Off-line available software license centralized security authentication system based on cloud computation, and method of the same
A centralized authentication and security authentication technology, applied in the field of software license centralized security authentication system, can solve the problems of high network environment requirements, inability to detect authentication services, and forged authentication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
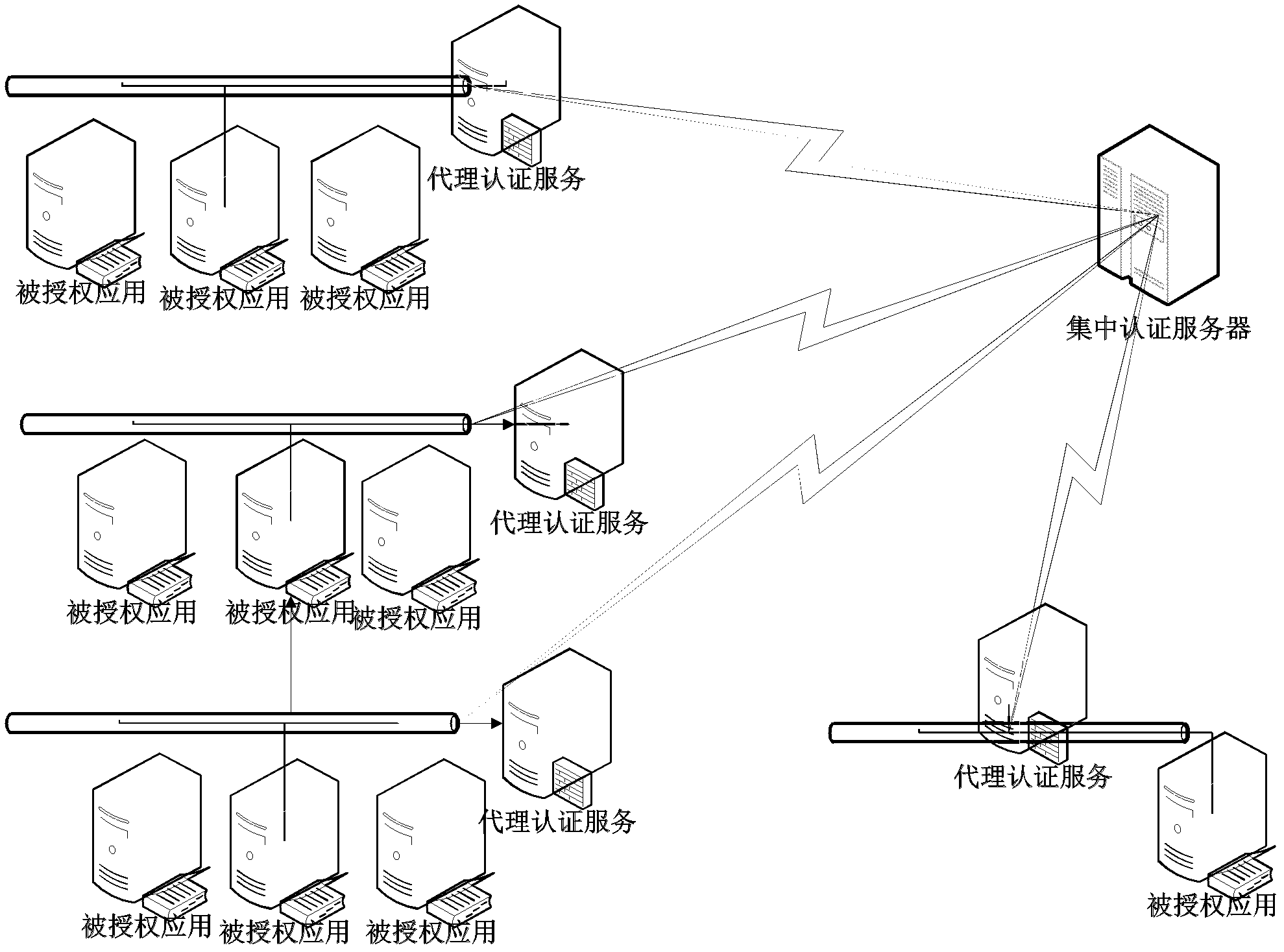
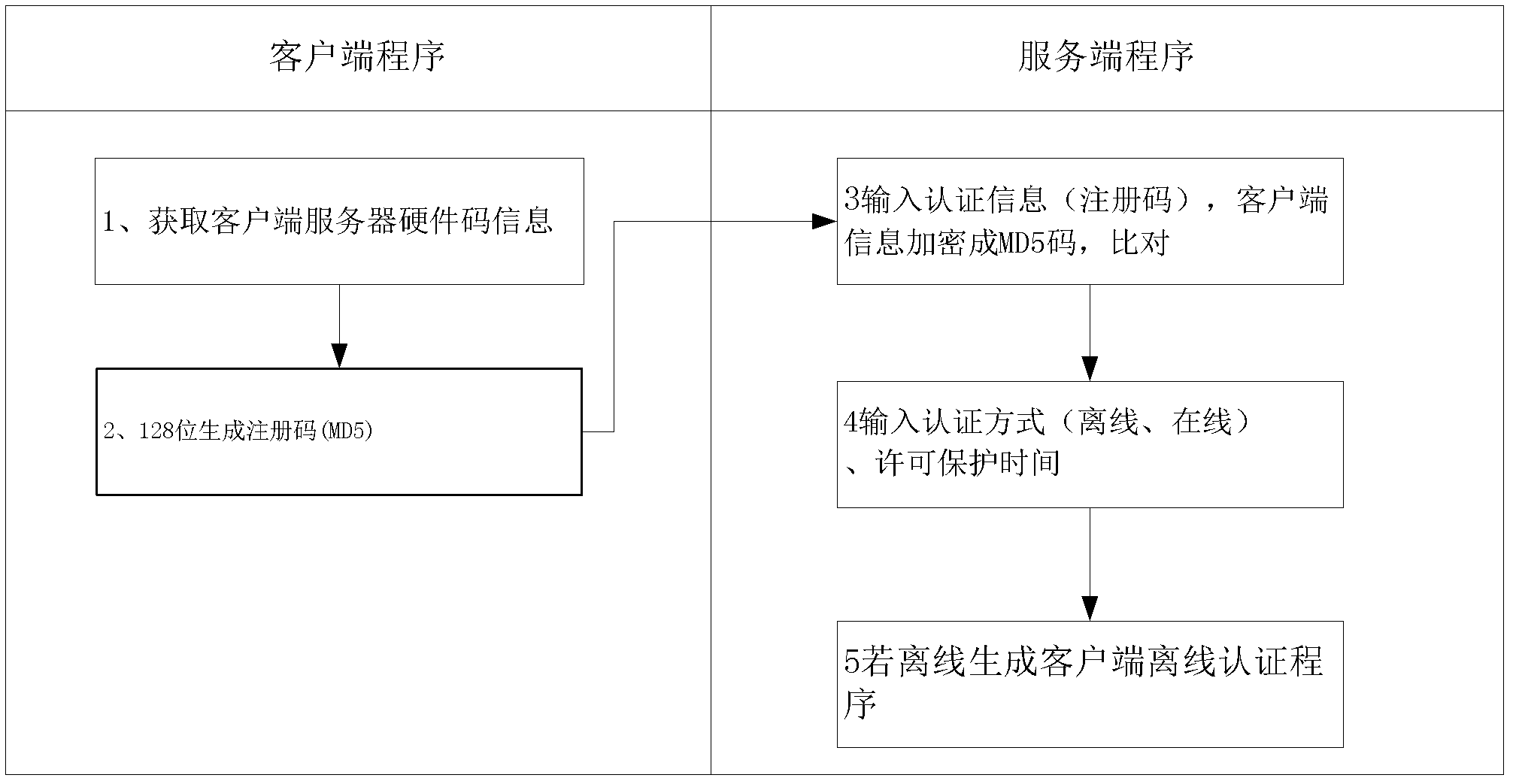
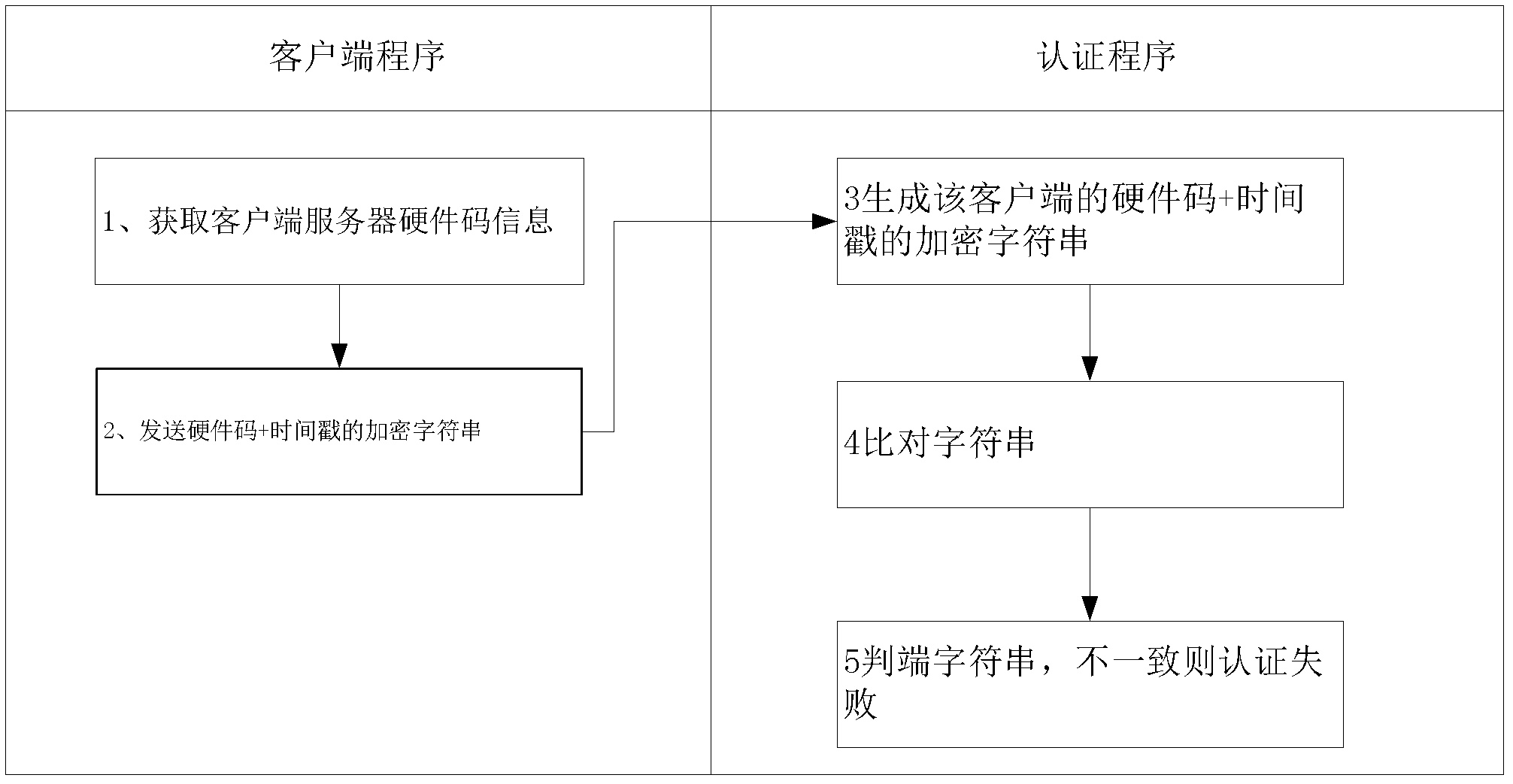
[0035] Such as figure 1 Shown is a network architecture diagram of a centralized security authentication system for software licenses that can be offline based on cloud computing, including an interconnected network composed of centralized authentication servers, proxy authentication servers, and clients. The centralized authentication server is responsible for producing authorization certificates and authenticating to agents The server or the client issues the authorization certificate; the proxy authentication server is responsible for accepting the authorized proxy authentication of the centralized authentication server and performing the offline authorization service of the client on behalf of the centralized authentication server; when the client is offline, it sends heartbeat detection information to the proxy authentication server The proxy authorization service program performs proxy authentication; or the client confirms the validity of the authorization certificate th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com