Key distribution and reception method, key management center, and first and second network elements
A technology for key management center and key distribution, which is applied in the fields of first and second network elements, key management center, key distribution and receiving methods, and can solve problems such as poor security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
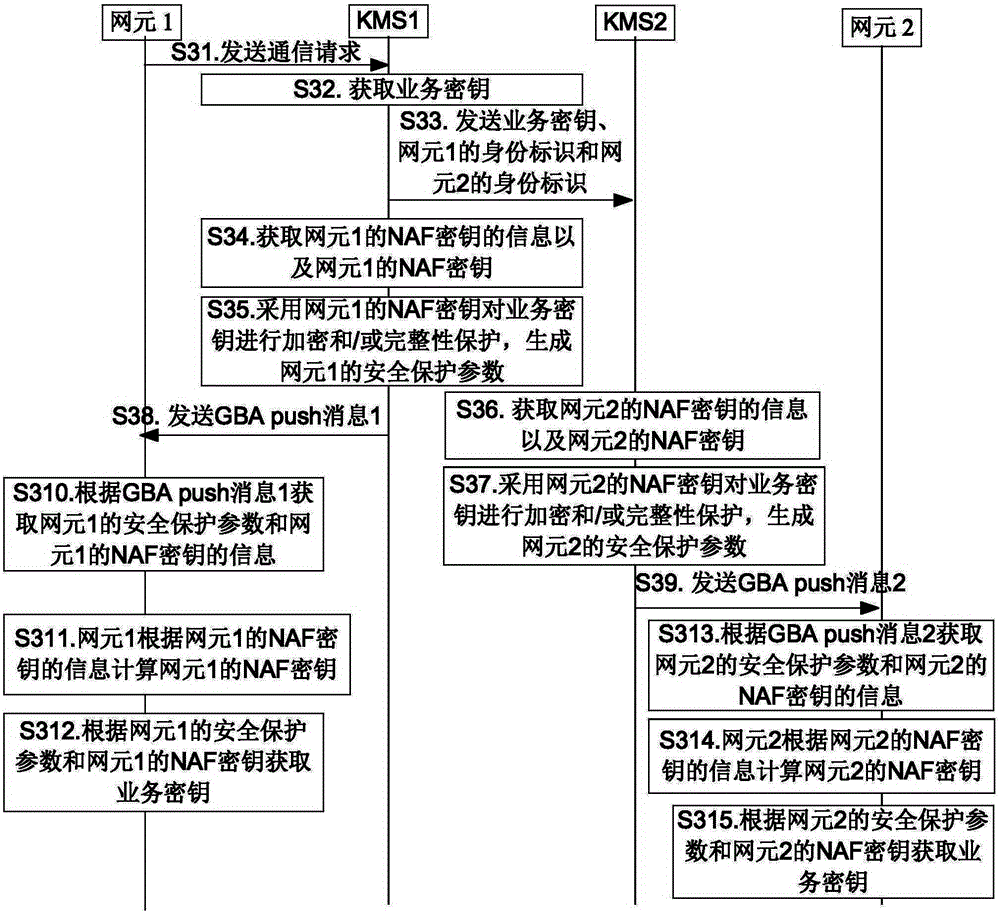
[0204] Example 1: KMS2 obtains the second random number and / or the NAF key of the second network element, and sends the second random number and / or the NAF key of the second network element to KMS1. KMS1 receives the second random number and / or the NAF key of the second network element sent by KMS2.
[0205] KMS1 calculates at least one of the identity, the time used to indicate the validity period of the service key, the sequence number, the random number determined by KMS1, the NAF key of the first network element, and the second random number and / or when the NAF key of the second network element is an argument of the preset key derivation function, the dependent variable of the preset key derivation function, and the service key is the dependent variable.
[0206] For example, K=KDF(key, ID), or, K=KDF(key, time), or, K=KDF(key, SN), or, K=KDF(key1, key2), where key and key2 includes the second random number and / or the NAF key of the second network element, ID is a set of...
example 3
[0208] Example 3: KMS1 and KMS2 negotiate the service key through DH key negotiation.
[0209] The method of DH key agreement is an existing technology, and will not be repeated here.
[0210] Example 4: KMS1 and KMS2 obtain the negotiation parameters through the DH key negotiation method, and KMS1 calculates the dependent variable of the preset key derivation function when the negotiation parameter is one of the independent variables of the preset key derivation function, so The service key includes the dependent variable.
[0211] A preset key derivation function is set in KMS1. When obtaining the arguments of the preset key derivation function, the negotiation parameter obtained through the DH key negotiation method is used as one of the arguments, and other arguments of the preset key derivation function are not limited here , for example, the other independent variable may be a random number determined by KMS1.
[0212] After all the independent variables of the preset...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com