Login method without password based on third party authentication, device and system thereof
A login method and password-free technology, applied to devices and systems, in the field of password-less login methods based on third-party authentication, can solve problems such as cumbersome login methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
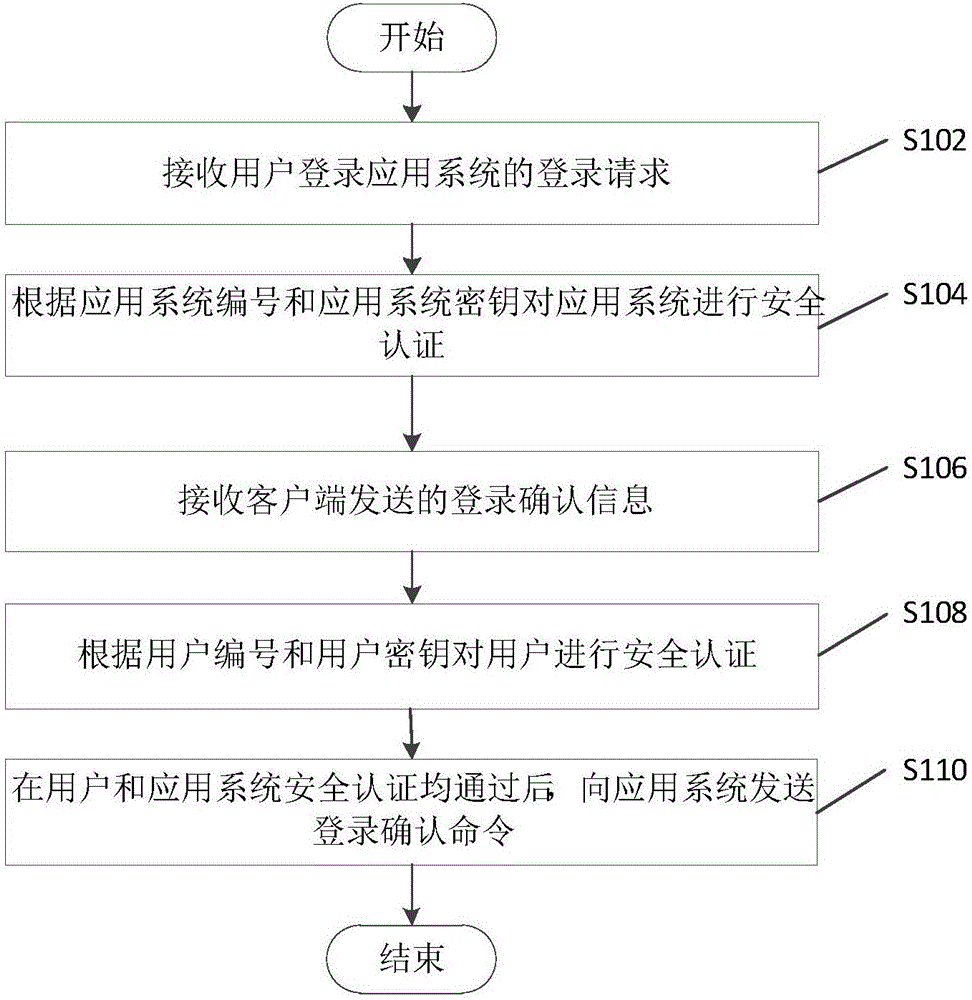
[0040] figure 1 The flow chart of the passwordless login method based on third-party authentication provided in the first embodiment of the present application. The login method implements the process of user login application system using a passwordless login method, wherein the third-party authentication server implements For the security authentication of users and application systems, each user uniquely corresponds to a user number and user key, and each application system uniquely corresponds to an application system number and application system password, and the user number and user key are judged by a third-party authentication server The credential for whether the user is safe, the application system number and the application system key are the credential for the third-party authentication server to judge whether the application system is safe.
[0041] In this embodiment, a third-party authentication server is used as an execution subject to describe a passwordless ...
no. 2 example
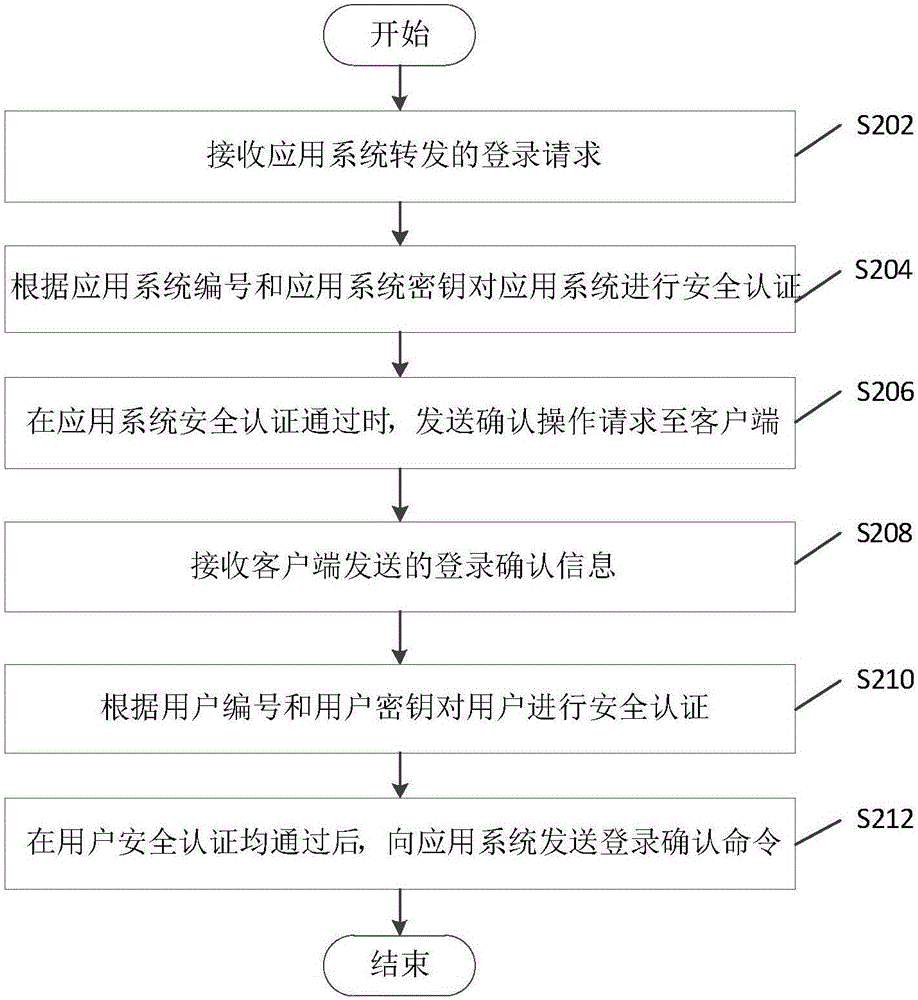
[0065] figure 2 The flow chart of the passwordless login method based on third-party authentication provided by the second embodiment of the present application is a preferred embodiment based on the first embodiment above, and relevant descriptions may refer to each other. Specifically, the method includes the following steps S202 to S212.
[0066] Step S202: Receive the login request forwarded by the application system.
[0067] Wherein, the login request is the content sent by the application system to the third-party authentication server when the login module receives the user number. Specifically, the application system sets up a login module. The login module is also provided with a user number receiving box and a user name and password receiving box. The security authentication process through the user name and password is used for security authentication, so that the embodiment of this application is compatible with the password login method in the prior art; when ...
no. 3 example
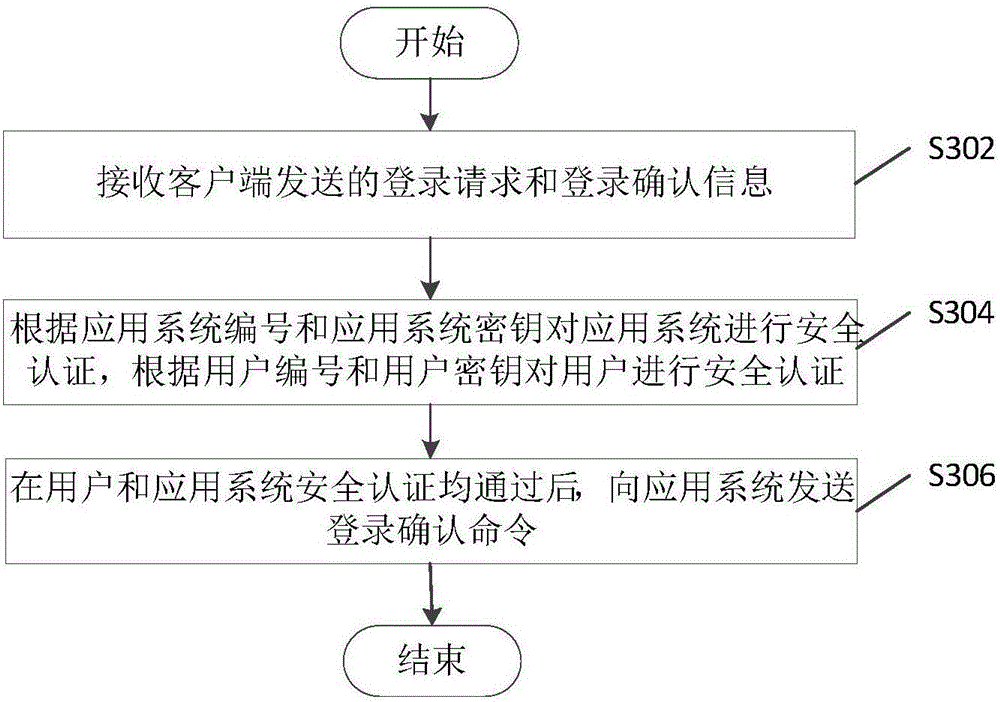
[0079] image 3 The flow chart of the third-party authentication-based passwordless login method provided by the third embodiment of the present application is a preferred embodiment based on the above-mentioned first embodiment, and relevant descriptions may refer to each other. Specifically, the method includes the following steps S302 to S306.
[0080] Step S302: Receive the login request and login confirmation information sent by the client.
[0081] In this embodiment, the client is provided with a scanning tool for scanning the image to obtain the application system number and the application system key, for example, a two-dimensional code scanning tool, which generates the two-dimensional code information for the application system number and the application system key, and scans the After the tool scans the QR code, the application system number and application system key can be obtained. The client is used to display the receiving control for receiving the confirmat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com