Systems and methods to securely generate shared keys
A public key and shared secret technology, which is applied in the field of systems and methods for safely generating shared keys, can solve the problems of not dealing with mobile device requirements, not dealing with confidentiality requirements, and limited implementation methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
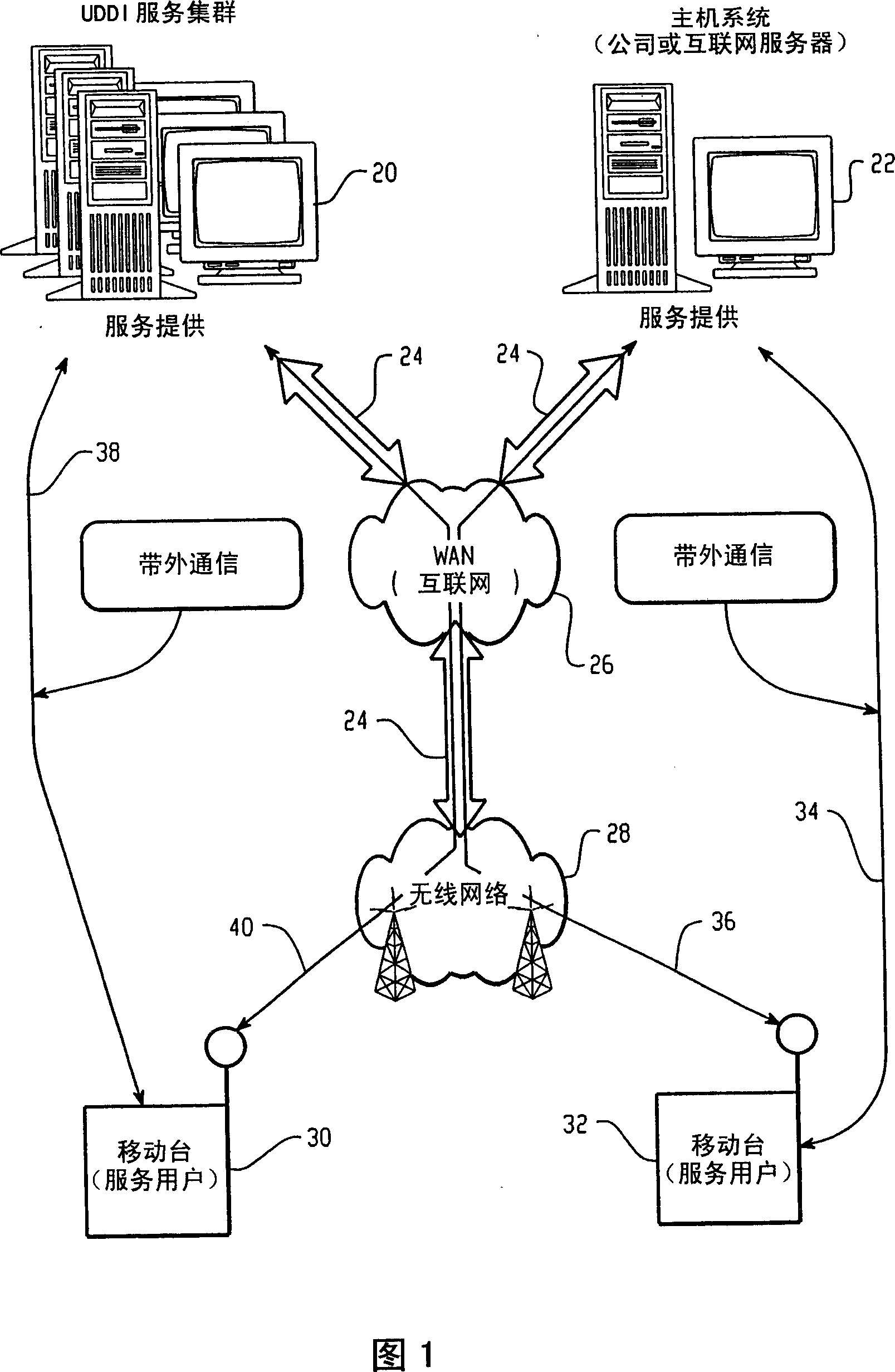
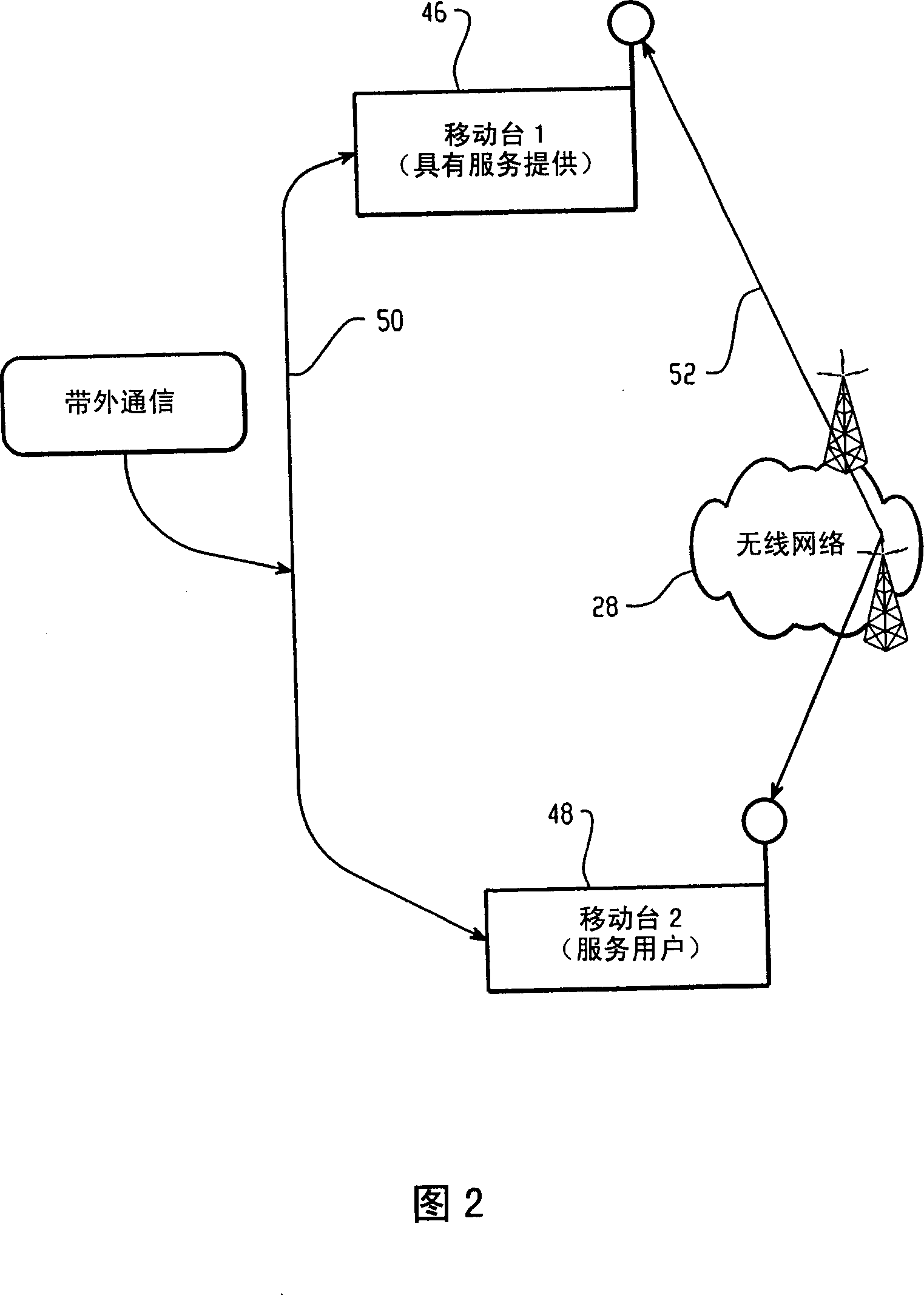
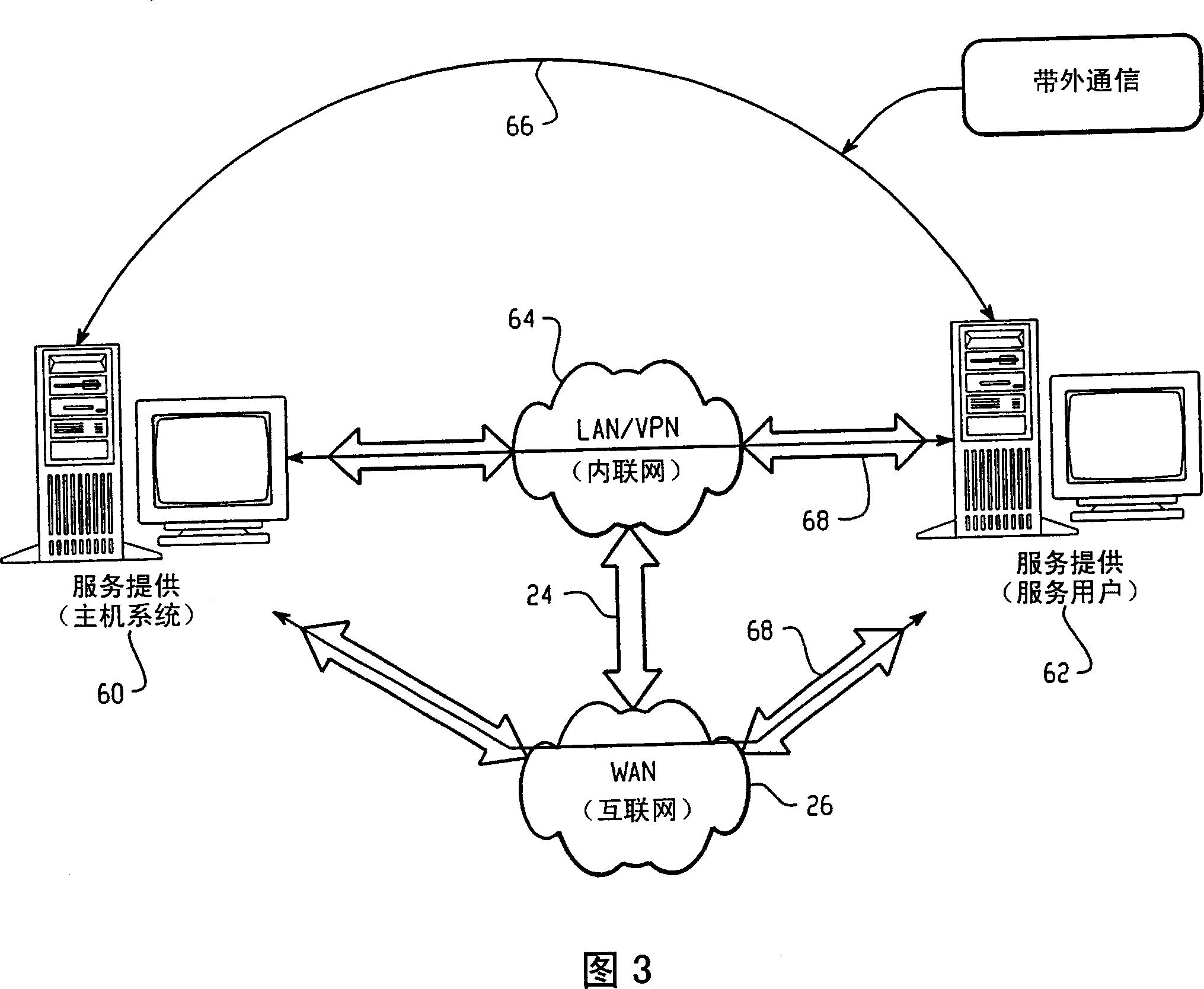
[0014] Referring to Figure 1, a block diagram of a first example communication system between fixed and wireless systems is shown. The overall cable diagram shows a network environment using the present invention. The figure illustrates an example embodiment of the invention and focuses on a network topology including wireless mobile devices. In this figure there are systems 20 and 22 that provide the service, and systems 30 and 32 that consume the service. There are one or more networks between the service provider (also referred to herein as a service provider) and the service user, and one or more connections enabling data flow between the two systems.
[0015] Turning now to FIG. 1, the service provider 20 or 22 may be any number of possible computers that provide services to users. For those skilled in the art, some well-known service providers may be computers on the Internet within an Internet Service Provider (ISP) or Application Service Provider (ASP). Service prov...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com