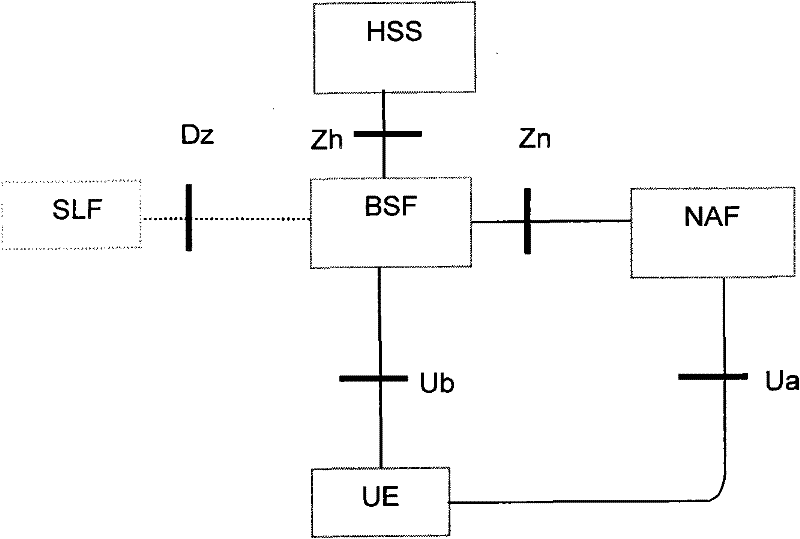
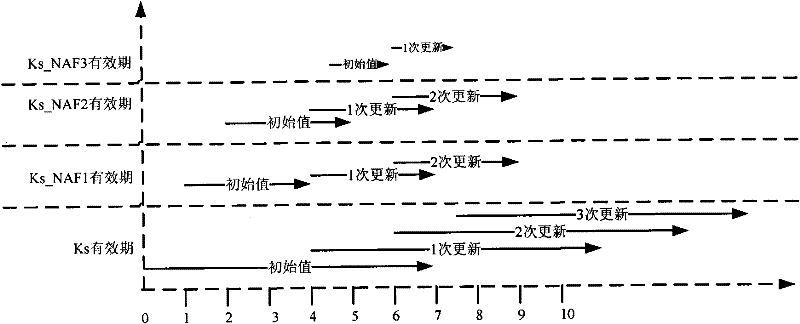
Method, device and system for updating key of general guide architecture
A general guidance architecture and key update technology, applied in security devices, wireless communications, electrical components, etc., can solve the problems of continuous update of validity period, frequent update of Ks_NAF, etc., and achieve the effect of avoiding frequent updates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0064] Figure 4 It is a flowchart of a GBA key update method according to an embodiment of the present invention. Such as Figure 4 As shown, this embodiment includes:
[0065] Step S102: receiving a Ks_NAF acquisition request;
[0066] Step S104: Obtain key parameters, and generate Ks_NAF according to Ks_NAF=KDF(Ks, preset character string, RAND, IMPI, NAF_Id, key parameters);
[0067] Step S106: save and return Ks_NAF and key parameters;
[0068] In this embodiment, the key parameter may be Ks_NAF validity period or a random number. The aforementioned preset character string may be "gba-me" or "gba-u".
[0069] 1. When the key parameter is the validity period of Ks_NAF, this embodiment specifically includes:
[0070] Step S112: receiving Ks_NAF acquisition request;
[0071] Step S114: Generate Ks_NAF valid period, generate Ks_NAF according to Ks_NAF valid period and pre-stored valid Ks, wherein, Ks_NAF=KDF(Ks, "gba-me", RAND, IMPI, NAF_Id, Ks_NAF valid period);
[0...
Embodiment 2
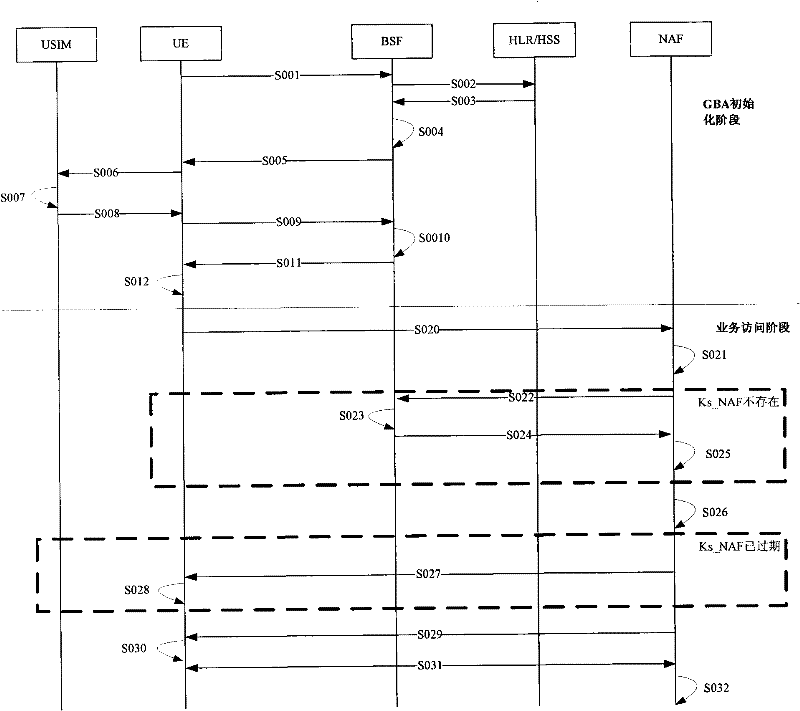
[0085] Most of the processes in Embodiment 1 are completed in BSF. This embodiment will describe the present invention from the perspective of the entire GBA architecture. Figure 5 It is a flow chart of the GBA key update method in Embodiment 2 of the present invention. Such as Figure 5 As shown, this embodiment includes:
[0086] Step S202: when the UE needs to access the service platform NAF, send the B-TID to the NAF;
[0087] Step S204: NAF locally inquires whether there is Ks_NAF according to B-TID, if it exists, execute step S206, otherwise, execute step S208;
[0088] Step S206: Check whether Ks_NAF is valid, if yes, execute step S220, otherwise, execute step S208, invalid Ks_NAF includes that Ks_NAF is not within the validity period or Ks_NAF needs to be updated according to the security policy of NAF;
[0089] Step S208: NAF sends Ks_NAF acquisition request to BSF according to B-TID, and BSF queries Ks according to B-TID;
[0090] Step S210: BSF judges whether ...
Embodiment 3
[0101] This embodiment provides a timestamp scheme, that is, the key parameter is the validity period of Ks_NAF. In this embodiment, the GBA initialization process is the same as that of the prior art, and the only change is the key update process. Figure 7 It is a flow chart of the GBA key update method in Embodiment 3 of the present invention. Such as Figure 7 As shown, this embodiment includes:
[0102] Step S302: When the UE needs to access the service platform NAF, send the B-TID to the NAF. In order to be compatible with the R8 version, you need to report your own GBA version number to NAF;
[0103] Step S304: NAF locally inquires whether Ks_NAF exists according to B-TID, if Ks_NAF does not exist, execute step S306, otherwise, execute step S320;
[0104] Step S306: NAF sends Ks_NAF acquisition request to BSF according to B-TID;
[0105] Step S308: BSF inquires whether there is a valid Ks according to the B-TID, if yes, execute step S310; otherwise, execute step S3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com