Secure session key generation
A session key and security technology, which is applied in the direction of public key for secure communication, security device, encryption device with shift register/memory, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
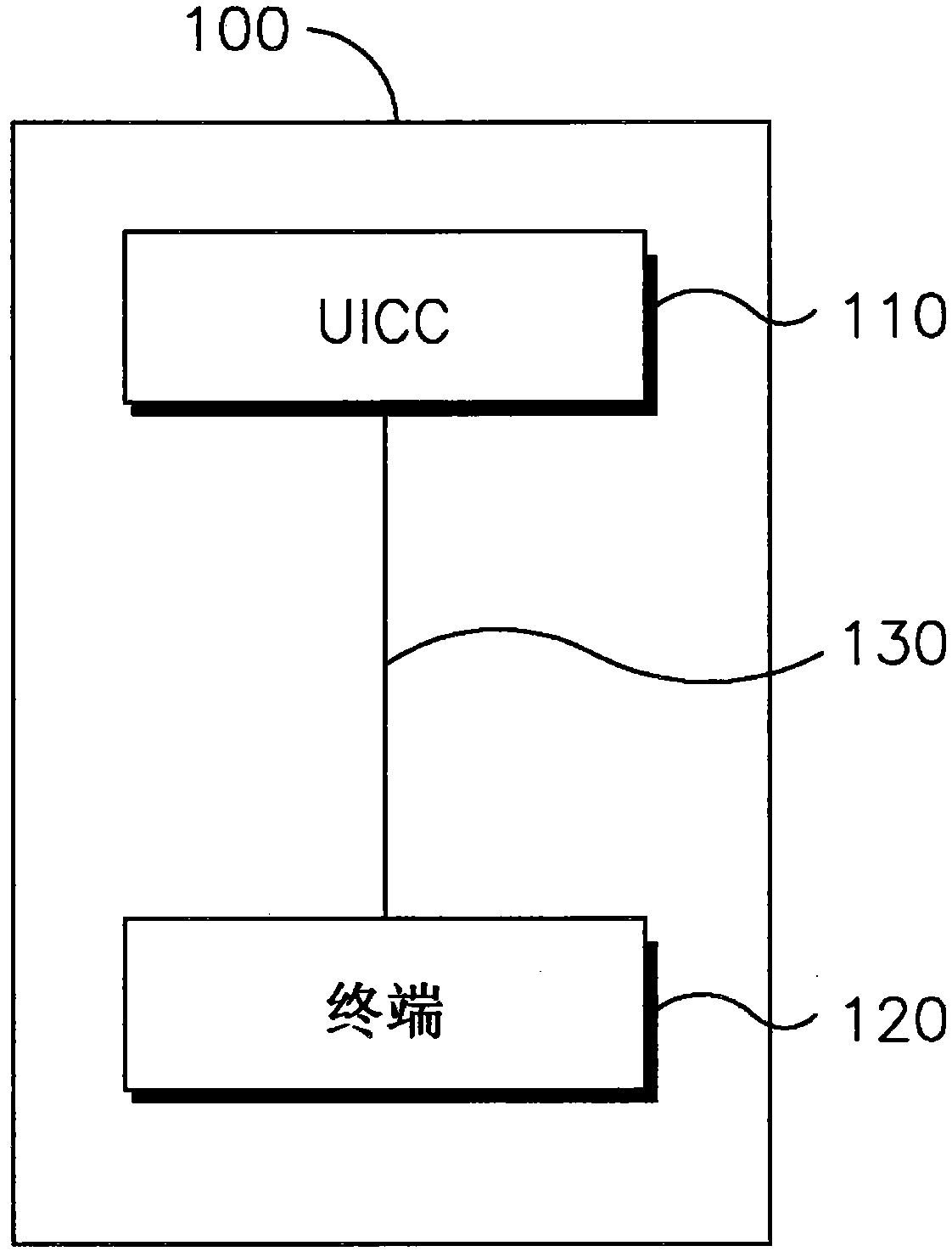
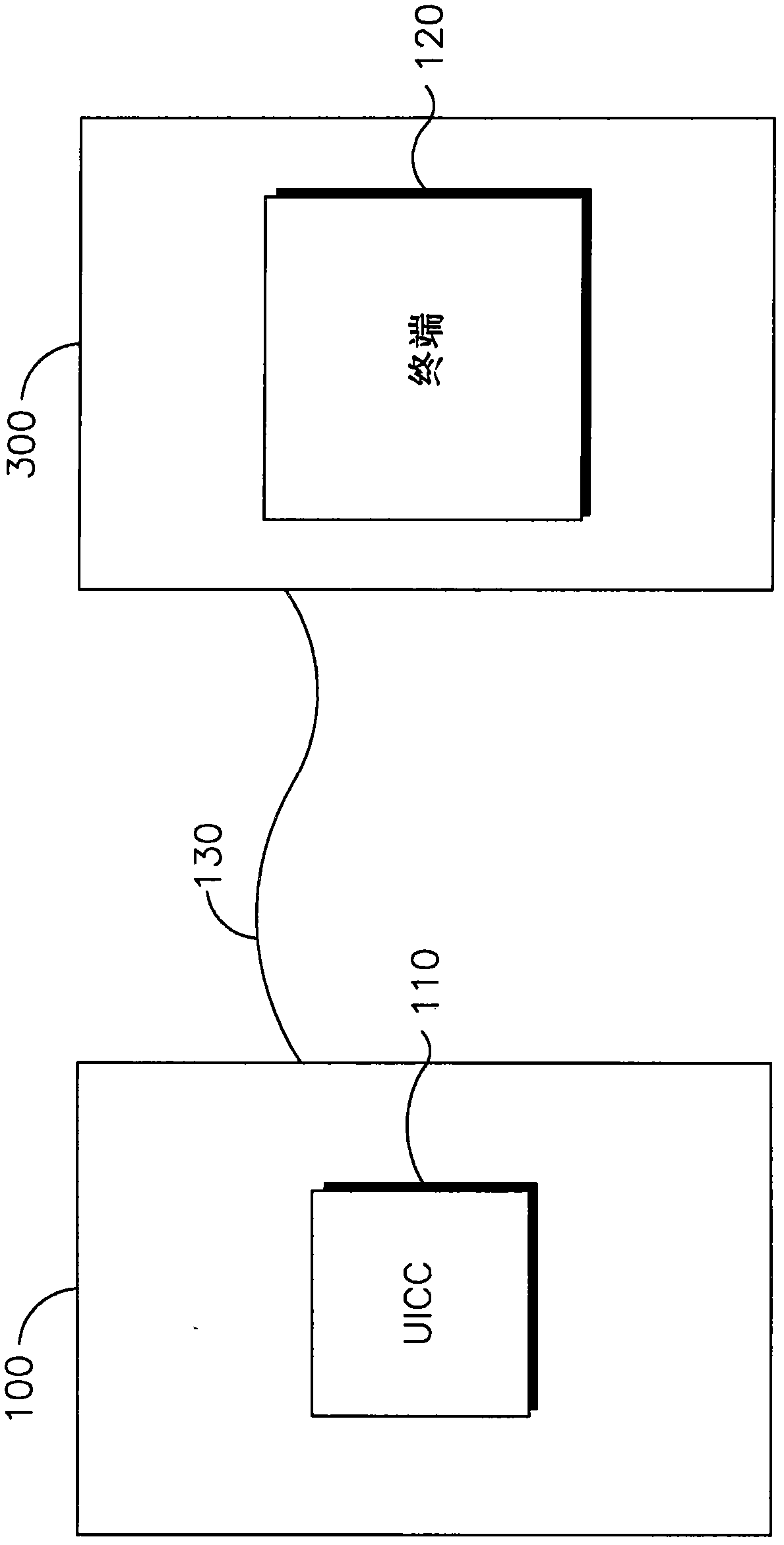
[0082] 1. A method for securing communication between a Universal Integrated Circuit Card (UICC) and a terminal.
[0083] 2. A method as in any one of the preceding embodiments, wherein securing the communication comprises generating a secure shared session key.
[0084] 3. The method as in any one of the preceding embodiments, wherein securing communications comprises using the secure shared session key to encrypt communications between the UICC and the terminal.
[0085] 4. The method as in any one of the preceding embodiments, wherein generating the secure shared session key comprises deriving the secure shared session key from a shared ciphertext.
[0086] 5. The method as in any one of the preceding embodiments, wherein deriving the secure shared session key from the shared secret comprises generating a session secret from the secret.
[0087] 6. The method as in any one of the preceding embodiments, wherein deriving the secure shared session key comprises performing a p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com