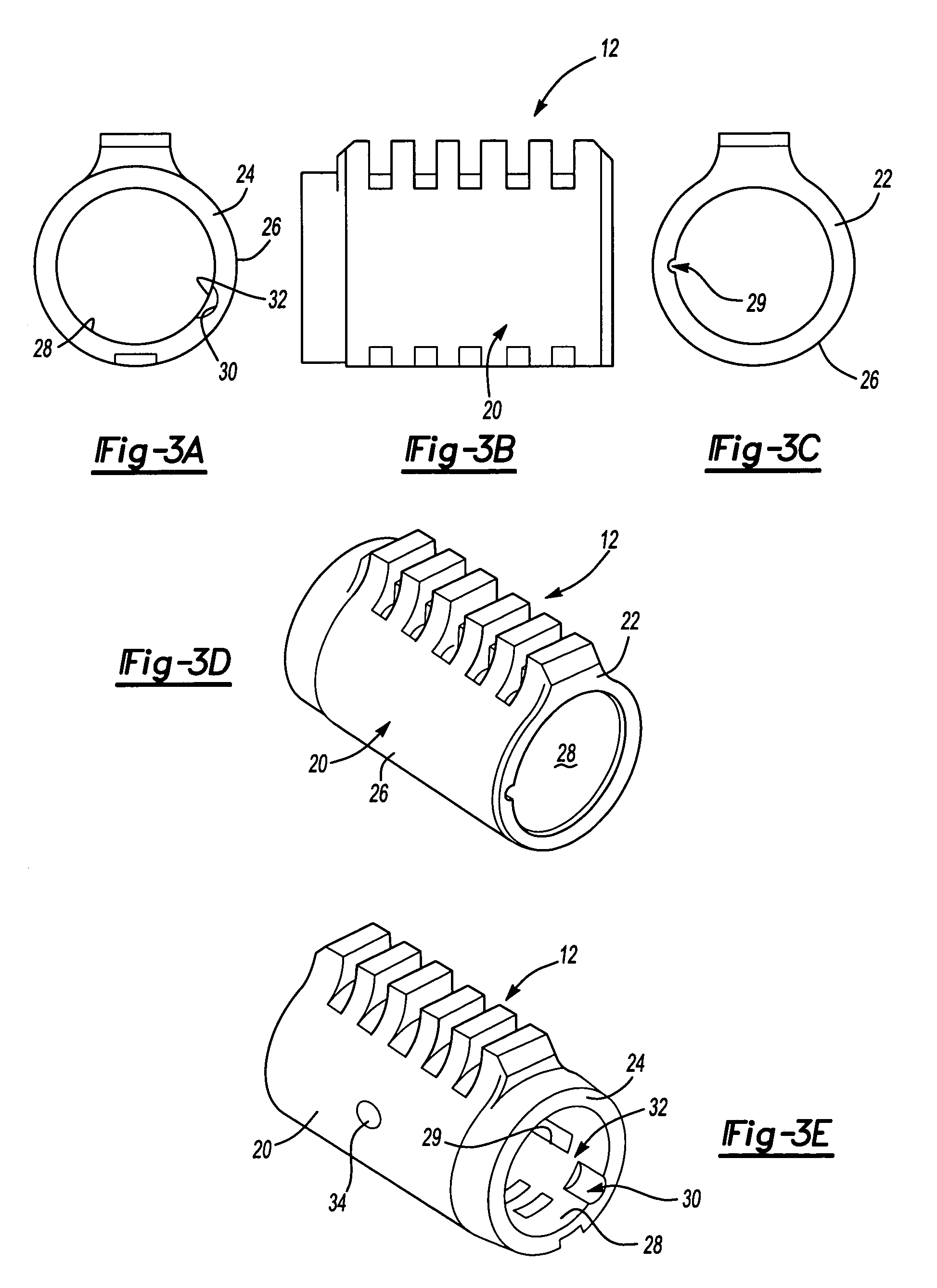
A re-keyable lockset that employs pairs of first and second pins. Coupling of the first and second pins to one another defines a key profile for a mating key. A second key with a different key profile may be installed to the lockset when the first and second pins are uncoupled from one another. Thereafter, the first and second pins may be re-coupled to one another to define the key profile of a new mating key. A method for re-keying a lockset is also provided.
Owner:RAYOVAC CORP
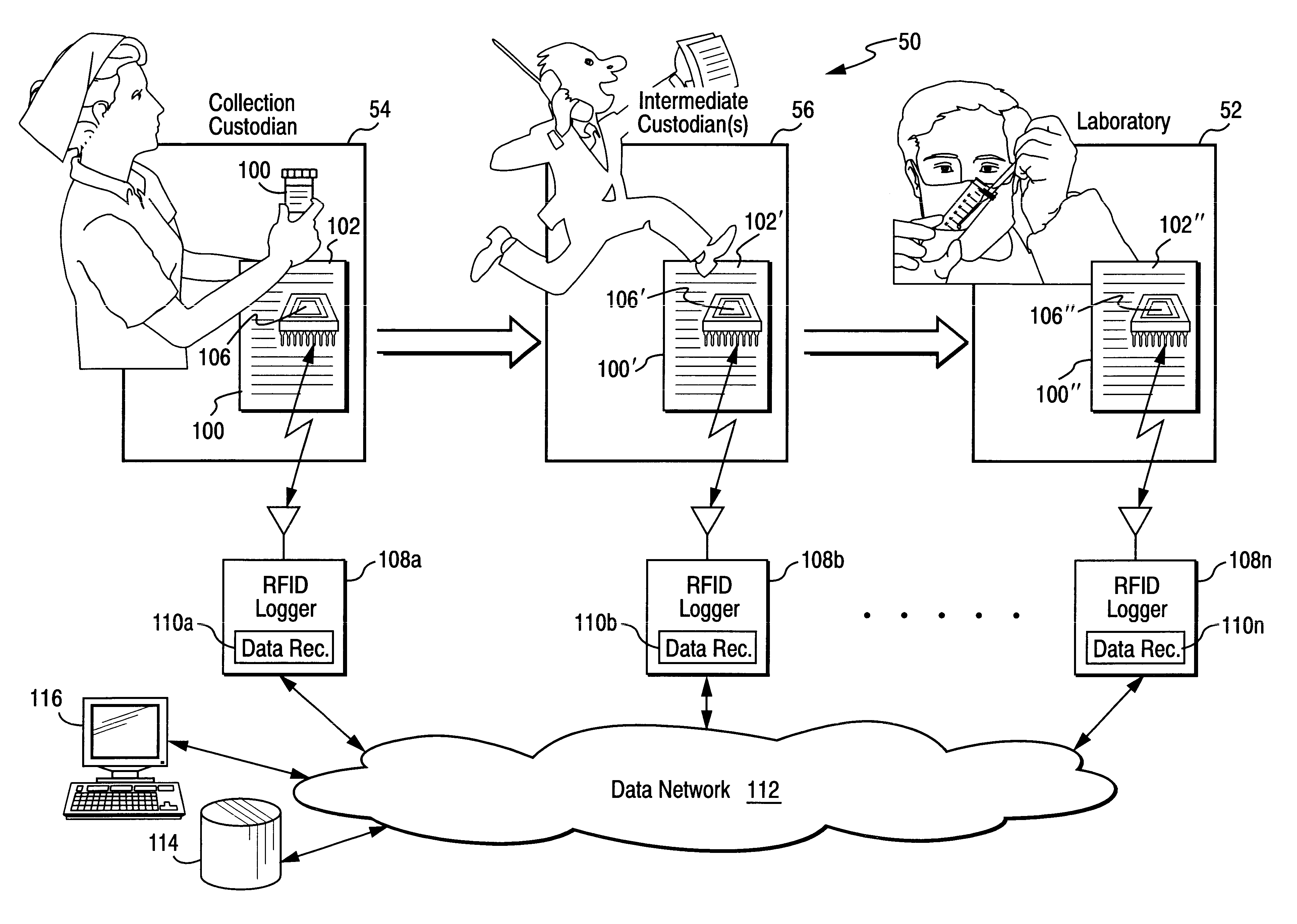
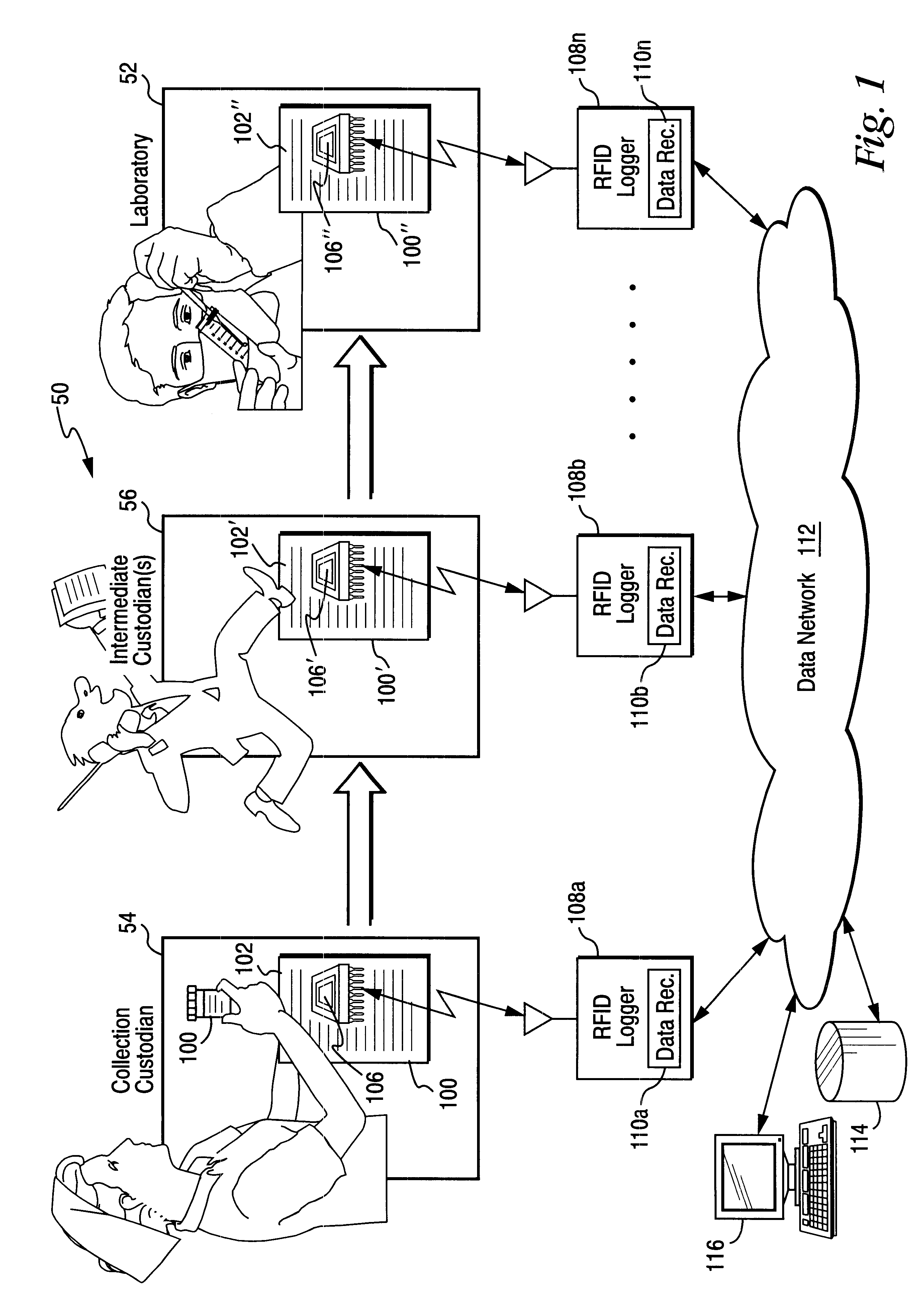
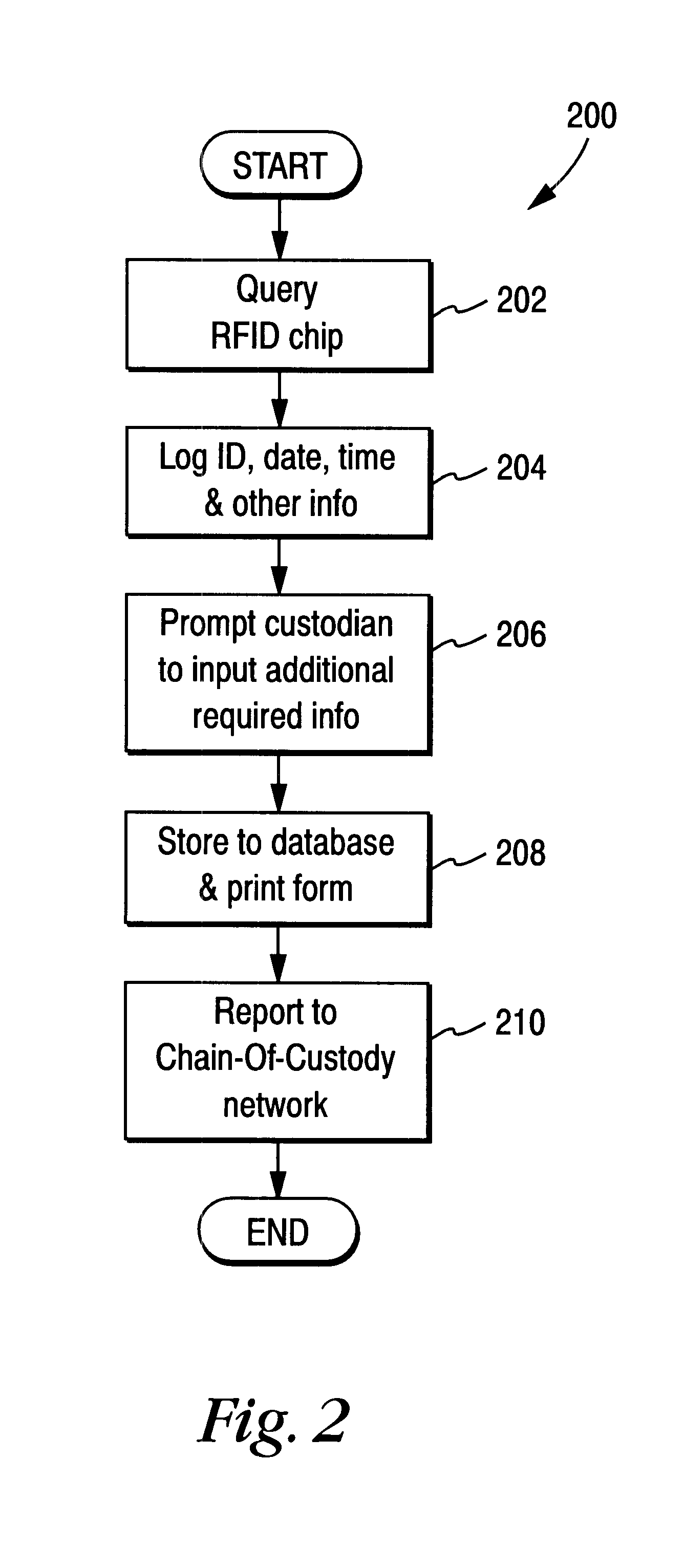
Chain of custody business form with automated wireless data logging feature
InactiveUS6535129B1Reduce consumable costsReliable identificationElectric signal transmission systemsDigital data processing detailsThird partyWireless data
A chain of custody form with an associated wireless (e.g., RFID) chip results in data being monitored and filed electronically, minimizes the need for a multi-part form and results in reduced consumable costs to the customer. Samples are no longer lost in transit or within a testing laboratory, as the RFID chip allows for complete tracking of the specimen. Positive location identification is always available. All data may be tracked using the RFID chip which may prompt the collector or other custodian to correctly enter data. The chain of custody is always accurate and is never broken. All data may be shared with all parties electronically including, for example, an employer, a collection site, a medical review officer, a third party administrator, etc. No re-keying of the information is necessary, eliminating multiple steps, reducing the potential for error, and providing increased efficiencies and decreased processing time at reduced costs.
Owner:MOORE NORTH AMERICA INC
Methods and apparatus for dynamic session key generation and rekeying in mobile IP
ActiveUS7475241B2Eliminate needDigital data processing detailsMultiple digital computer combinationsPasswordRe keying
Methods and apparatus for providing a centralized source of session keys to be shared by a Home Agent and a Mobile Node are disclosed. In accordance with one aspect of the invention, a Mobile Node registers with a Home Agent supporting Mobile IP by sending a registration request to the Home Agent. The Home Agent sends a request message (e.g., access-request message) to a AAA server, the request message identifying the Mobile Node. The AAA server then derives key information from a key or password associated with the Mobile Node. The AAA server then sends a reply message (e.g., access-reply message) to the Home Agent, the reply message including the key information associated with the Mobile Node, thereby enabling the Home Agent to derive a shared key to be shared between the Mobile Node and the Home Agent from the key information. The Home Agent derives a key from the key information, the key being a shared key between the Mobile Node and the Home Agent. A registration reply is then sent to the Mobile Node. When the Mobile Node receives a registration reply from the Home Agent, the registration reply indicates that the Mobile Node is to derive a key to be shared between the Mobile Node and the Home Agent. The Mobile Node then derives a key to be shared between the Mobile Node and the Home Agent from key information stored at the Mobile Node. The Mobile Node may initiate “re-keying” by sending a subsequent registration request to the Home Agent.
Owner:CISCO TECH INC
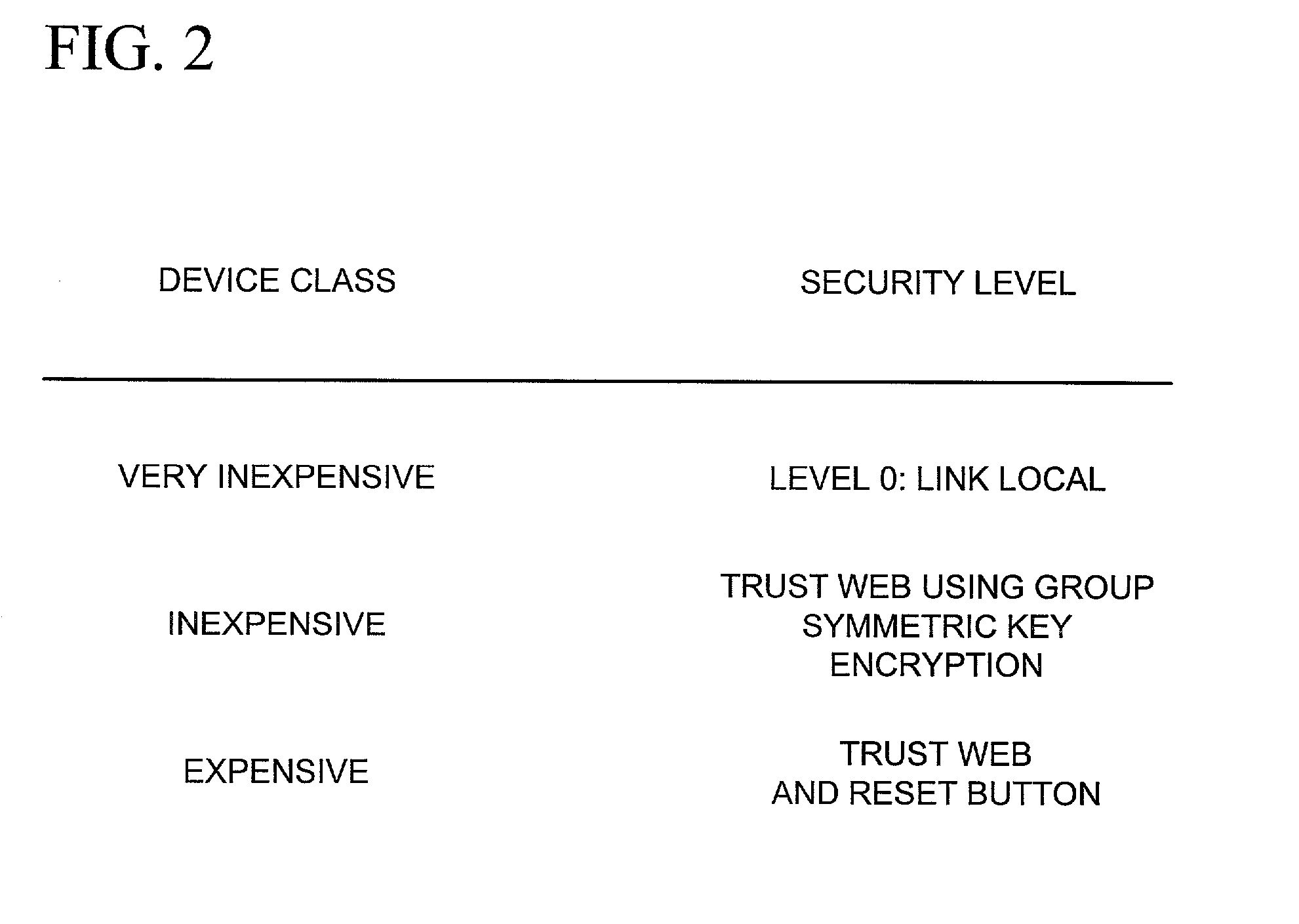
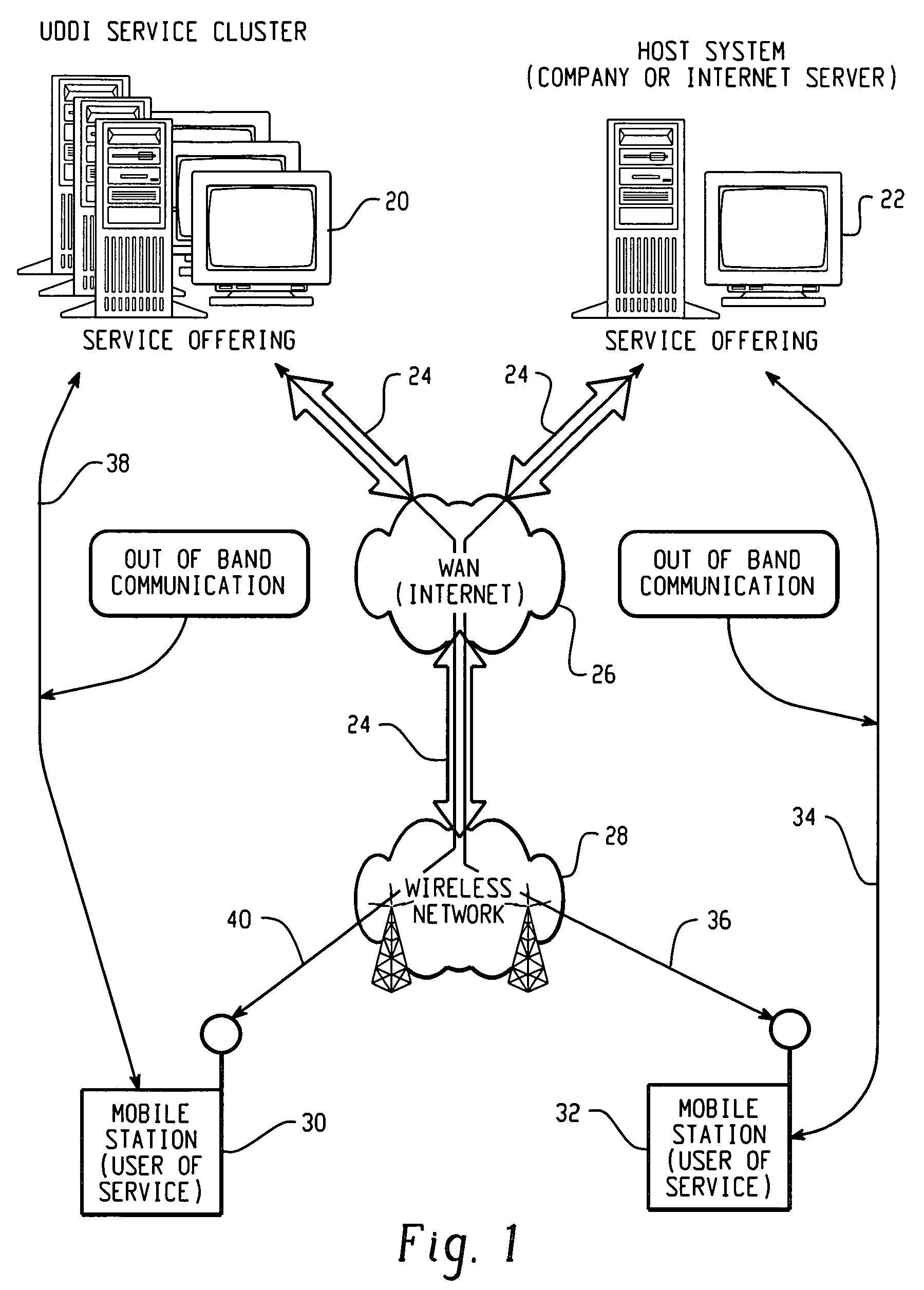
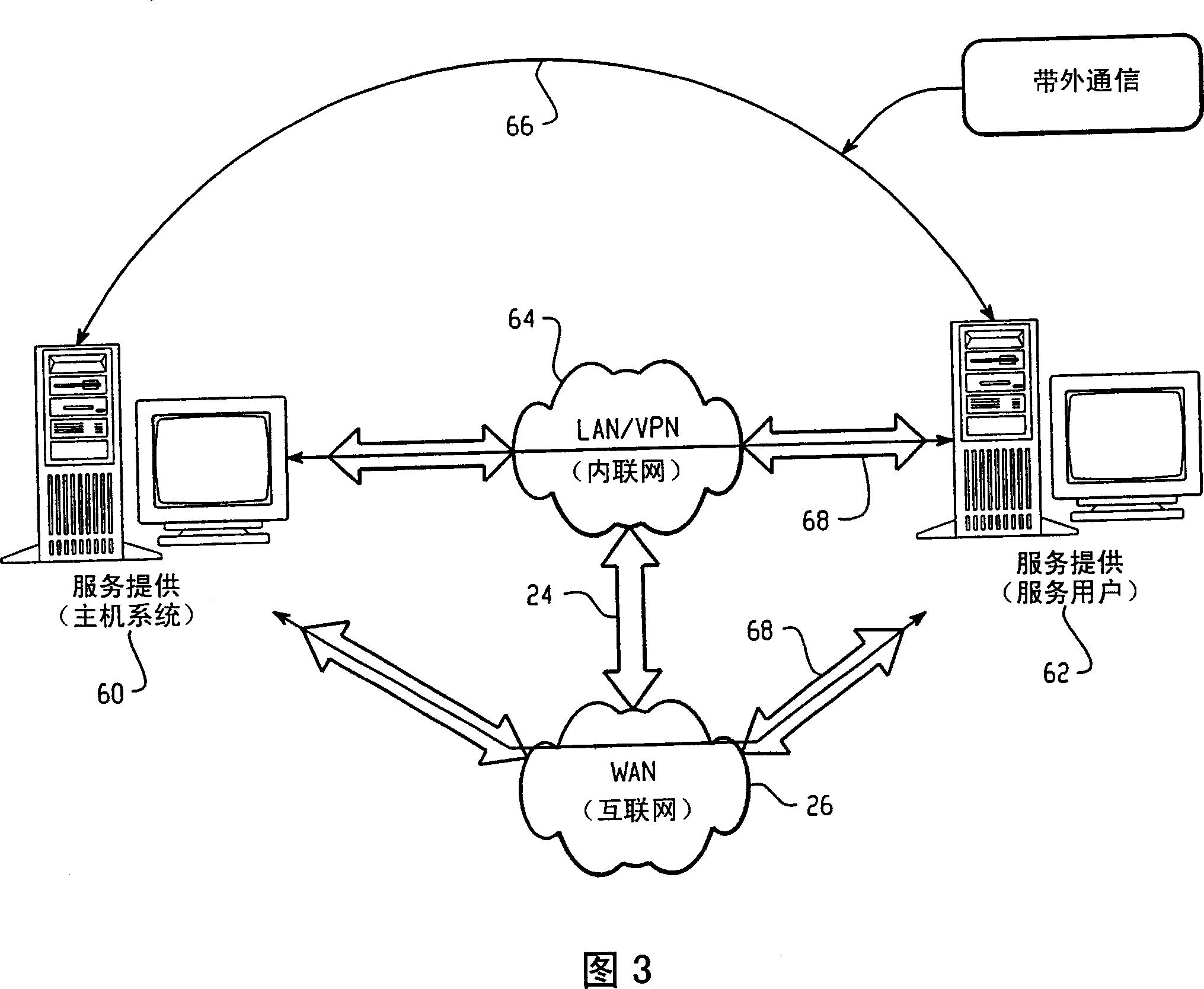
Establishing secure peer networking in trust webs on open networks using shared secret device key
InactiveUS7082200B2CostImprove connectivityKey distribution for secure communicationDigital data processing detailsS/KEYVia device
Owner:MICROSOFT TECH LICENSING LLC
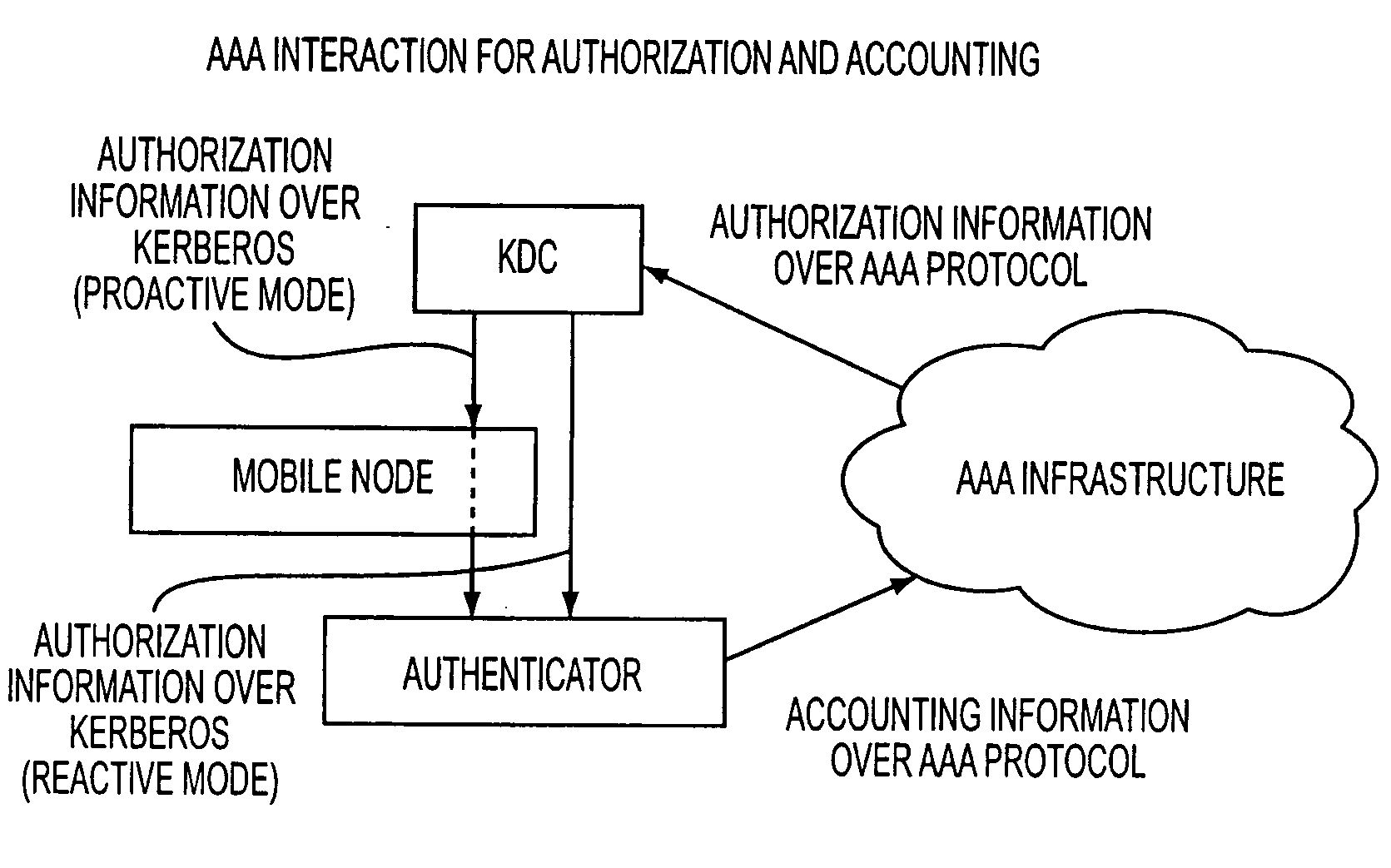
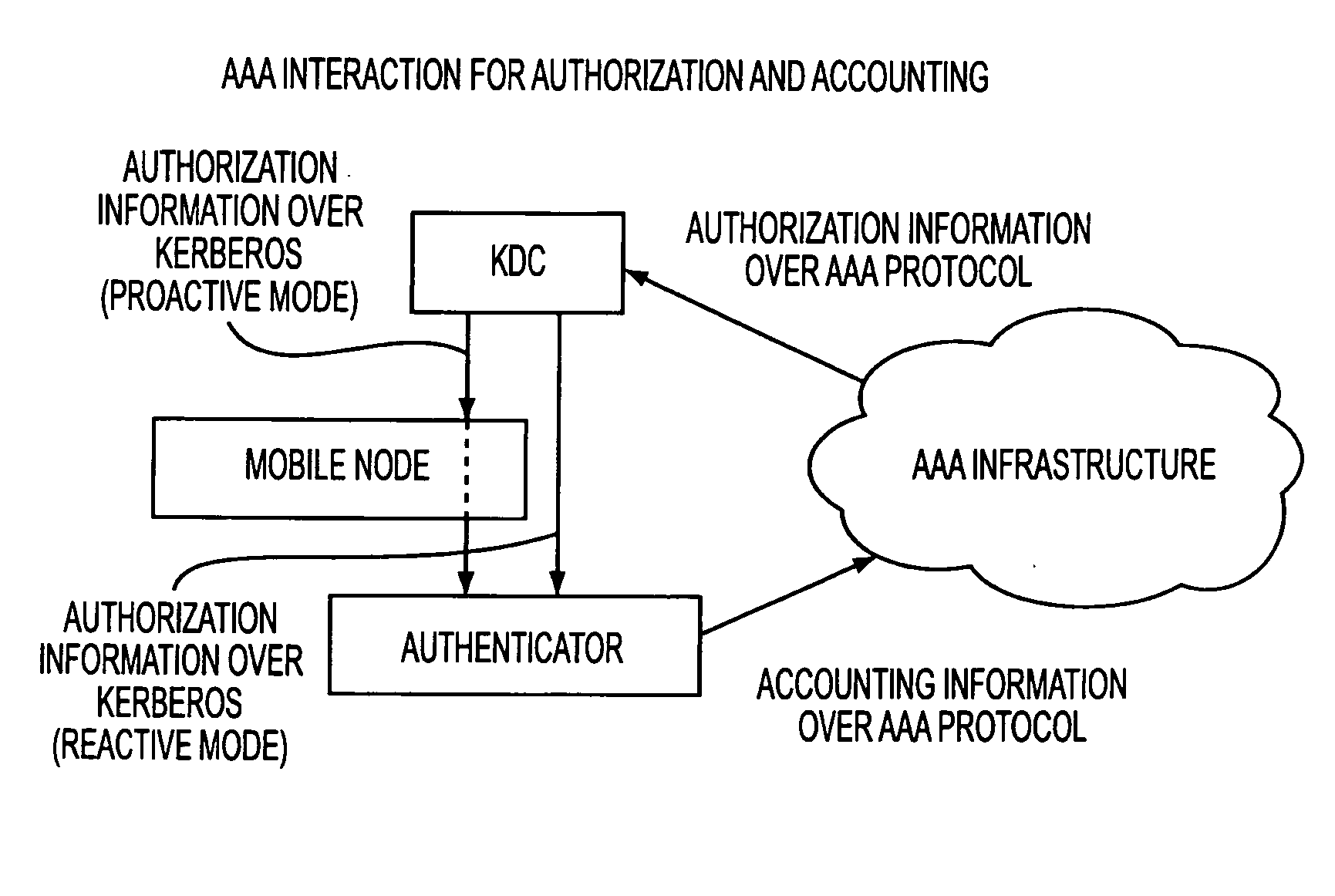
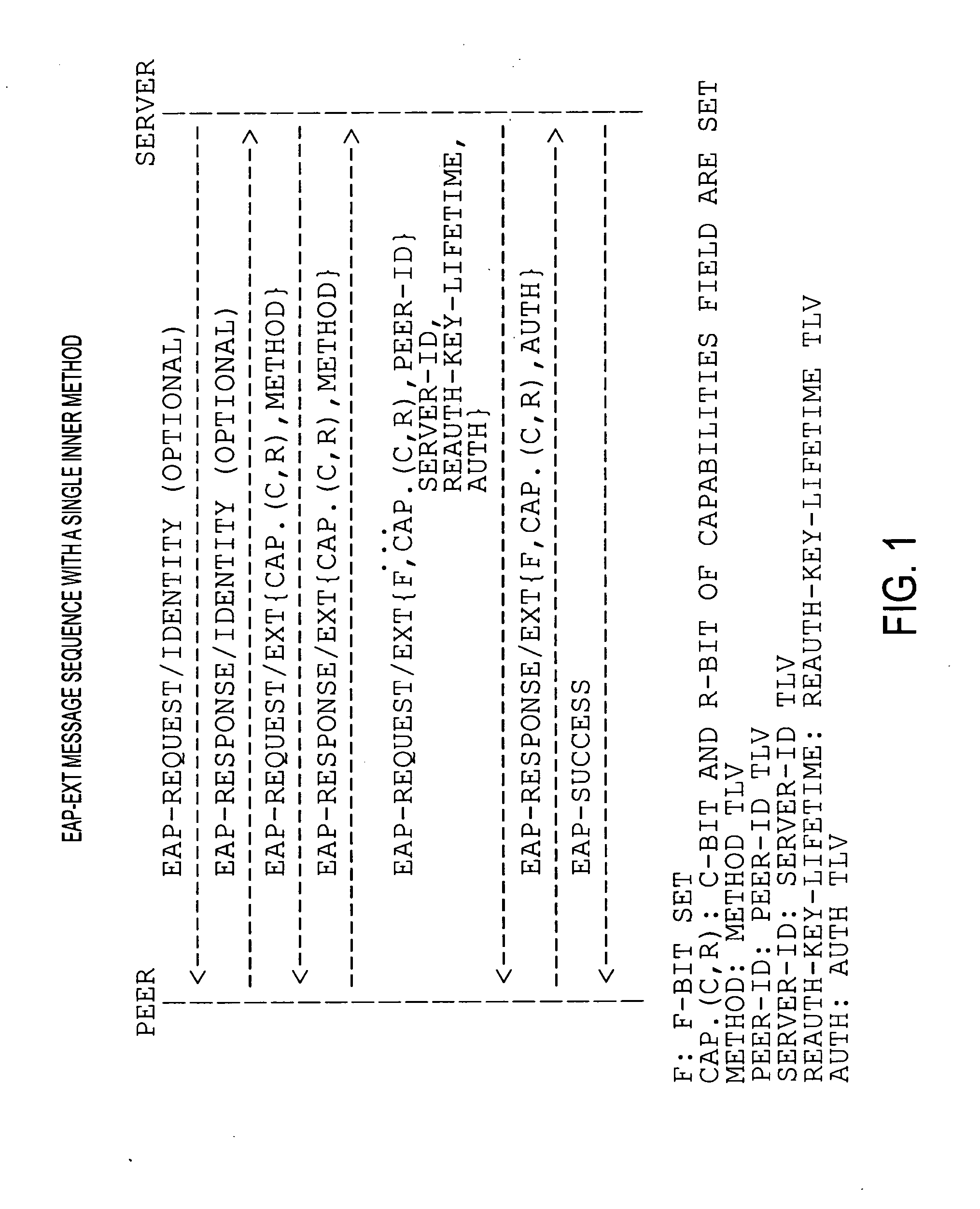
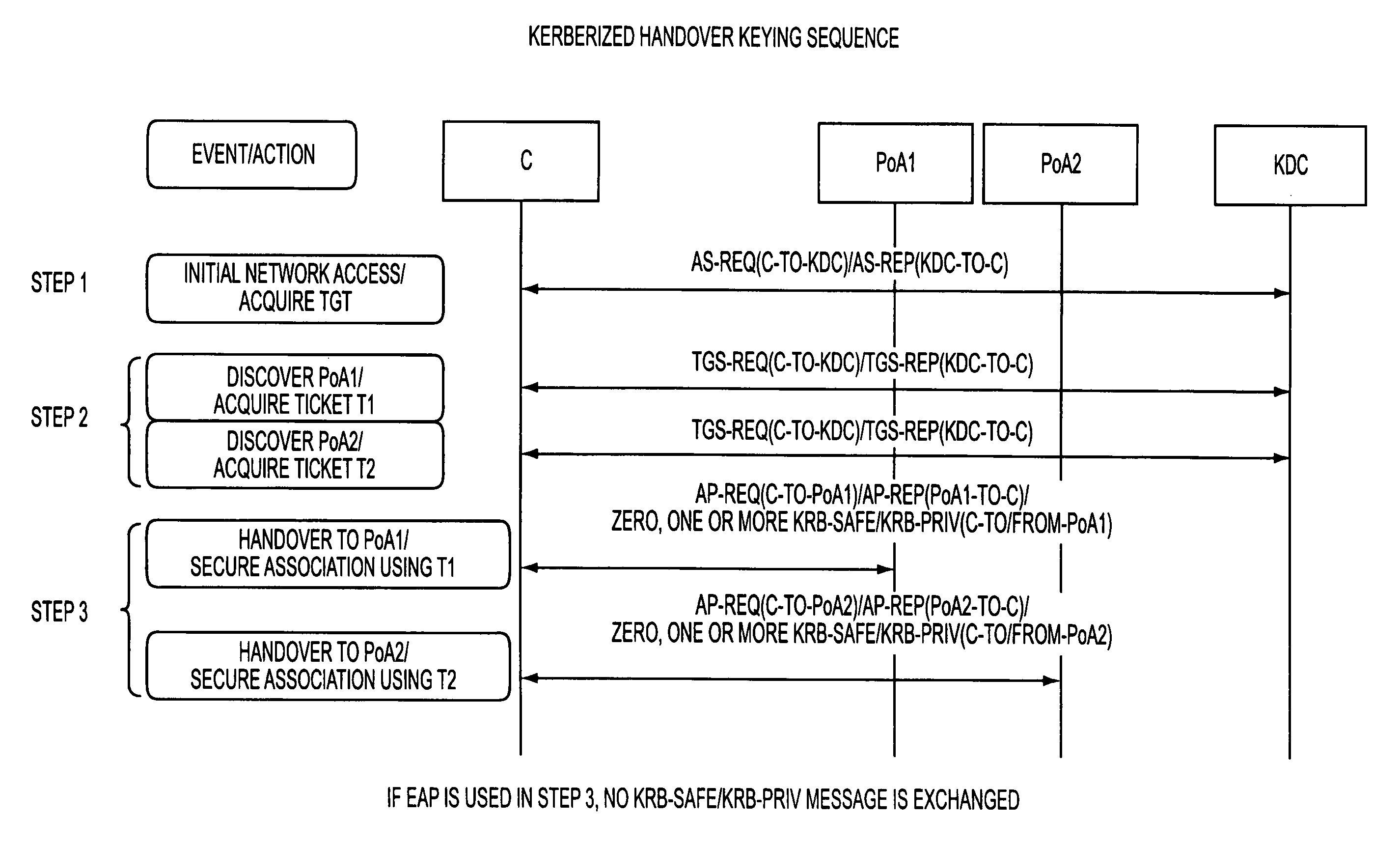
Kerberized handover keying improvements
InactiveUS20080212783A1Key distribution for secure communicationDigital data processing detailsSecurity associationOperation mode
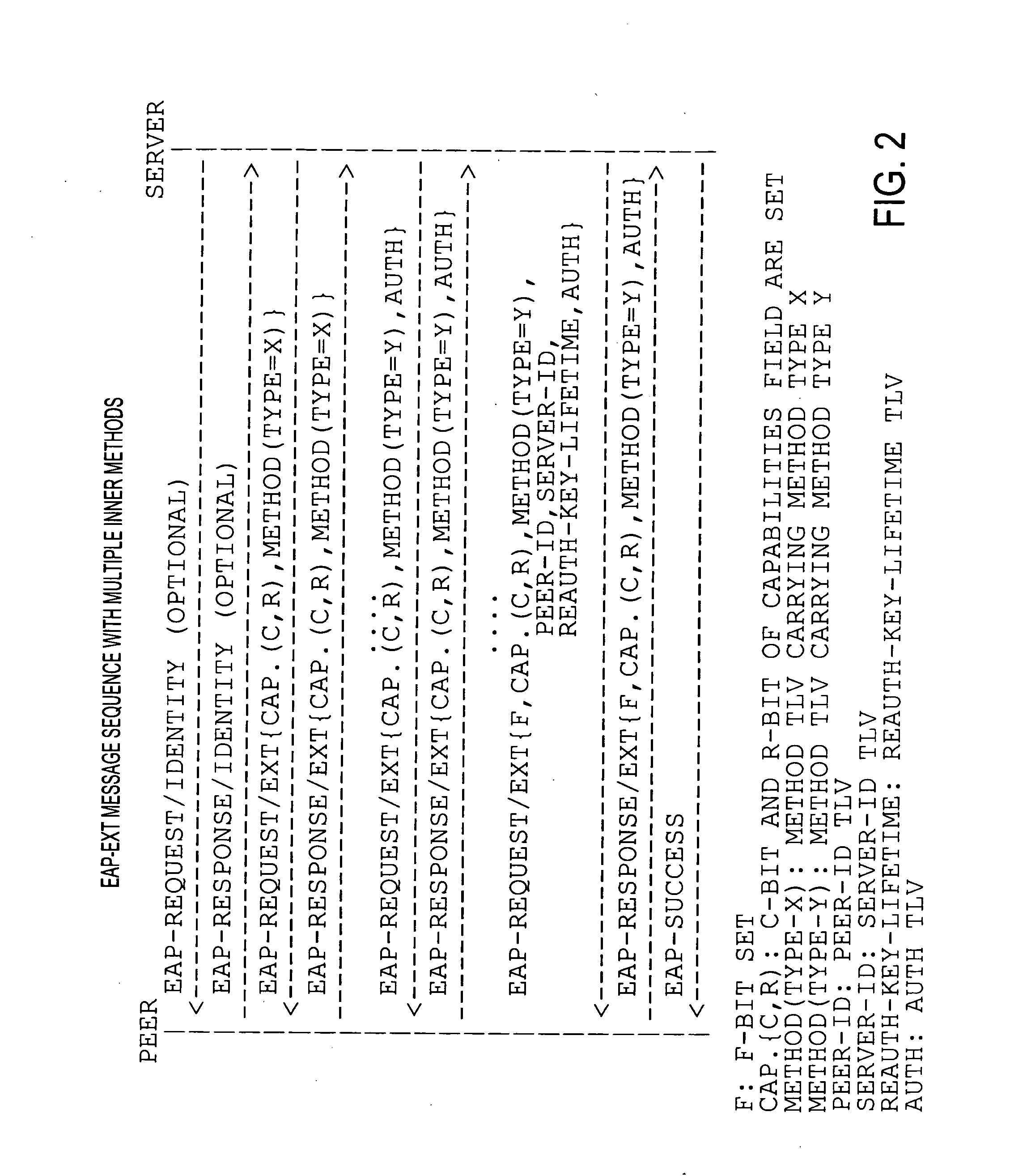
A media-independent handover key management architecture is disclosed that uses Kerberos for secure key distribution among a server, an authenticator, and a mobile node. In the preferred embodiments, signaling for key distribution is based on re-keying and is decoupled from re-authentication that requires EAP (Extensible Authentication Protocol) and AAA (Authentication, Authorization and Accounting) signaling similar to initial network access authentication. In this framework, the mobile node is able to obtain master session keys required for dynamically establishing the security associations with a set of authenticators without communicating with them before handover. By separating re-key operation from re-authentication, the proposed architecture is more optimized for a proactive mode of operation. It can also be optimized for reactive mode of operation by reversing the key distribution roles between the mobile node and the target access node.
Owner:TELCORDIA TECHNOLOGIES INC +1
Kerberized handover keying
ActiveUS20080175393A1Key distribution for secure communicationDigital data processing detailsRe keyingProtocol for Carrying Authentication for Network Access
A media-independent handover key management architecture is disclosed that uses Kerberos for secure key distribution among a server, an authenticator, and a mobile node. In the preferred embodiments, signaling for key distribution is based on re-keying and is decoupled from re-authentication that requires EAP (Extensible Authentication Protocol) and AAA (Authentication, Authorization and Accounting) signaling similar to initial network access authentication. In this framework, the mobile node is able to obtain master session keys required for dynamically establishing the security associations with a set of authenticators without communicating with them before handover. By separating re-key operation from re-authentication, the proposed architecture is more optimized for a proactive mode of operation. It can also be optimized for reactive mode of operation by reversing the key distribution roles between the mobile node and the target access node.
Owner:TELCORDIA TECHNOLOGIES INC +1
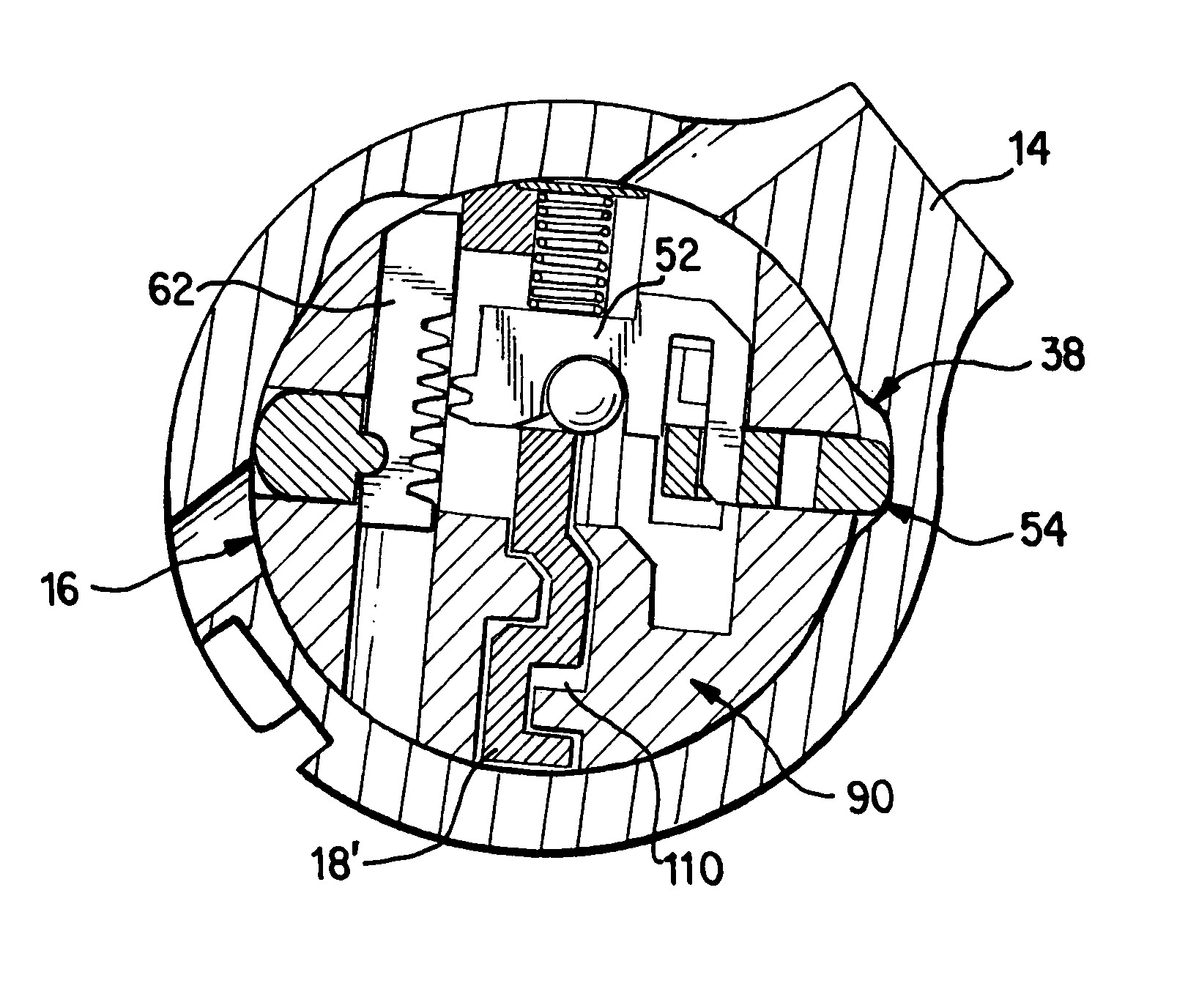
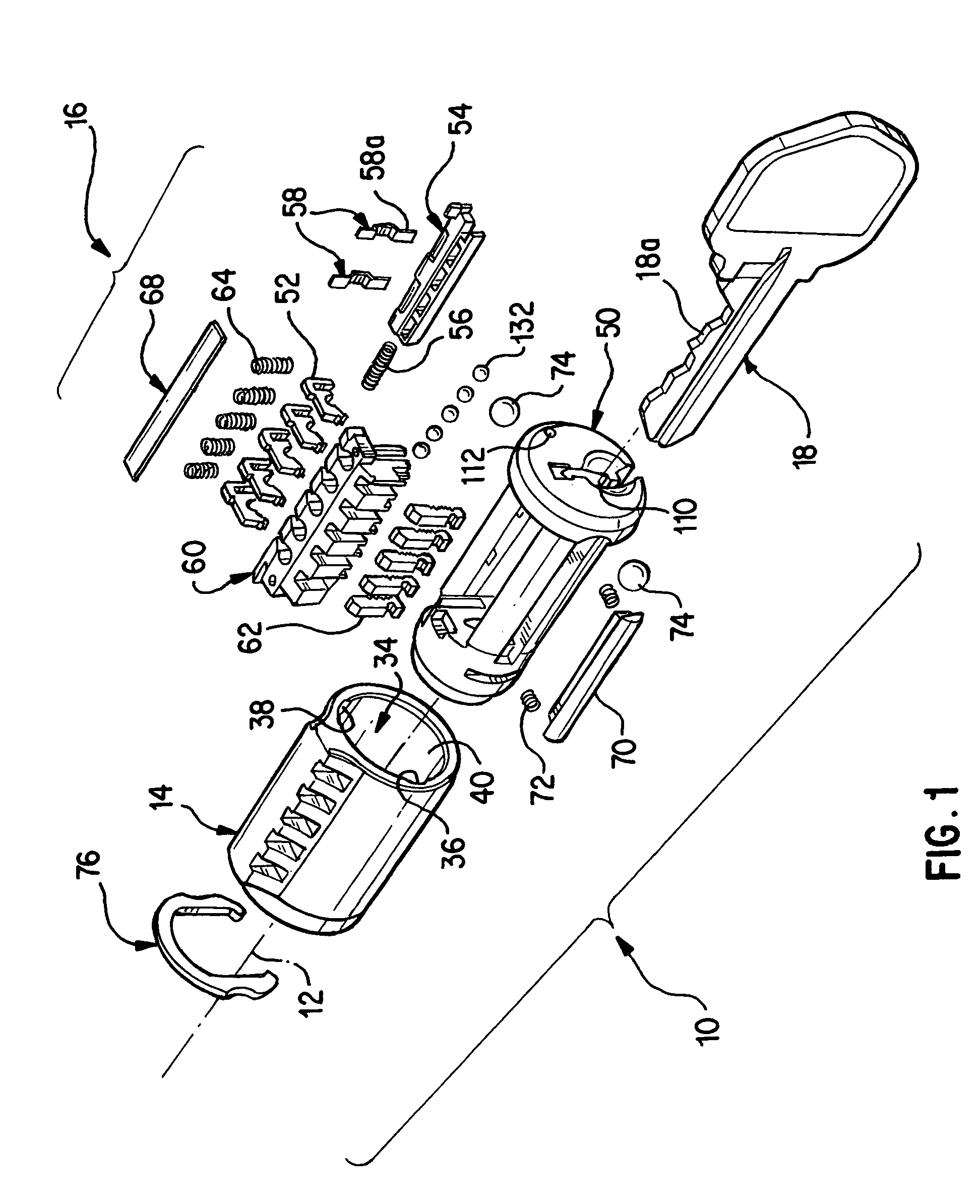
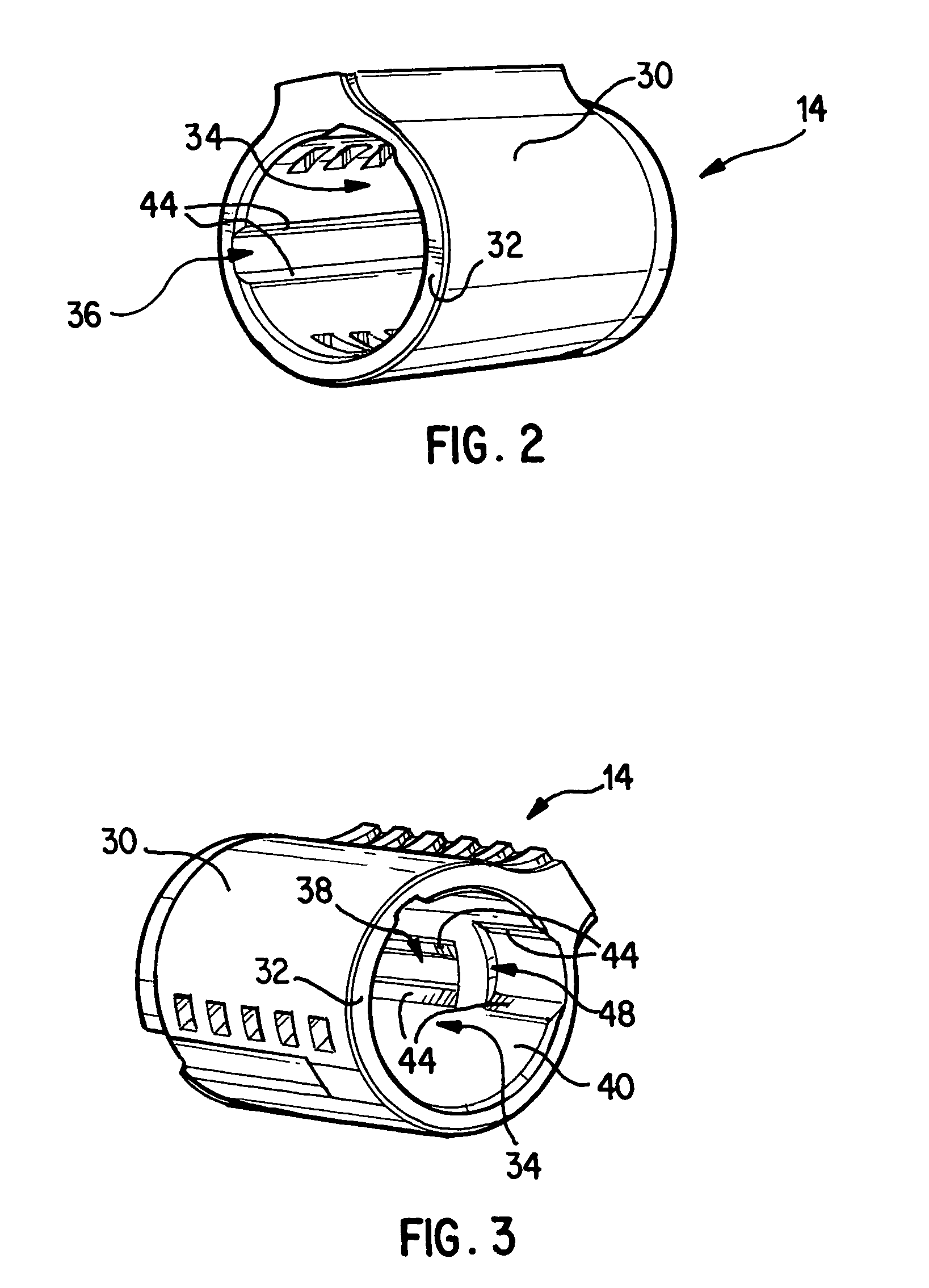
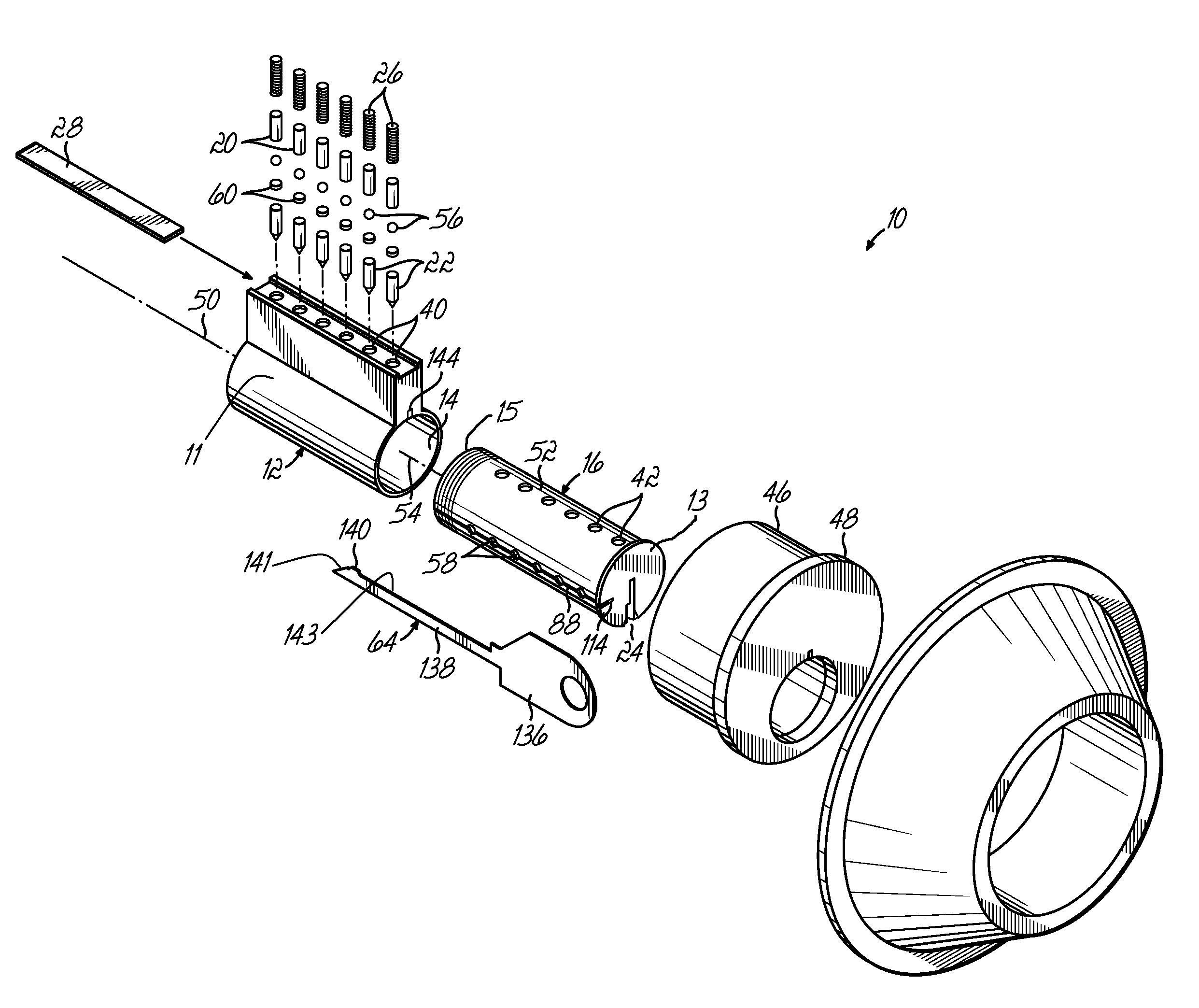
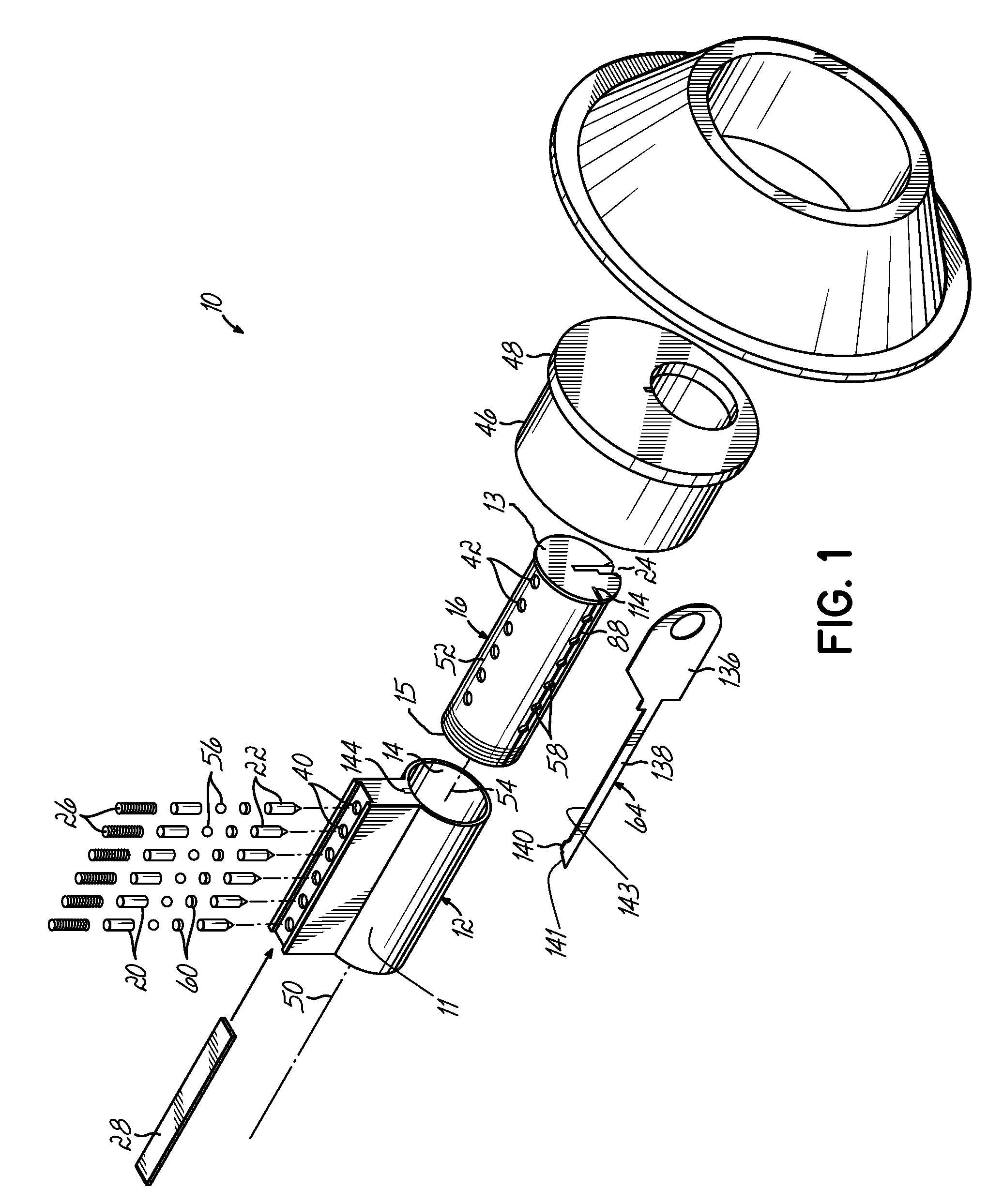
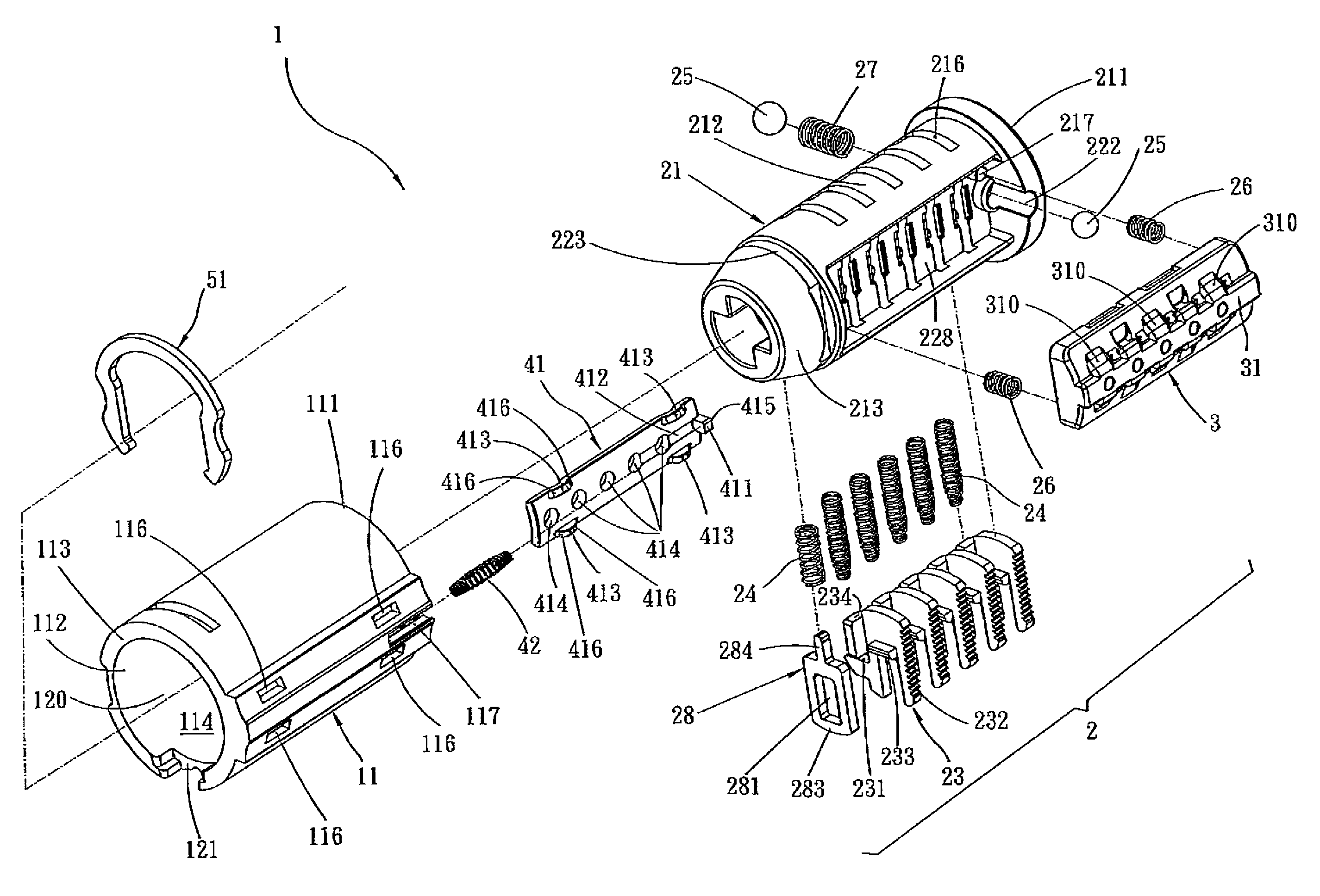
Re-keyable lock assembly
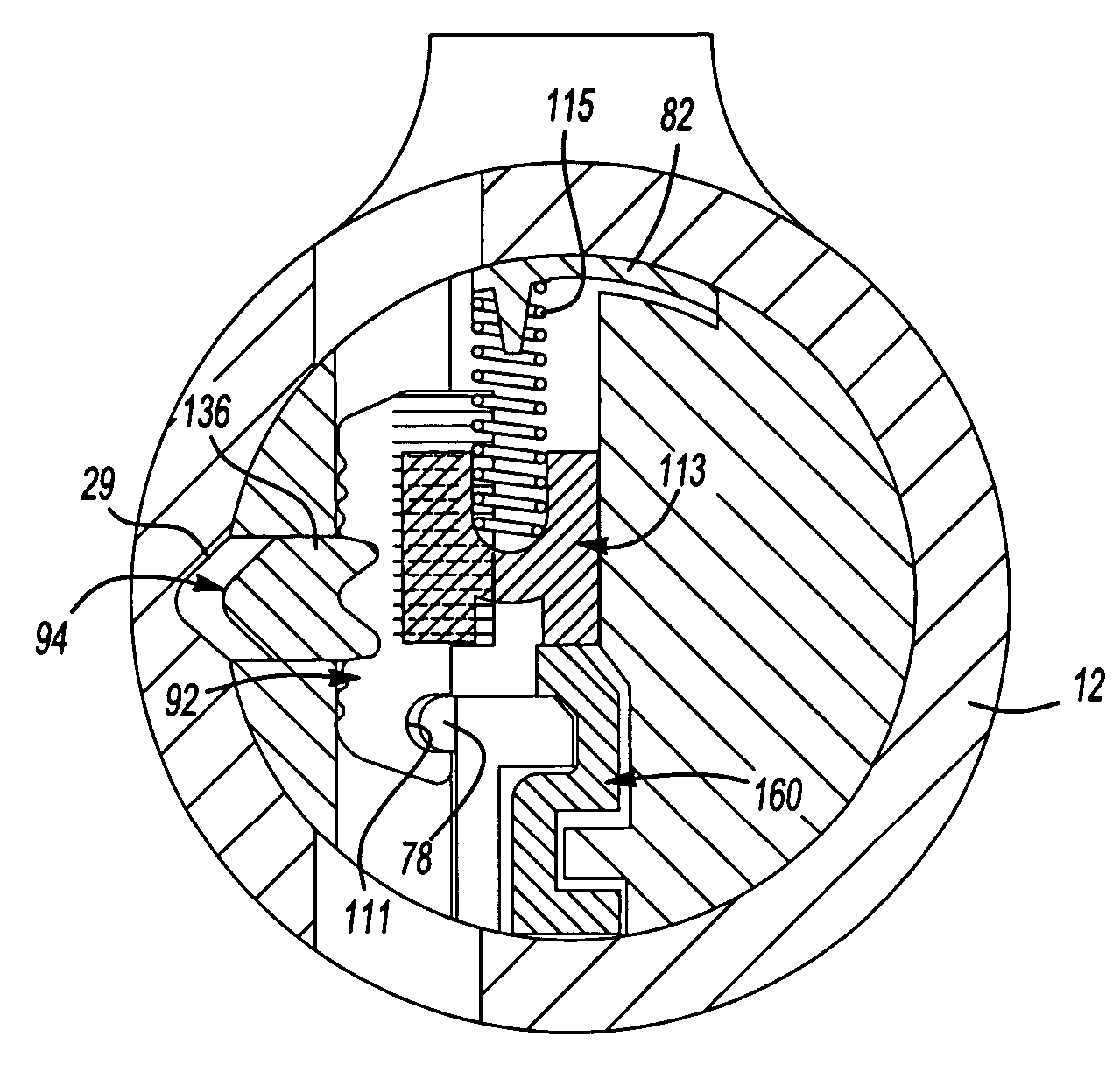
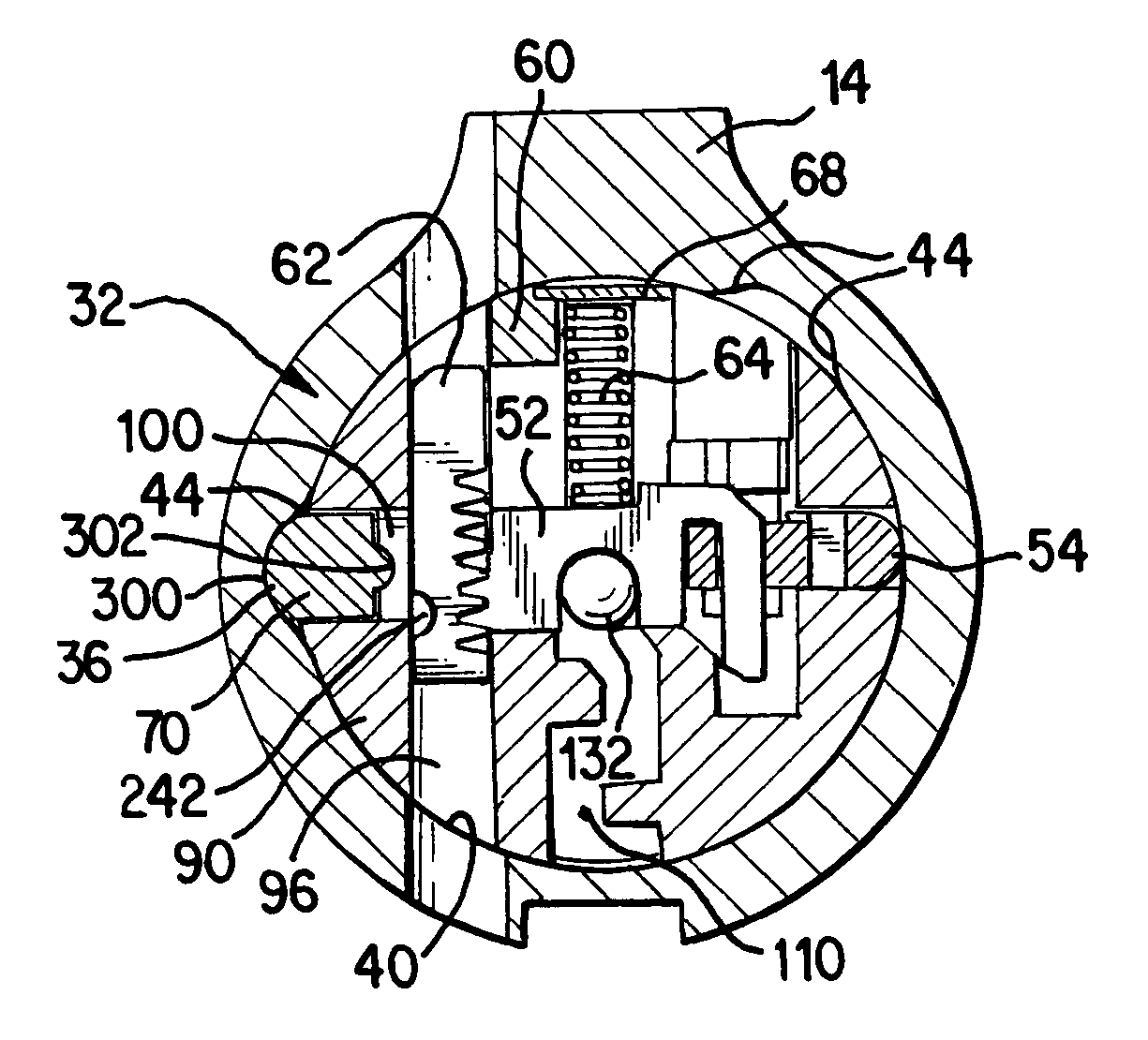
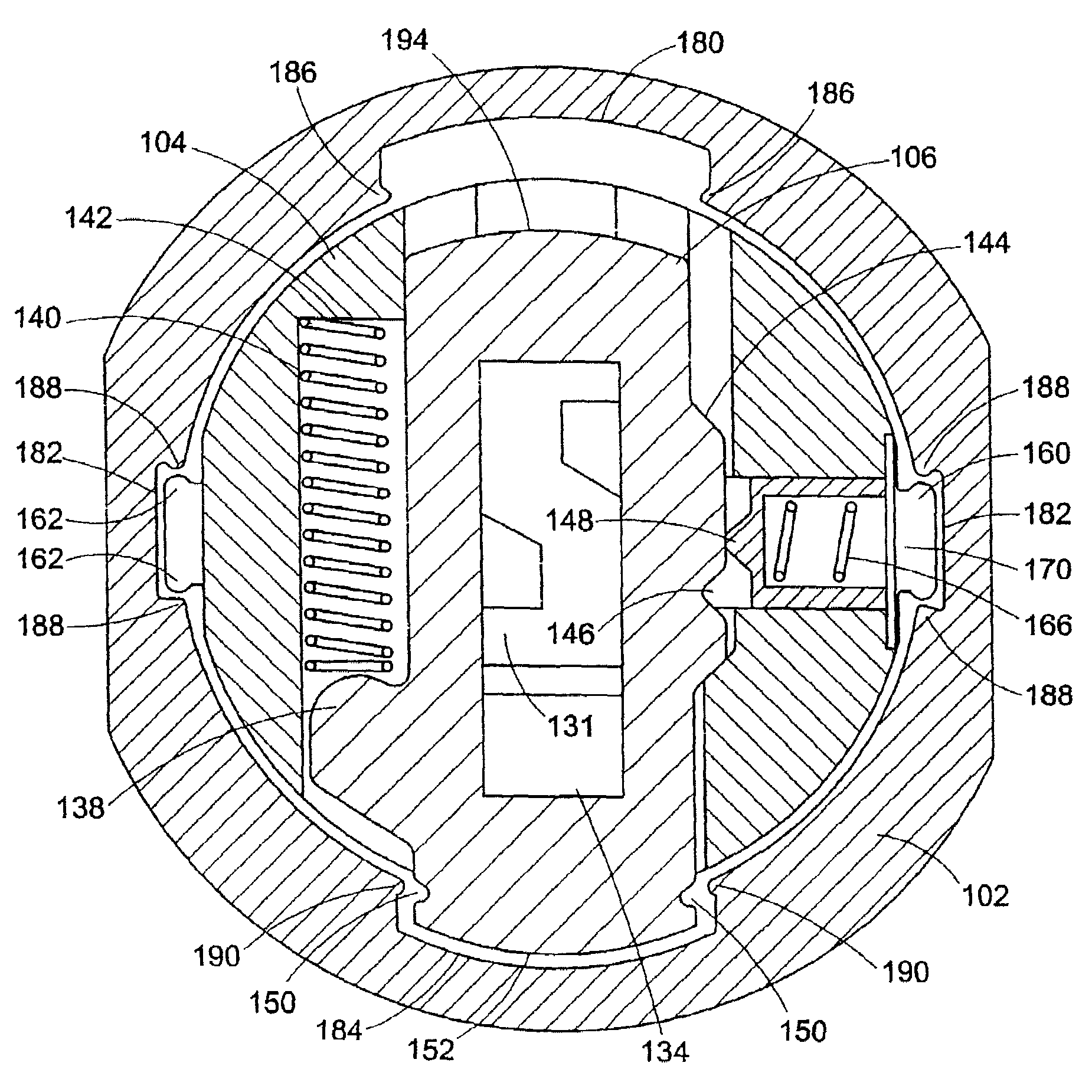
A re-keyable lock cylinder includes a plug body and a carrier sub-assembly disposed adjacent the plug body. The plug assembly includes a plurality of planar wafers and the carrier sub assembly includes a plurality of racks for engaging the wafers in a face-to-face teeth arrangement. The racks disengage from the wafers to separate the teeth in response to movement of the carrier such that the lock cylinder is in a re-keyable condition when the racks are disengaged from the wafers.
Owner:RAYOVAC CORP
Re-keyable lock cylinder
A re-keyable lockset that employs pairs of first and second pins. Coupling of the first and second pins to one another defines a key profile for a mating key. A second key with a different key profile may be installed to the lockset when the first and second pins are uncoupled from one another. Thereafter, the first and second pins may be re-coupled to one another to define the key profile of a new mating key. A method for re-keying a lockset is also provided.
Owner:RAYOVAC CORP
Dynamic source authentication and encryption cryptographic scheme for a group-based secure communication environment
InactiveUS20050111668A1Key distribution for secure communicationMultiple keys/algorithms usageSecure communicationAdemetionine
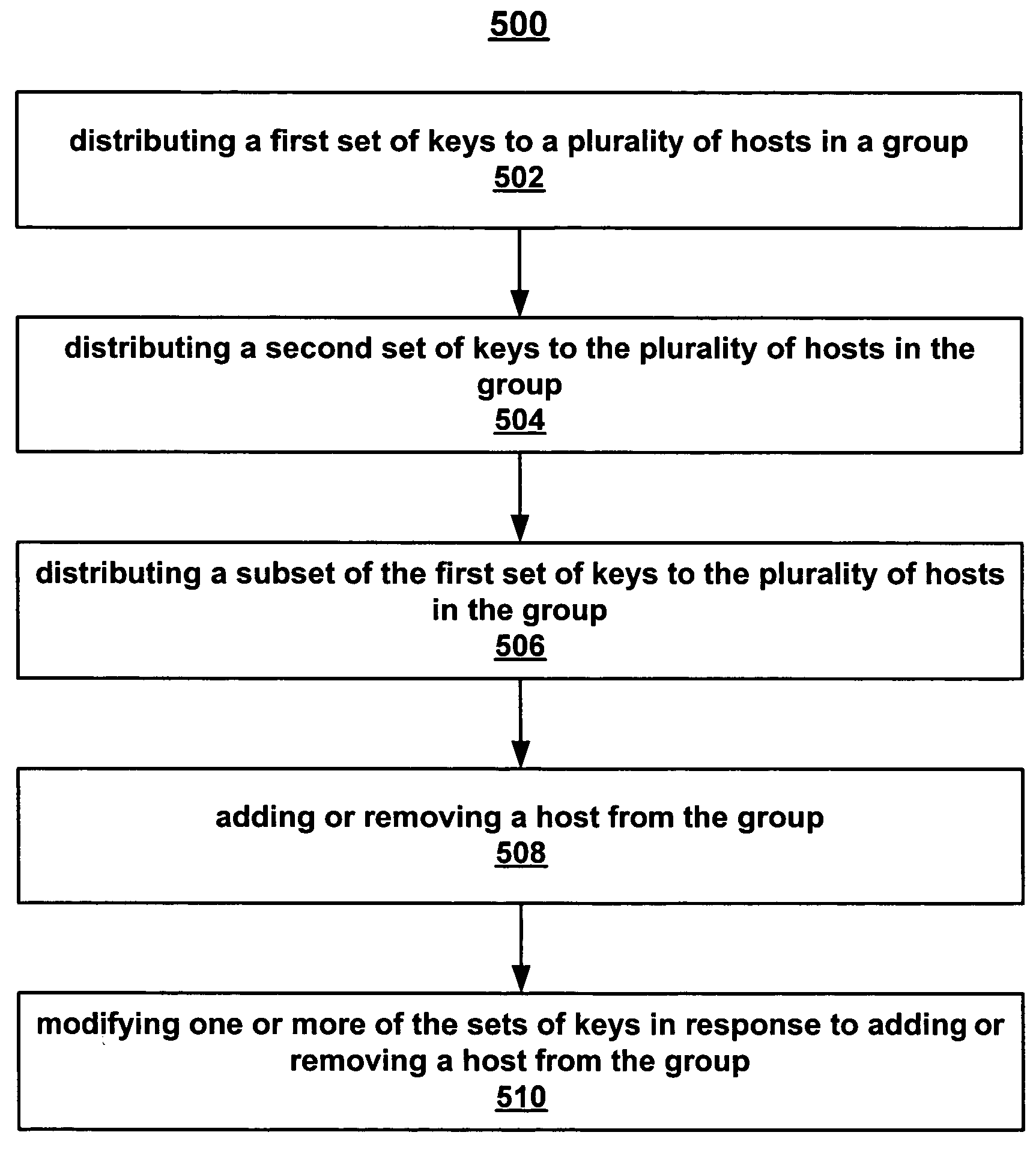
Embodiments of the present invention include a method for establishing secure group-based communication comprising: distributing a first set of keys to a plurality of hosts for encrypting communication and for source authentication of group-based communication between the plurality of hosts. The method further includes distributing a second set of keys to the plurality of hosts for dynamically modifying the first set of keys as also any other keys used (encryption keys or seed variables) when required (viz. for periodic re-keying or for adjusting to a change in group membership).
Owner:HEWLETT PACKARD DEV CO LP
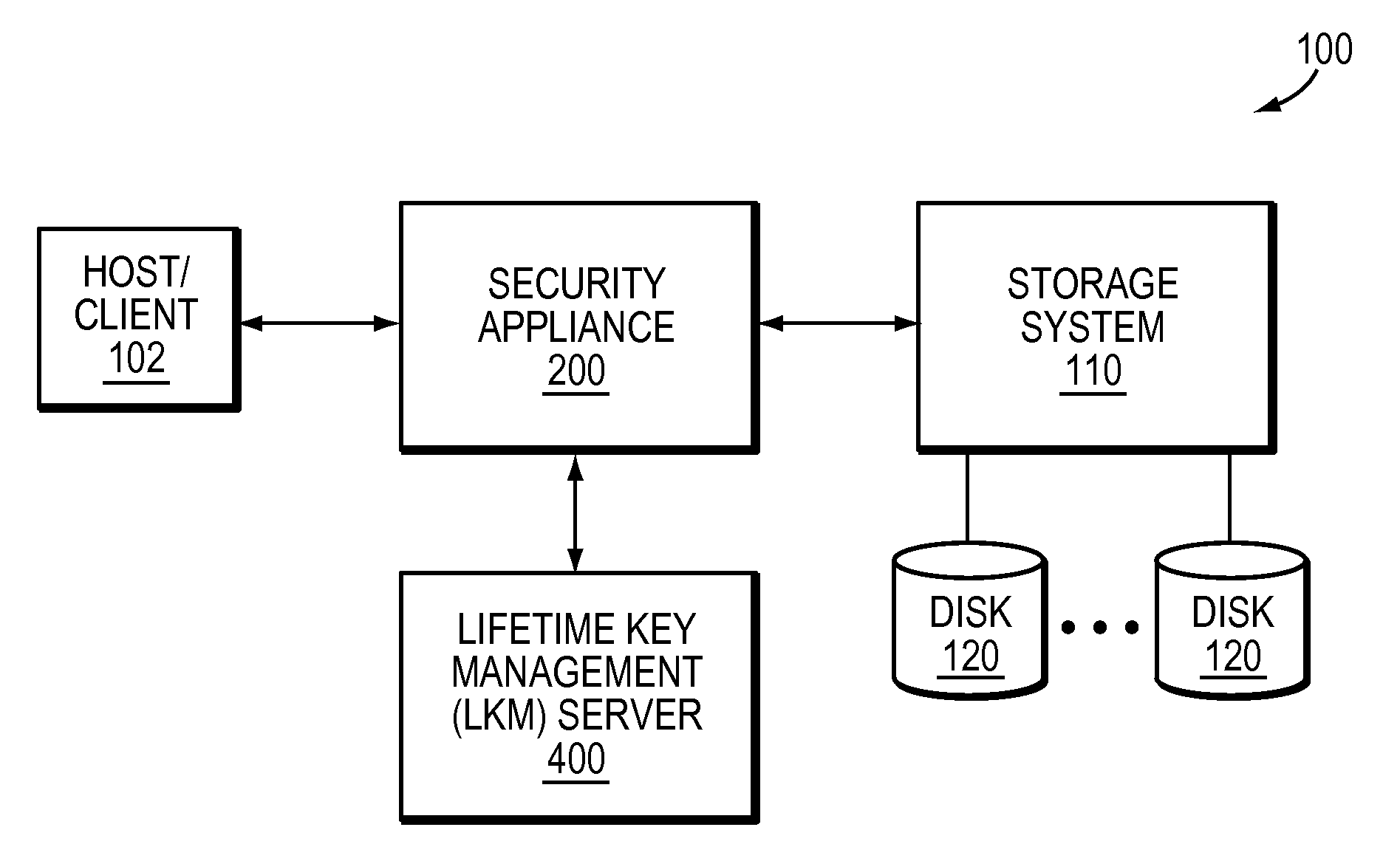
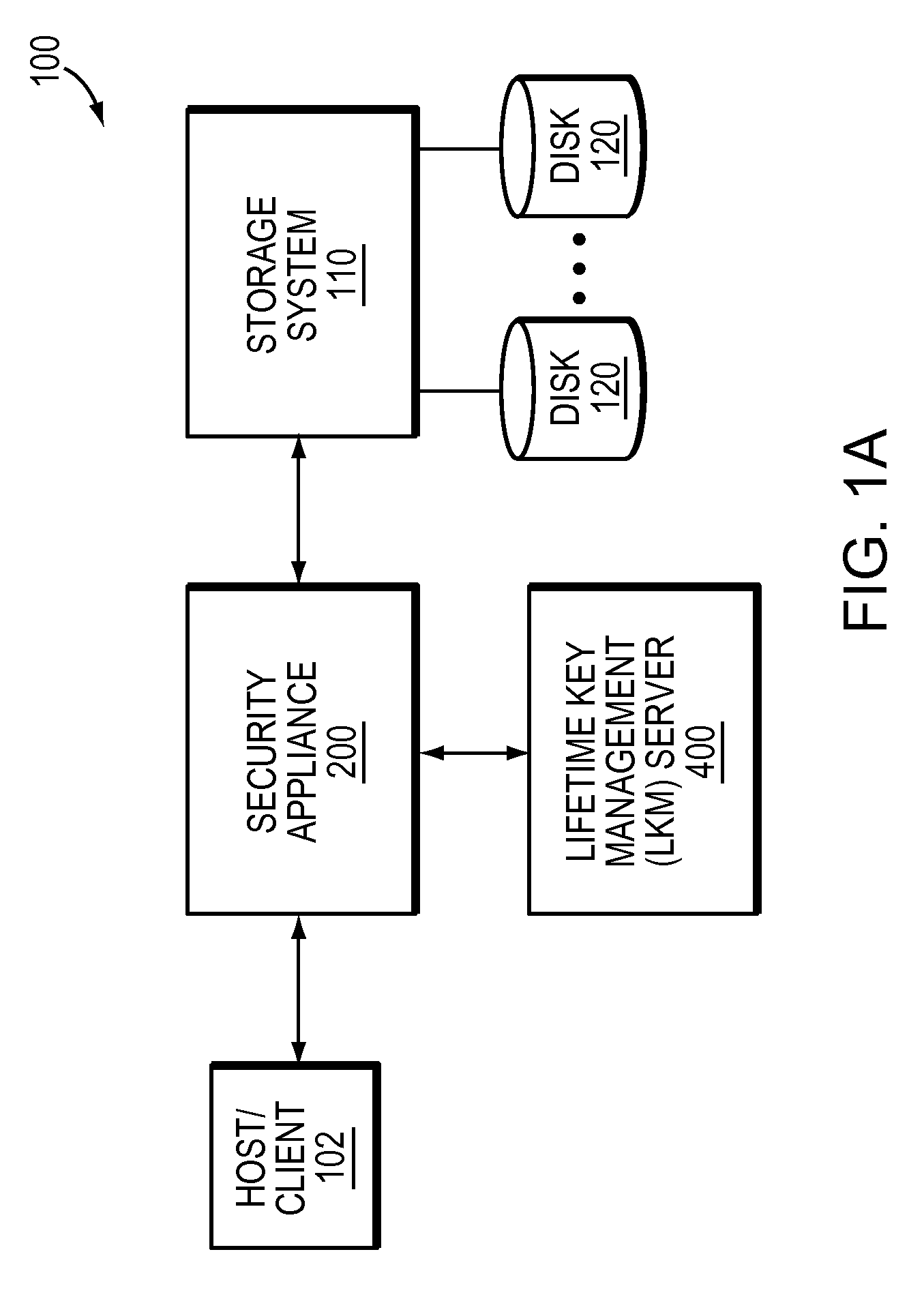
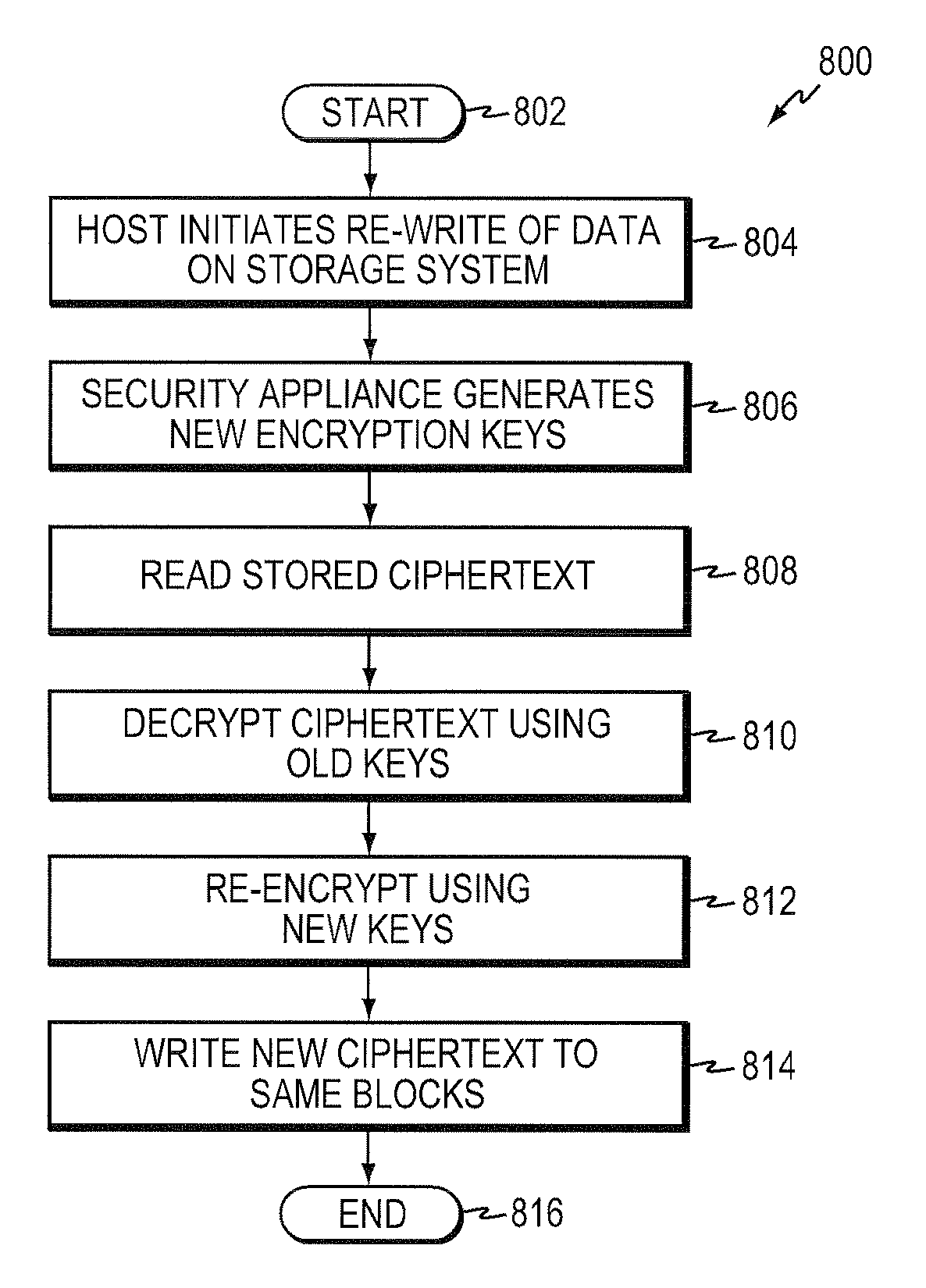
Re-keying based on pre-generated keys
ActiveUS7983423B1Key distribution for secure communicationMultiple keys/algorithms usageCiphertextRe keying
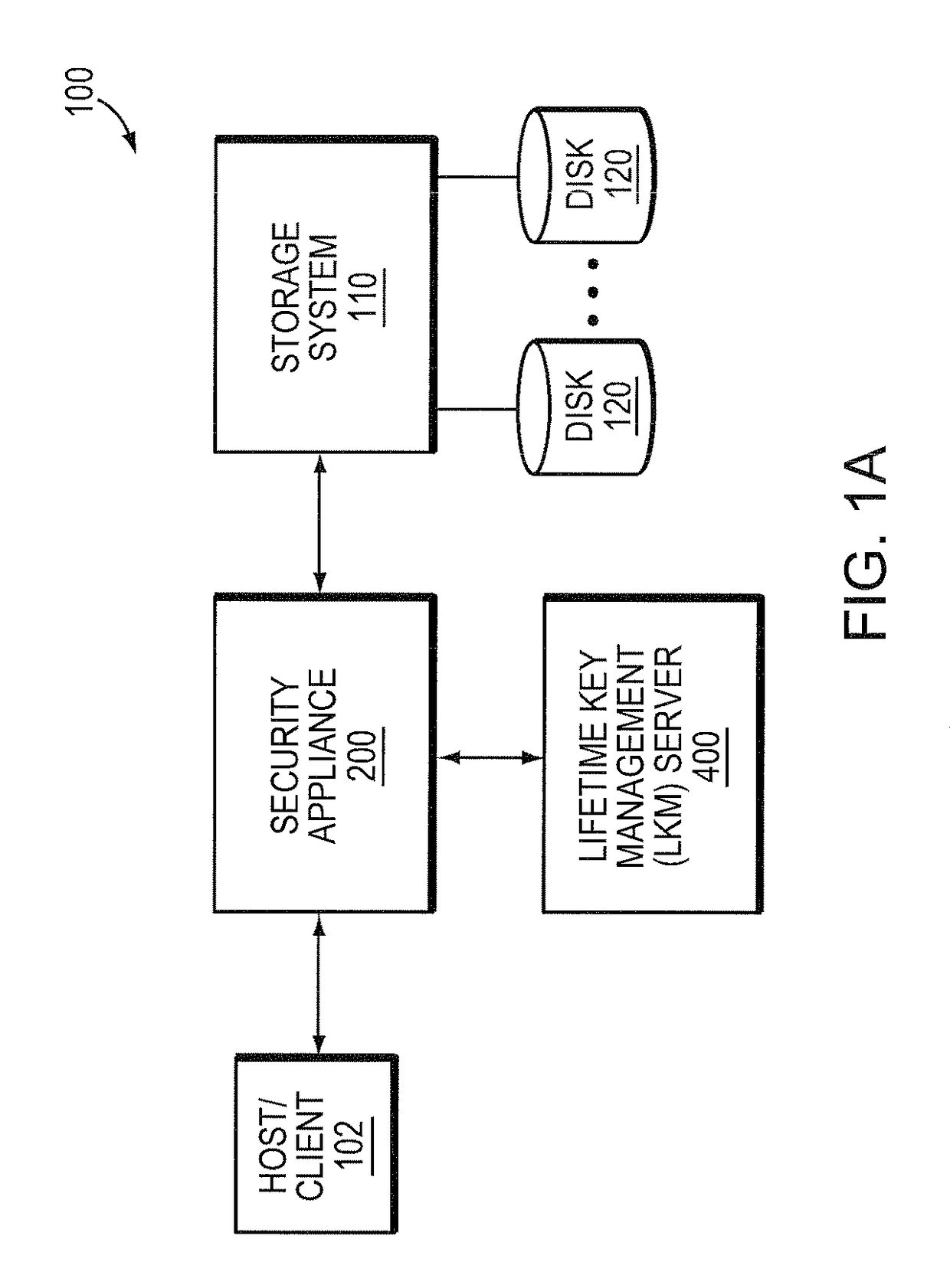
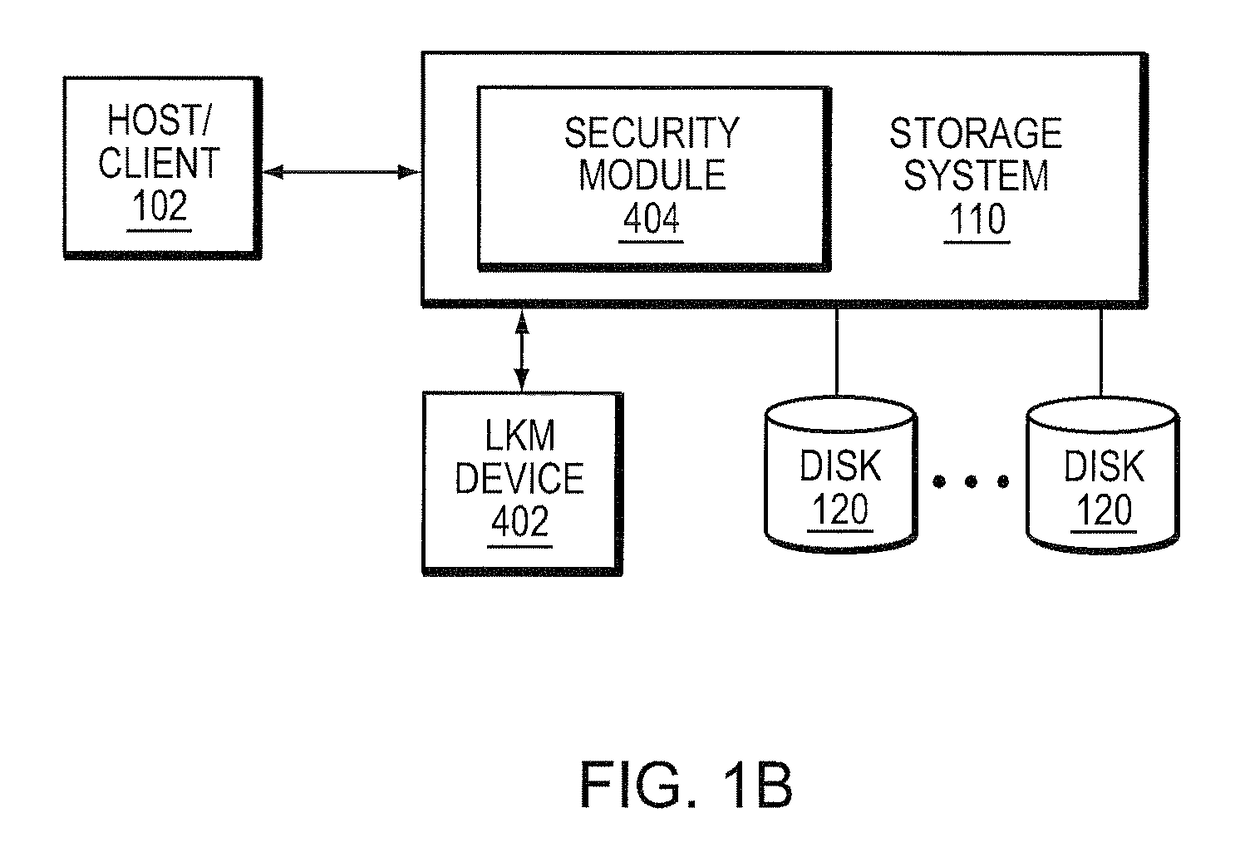
A system and method for pre-generating encryption keys for re-keying stored ciphertext. The encryption keys are illustratively distributed to LKMs and therefrom to the security appliances communicating with each other. A minimum number of un-used pre-generated encryption keys is established wherein when that number is reached more pre-generated encryption keys are created and distributed.
Owner:NETWORK APPLIANCE INC
Method and apparatus for key management in distributed sensor networks
InactiveUS7486795B2Key distribution for secure communicationOptical rangefindersSensor arraySecure communication
In a distributed sensor network, a method of key management is carried out in several phases, particularly key pre-distribution phase, shared key discovery phase, and as needed, a path key establishment phase. In the key pre-distribution phase, prior to DSN deployment, a ring of keys is distributed to each sensor node, each key ring consisting of randomly chosen keys from a large pool of keys which is generated off-line. A shared key exists between each two key rings with a predetermined probability. In the shared key discovery phase, which takes place upon deployment of the DSN, every sensor node discovers its neighbors in wireless communication range with which it shares keys, and the topology of the sensor array is established by forming secure communication links between respective sensor nodes. The path key establishment phase assigns a path key to selected pairs of sensor nodes in wireless communication range that do not share a key but are connected by two or more links at the end of the shared key discovery phase. The key management scheme also assumes a revocation phase for removal of the key ring of the compromised sensor node from the network. Also, re-keying phase is assumed for removal of those keys with the expired lifetime.
Owner:MARYLAND UNIV OF
Systems and methods to securely generate shared keys
ActiveUS7646872B2Key distribution for secure communicationPublic key for secure communicationMaster keyRe keying
A method for secure bidirectional communication between two systems is described. A first key pair and a second key pair are generated, the latter including a second public key that is generated based upon a shared secret. First and second public keys are sent to a second system, and third and fourth public keys are received from the second system. The fourth public key is generated based upon the shared secret. A master key for encrypting messages is calculated based upon a first private key, a second private key, the third public key and the fourth public key. For re-keying, a new second key pair having a new second public key and a new second private key is generated, and a new fourth public key is received. A new master key is calculated using elliptic curve calculations using the new second private key and the new fourth public key.
Owner:MALIKIE INNOVATIONS LTD
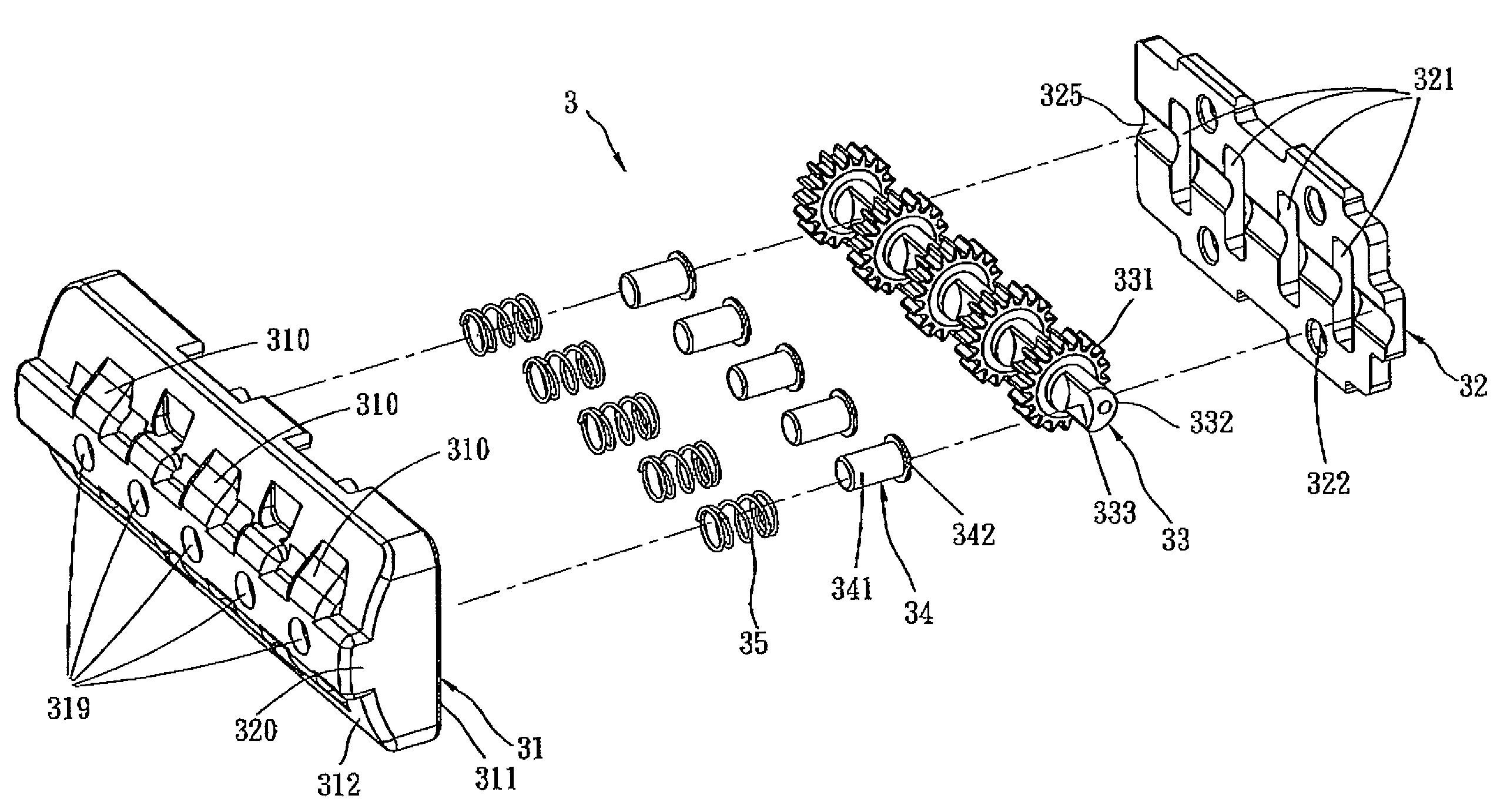
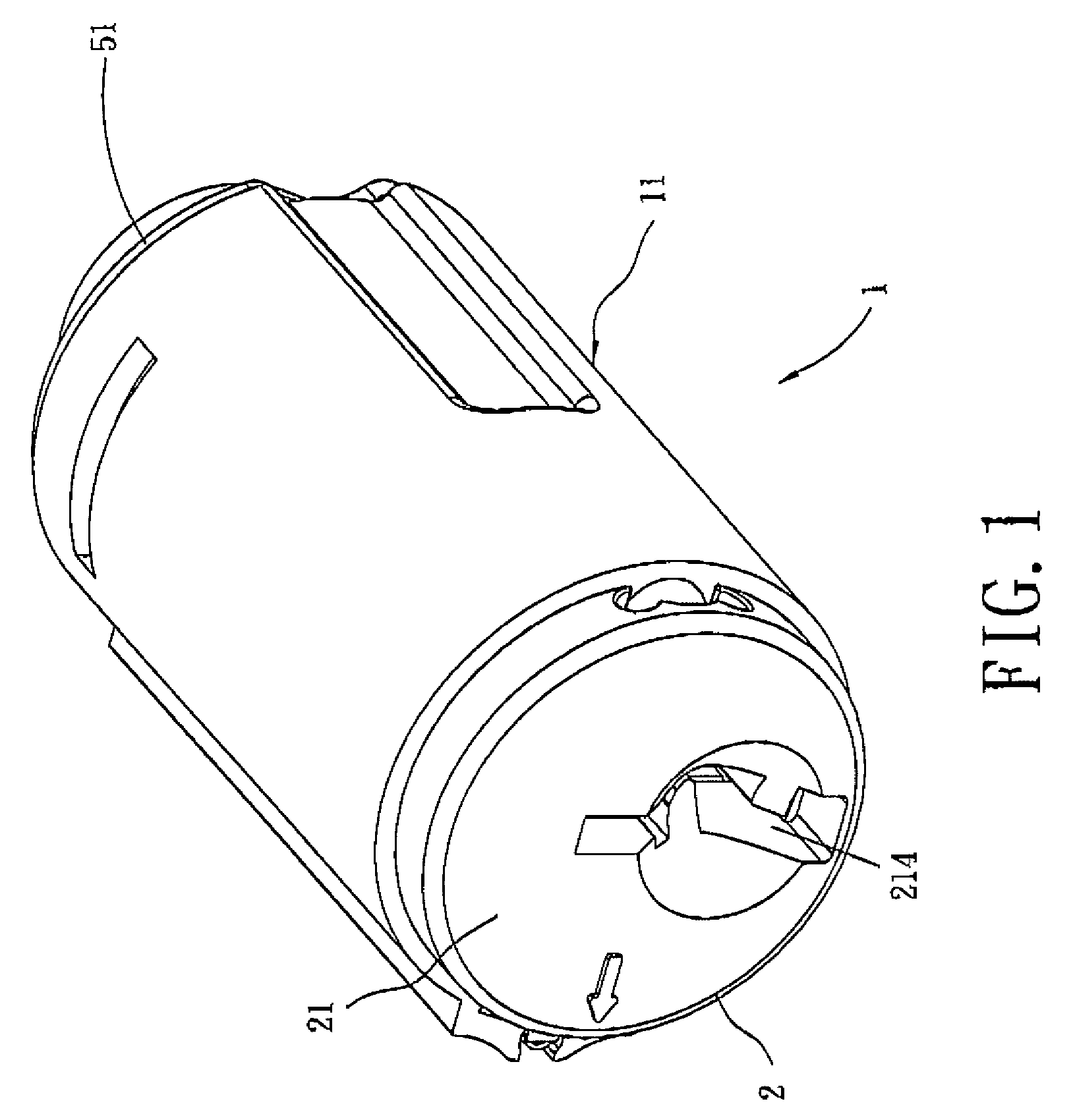
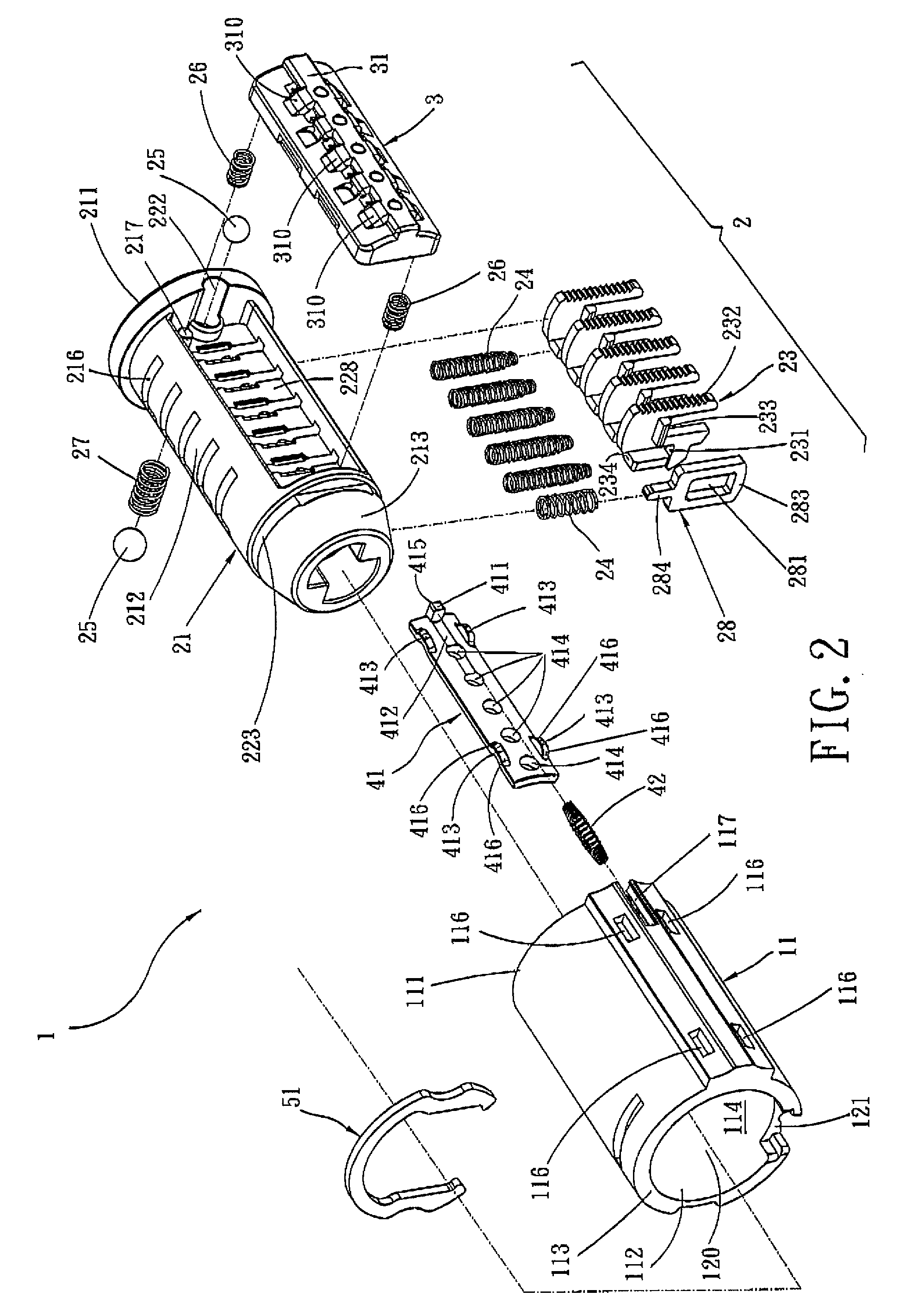
Re-keyable cylinder lock
A re-keyable cylinder lock has a control member to permit or restrict transverse movement of a re-keying unit. The control member is movable axially between first and second positions and transversely to a third position from the second position. In the third position, the re-keying unit moves transversely and disengages from first tumbler pieces. A limit member is provided to prevent the control member from moving axially when no right key is inserted into a plug. A security arm is connected to the control member and is breakable so that destructive forces cannot reach the control member.
Owner:TONG LUNG METAL IND
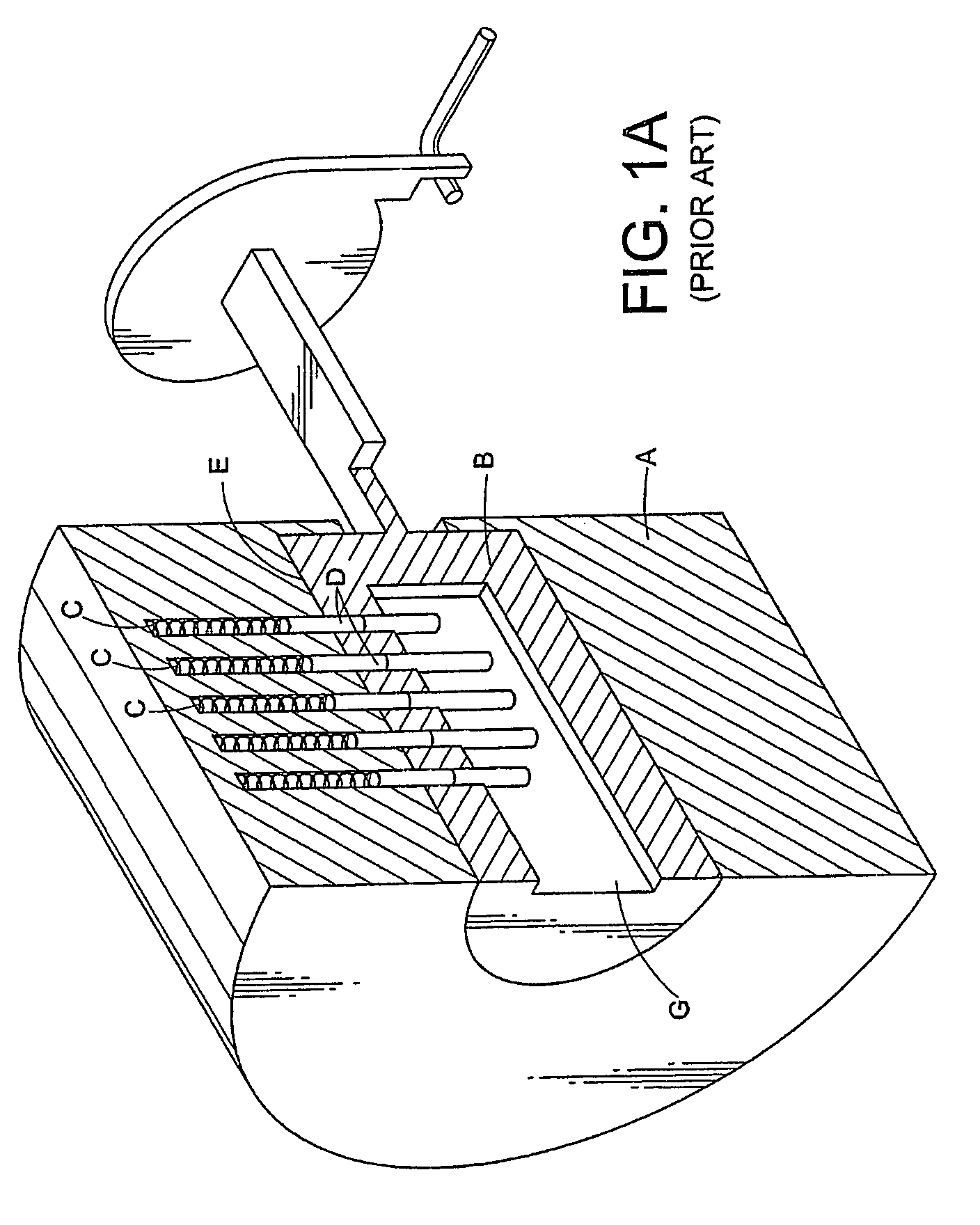
Pick-resistant wafer tumbler lock with sidebars
The invention provides a pick-resistant locking mechanism with wafer tumblers, sidebars and an interchangeable cylinder that allows re-keying of the lock. The sidebars have projections with beveled sides that engage with cavities in the lock shell when rotational torque is applied to the lock in the absence of the correct key. A sidebar of the lock contacts two, nonadjacent wafer tumblers. The wafer tumblers have indentations that engage cavities in the lock shell when rotational torque is applied during picking of the lock. Tolerance between sidebars and the lock shell is less than the tolerance between tumblers and the lock shell. The tumbler springs are not accessible from the keyway of the lock and are more powerful than the sidebar springs.
Owner:MASTER LOCK COMANY LLC
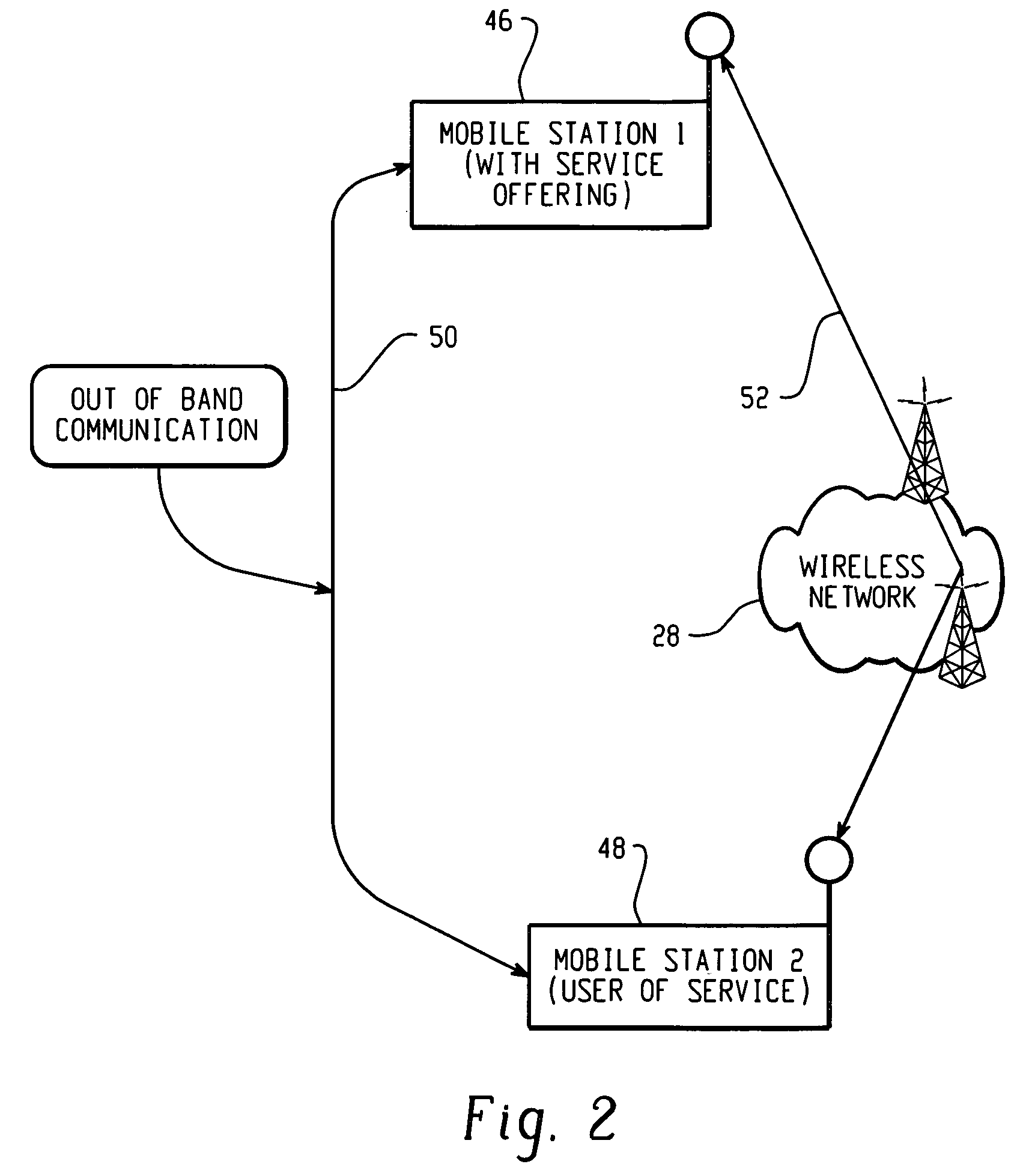
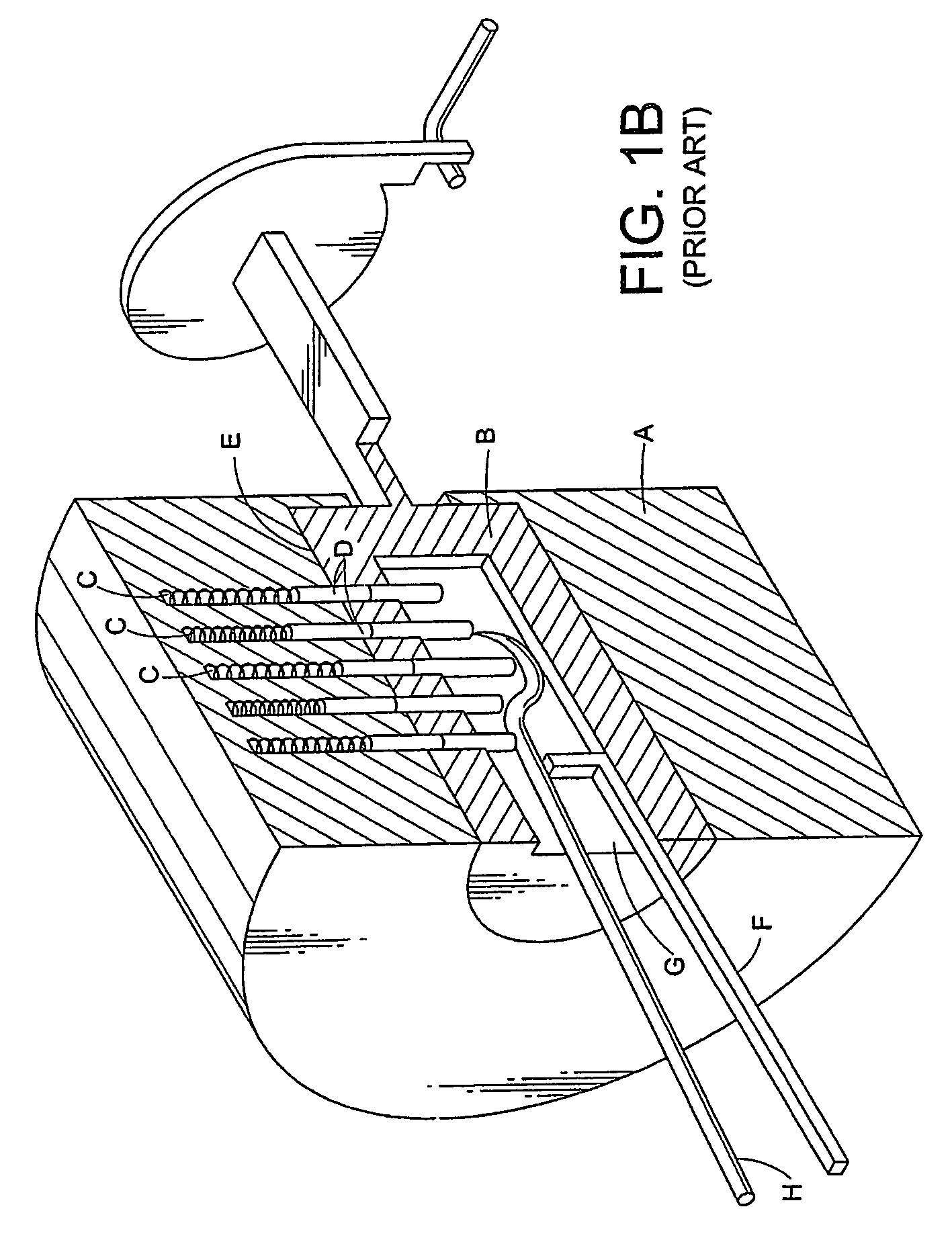
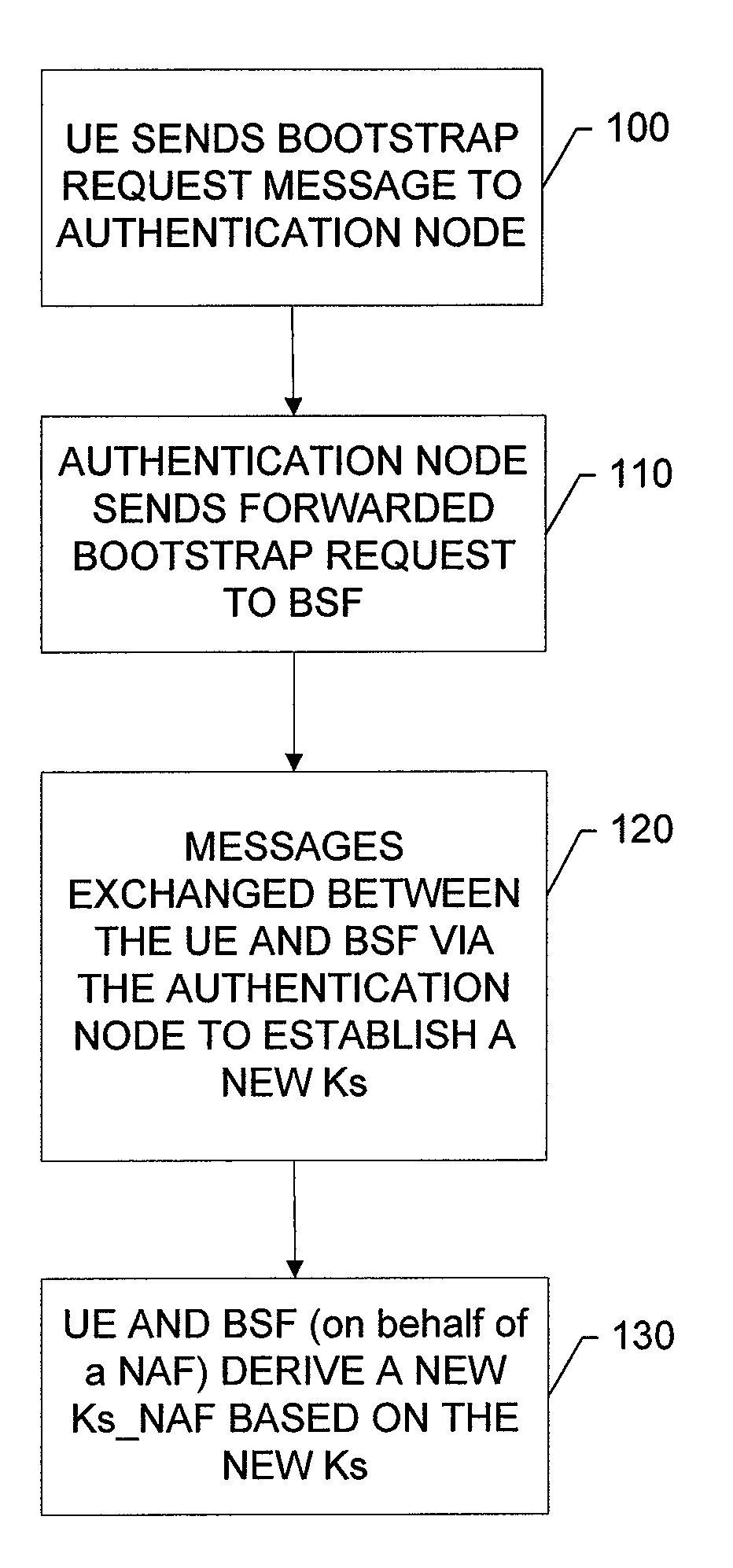
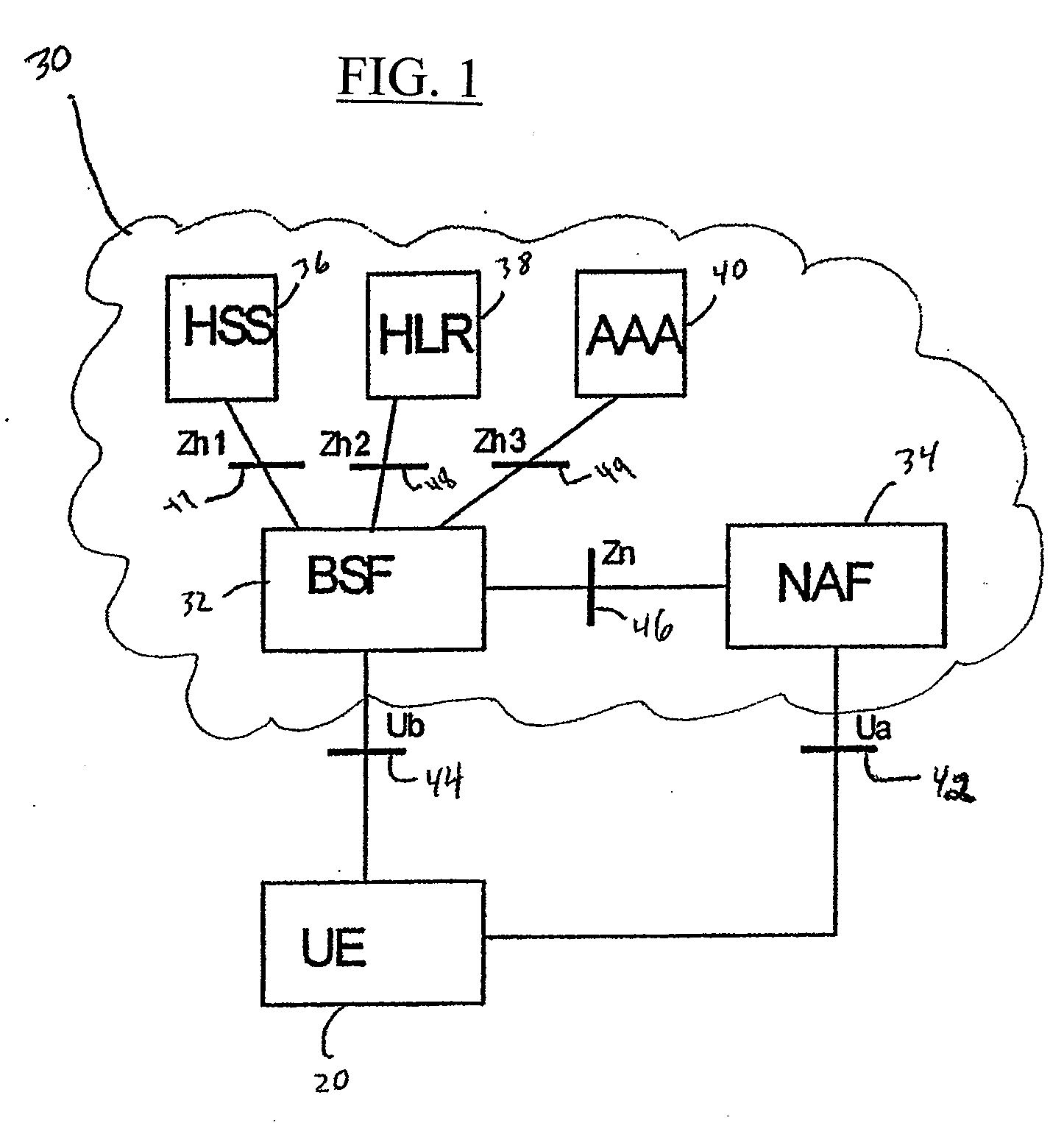
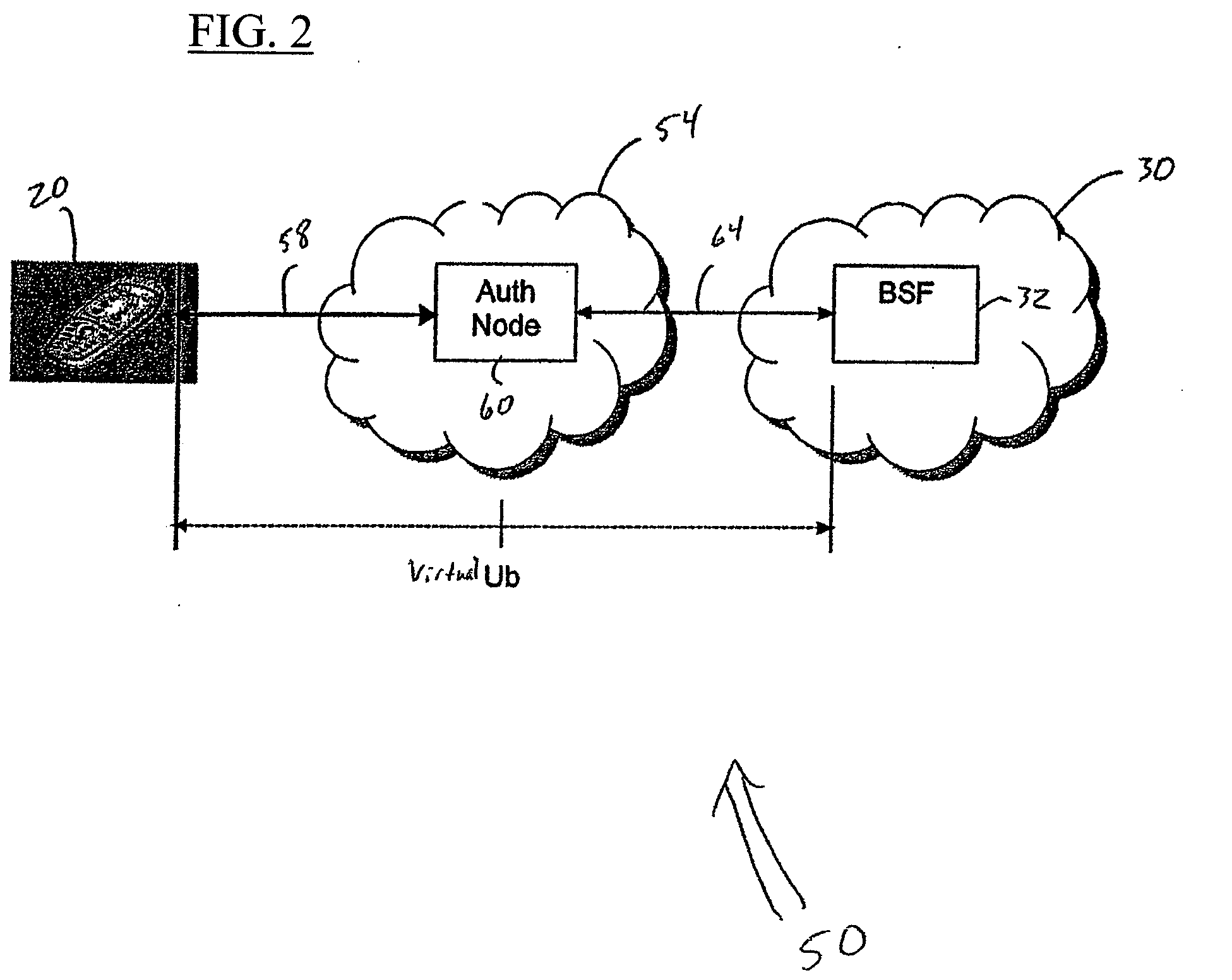
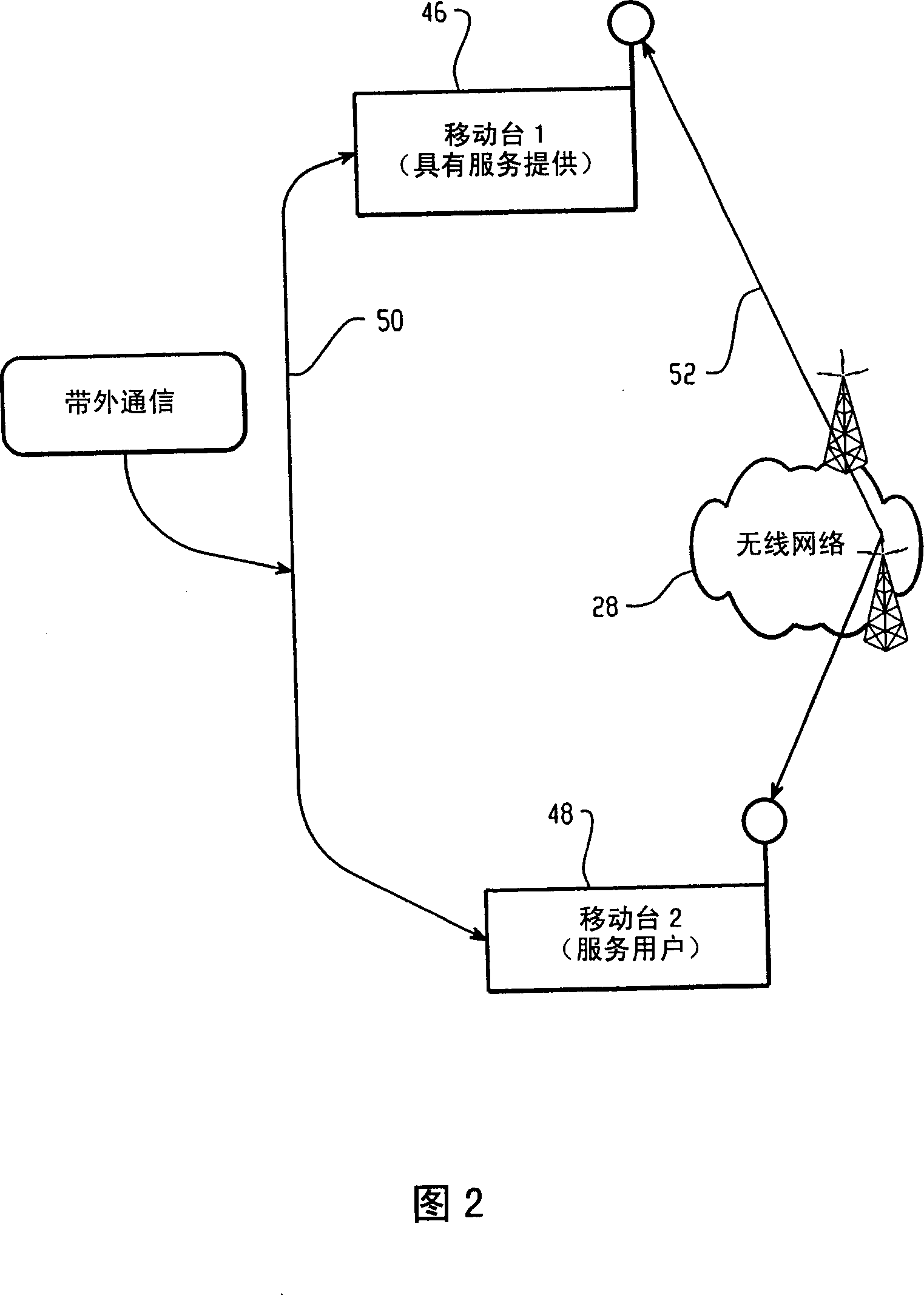
Re-Keying in a Generic Bootstrapping Architecture Following Handover of a Mobile Terminal
InactiveUS20070124587A1User identity/authority verificationSecurity arrangementGeneric Bootstrapping ArchitectureRe keying
An apparatus for re-keying a mobile terminal in a foreign network includes a processor. The processor is configured to receive, at the apparatus which is physically located in the foreign network, a request for re-keying from the mobile terminal in the foreign network. The processor is also configured to translate the request for transmission to a home network of the mobile terminal and to transmit the translated request to a bootstrapping server function of the home network.
Owner:NOKIA CORP
Re-keying data in place
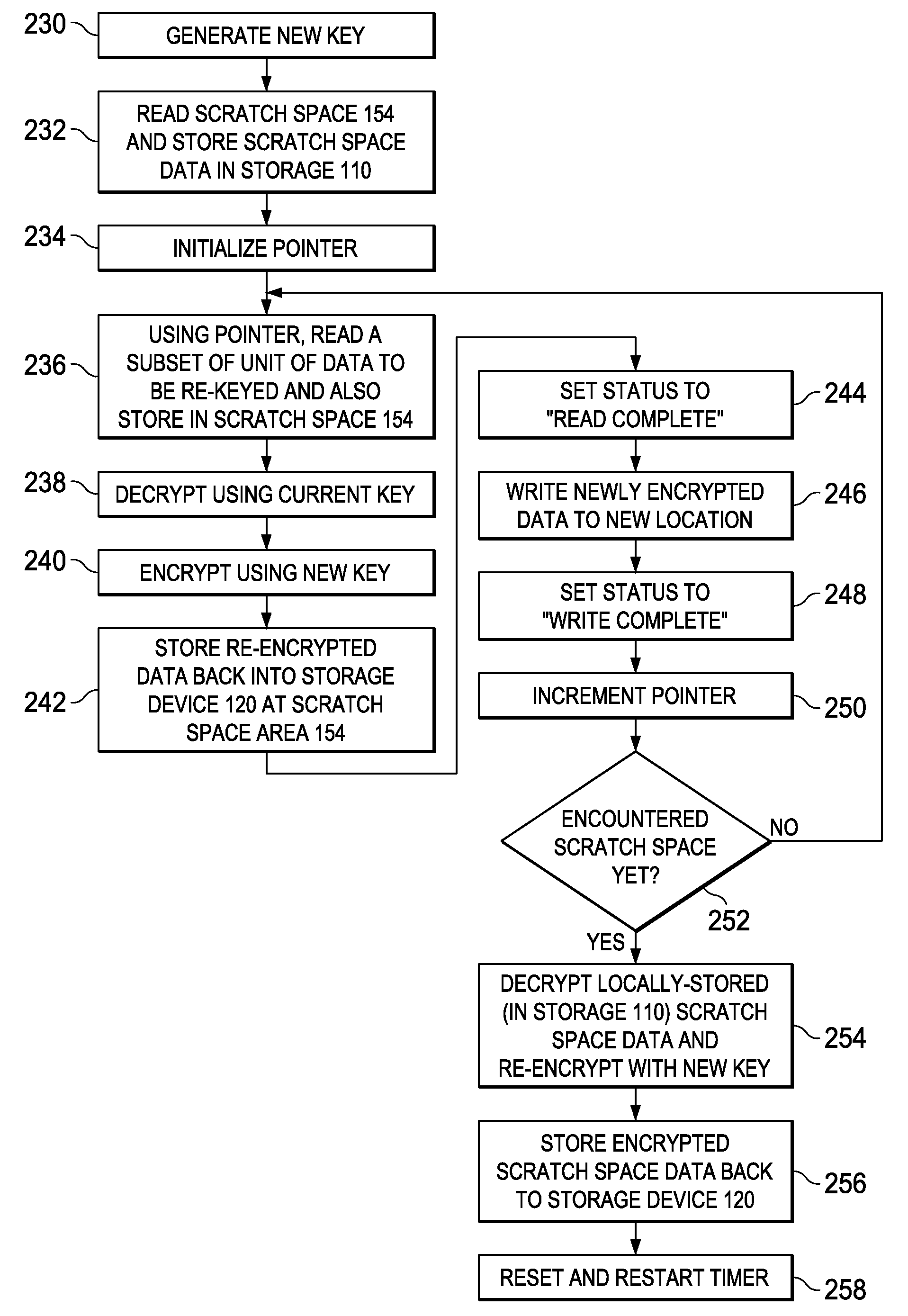
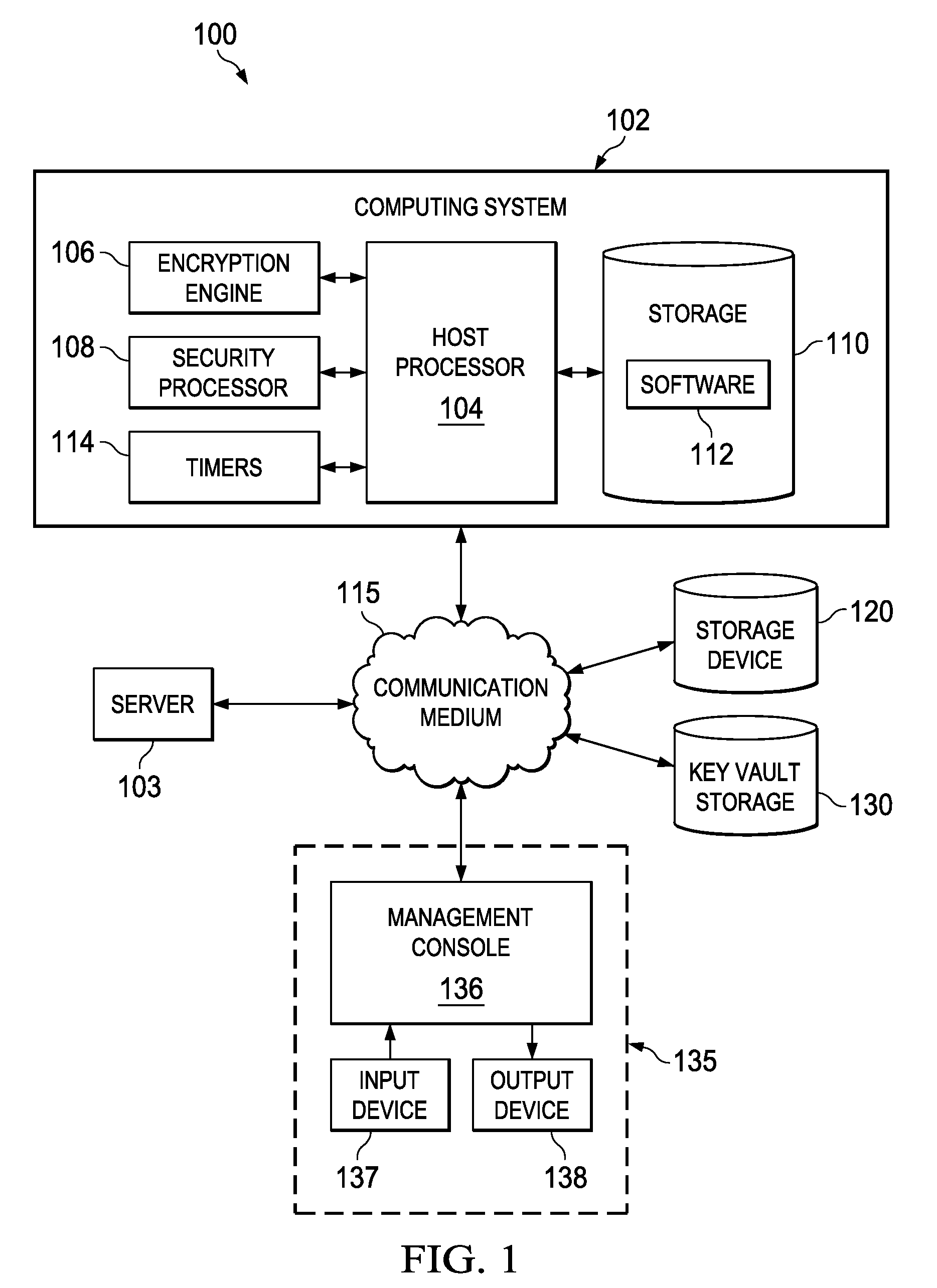
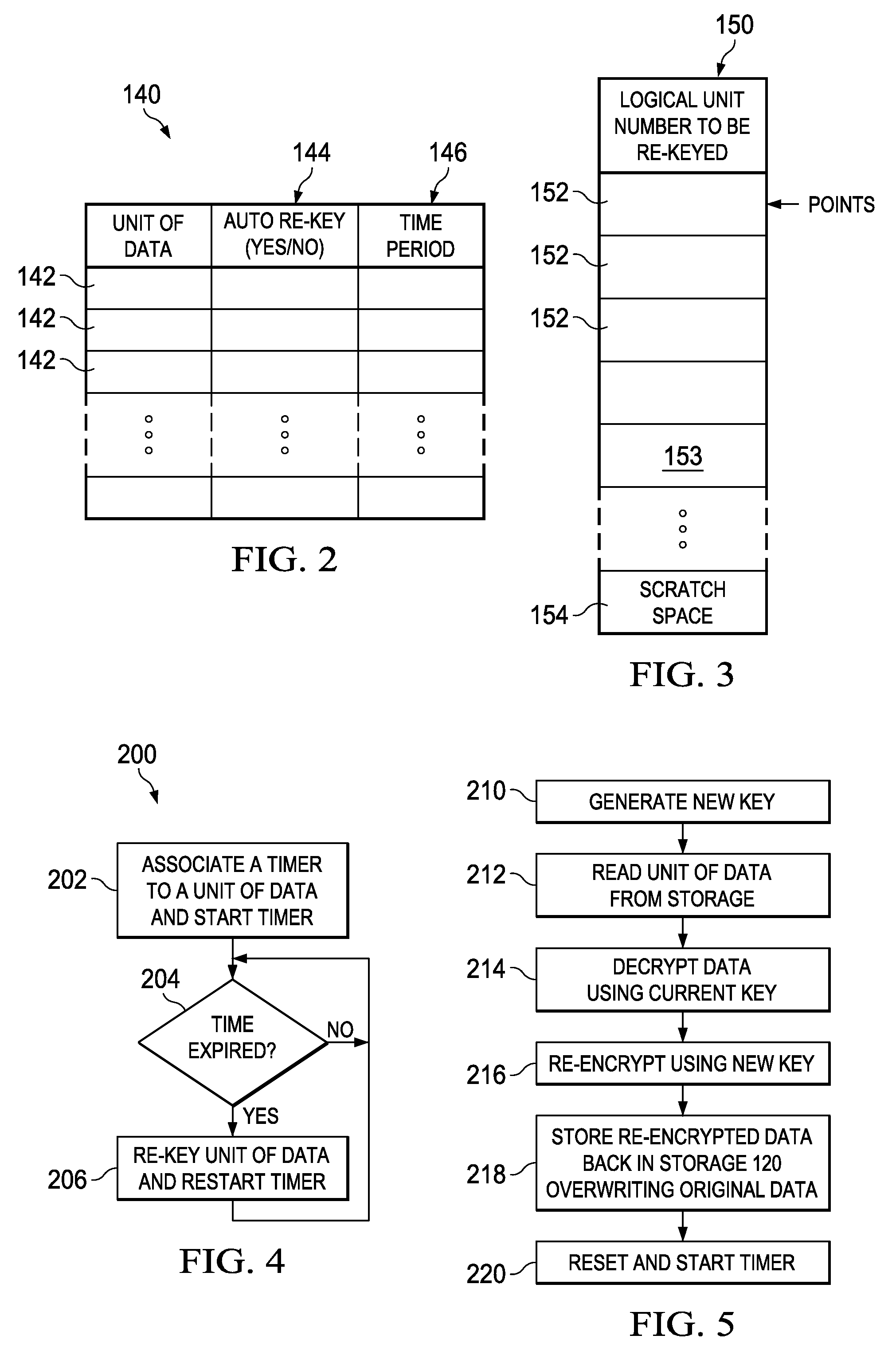
InactiveUS20110038477A1Digital data processing detailsUnauthorized memory use protectionTime segmentRe keying
A system comprises an encryption engine and a host processor coupled to the encryption engine. The host processor determines when a time period has expired for a unit of data. Upon determining that the time period has expired, the host processor causes the encryption engine to re-key the unit of data in place.
Owner:AVAGO TECH INT SALES PTE LTD
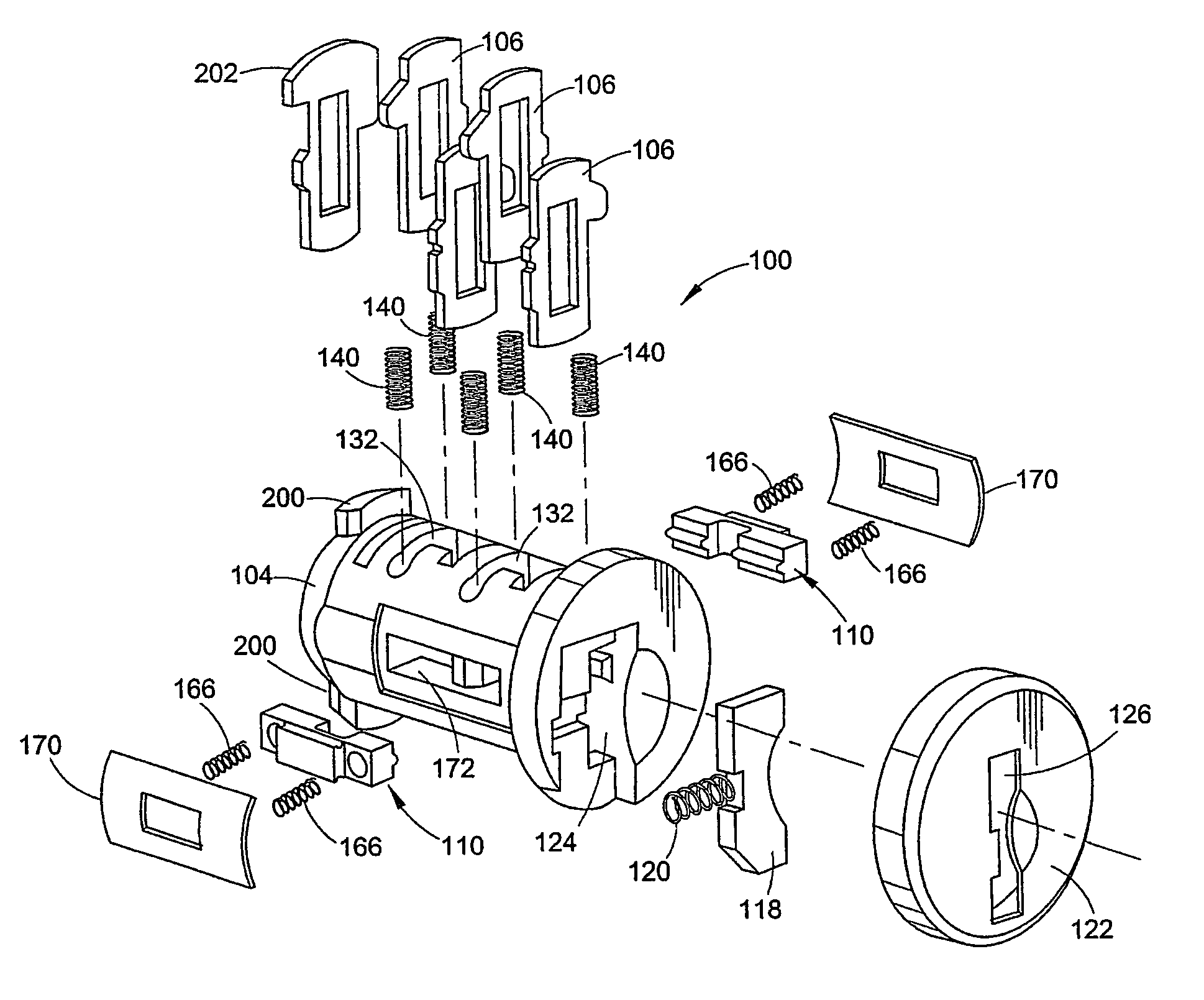
Re-keyable lock and method
A re-keyable lock and method. The lock has locked and unlocked positions and includes a housing and a cylinder rotatably supported in the housing. The lock includes a plurality of wafer tumblers resiliently supported in corresponding channels formed in the cylinder. Each wafer tumbler includes a rider element selectively engaged with a base element in first and second engagement positions, wherein the first engagement position corresponds to a first key and the second engagement position corresponds to a second key. The lock also includes a re-keying mechanism such as a re-keying tool which is inserted in a re-keying slot when the lock is in the unlocked position to disengage the rider element from the corresponding base element in the first engagement position and to re-engage the rider element to the base element in the second engagement position.
Owner:ASSA ABLOY AMERICAS RESIDENTIAL INC
Rapid-change lock
InactiveUS7533550B2Change positionWithout of assemblyKeysCylinder locksRe keyingMechanical engineering
A changeable lock assembly suitable for re-keying a lock without disassembly of the lock. The assembly includes a housing having a bore therein, and a plug rotatably mounted in the bore. The plug includes a longitudinal axis and a keyway. The keyway is adapted to receive at least a first user key and a second user key. The lock further includes a change member movable within the lock between a first position to a second position. The change member can move solely in response to operation of the second key. Thus, when the change member is in the first position, the first key operates the lock, and when the change member is in the second position, the first key does not operate the lock. The lock assembly can also employ a change tool that, when inserted into a change slot, can move a change ball from the second position back to the first position.
Owner:JANAKA PARTNERSHIP
Cylinder lock
A cylinder lock includes a lock housing receiving a plug assembly that has a key hole, tumbler pieces having respective toothed parts, and a re-keying unit. The re-keying unit has rotatable gear wheels engaged releasably with the respective toothed parts to reposition the respective tumbler pieces. The gear wheels disengage from the respective tooth parts by moving transversely of a longitudinal axis of the lock housing. Re-keying methods are also disclosed.
Owner:TONG LUNG METAL IND
Host based rekeying
ActiveUS9774445B1Improve system performanceImprove performanceKey distribution for secure communicationSecret communicationCiphertextClient-side
A system and method for re-keying ciphertext on a storage system is resident on a host / client communicating with a storage system. The generation of encryption keys and tracking which storage system blocks are encrypted with what keys remain with the security appliance or storage system, but the policy governing re-keying and initiating actions in accordance with that policy reside with the client / host.
Owner:NETWORK APPLIANCE INC
Pick-resistant wafer tumbler lock with sidebars
The invention provides a pick-resistant locking mechanism with wafer tumblers, sidebars and an interchangeable cylinder that allows re-keying of the lock. The sidebars have projections with beveled sides that engage with cavities in the lock shell when rotational torque is applied to the lock in the absence of the correct key. A sidebar of the lock contacts two, nonadjacent wafer tumblers. The wafer tumblers have indentations that engage cavities in the lock shell when rotational torque is applied during picking of the lock. Tolerance between sidebars and the lock shell is less than the tolerance between tumblers and the lock shell. The tumbler springs are not accessible from the keyway of the lock and are more powerful than the sidebar springs.
Owner:MASTER LOCK CO INC
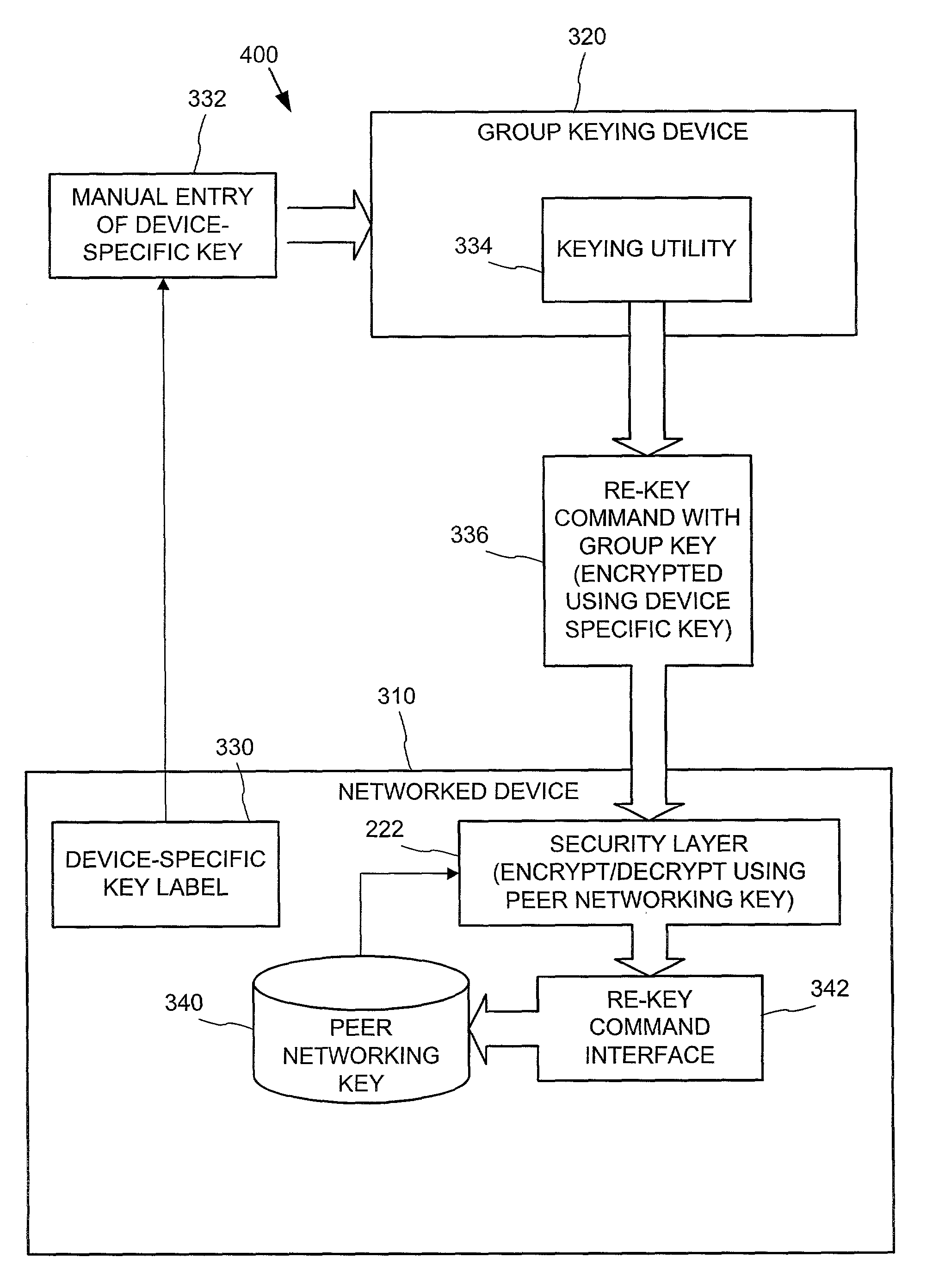
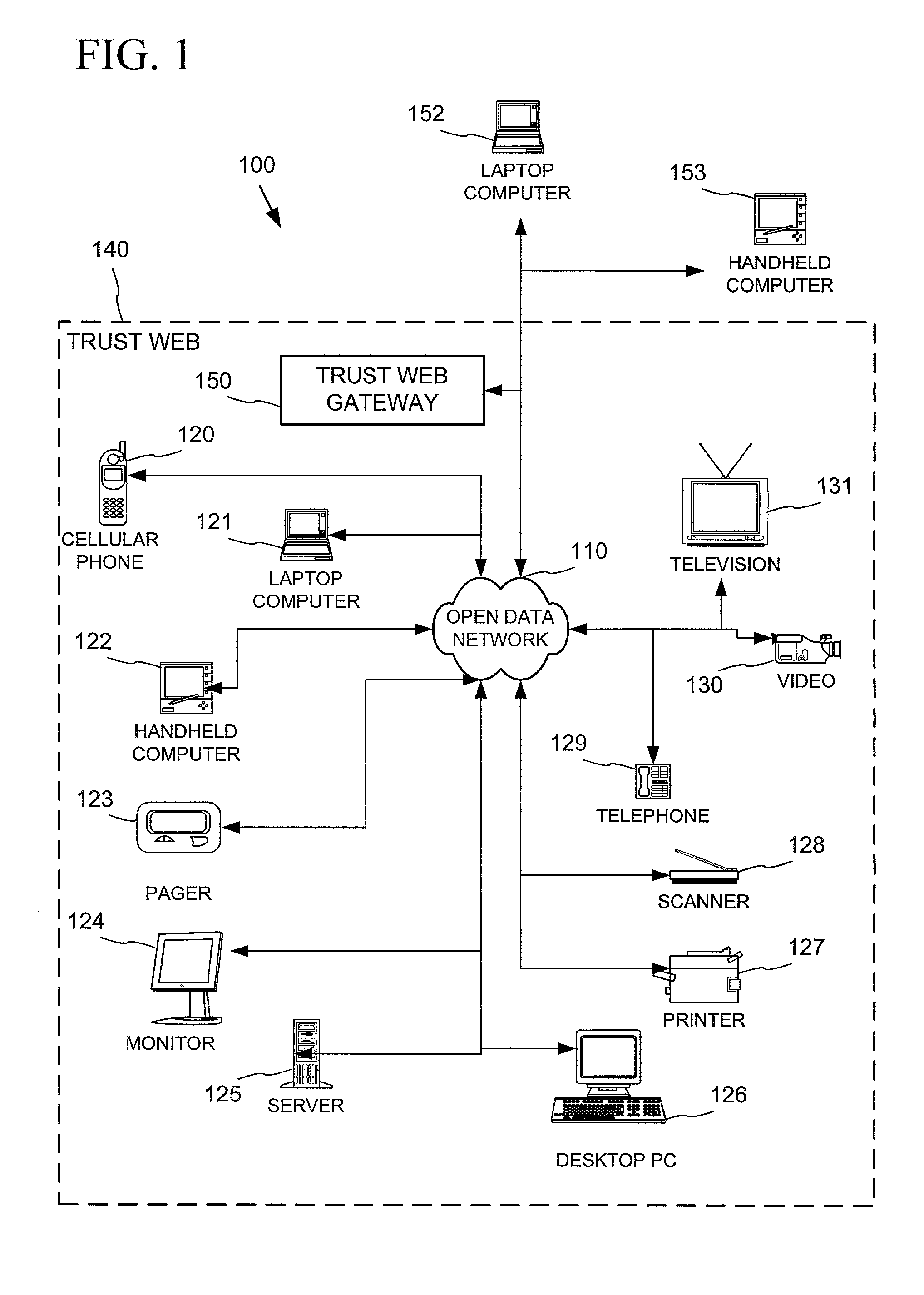
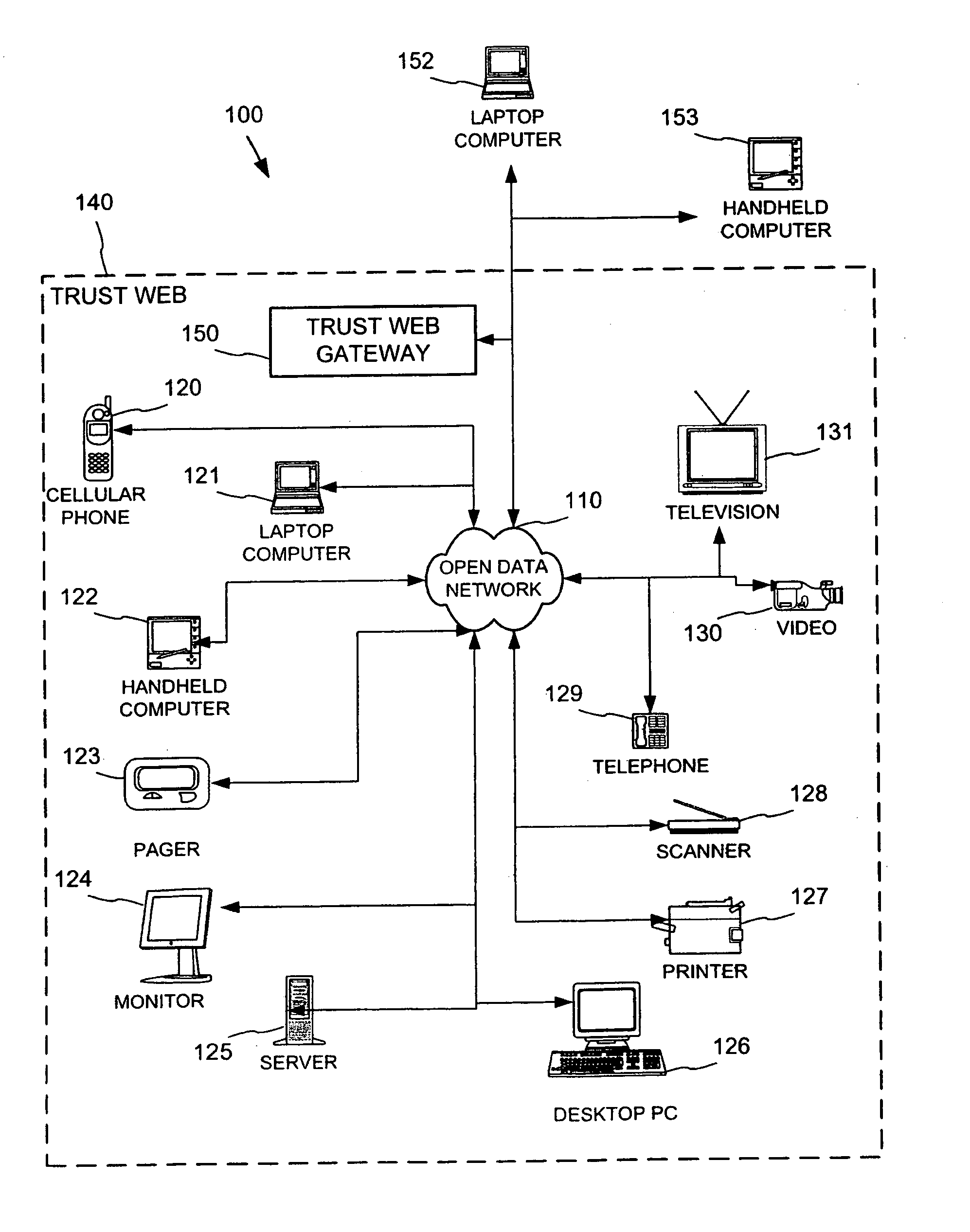
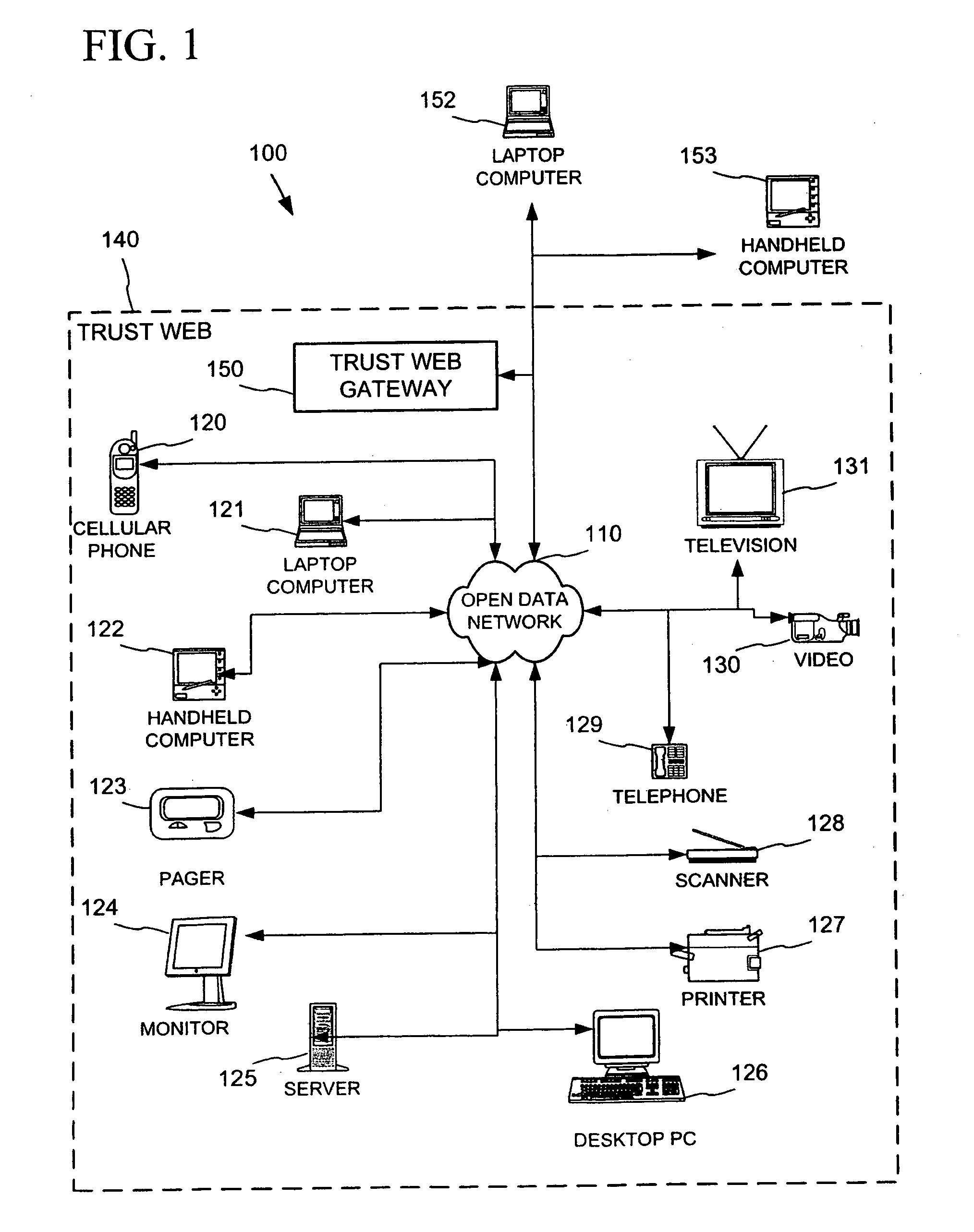
Establishing secure peer networking in trust webs on open networks using shared secret device key
InactiveUS20050286722A1CostInexpensive and reliableData switching networksSecuring communicationRe keyingComputer security
A trust web keying process provides secure peer networking of computing devices on an open network. A device is initially keyed at distribution to an end user or installer with a device-specific cryptographic key, and programmed to respond only to peer networking communication secured using the device's key. The device-specific key is manually entered into a keying device that transmits a re-keying command secured with the device-specific key to the device for re-keying the device with a group cryptographic key. The device then securely peer networks with other devices also keyed with the group cryptographic key, forming a trust web. Guest devices can be securely peer networked with the trust web devices via a trust web gateway.
Owner:MICROSOFT TECH LICENSING LLC
Cylinder lock
A cylinder lock includes a lock housing receiving a plug assembly that has a key hole, tumbler pieces having respective toothed parts, and a re-keying unit. The re-keying unit has rotatable gear wheels engaged releasably with the respective toothed parts to reposition the respective tumbler pieces. The gear wheels disengage from the respective tooth parts by moving transversely of a longitudinal axis of the lock housing. Re-keying methods are also disclosed.
Owner:TONG LUNG METAL IND
Kerberized handover keying
ActiveUS8332923B2Key distribution for secure communicationDigital data processing detailsSecurity associationOperation mode
A media-independent handover key management architecture is disclosed that uses Kerberos for secure key distribution among a server, an authenticator, and a mobile node. In the preferred embodiments, signaling for key distribution is based on re-keying and is decoupled from re-authentication that requires EAP (Extensible Authentication Protocol) and AAA (Authentication, Authorization and Accounting) signaling similar to initial network access authentication. In this framework, the mobile node is able to obtain master session keys required for dynamically establishing the security associations with a set of authenticators without communicating with them before handover. By separating re-key operation from re-authentication, the proposed architecture is more optimized for a proactive mode of operation. It can also be optimized for reactive mode of operation by reversing the key distribution roles between the mobile node and the target access node.
Owner:TELCORDIA TECHNOLOGIES INC +1
Programmable lock having incidental change control
InactiveUS20080276675A1Elimination and reduction of incidentalElimination and reduction of and accidental re-keyingCylinder locksEngineeringChange control
A key-operated cylinder lock for operating a bolt or a latch, that can be programmed for use with one of a plurality of user keys without disassembling the lock or replacing the tumblers, with reduction or elimination of incidental or accidental re-keying of the lock. The lock has a rotating plug having one or more retainer cavities formed into the periphery, and lock configuration change balls, movable within the lock between a first position within a driver chamber and a second position within a corresponding retainer cavity when the plug is in a programming position. The positioning of the change balls within either the pin chambers or the retainer cavities determines the key configuration that can operate the lock. The lock employs a means for isolating selectively the retainer cavities from the corresponding driver chambers when the plug is in the programming position, to prevent incidental or accidental movement of the change members from the driver chamber into the retainer cavities.
Owner:JANAKA PARTNERSHIP
Systems and methods to securely generate shared keys
ActiveCN1969501AKey distribution for secure communicationMultiple keys/algorithms usageMaster keyRe keying
A method for secure bidirectional communication between two systems is described. A first key pair and a second key pair are generated, the latter including a second public key that is generated based upon a shared secret. First and second public keys are sent to a second system, and third and fourth public keys are received from the second system. The fourth public key is generated based upon the shared secret. A master key for encrypting messages is calculated based upon a first private key, a second private key, the third public key and the fourth public key. For re-keying, a new second key pair having a new second public key and a new second private key is generated, and a new fourth public key is received. A new master key is calculated using elliptic curve calculations using the new second private key and the new fourth public key.
Owner:RES IN MOTION LTD
Re-keyable cylinder lock
A re-keyable cylinder lock has a control member to permit or restrict transverse movement of a re-keying unit. The control member is movable axially between first and second positions and transversely to a third position from the second position. In the third position, the re-keying unit moves transversely and disengages from first tumbler pieces. A limit member is provided to prevent the control member from moving axially when no right key is inserted into a plug. A security arm is connected to the control member and is breakable so that destructive forces cannot reach the control member.
Owner:TONG LUNG METAL IND
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com