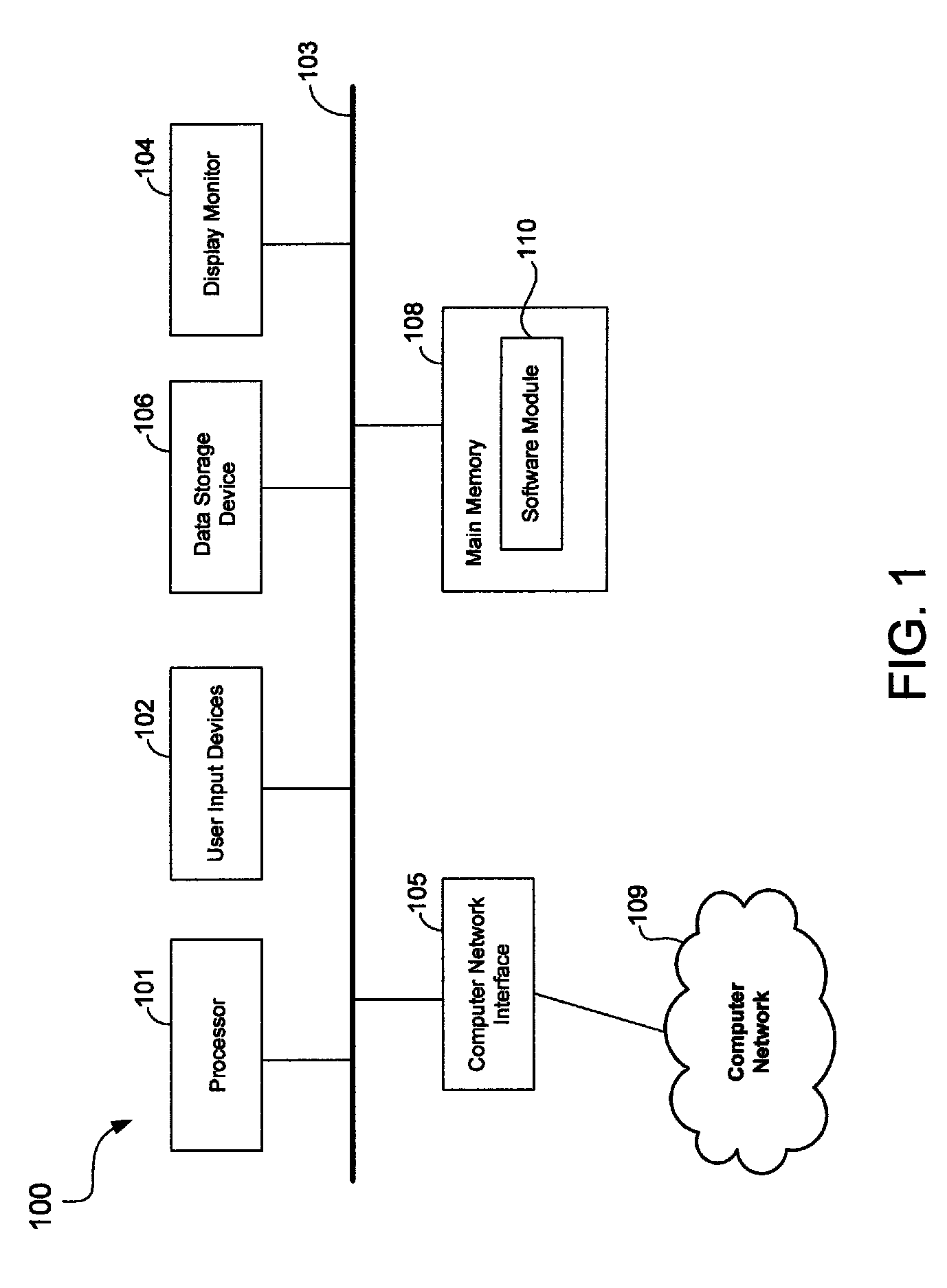
Patents
Literature
73 results about "Encrypted file system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
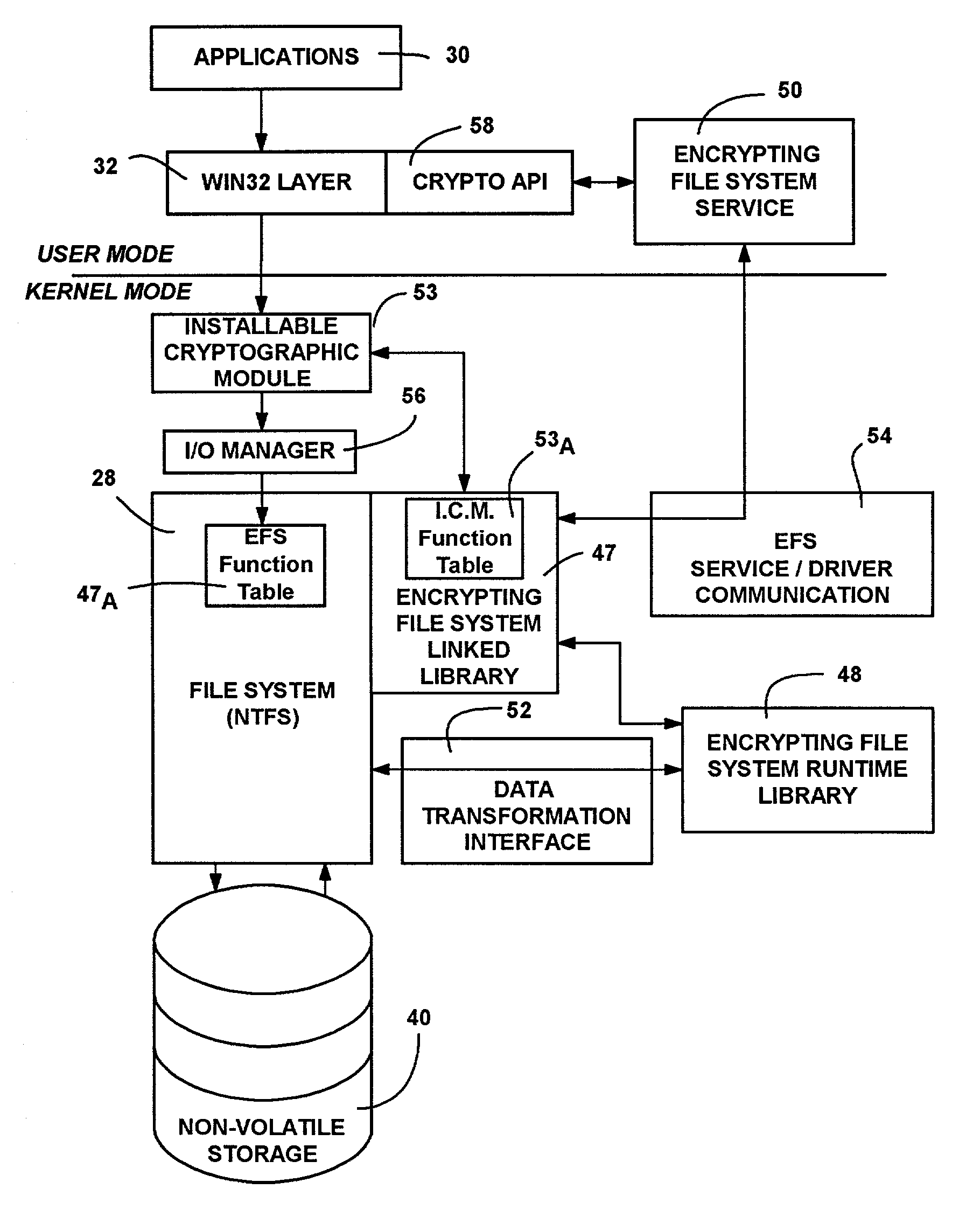
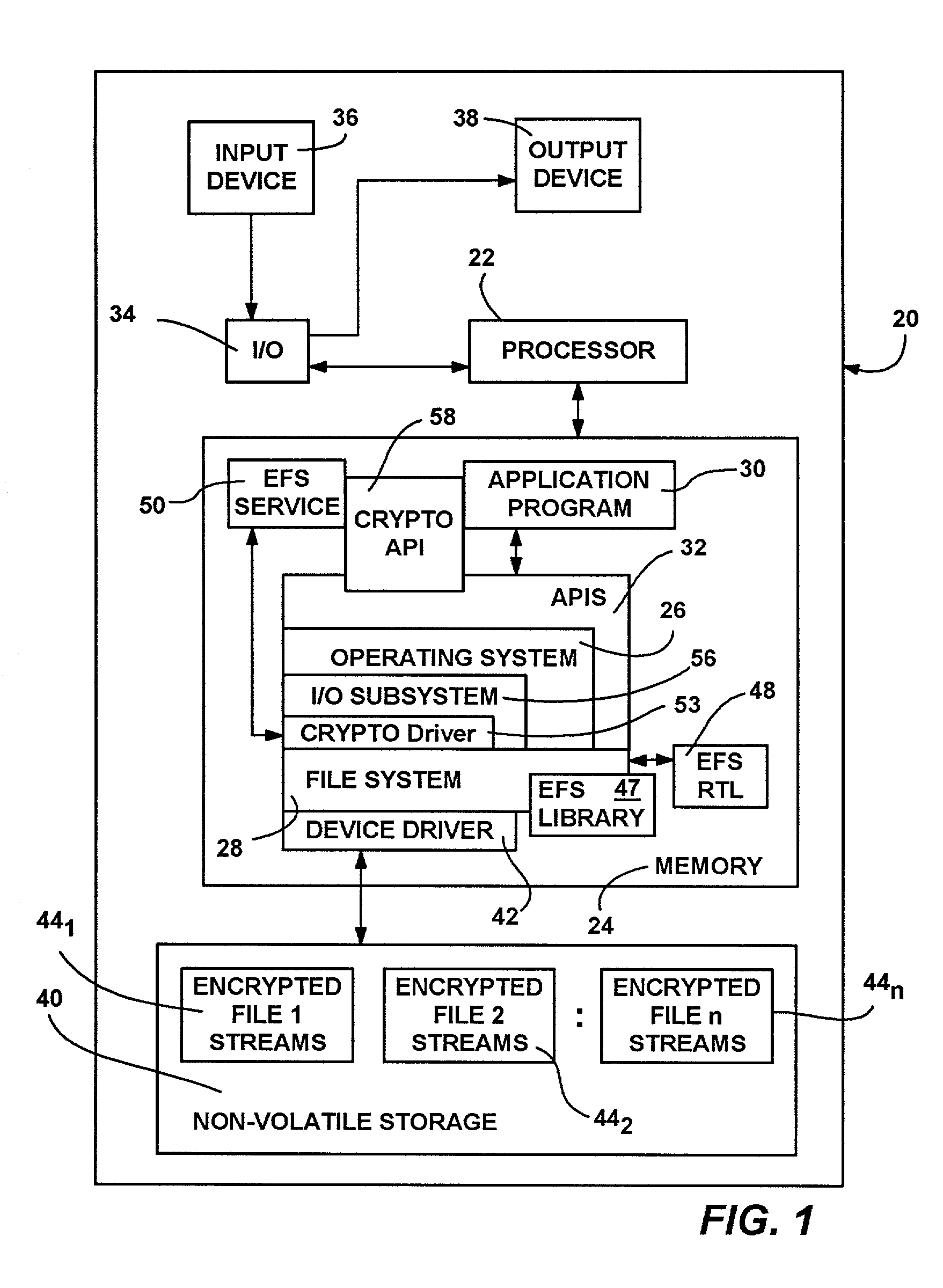
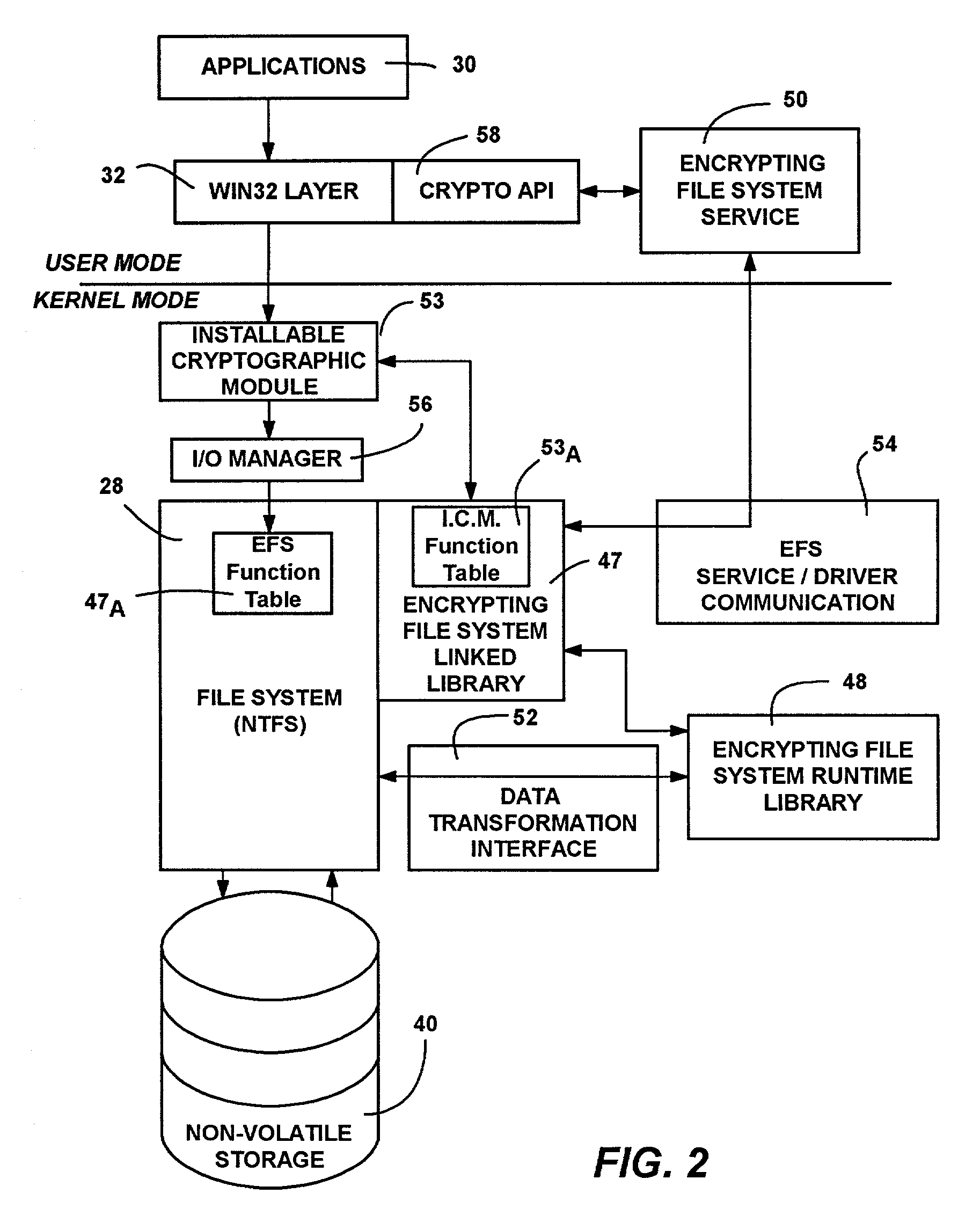
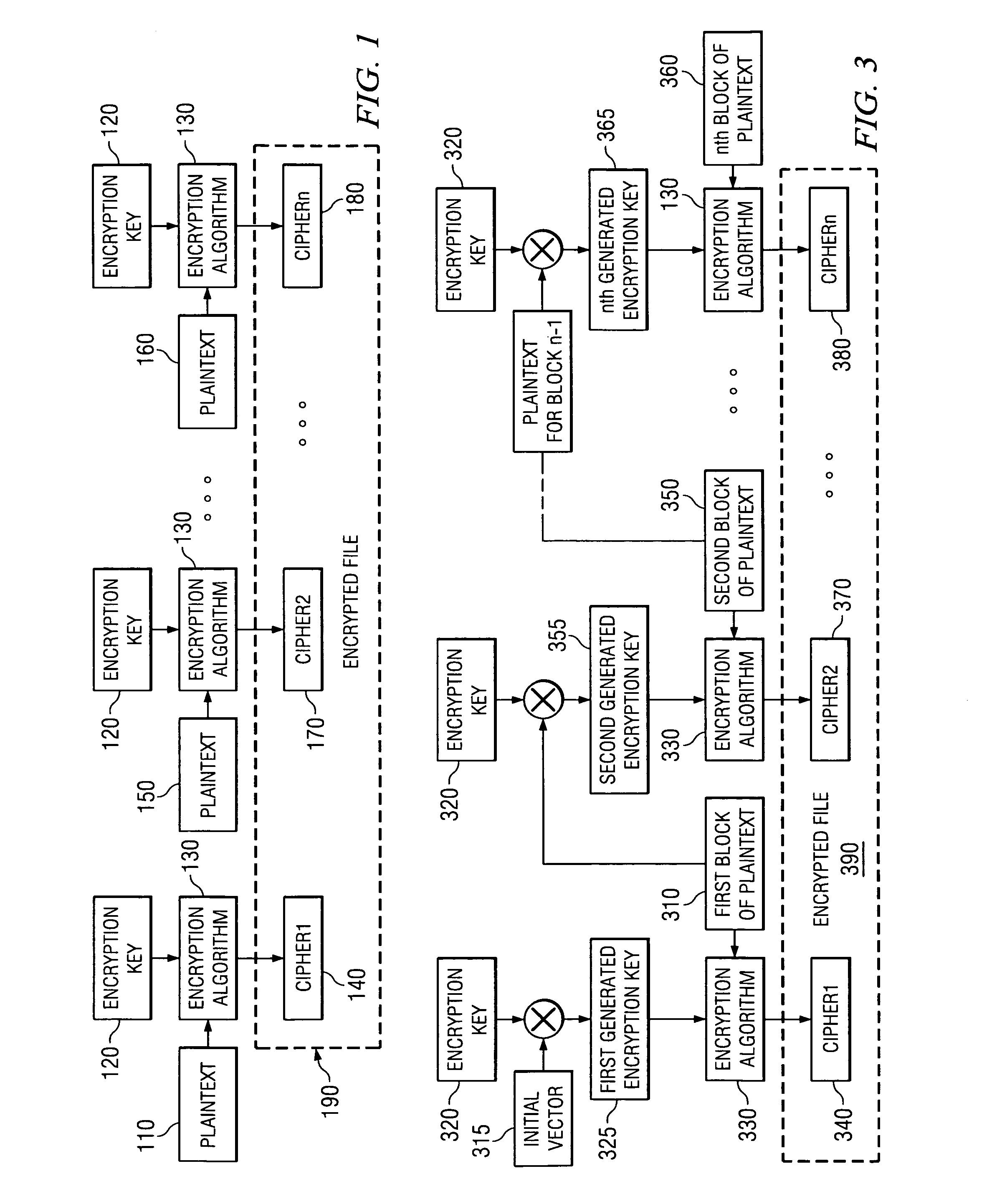
Encrypting File System The Encrypting File System ( EFS) on MicrosoftWindows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption. ... EFS works by encrypting a file with a bulk symmetric key, also known as the File Encryption Key, or FEK. It uses a symmetric encryption algorithm because it takes less time to encrypt and decrypt large amounts of data than if an asymmetric key cipher is used.
Encrypting file system and method
InactiveUS6986043B2Key distribution for secure communicationDigital data processing detailsEncrypted file systemRandom number generation
A system and method for encryption and decryption of files. The system and method operate in conjunction with the file system to transparently encrypt and decrypt files in using a public key-private key pair encryption scheme. When a user puts a file in an encrypted directory or encrypts a file, data writes to the disk for that file are encrypted with a random file encryption key generated from a random number and encrypted with the public key of a user and the public key of at least one recovery agent. The encrypted key information is stored with the file, whereby the user or a recovery agent can decrypt the file data using a private key. With a correct private key, encrypted reads are decrypted transparently by the file system and returned to the user. One or more selectable encryption and decryption algorithms may be provided via interchangeable cryptographic modules.
Owner:MICROSOFT TECH LICENSING LLC
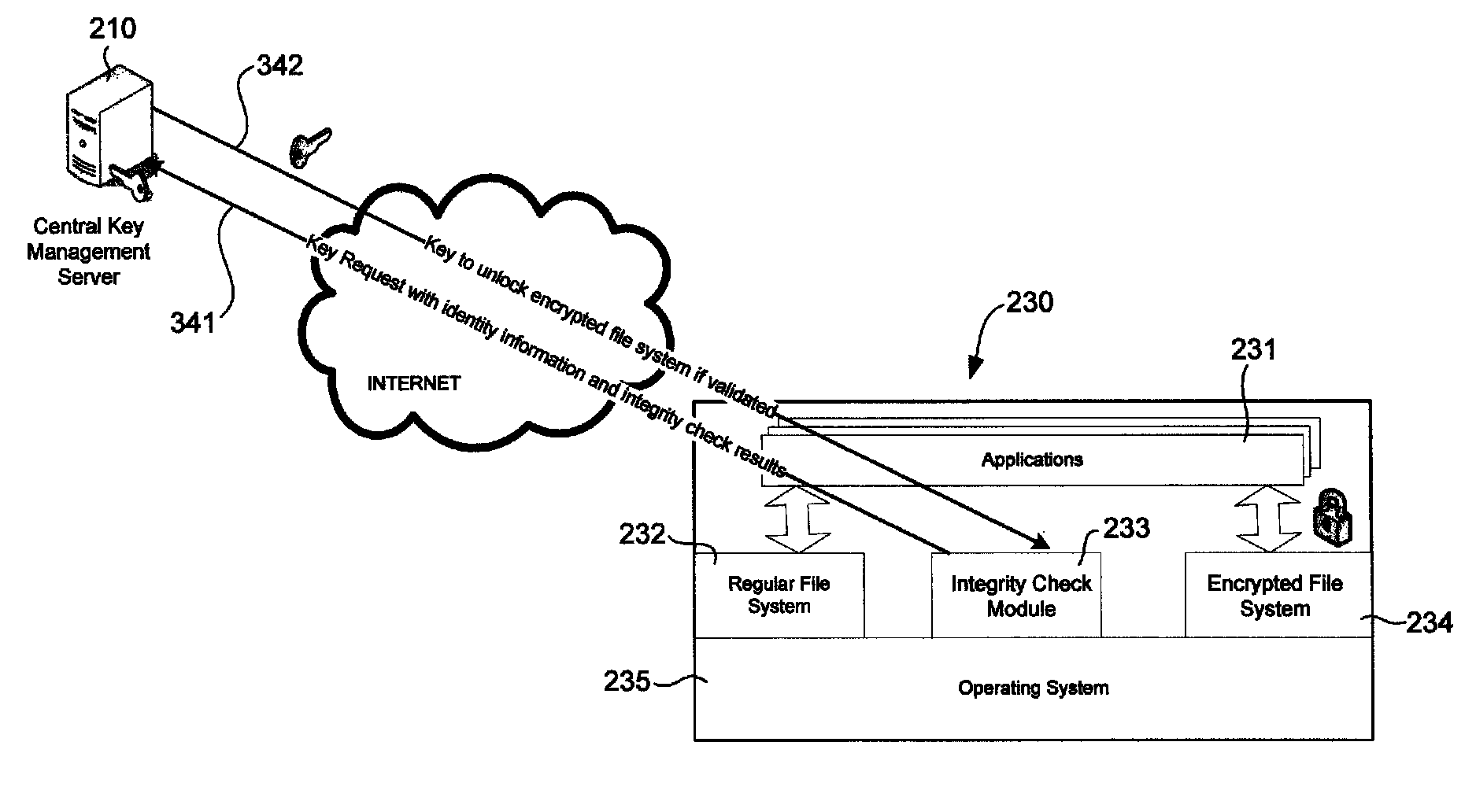
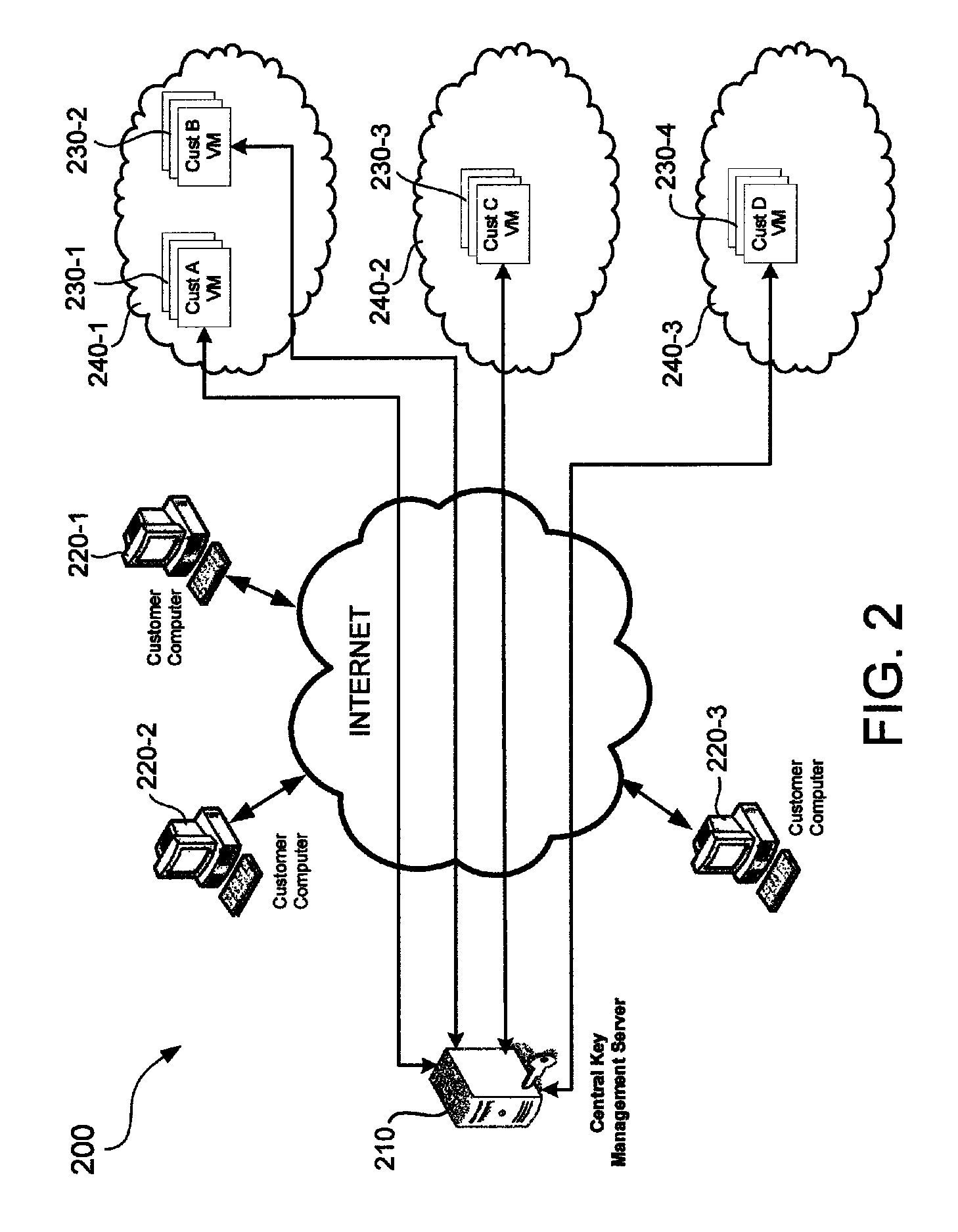
Protection of customer data in cloud virtual machines using a central management server
ActiveUS8826013B1Complete banking machinesKey distribution for secure communicationEncrypted file systemCentral management
A cloud computing environment includes a key management server and a cloud computer system running several virtual machines. A virtual machine hosted by the cloud computer system includes an integrity check module for checking the integrity of the virtual machine and getting identity information of the virtual machine. The integrity check module sends a key request to a key management server, which provides key service to different cloud computer systems. The key management server validates the request and, if the request is valid, provides the key to the virtual machine. The key is used to unlock an encrypted file system in the virtual machine.
Owner:TREND MICRO INC
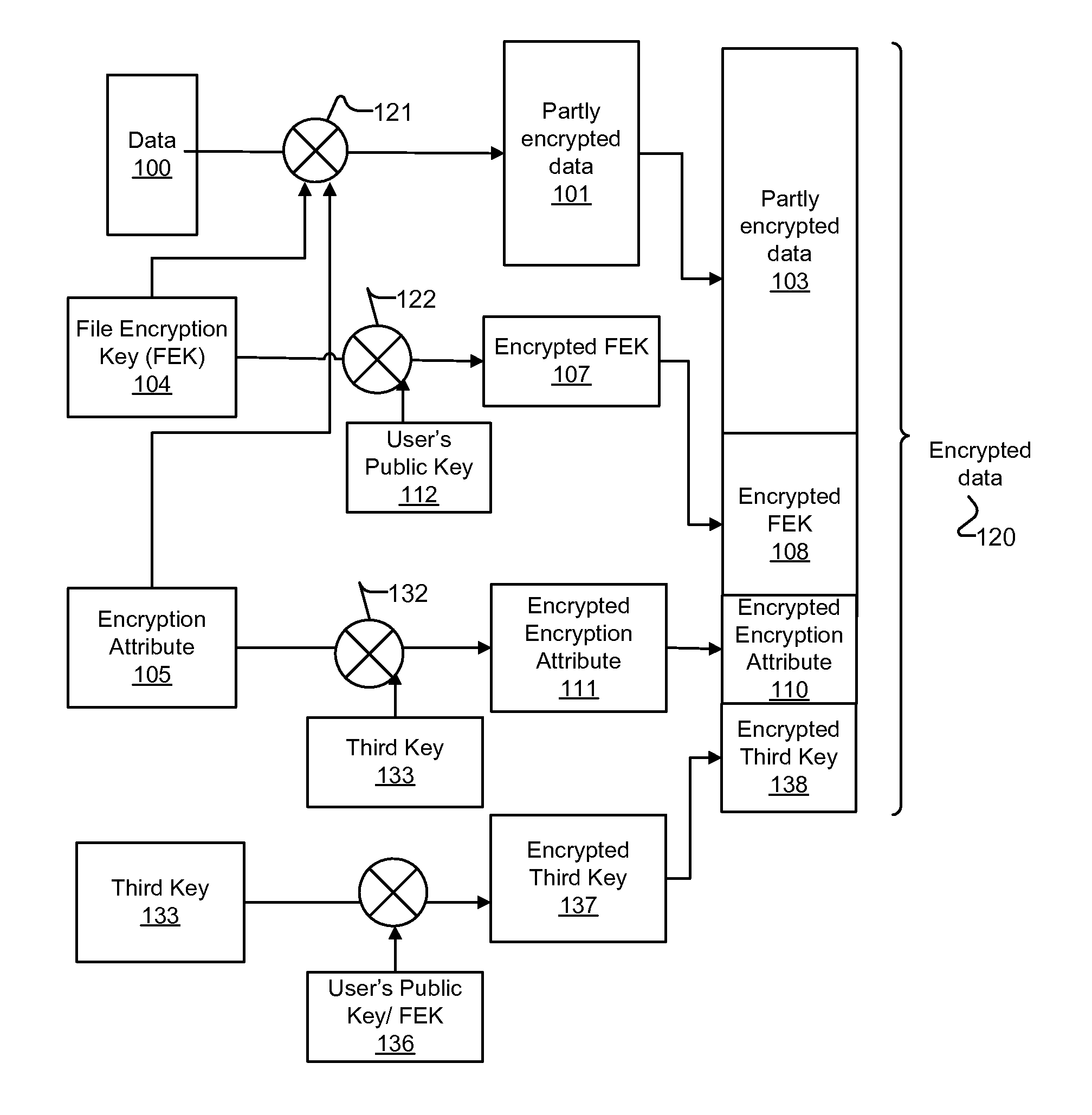
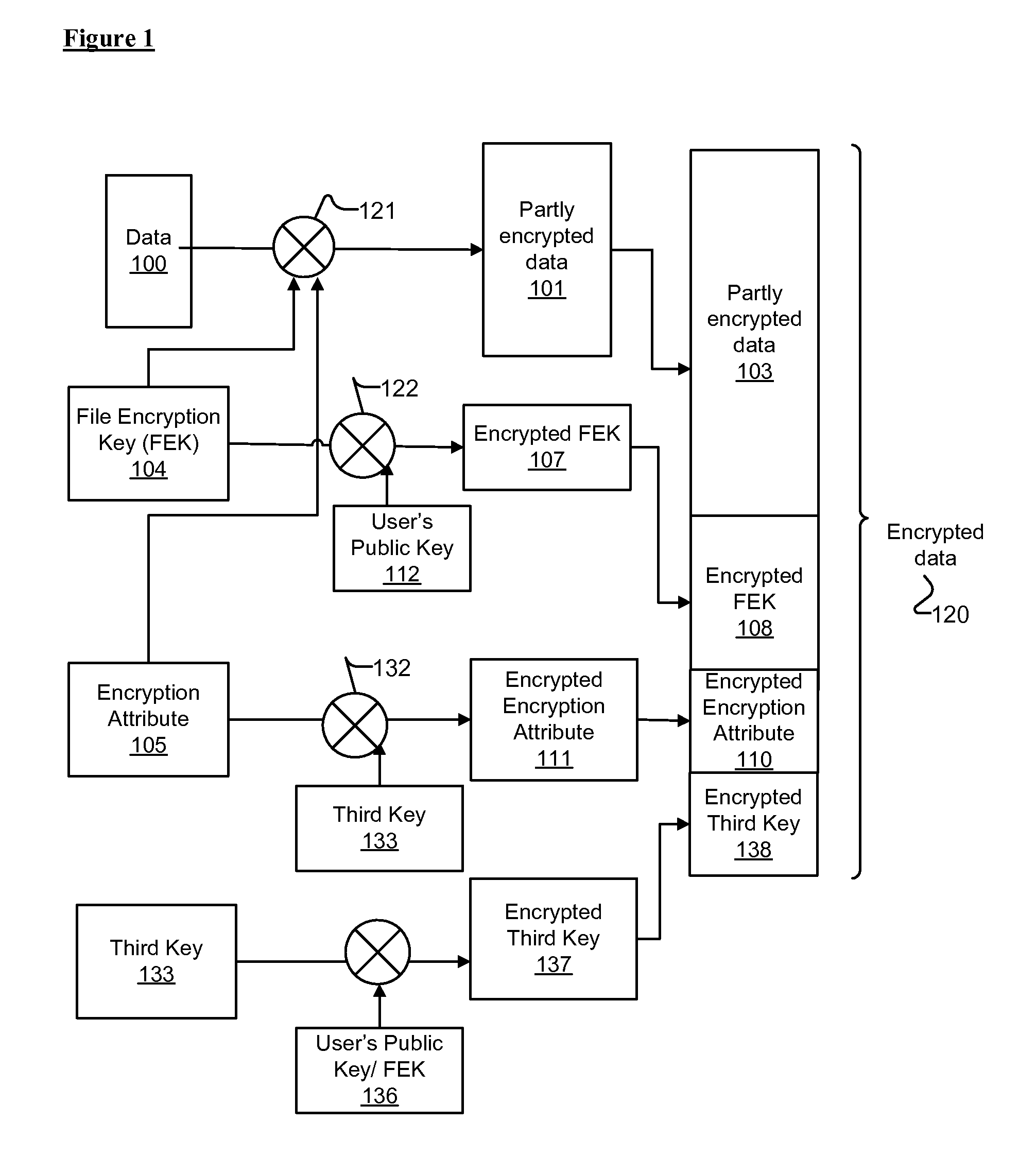
Multi-key cryptography for encrypting file system acceleration
ActiveUS20120057696A1Multiple keys/algorithms usagePublic key for secure communicationEncrypted file systemComputer science
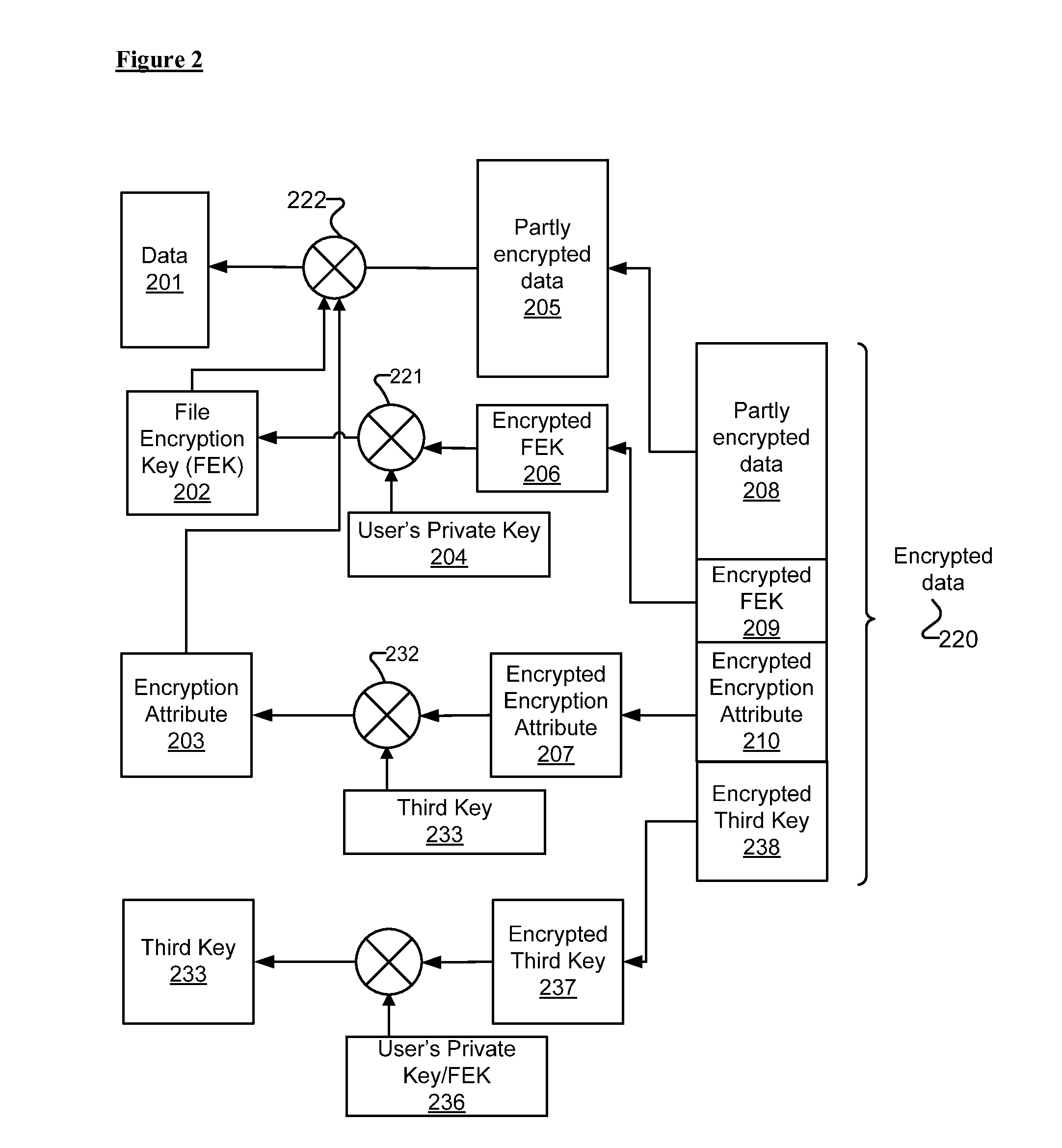
Embodiments of methods and systems for encrypting and decrypting with encryption attributes are presented. An encryption attribute contains information to identify one or more segments of a file to be encrypted. An encryption process encrypts those one or more segments to generate a partly encrypted file instead of encrypting the entire file. That is, the file includes some data that are encrypted and some data that are not. In one embodiment, at least three encryption keys are used such that the encryption attribute is encrypted with using a third key.
Owner:INTEL CORP
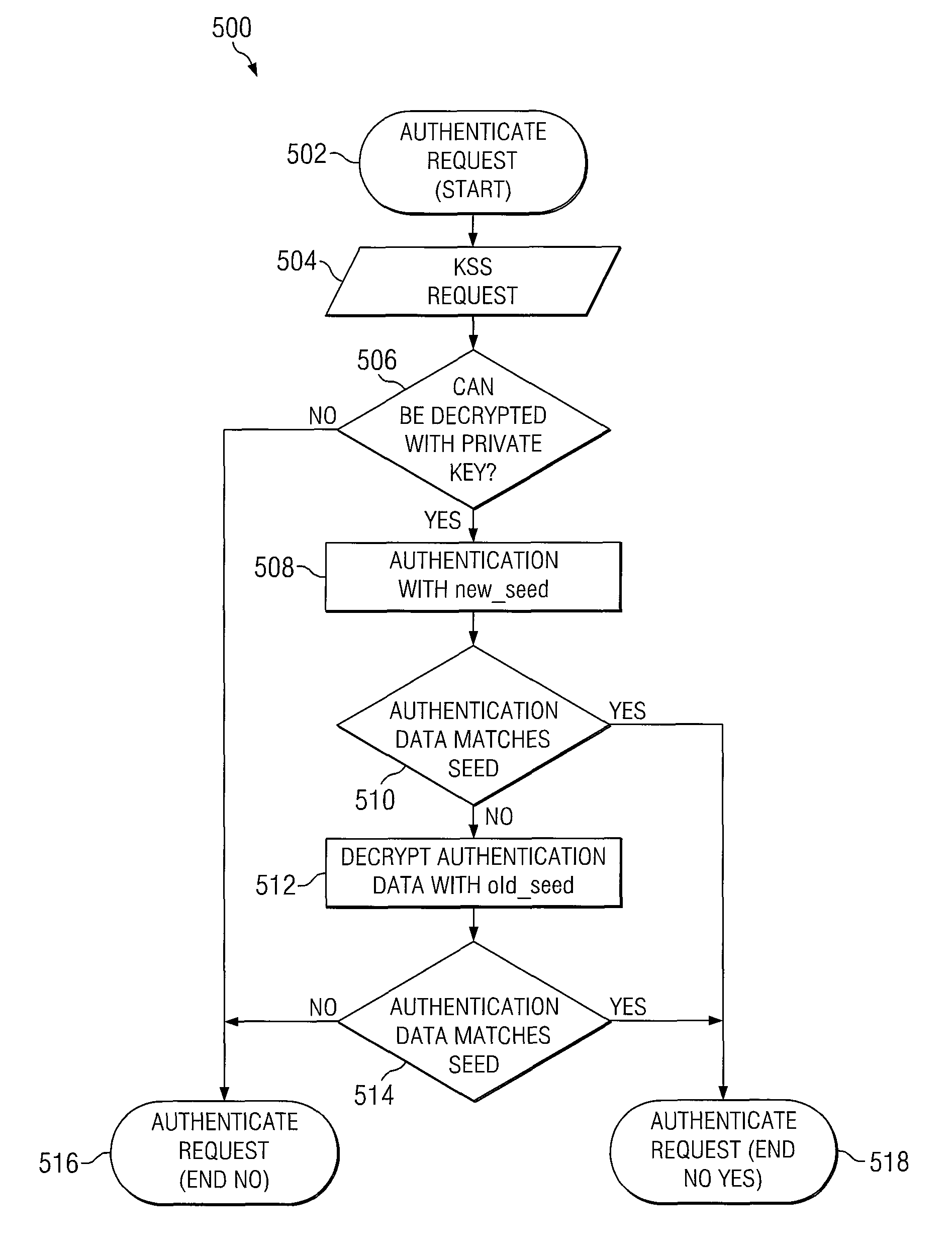
System and method for communicating with a key management system
ActiveUS8667267B1Digital data processing detailsUser identity/authority verificationKey serverBlock match
A method for providing authenticated access to an encrypted file system includes generating a first seed; providing a request for a key to a key server, the request including at least a first seed block having a first encryption, a message block having a second encryption, and an encryption encapsulation block having a third encryption, the encryption encapsulation block including information for decrypting the message block; at the key server, decrypting the encryption encapsulation block and using the information therein to decrypt the at least a first seed block and the message block; and authenticating the message if the first seed in the at least a first seed block matches a first predetermined seed.
Owner:CLOUDERA
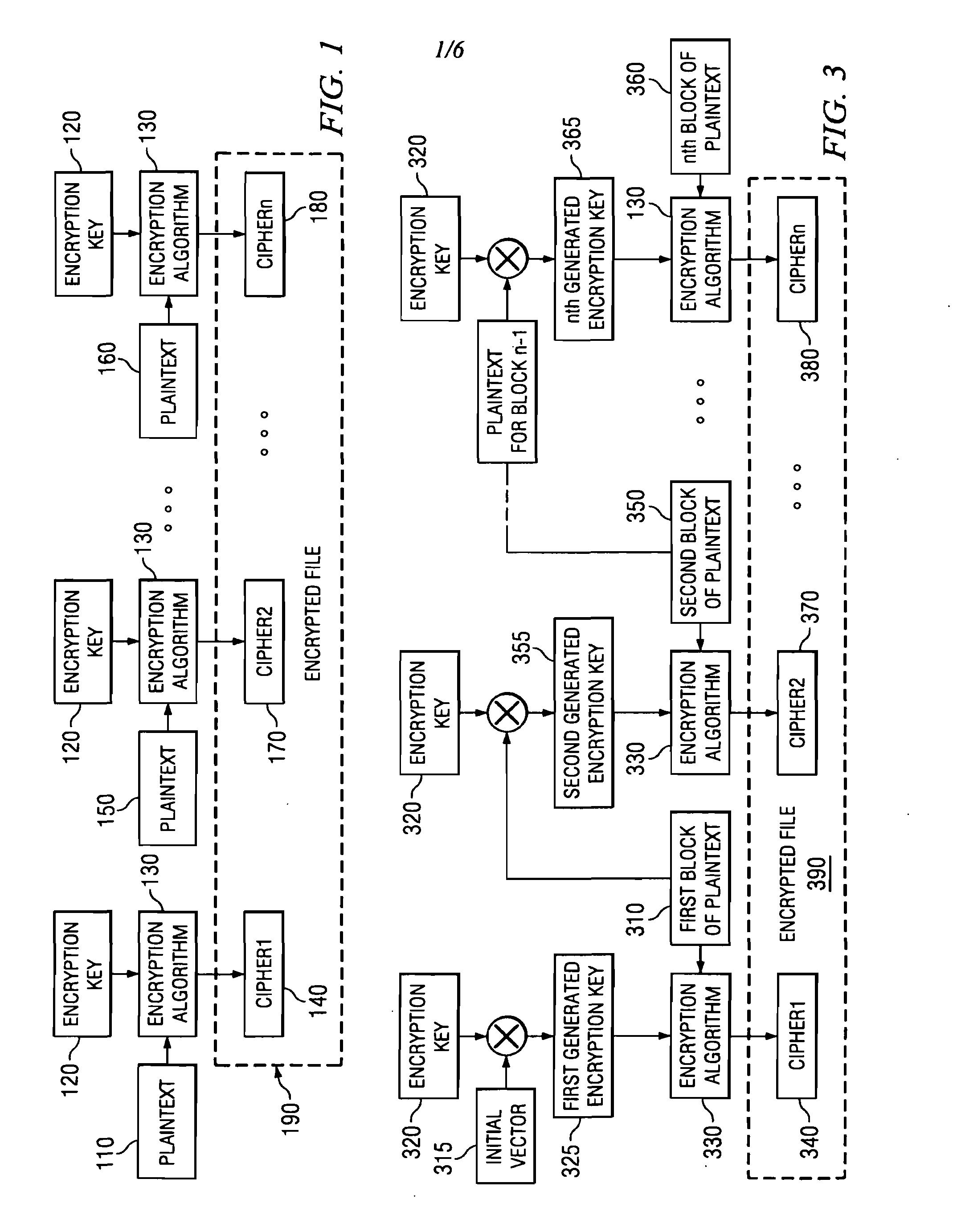
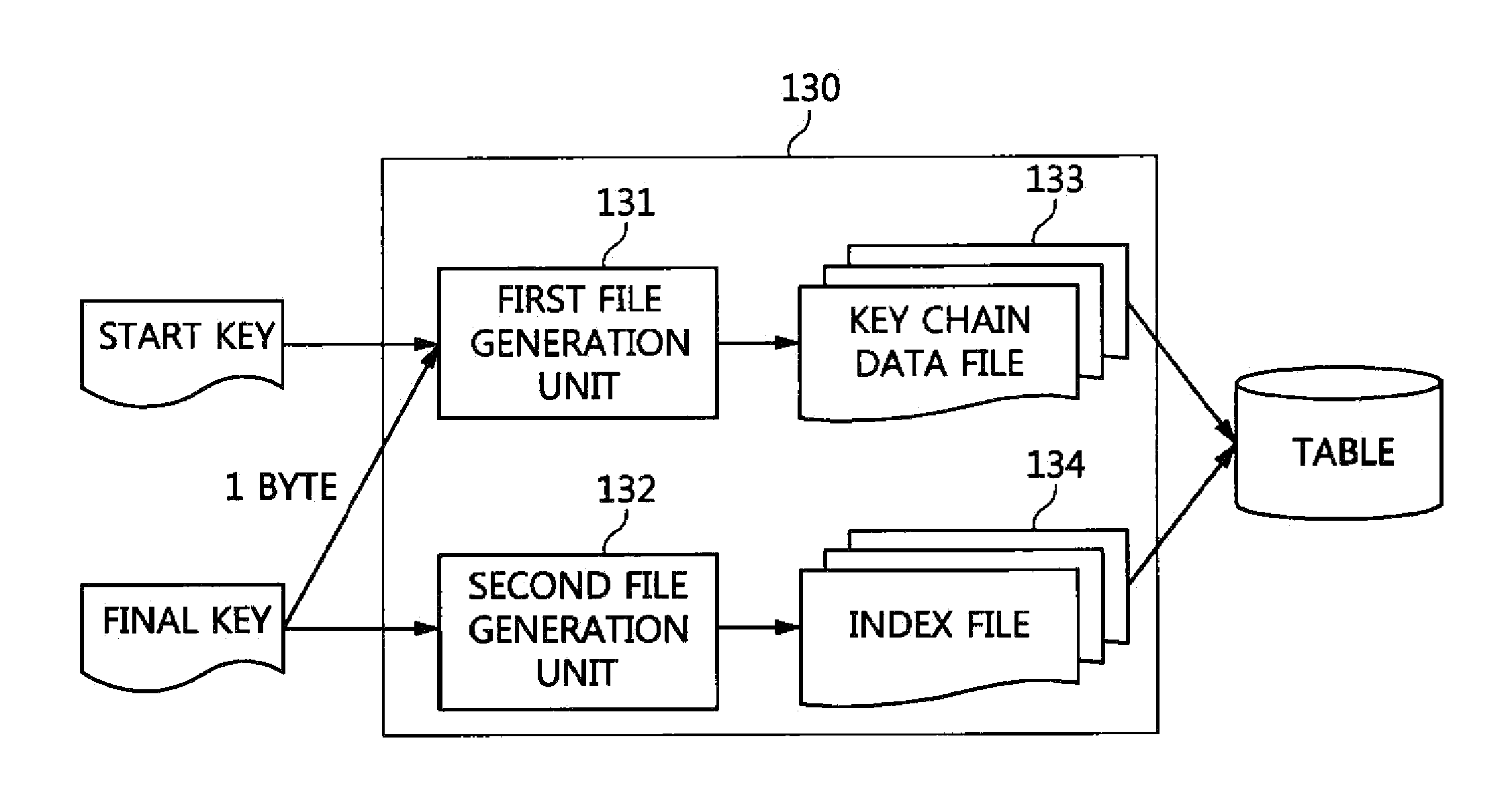
Encryption apparatus and method for providing an encrypted file system
InactiveUS7428306B2Reduce the amount requiredReduce in quantityMultiple keys/algorithms usageComputer security arrangementsComputer hardwarePlaintext
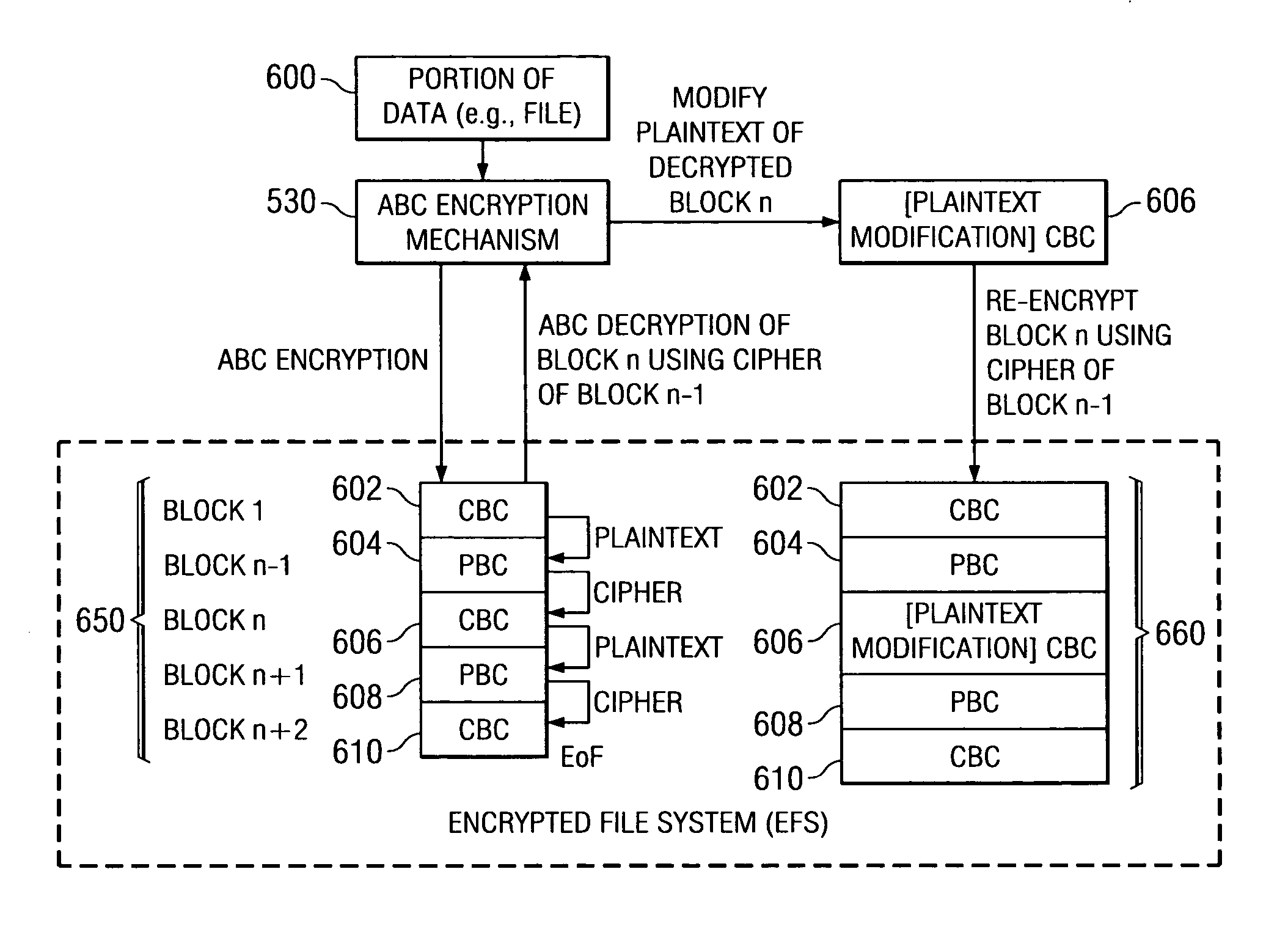
An encryption apparatus and method for providing an encrypted file system are provided. The encryption apparatus and method of the illustrative embodiments uses a combination of encryption methodologies so as to reduce the amount of decryption and re-encryption that is necessary to a file in the Encrypted File System in the event that the file needs to be modified. The encryption methodologies are interleaved, or alternated, with regard to each block of plaintext. In one illustrative embodiment, Plaintext Block Chaining (PBC) and Cipher Block Chaining (CBC) encryption methodologies are alternated for encrypting a sequence of blocks of data. The encryption of a block of plaintext is dependent upon the plaintext or a cipher generated for the plaintext of a previous block of data in the sequence of blocks of data so that the encryption is more secure than known Electronic Code Book encryption methodologies.
Owner:IBM CORP
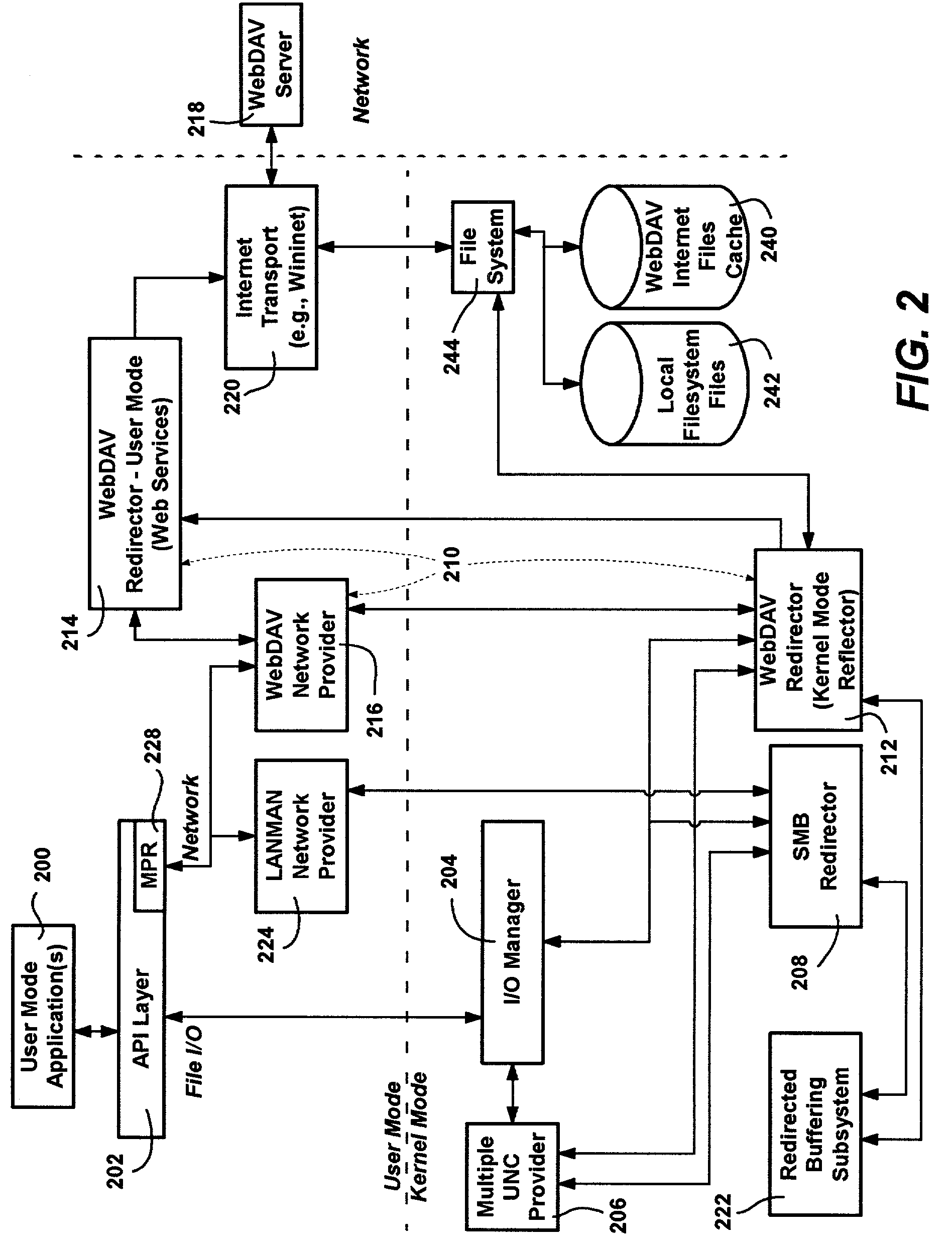
System and method for providing transparent access to distributed authoring and versioning files including encrypted files
InactiveUS7437429B2Data processing applicationsMultiple digital computer combinationsApplication softwareEncrypted file system
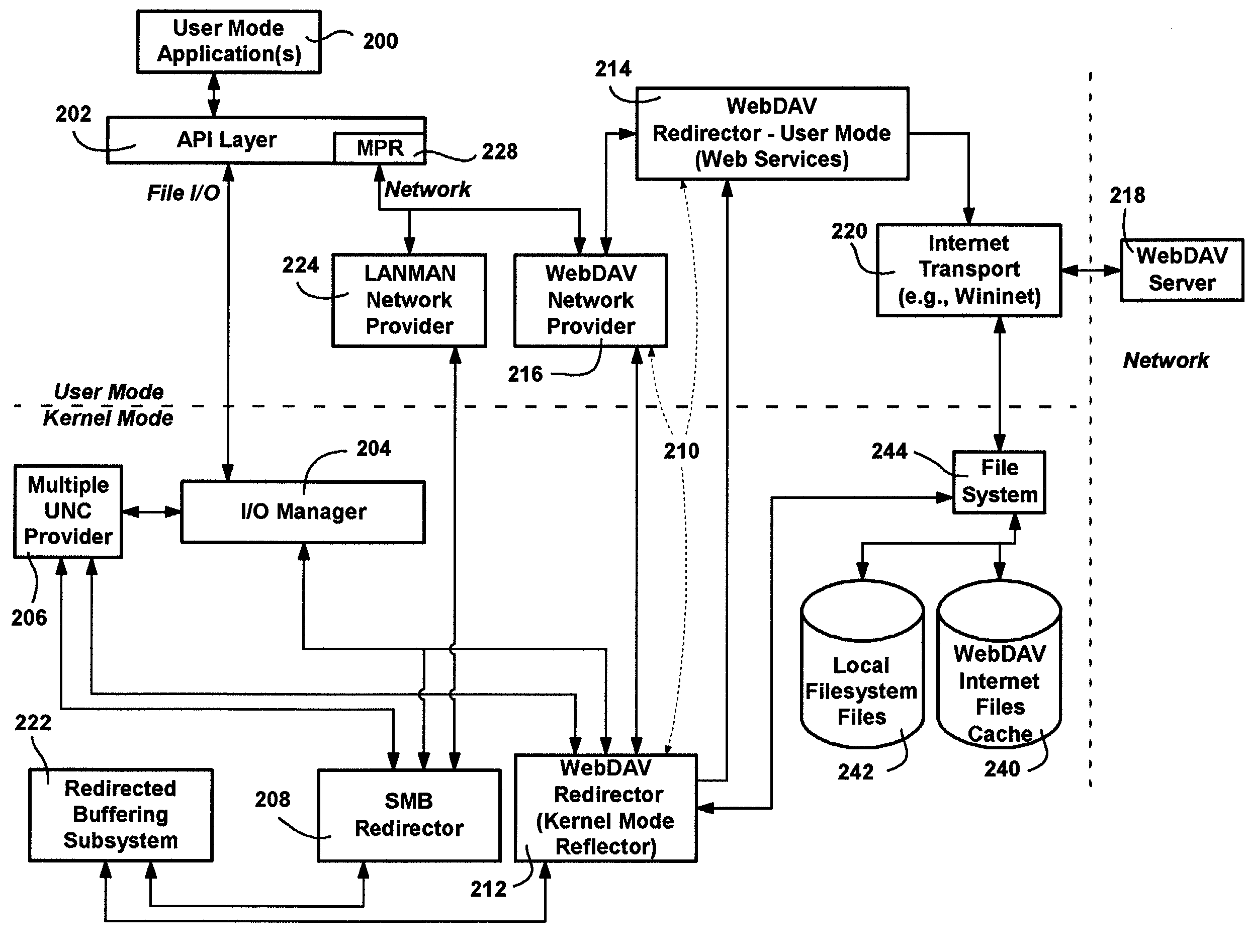
Access to WebDAV (Distributed Authoring and Versioning) servers is provided in a manner that is essentially transparent to applications. A WebDAV redirector and related components support file system I / O requests and network requests directed to WebDAV servers identified by URI (Universal Resource Identifier) names, or by a drive may be mapped to a WebDAV share. An application's create or open I / O requests directed to a WebDAV server are detected, and result in a local copy of the file being downloaded and cached for local access. When closed, the local file is uploaded to the WebDAV server. Network-related requests such as for browsing that are directed to a WebDAV server are also handled transparently. WebDAV files may be locally encrypted and decrypted at the file system level, transparent to applications and the WebDAV server, via an encrypting file system that performs local encryption and decryption at the local file system level.
Owner:MICROSOFT TECH LICENSING LLC
Encryption Apparatus and Method for Providing an Encrypted File System
InactiveUS20080310624A1Reduce the amount requiredReduce in quantityEncryption apparatus with shift registers/memoriesComputer security arrangementsPlaintextComputer hardware
An encryption apparatus and method for providing an encrypted file system are provided. The encryption apparatus and method of the illustrative embodiments uses a combination of encryption methodologies so as to reduce the amount of decryption and re-encryption that is necessary to a file in the Encrypted File System in the event that the file needs to be modified. The encryption methodologies are interleaved, or alternated, with regard to each block of plaintext. In one illustrative embodiment, Plaintext Block Chaining (PBC) and Cipher Block Chaining (CBC) encryption methodologies are alternated for encrypting a sequence of blocks of data. The encryption of a block of plaintext is dependent upon the plaintext or a cipher generated for the plaintext of a previous block of data in the sequence of blocks of data so that the encryption is more secure than known Electronic Code Book encryption methodologies.
Owner:INT BUSINESS MASCH CORP
Revocation of a system administrator in an encrypted file system
ActiveUS20090116649A1Safe storageMultiple keys/algorithms usageDigital data processing detailsElectronic informationEncrypted file system
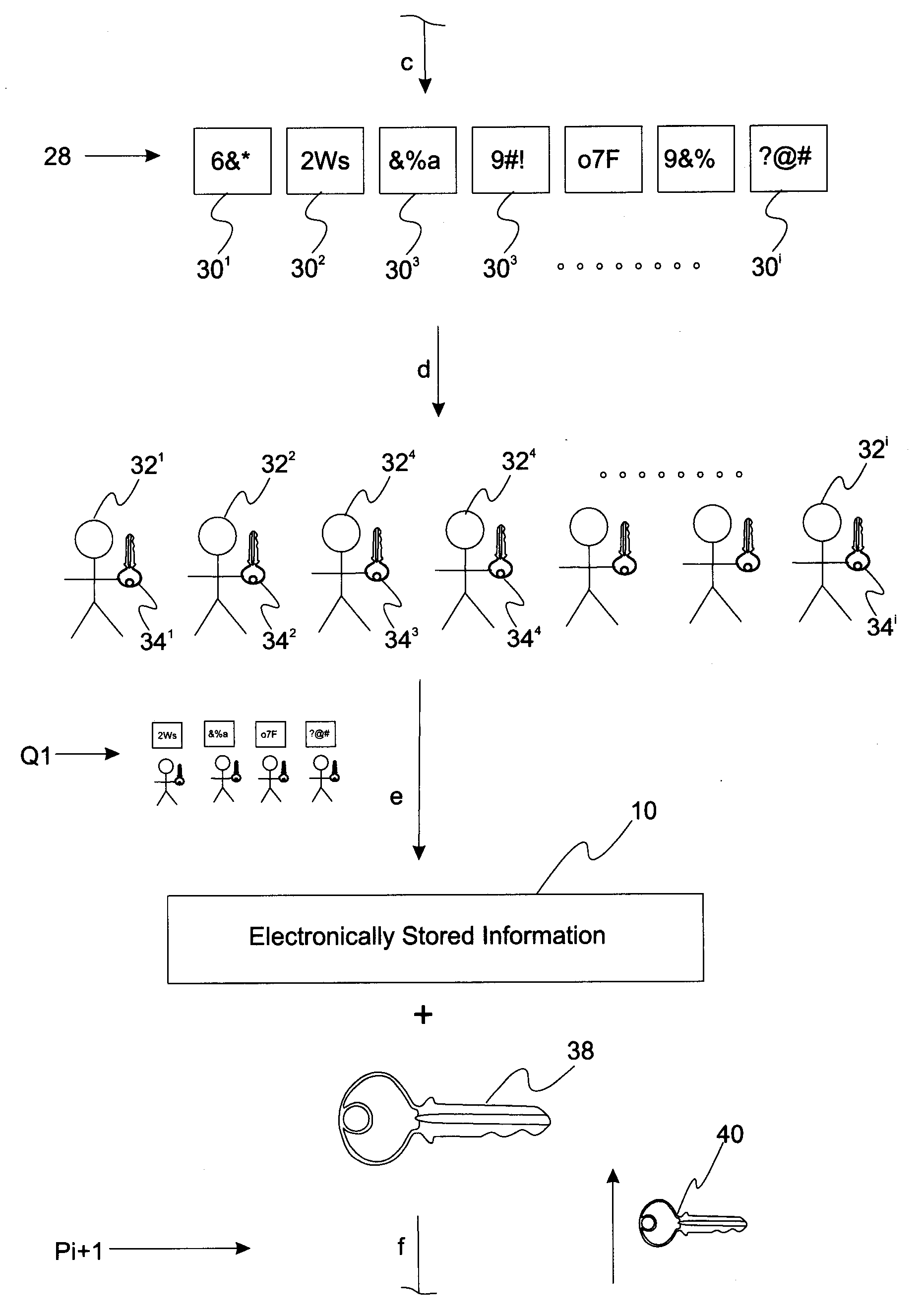
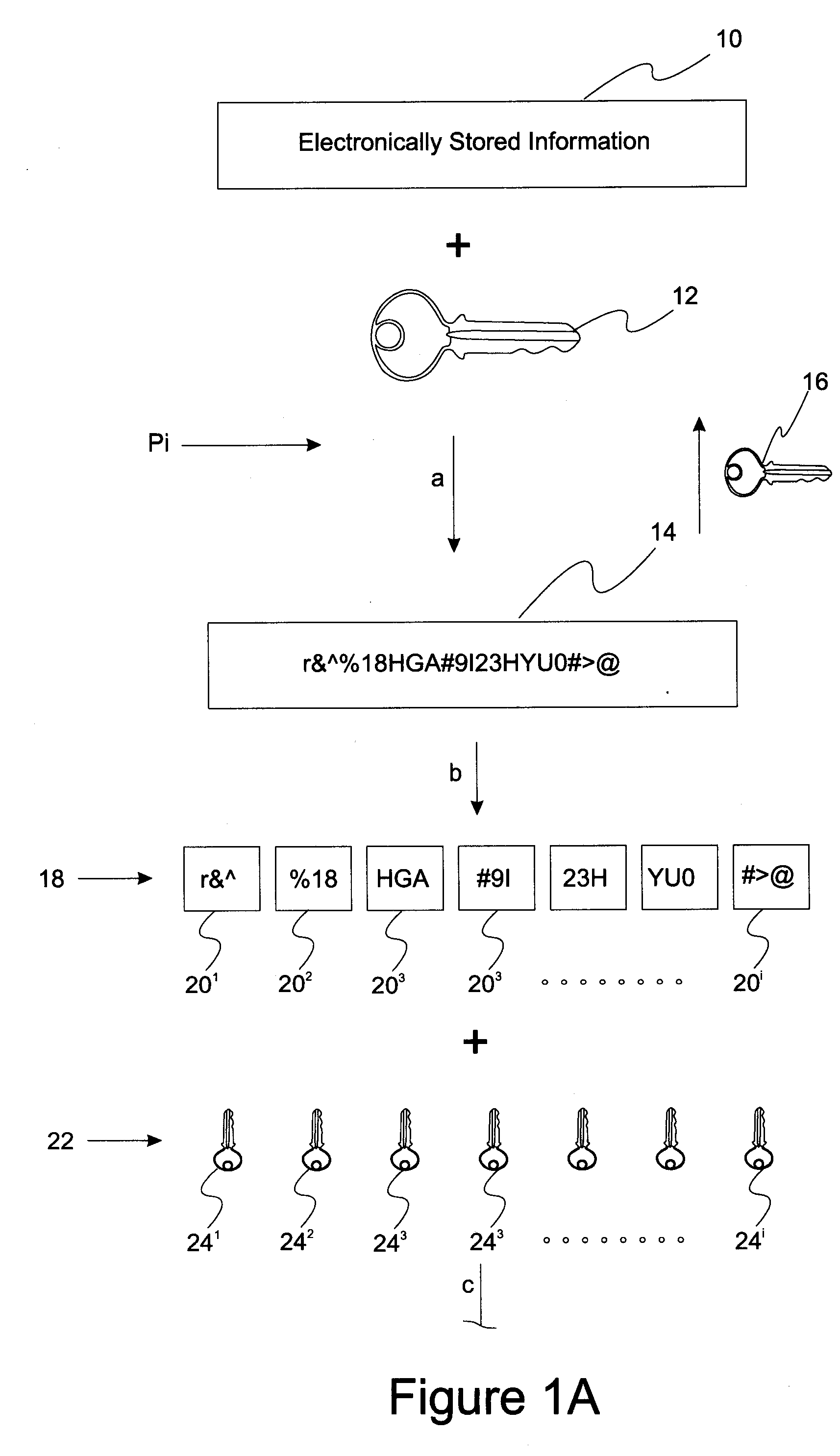
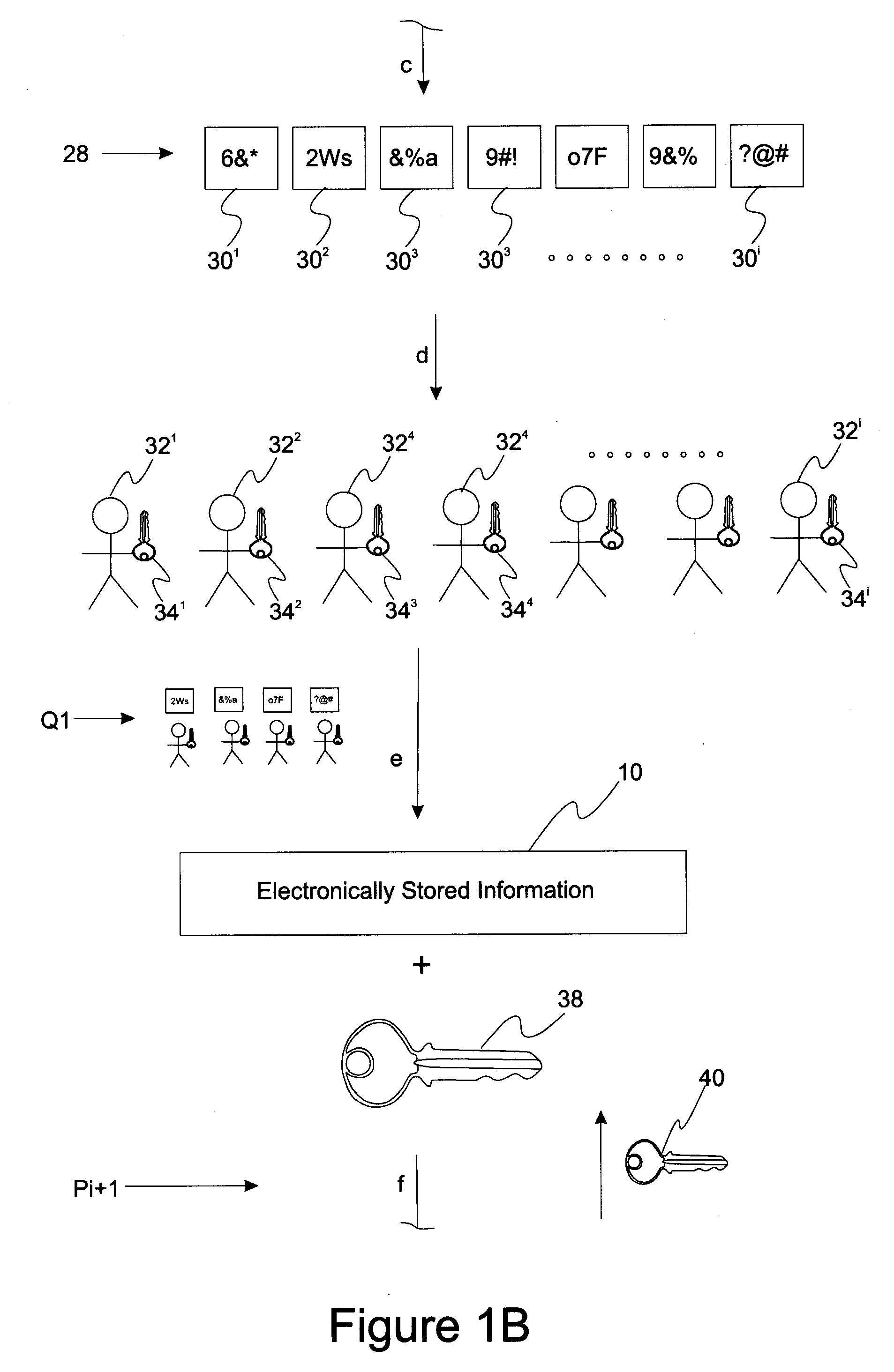
A method of securely storing electronic information includes a step in which target electronically stored information is encrypted with a first encryption key and then partitioned into a first set of encrypted ESI partitions a subset of which is able to reconstruct the unpartitioned encrypted ESI. This first set of encrypted ESI partitions is then encrypted with a first set of user encryption keys to form a first set of user-associated encrypted ESI partitions that are made available to a first set of users. When access to the target electronically stored information is changed, the target electronically stored information is accessed and then re-encrypted with a second encryption key to form a second encrypted ESI. This second encrypted ESI is then partitioned and distributed to a second set of users.
Owner:ORACLE INT CORP
File encryption method and electronic device
ActiveCN105260668AEnsure safetyImprove confidentialityDigital data protectionComputer hardwareEncrypted file system
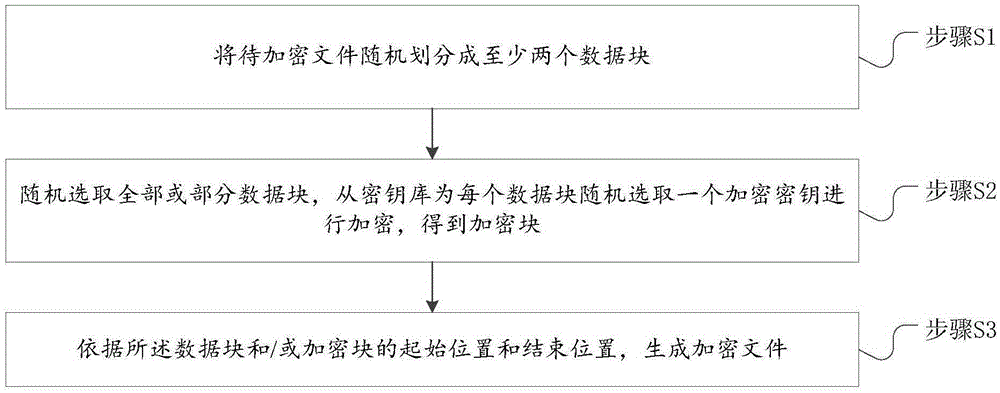
The present invention discloses a file encryption method and an electronic device. The method comprises: after determining a to-be-encrypted file, randomly dividing the to-be-encrypted file into at least two data blocks; then randomly selecting all or a part of the data blocks, and randomly selecting one encryption key from a key library for each data block to perform encryption to obtain an encrypted block; and then generating an encrypted file according to starting locations and ending locations of the data blocks and / or the encrypted blocks. According to the file encryption method and the electronic device provided by the present invention, the whole to-be-encrypted file is divided, thereby increasing the encryption efficiency; and during encryption, selection of the data blocks and selection of the encryption key are both random, so that the secrecy of the encrypted file is improved, the decryption difficulty is increased, and the security of the encrypted file is ensured.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
User mode encrypt file system
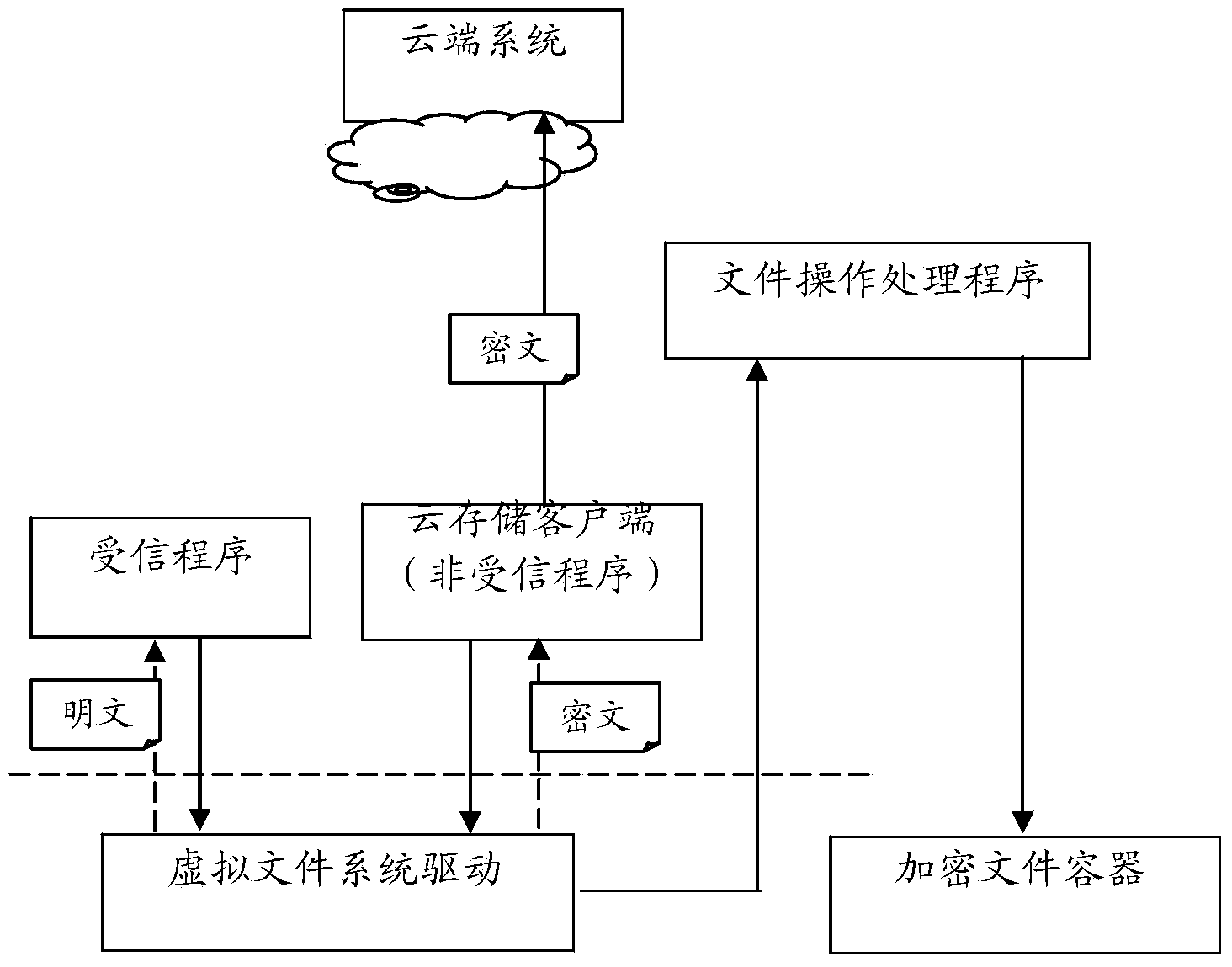
The invention discloses a user mode encrypt file system capable of automatically achieving encryption of a cloud storage file. The system comprises an encrypt file container, a virtual file system drive and file operation processing program, wherein the encrypt file container is used for storing the encrypt file and comprises organization structures of a file and a file catalogue in the internal part; the virtual file system drive and file operation processing program map the file and the file catalogue in the encrypt file container to a virtual file tray or a virtual file catalogue of a computer file system, transform an operation of application program or system program aiming at the file and the file catalogue in the virtual file tray or the virtual file catalogue into an operation aiming at the file and the file catalogue in the encrypt file container, and automatically decrypt or encrypt file data read or written by accredited program in the treatment process. The file data read from the virtual file tray or the virtual file catalogue as a cloud storage client of unaccredited program are encrypted.
Owner:WUHAN UNIV OF TECH
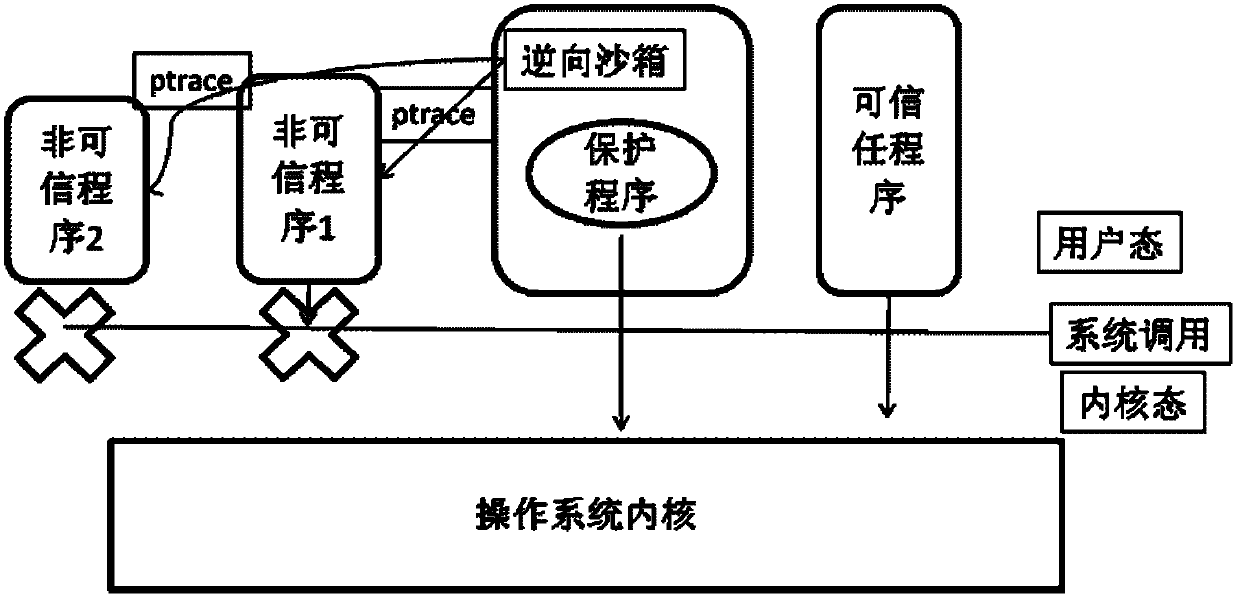
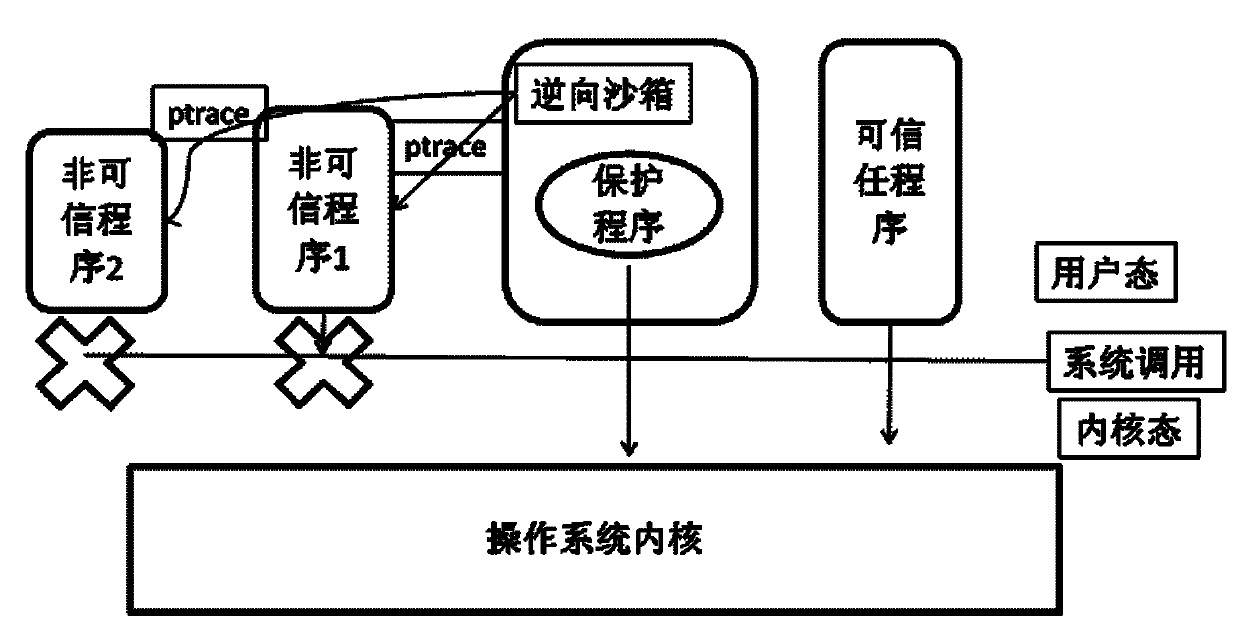
Reverse-sandbox-based mobilephone payment protection method
ActiveCN102184372AAchieve local securityCache data protectionPayment architecturePlatform integrity maintainancePaymentOperational system
The invention provides a reverse-sandbox-based mobilephone payment protection method, comprising the following steps: 1. classifying application programs on the operating system of an Android mobile phone according to the file identification strategy; and 2. stopping non-trusted program and running a protection program on the basis of a reverse sandbox, and starting the non-trusted program after the protection program is running over. The invention further provides an encrypted file system, and all reading and writing of the protection program are redirected to the file system.
Owner:BEIJING BANGCLE TECH CO LTD
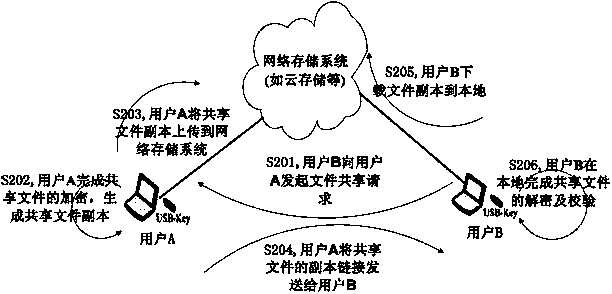
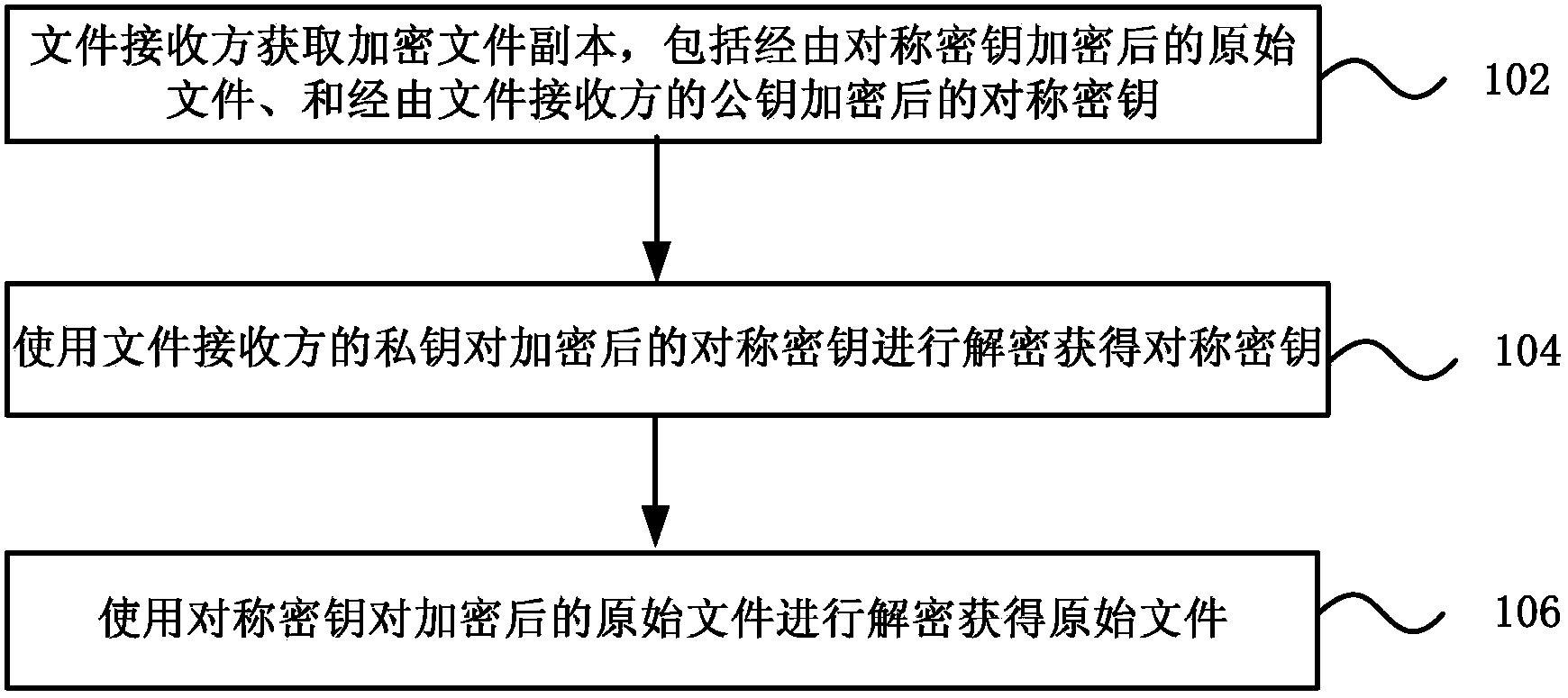
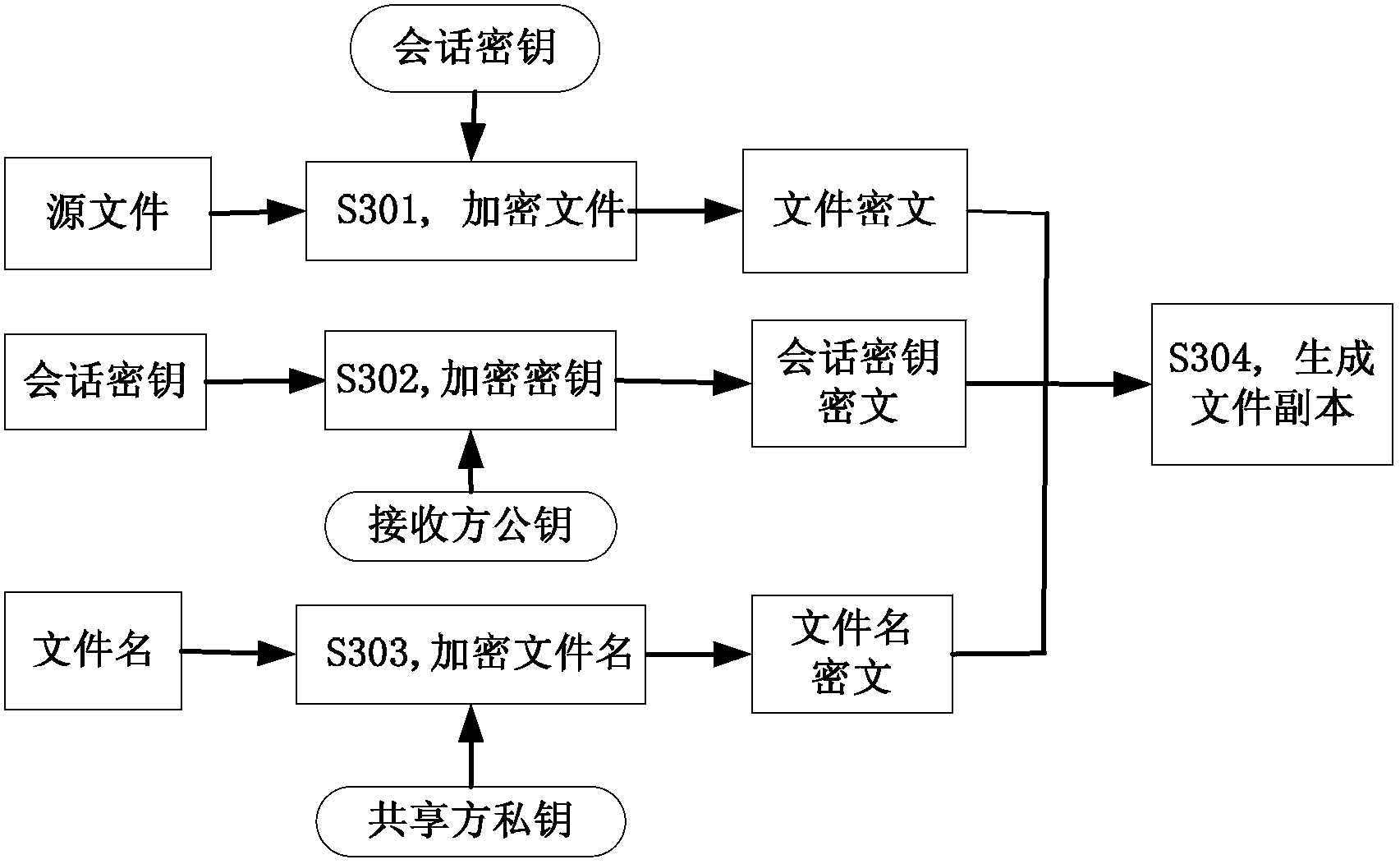
File safe sharing method, system and terminal
ActiveCN103516516ARealize peer-to-peer security sharingImprove securityPublic key for secure communicationUser identity/authority verificationDigital signatureService provision
The invention discloses a file safe sharing method, system and terminal, and relates to the technical field of networks and information safety. The file safe method comprises the steps that a file receiving side obtains an encrypted file copy, the encrypted file copy comprises an original file encrypted by a symmetrical secret key and the symmetrical secret key encrypted by a public key of the file receiving side; a private key of the file receiving side is used for decrypting the encrypted symmetrical secret key and the symmetrical secret key is obtained; the symmetrical secret key is used for decrypting the encrypted original file and an original file is obtained. According to the file safe sharing method, system and terminal, a server does not need to execute the encryption, decryption and verification of the file, point-to-point safe sharing of the file level is achieved, the server side and a service provider cannot obtain the decryption authentication of the file, and therefore safety is higher; in addition, a digital signature using the file sharing method achieves the credibility of the source of the file.
Owner:CHINA TELECOM CORP LTD
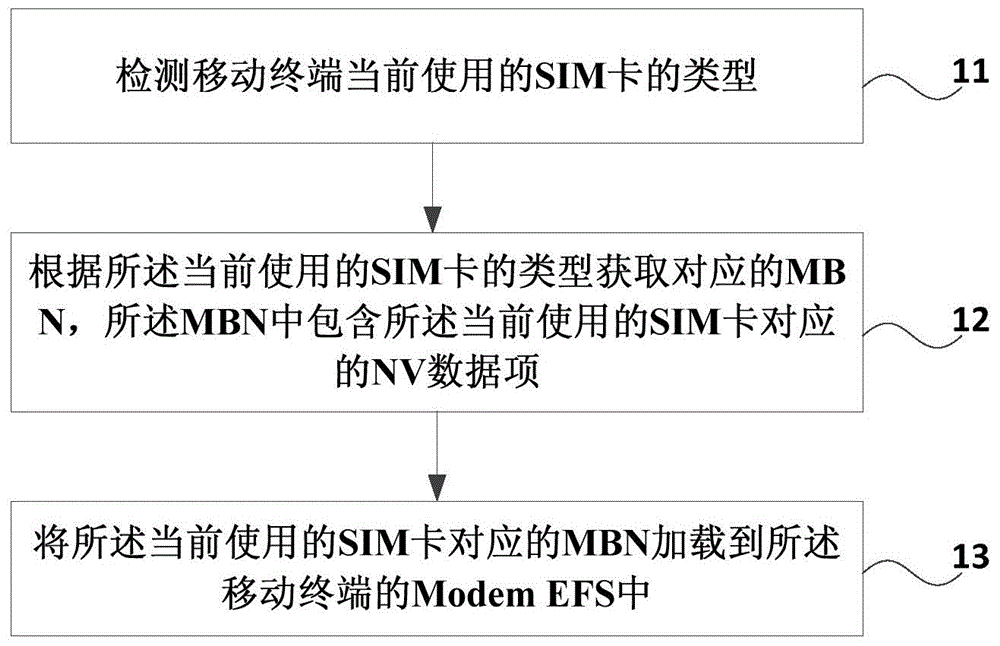
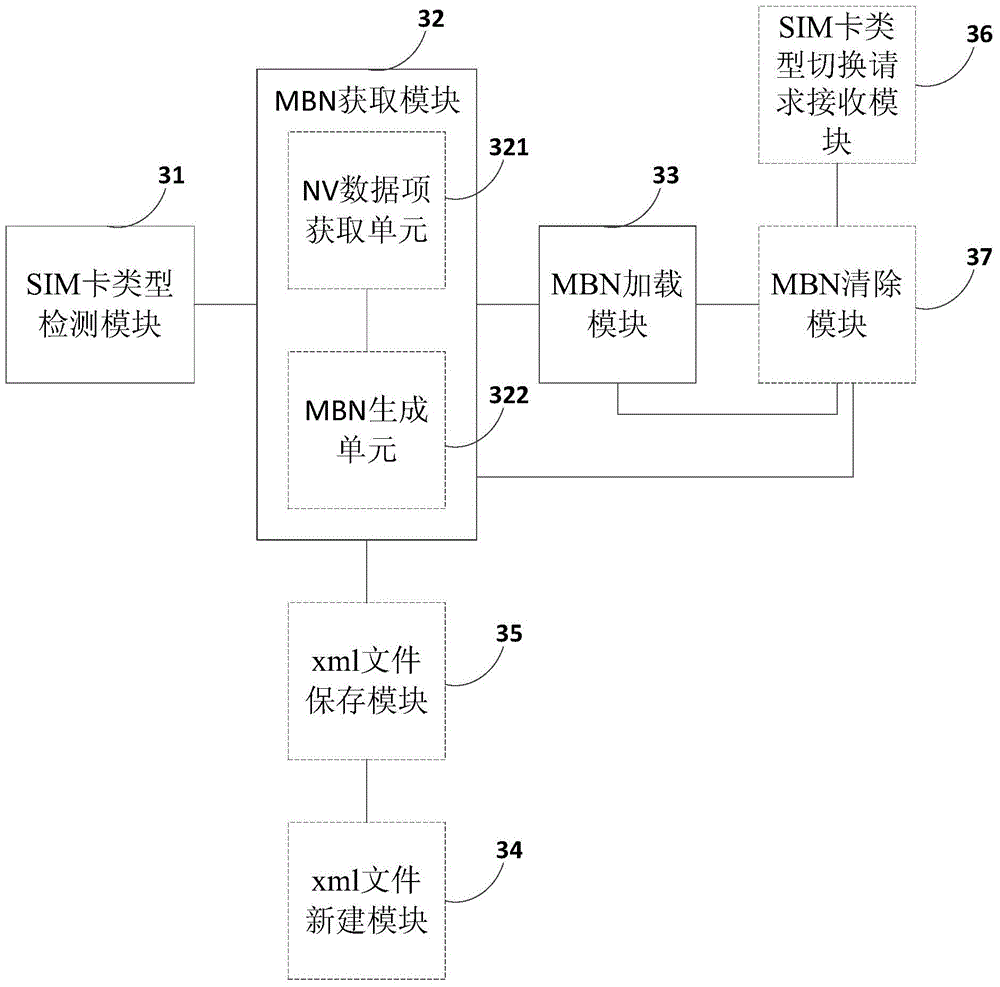
Method and device for automatically loading MBN (ModemConfiguration Binary File)
InactiveCN105101162AImprove loading efficiencyNetwork data managementModem deviceEncrypted file system
The invention discloses a method and device for automatically loading an MBN (ModemConfiguration Binary File). The method comprises the following steps: detecting the type of a subscriber identity module (SIM) card currently used by a mobile terminal; acquiring a corresponding MBN according to the type of the currently-used SIM card, wherein the MBN includes a corresponding nonvolatile item (NV) data item of the currently-used SIM card; and loading the MBN corresponding to the currently-used SIM card into a modem encrypting file system (Modem EFS) of the mobile terminal. Through the embodiment of the invention, the MBN can be loaded into the Modem EFS of a mobile phone automatically, and the loading efficiency is increased.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
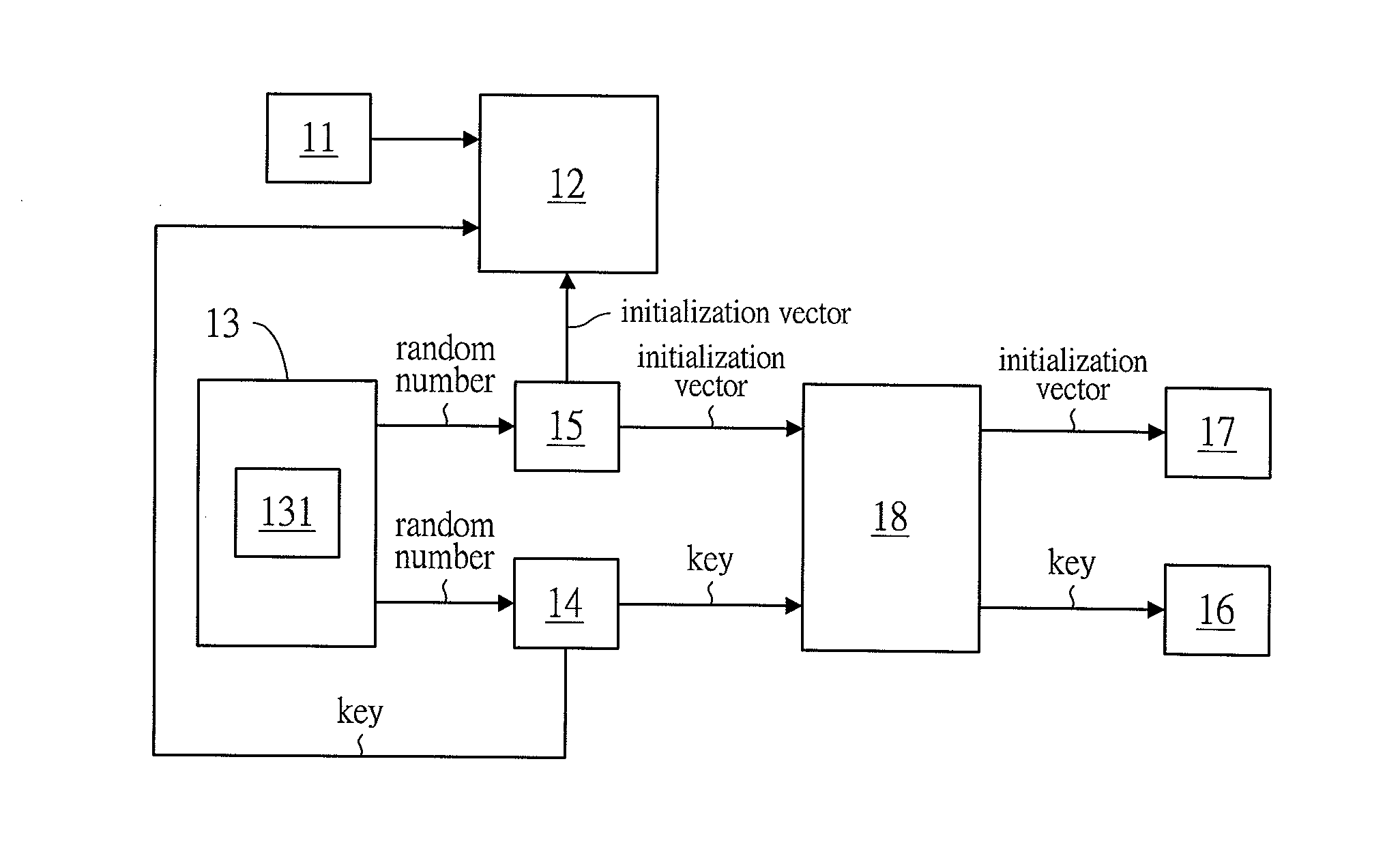
Multiple encrypting method and system for encrypting a file and/or a protocol
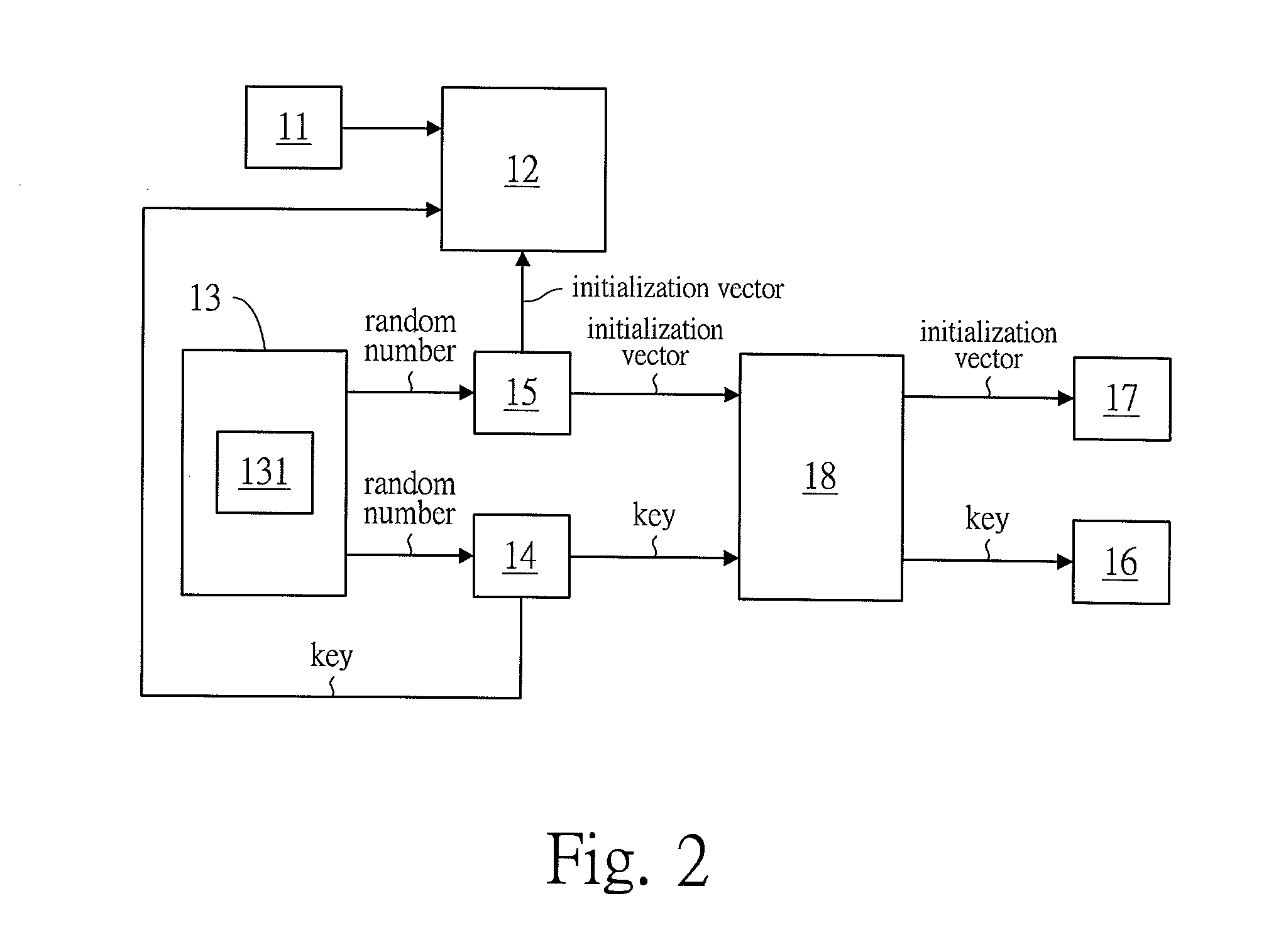
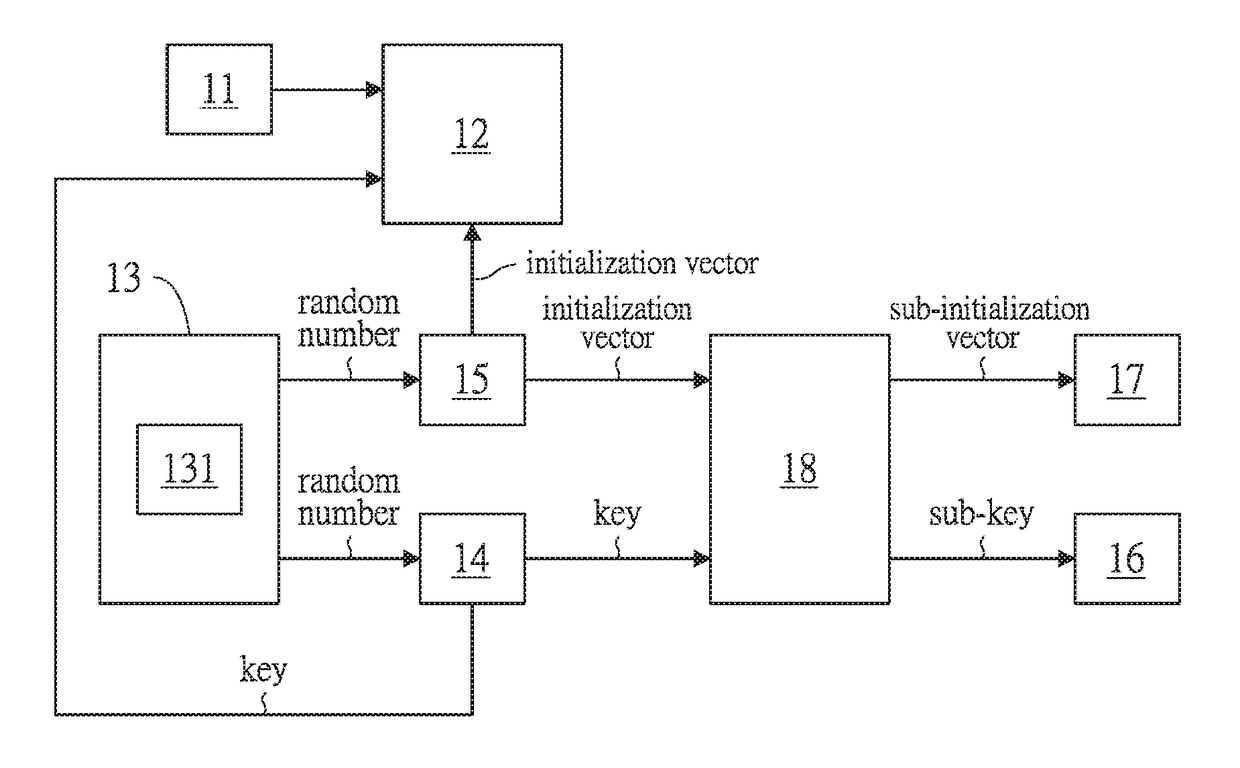
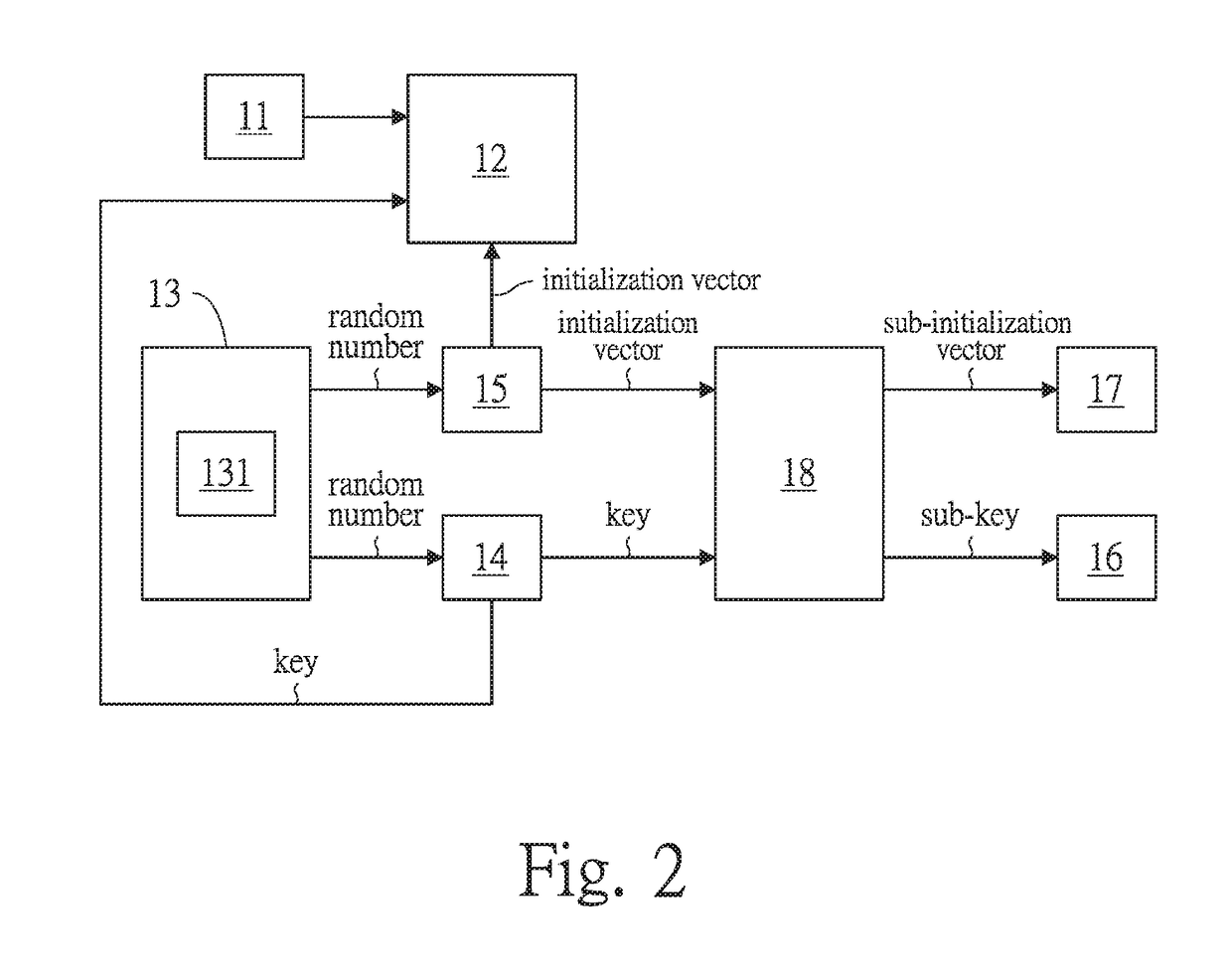
InactiveUS20160028540A1Key distribution for secure communicationMultiple keys/algorithms usageMultiple encryptionInitialization vector
The present invention relates to a multiple encrypting method, for encrypting a file and / or a protocol and generating encryption keys. Comprising the steps of: uploading at least one of a file and a protocol by a file uploading unit; generating random numbers by a random number generation unit; arranging the random numbers to form at least one key and at least one initialization vector respectively by a key generation unit and an initialization vector generation unit; encrypting the file and / or the protocol from the file uploading unit via using AES encryption by an encryption unit, so as to generate an encrypted file and / or an encrypted protocol; saving the key and the initialization vector respectively in a first storage unit and a second storage unit; Repeating the above steps at least one time.
Owner:KO CHENG HAN
Encrypting file system, encrypting method and deciphering method based on EXT2 file system
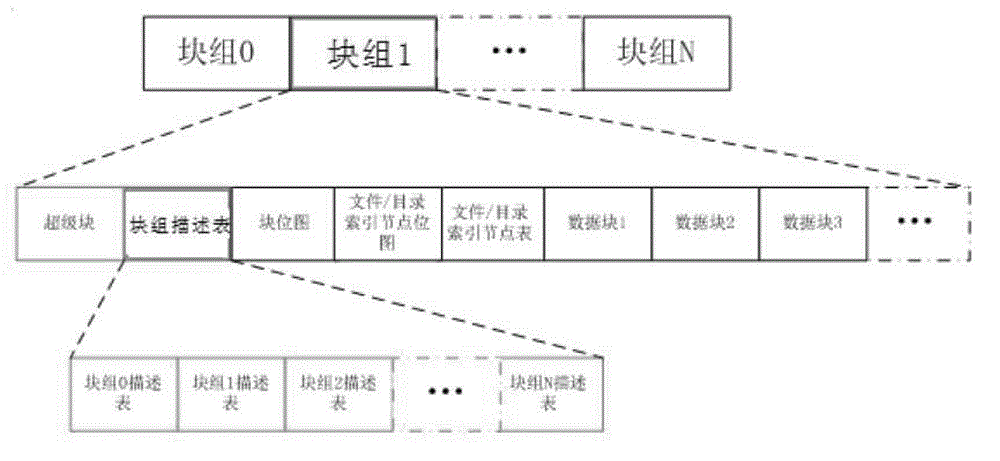
InactiveCN103067170AImprove securityEncryption apparatus with shift registers/memoriesPublic key for secure communicationBlock graphEncrypted file system
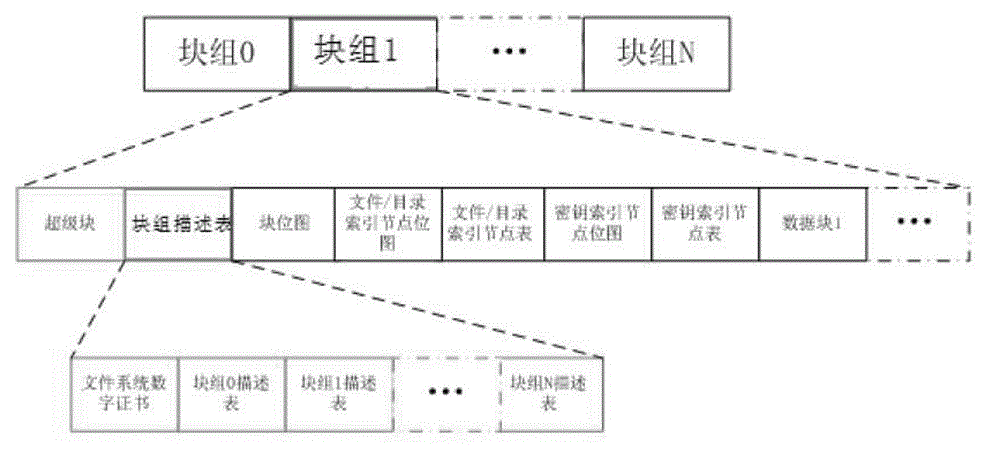
The invention discloses an encrypting file system based on an EXT2 file system. The encrypting file system based on the EXT2 file system comprises a plurality of block groups, and each block group comprises memory spaces corresponding to the data of a superblock, a block group description list, a block bitmap, a file and catalogue index node bitmap, a file and catalogue index node list and a plurality of data blocks. A plurality of block group description lists are stored in a memory space corresponding to the block group description list. Each block group further comprises a secret key index node bitmap which is arranged behind the file and catalogue index node list and a memory space corresponding to a secret key index node list. The memory space corresponding to the block group description list is further provided with a file system digital certificate (DC). By means of the encrypting file system based on the EXT2 file system, the security of the EXT2 file system is improved. The invention further provides an encrypting method and a deciphering method based on the EXT2 file system.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Document download method and system
ActiveCN103248650AImprove transmission efficiencyImprove securityMultiple keys/algorithms usageComputer security arrangementsComputer hardwareNetwork management
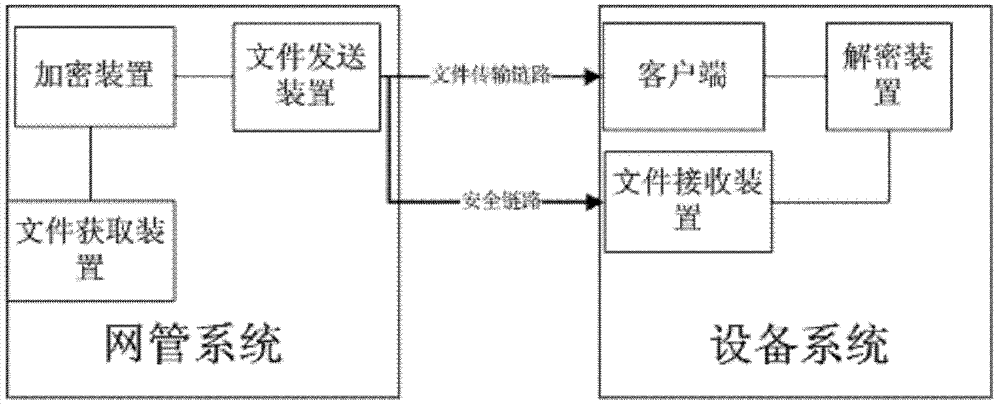
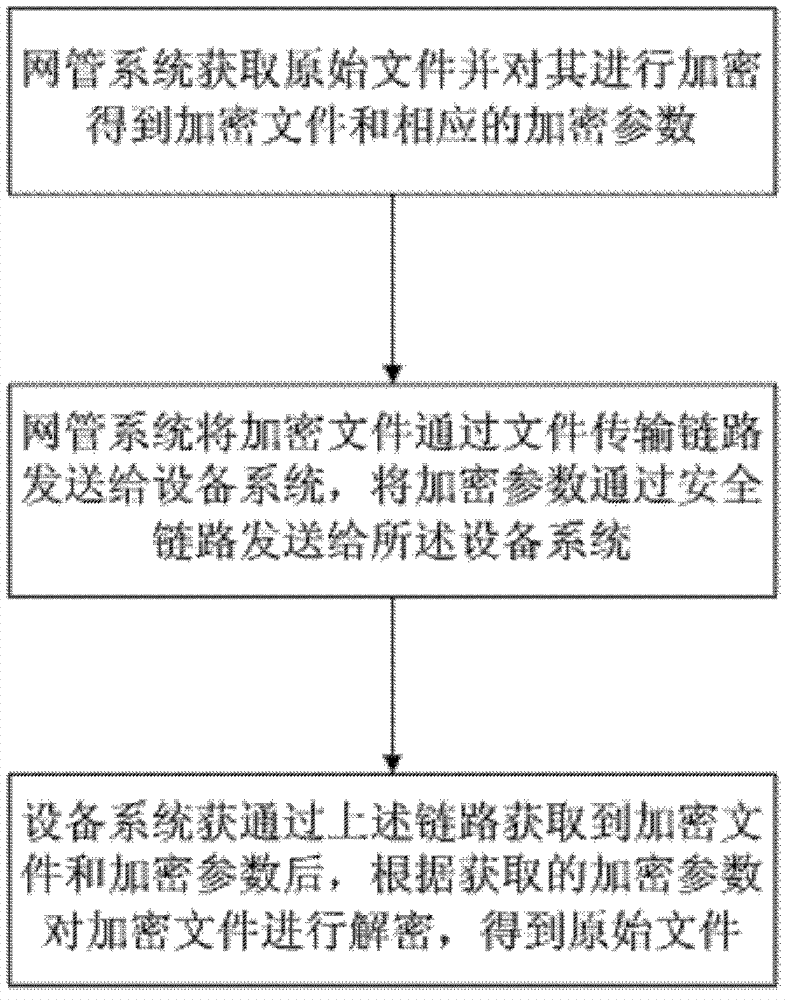
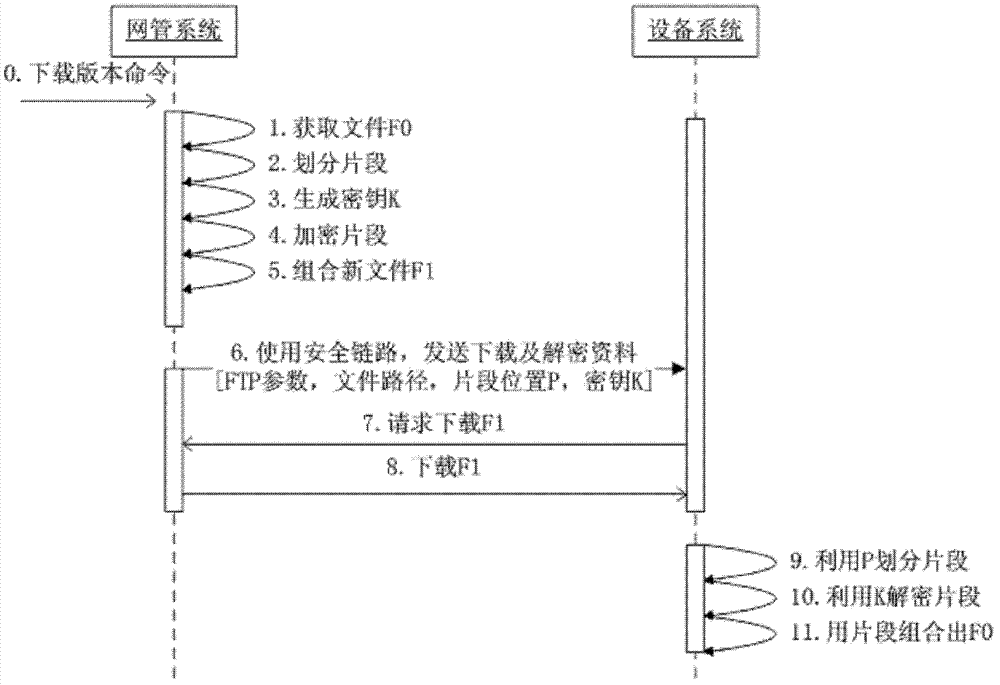
The present invention relates to the field of communications. Disclosed are a method and an apparatus for downloading a file. In the present invention, a network management system acquires an original file and encrypts the acquired original file to obtain an encrypted file and a corresponding encryption parameter; sends the obtained encrypted file to a device system through a file transfer link and sends the obtained encryption parameter to the device system through a secure link. Upon acquiring the encrypted file and the encryption parameter through the different paths, the device system decrypts the encrypted file according to the encryption parameter to obtain the original file, thereby improving the efficiency and security of file transmission.
Owner:ZTE CORP
Apparatus and method for decrypting encrypted file
InactiveUS20150134971A1Key distribution for secure communicationUnauthorized memory use protectionPlaintextPassword
Owner:ELECTRONICS & TELECOMM RES INST
File encryption system and file encryption method
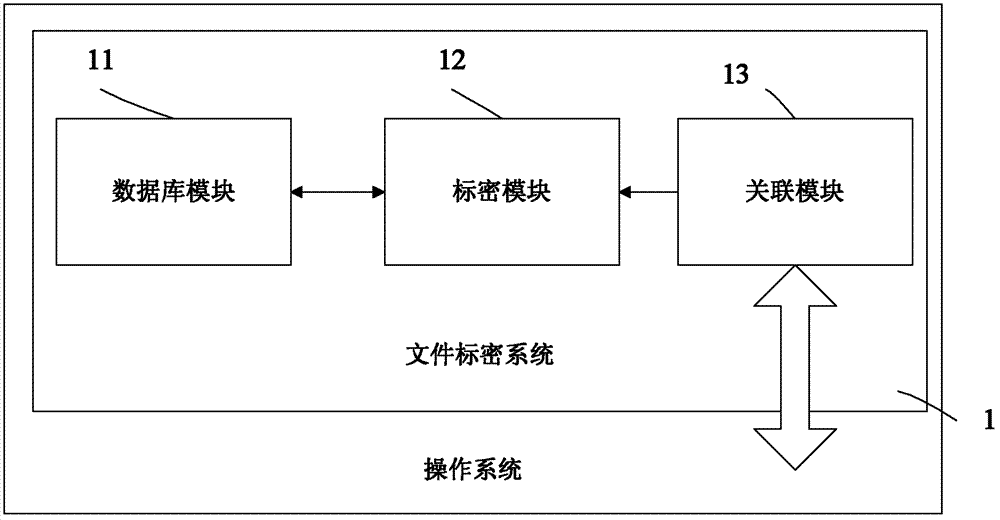
InactiveCN102902931AAvoid LeapfroggingImprove securityDigital data protectionComputer hardwareOperational system
The invention provides a file encryption system and a file encryption method. The file encryption system is carried on an operation system platform and comprises a database module, an encryption module and a related module, wherein the database module establishes a database file under each drive letter of a computer hard disk to store time of encrypting a file, a file name of the encrypted file, a file full path of the encrypted file and a file encryption grade; the related module is related to an operation system to monitor the operation to the file by a user, generates a corresponding instruction according to the operation to the file by the user and transmits the instruction to the encryption module; and the encryption module receives the instruction, operates the time of encrypting the file, the file name of the encrypted file, the file full path of the encrypted file and the file encryption grade, which are stored by the database file under the drive letter related to user operation, according to the instruction to mark the encryption grade of the file, and meanwhile, realizes the binding between encryption information and an electronic file, so that the encryption information of the electronic file is not lost in a transmission and copying process, and the safety and the controllability of the file are improved.
Owner:中国航天科工集团第二研究院七0六所
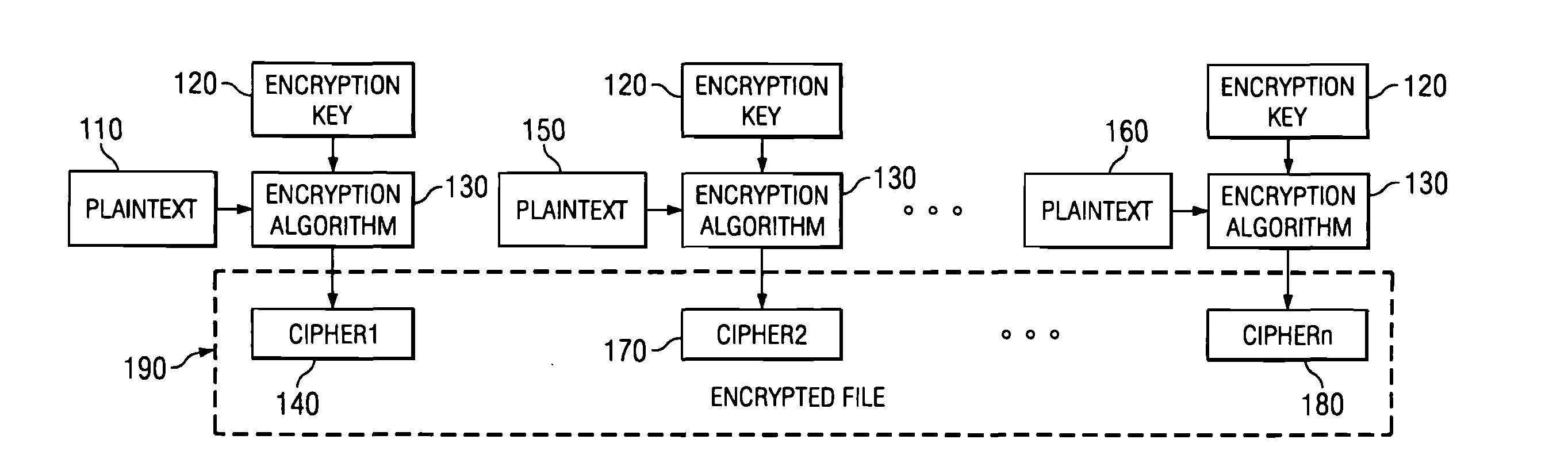
Encrypting file system
An encryption method that is largely transparent to a user is accomplished by intercepting a change document or open document command, carrying out an encryption or decryption process, and then completing the command on an encrypted or decrypted file. The encryption method can be used in a wide variety of environments, such as an individual computer program, a database or electronic messaging over the Internet. The encryption method can select from a plurality of encryption algorithms.
Owner:RPX CORP
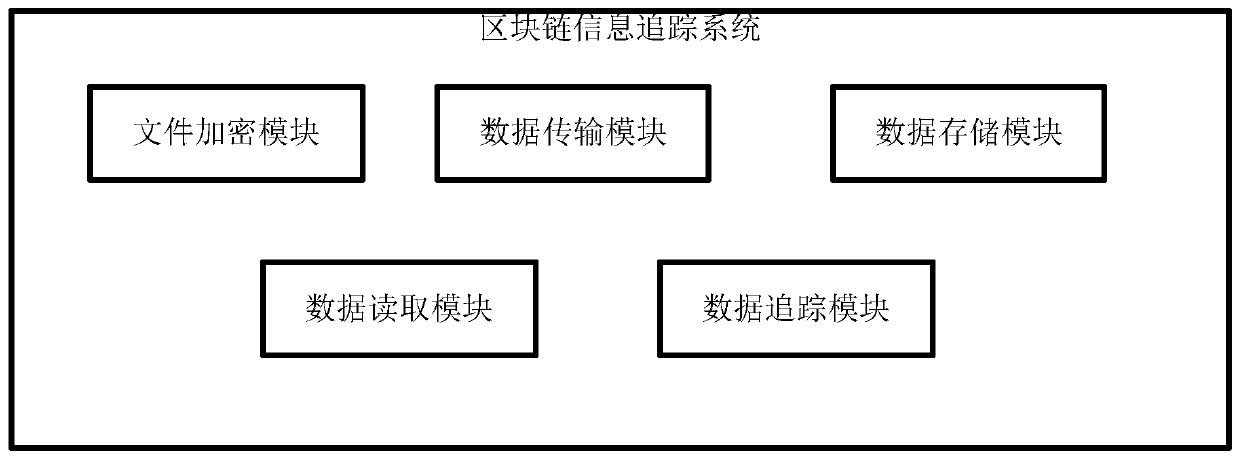
Blockchain information tracking method and system
ActiveCN109802967AEnsure safetyRealize data connectionKey distribution for secure communicationPublic key for secure communicationTimestampEncrypted file system
The invention provides a blockchain information tracking method and system, and the method comprises the steps: employing an asymmetric encryption algorithm to generate a key pair, employing the key pair to encrypt an account, employing an electronic signature to carry out the signature processing of a file, and obtaining a first encrypted file; A P2P network is adopted for data transmission, a connection channel is established between a first node and a newly-added node through searching of a server, the newly-added node is made to conduct whole-network broadcasting through a flooding mechanism, and a public key of a key pair is published to the P2P network; Wherein the first encrypted file is stored in a stand-alone designated storage area, and the networking verifies the transmission request through a private key of a key pair; Enabling the first encrypted file to generate a timestamp and then encrypt the timestamp to obtain a second encrypted file, enabling the second encrypted file to generate a public chain, and enabling the public chain to comprise file process information; Verifying the data reading request through the private key of the key pair, reading the public chain after the data reading request passes the verification, and checking the downloaded file. Distributed storage of public key information records at a server side is realized, and the data security performance is ensured.
Owner:VISION MICROSYST SHANGHAI
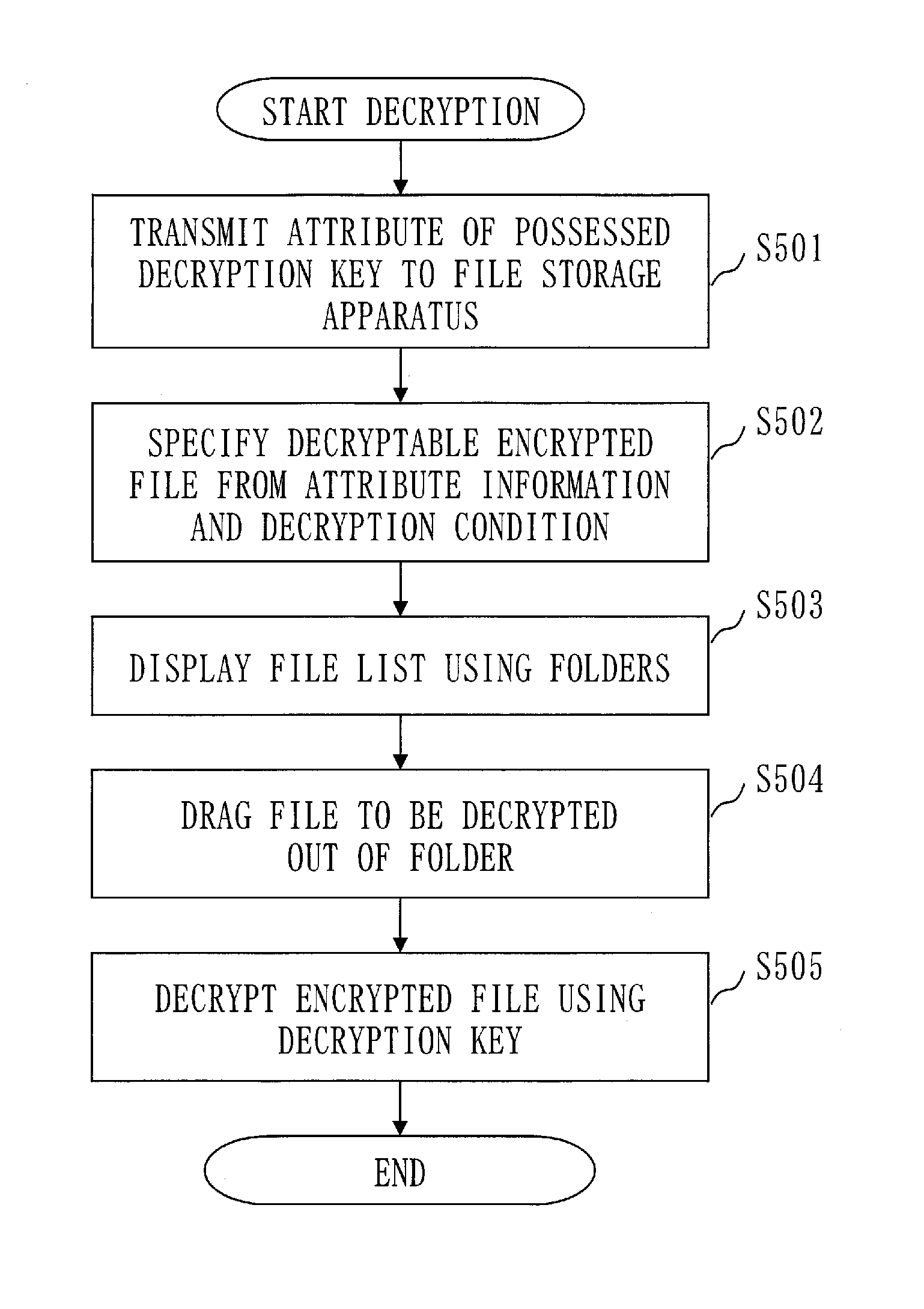
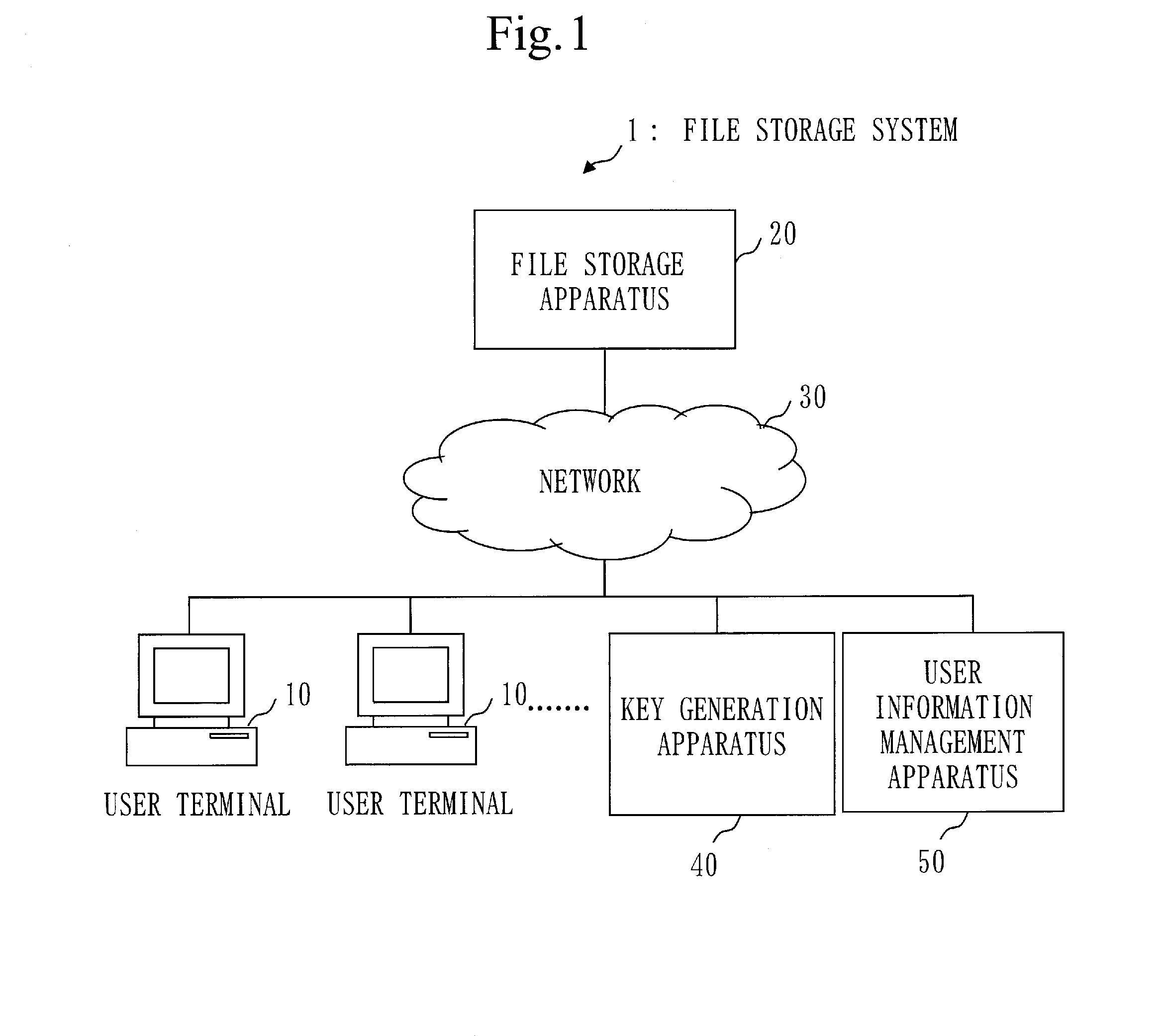
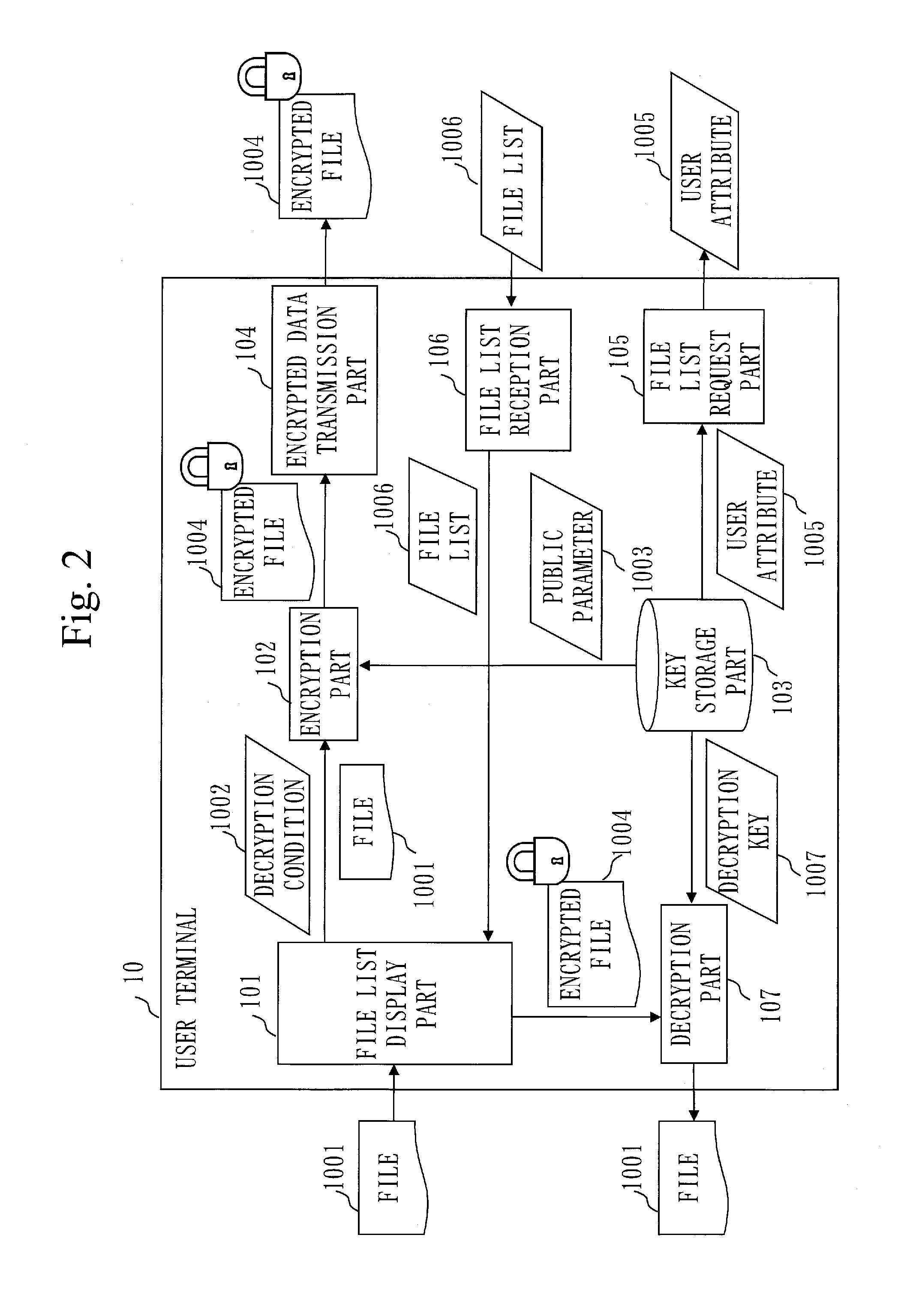
File storage system and user terminal
InactiveUS20160253517A1Reduce in quantityNo damageMultiple keys/algorithms usageDigital data protectionComputer terminalEncrypted file system
A data storage system (1) uses an encryption scheme in which an encrypted file can be decrypted using a decryption key when a decryption condition set in the encrypted file is satisfied by a user attribute set in the decryption key. The data storage system (1) stores encrypted files encrypted by the encryption scheme in a file storage apparatus (20). When user attribute is specified from a user terminal (10), the data storage system (1) extracts the encrypted file of which the decryption condition is satisfied by the specified user attribute from among the encrypted files stored in the file storage apparatus (20), and displays the extracted encrypted files classified by decryption condition.
Owner:MITSUBISHI ELECTRIC CORP
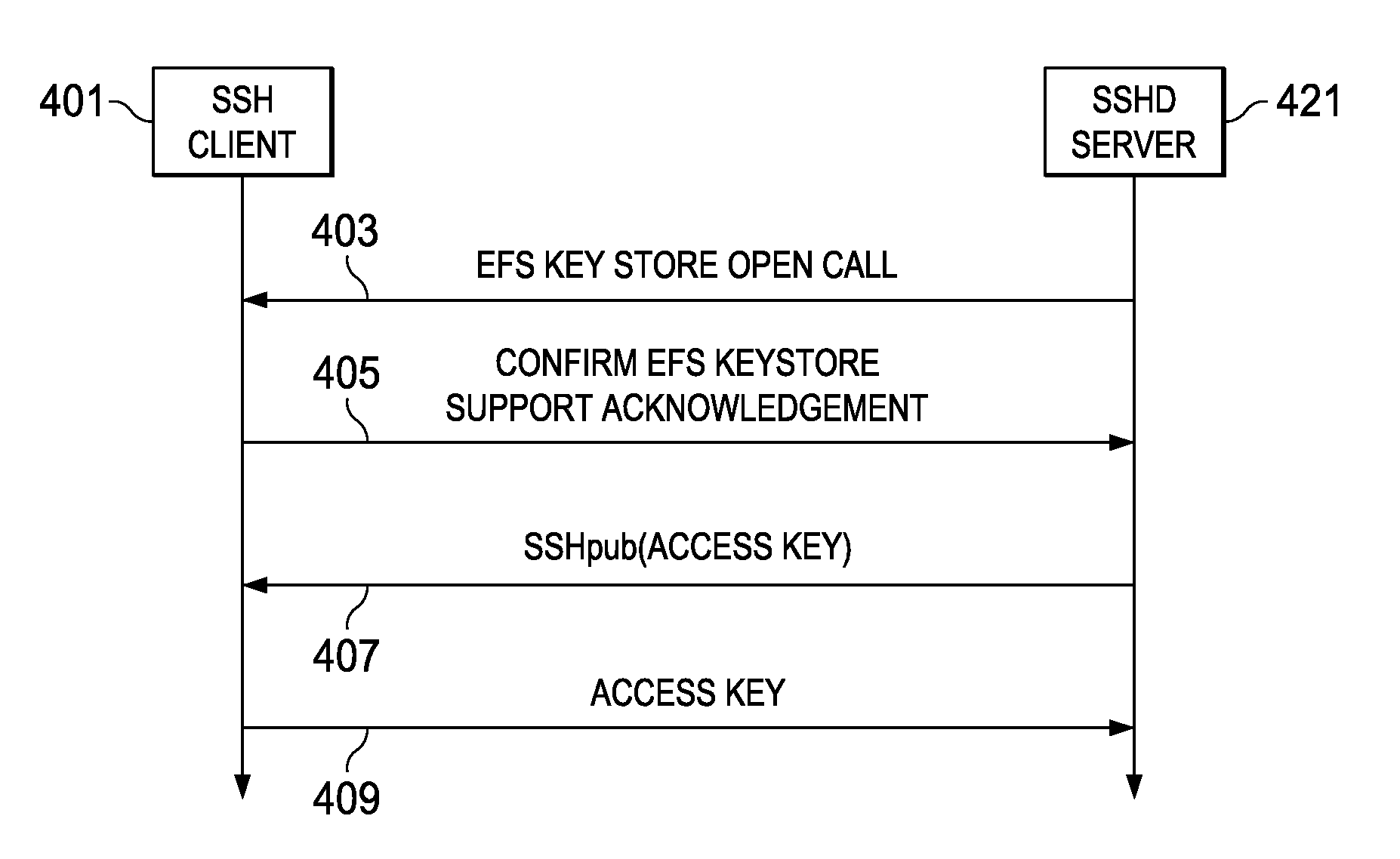
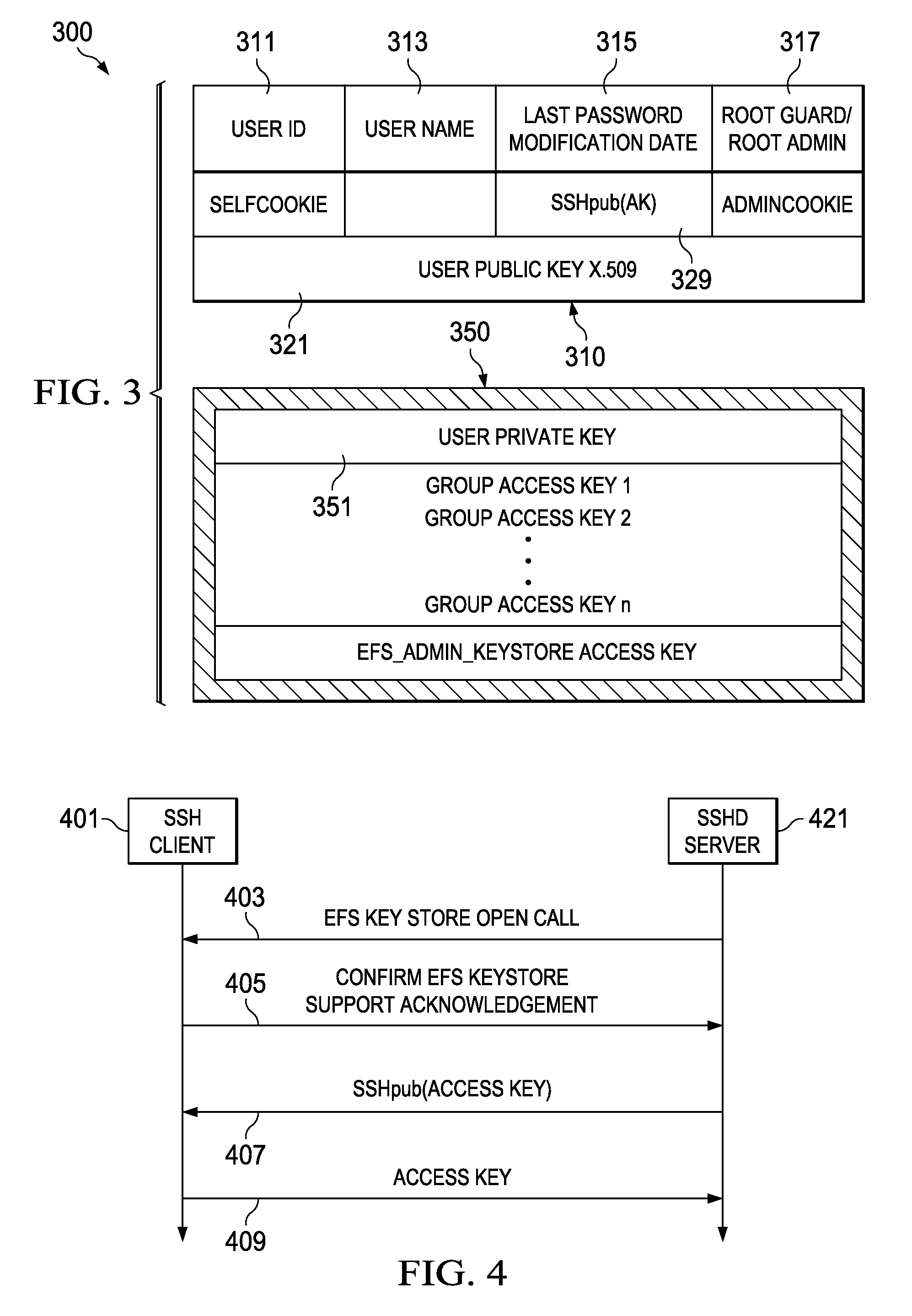
Secure shell used to open a user's encrypted file system keystore
InactiveUS8391495B2Key distribution for secure communicationDigital data processing detailsData processing systemUser authentication
The present invention provides a computer implemented method, apparatus, and data processing system for associating a private part of a keystore of a user with a user authentication process in an encrypting file system. A secure shell daemon server establishes the user authentication process with a secure shell client such that the user authentication process is associated with a user and the user is authenticated. The secure shell daemon server obtains an acknowledgment from the secure shell client. The secure shell daemon server accesses a user public key of the user from the keystore of the user, responsive to receiving the acknowledgment. The secure shell daemon obtains a public secure shell cookie associated with the user from the keystore of the user. The public secure shell cookie is an access key in encrypted form. The access key is based on the user's public key to form the public secure shell cookie. The secure shell daemon server obtains the access key from the secure shell client. The private part of the keystore is associated with the user authentication process, wherein the private part is accessed based on the access key.
Owner:INT BUSINESS MASCH CORP
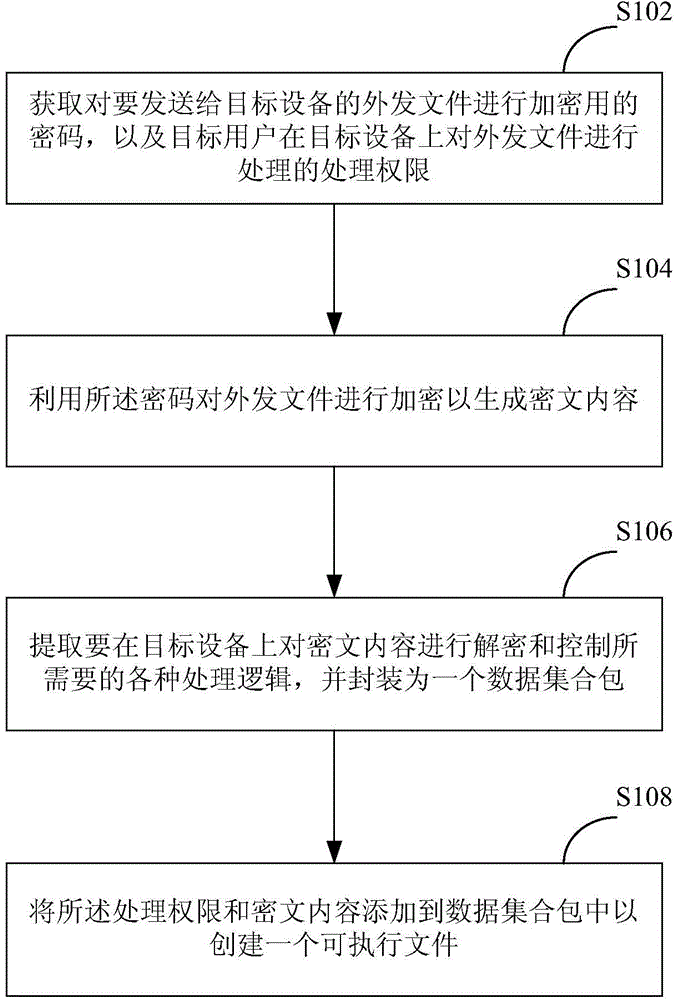
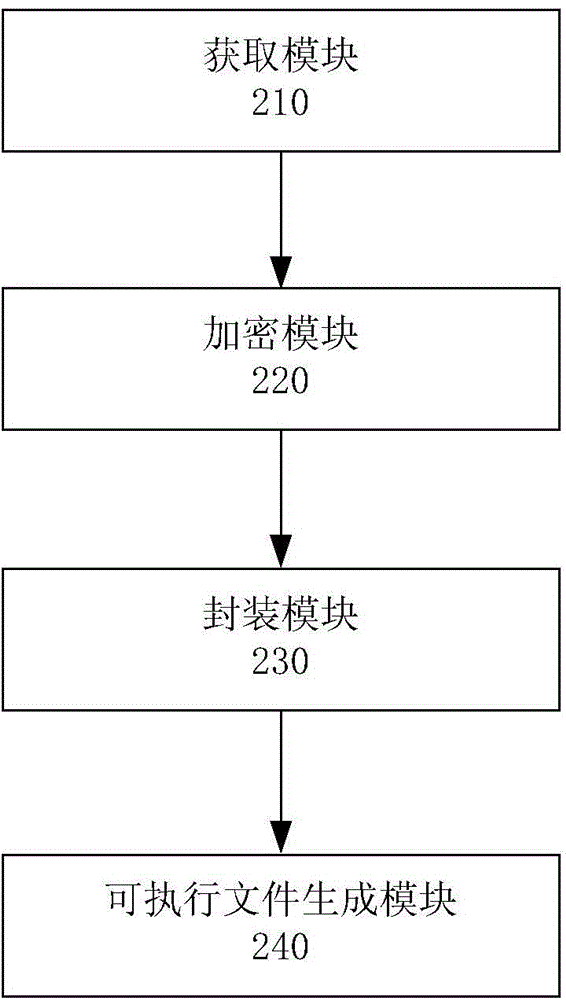
Generation method and device of encrypted file and computing equipment
The invention discloses a generation method of an encrypted file. The method is executed in the computing equipment, and comprises the following steps: acquiring a password for encrypting an outgoing file to be transmitted to target equipment and processing authority for processing the outgoing file on the target equipment by a target user; encrypting the outgoing file by using the password to generate a cipher text content; extracting various processing logics required for decrypting and controlling the cipher text content on the target equipment and packaging into a data set packet; adding the processing authority and the cipher text content into the data set packet to establish an executable file. The invention also discloses a generation device of the encrypted file and the computing equipment comprising the device.
Owner:深圳市大成天下信息技术有限公司
NandFlash encryption file system of adopting random salt value
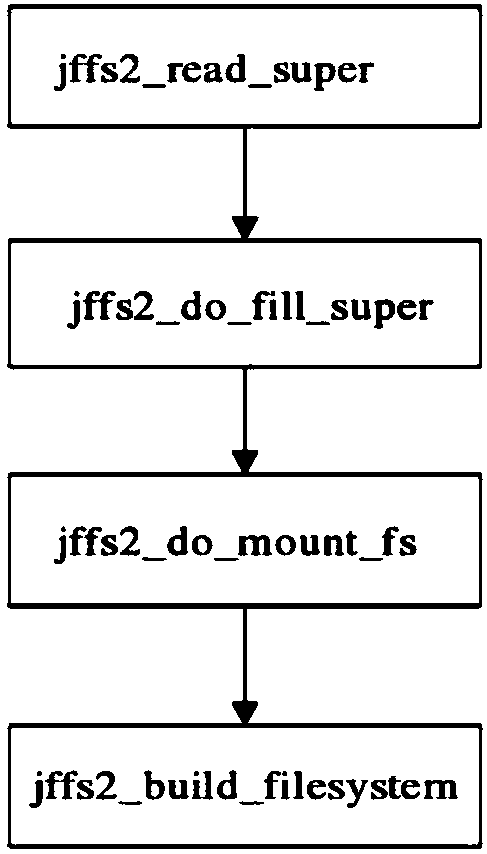
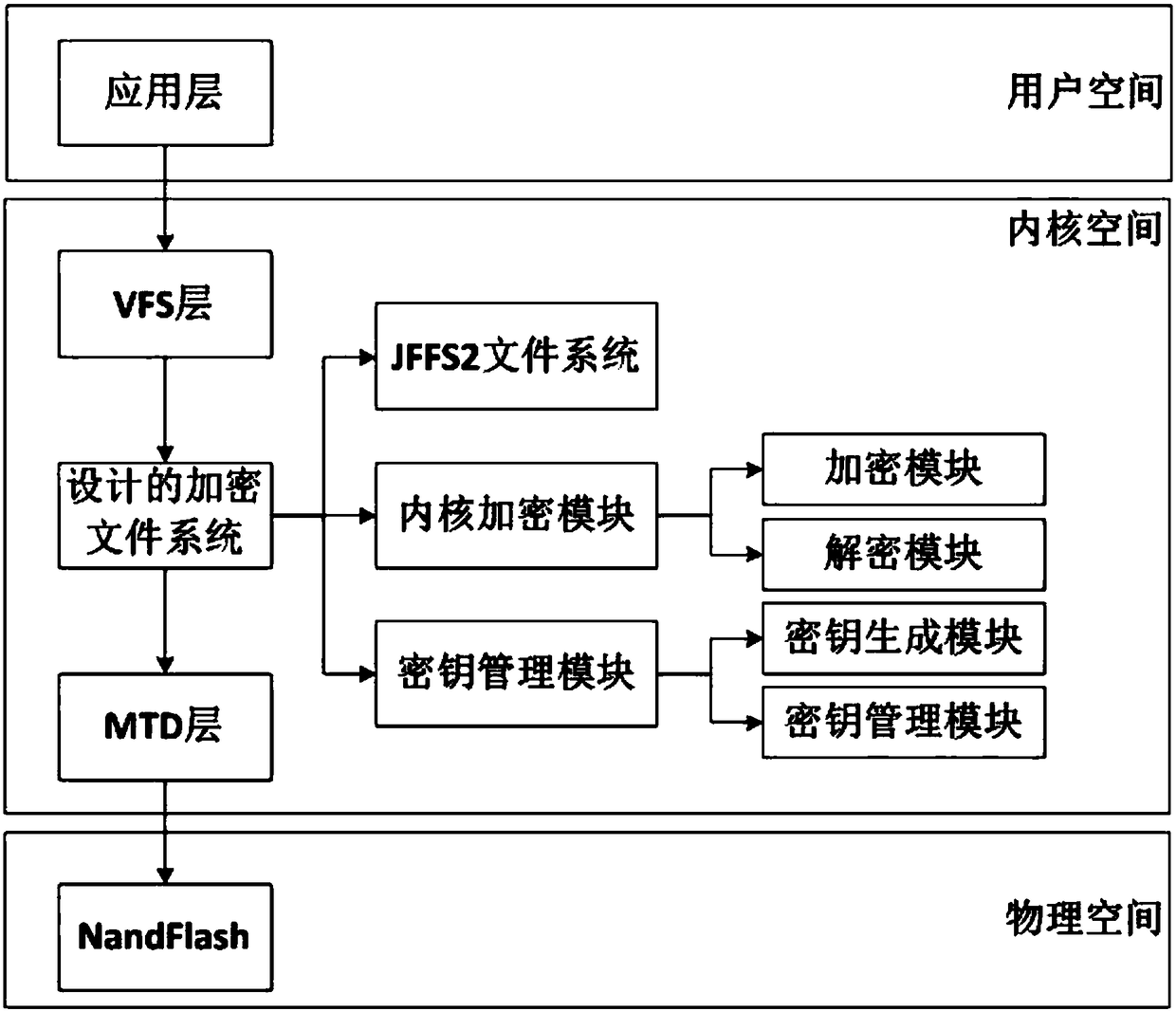
InactiveCN108197478AAvoid safety hazardsImprove securityRandom number generatorsDigital data protection128-bitJFFS2
The invention provides a NandFlash encryption file system of adopting a random salt value. For the physical characteristics of NandFlash different from ordinary disk storage equipment, a JFFS2 file system is migrated into the NandFlash and used as a bottom-layer storage system thereof, the problems of inadaptability of directly applying the NandFlash to embedded equipment are solved, a national-password SM4 algorithm and SM3 algorithm are adopted on file encryption algorithms, then combination of a user password and the random salt value is adopted to generate a 128-bit user key in a process of generating the user key, the security hidden-troubles of directly storing user passwords and results after hash processing by original algorithms are avoided, and security of giving the user key bythe system is further improved.
Owner:HONGQIN (BEIJING) TECHNOLOGY CO LTD
Folder encryption method and device for Unix-like operating system
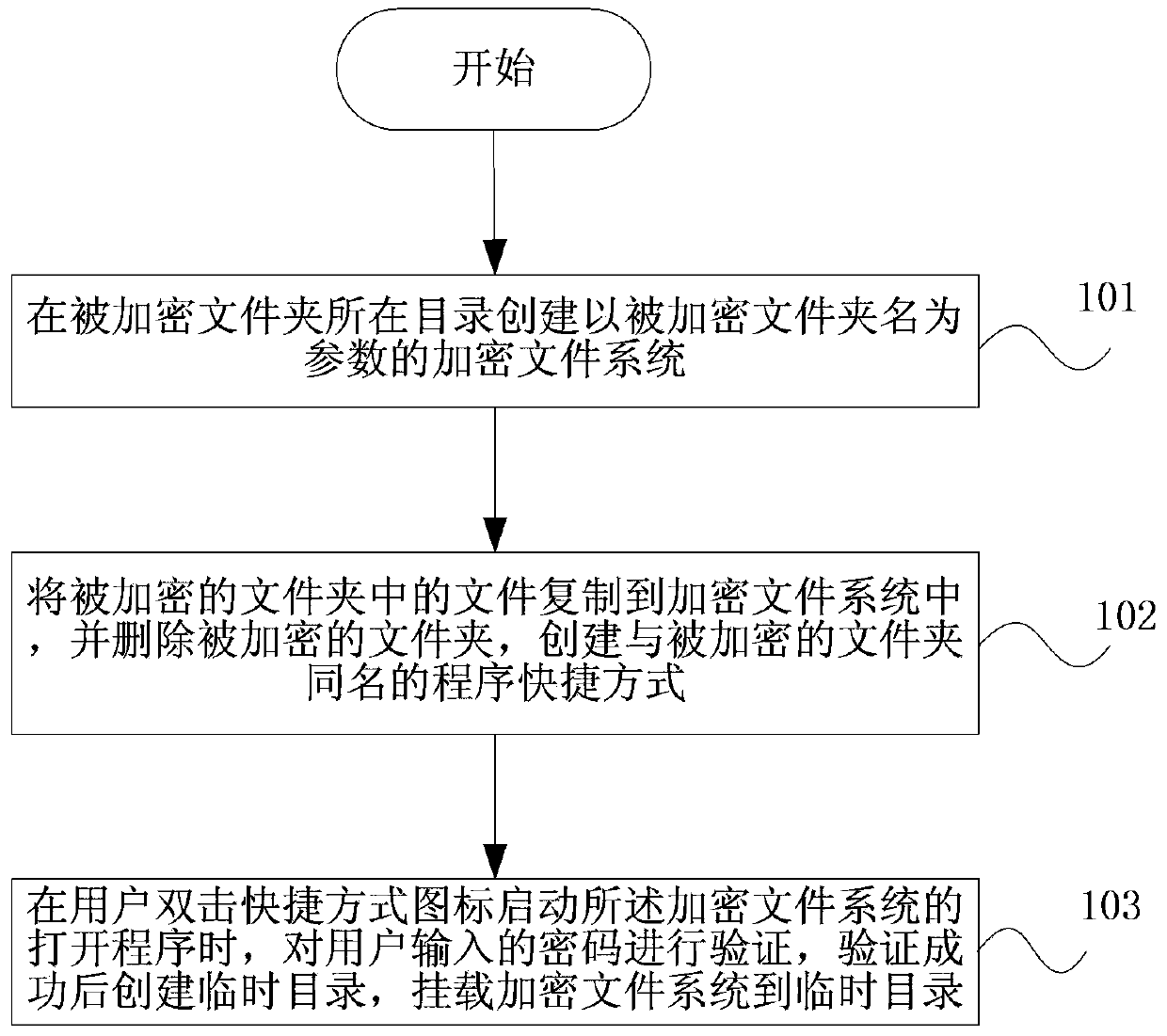
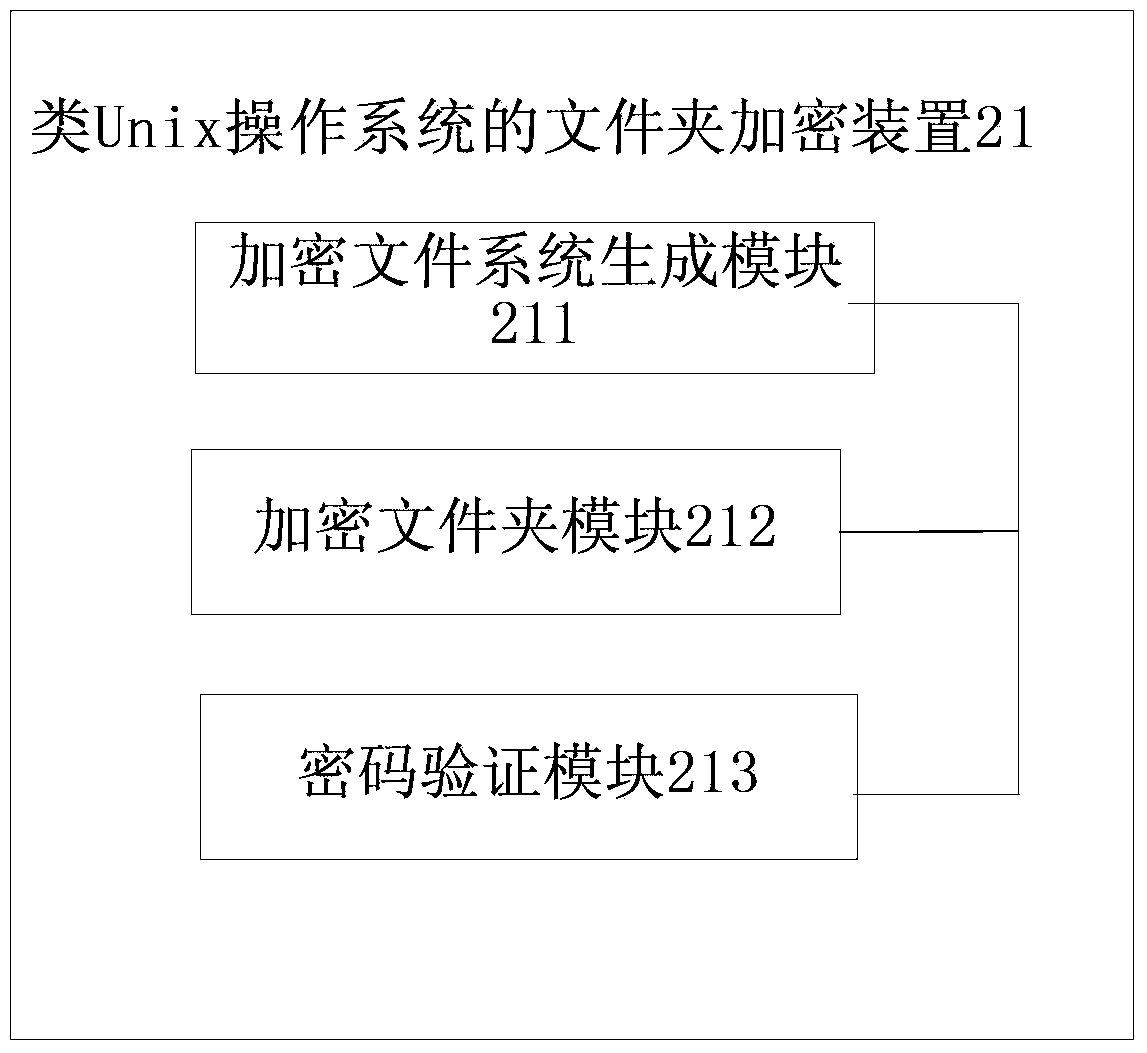
InactiveCN103425938AIntuitive EncryptionWork intuitivelyDigital data protectionOperational systemPassword
The invention discloses a folder encryption method and device for a Unix-like operating system. An encrypted file system is created in a catalog where an encrypted folder is located, wherein the name of the encrypted folder is used as a parameter of the encrypted file system; files in the encrypted folder are copied to the encrypted file system, the encrypted folder is deleted, and a routine shortcut with the same name as the encrypted folder is created; when a user double clicks a shortcut icon to enable a start routine of the encrypted file system, a password input by the user is verified, a temporary catalogue is created after the verification succeeds, and the encrypted file system is mounted to the temporary catalogue. The folder encryption method and device for the Unix-like operating system can encrypt folders and achieve the effect that encrypted files can be in a protection state under both a dynamic condition and a static condition by loading and unloading the encrypted file system.
Owner:亚太宝龙科技(湖南)有限公司
Multiple encrypting method and system for encrypting a file and/or a protocol
InactiveUS20180205541A1Key distribution for secure communicationMultiple keys/algorithms usageMultiple encryptionInitialization vector
The present invention relates to a multiple encrypting method, for encrypting a file and / or a protocol and generating encryption keys. Comprising the steps of: uploading at least one of a file and a protocol by a file uploading unit; generating random numbers by a random number generation unit; arranging the random numbers to form at least one key and at least one initialization vector respectively by a key generation unit and an initialization vector generation unit; encrypting the file and / or the protocol from the file uploading unit via using AES encryption by an encryption unit, so as to generate an encrypted file and / or an encrypted protocol; saving the key and the initialization vector respectively in a first storage unit and a second storage unit; Repeating the above steps at least one time.
Owner:KO CHENG HAN
File transparent encryption and decryption method and system based on domestic operating system
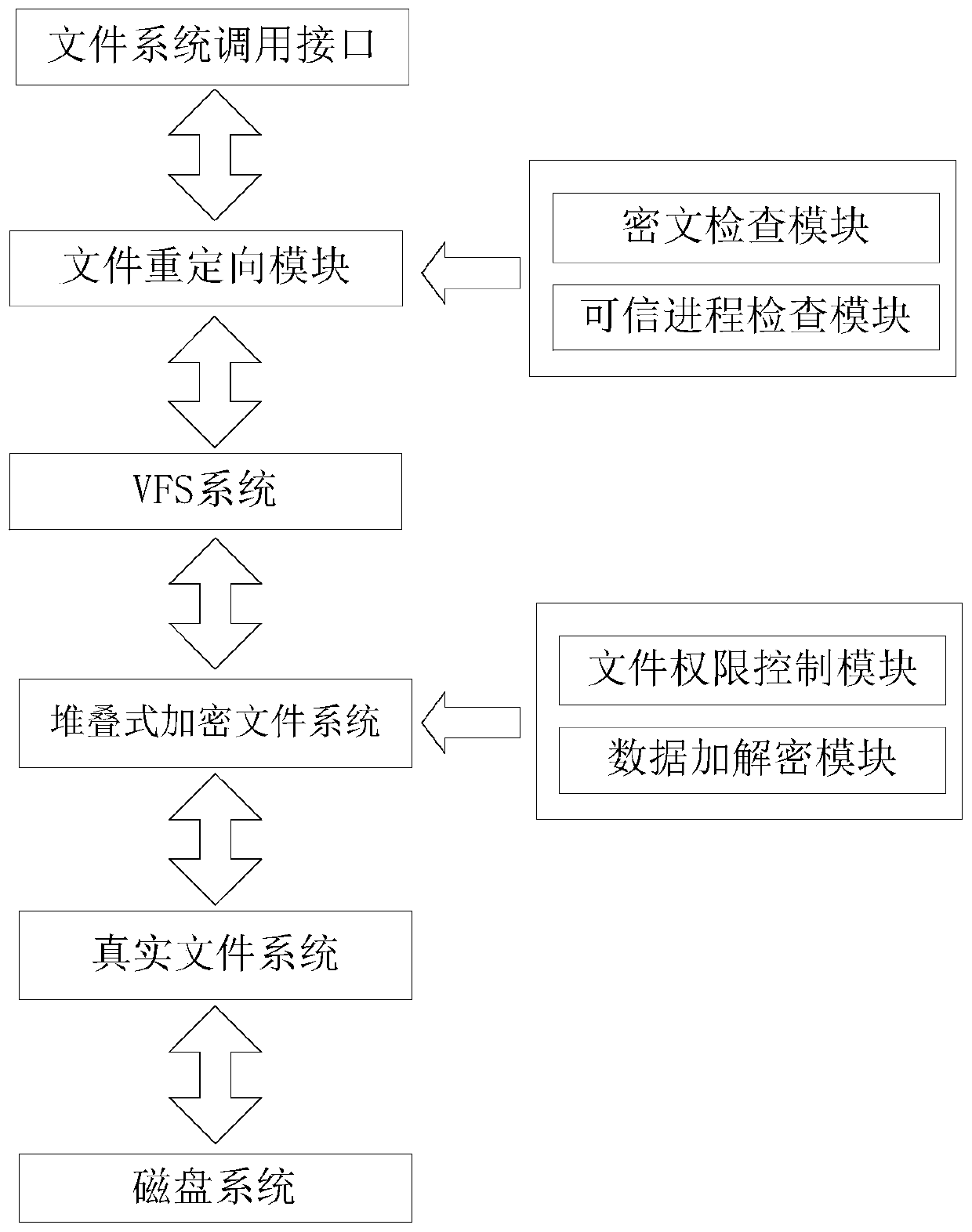
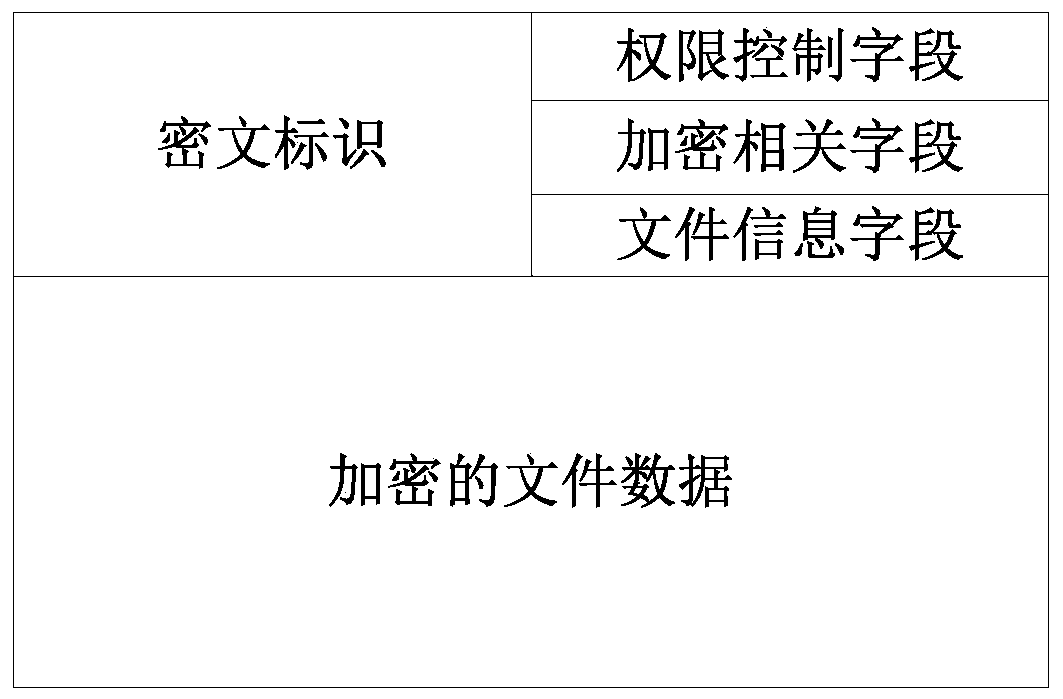
The invention provides a file transparent encryption and decryption method and system based on a domestic operating system. The system comprises a file system calling interface, a file redirection module, a VFS system, a stacked encryption file system, a real file system and a disk system. The file redirection module is used for redirecting files; wherein the stacked encrypted file system is deployed in a domestic operating system kernel layer to intercept and check an access request of a file, and the stacked encrypted file system is formed by inserting a layer of file system driver between aVFS system and a real file system and is used for calling a real file system interface to realize the access request of the file; and the stacked encrypted file system calls the file permission control module to control the file access permission. According to the scheme provided by the invention, the ciphertext is prevented from being divulged under an unauthorized condition, and the operation safety can be ensured.
Owner:北京明朝万达科技股份有限公司
Decryption method used for image data secure transmission
ActiveCN105049176AFast encryptionImprove encryption efficiencySteroscopic systemsSecuring communicationCiphertextSecure transmission
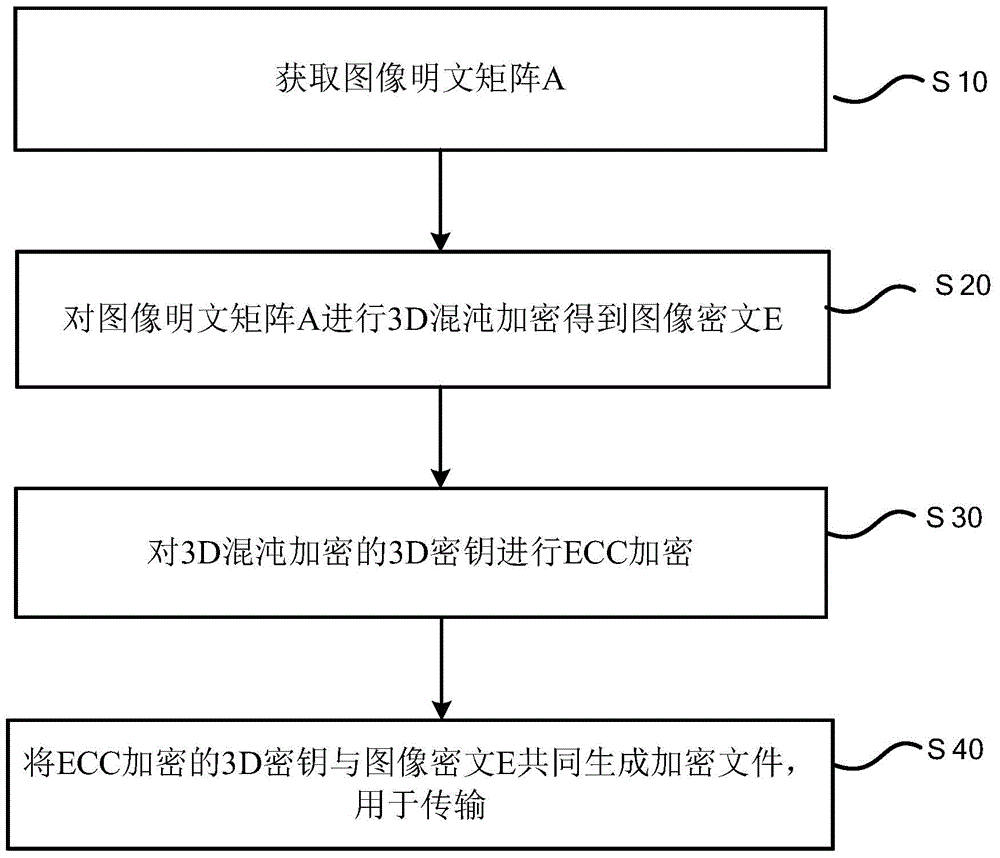
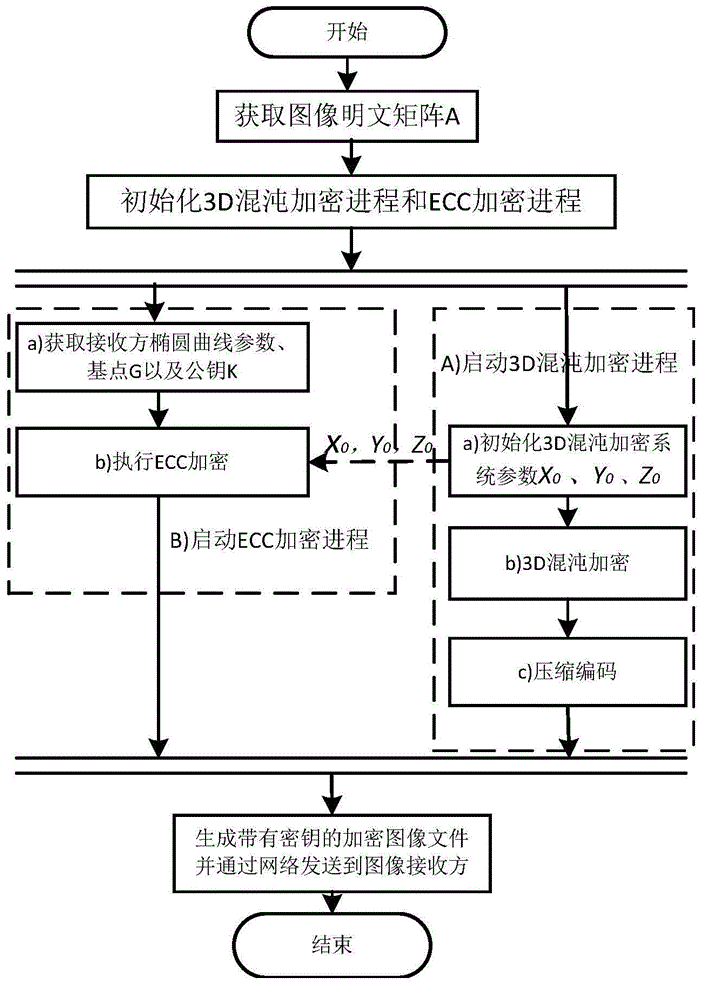
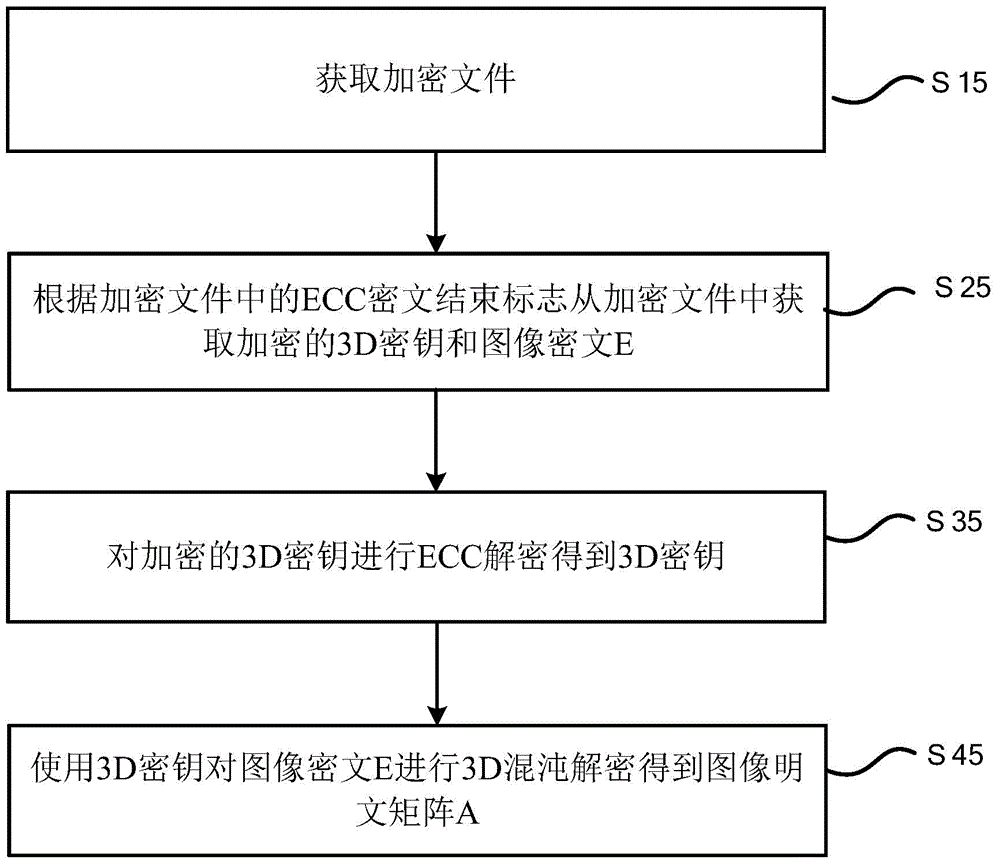
The application relates to a decryption method used for image data secure transmission, comprising the following steps: acquiring an encrypted file; acquiring an encrypted 3D secret key and an image cipher text E from the encrypted file according to an ECC (Elliptic Curves Cryptography)cipher text end mark in the encrypted file; performing ECC decryption for the encrypted 3D secret key to obtain a 3D secret key; and performing 3D chaotic decryption for the image cipher text E by using the 3D secret key to obtain an image clear text matrix A. The technical solution of the decryption method of the application combines the advantages of chaotic encryption and ECC encryption, and effectively improves encryption speed, encryption efficiency and security of a traditional image encryption method.
Owner:XIANGTAN UNIV
Dynamically retrievable cloud computing data encryption method
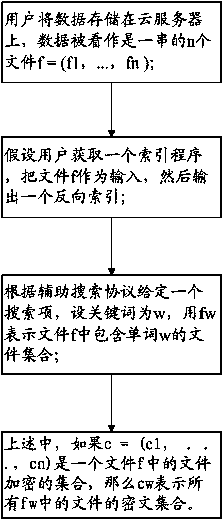
The invention discloses a dynamically retrievable cloud computing data encryption method. The method comprises the following steps: storing data on a cloud server by a user, wherein the data are considered as a string of n files, and f is equal to (f1, ellipsis, fn); supposing that the user acquires an index program, taking the file f as input and outputting a reverse index; giving a search item according to an auxiliary search protocol, setting a keyword as w, and representing a file set containing the word w in the file f by using fw, wherein if c which is equal to (c1, ellipsis, cn) is a set of encrypted files in the file f, cw represents a cipher text set of all the files in fw. By such a mode, the retrieval of encrypted data is realized, so that the privacy, the integrality and the verifiability can be guaranteed, the user can efficiently retrieve data through a search interface, and the data can also be safely added and deleted.
Owner:SUZHOU UNIV
Method for file security of NAND Flash, as well as device and system thereof
InactiveCN101694662AImprove securitySpecial data processing applicationsFlash file systemEncrypted file system
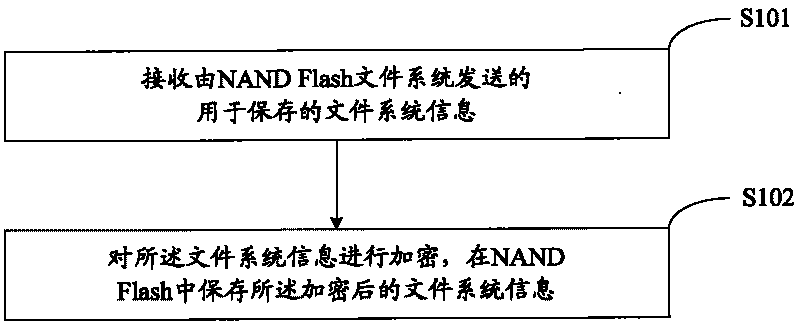
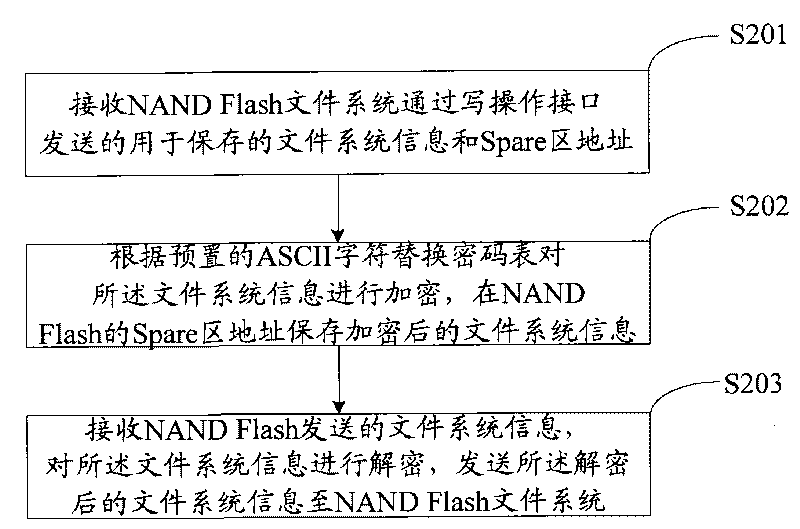
The embodiment of the invention provides a method for file security of NAND Flash, as well as a device and a system thereof. The embodiment of the method for file security of NAND Flash comprises: receiving file system information which is sent by an NAND Flash file system and is used for storing; encrypting the file system information; and storing the encrypted file system information in the NAND Flash. The embodiment of the invention improves the safety of the NAND Flash file system used for an embedded system.
Owner:SHANGHAI HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com