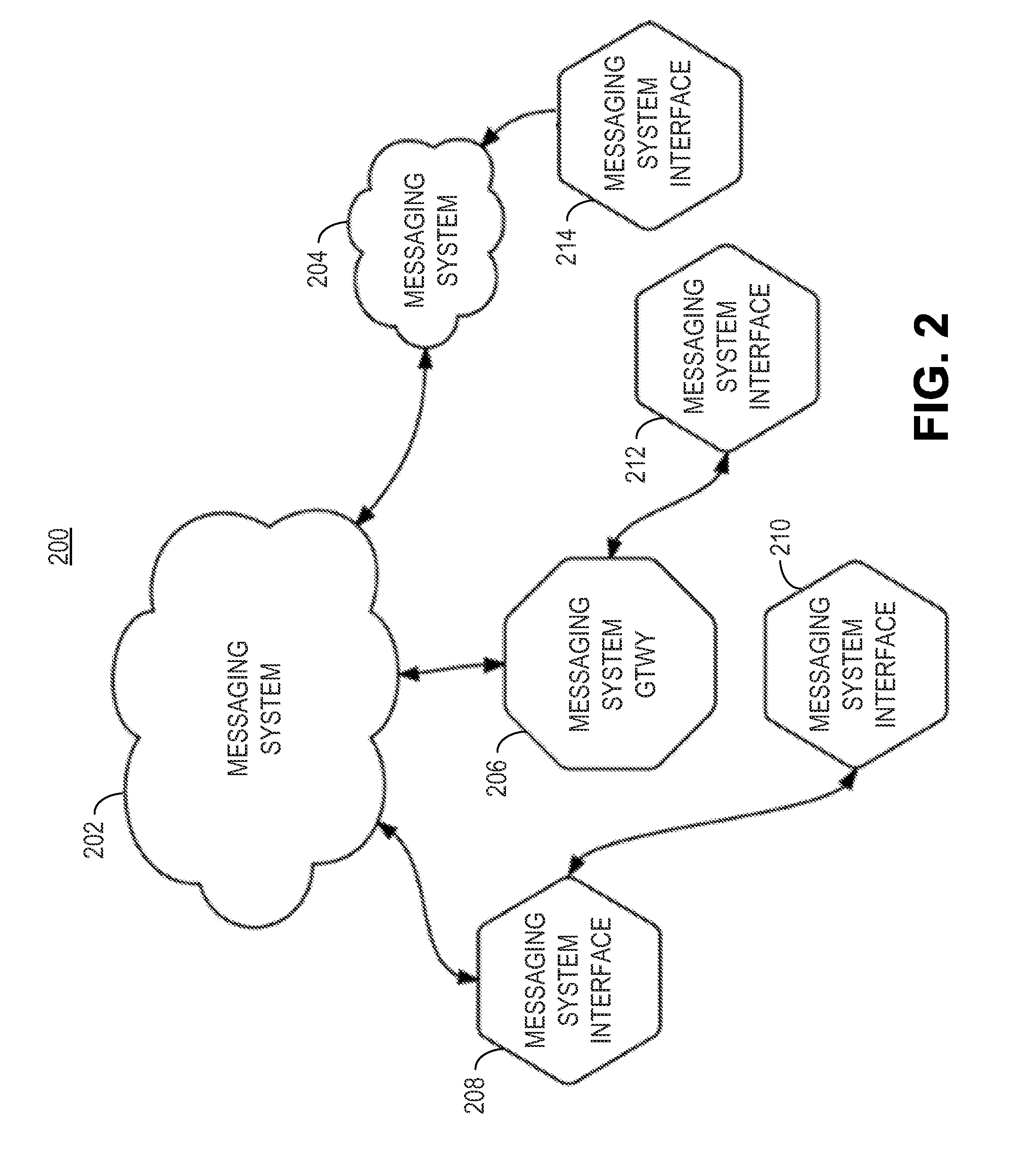
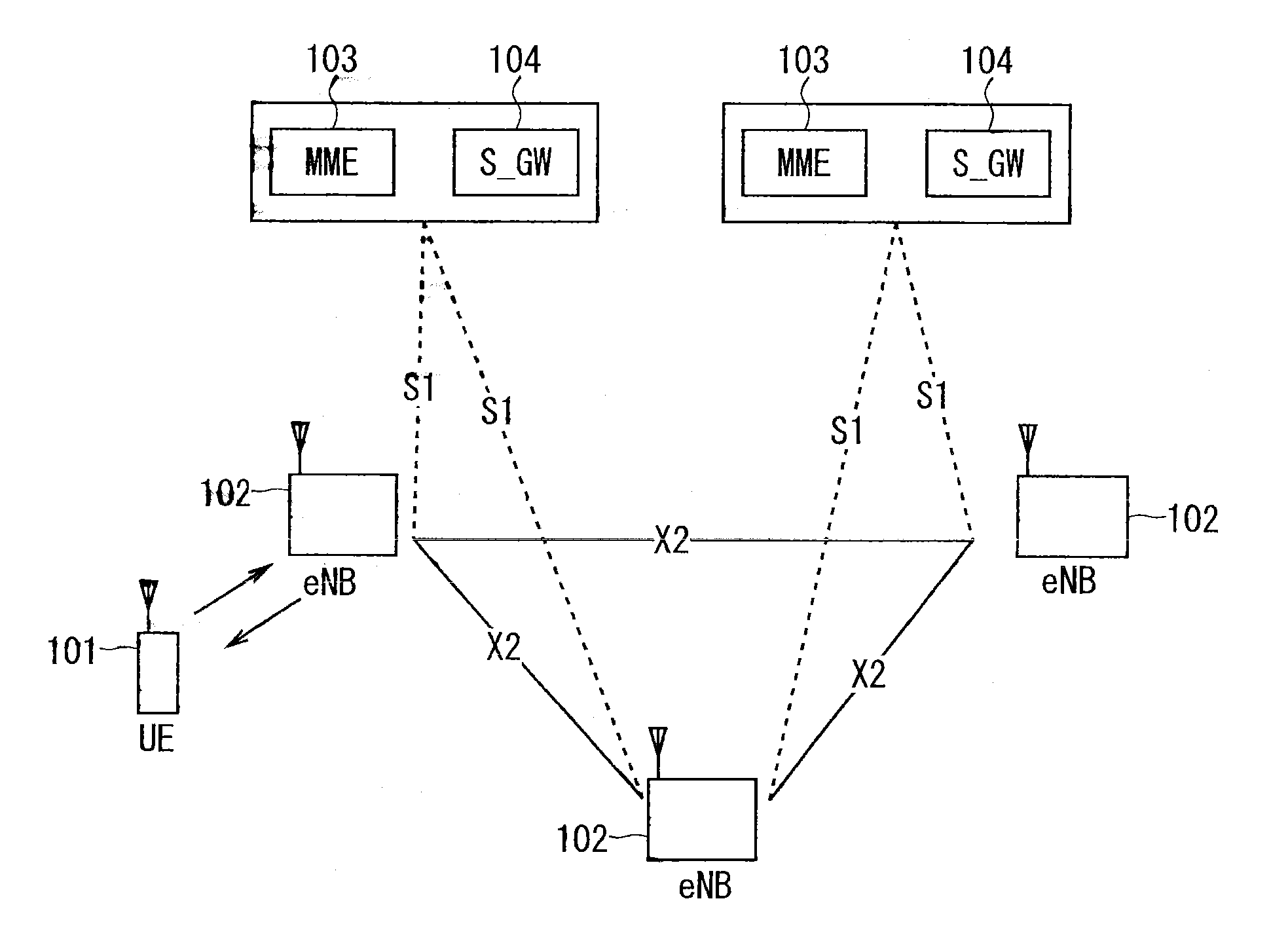
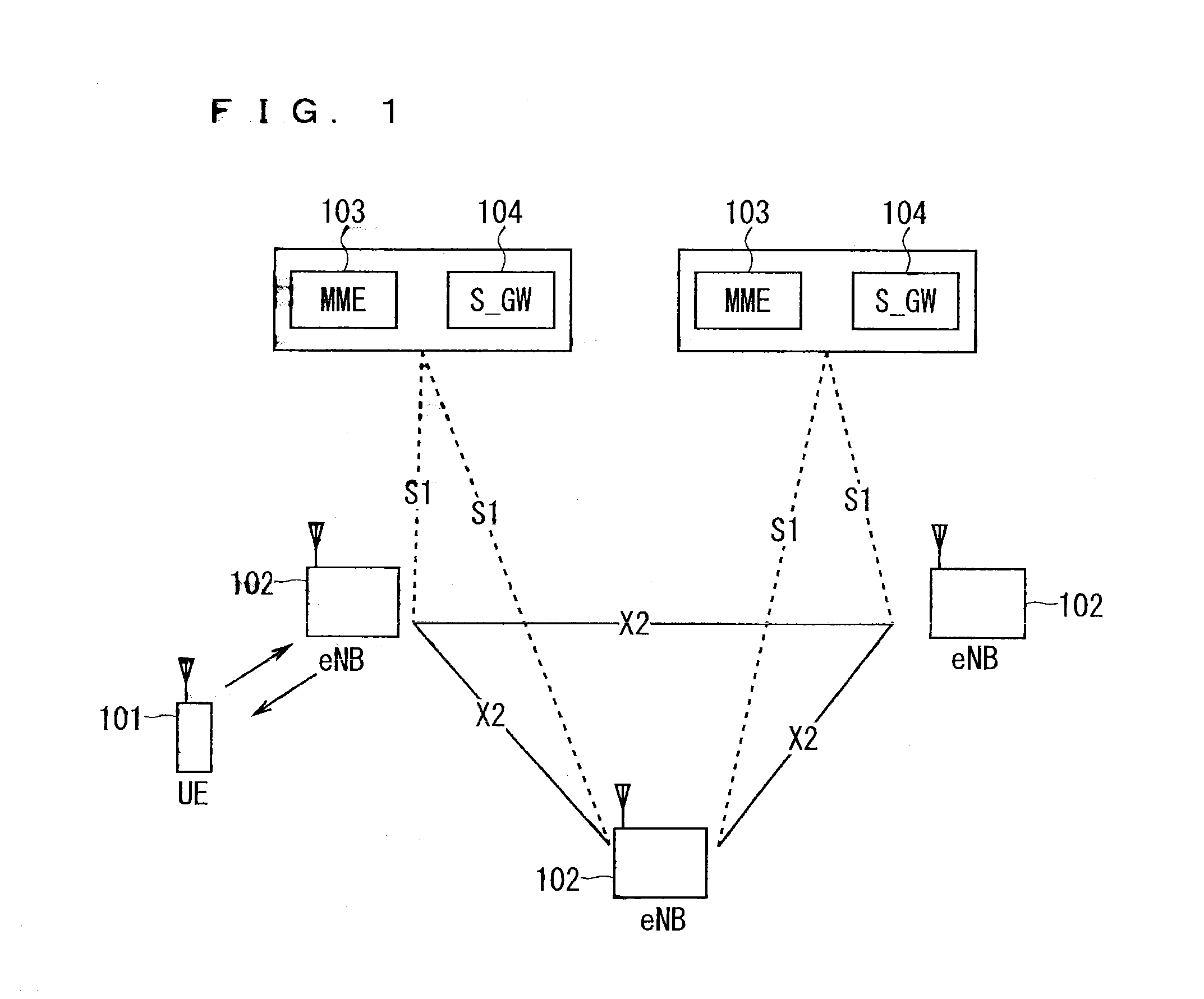
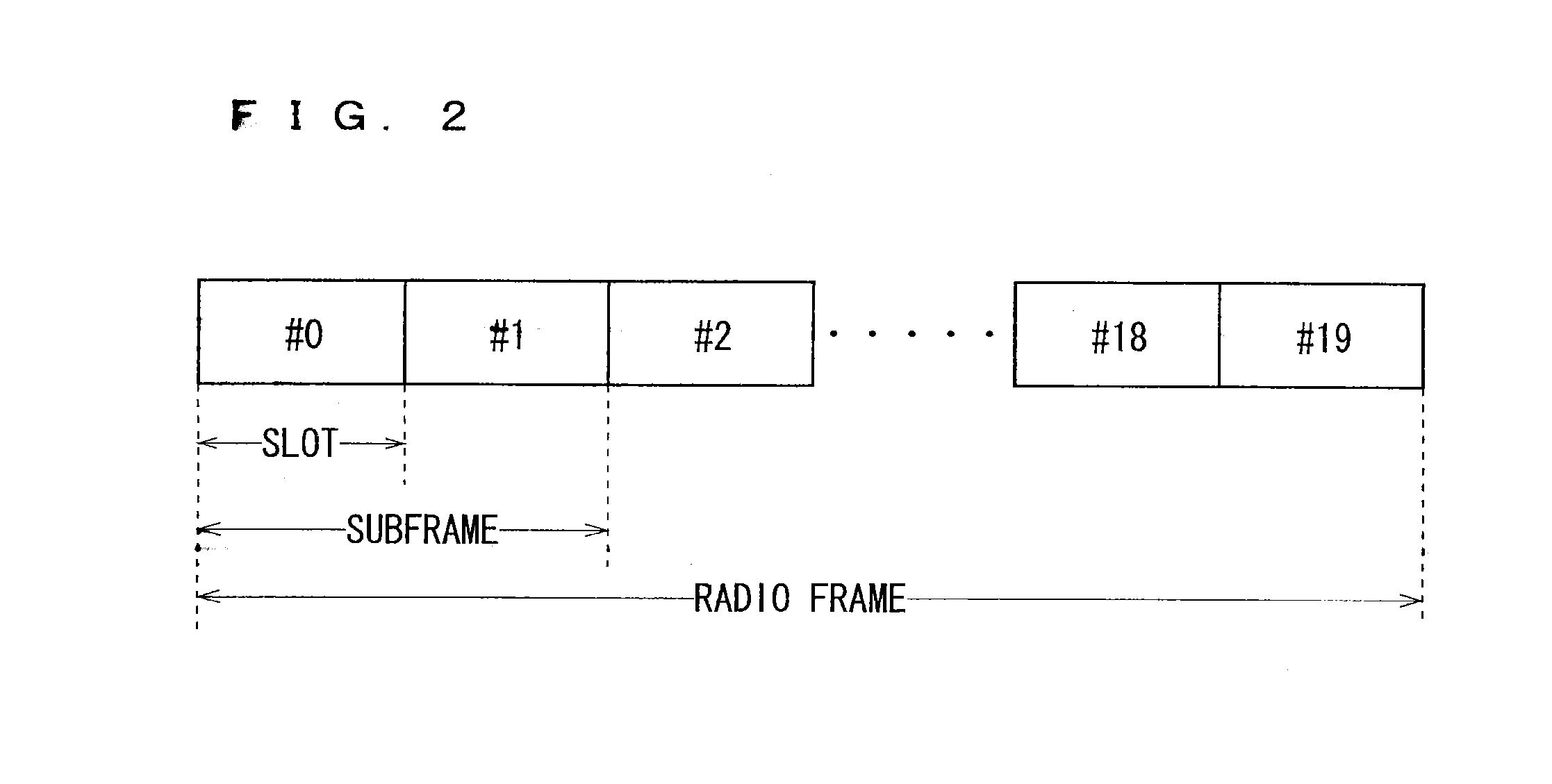
Patents
Literature
953 results about "Machine to machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
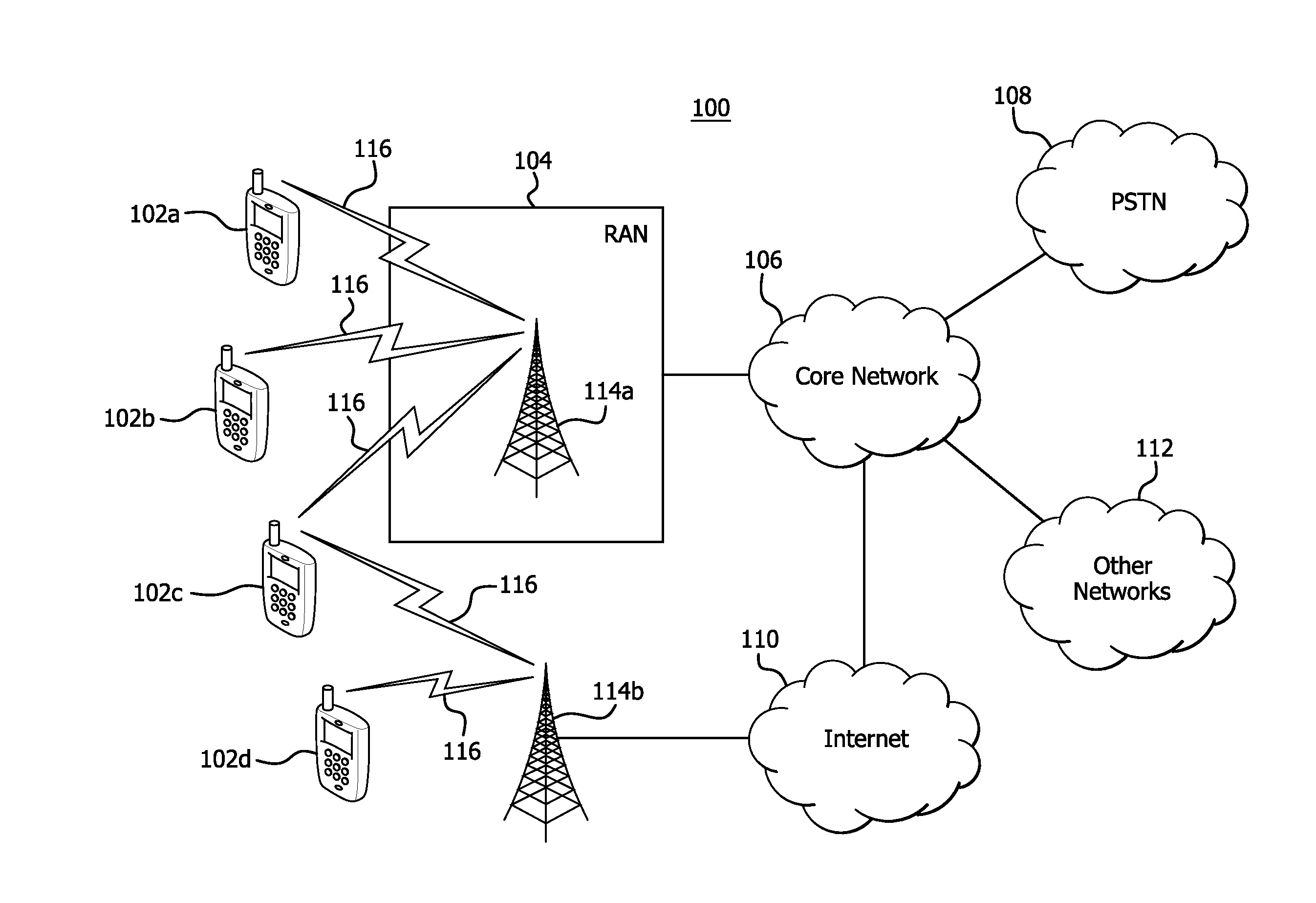
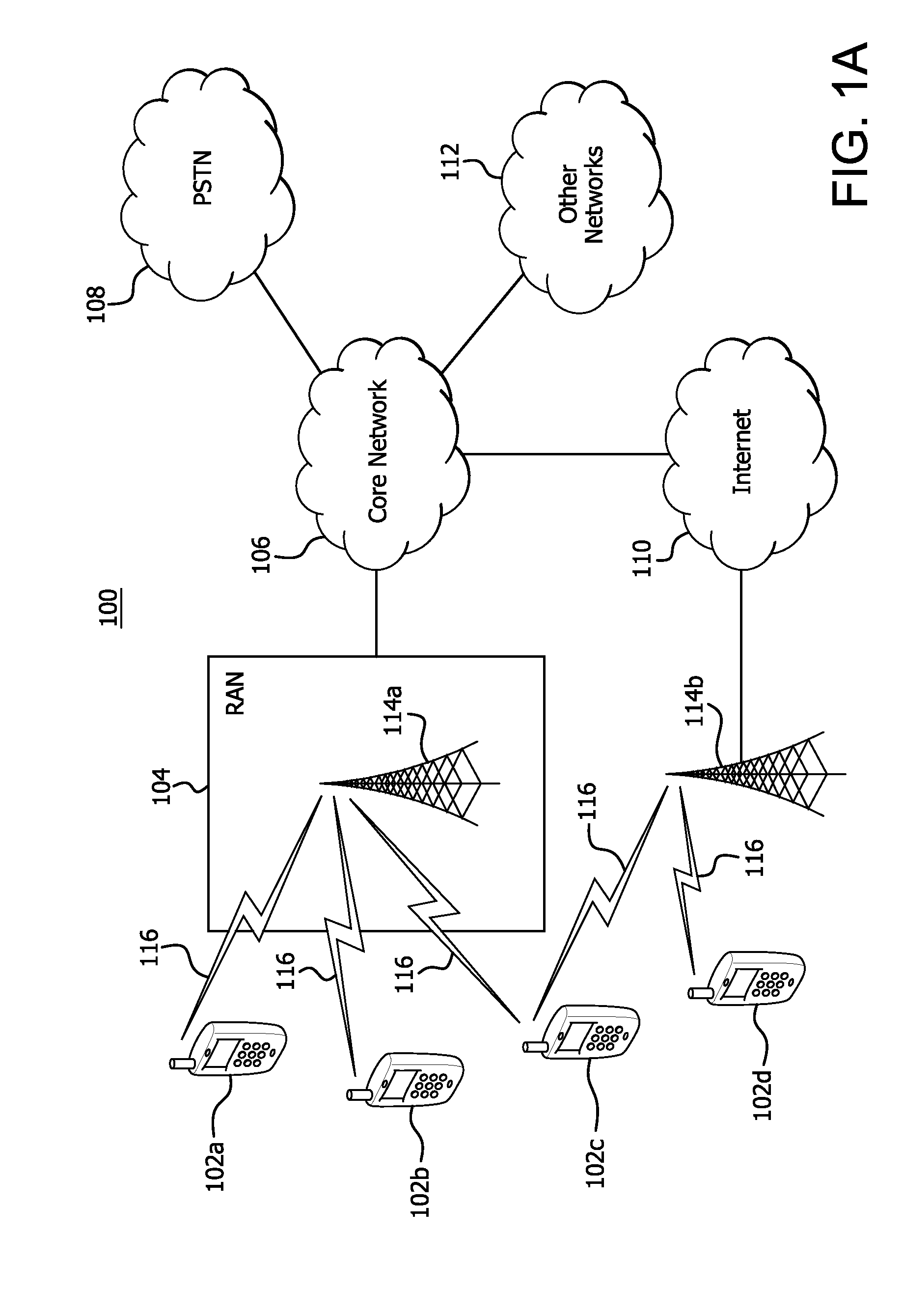
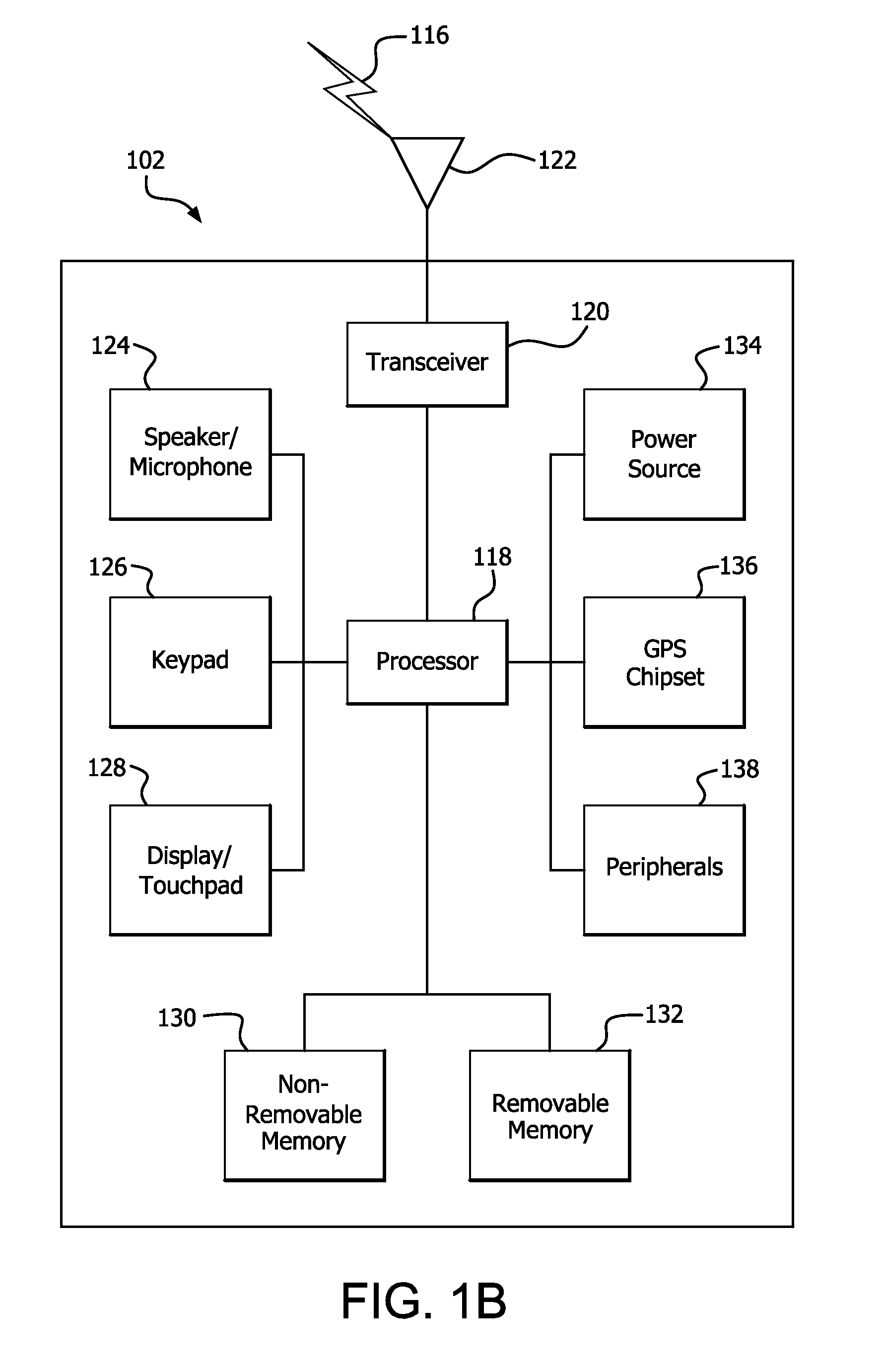
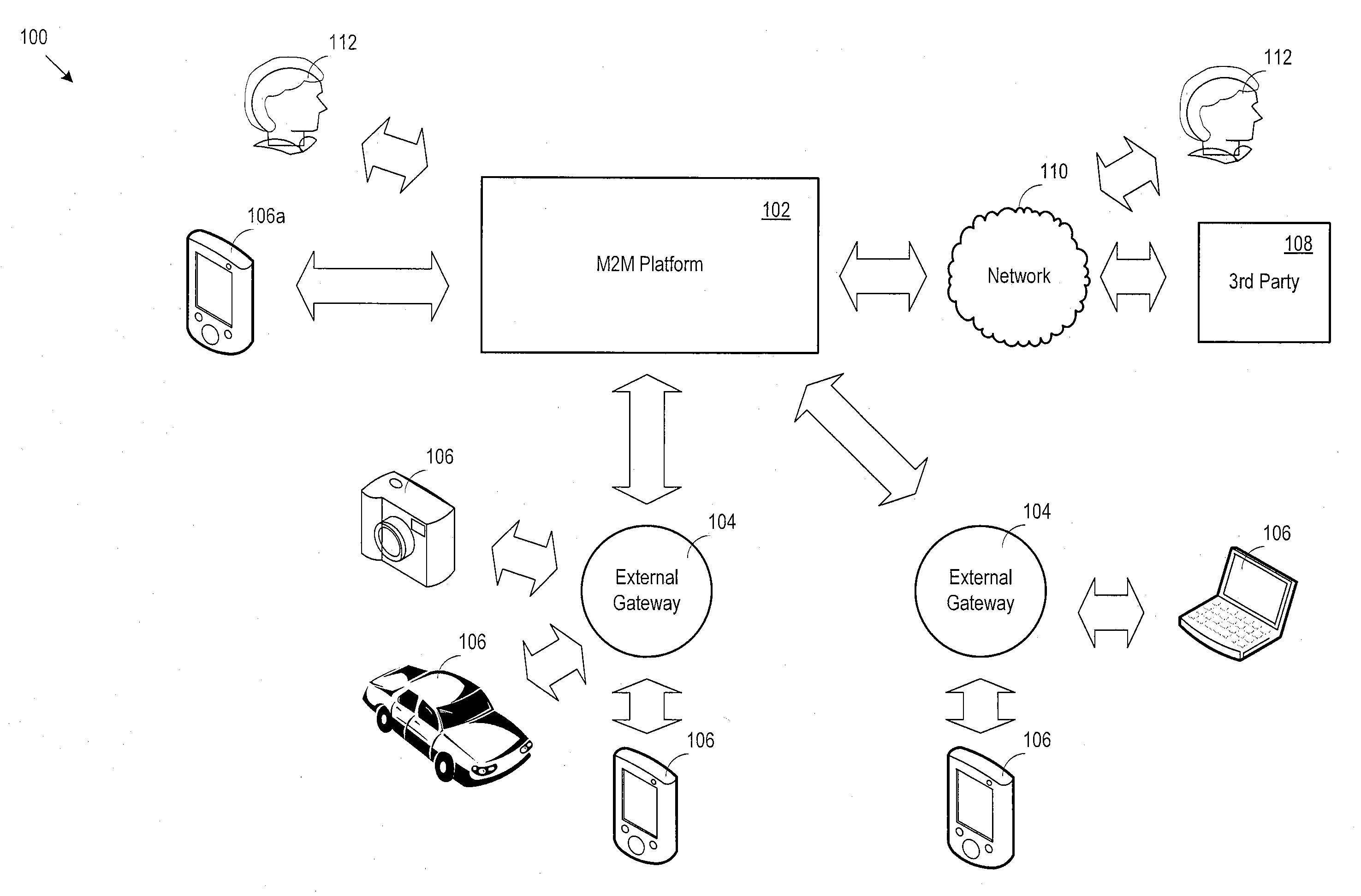
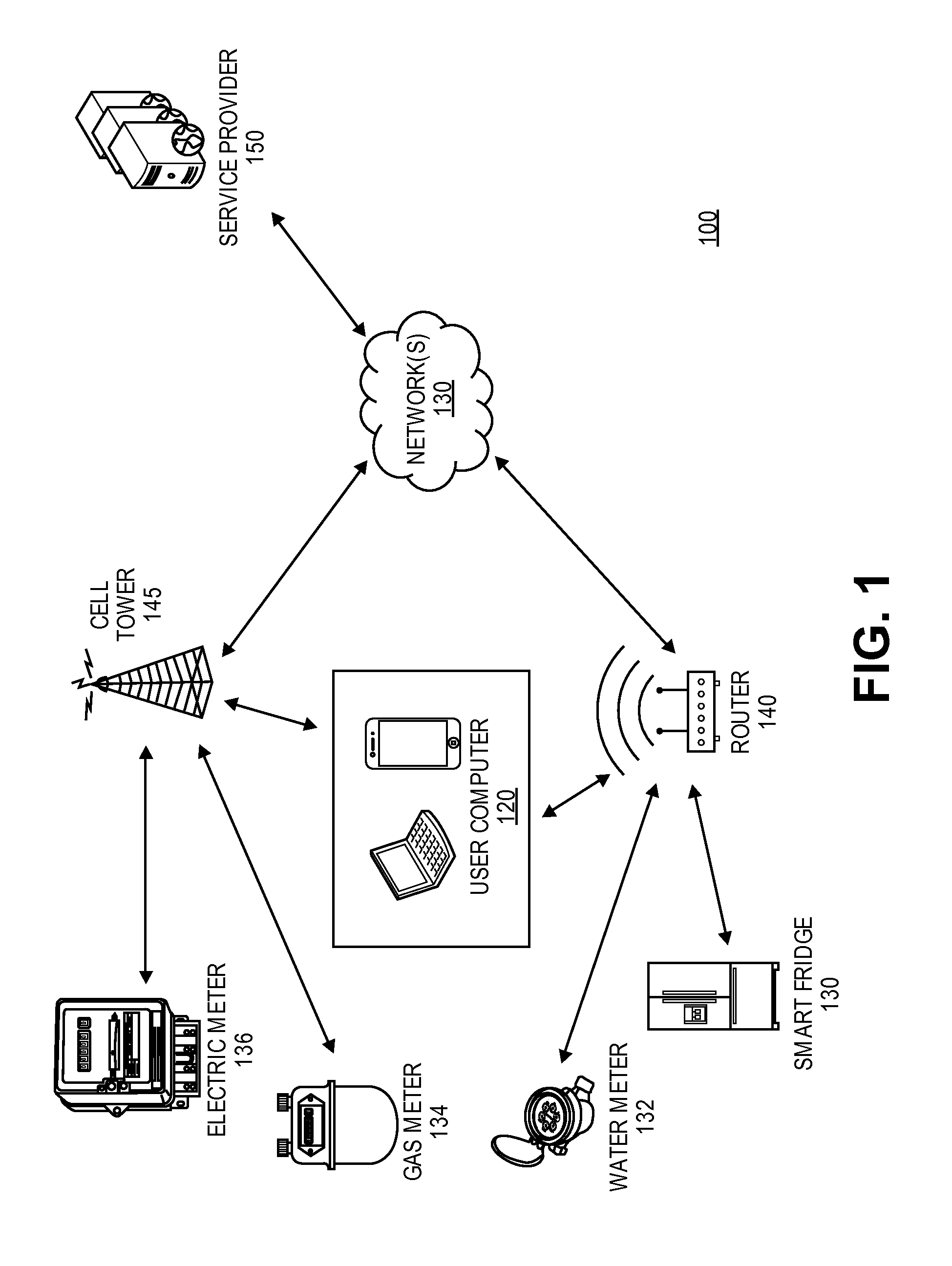
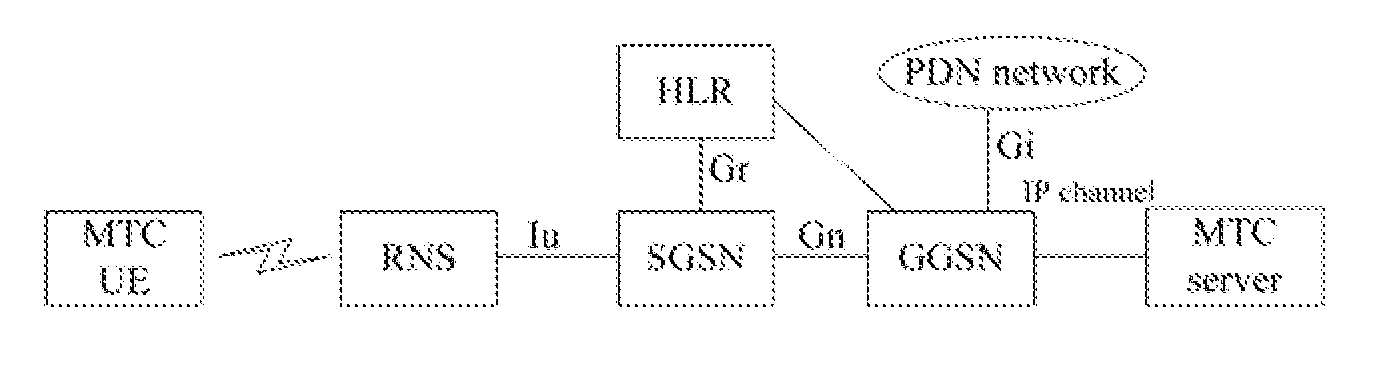
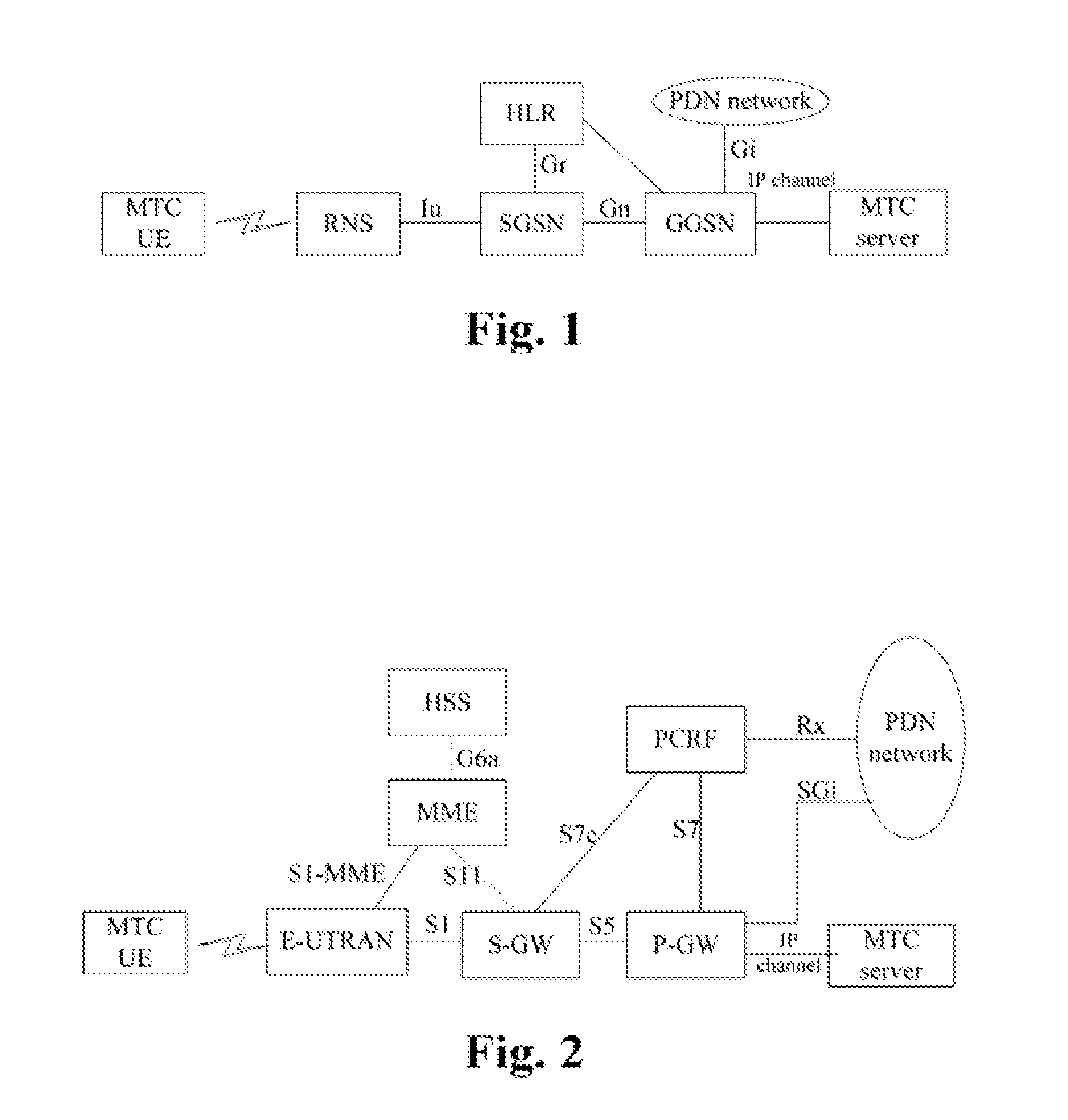
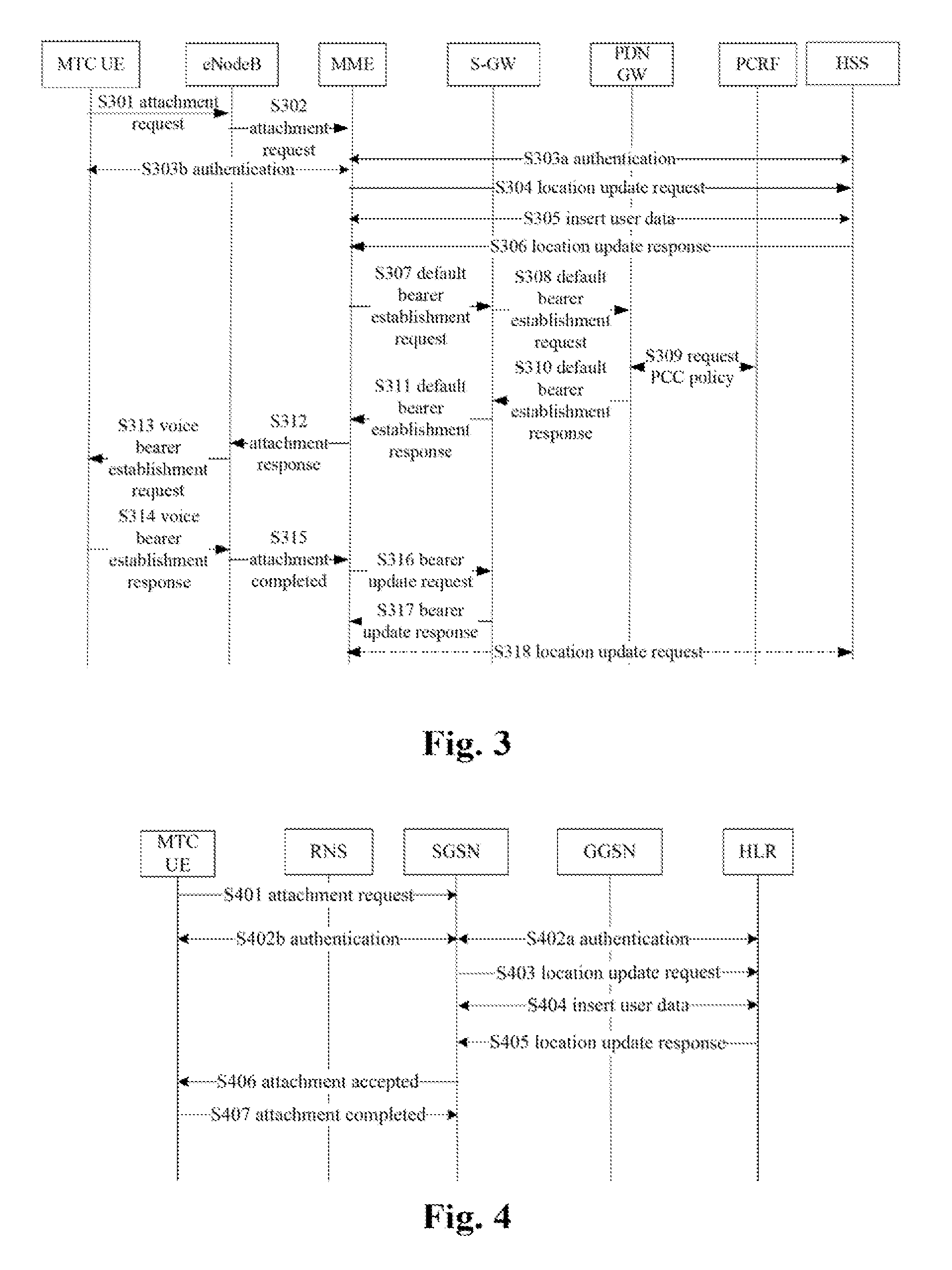
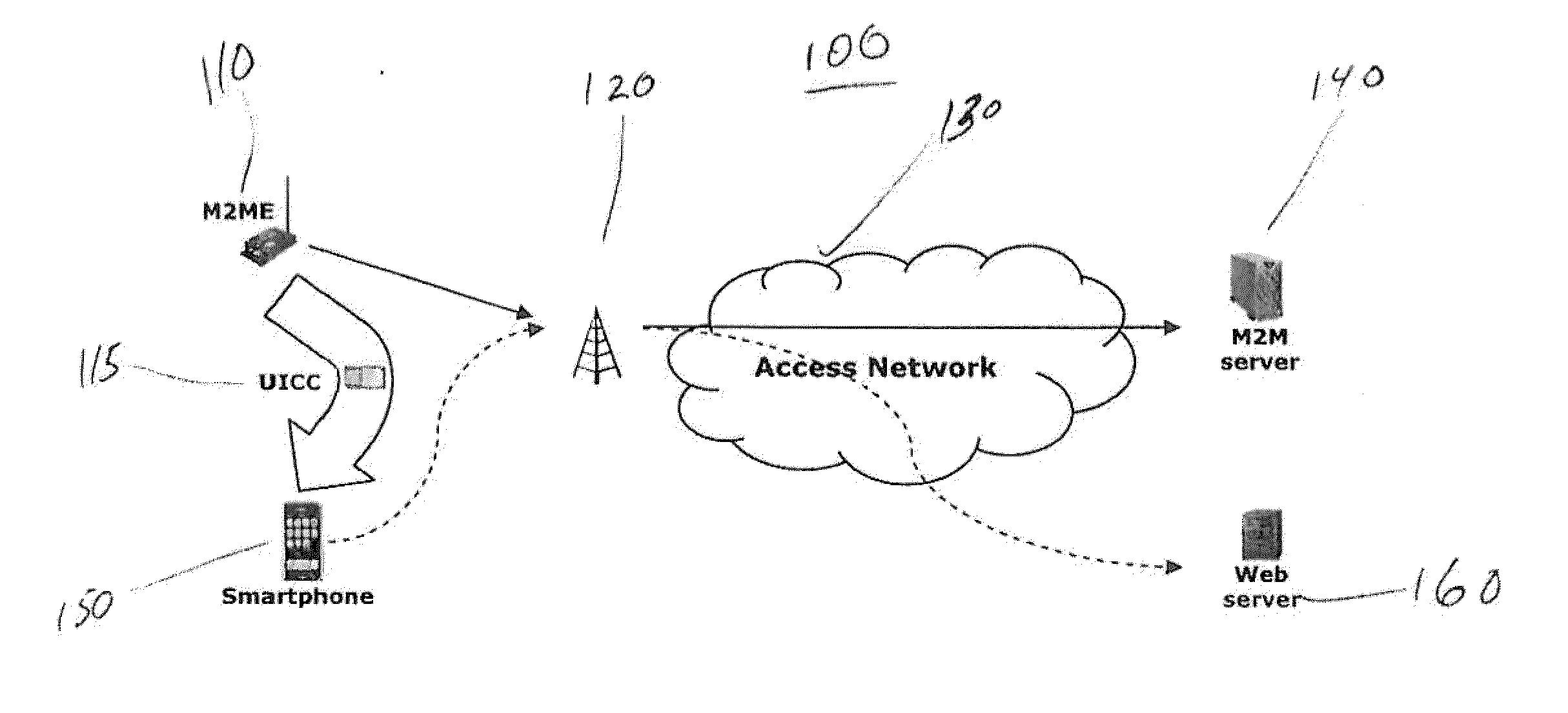
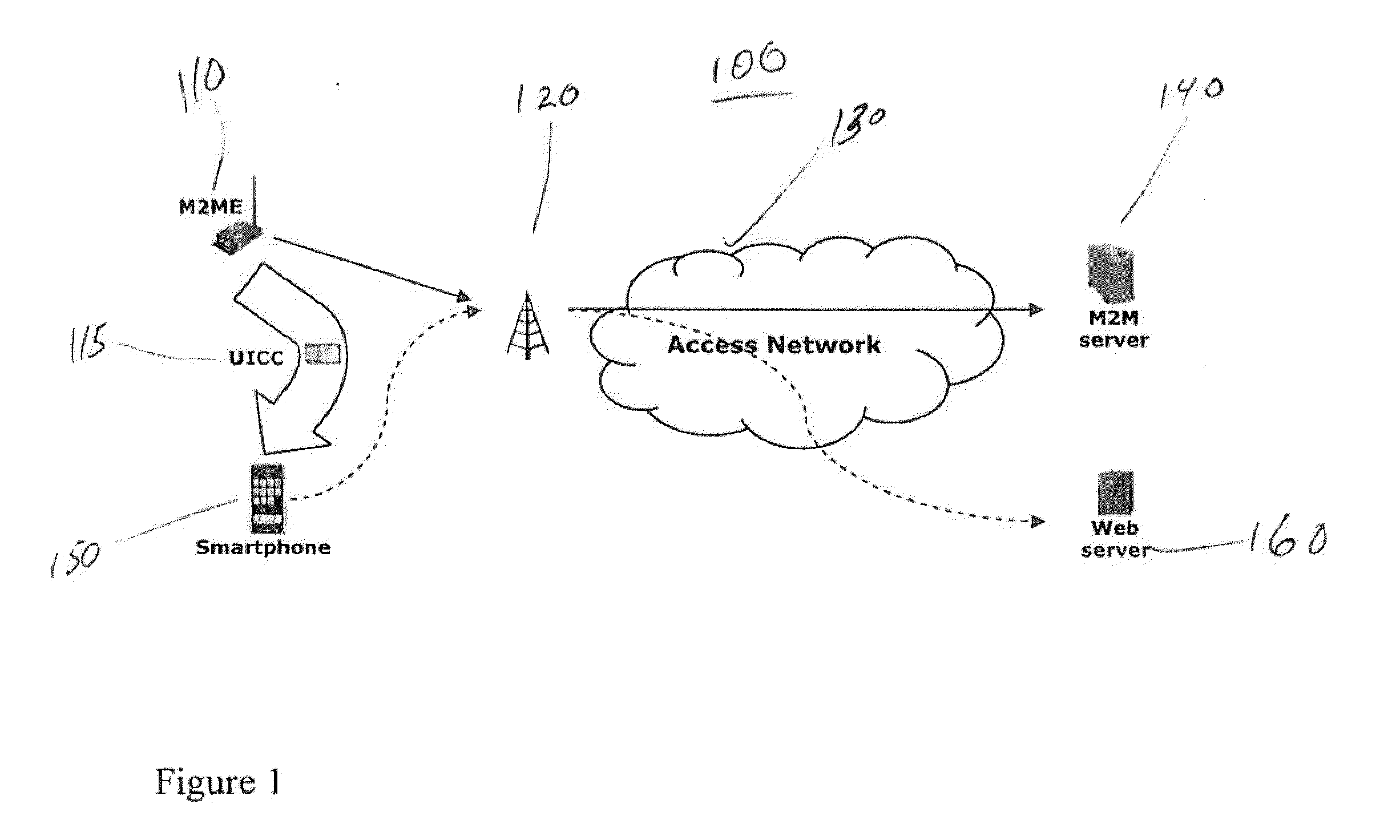
Machine to machine (M2M) is direct communication between devices using any communications channel, including wired and wireless. Machine to machine communication can include industrial instrumentation, enabling a sensor or meter to communicate the information it records (such as temperature, inventory level, etc.) to application software that can use it (for example, adjusting an industrial process based on temperature or placing orders to replenish inventory). Such communication was originally accomplished by having a remote network of machines relay information back to a central hub for analysis, which would then be rerouted into a system like a personal computer.
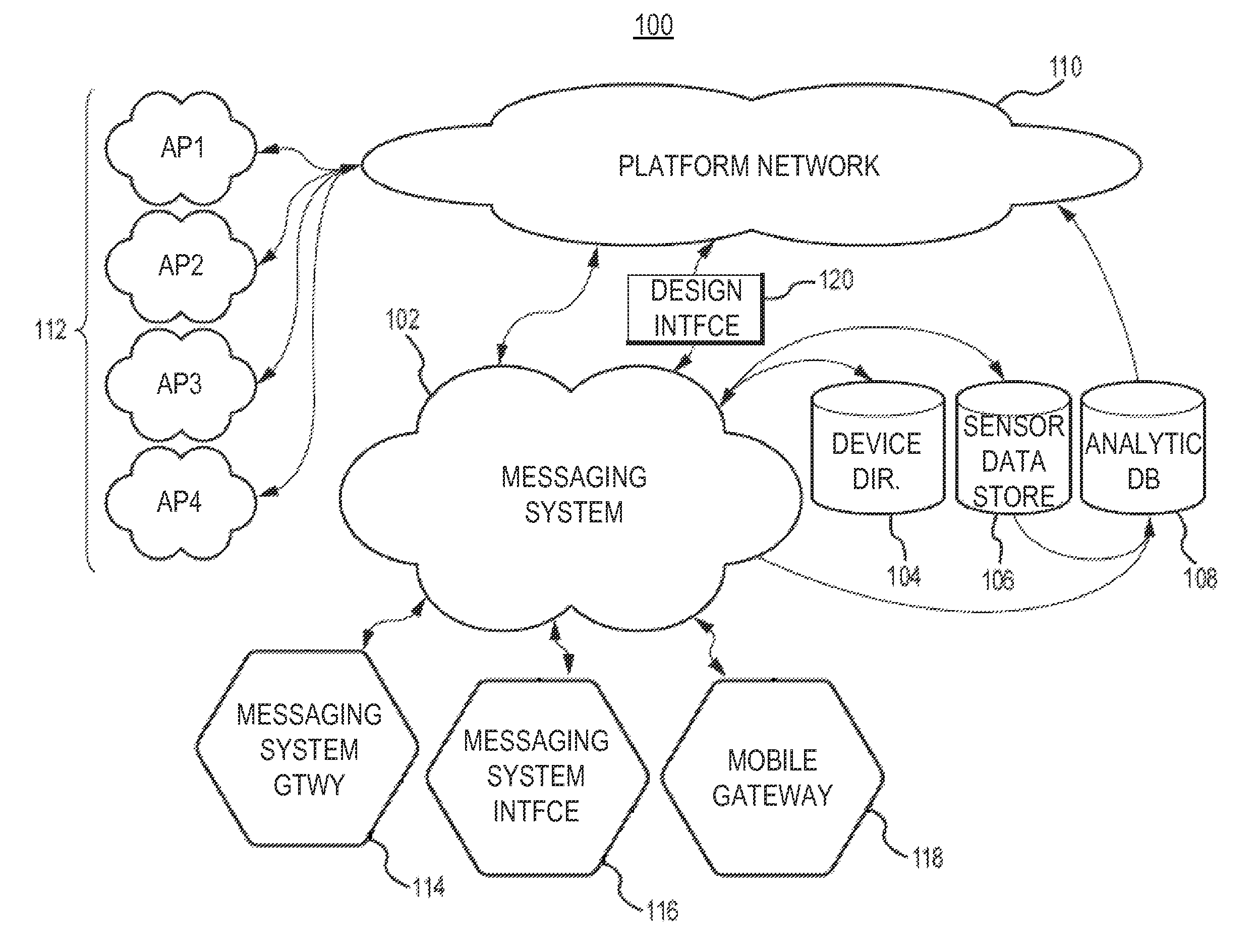
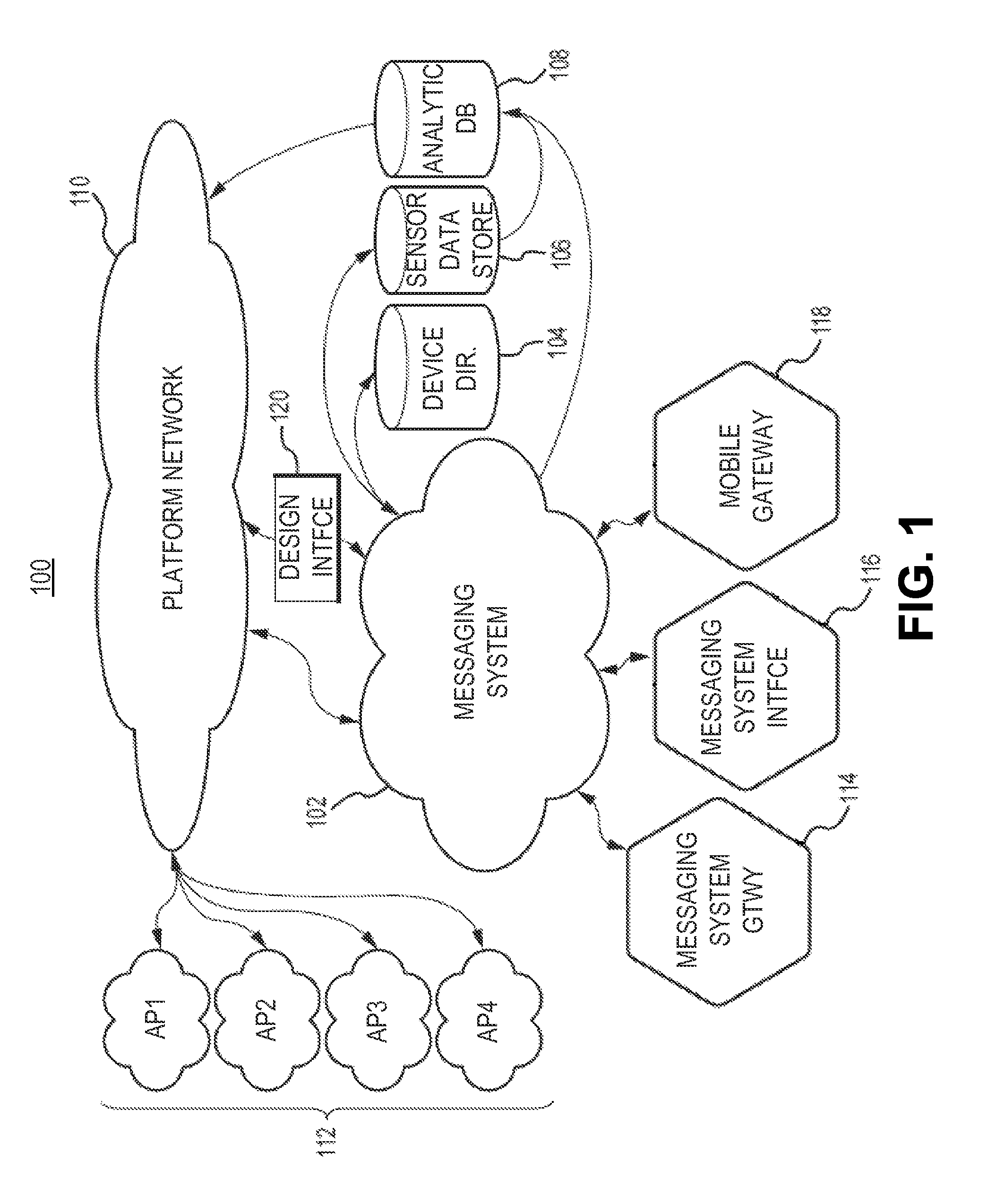
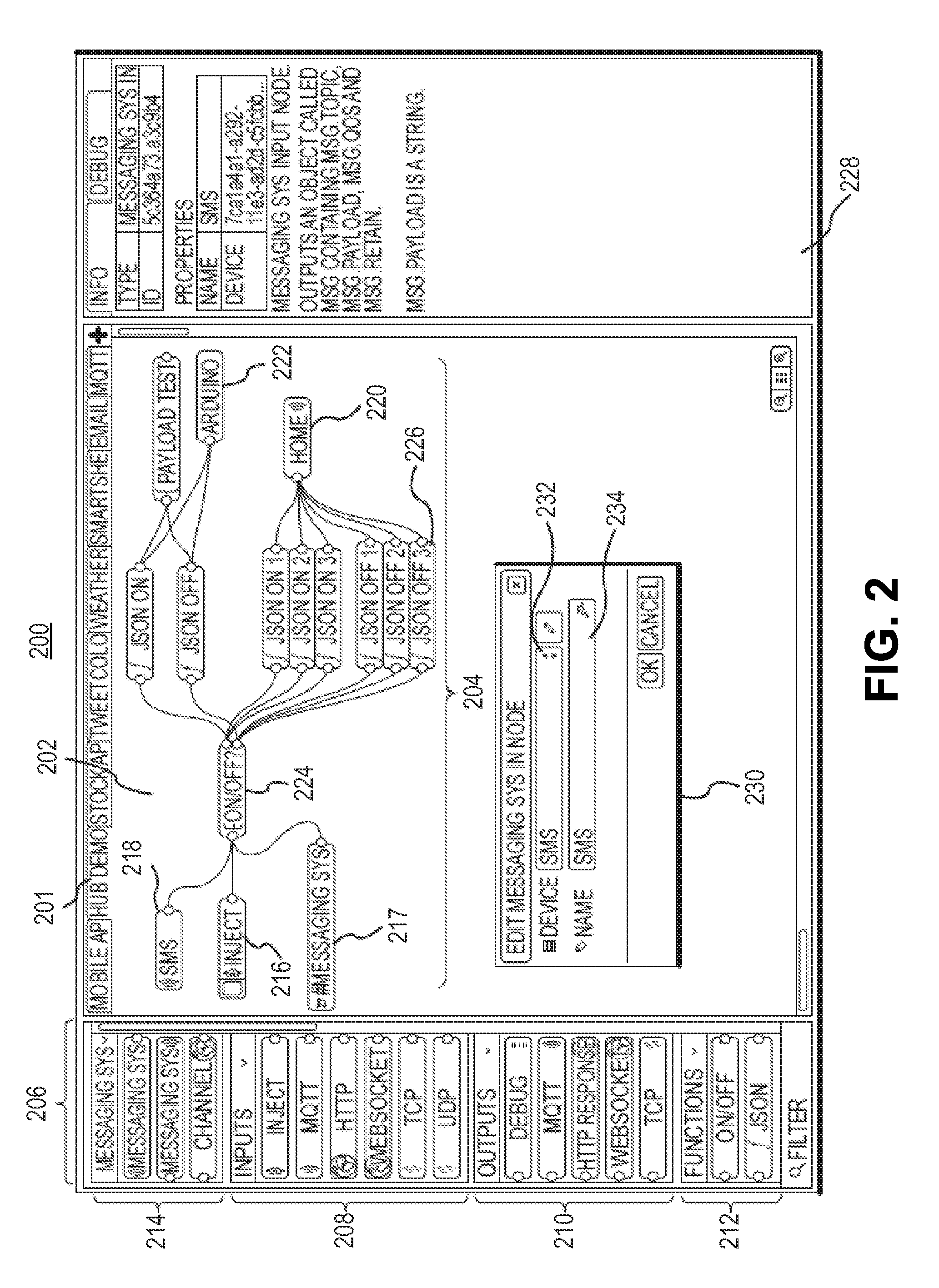
Security and rights management in a machine-to-machine messaging system
Techniques for providing security and rights management in a machine-to-machine messaging system are provided, such as a computing device, a method, and a computer-program product for detecting unauthorized message attempts. For example, the method may receive a communication sent from a first Internet of Things (IoT) device and destined for a second IoT device. The first IoT device is assigned a first universally unique identifier, and the communication includes a second universally unique identifier assigned to the second IoT device. The method may further include obtaining the second universally unique identifier, determining that the second universally unique identifier is assigned to the second IoT device, and determining, using the second universally unique identifier, that the communication received from the first IoT device is an unauthorized message attempt by the first IoT device to exchange a message with the second IoT device.
Owner:CITRIX SYST INC
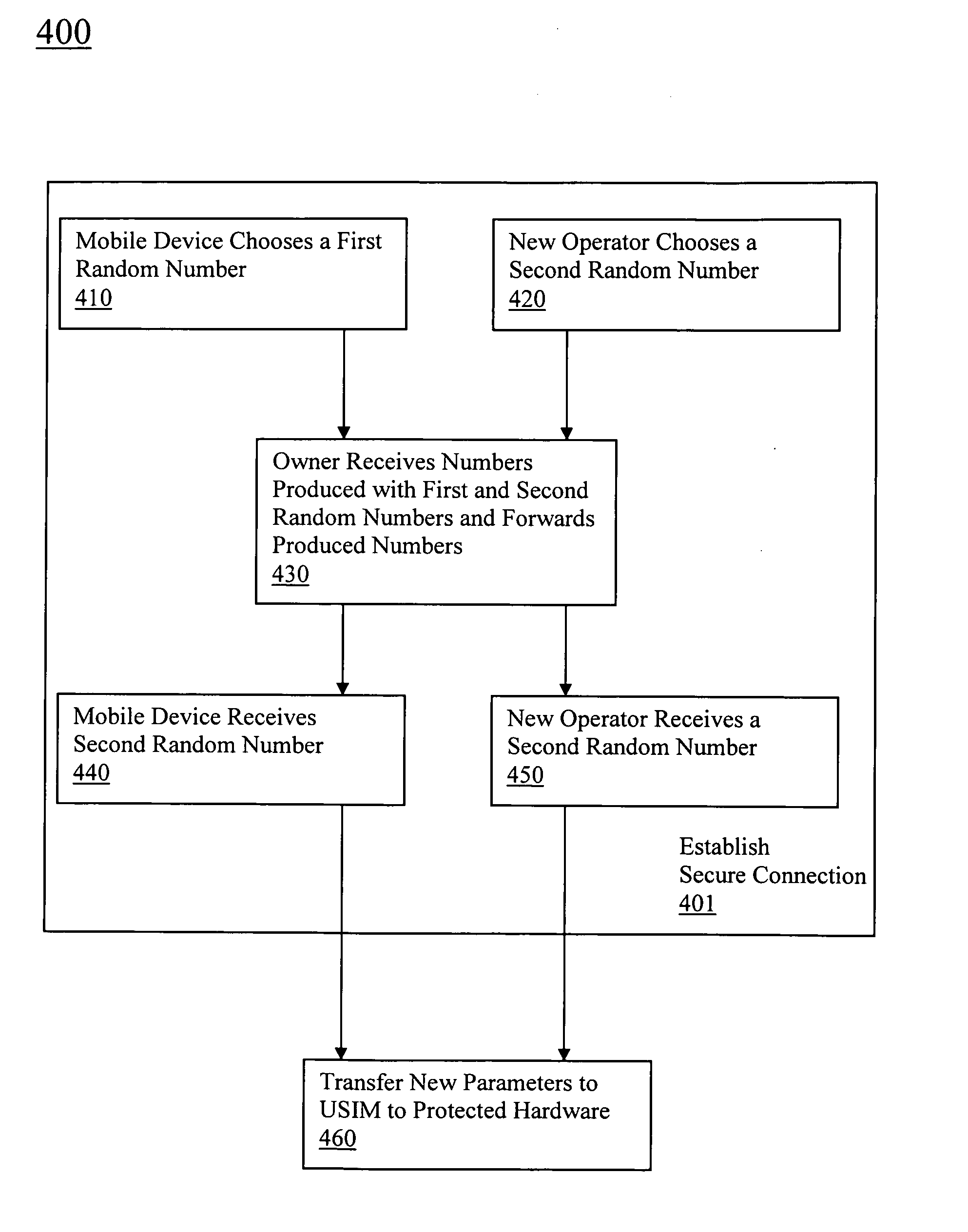
Universal subscriber identity module provisioning for machine-to-machine communications
InactiveUS20090191857A1Automatic exchangesWireless commuication servicesSubscriber identity moduleSafety Connect
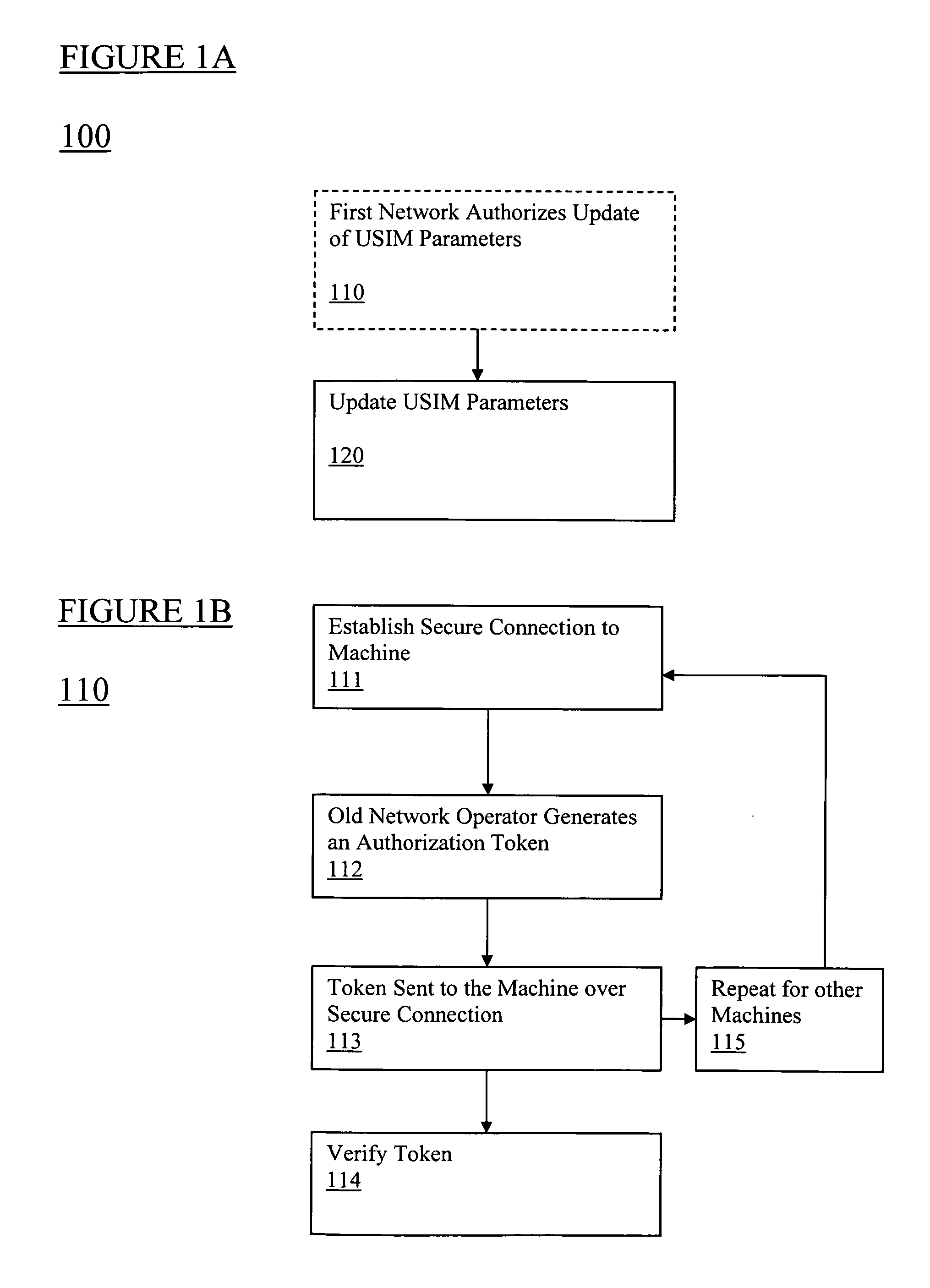
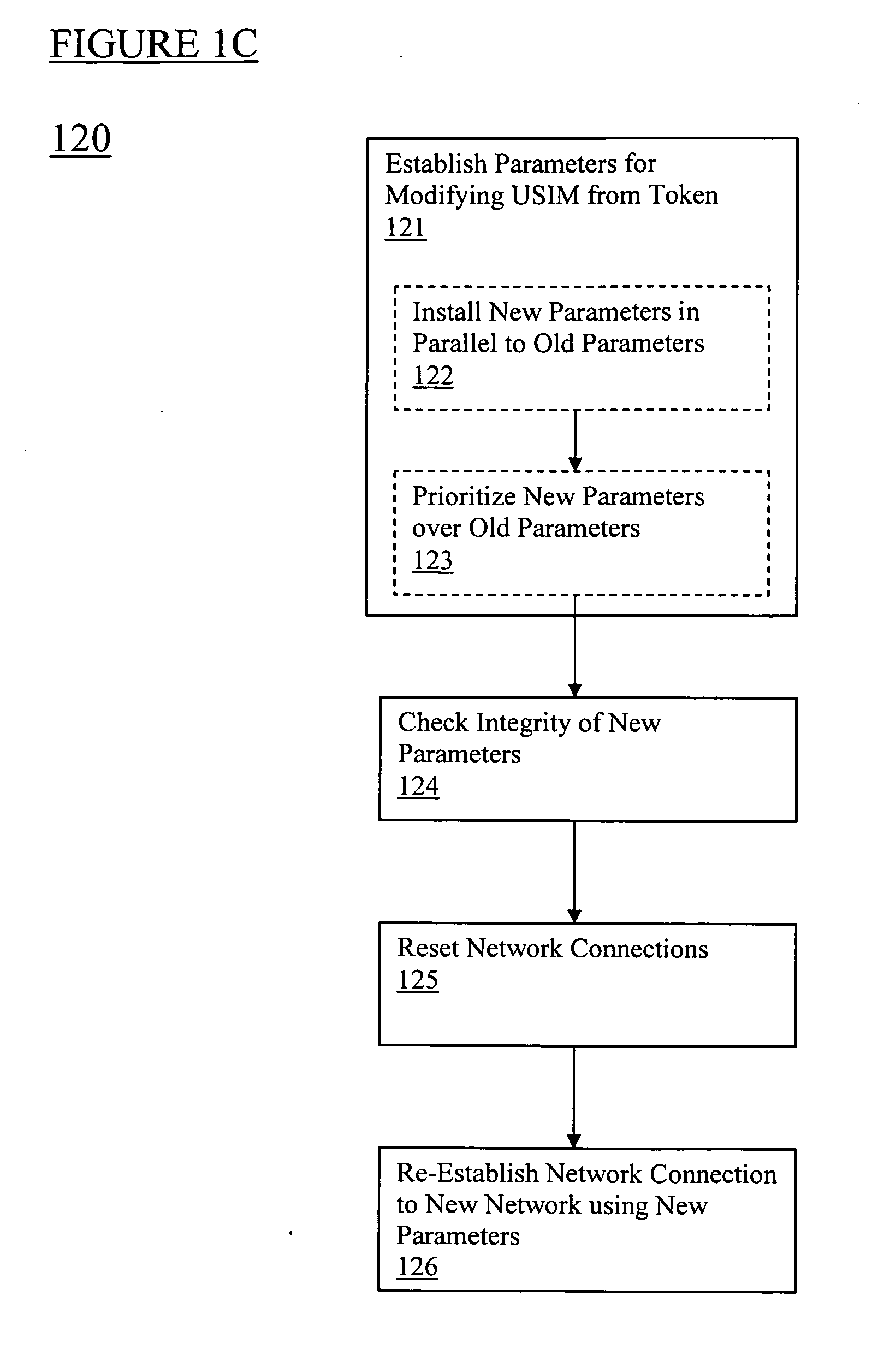
The present invention relates to remotely provisioning subscriber identification parameters in a device on a wireless network. A secure connection is established with the device, and a token containing the new subscriber identification parameters is forwarded over the secure connection. The device may verify the received token. In one embodiment, the subscriber identification parameters are updated to change network operators. The secure connection can be with the old network operator or the new network operator. The device on the wireless network may be a machine-to-machine device. The provisioned subscriber identification may be part of a universal subscriber identification module.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Method and apparatus for machine-to-machine communication registration
ActiveUS20110128911A1Network traffic/resource managementBroadcast service distributionControl channelComputer science
Methods and apparatus are disclosed for Machine to Machine (M2M) communication registration. The methods provide single and periodic registration and may be device or network based. The devices in the system may be divided into groups. A single device member may perform the basic access steps for the group. Other devices may receive related access information on a control channel and use the information to access the system. The devices may send data, get updates, and then go to sleep. Internet addresses may be released or maintained. During a control cycle, the devices may wake up and listen to the control channel for any paging messages. Individual devices or the entire group may access the system. During a reporting cycle, all the devices may wake up and access the system to connect to the M2M system to upload data.
Owner:INTERDIGITAL PATENT HLDG INC
Separate upgrade/modification of remote software in machine to machine communication
InactiveUS20140007076A1Reduce work loadReducing wireless resource occupancyService provisioningProgram loading/initiatingUpgradeSoftware
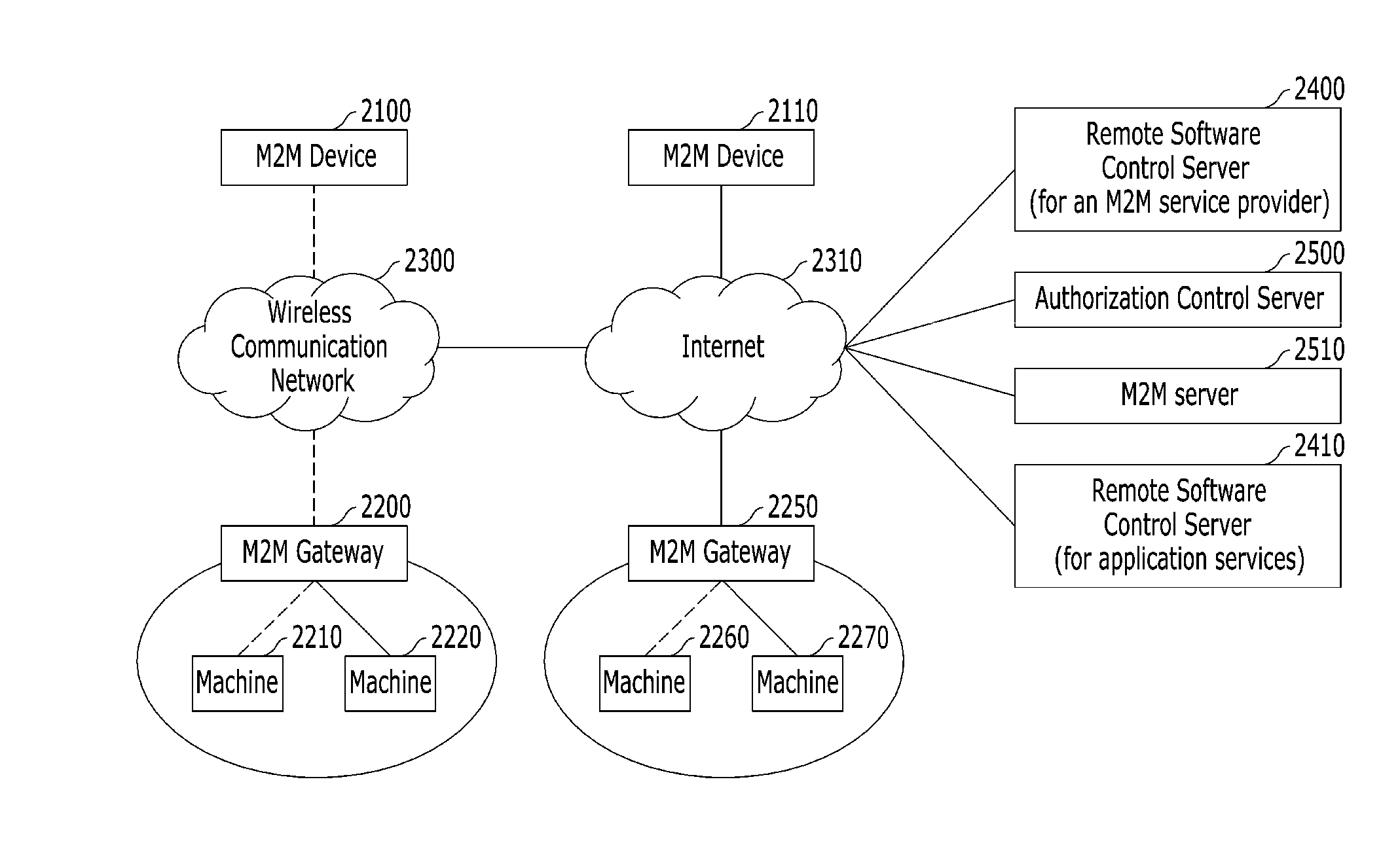
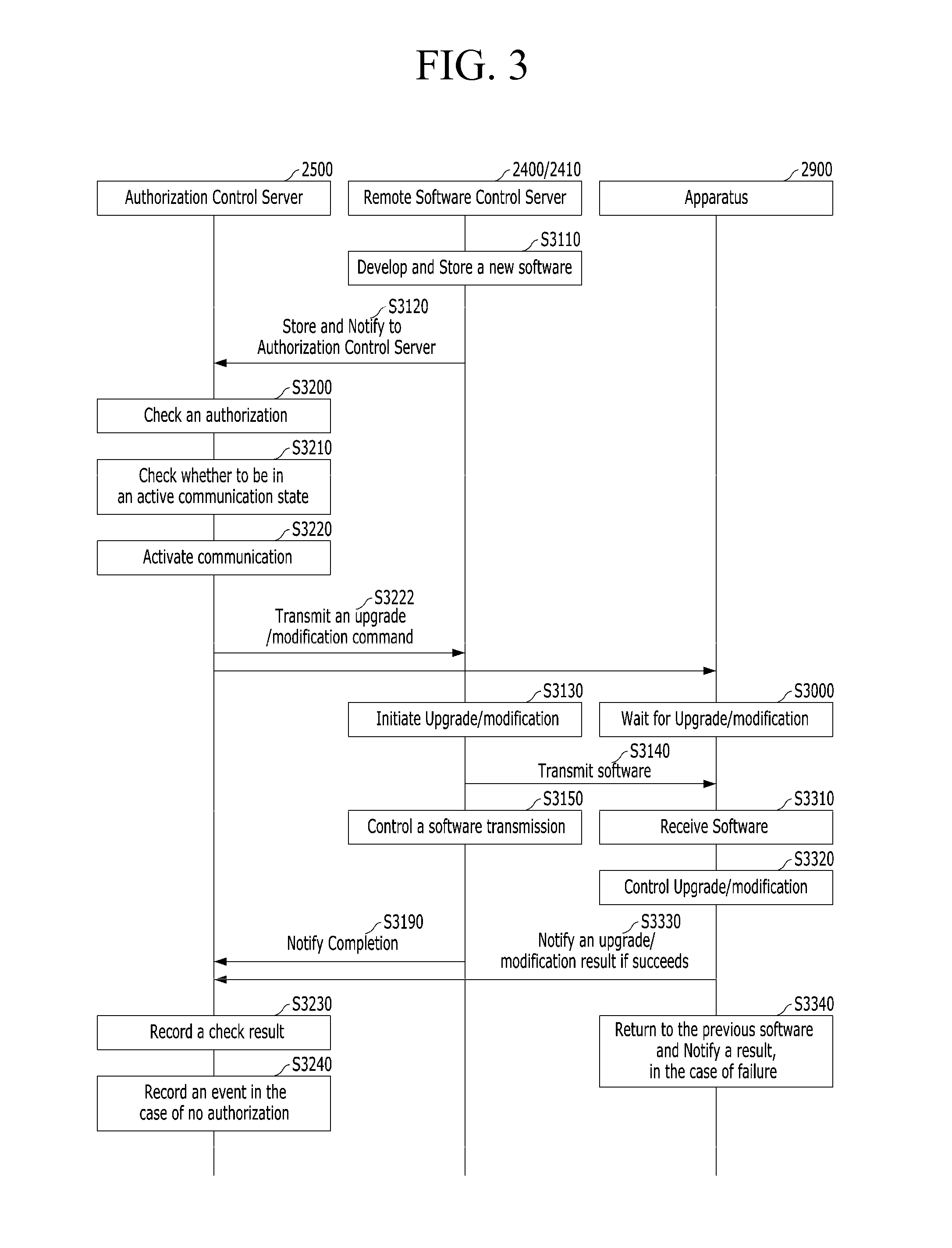
The present disclosure is related to separately upgrading or modifying a remote software in a machine to machine (M2M) communication. Particularly, in the case of upgrading or modifying firmware of an M2M device or an M2M gateway, the present disclosure relates to separating an M2M service provider domain and a manufacturer domain, and independently upgrading or modifying each of the separated domains.
Owner:KT CORP
Machine-to-machine gateway architecture and functionality
ActiveUS20110213871A1Easy to shareGood synchronizationService provisioningMultiple digital computer combinationsReachabilityData aggregator
A machine-to-machine (M2M) gateway (GW) includes reachability, addressing, and repository (RAR) capability. The GW maintains a local mapping table and local device application repository, performs data aggregation, address / name translation, provides event reporting and establishes GW reachability and wake-up time. The GW supports requests from M2M applications or other capabilities within the GW, and from a network and application (N&A) domain RAR. The GW may include an M2M device and M2M gateway management (MDGM) capability that receives management requests for an M2M device and functions as a network proxy. The MDGM accepts and processes requests from the N&A domain on behalf of the M2M device and performs management functions of the M2M device on behalf of the N&A domain. The MDGM may request the N&A domain for permission to interact with the M2M device, initiate an interaction for device management tasks with the M2M device, and report to the N&A domain.
Owner:DRNC HLDG INC
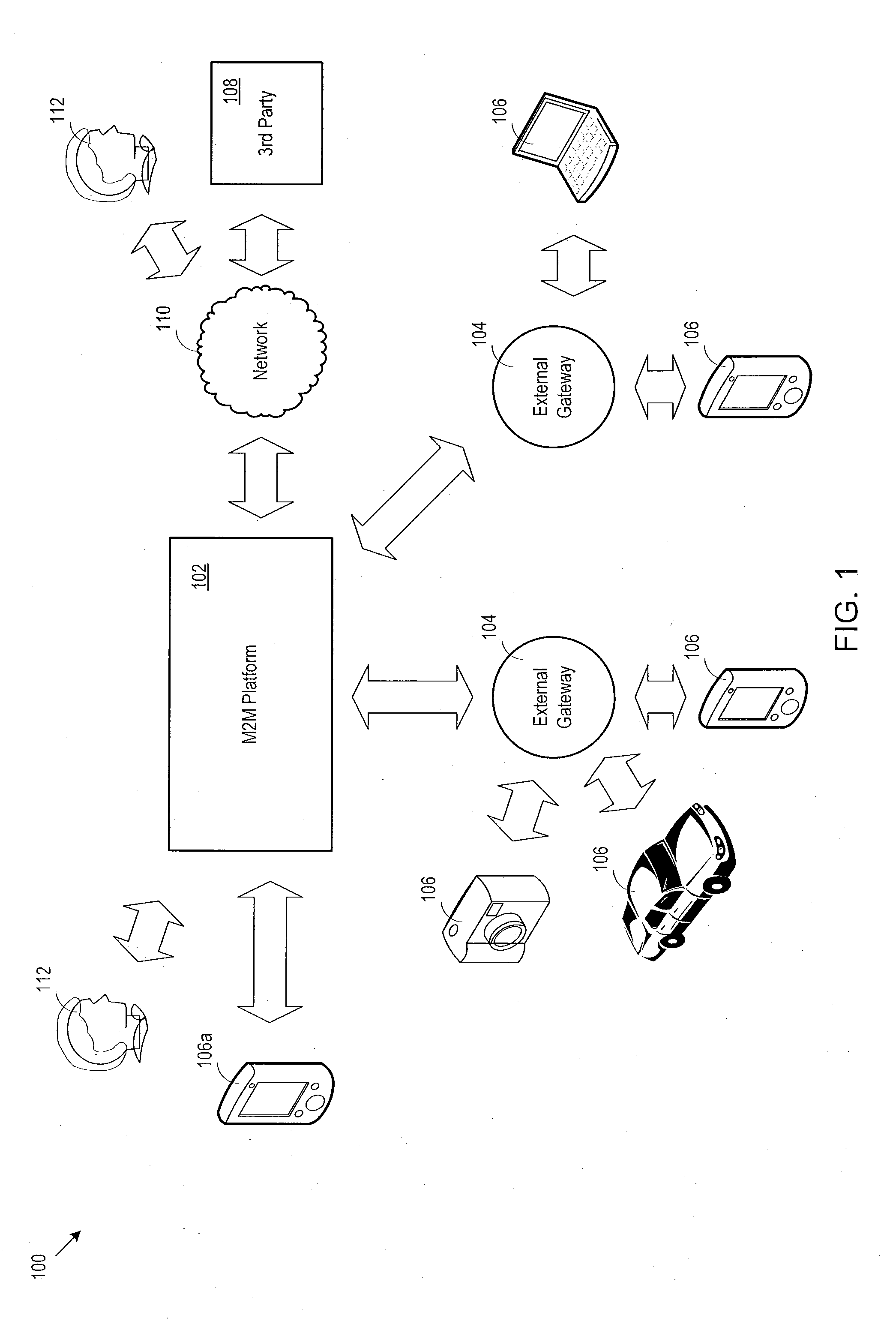
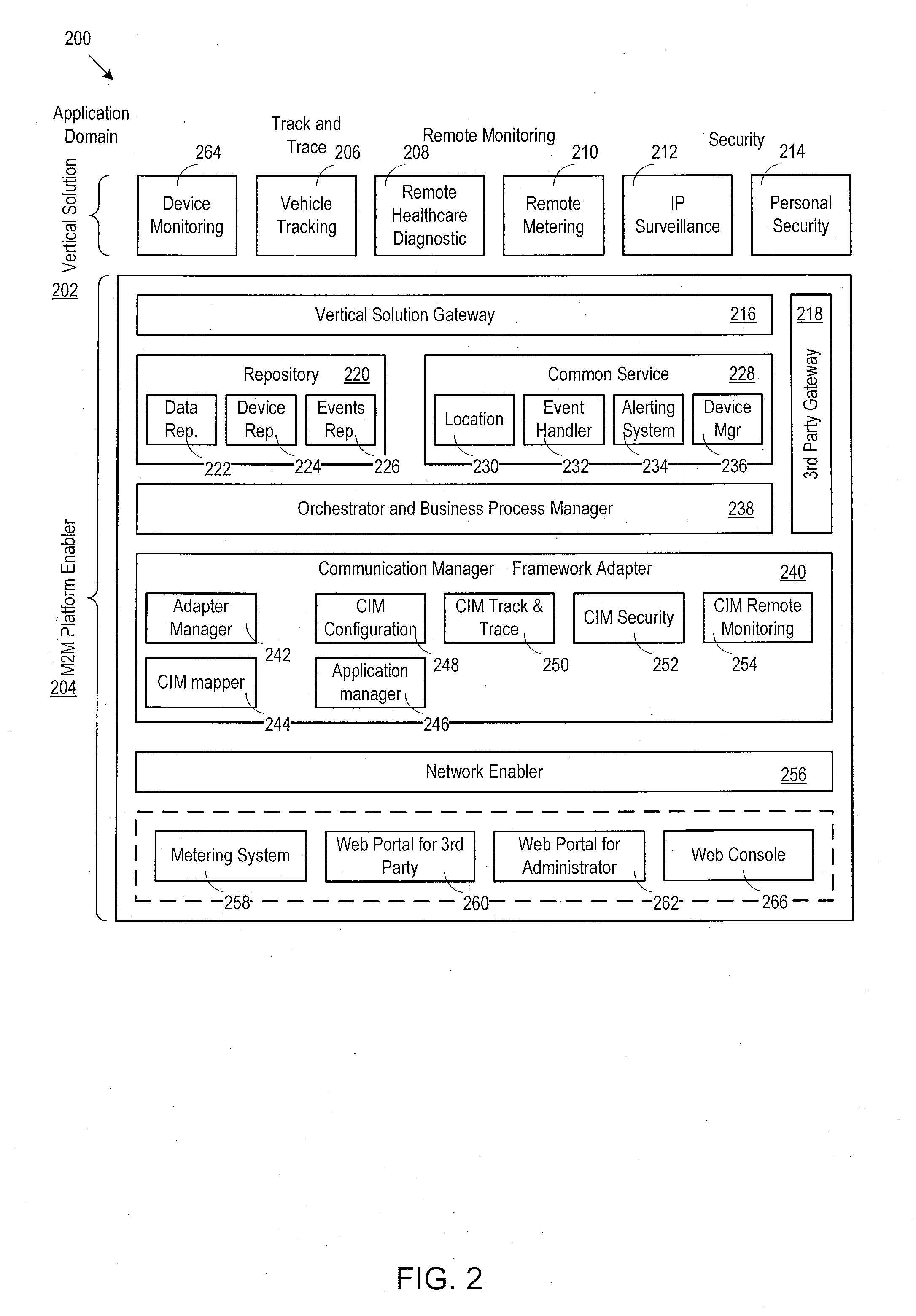
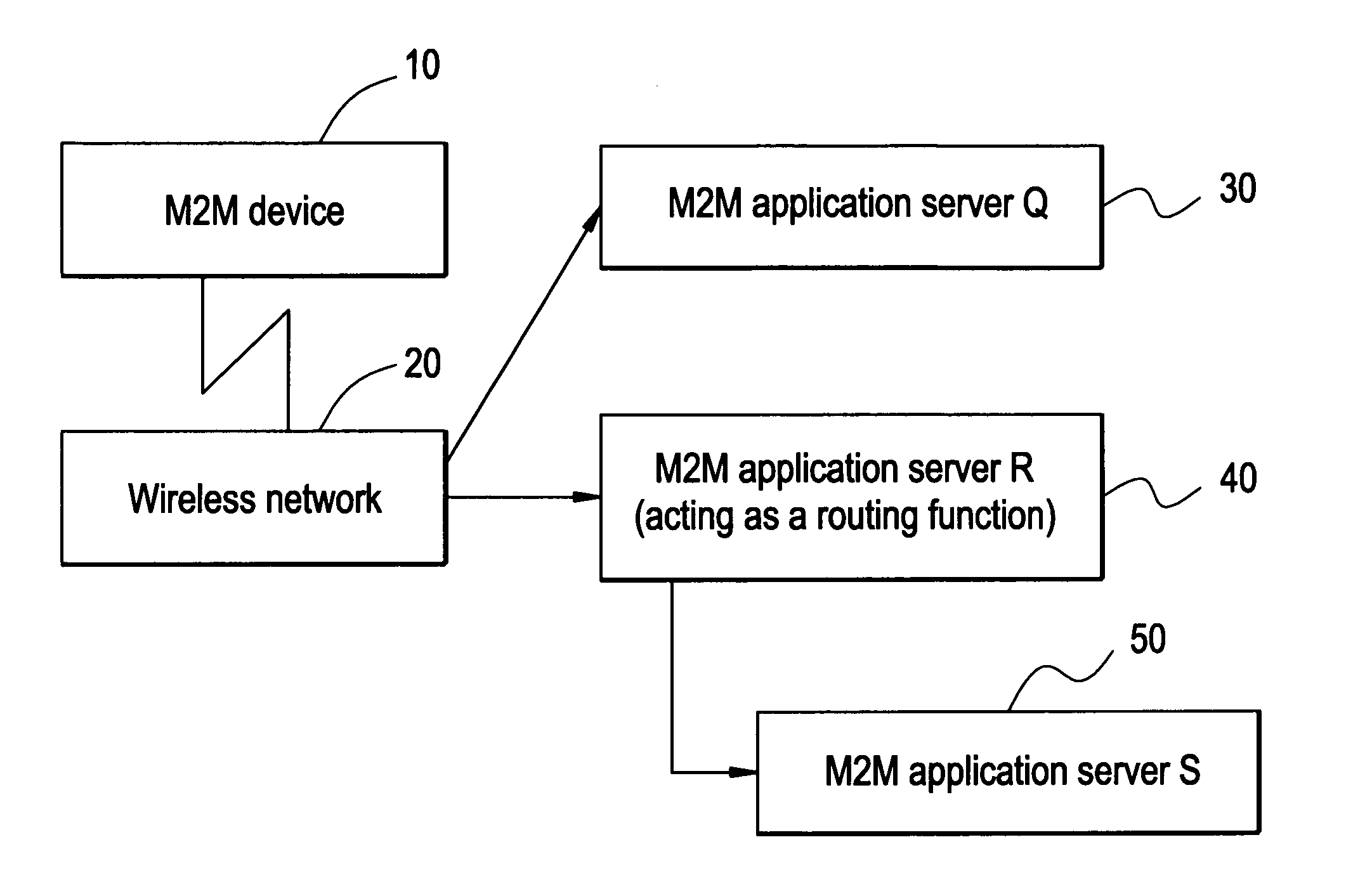
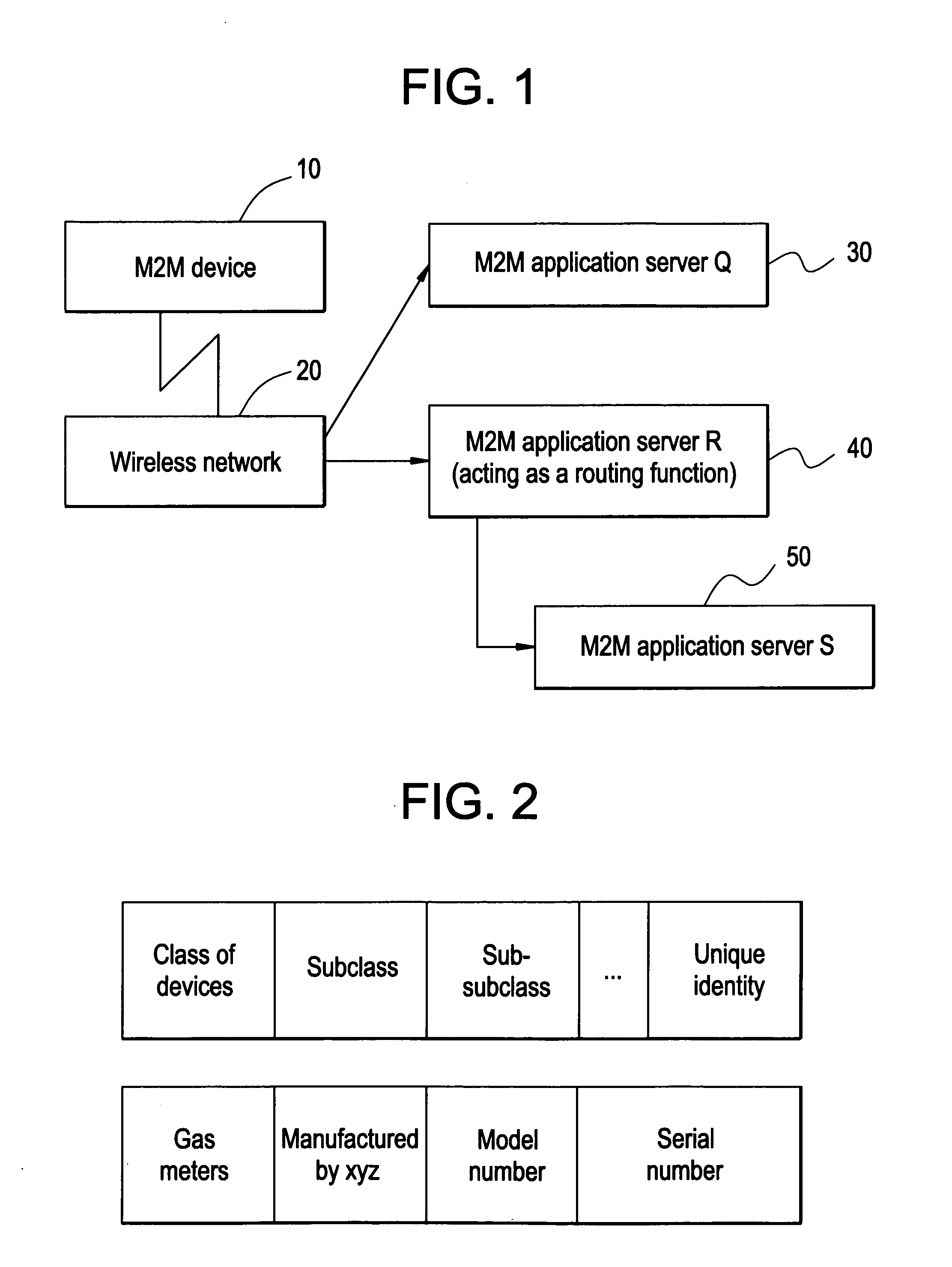
Machine to machine architecture
ActiveUS20110200052A1Data switching by path configurationMachine-to-machine/machine-type communication serviceThird partyInternet privacy
A machine-to-machine communication platform provides a flexible system for device control and solution hosting. In particular, the communication platform hosts and manages third party vertical solutions that interact with external devices. A third party gateway provides the third parties with access to the communication platform so that the third parties may define, configure, and monitor custom vertical solutions that are locally hosted in the communication platform. The communication platform provides a communication manager that implements a device independent communication facility for communicating with the external devices. As a result, the communication platform connects to, communicates with, and controls virtually any external device.
Owner:ACCENTURE GLOBAL SERVICES LTD
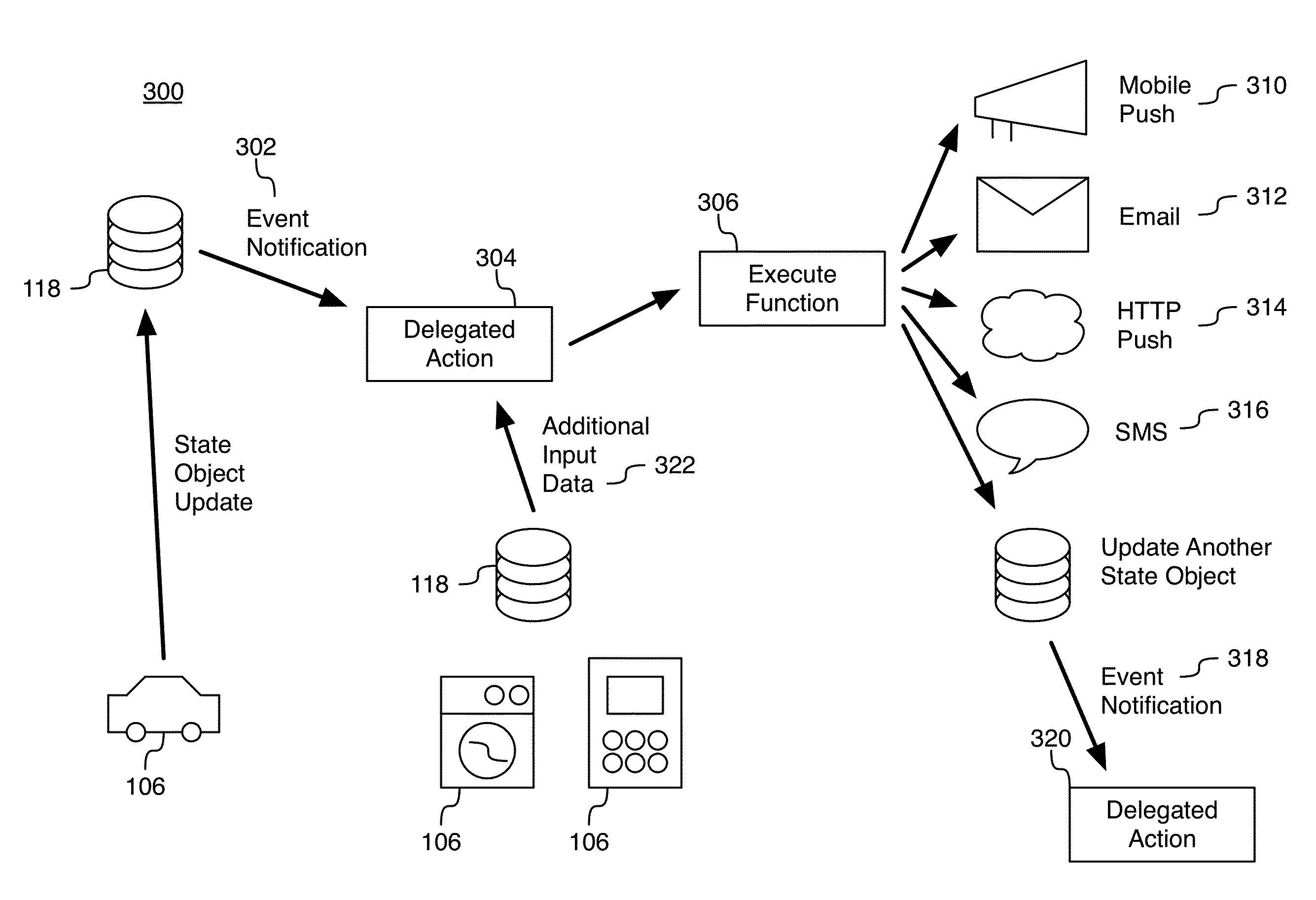
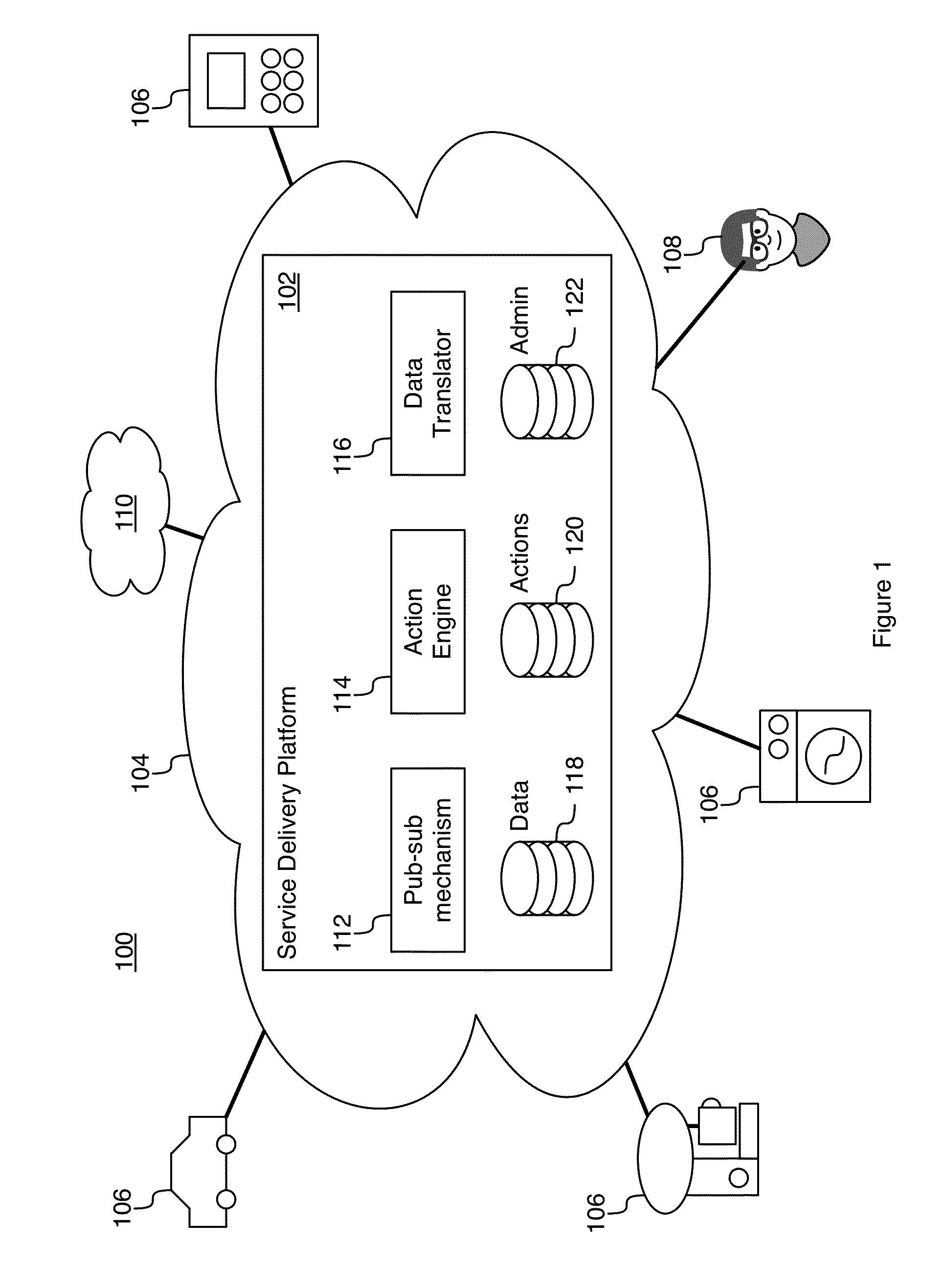
System and method for machine-to-machine communication
InactiveUS20150195349A1TransmissionMachine-to-machine/machine-type communication serviceSemantic representationComputer science
The system and method provide for data interactions between interconnect nodes so that they can create outcomes cooperatively with responsiveness and flexibility. Each node may transmit data and events of interest to other nodes. The other nodes may receive notification of data and event transmissions. Delegated actions may be created for off-node (e.g. network-based) execution that may act as delegates for corresponding nodes without the need for the nodes to be connected to a network nor for data and event transmissions to be processed directly by the nodes. The system and method may provide for translation of data and events received, from a node, in a first semantic representation to be translated to a second semantic that is compatible with one or more other nodes.
Owner:MALIKIE INNOVATIONS LTD +1
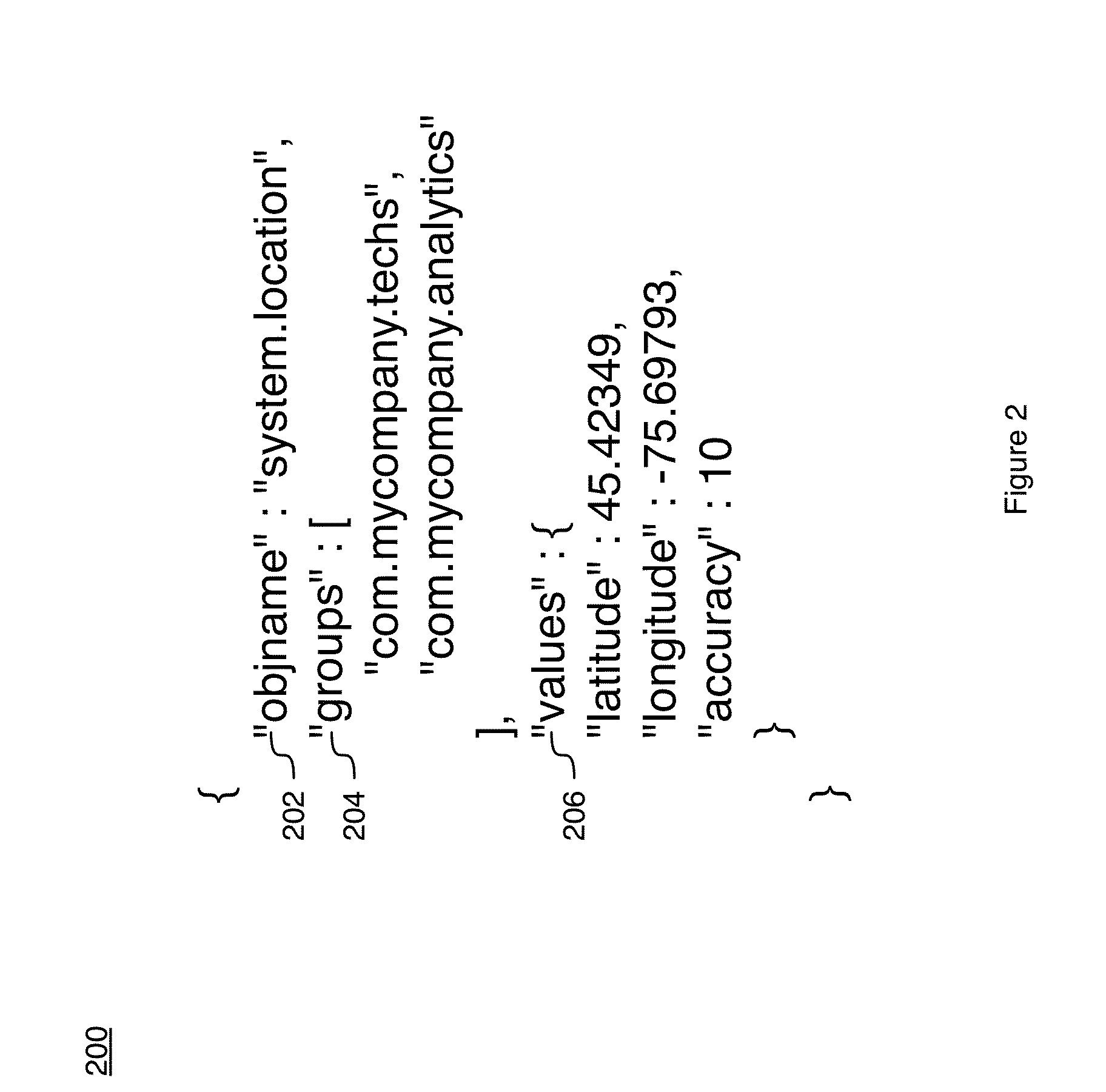
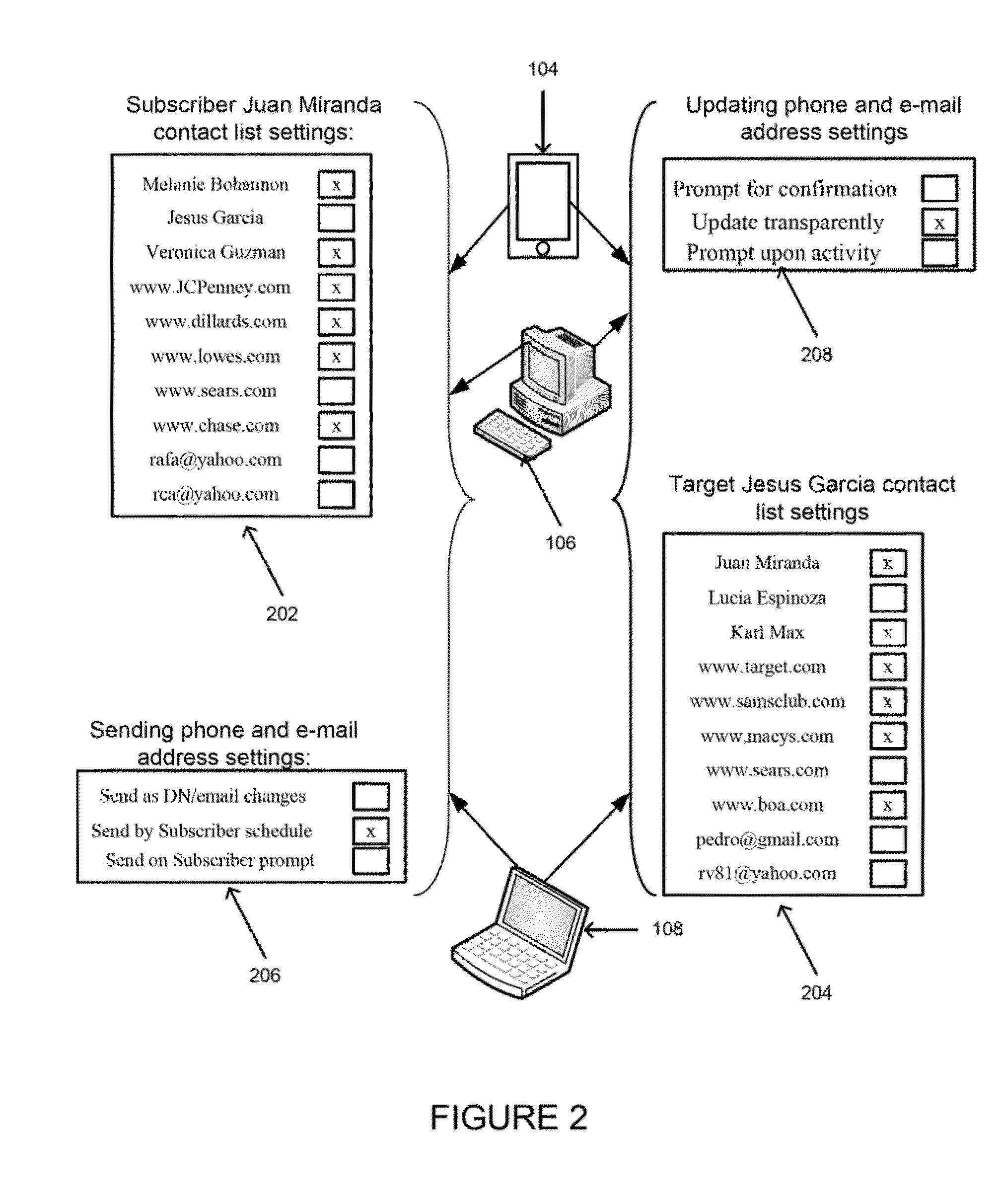
Automatic machine to machine distribution of subscriber contact information
A method and system for replacing contact information without significant human intervention. A subscriber's replacement contact information is automatically sent to specified recipients in a telecommunication system. A program on a subscriber's network appliance upon receipt of a prompt generated by the subscriber to notify contacts of a change or, the program automatically generating instructions when new contact information is installed in a subscriber's network appliance, causes a list of selected recipient addresses to be displayed on the subscriber's appliance display. The subscriber selects the addresses to be notified of the change and the subscriber's network appliance automatically sends the contact information via the telecommunication system's authentication process, to the address selections. Each receiving device has instructions for receiving the replacement contact address information and then replacing the subscriber's current contact address information, that is stored on the device, with the replacement contact address information.
Owner:TELEFON AB LM ERICSSON (PUBL)
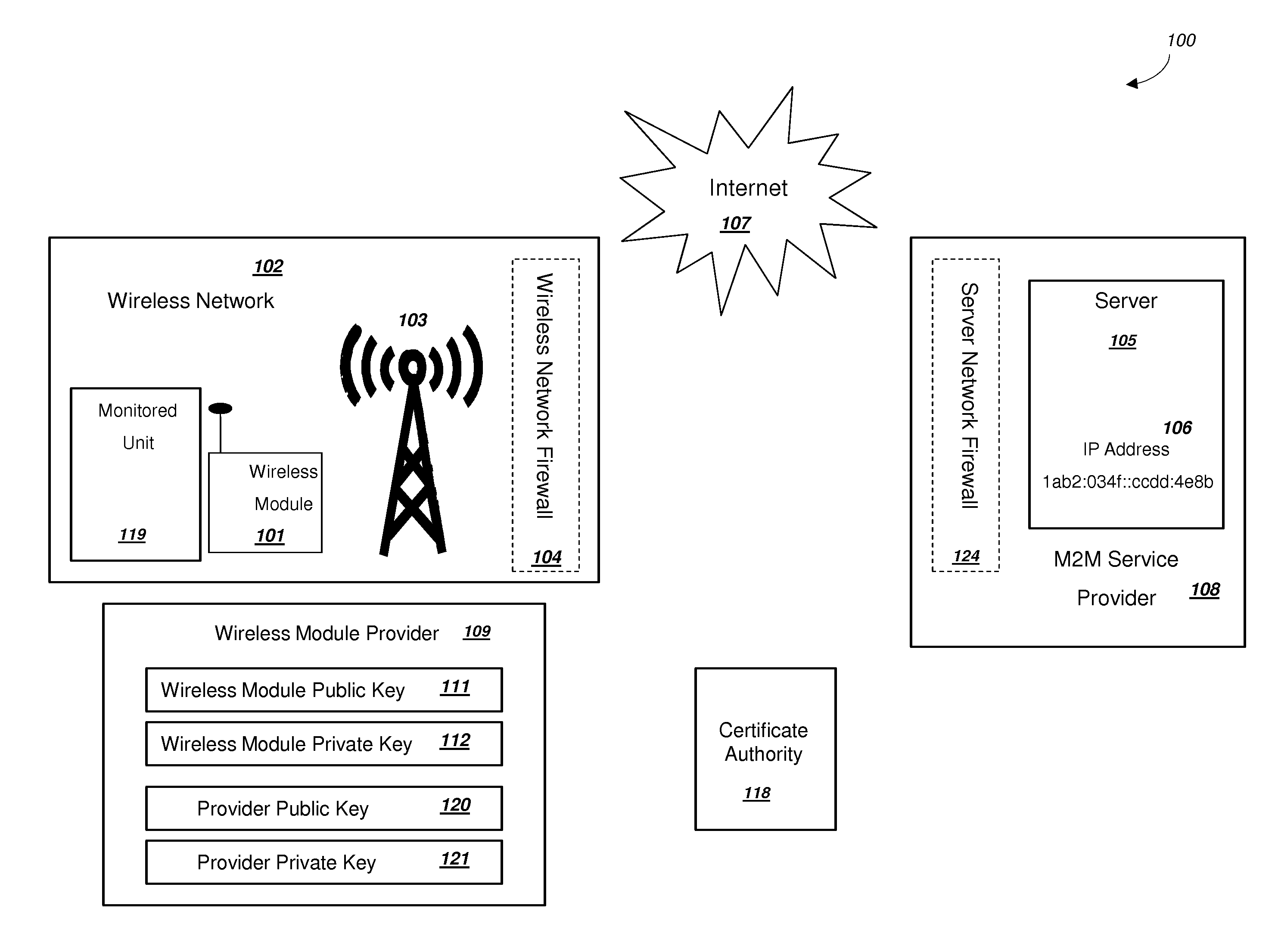
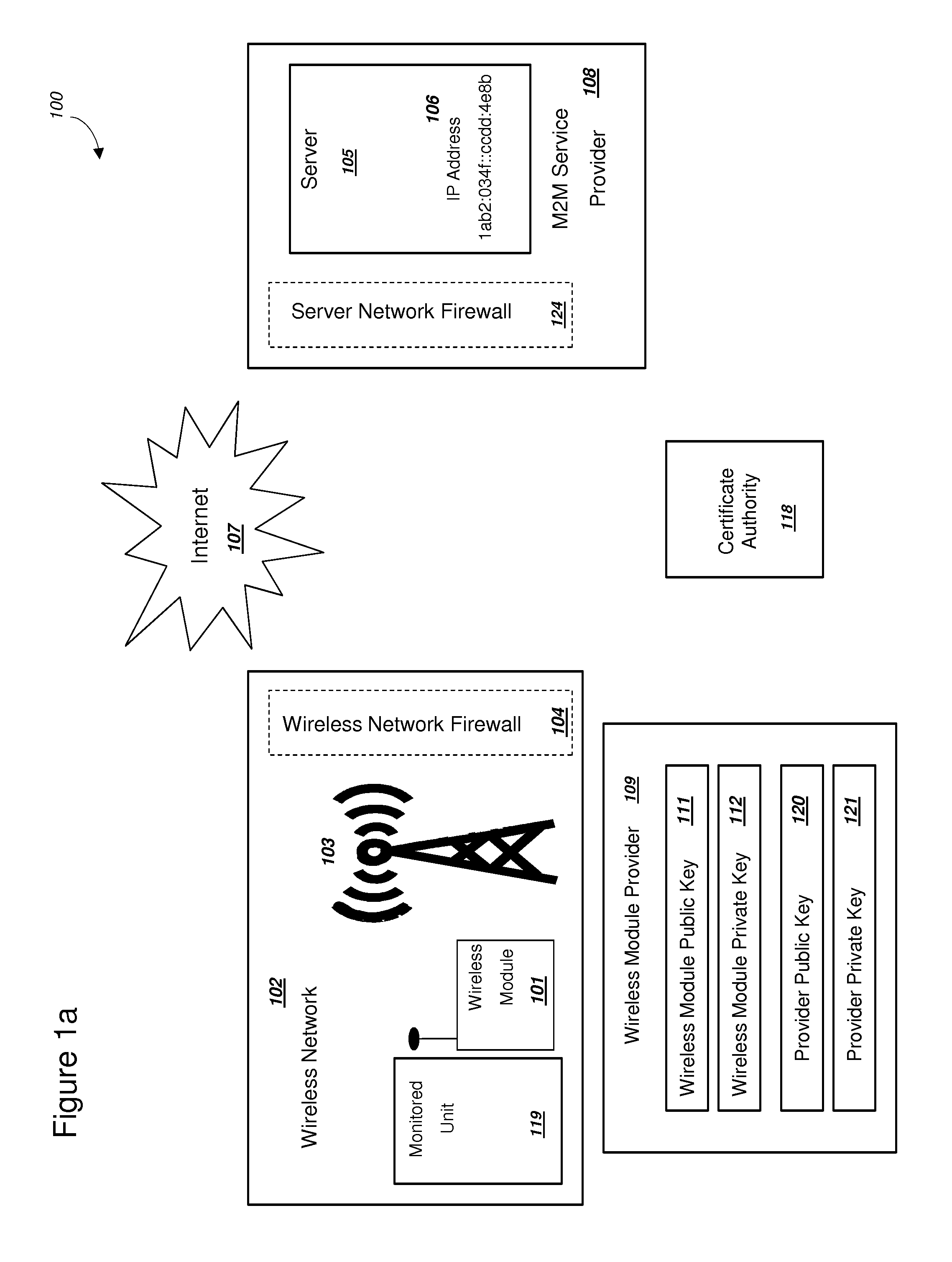
Secure PKI Communications for "Machine-to-Machine" Modules, including Key Derivation by Modules and Authenticating Public Keys
ActiveUS20150095648A1Extend battery lifeImprove efficiencyKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareDigital signature
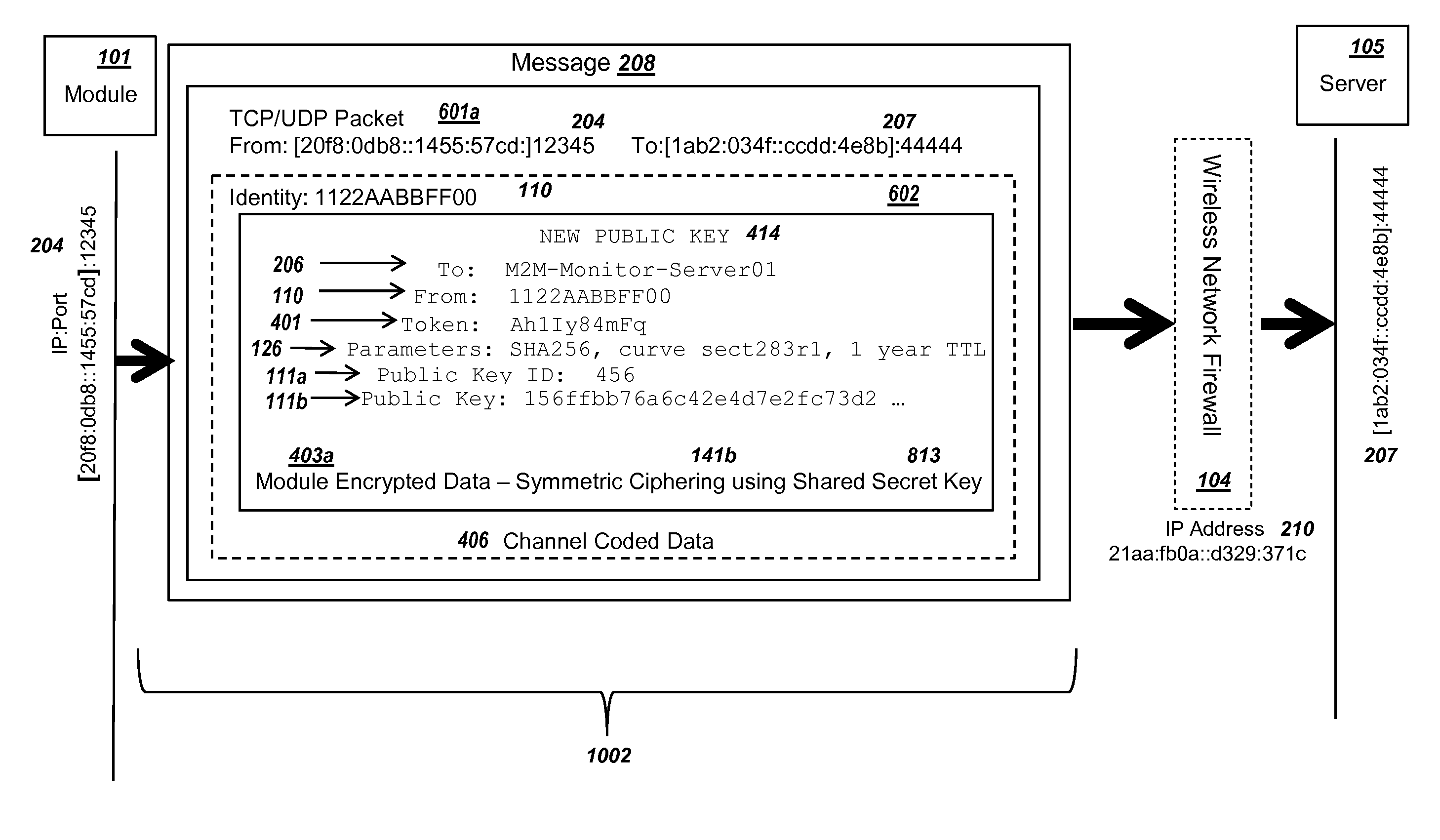
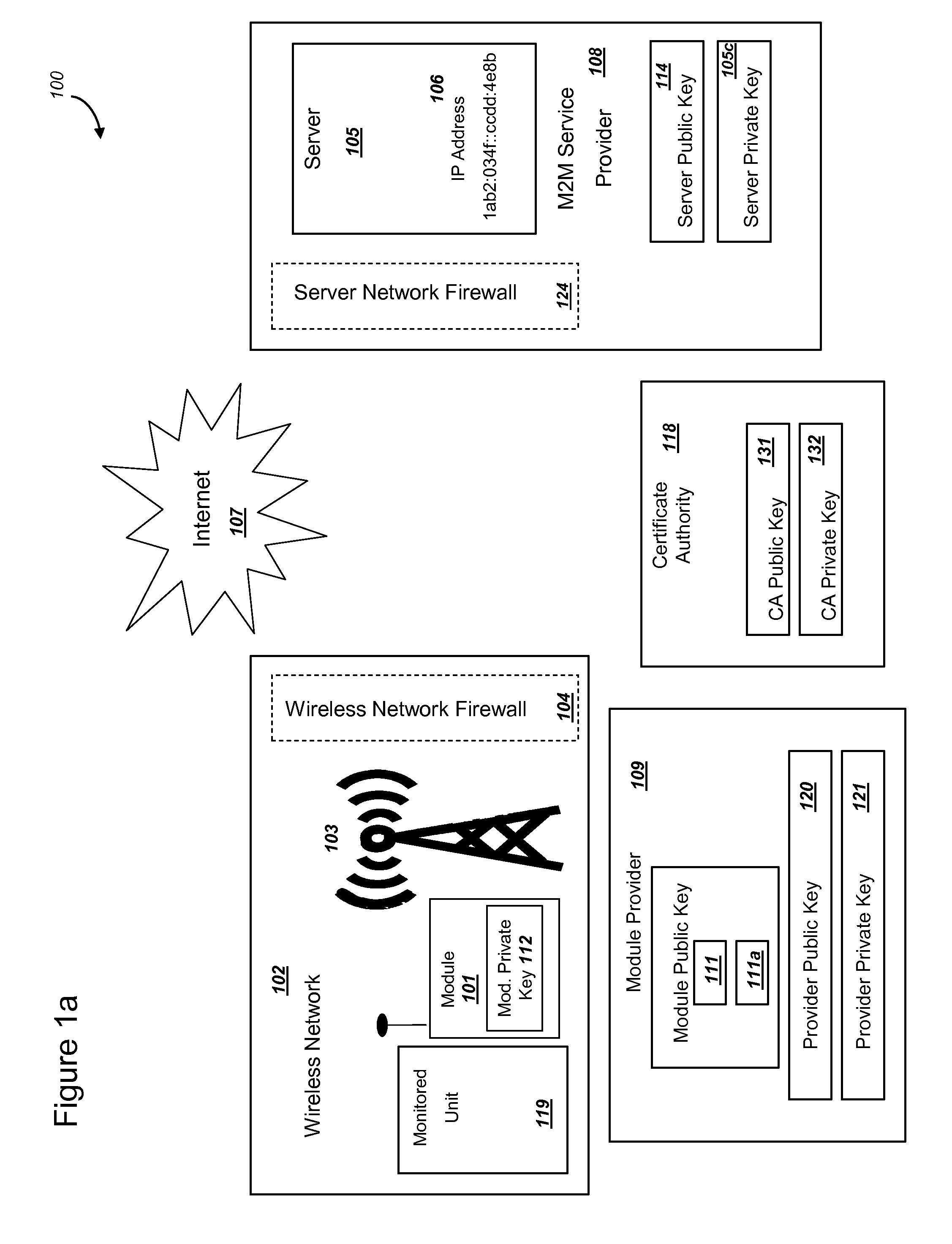
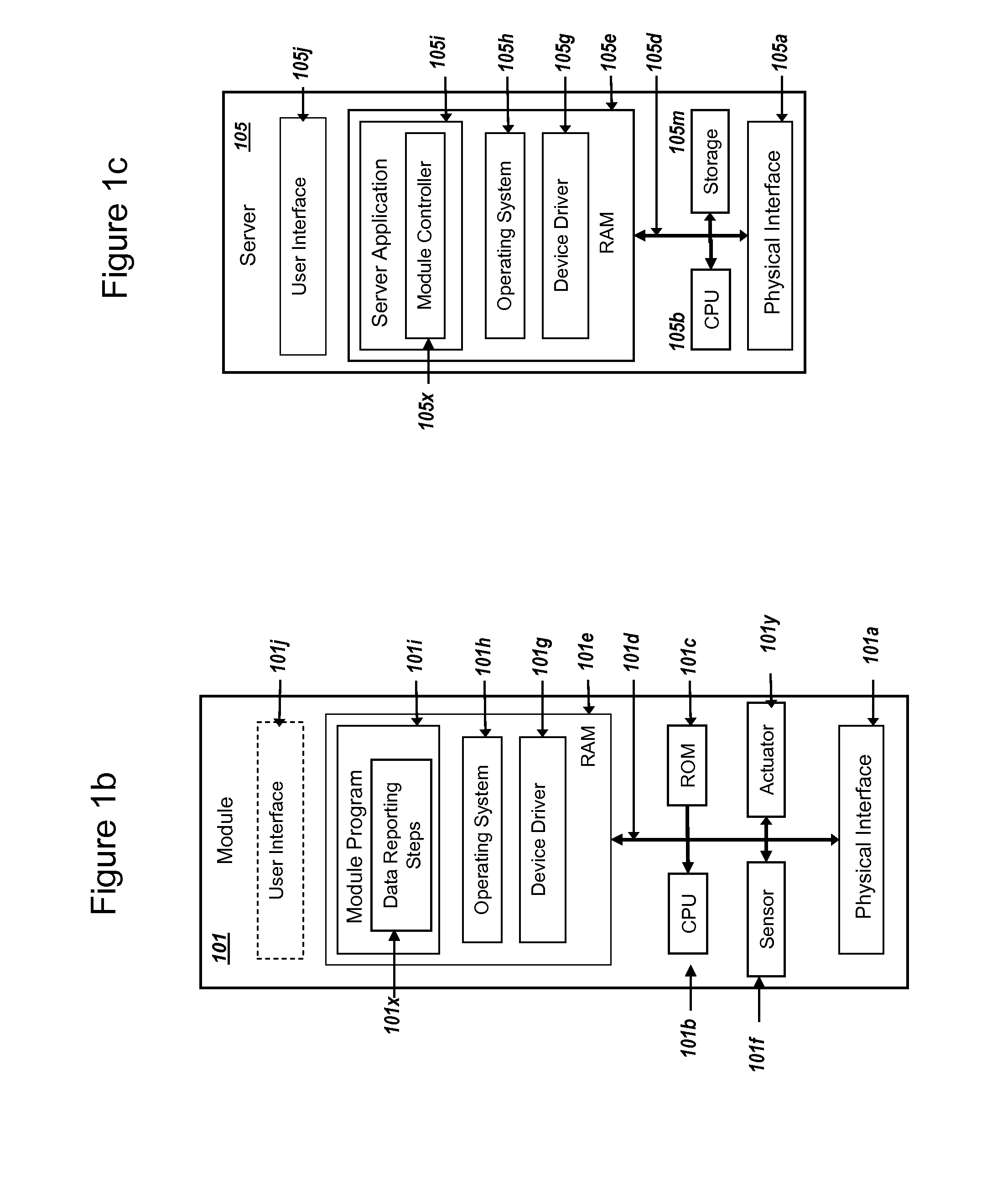
Methods and systems are provided for efficient and secure “Machine-to-Machine” (M2M) between modules and servers. A module can communicate with a server by accessing the Internet, and the module can include a sensor and / or actuator. The module and server can utilize public key infrastructure (PKI) such as public keys to encrypt messages. The module and server can use private keys to generate digital signatures for datagrams sent and decrypt messages received. The module can internally derive pairs of private / public keys using cryptographic algorithms and a set of parameters. A server can use a shared secret key to authenticate the submission of derived public keys with an associated module identity. For the very first submission of a public key derived the module, the shared secret key can comprise a pre-shared secret key which can be loaded into the module using a pre-shared secret key code.
Owner:NETWORK 1 TECH +1
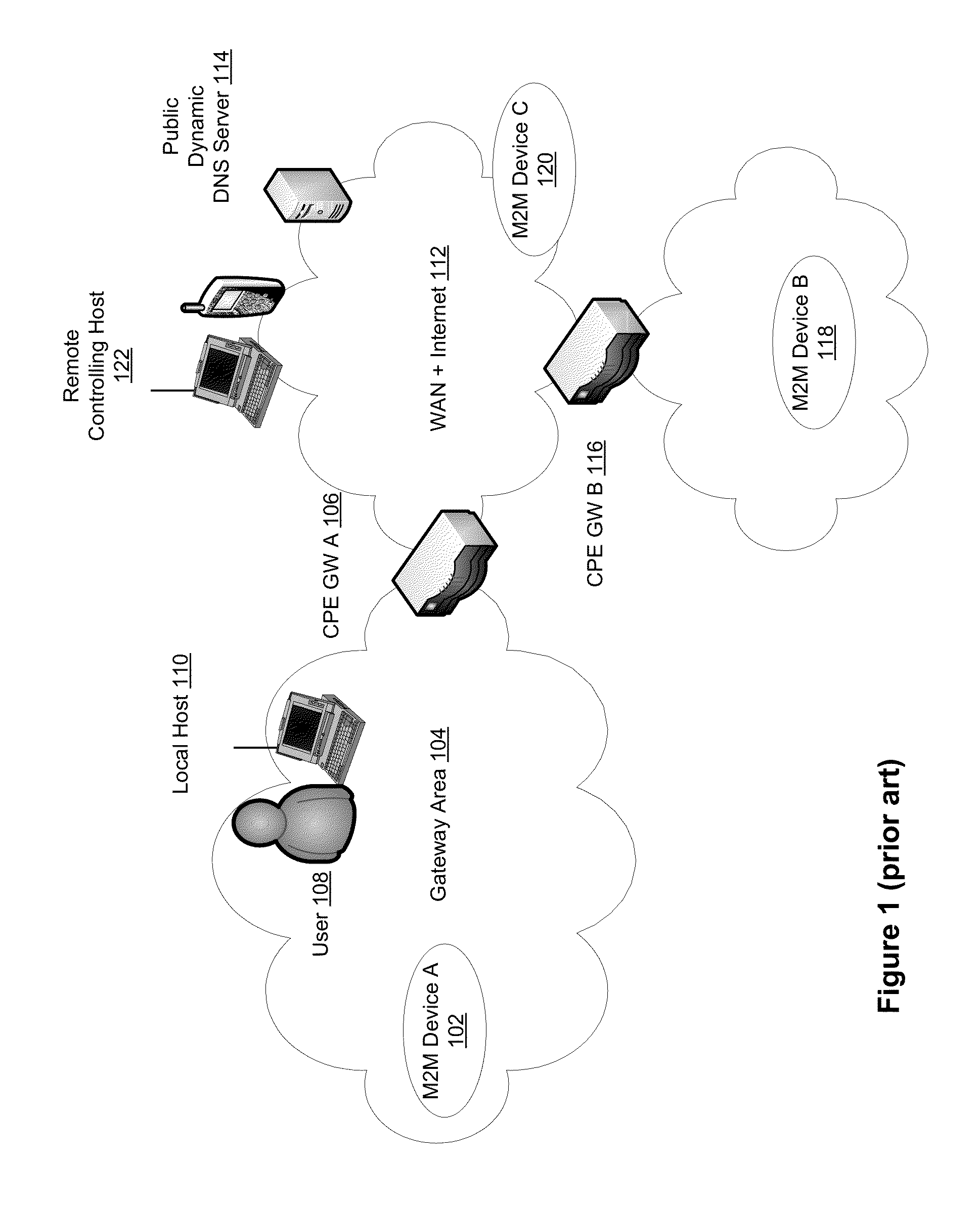
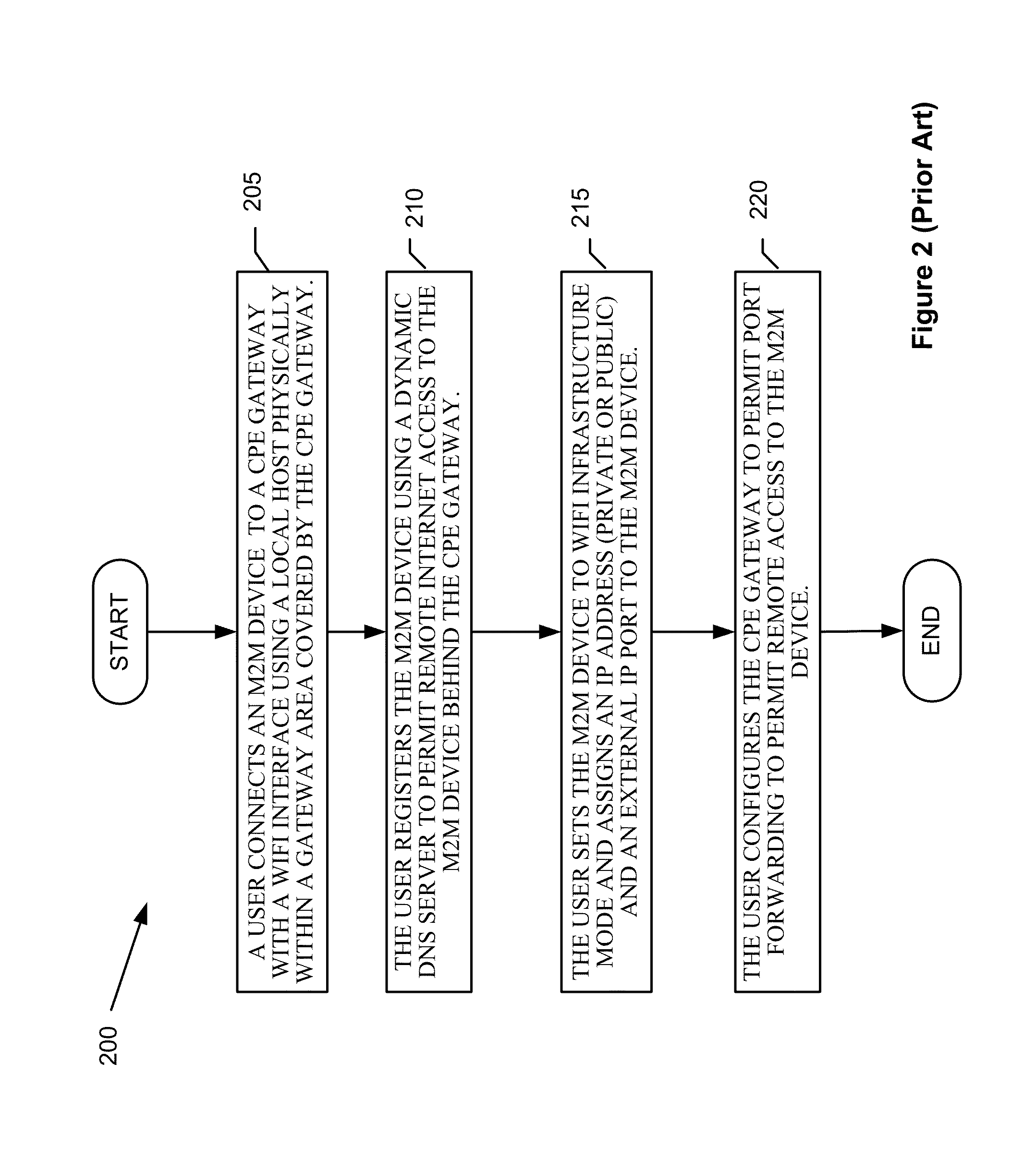
Automatic provisioning of an m2m device having a WIFI interface
InactiveUS20130094444A1Facilitate fast responseService provisioningNetwork topologiesDomain nameFully qualified domain name
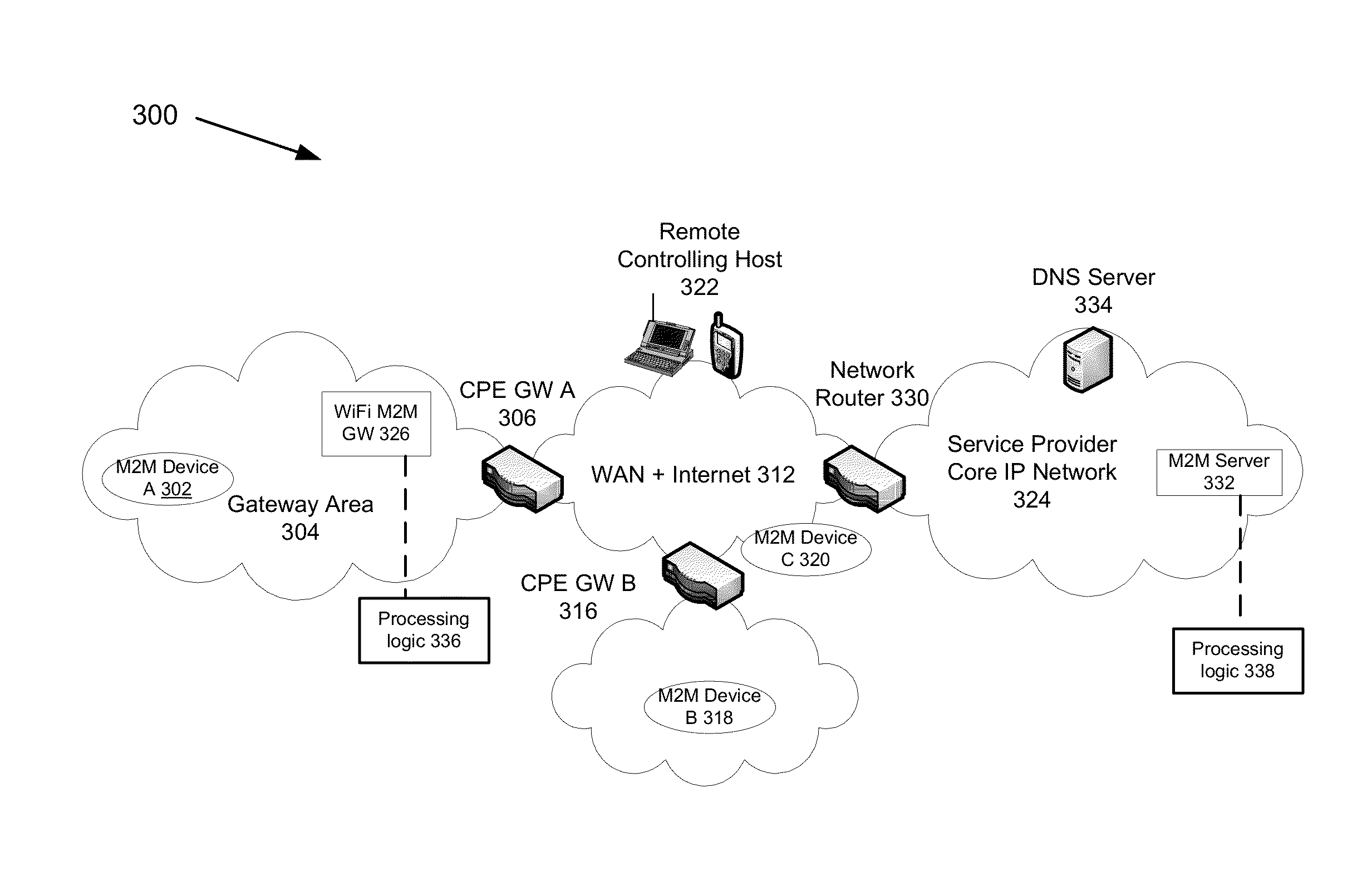
A method for automatically provisioning a WiFi-equipped machine-to-machine (M2M) device is disclosed. A WiFi M2M gateway identifies a WiFi network identifier broadcast by a powered-on M2M device in WiFi ad hoc mode through a scanning procedure and joins the ad hoc network defined by the M2M device. The WiFi M2M gateway obtains device information (e.g., MAC address) of the M2M device. The WiFi M2M gateway transmits a command to the M2M device to switch from ad hoc mode to infrastructure mode. The WiFi M2M gateway registers the M2M device with an M2M server associated with a service provider based on the device information of the M2M device. The WiFi M2M gateway receives a fully qualified domain name (FQDN) associated with the M2M device from the M2M server.
Owner:APPLIED COMMUNICATION SCIENCES
Power Management and Security for Wireless Modules in "Machine-to-Machine" Communications
ActiveUS20150071139A1Efficient power controlExtend battery lifeMultiple keys/algorithms usagePublic key for secure communicationPublic land mobile networkThe Internet
Methods and systems are provided for power management and security for wireless modules in “Machine-to-Machine” communications. A wireless module operating in a wireless network and with access to the Internet can efficiently and securely communicate with a server. The wireless network can be a public land mobile network (PLMN) or a wireless local area network (LAN). The wireless module may include a sensor and may be installed next to a monitored unit. The wireless module may utilize active states for collecting and sending data, and sleep states at other times to conserve a battery and / or energy usage. The wireless module minimize the time spent in a radio resource control (RRC) connected state. Messages between the wireless module and server can be transmitted according to a user datagram protocol (UDP). The wireless module and server can utilize public key infrastructure (PKI) for encryption and digital signatures.
Owner:NIX JOHN A +1
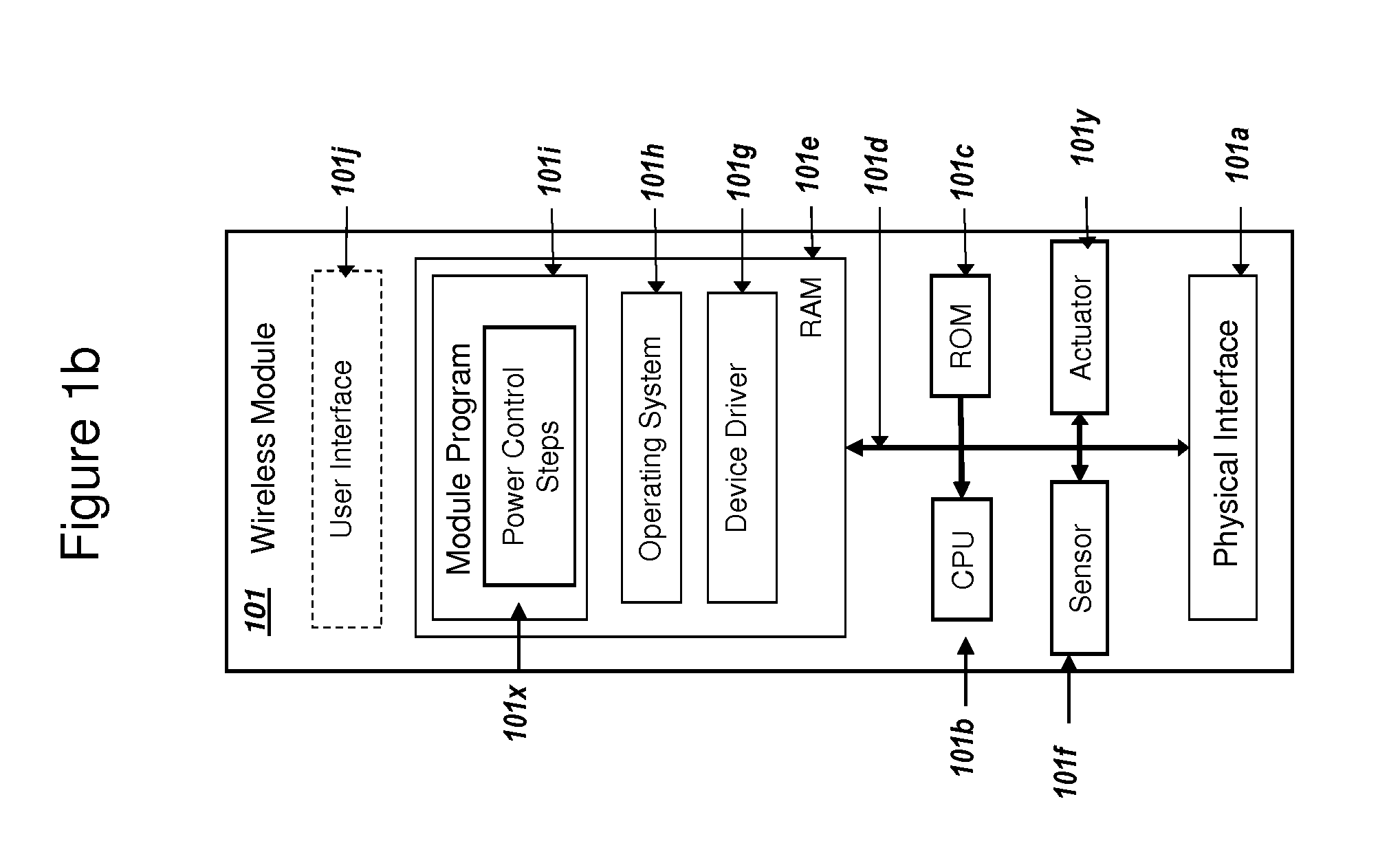
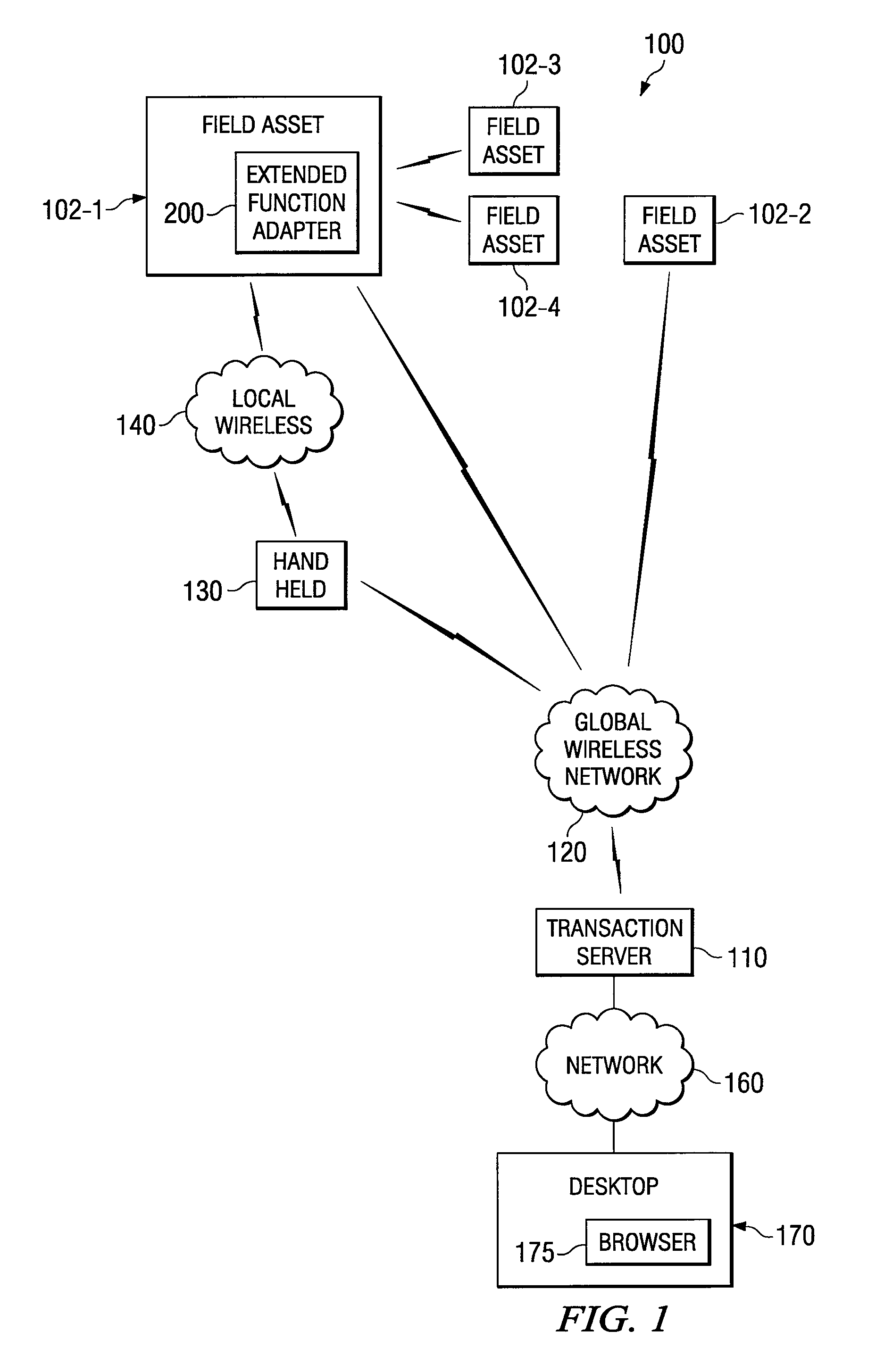
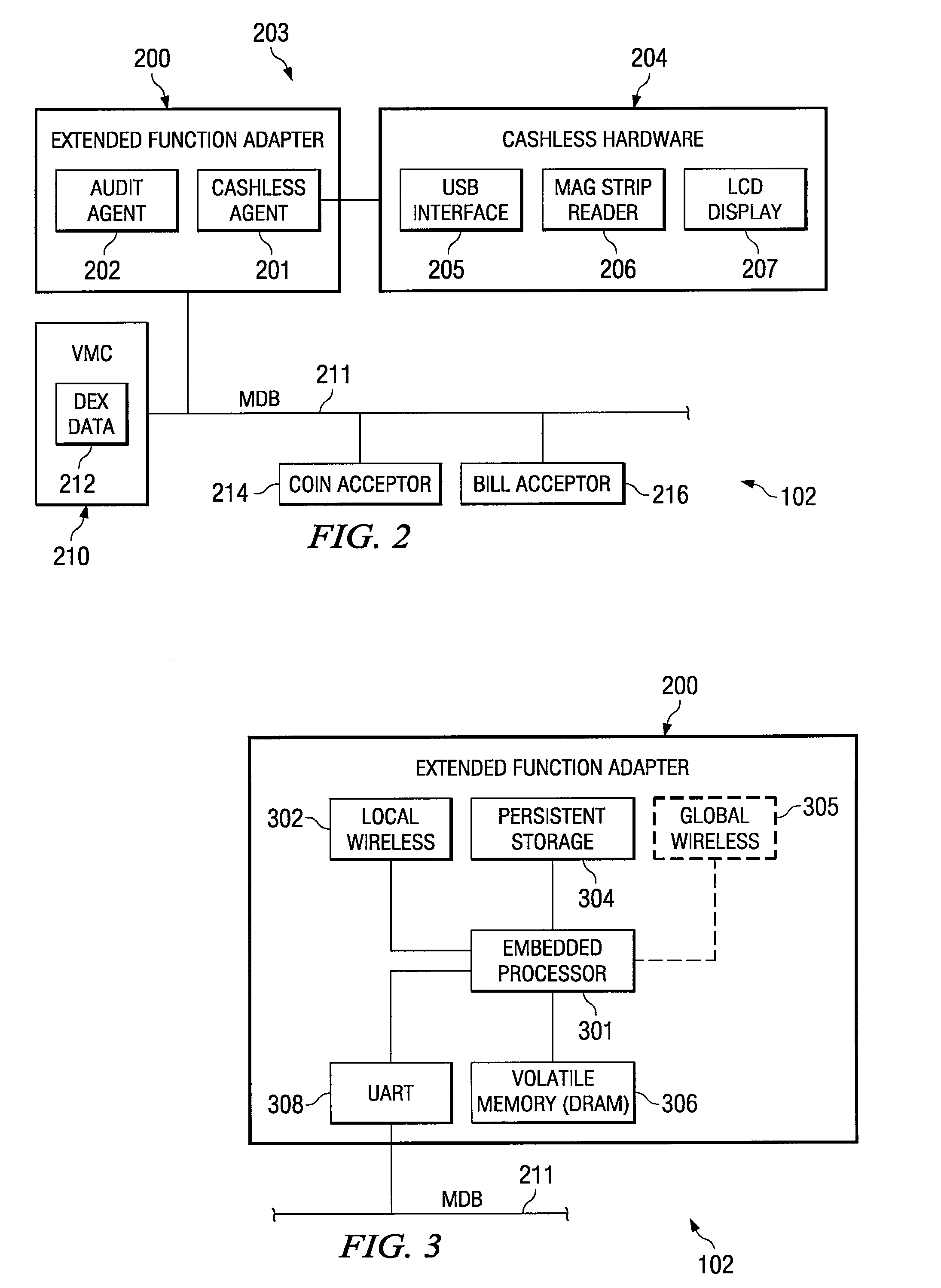
Processing Cashless Transactions of Remote Field Assets
InactiveUS20070187491A1Convenient transactionFast and reliable and inexpensiveFinanceVerifying markings correctnessFinancial transactionCard reader
A field asset for use in a machine to machine environment that includes a plurality of field assets in communication with a remote transaction processing server may comprise a card reader and an extended function adapter (EFA). The card reader may detect a cashless payment card presented to the card reader and the EFA may facilitate a cashless transaction in response to presentment of the cashless payment card to the card reader. The EFA may be operable to locally authorize the cashless transaction based on locally stored transaction information if said field asset lacks connectivity to the remote transaction processing server and may further be operable to remotely authorize the cashless transaction based on remotely stored transaction information if the field asset has connectivity to the remote transaction processing server.
Owner:CRANE MERCHANDISING SYSTEMS
Automated Security Provisioning Protocol for Wide Area Network Communication Devices in Open Device Environment
ActiveUS20110016321A1User identity/authority verificationNetwork topologiesSecure communicationCommunication device
An automated security provisioning protocol is provided for wide area network communication devices in an open device environment, such as cellular communication devices in a machine-to-machine (M2M) environment. For example, a method for performing a security provisioning protocol between a first communication device and a second communication device over at least one wide area communication network comprises the following steps from the perspective of the first communication device. The first communication device automatically uses access information not previously provisioned in the wide area communication network to gain access to the wide area communication network for an initial purpose of communicating with the second communication device. The first communication device, upon gaining access to the wide area communication network, automatically performs an authenticated key exchange operation with the second communication device over the wide area communication network and establishes a secure communication key as a result of the authenticated key exchange operation for subsequent use by the first communication device for secure communications. The wide area communication network is operated by a first entity and the second communication device is operated by a second entity.
Owner:ALCATEL LUCENT SAS
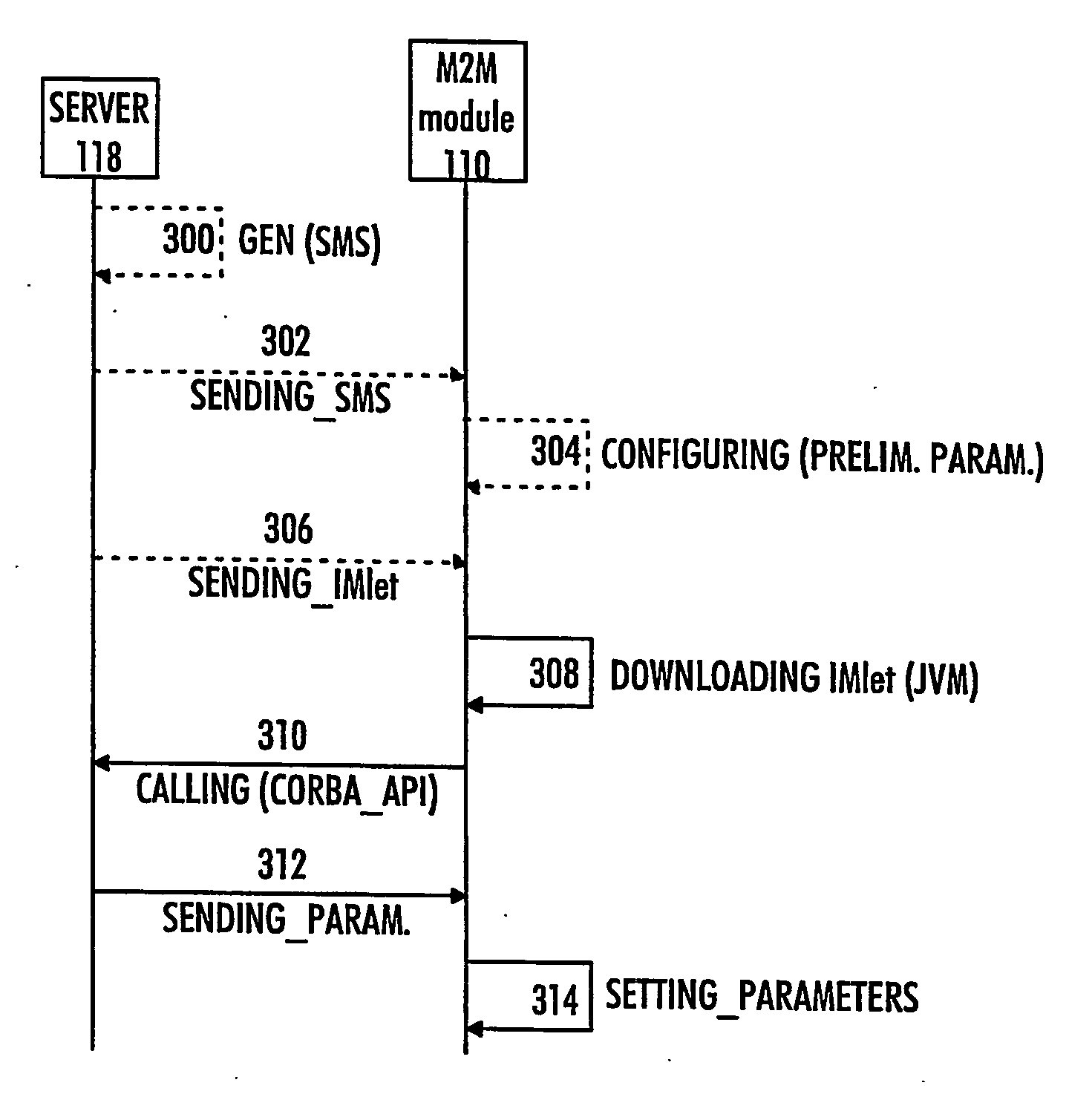
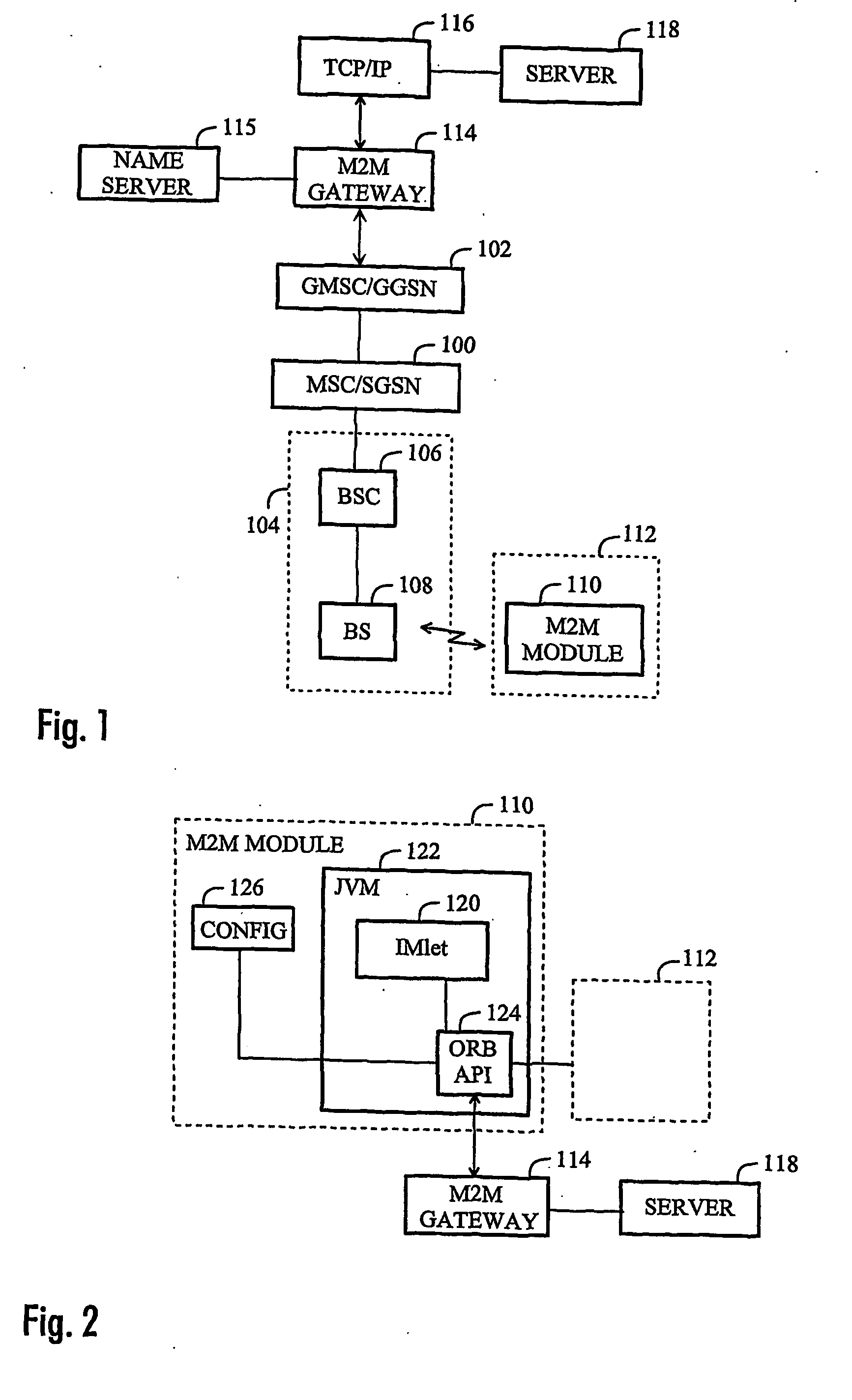
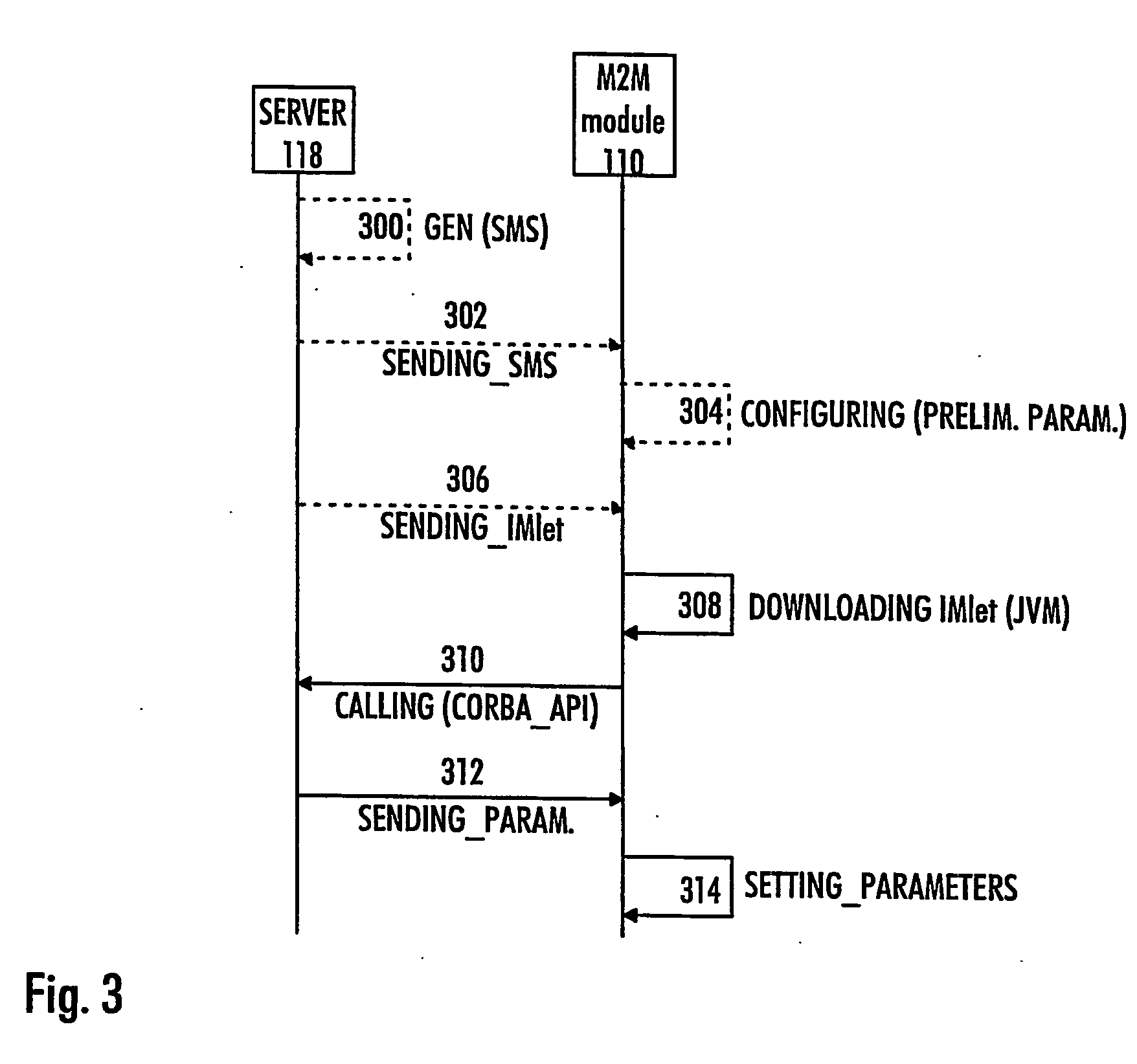
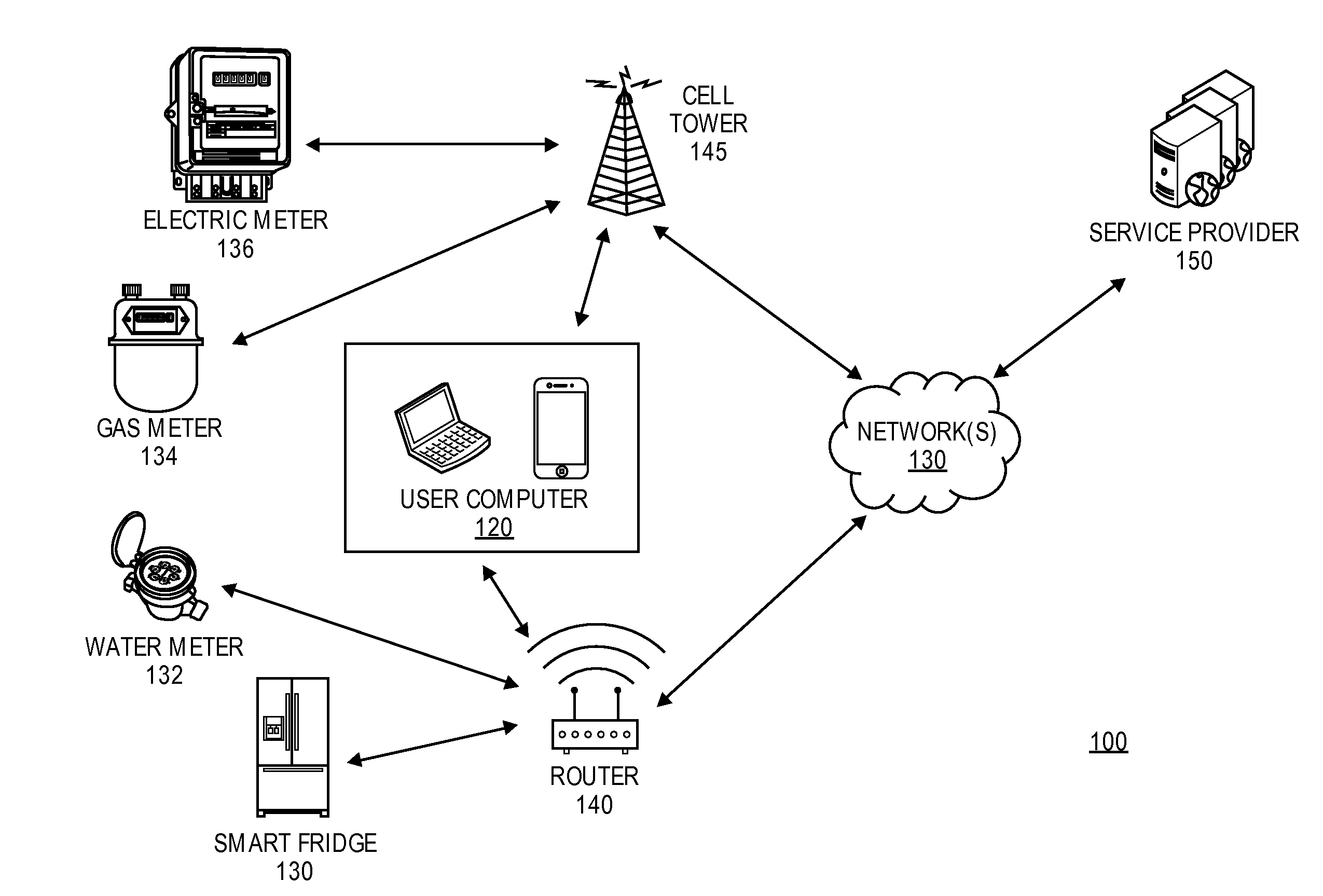
Method of configuring parameters of machine-to-machine module and machine-to-machine module
InactiveUS20070169107A1Services signallingProgram loading/initiatingApplication programming interfaceJava virtual machine
The invention relates to an M2M (machine-to-machine) module and to a method of configuring parameters of an M2M module, the method comprising establishing a connection between the M2M module and a server. The method comprises: downloading, to the M2M module, an application having an application programming interface (API) for configuring the M2M module, the application being configured to run on a Java virtual machine (JVM); communicating with the server by the application for receiving configuration parameters; and setting the parameters of the M2M module by the application based on the received configuration parameters.
Owner:NOKIA CORP
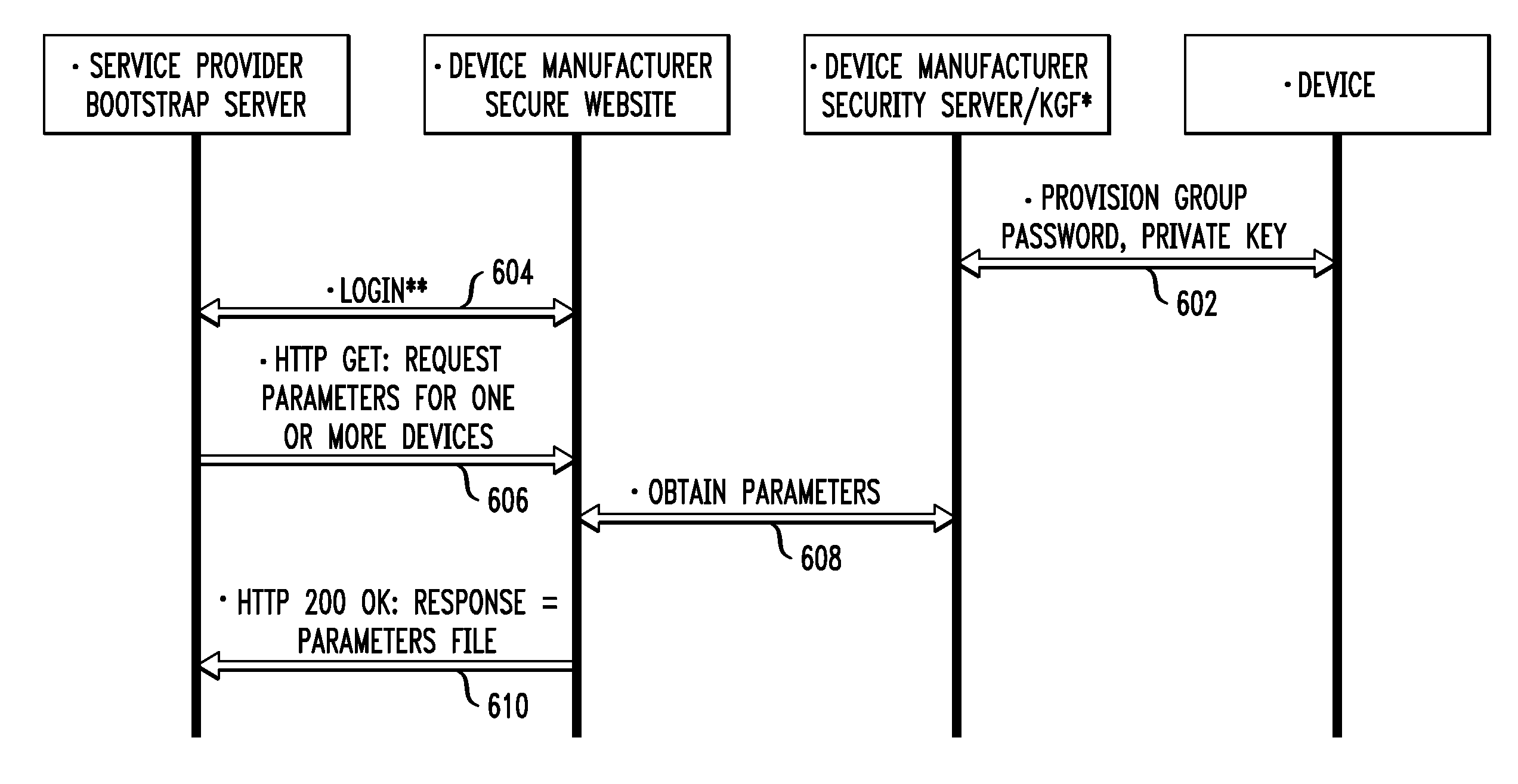
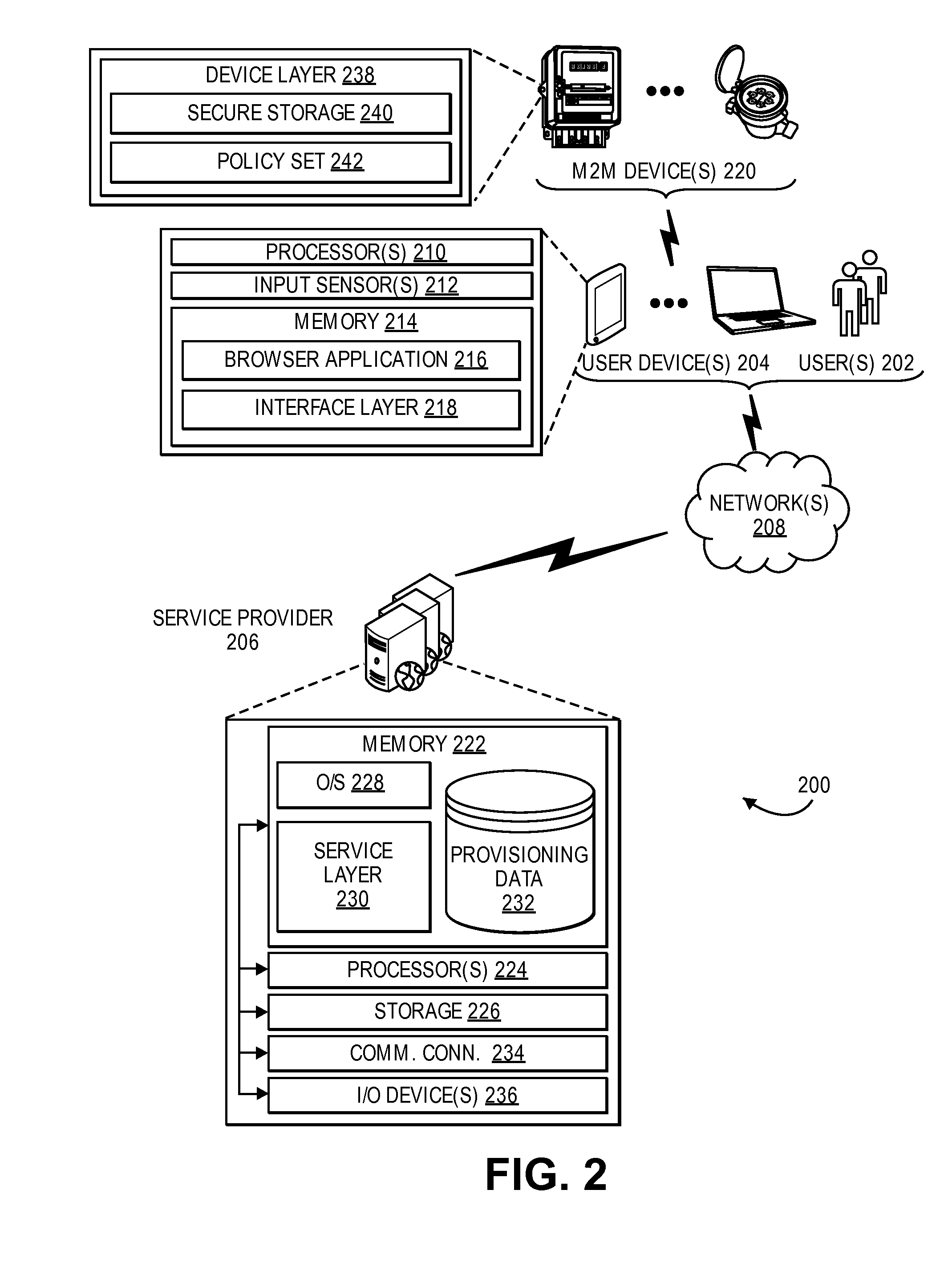
Provisioning platform for machine-to-machine devices
Techniques described herein include a platform and process for provisioning user information onto a machine-to-machine device in order to enable the machine-to-machine device to conduct transactions utilizing the user information. In some embodiments, a user device is used to relay information between a machine-to-machine device and a provisioning service provider computer. In some embodiments, a machine-to-machine device is connected to the provisioning service provider computer via a network connection. Upon receiving a request to provision the machine-to-machine device, the service provider computer may identify the device from a device identifier. The service provider computer may generate an access credential or token for the machine-to-machine device. The access credential, token, and / or one or more policies may be provisioned onto the machine-to-machine device.
Owner:VISA INT SERVICE ASSOC
Method and apparatus for implementing access to machine to machine (M2M) core ntework
ActiveUS20120287854A1Assess restrictionWireless commuication servicesTerminal equipmentComputer terminal
The present invention discloses a method and an apparatus for implementing an access to a Machine to Machine (M2M) core network. In the method, a network element receives an access request message carrying equipment identity indication information, wherein the access request message is initiated by terminal equipment; the network element determines that the terminal equipment is M2M equipment according to the equipment identity indication information; and the network element selects a corresponding M2M core network for the terminal equipment to implement the access of the terminal equipment. According to the technical solution provided by the present invention, the existing network can meet the M2M service requirement while providing services for existing Human to Human (H2H) equipment, without any need of enhancement and mass expansion.
Owner:ZTE CORP
Apparatus, method and system for providing machine-to-machine applications development
ActiveUS20160055573A1Buying/selling/leasing transactionsSoftware deploymentSoftware engineeringApplication software
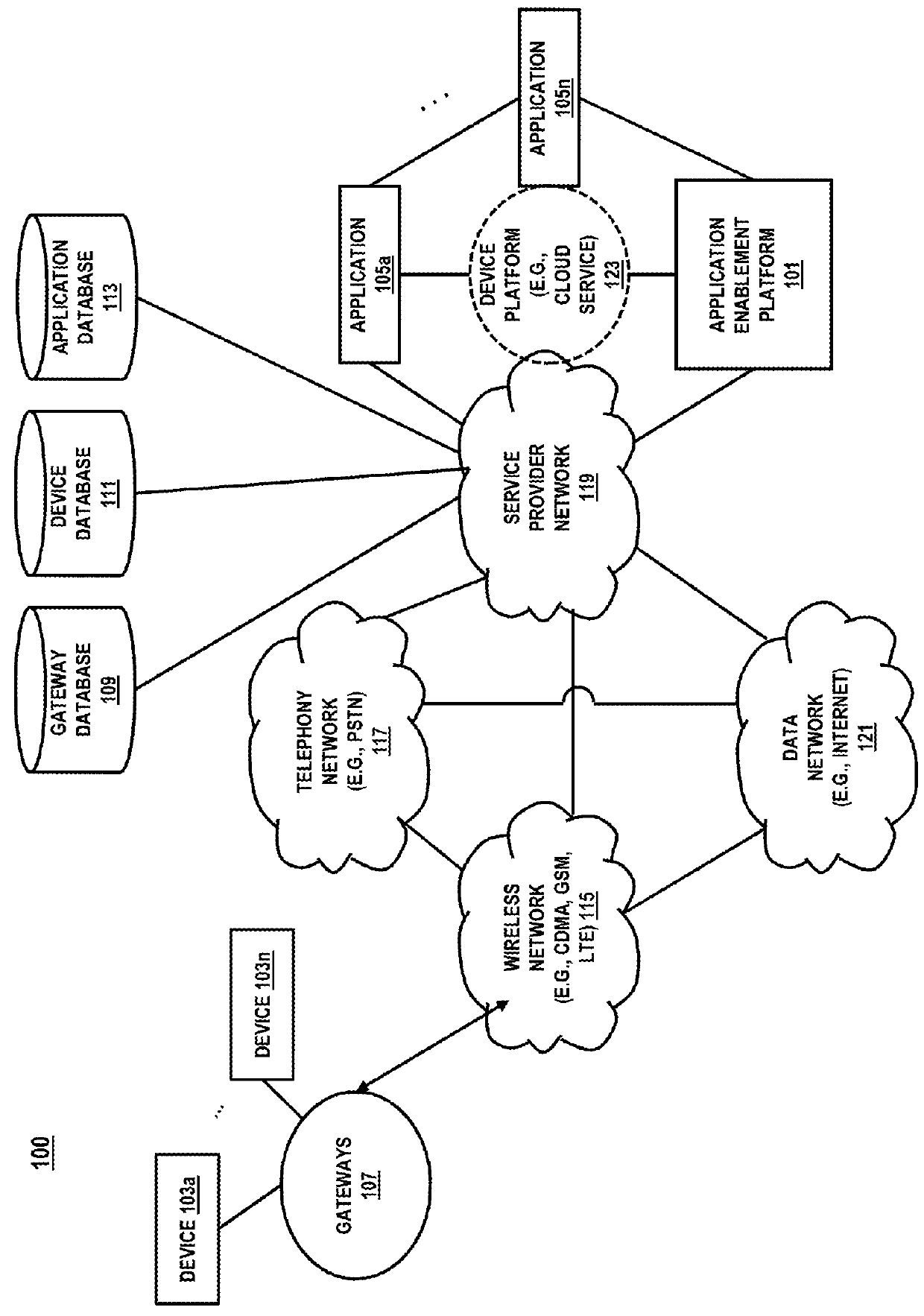
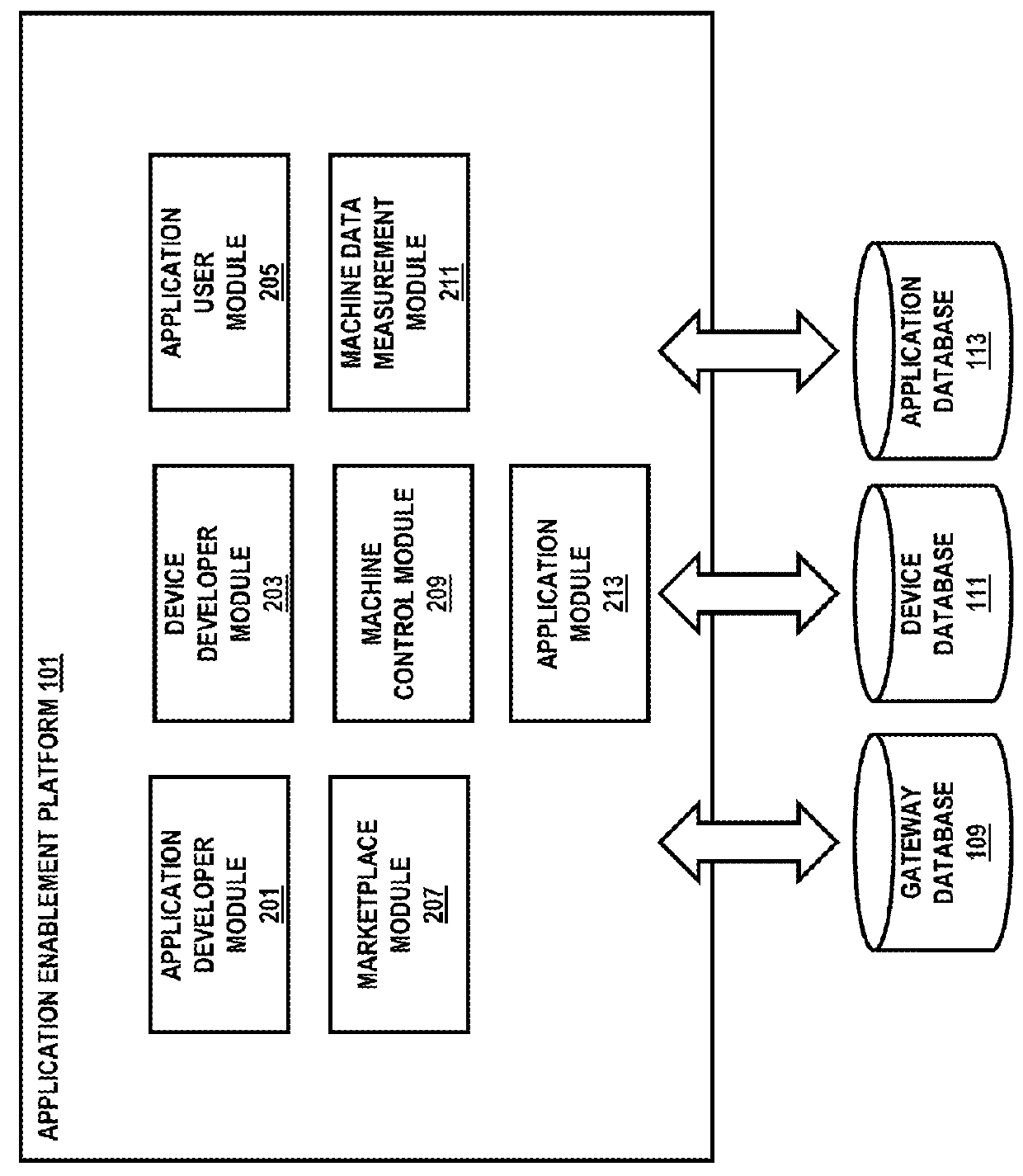
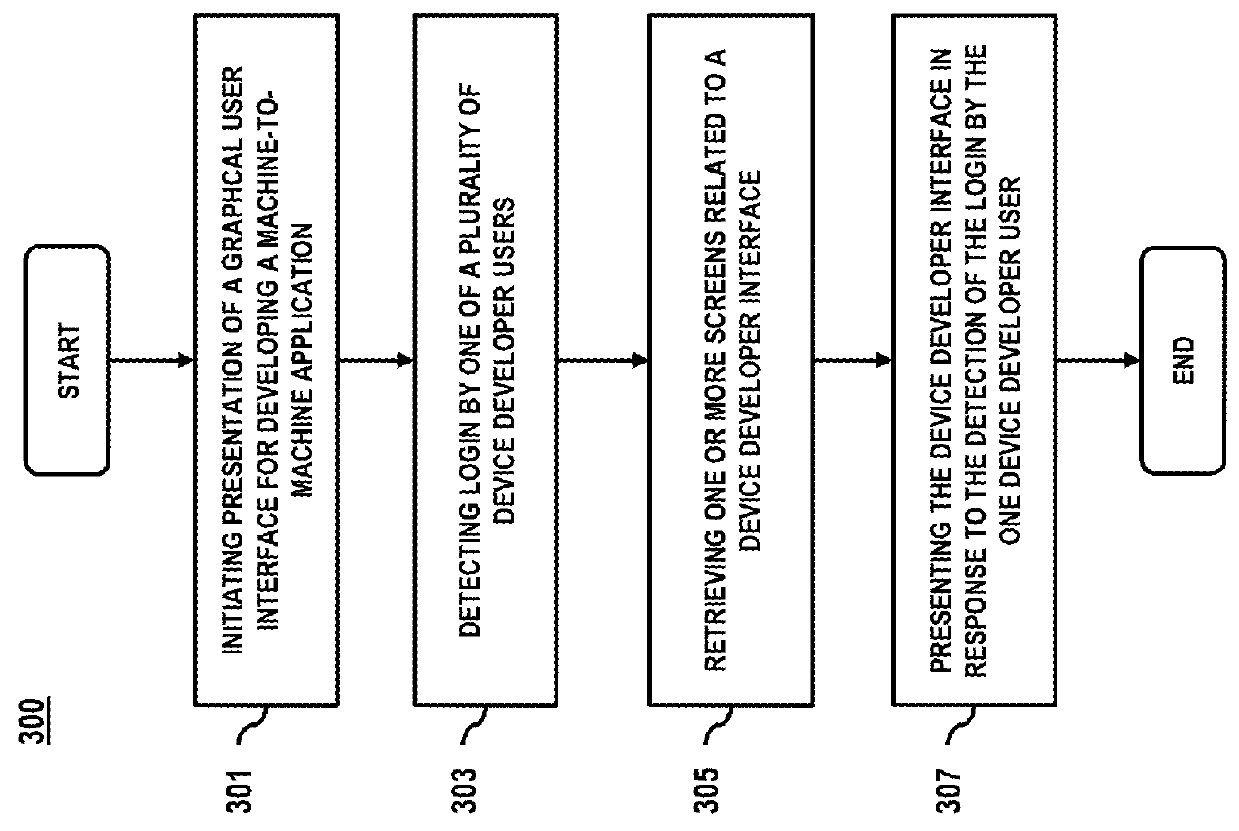
A framework for a machine-to-machine (M2M) application development is disclosed. The framework enables users to login and affect devices and applications that may interact with the devices by enabling M2M applications. The framework enables M2M application creation, management, and development of various profiled devices based on pre-defined data models associated with corresponding devices. Furthermore, the framework enables marketplace options to permit users to specify purchase options as well as to buy devices and applications.
Owner:VERIZON PATENT & LICENSING INC
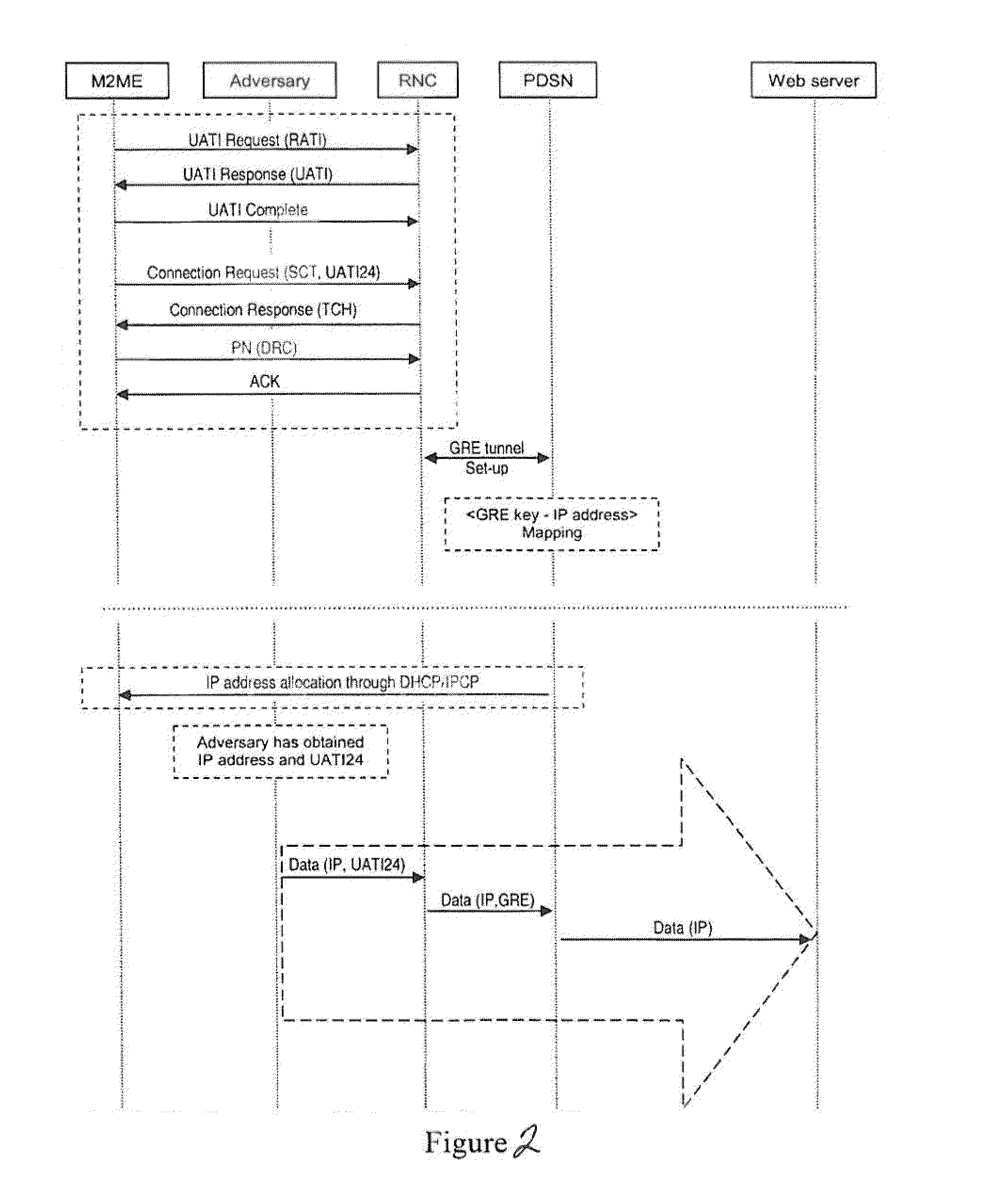
Detection And Prevention Of Machine-To-Machine Hijacking Attacks
InactiveUS20130291100A1Well formedMemory loss protectionError detection/correctionPacket forwardingMachine to machine
An example method includes receiving at a network node a packet destined for an intended destination. The network node determines whether the packet is associated with a machine-to-machine communication. The network node determines whether forwarding of the packet to the intended destination is prohibited, wherein forwarding of the packet is prohibited when the packet is originated from a first machine-to-machine device and is destined to a first host other than a machine-to-machine server associated with machine-to-machine communications. The network node forwards the packet to the intended destination when forwarding the packet is not prohibited.
Owner:ALCATEL LUCENT SAS
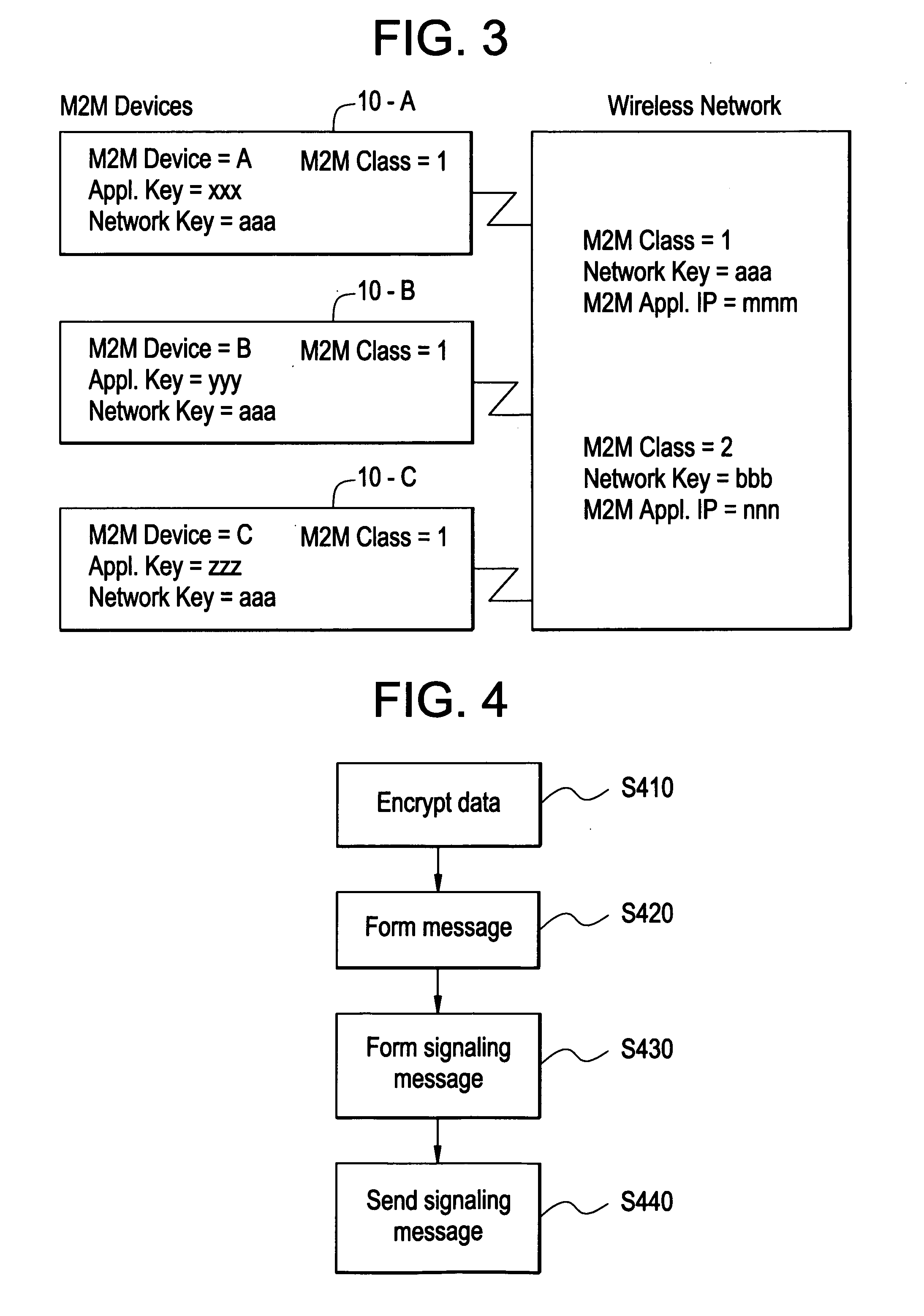
Method of machine-to-machine communication
In one embodiment, the method includes encrypting, at a device, data with a first key, and forming a message that includes a device identifier and the encrypted data. The device identifier identifies the device. A signaling message is formed that includes a class identifier, the message and an action code. The class identifier identifies a group of devices to which one or more devices belong. The action code indicates the type of data, and may be part of the message. The signaling message is sent to a network, for example, a wireless network. The wireless network identifies and routes the message portion of the signaling message based on the class identifier. And, using the class identifier and perhaps a device identifier, the wireless network may signal the device to change an operating parameter.
Owner:GEMPLU
Distributed Hybrid Virtual Media and Data Communication System
ActiveUS20120290702A1Low costHigh maintenance costInterprogram communicationDigital computer detailsAdaptive servicesCommunications system
Novel methods and systems for construction a distributed adaptive server computing network system. Virtual Appliance platforms of a network service server are configured on a local computer of a registered user. Machine to machine communication channels are established through the Virtual appliance platforms and the local computer of the user is enabled to function as a part of the network service server. Direct streaming communications between users are enabled.
Owner:OUTTA THE CLOUD LLC
M2M user equipment as well as operation control method and system thereof
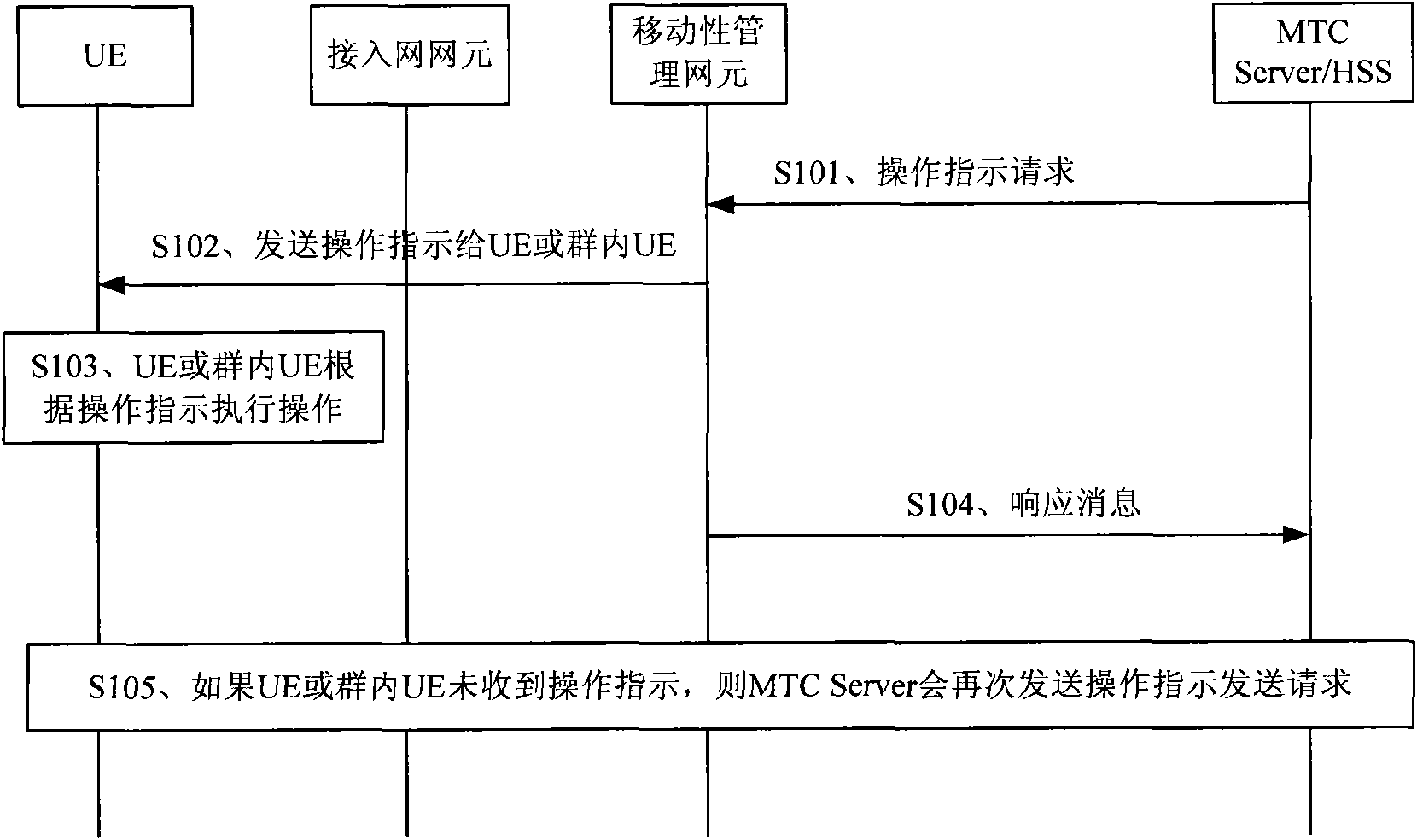
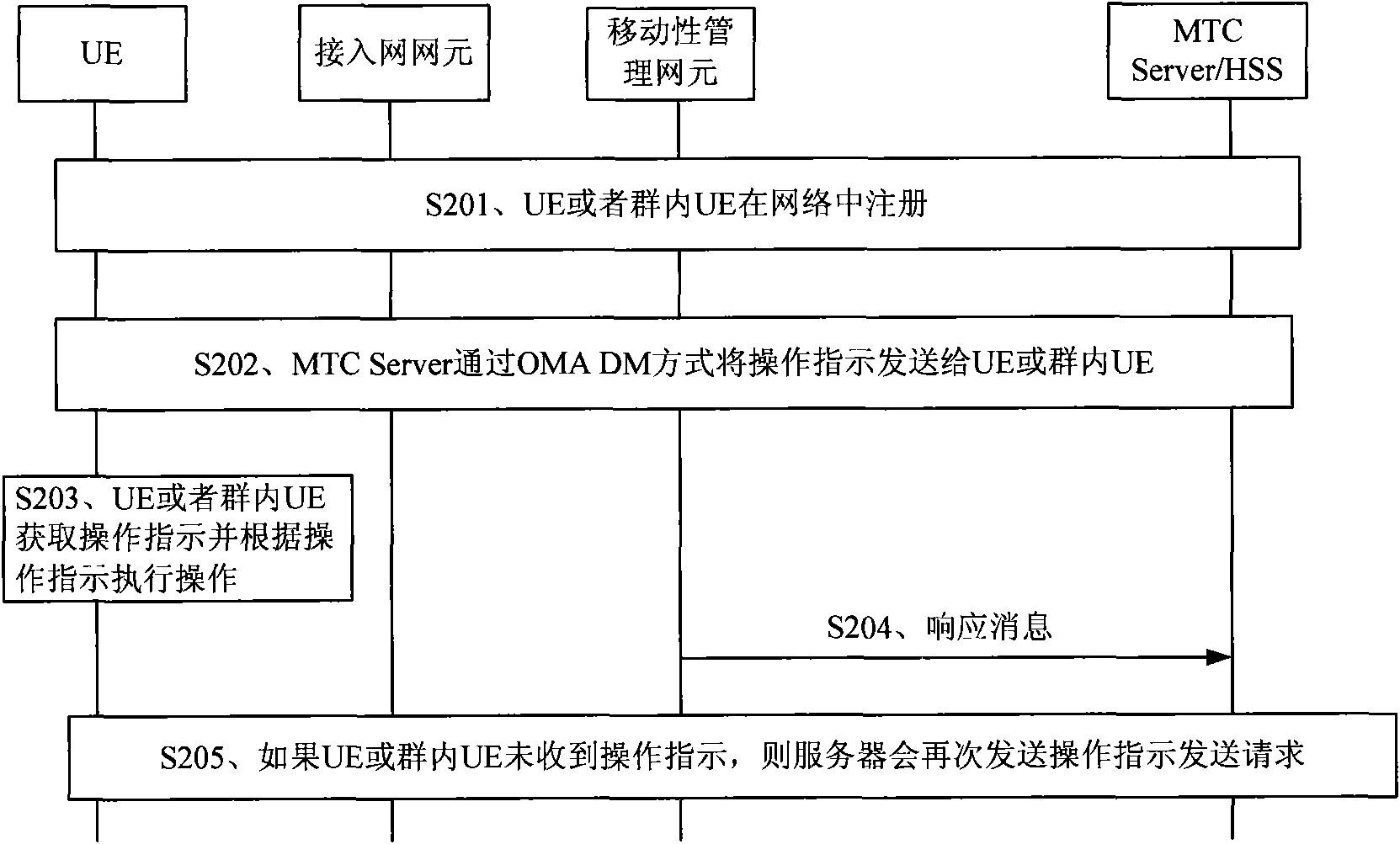
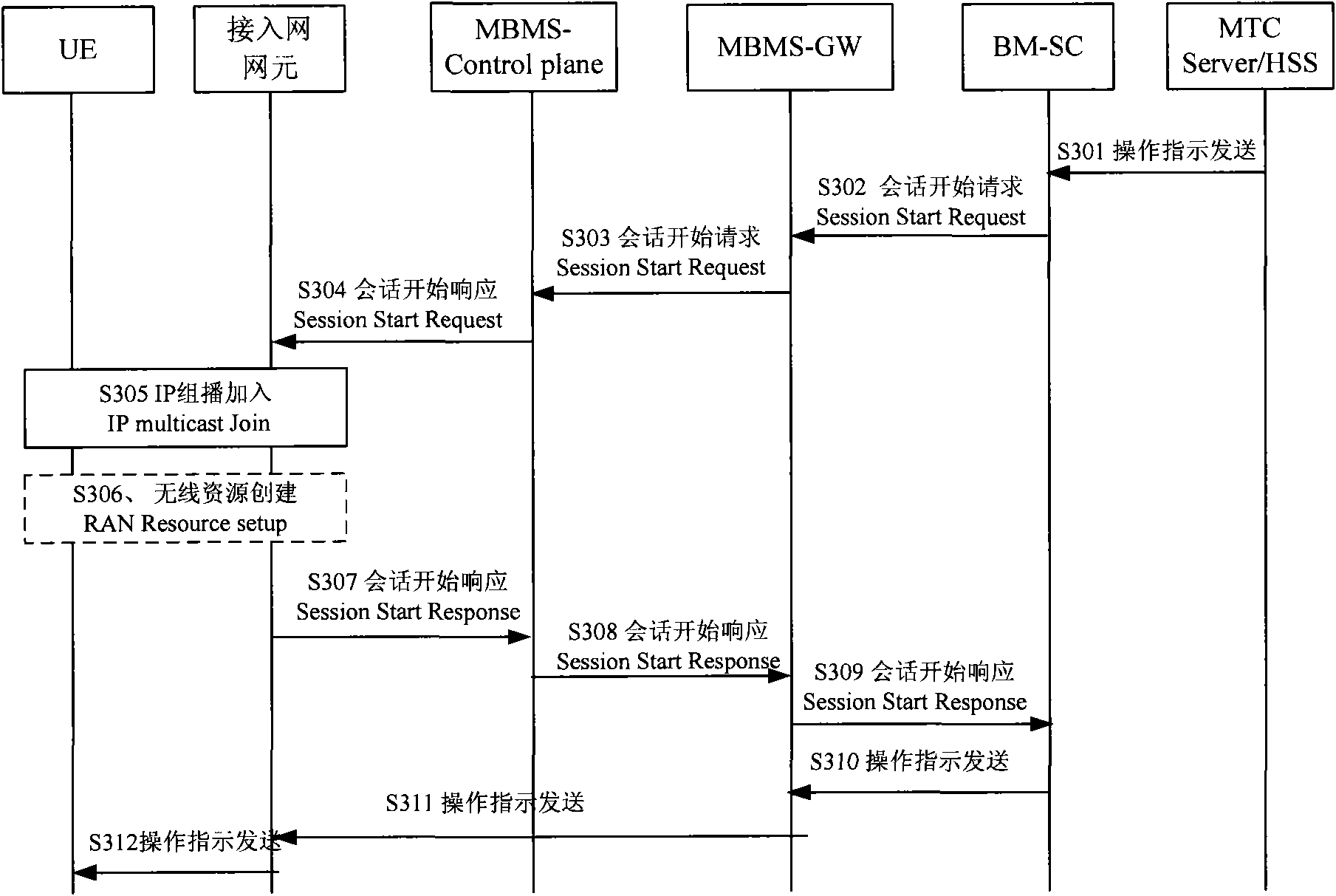
InactiveCN101959133AImprove resource utilizationReduce shockBroadcast service distributionWireless commuication servicesControl systemBusiness data
The embodiment of the invention discloses an operation control method for a M2M user equipment applied in machine to machine, which comprises the steps of: receiving information including operation instructions and sent from a network side, wherein the operation instructions comprise at least one of the instructions of indicating a user equipment UE or a group UE to register, activating signed data and transmitting business data; and operating the user equipment UE or the group UE according to the received operation instruction. The embodiment of the invention also provides corresponding user equipment, a corresponding server and a corresponding control system. In the embodiment of the invention, the user equipment is controlled by the network side to perform operation, the UE can be indicated to register, activate the signed data or transmit the business data at any time, the UE or the group UE can be in a dormant state or the state of going to register, and the impact and the influence from a large number of user equipment UE on the network side can be reduced so as to greatly improve the utilization ratio of network resources, meet the current M2M application and provide convenient and effective services for operators and users.
Owner:HUAWEI TECH CO LTD
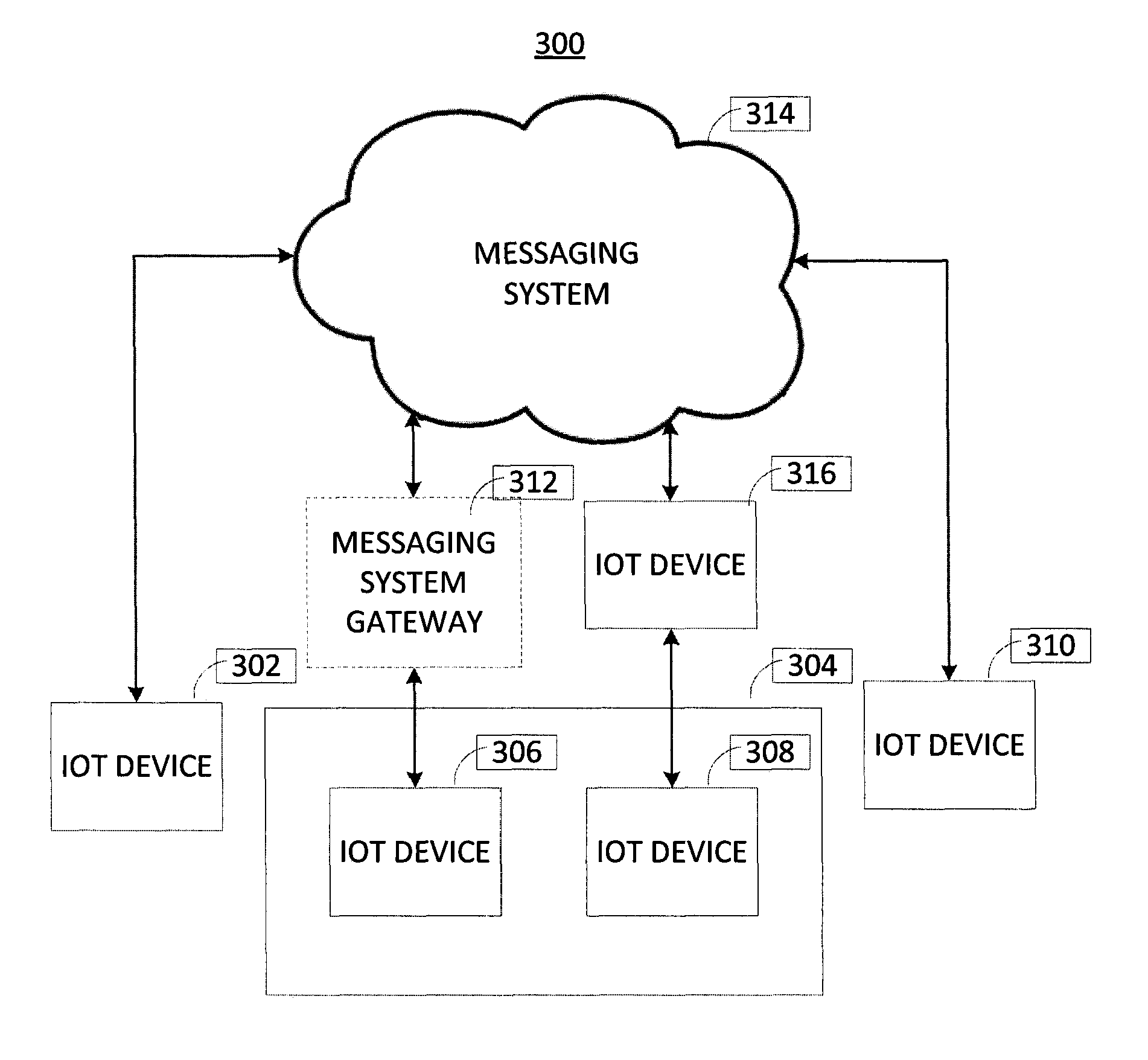
Location assistance in a machine to machine instant messaging system
ActiveUS9210534B1Multiple digital computer combinationsWireless commuication servicesCloud computingTransmitter
A cloud computing messaging system for location-based searching for Internet of Things (IoT) devices includes data processors, a receiver, and a transmitter. The system includes a storage medium containing instructions for the processors to receive a communication from a first IoT device connected with the system using a first protocol. The communication includes a location query and is received using the first protocol. The processors determine a second IoT device having a location that matches the location query. The second IoT device is connectable using a second protocol. The processors transmit information to the first IoT device related to the second IoT device and is transmitted using the first protocol. The processors receive a transmission from the first IoT device for the second IoT device using the first protocol, translate the transmission to the second protocol, and transmit the translated transmission to the second IoT device using the second protocol.
Owner:CITRIX SYST INC
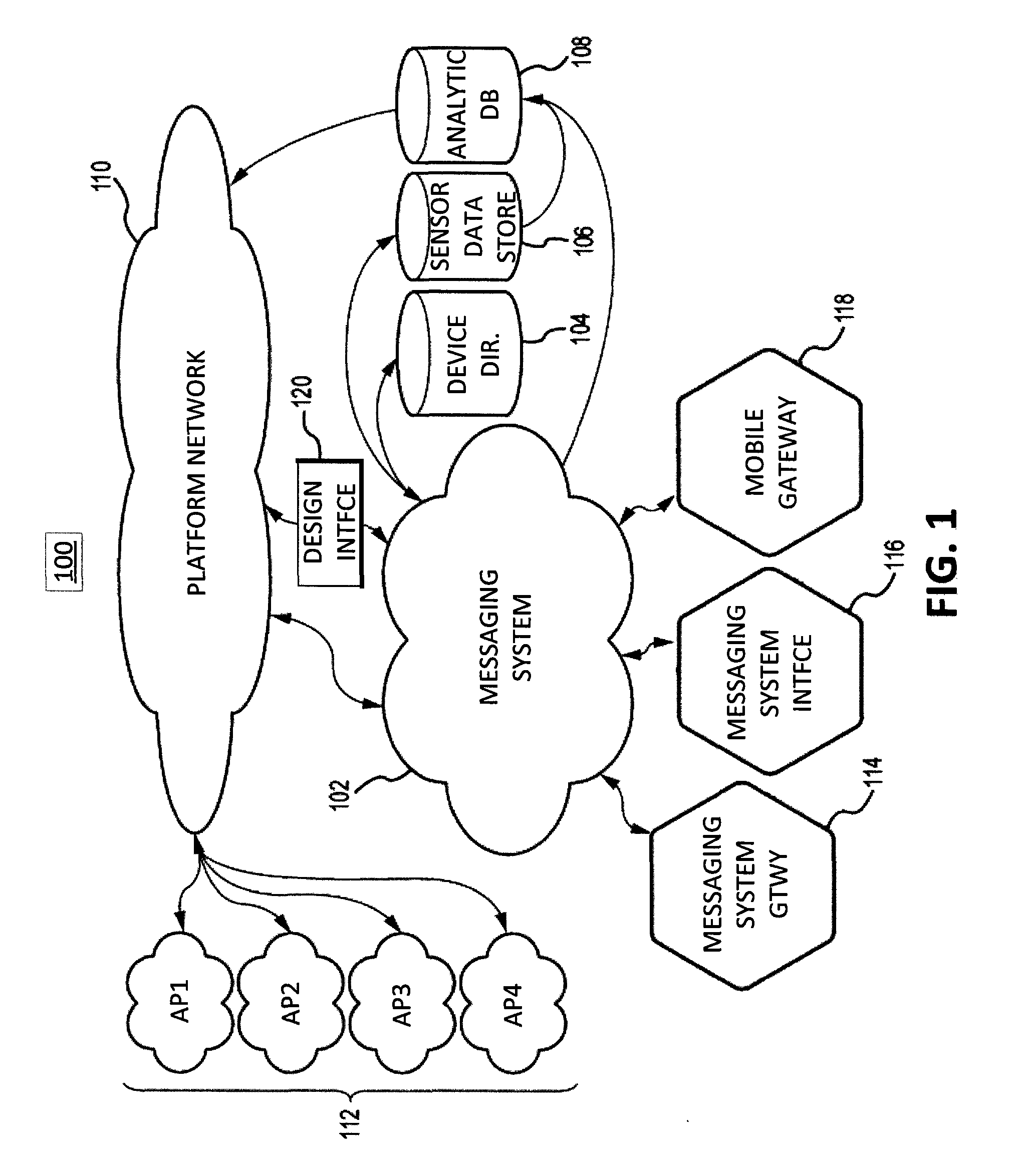
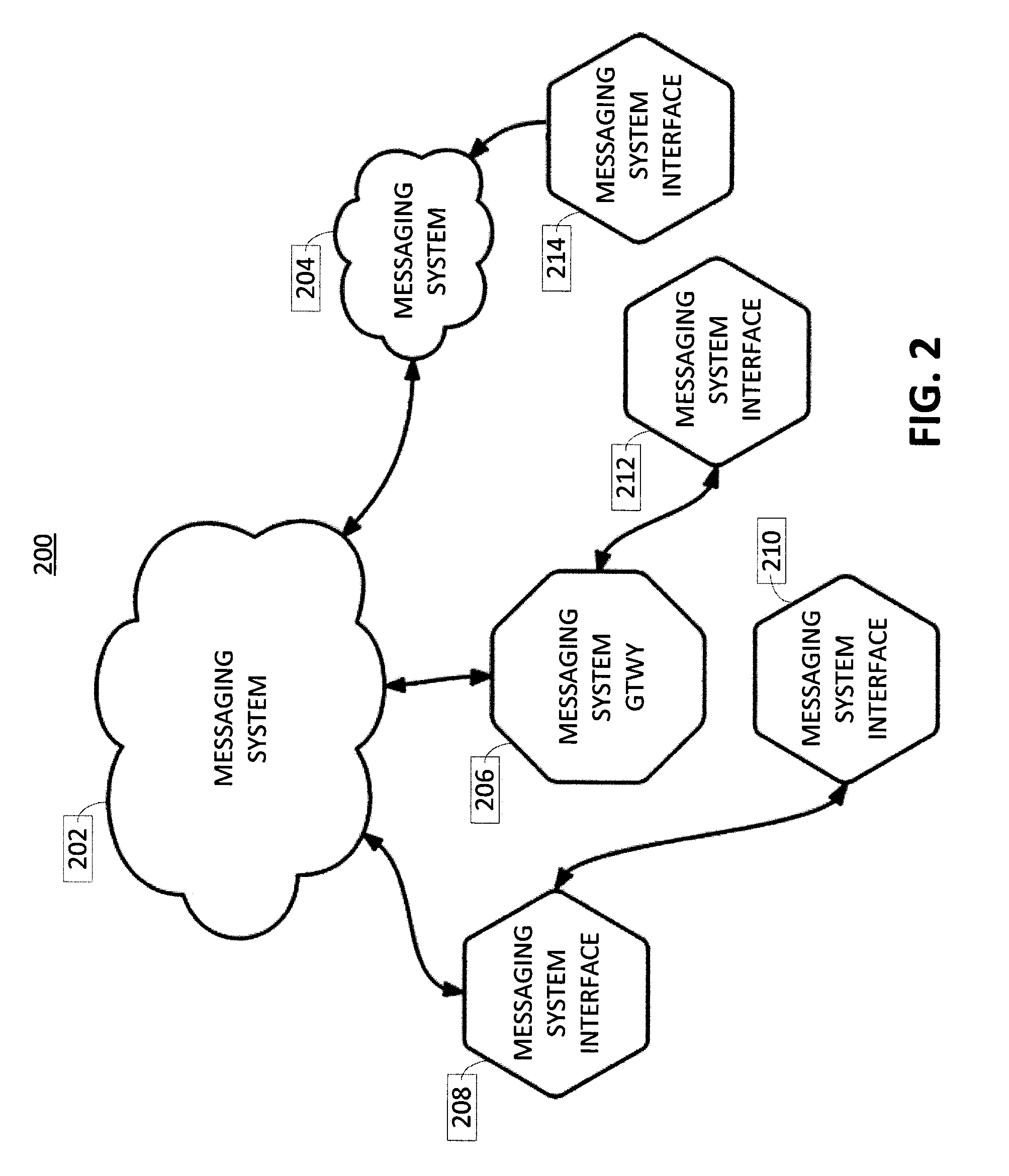
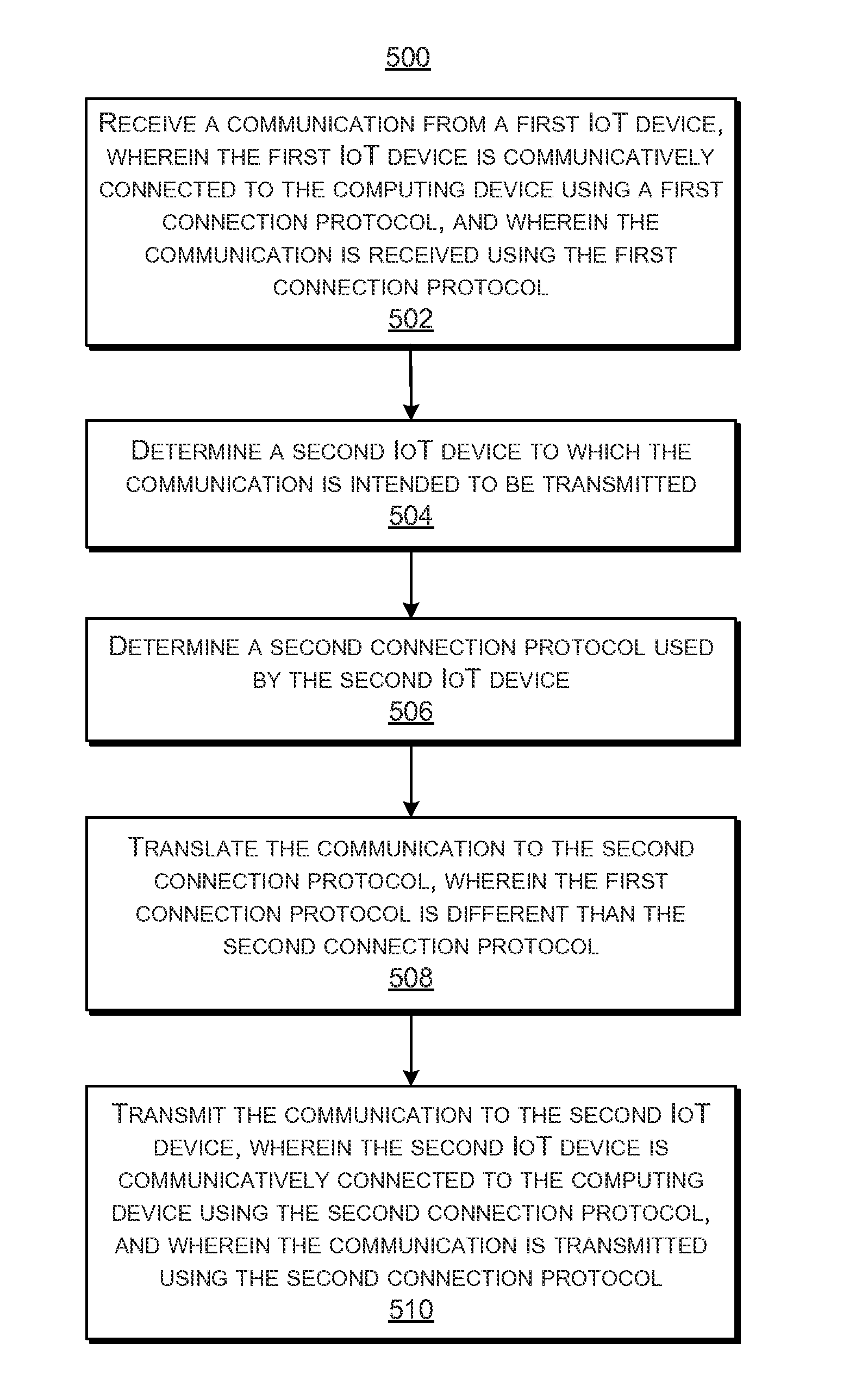
Machine-to-machine instant messaging
Techniques and systems for interfacing Internet Things (IoT) devices using different connection protocols are provided. For example, computing device, a method, and a computer-program product may be provided, and may include one or more data processors and a receiver for receiving a communication from a first IoT device communicatively connected to the computing device using a first connection protocol. The communication is received using the first connection protocol. A non-transitory computer-readable storage medium may contain instructions which when executed on the one or more data processors, cause the one or more processors to determine a second IoT device to which the communication is intended to be transmitted, determine a second connection protocol used by the second IoT device, and translate the communication to the second connection protocol. A transmitter may transmit the communication to the second IoT device that is communicatively connected to the computing device using the second connection protocol. The communication is transmitted using the second connection protocol.
Owner:CITRIX SYST INC
Communication system
ActiveUS20130203450A1Avoid congestionAvoid communicationNetwork topologiesMachine-to-machine/machine-type communication serviceCommunications systemUser equipment
The present invention has an object to provide a communication system capable of avoiding congestion in downlink communication or uplink communication and a shortage of radio resources arising therefrom. In the present invention, in a communication system including a normal user equipment (normal UE) that performs human to human communication and a machine type communication device (MTCD) that performs machine to machine communication, a base station device transmits a paging message to the normal UE and the MTCD for calling the normal UE and the MTCD. The paging message contains, for example, an equipment identity (UE-ID). A maximum number of equipment identities (UE-IDs) that can be accommodated within this paging message is set individually for the normal UE and the MTCD. Alternatively, the paging message contains a calling indicator in place of the equipment identity of the MTCD (UE-ID of MTCD).
Owner:MITSUBISHI ELECTRIC CORP
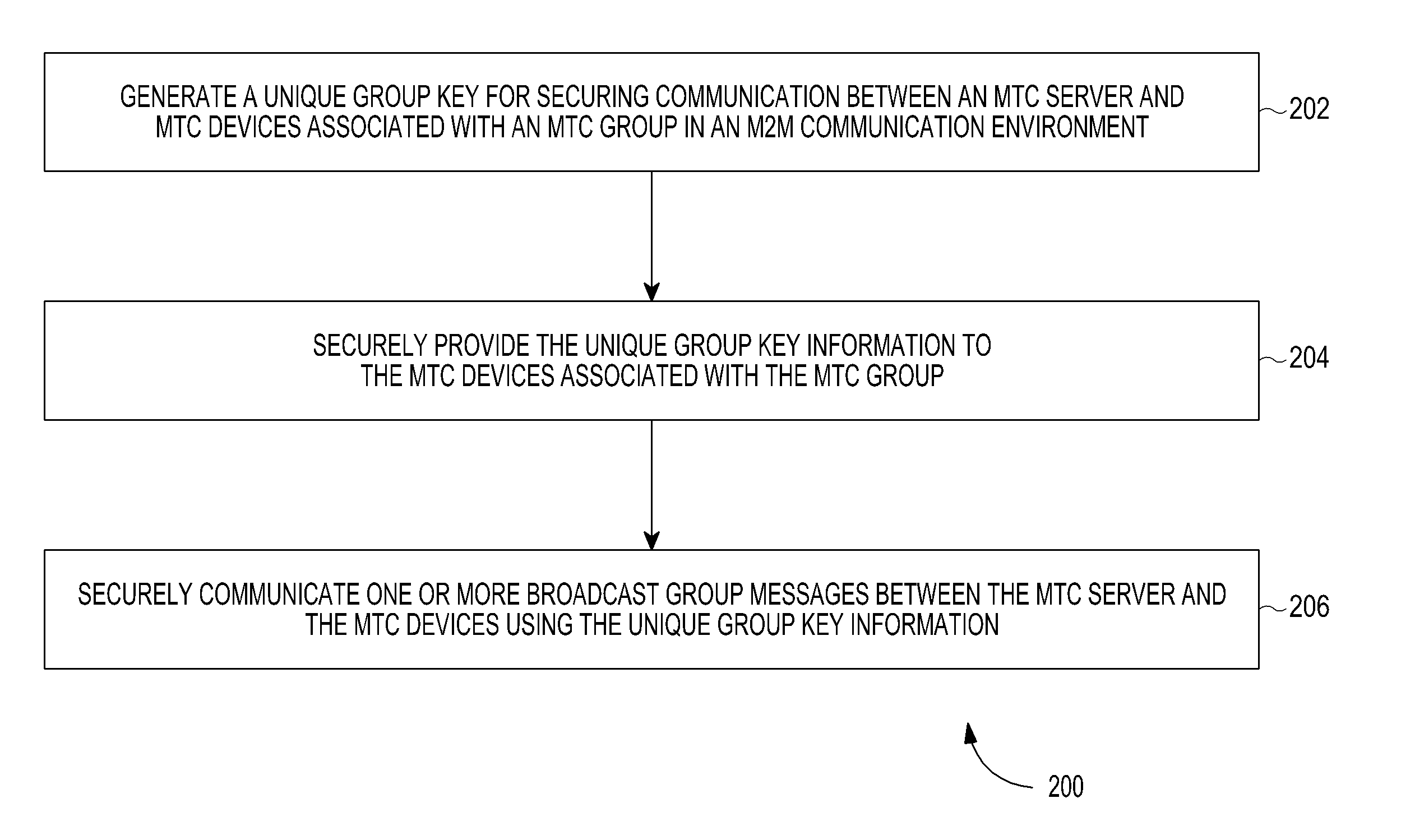
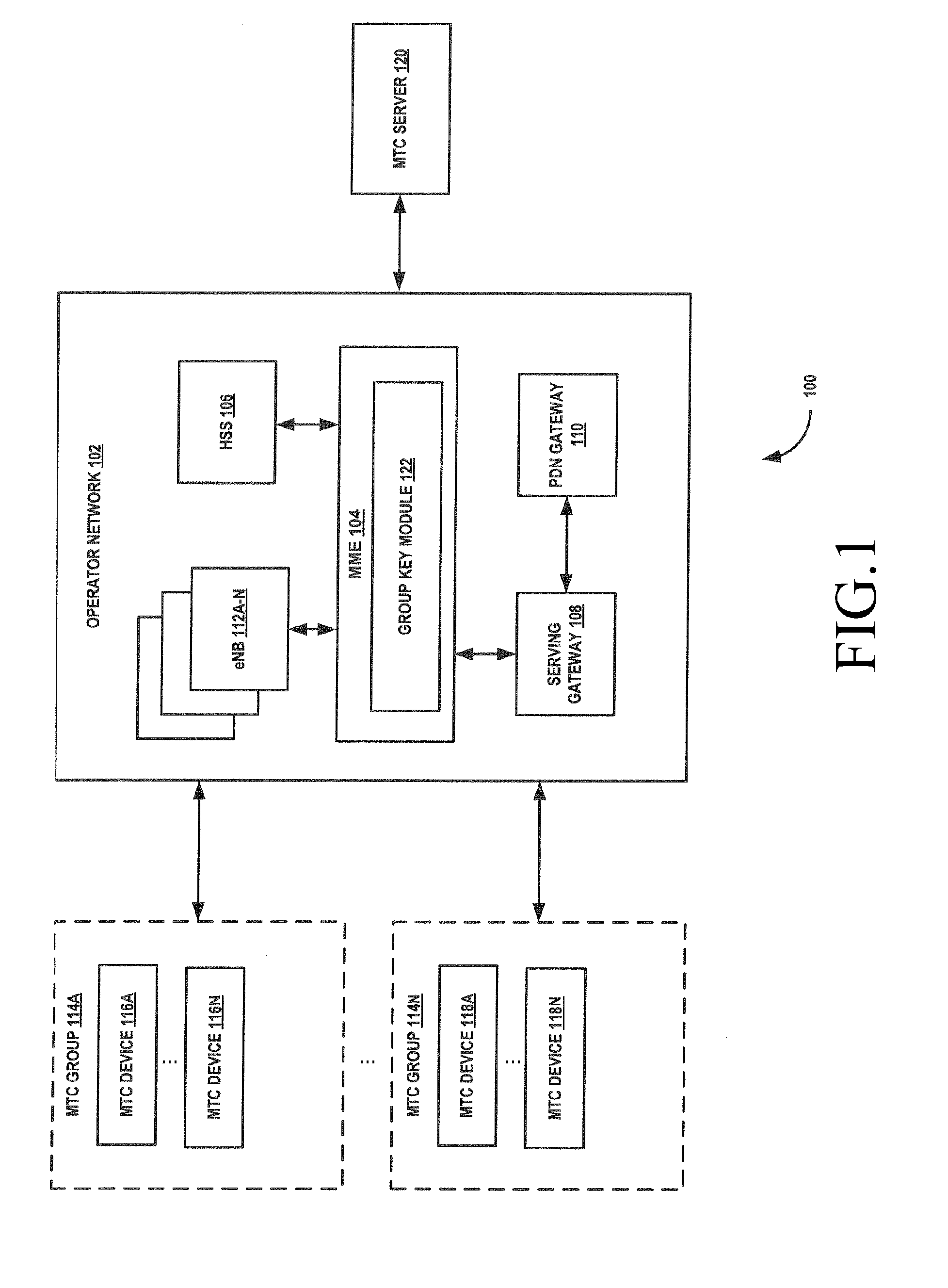
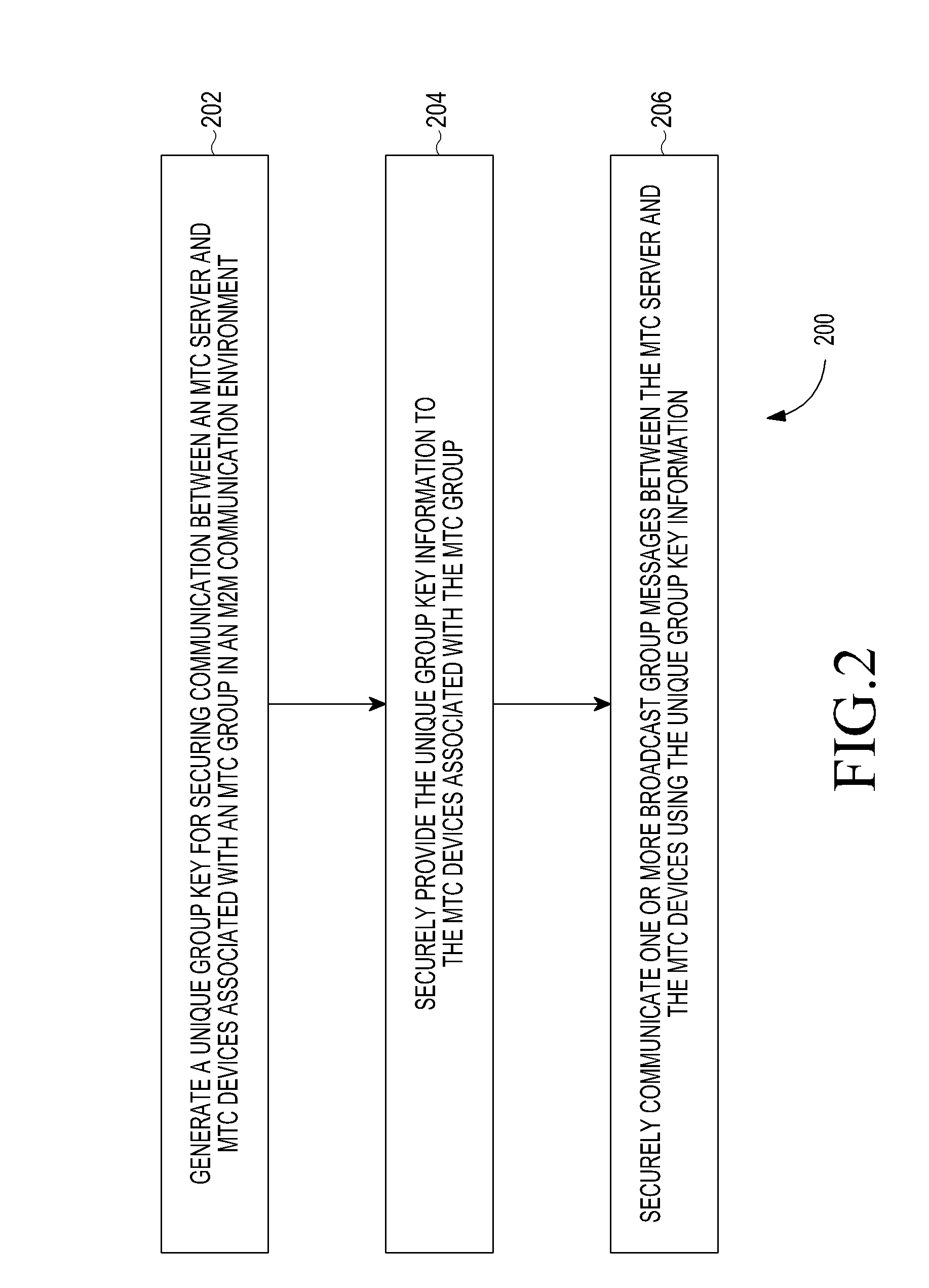
Method and system of securing group communication in a machine-to-machine communication environment
ActiveUS20130080782A1Communication securitySecure CommunicationsKey distribution for secure communicationUser identity/authority verificationSecure communicationInformation security
A method and system for securing group communication in a Machine-to-Machine (M2M) communication environment including a plurality of Machine Type Communication (MTC) groups, wherein each of the plurality of MTC groups includes a plurality of MTC devices. The method includes generating a unique group key for securing communication with MTC devices associated with an MTC group in an M2M communication environment, securely providing information on the unique group key to the MTC devices associated with the MTC group, and securely communicating at least one broadcast group message with the MTC devices using the unique group key information.
Owner:SAMSUNG ELECTRONICS CO LTD
Radio frequency for consumer electronics based communication system and method
InactiveUS20130271270A1Electric signal transmission systemsNetwork topologiesCommunications systemEngineering
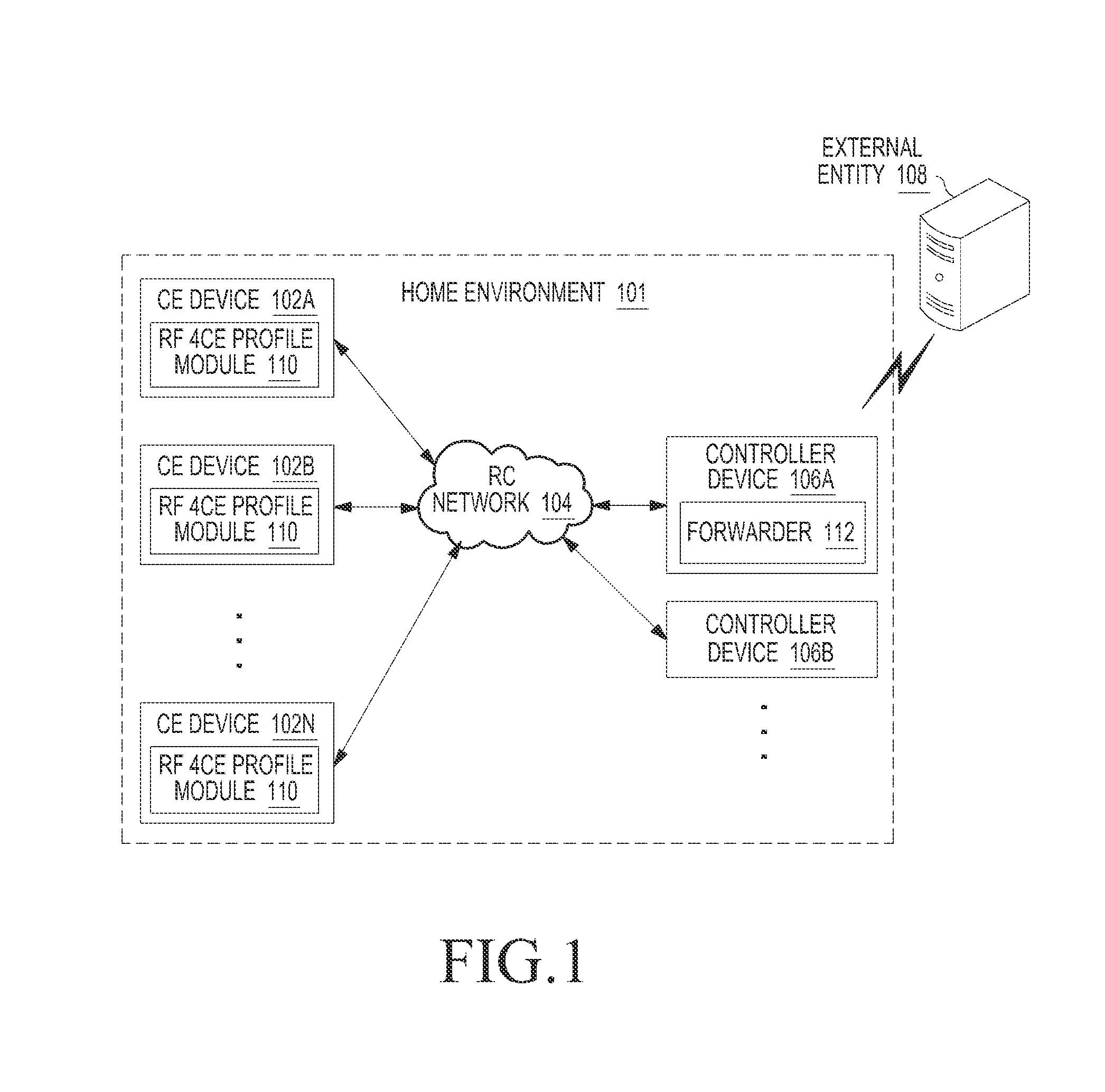
A Radio Frequency for Consumer Electronics (RF4CE) based communication system and method is provided. The method includes discovering one or more controller devices in an RF4CE based radio communication network. The RF4CE based radio communication network includes one or more Consumer Electronics (CE) devices and one or more controller devices. The method also includes selecting one of the one or more controller devices based on capabilities of each of the one or more controller devices, transmitting an RF4CE data packet including Machine to Machine (M2M) communication data to the selected one of the one or more controller devices over an RF4CE protocol, such that the M2M communication data is forwarded to an intended external entity by the controller device via a communication channel.
Owner:SAMSUNG ELECTRONICS CO LTD
System for electronic device monitoring
InactiveUS20110016199A1Digital data processing detailsComputer security arrangementsComputer hardwareComputer science
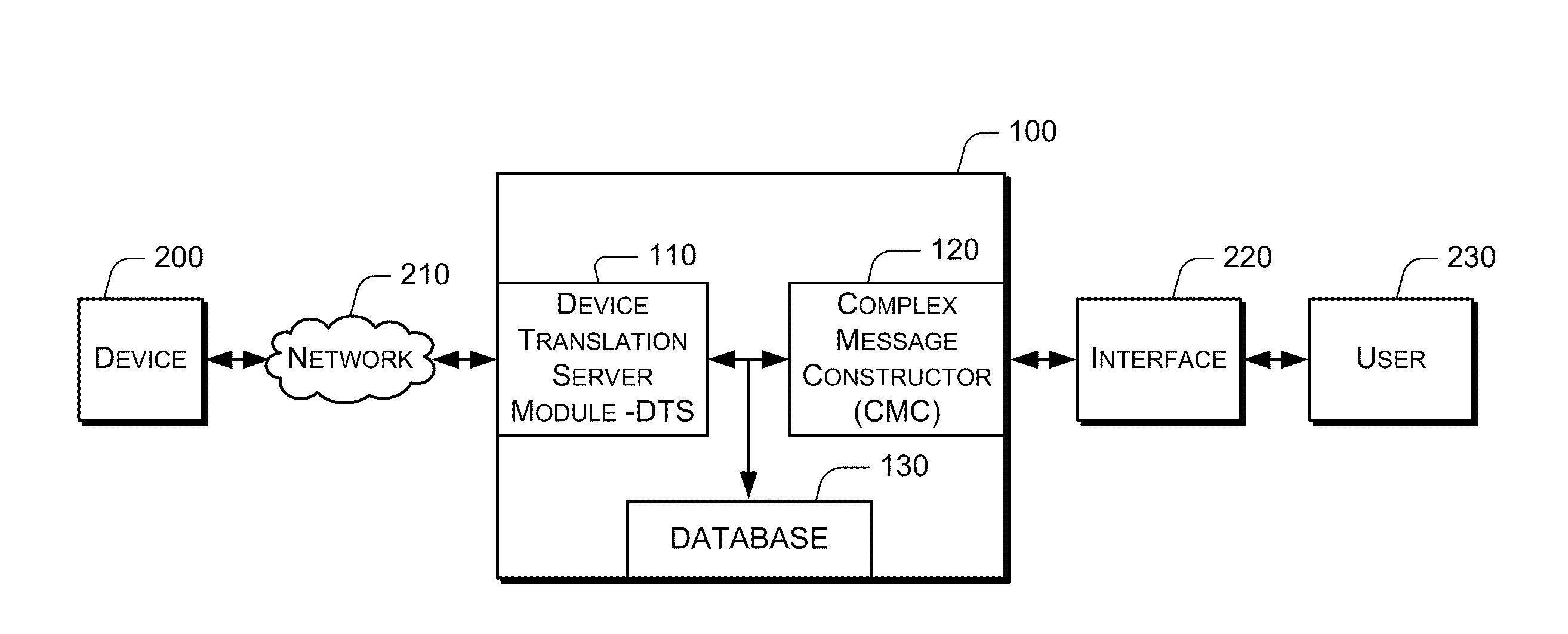
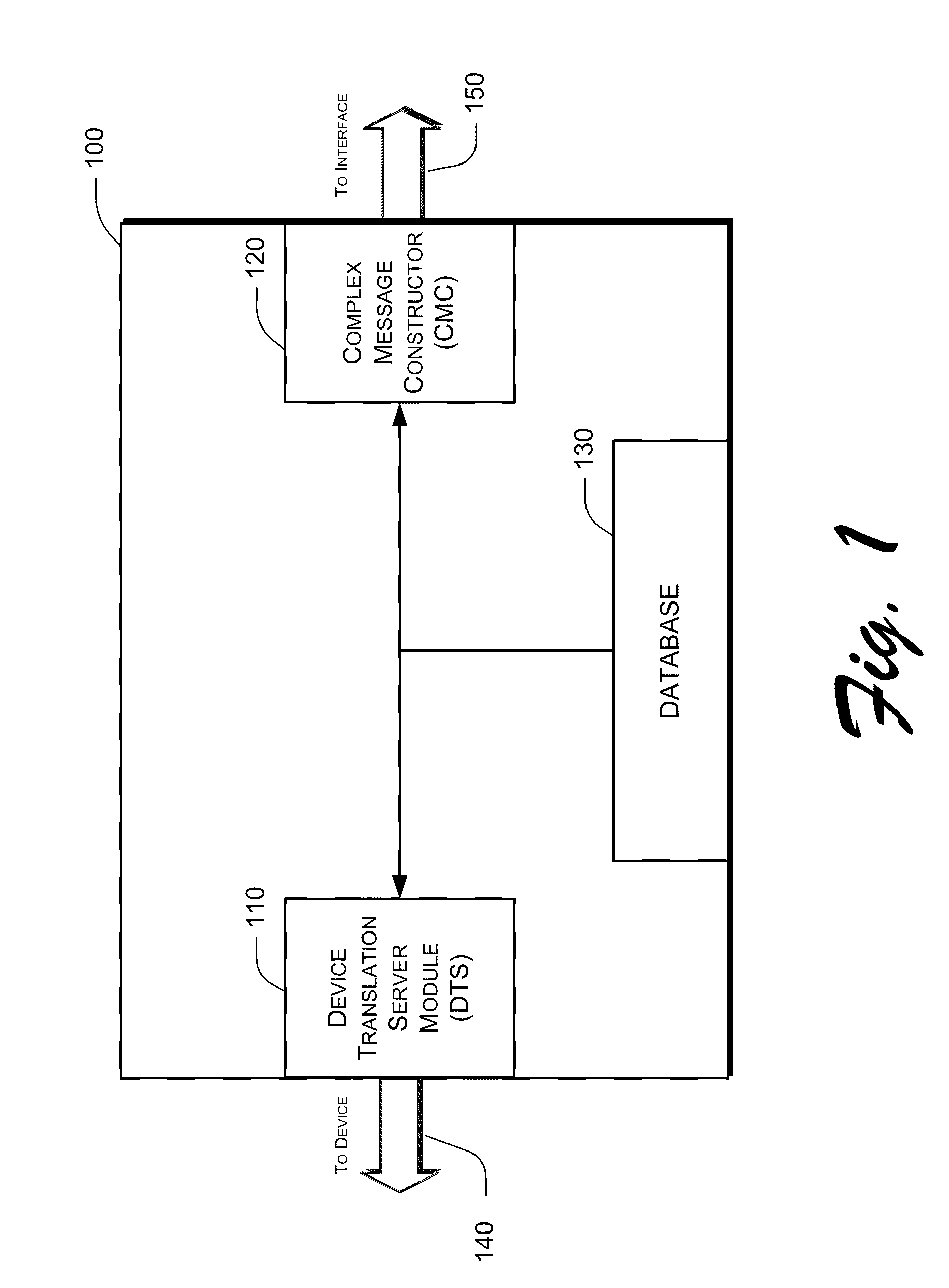
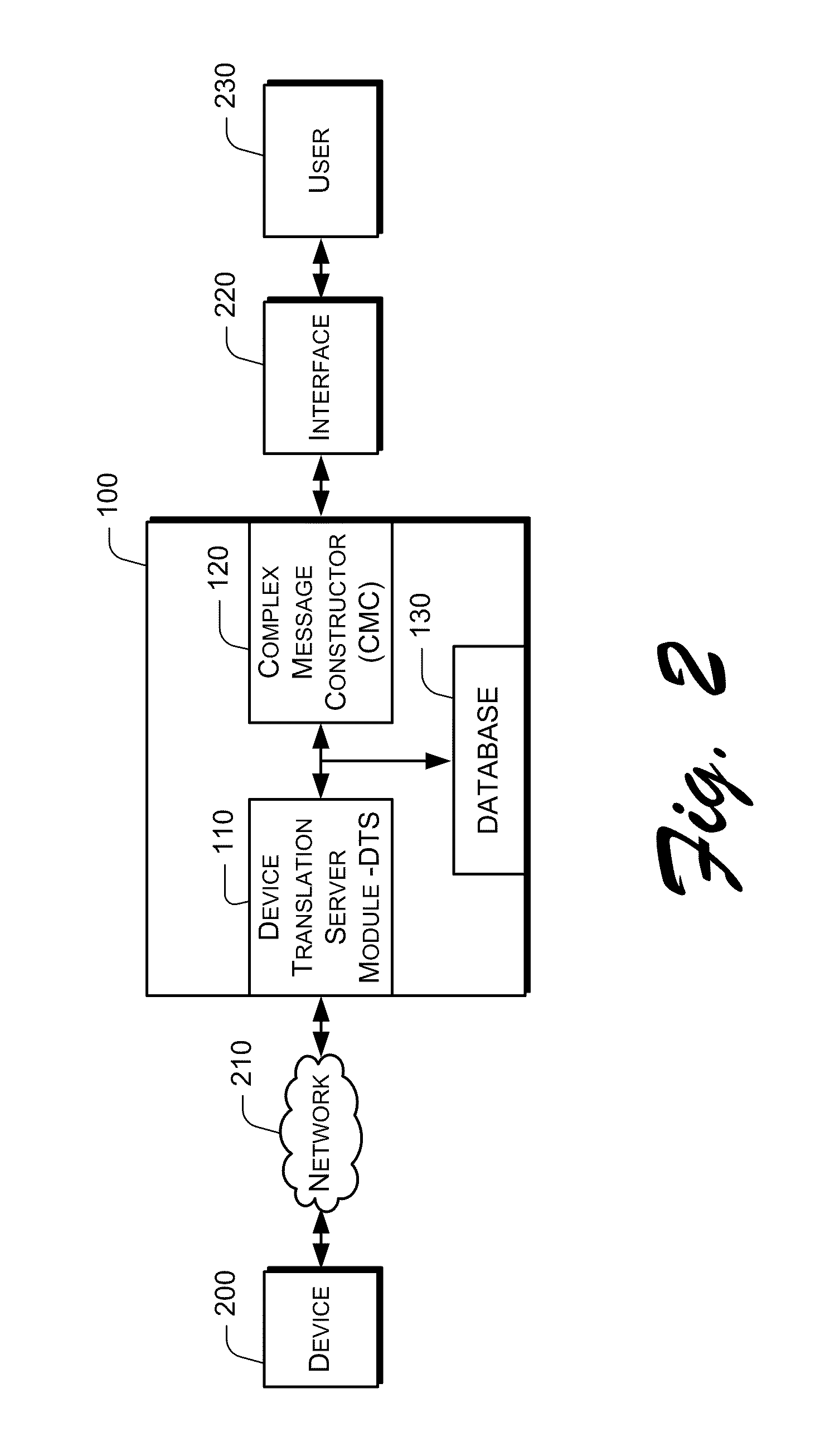
The present invention relates to telemetry methods and systems and more particularly, to telemetry network connectivity systems, devices and methods. In accordance with various embodiments, a suite of software components configured to provide machine-to-machine network connectivity includes a configurable device translation server module, a complex message constructor and at least one database. In some embodiments the suite of software components, specifically the complex message constructor, may be configured to authenticate commands between an interface and the device translation server. Additionally, the suite of software components, specifically the complex message constructor, may be configured to manage messages between the interface and the device translation server. Managing messages may include initiating alerts and notifications based on a comparison of programming and substantially synchronous and stored information.
Owner:INILEX
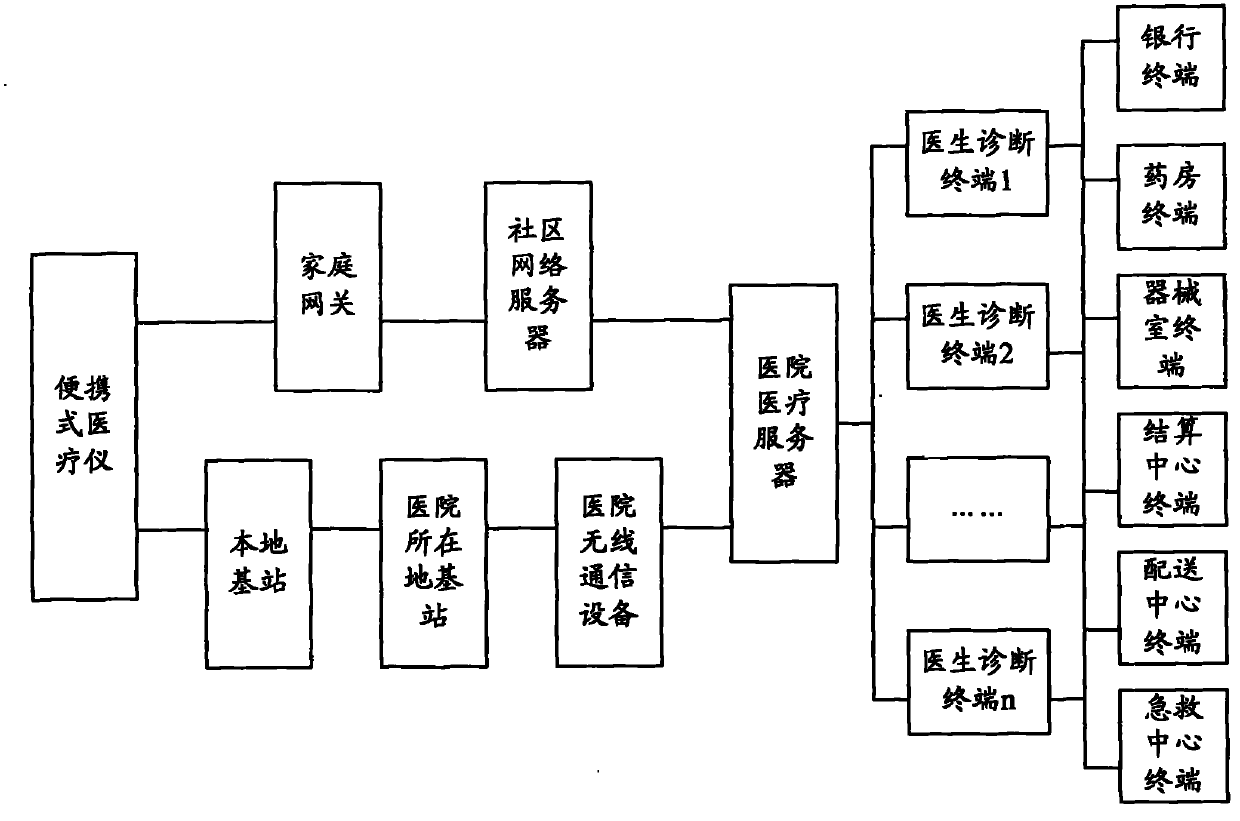
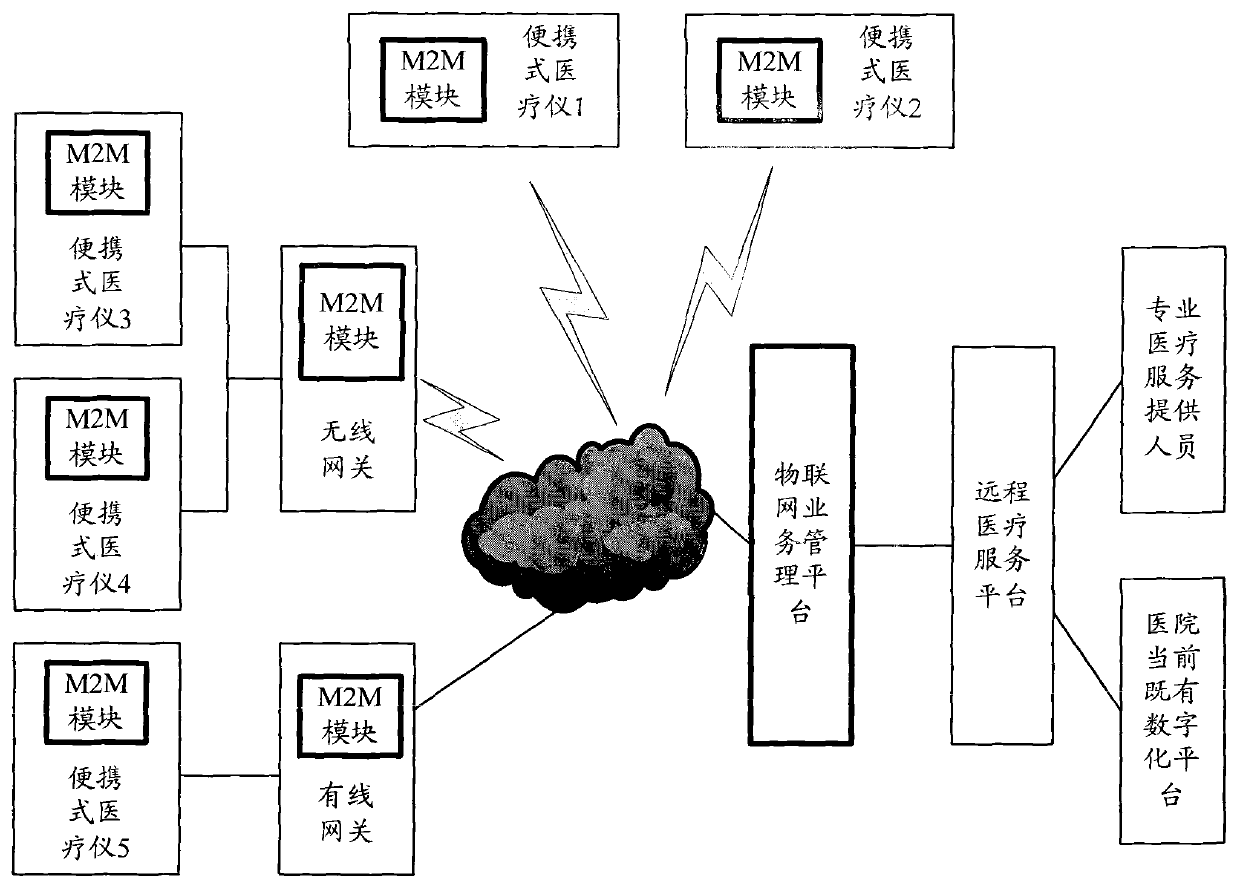
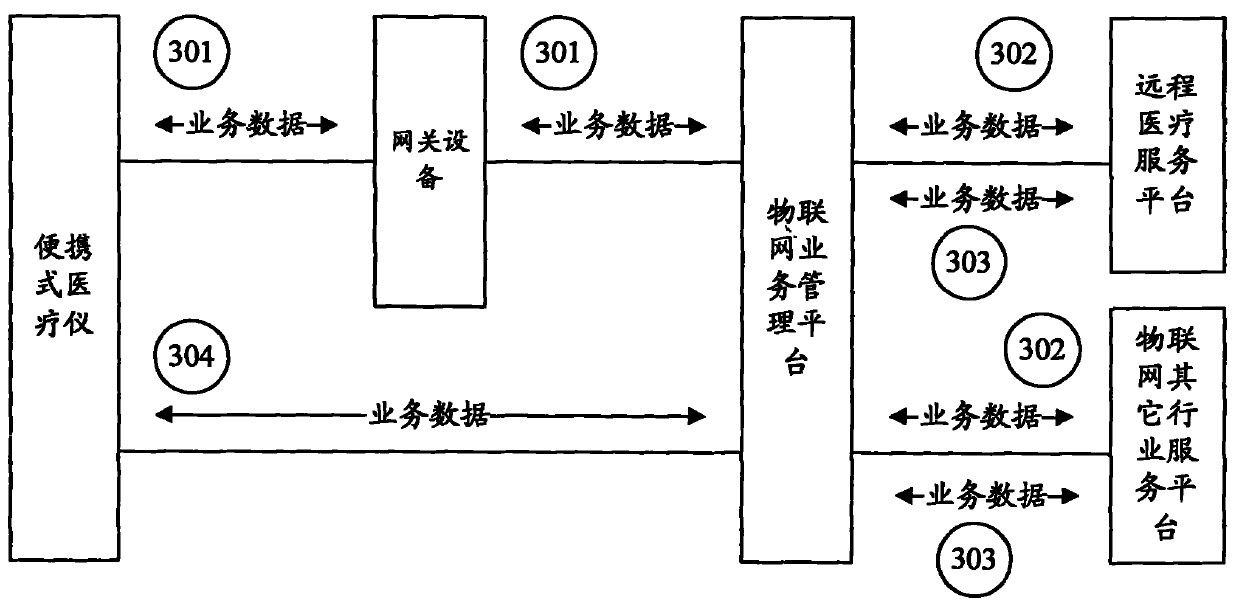
Telemedicine system and telemedicine equipment
ActiveCN102567611AEasy to shareReduce development costsSurgeryDiagnostic recording/measuringInformation sharingThe Internet
The invention discloses a telemedicine system and telemedicine equipment. The telemedicine system comprises a portable medical instrument, an Internet of things business management platform and a telemedicine service platform, wherein the portable medical instrument is used for receiving control information, monitoring a self running status and acquiring control data, collecting physiological indexes of a user to obtain business data, packaging the control data and the business data according to a preset machine-to-machine (M2M) protocol and then sending, receiving diagnostic information and showing the diagnostic information to the user; the Internet of things business management platform is used for receiving the control data and the business data, analyzing the control data and the business data, sending the business data to the telemedicine service platform, analyzing information contained in the control data, generating the control information according to a preset strategy, sending the control information to the portable medical instrument, receiving the diagnostic information and sending the diagnostic information to the portable medical instrument; and the telemedicine service platform is used for receiving the business data, analyzing the business data to generate the diagnostic information and sending the diagnostic information to the Internet of things business management platform. By applying the telemedicine system and the telemedicine equipment, the running reliability of the system can be increased, the development can be reduced, and the information sharing capacity can be promoted.
Owner:CHINA MOBILE GROUP JIANGSU
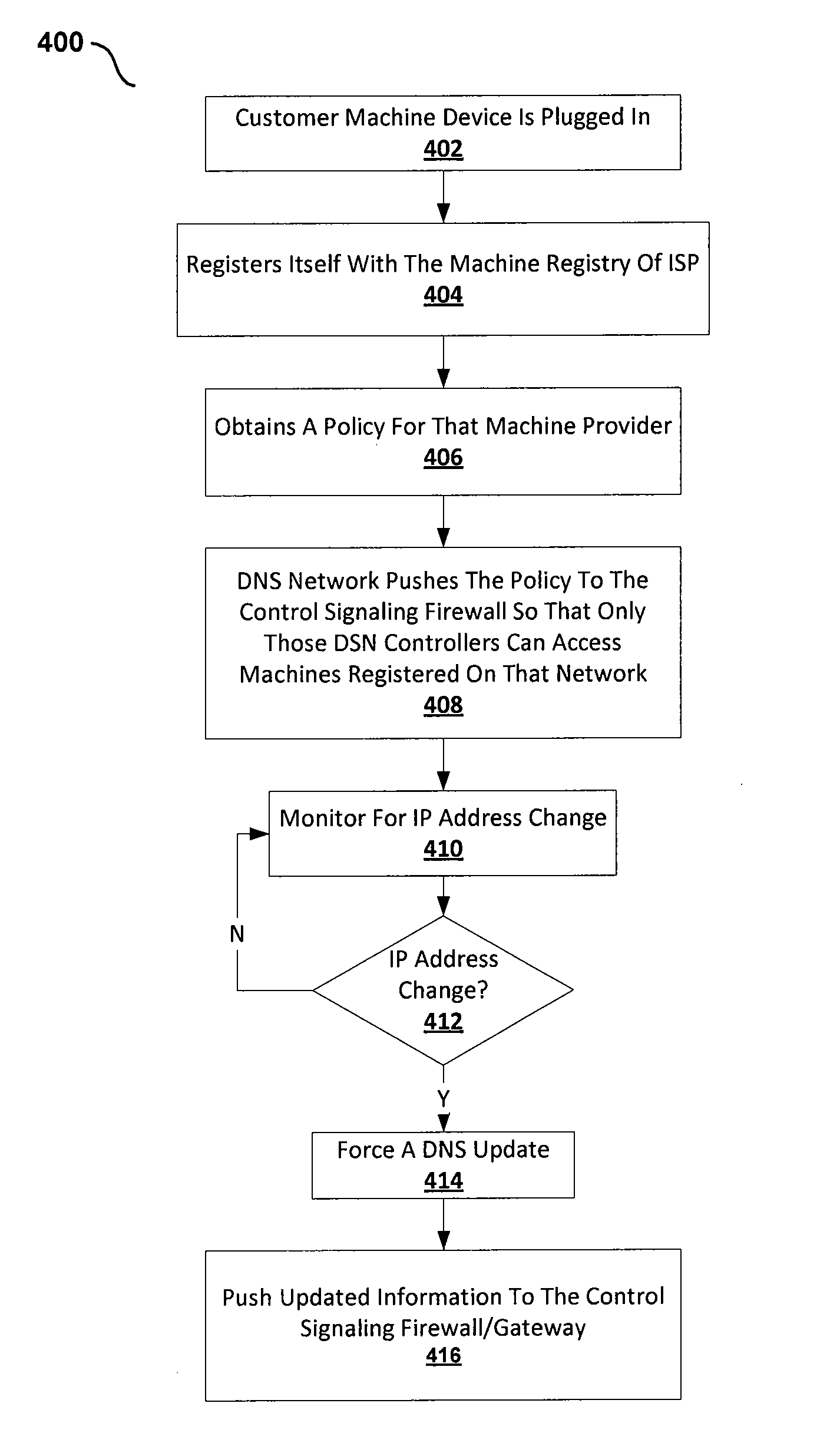
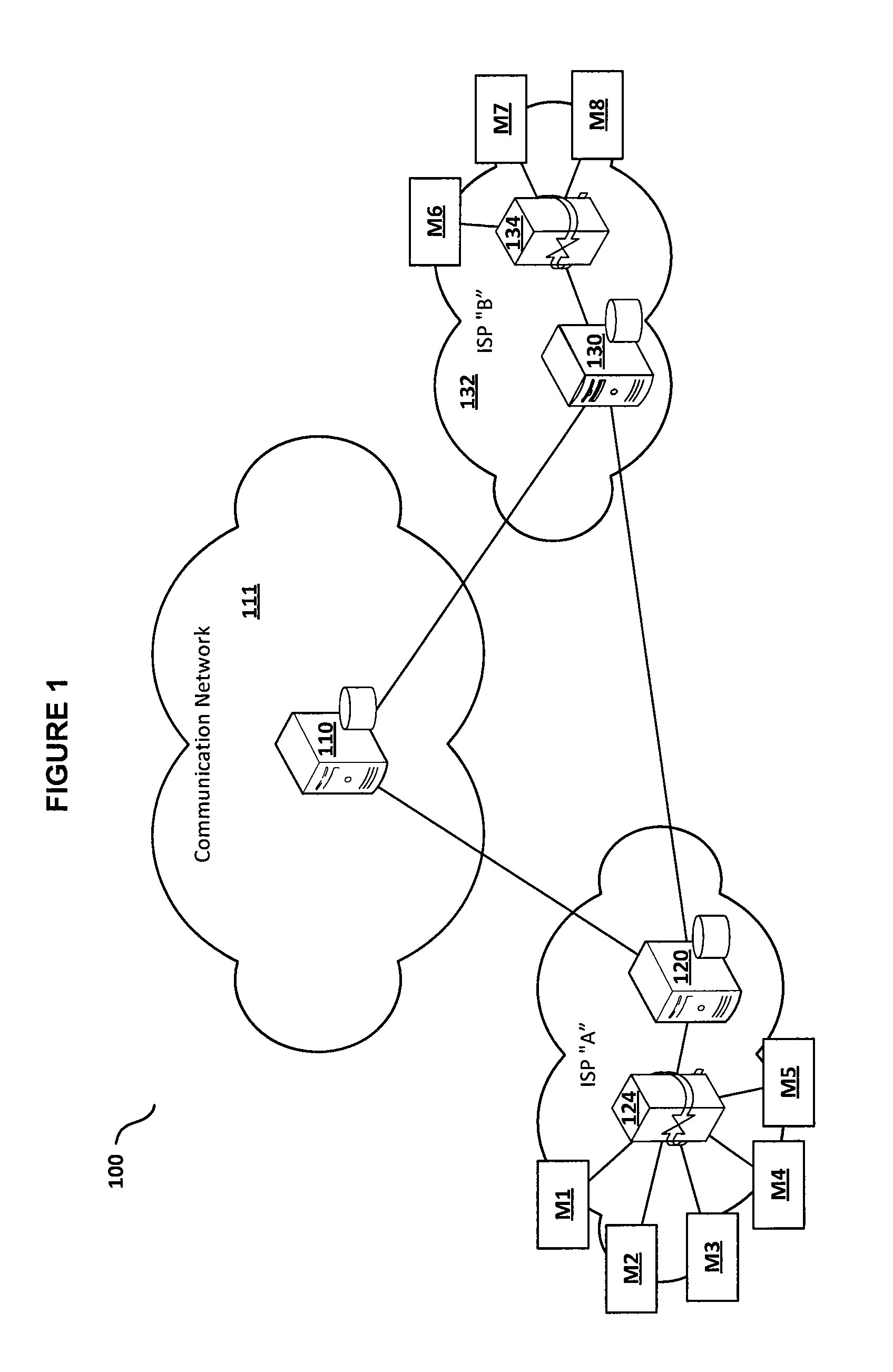
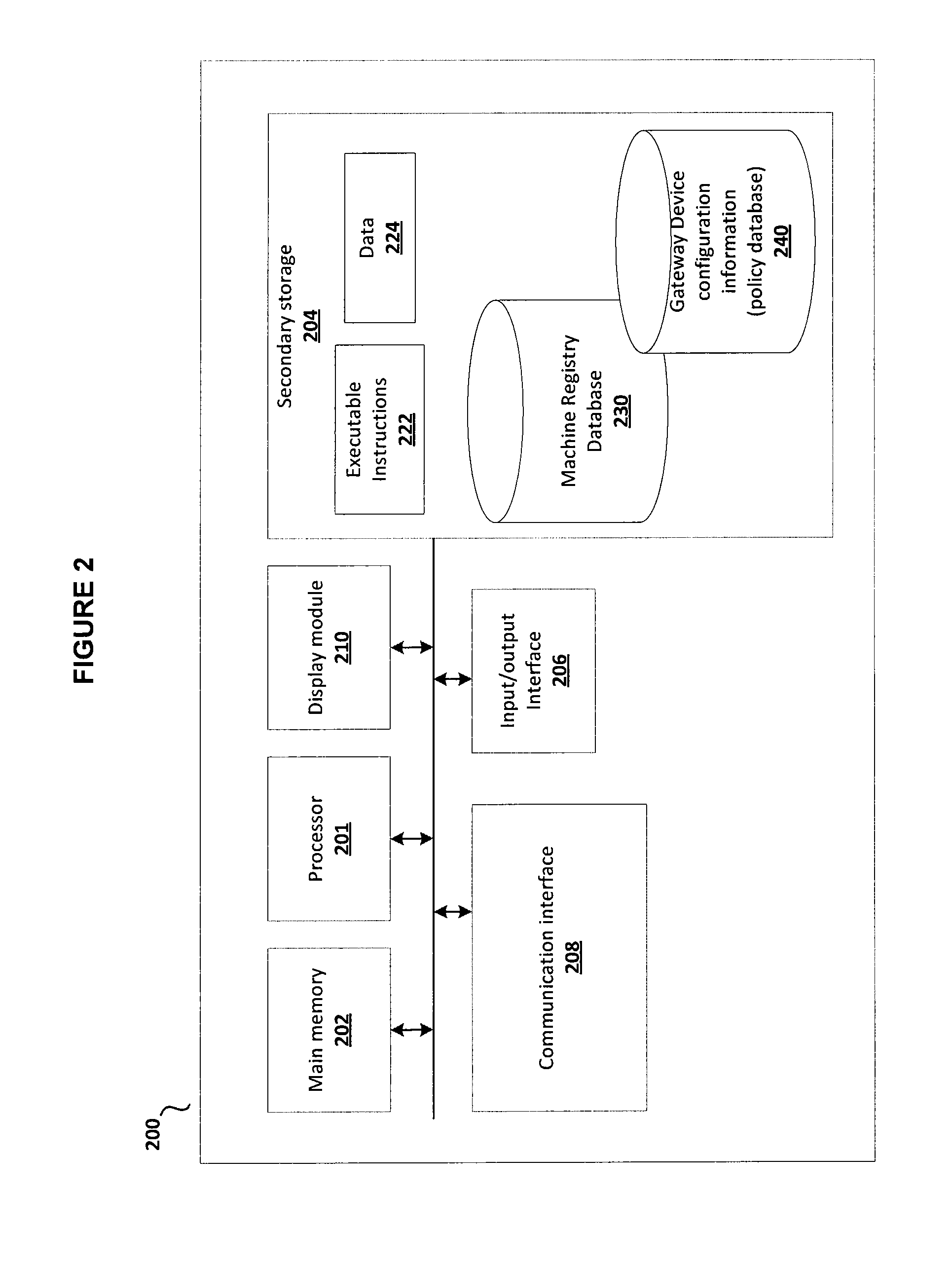
System and method for secure machine-to-machine communications
ActiveUS20130305345A1Eliminate riskFacilitate communicationMultiple digital computer combinationsProgram controlRegistry dataDomain name
Embodiments of the present invention include a method for providing a secure domain name system (DNS) for machine to machine communications. In one embodiment, the method includes storing policy information for machine to machine communications in a global DNS registry database server. The method further includes communicating the policy information for machine to machine communications from the global DNS registry database server to a machine DNS registry server located in an Internet service provider (ISP) network, wherein a control signaling gateway located in the ISP network is configured to utilize the policy information for machine to machine communications to allow only registered controllers associated with a machine to communicate with the machine.
Owner:CENTURYLINK INTPROP
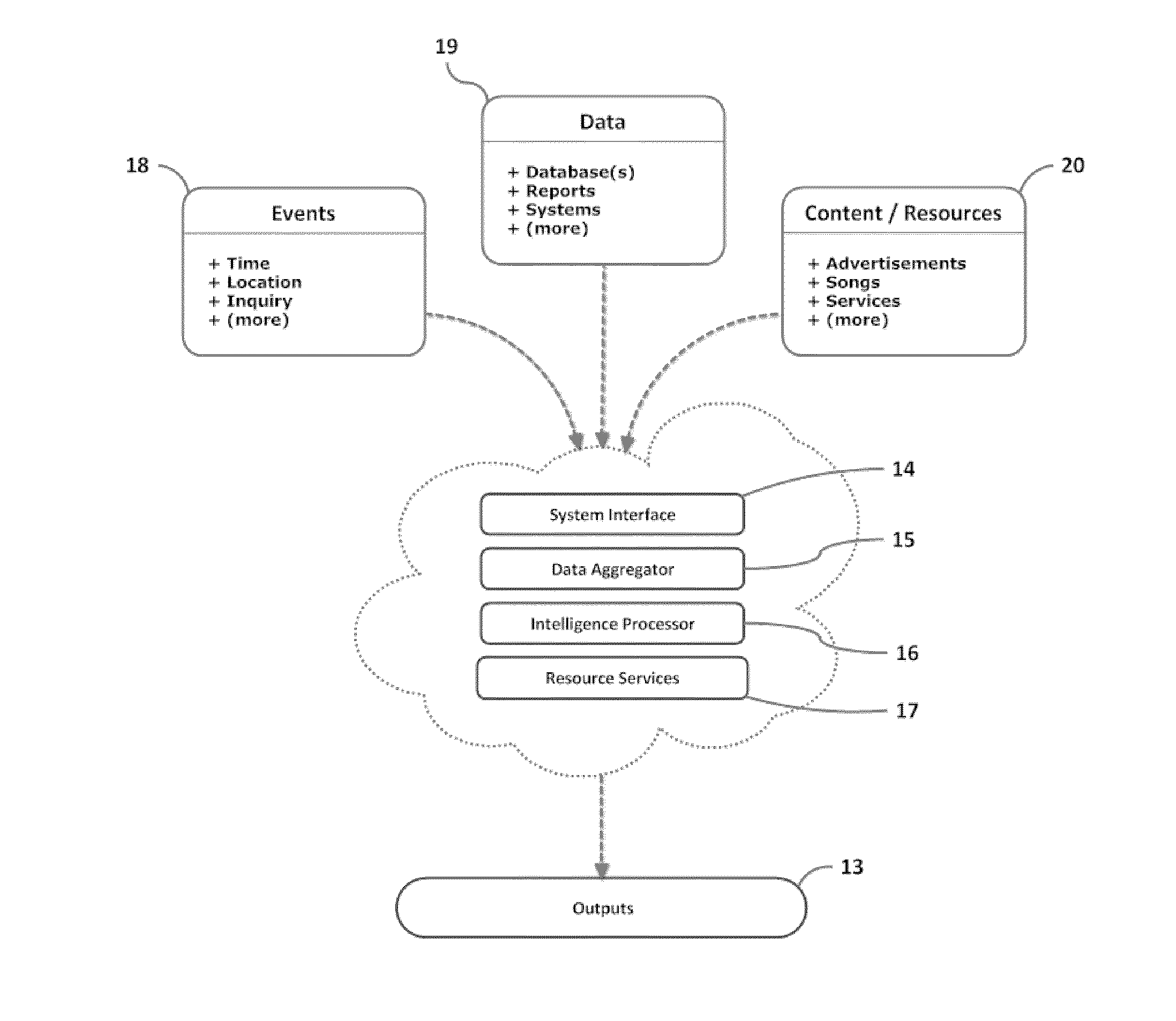
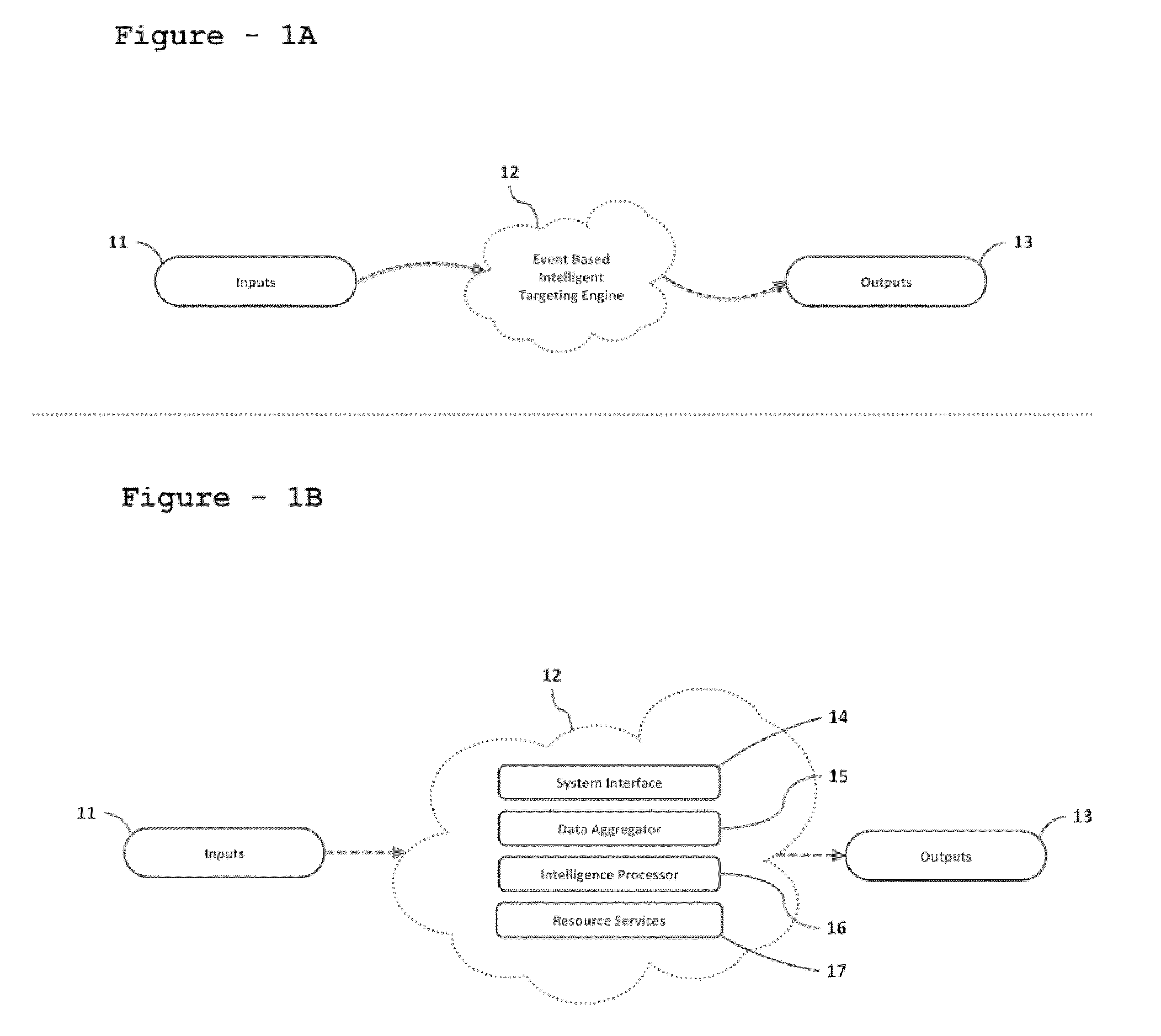
System for event-based intelligent-targeting
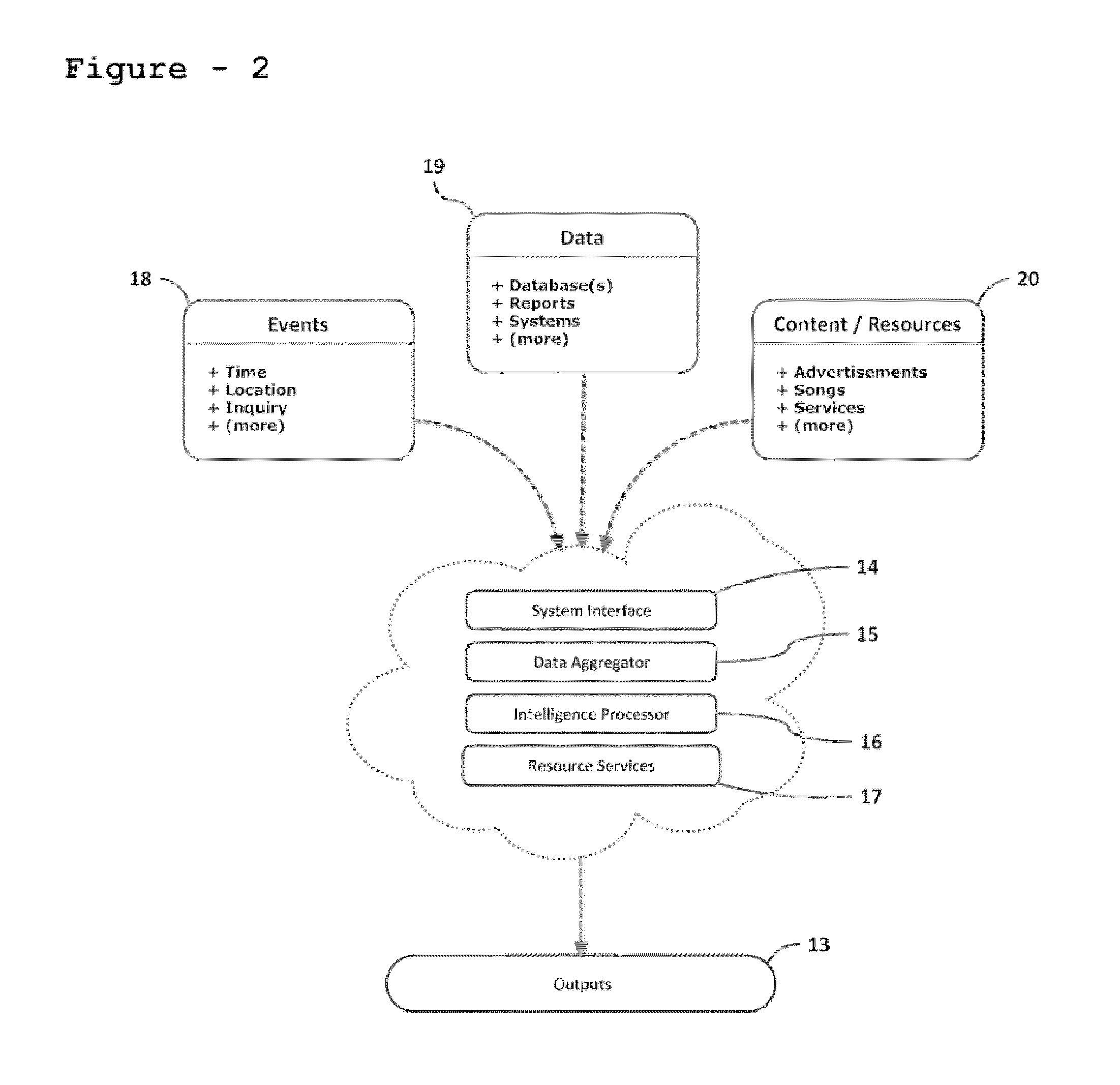
InactiveUS20110238647A1Road vehicles traffic controlDigital data processing detailsComputer sciencePositioning system
An event-based intelligent targeting engine is capable of delivering highly relevant content, including, but not limited to, advertisements, alerts, messages, notifications, warnings, signals, machine-to-machine (M2M) telemetry, entertainment / media, and any communications thereof, etc. based on real-time situations (i.e., observed events) of a user as well as, historical preferences both explicitly stated or observed in behavior including demographics, psychographics, and sociographics.
Owner:MAVIZON
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com