Patents
Literature
451 results about "Private line" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
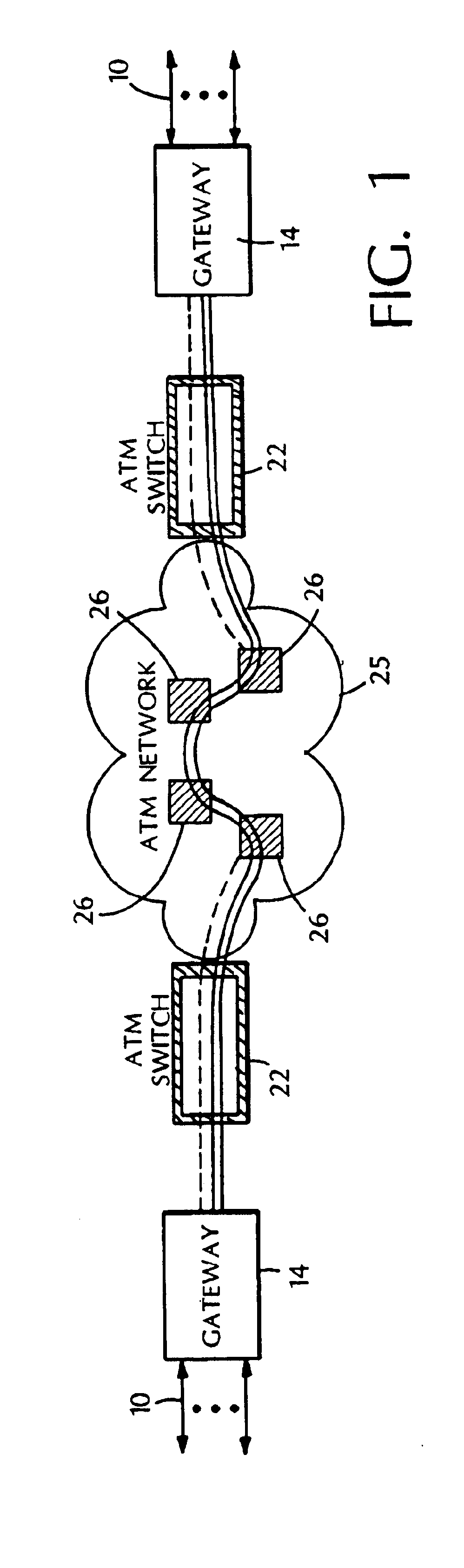
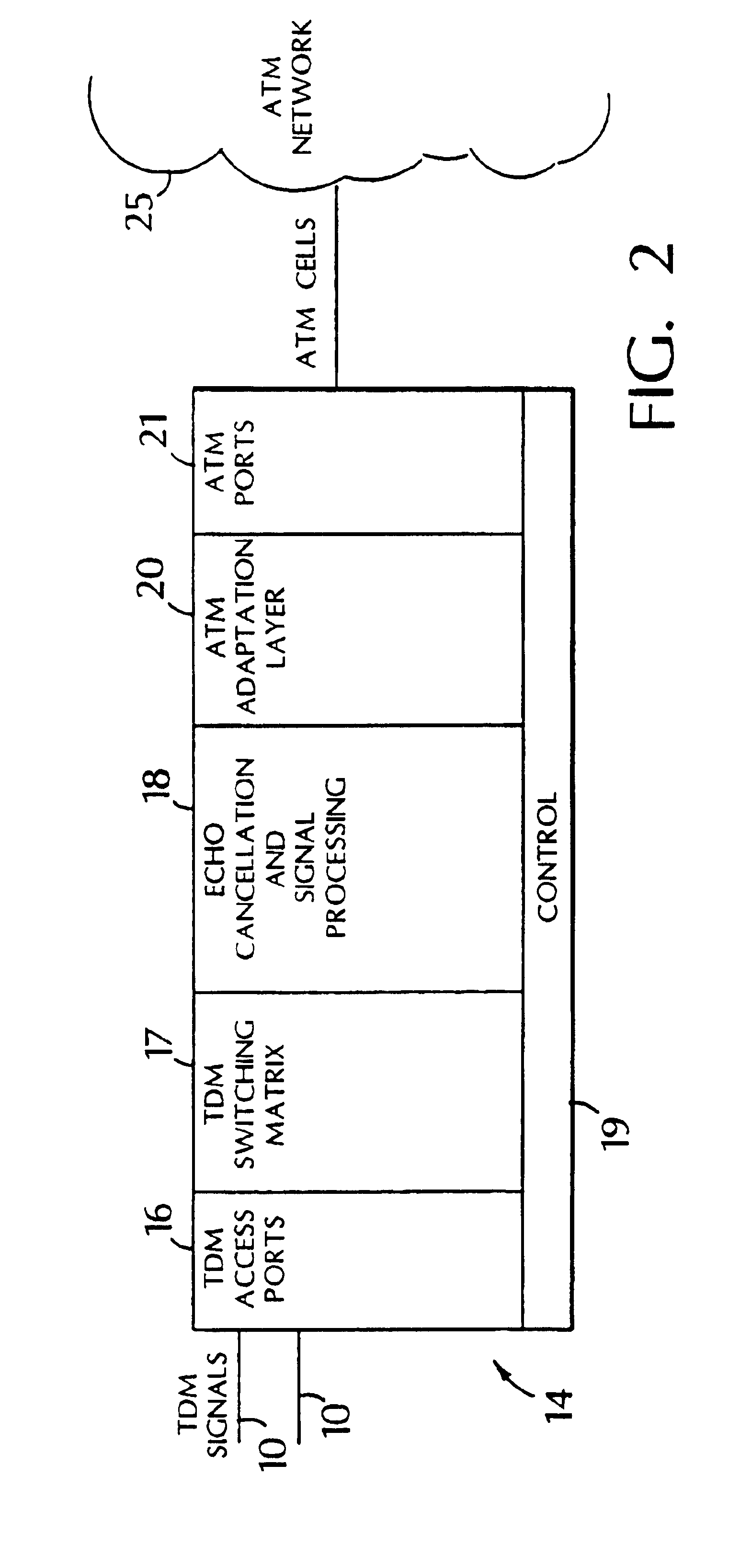
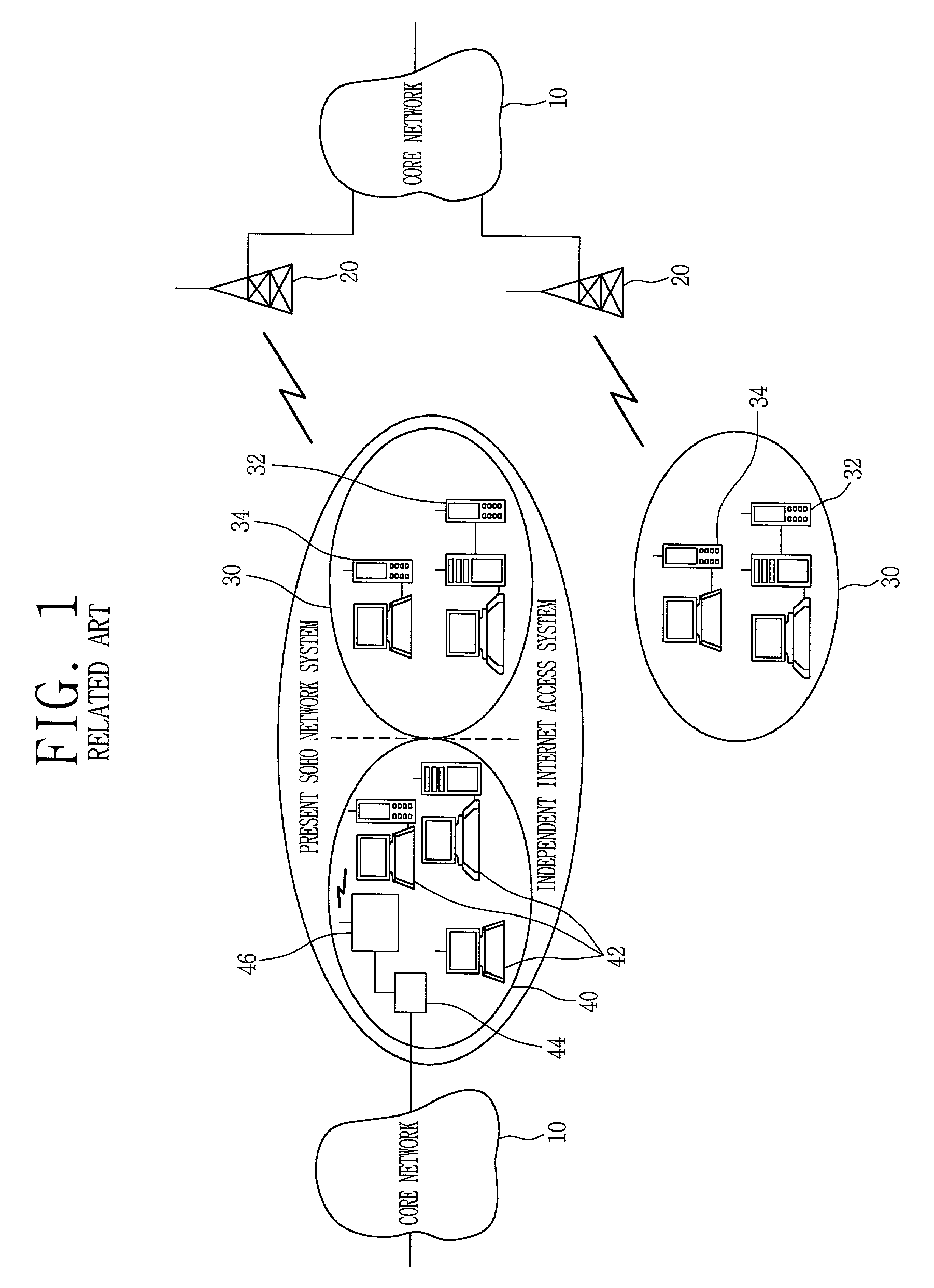
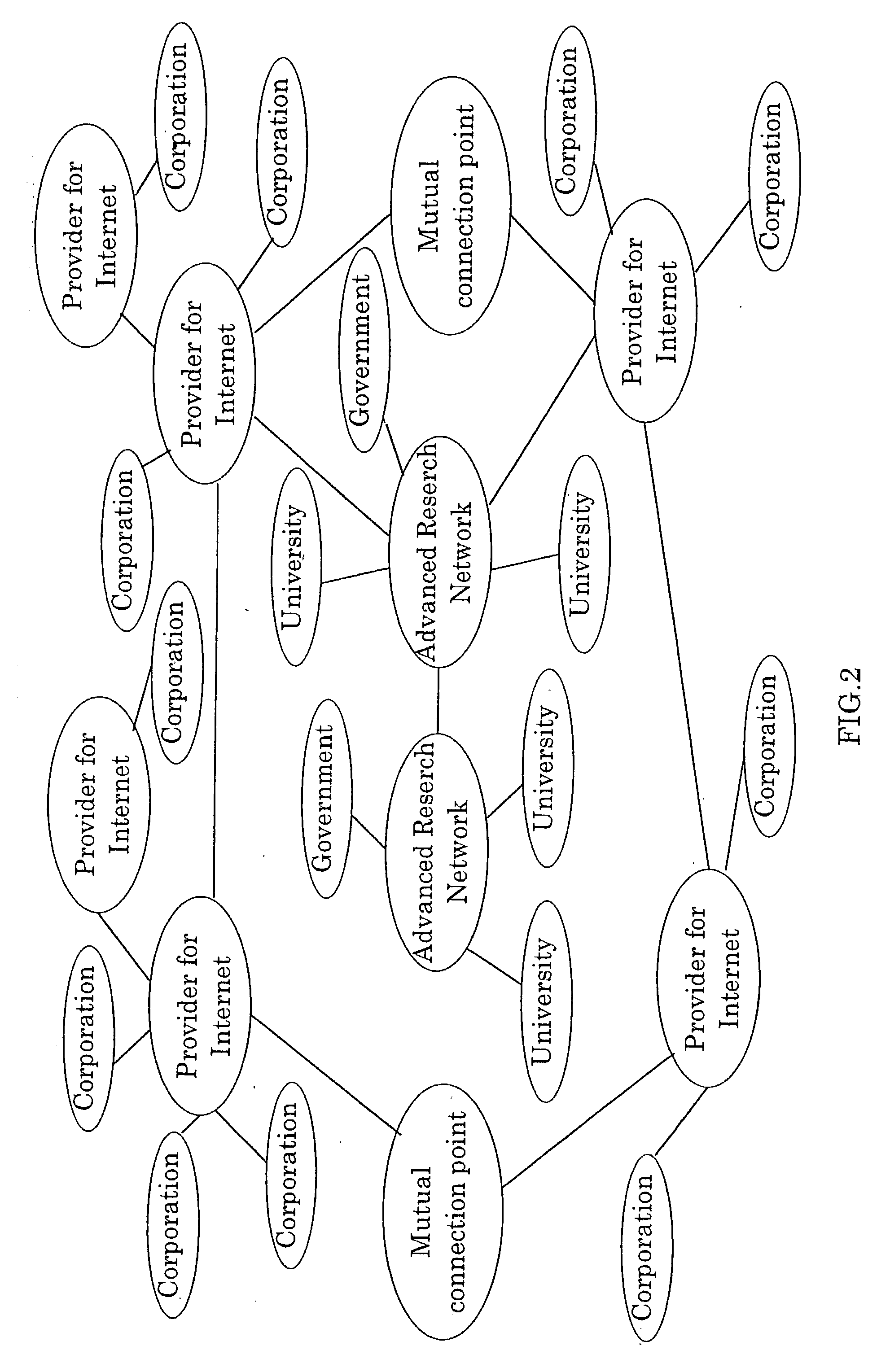
In telecommunication, a private line is typically a telephone company service that uses a dedicated, usually unswitched point-to-point circuit, but it may involve private switching arrangements, or predefined transmission physical or virtual paths. Most private lines connect only two locations, but some have multiple drop points. If the circuit is used for interconnecting switching systems, including manual switchboards, it is often called a tie line.
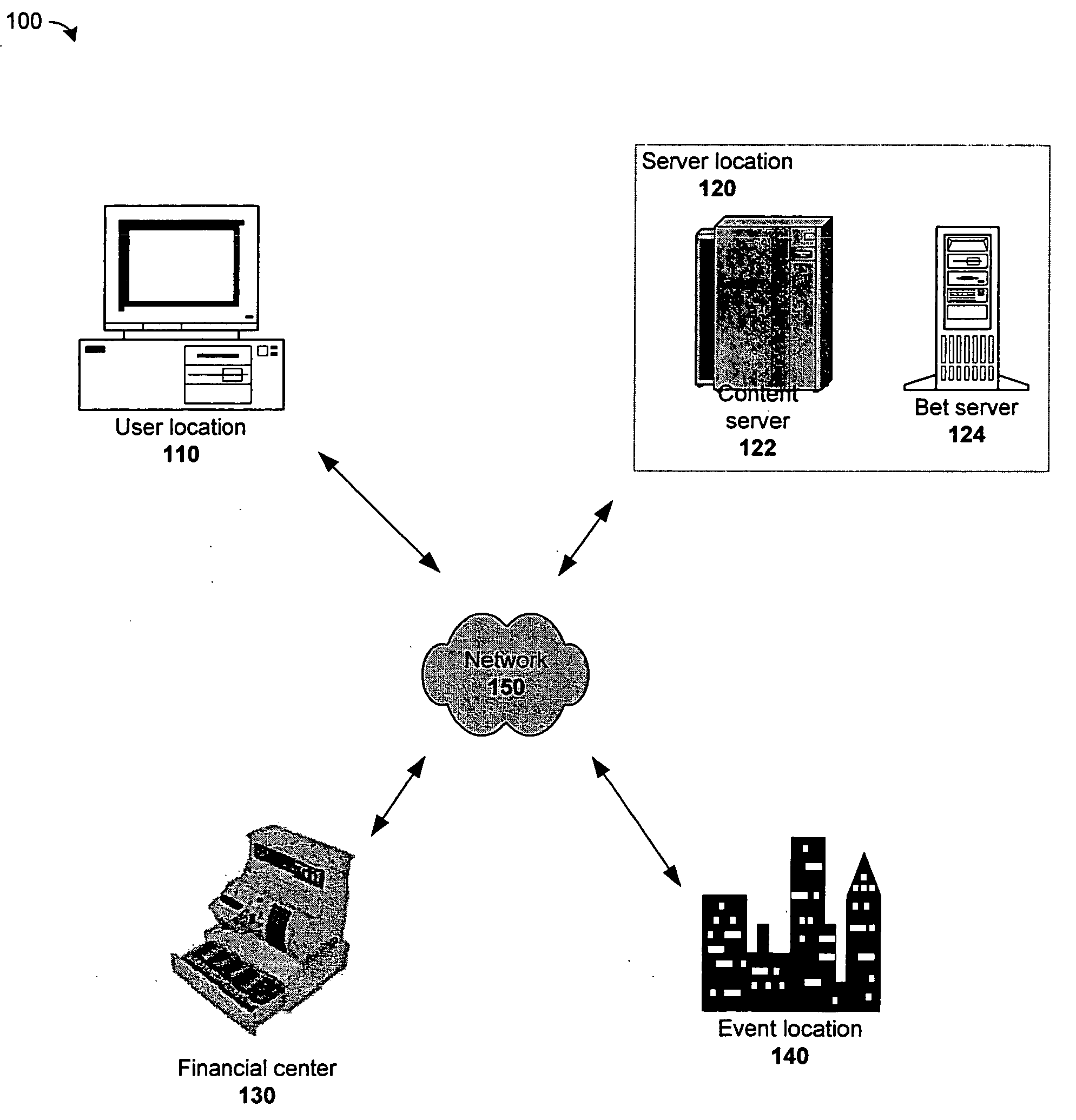
System and method for interactive wagering from a remote location
InactiveUS20050003893A1Avoid chargingData processing applicationsApparatus for meter-controlled dispensingDedicated lineComputer science
A system and method for interactive wagering from a remote location. The invention may preferably be implemented on a multi-purpose device, and preferably uses a multi-purpose communication means, such that a dedicated terminal and / or dedicated line are not required. Various customizable features may be provided, allowing for user-friendly, interactive wagering and related communications between the remote location and an event location over a network, which may further include content locations and server locations, among others.
Owner:HOGWOOD WILLIAM EDWARD +4
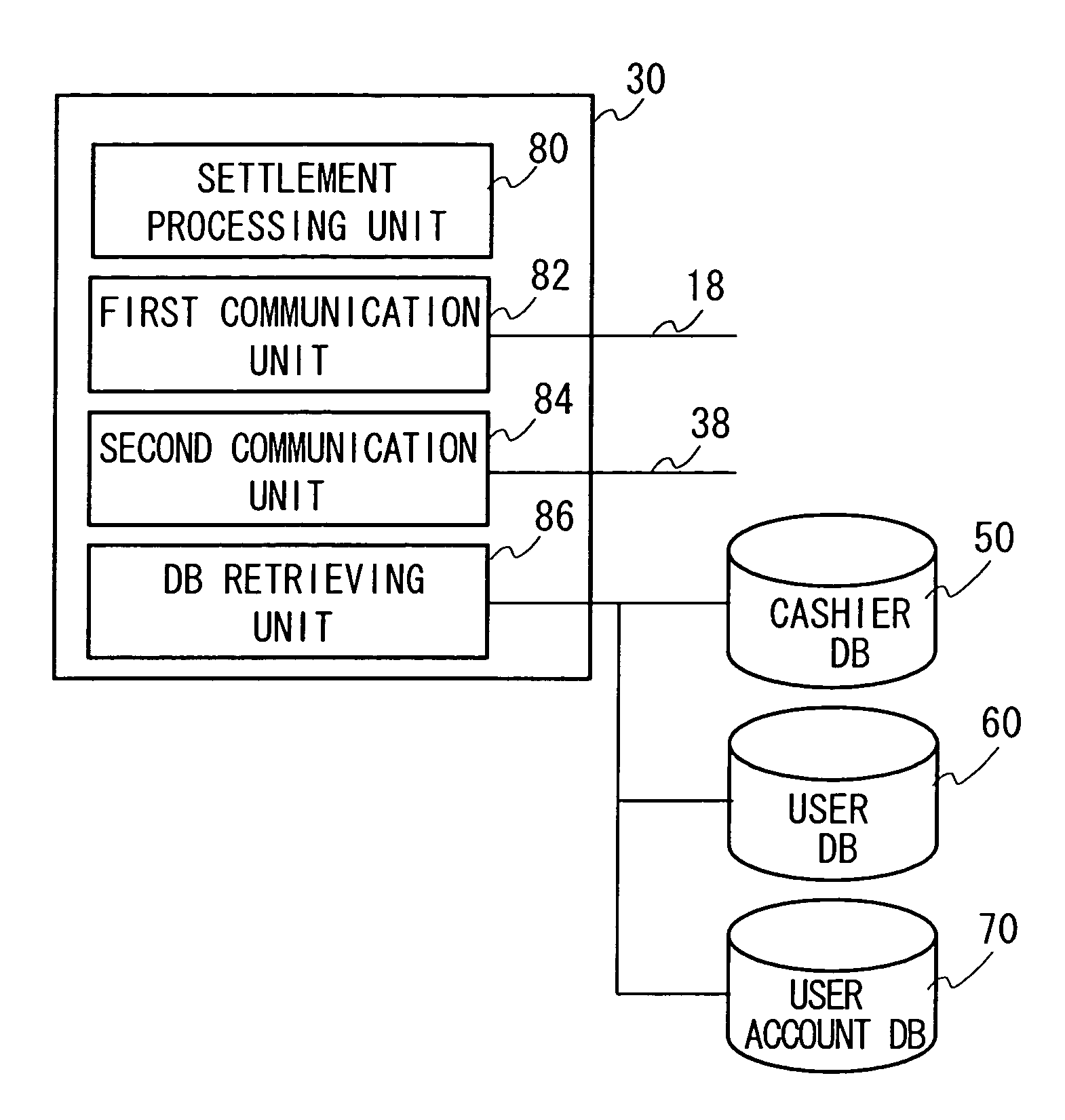
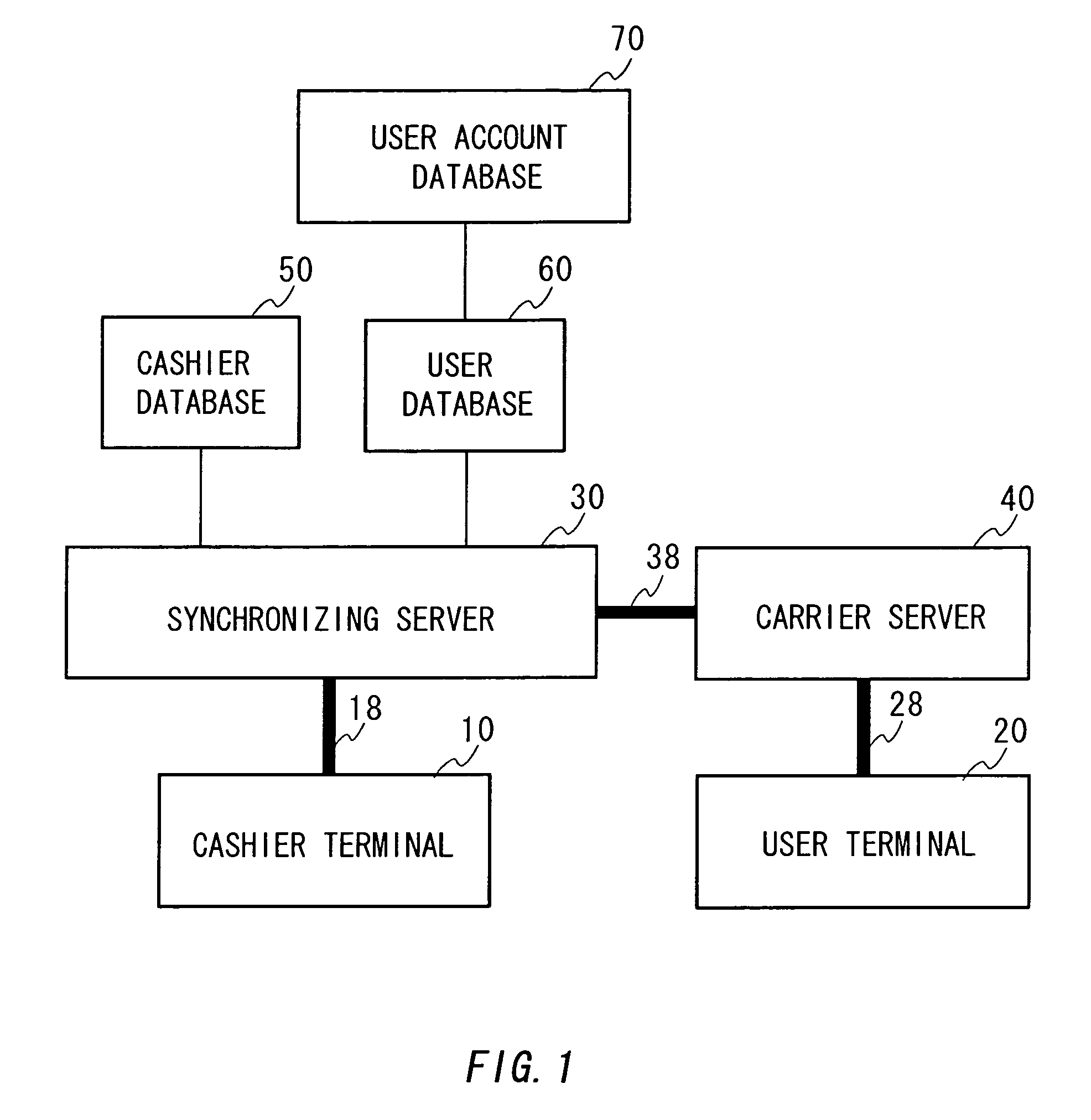
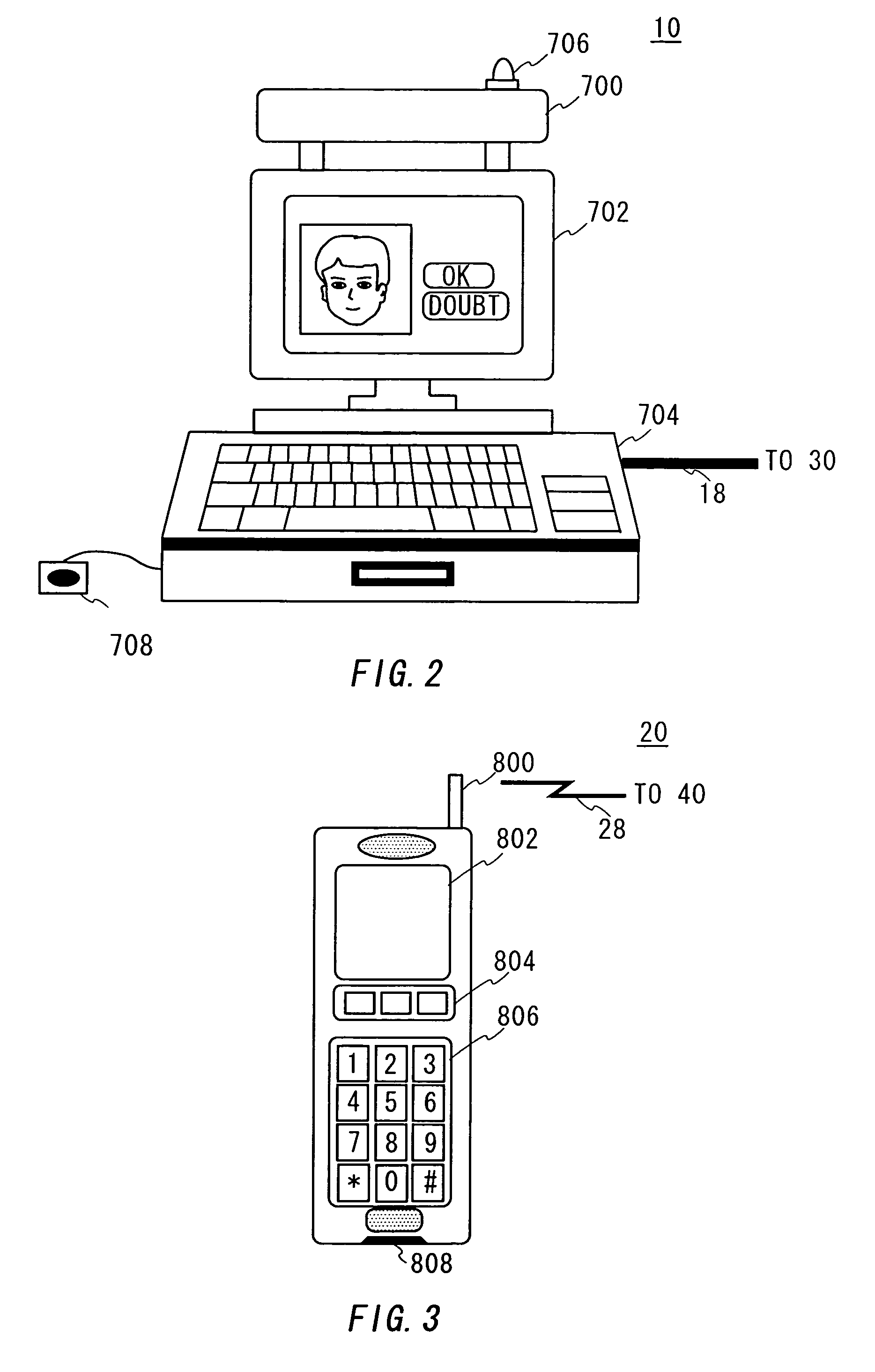
Electronic settlement system, settlement apparatus, and terminal
A simple, easy, and safe electronic settlement system is provided. A user terminal such as a cellular phone is wirelessly connected to a synchronizing server at a counter of a retailer. A cashier terminal of the retailer connects to the synchronizing server via a private line and so on. The cashier terminal receives a transaction identifying number in order to identify the transaction from the synchronizing server, and notifies to a user. A user inputs the transaction identifying number to the user terminal and transmits the transaction identifying number to the synchronizing server. The synchronizing server completes a transaction between the virtual cashier terminal and the user terminal, both of which are corresponded to each other by the transaction identification number. The cashier terminal authenticates the user intermediated by the synchronizing server. The user can complete a settlement without telling his or her personal information such as a credit card number or a password to a retailer. A security of the system is improved.
Owner:KIOBA PROCESSING LLC
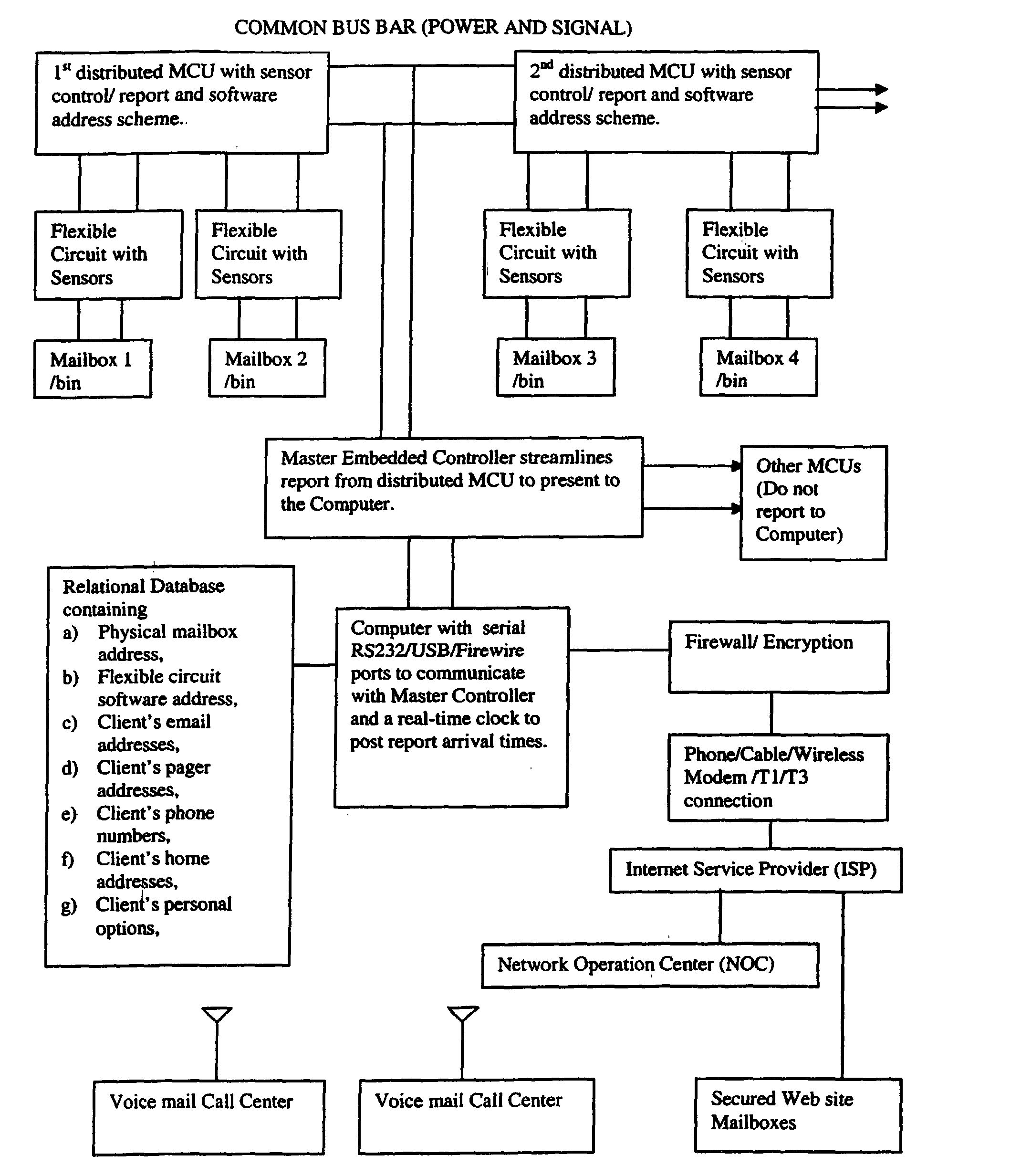
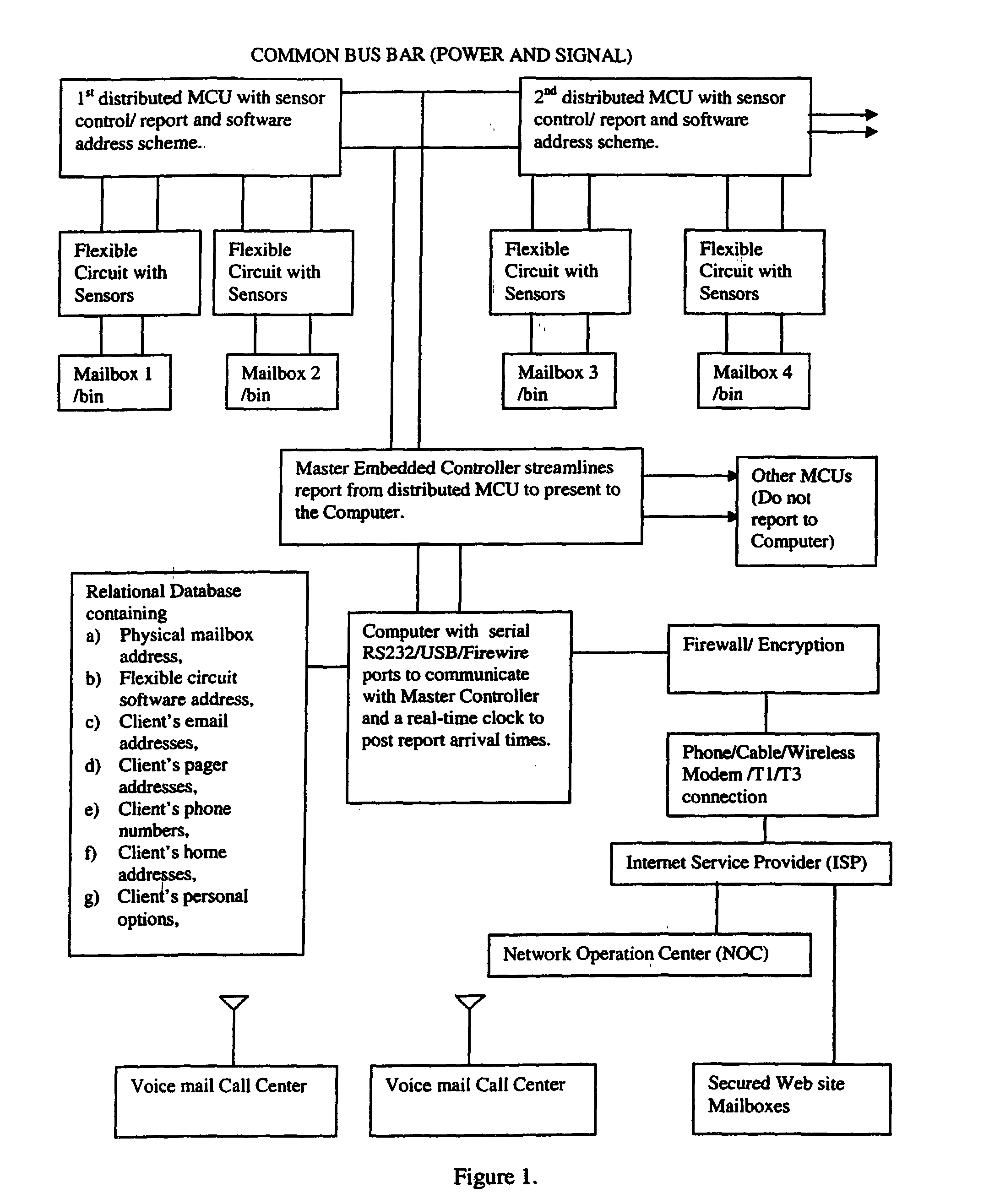
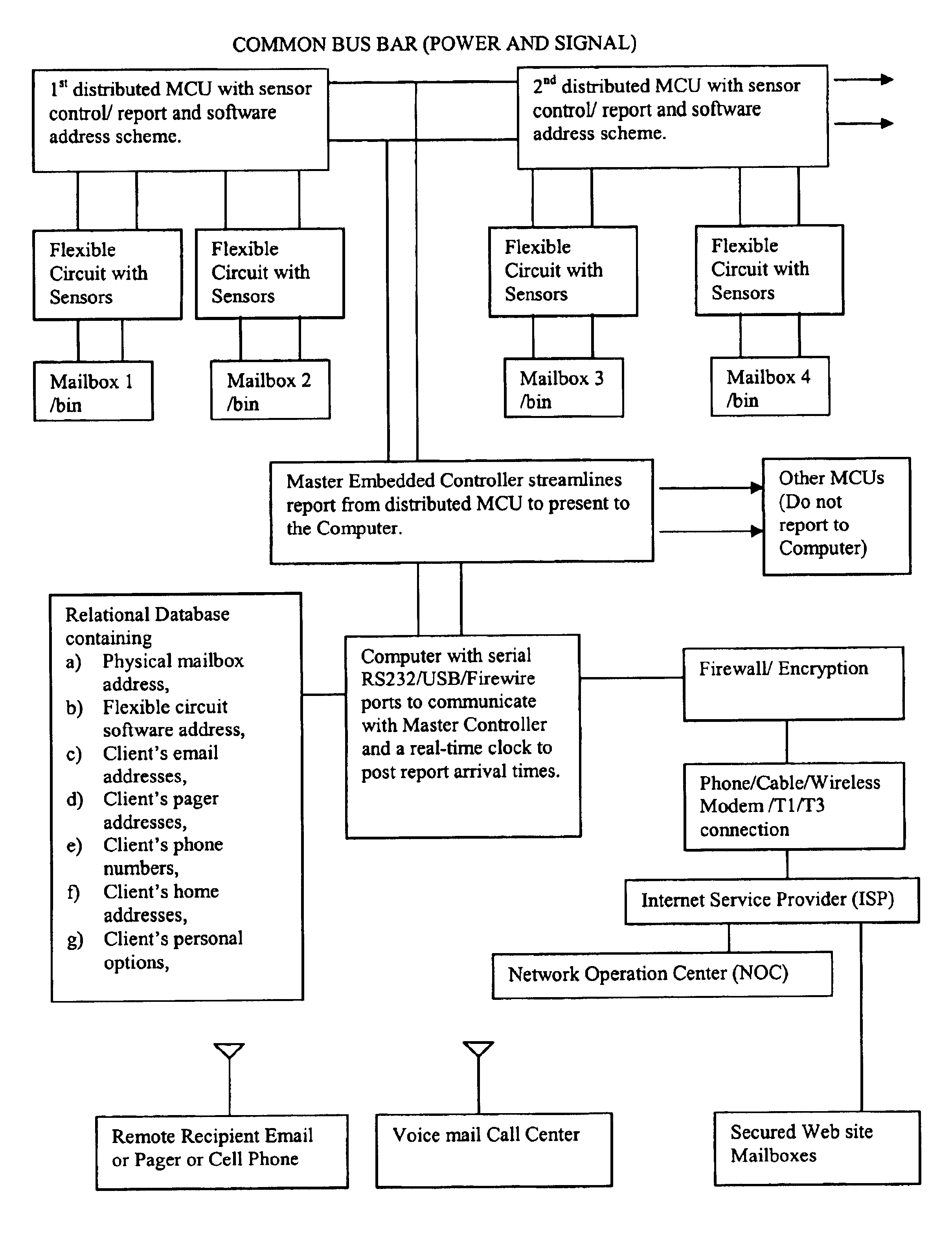
Automated delivery and inventory status notification system and method
InactiveUS20030052778A1Frequency-division multiplex detailsNetwork topologiesMicrocontrollerFlexible circuits
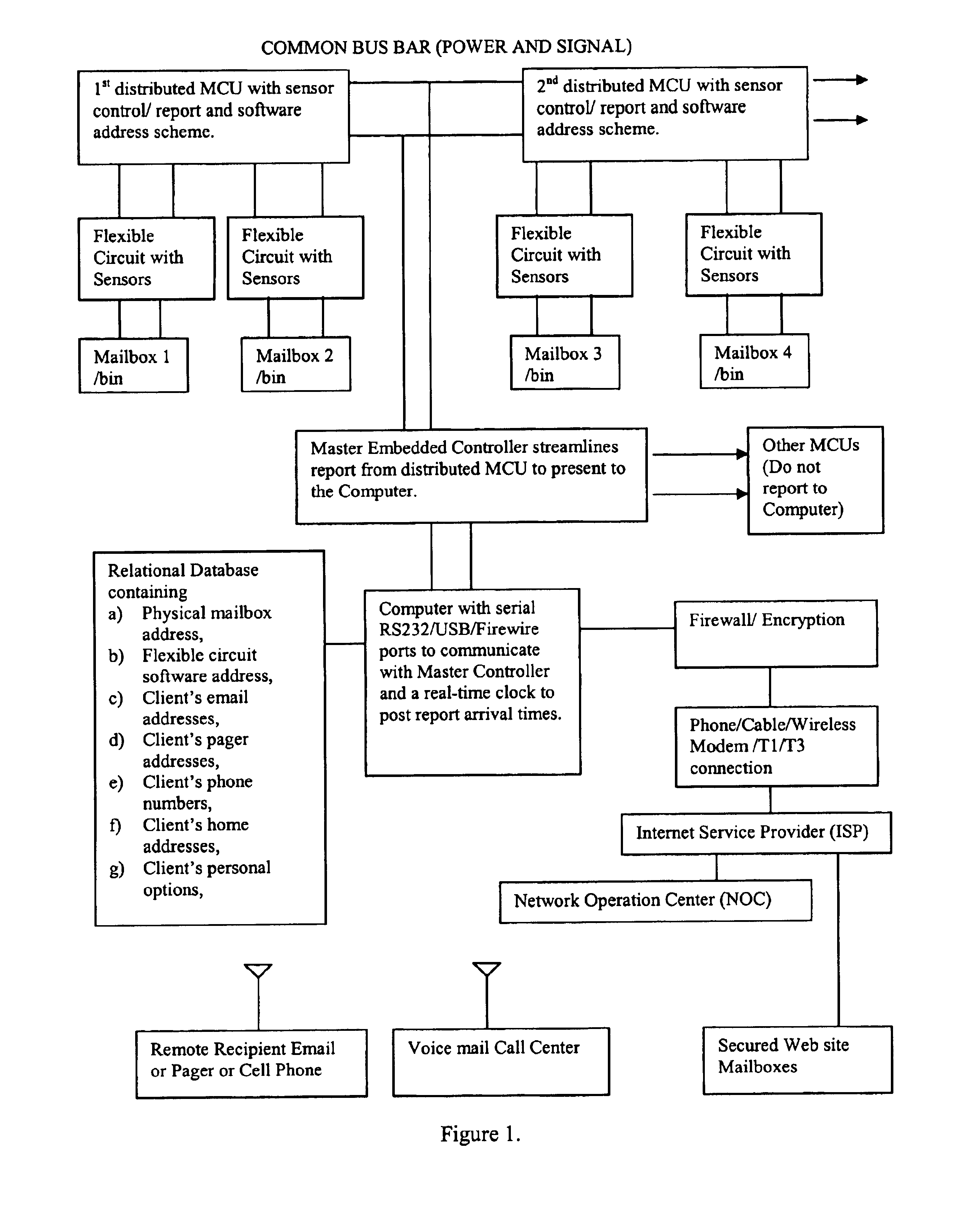
An automated, flexible and programmable system to update delivery and inventory status for an aggregate of remote mailboxes, bins, shelves, sorter bins, and / or a plurality of bins to distant customers and vendors through email, pager, personal digital assistant (PDA), cellular phone mail, voice mail at call centers and / or web site mailboxes. It can function as a delivery notice to mailbox recipients or as inventory stock management to store owners and vendors at remote locations. Various sensors mounted on flexible circuit boards located on the mailboxes, bins, or shelves together with distributed microcontrollers report status through a common bus to a master controller and then to a computer system. The computer in turn dispatches reports and information to various owners and vendors via a remote network operation center accessed through a dedicated line, a wireless service or an Internet Service Provider. The frequency of report update, changing of locations of update, and the relational database can also be reprogrammed at any time from a remote central service location.
Owner:WONG CHON MENG
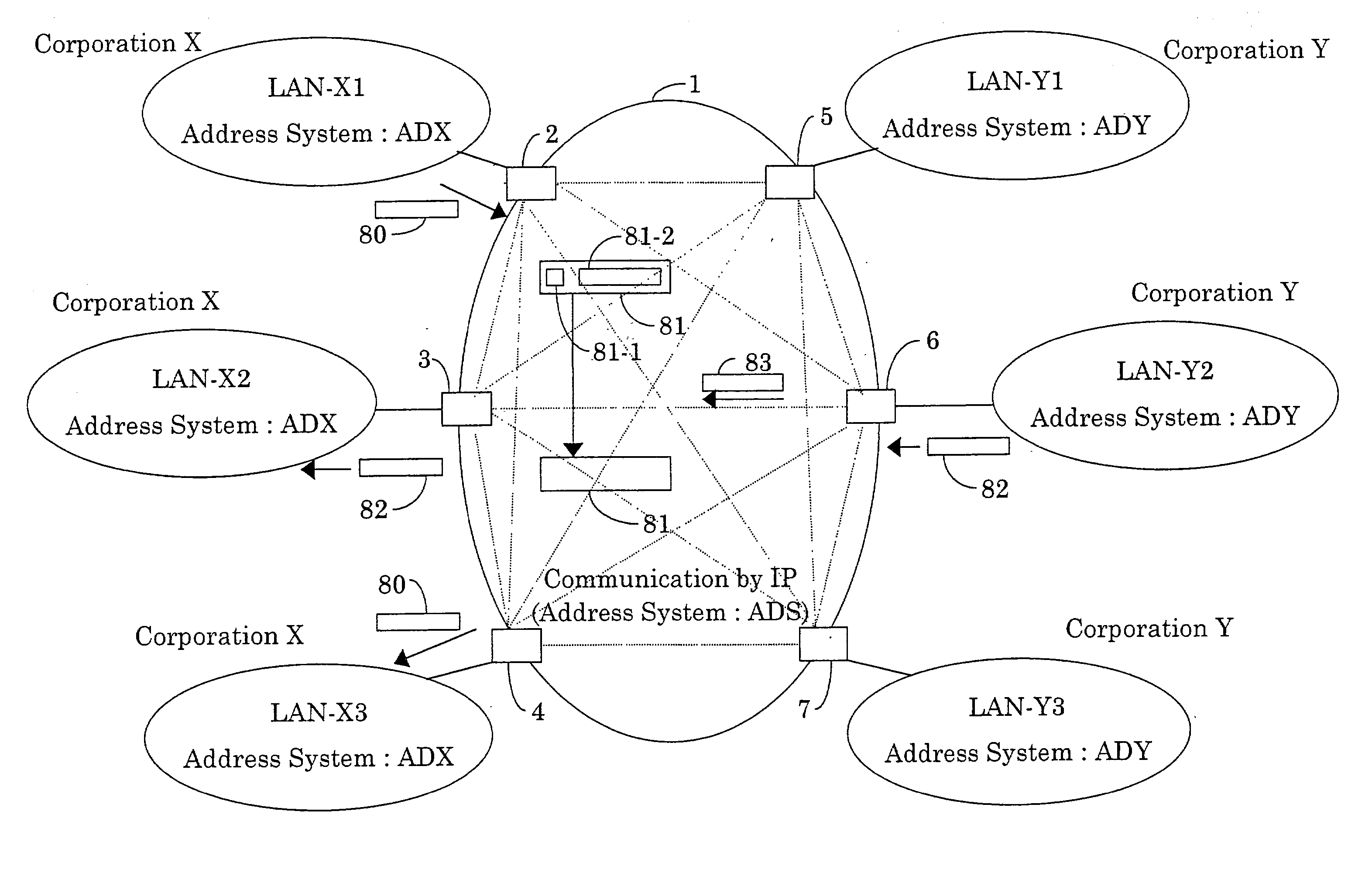
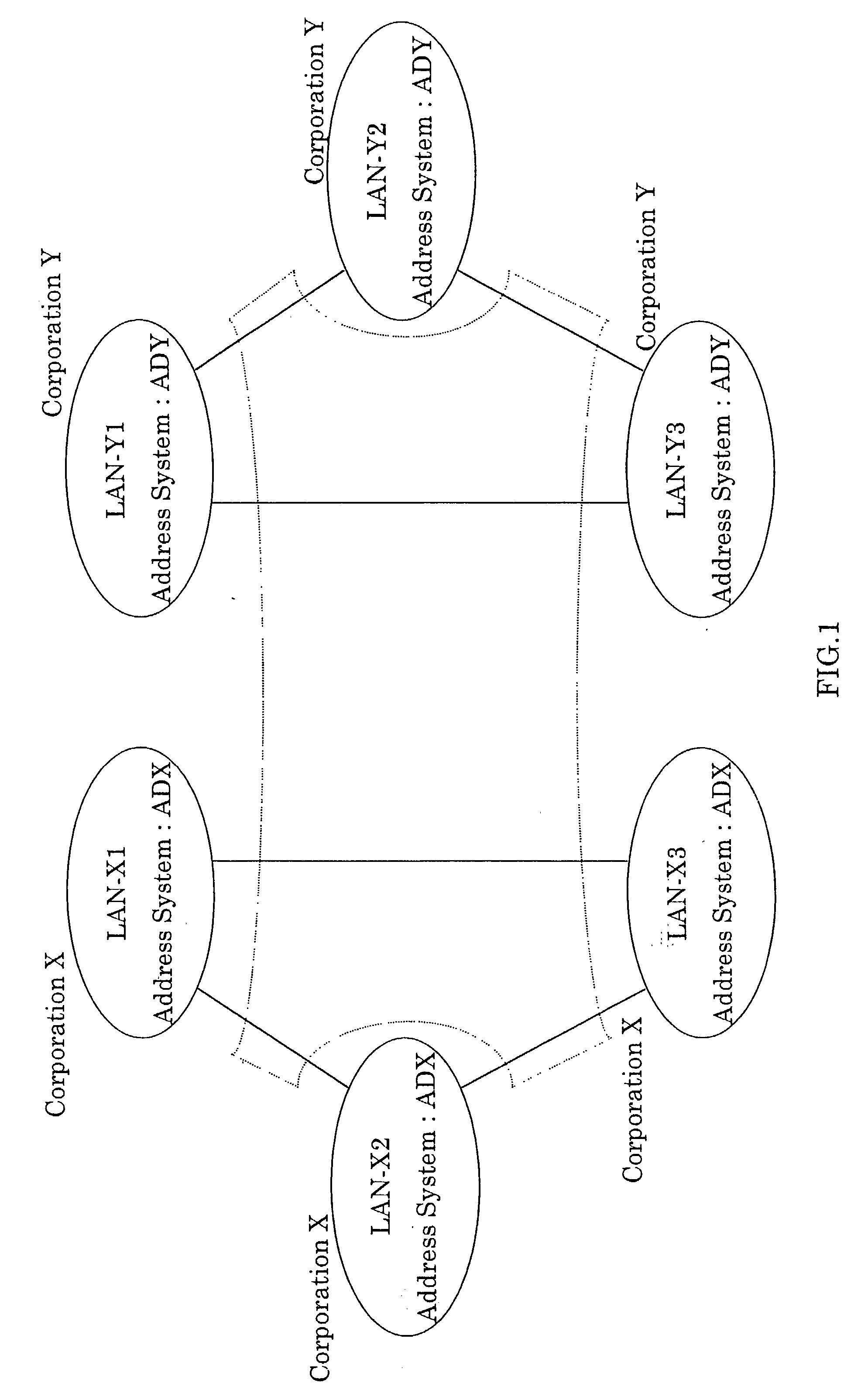
Integrated information communication system
InactiveUS6618366B1Metering/charging/biilling arrangementsInterconnection arrangementsCommunications systemCommunication quality
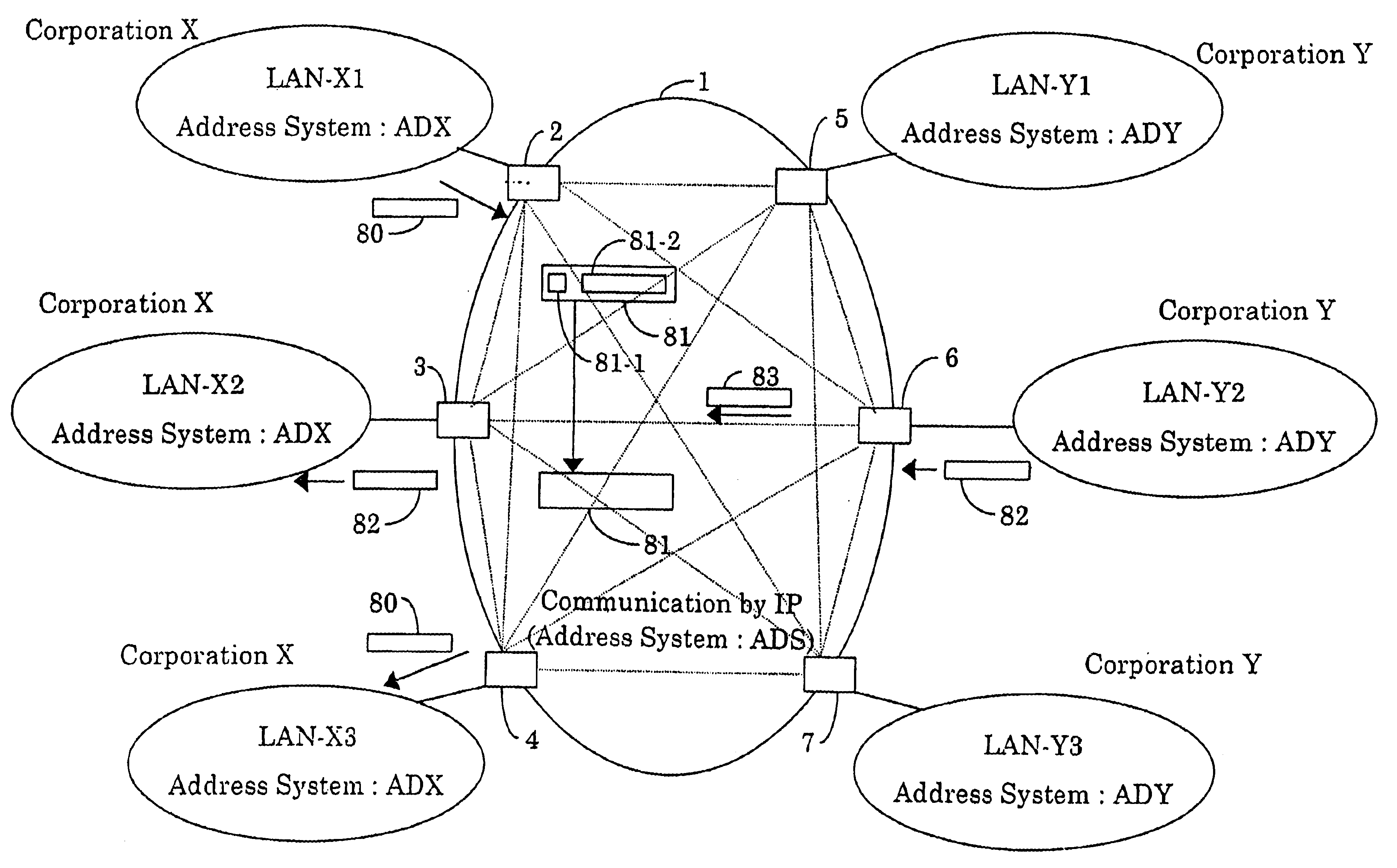
To provide an integrated information communication system without using dedicated lines or the Internet, ensuring communication speed, communication quality, communication trouble countermeasures in a unified manner, wherein security and reliability in communication is ensured. The system is comprised of an access control apparatus for connecting a plurality of computer communication networks or information communication equipment to each, and a relay device for networking the aforementioned access control apparatus, the system having functions for performing routing by transferring information by a unified address system, and is configured such that the aforementioned plurality of computer communication networks or information communication equipment can perform communications in an interactive manner.
Owner:THE DISTRIBUTION SYST RES INST
Repeating installation using telephone line
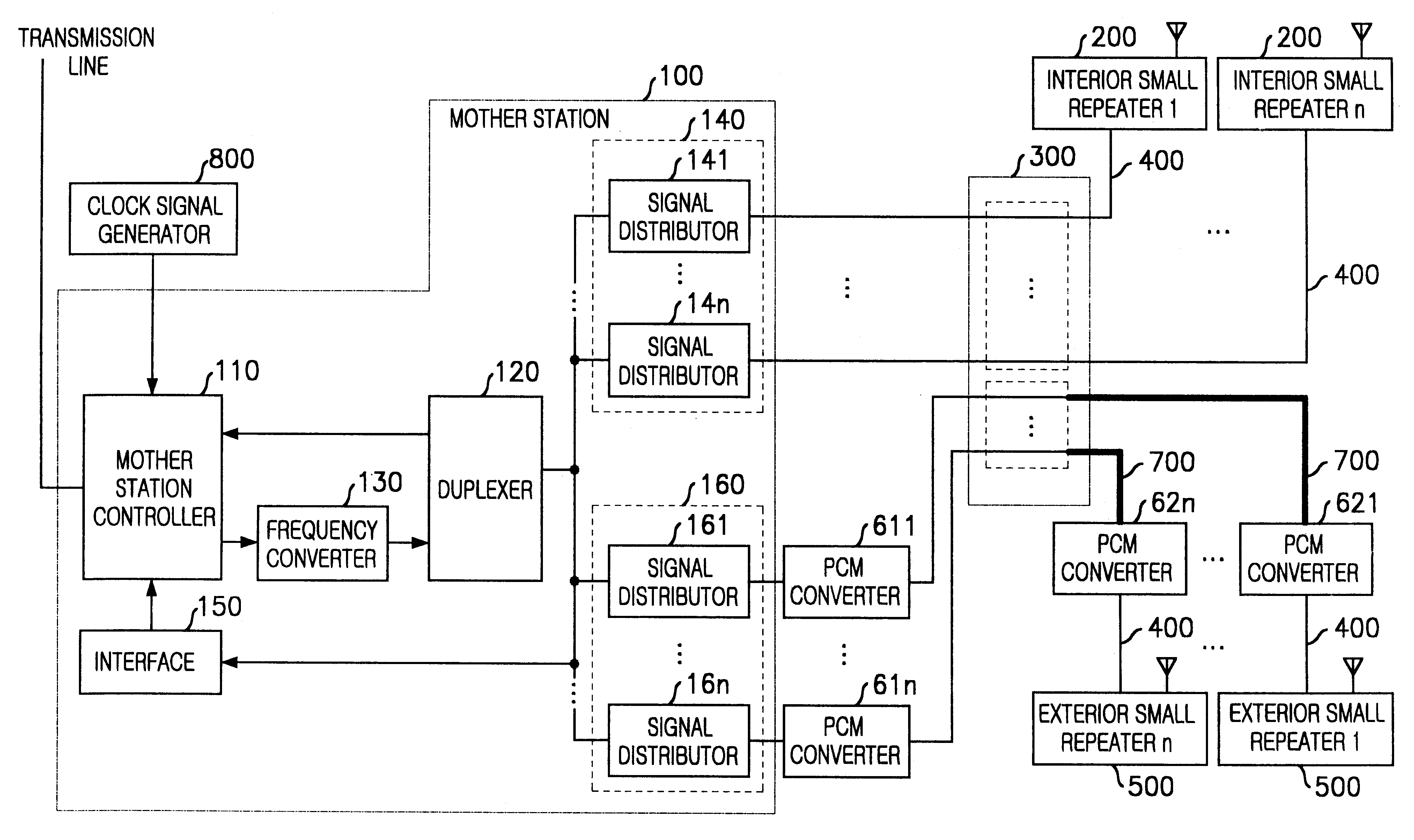
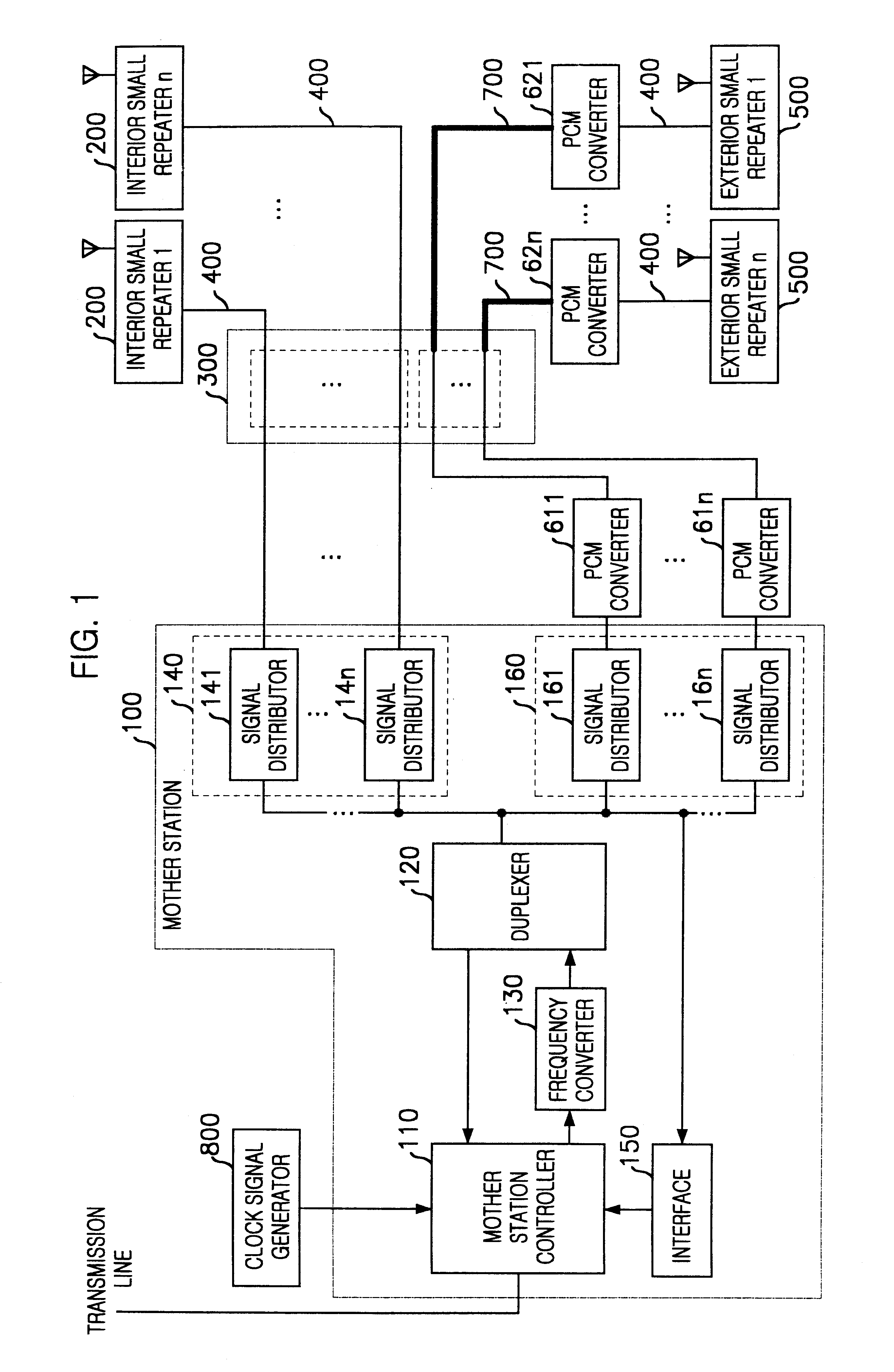
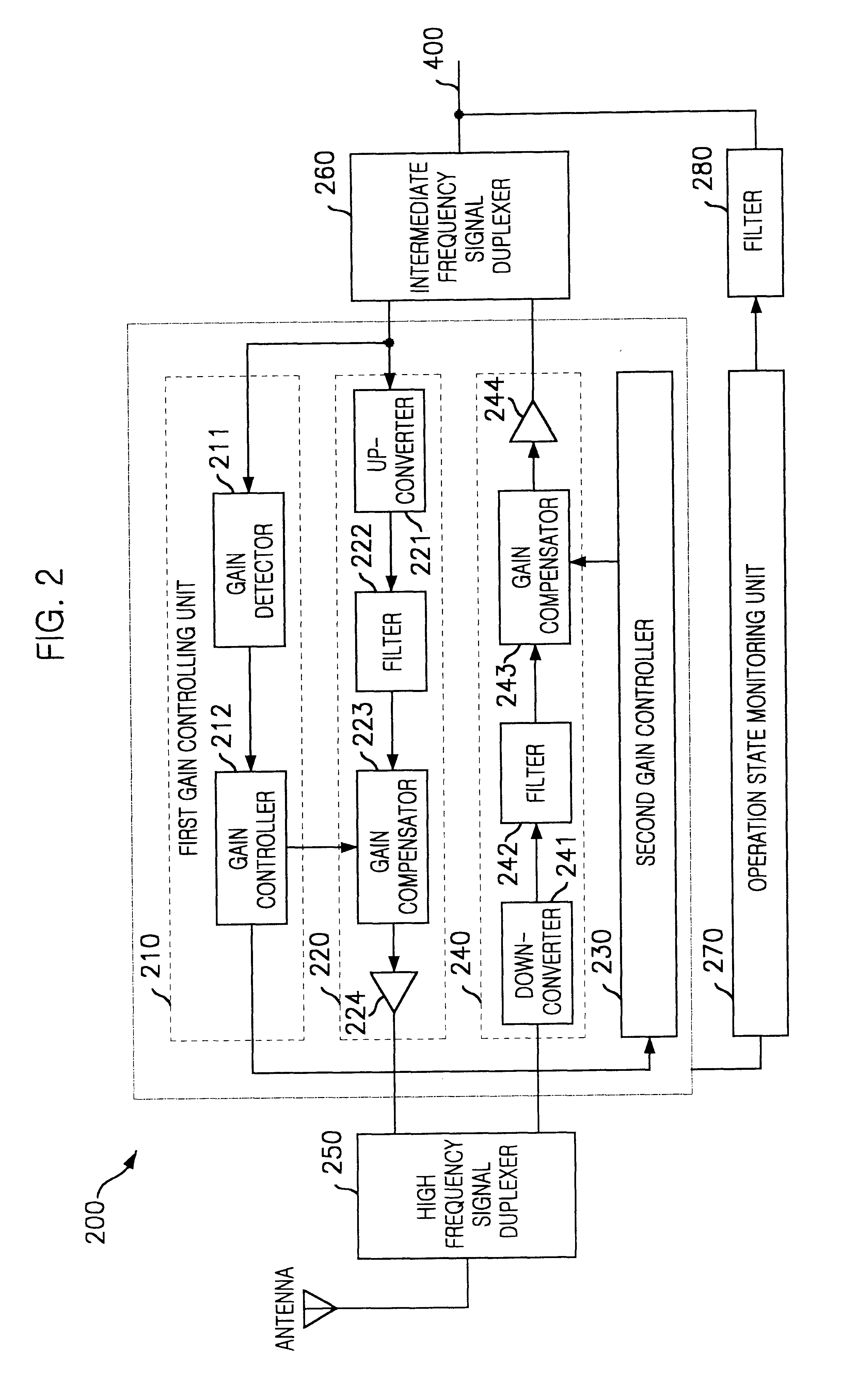
InactiveUS6738597B1Quality improvementPreventing a call dropPower distribution line transmissionActive radio relay systemsIntermediate frequencyData signal
A repeating apparatus of the present invention converts a data signal from the mobile switching center to an intermediate frequency signal and transfers the intermediate frequency signal to an unused telephone line and a dedicated line network. The apparatus converts the intermediate frequency signal transferred through the unused telephone line and the dedicated line network to the data signal frequency signal and transfers the data signal to the mobile switching center. In the present invention, the intermediate frequency signal is transferred between a mother station and at least one first child station through the unused telephone line and the intermediate frequency signal is modulated to transfer between the mother station and at least one second child station through the dedicated line network.
Owner:SK TELECOM CO LTD
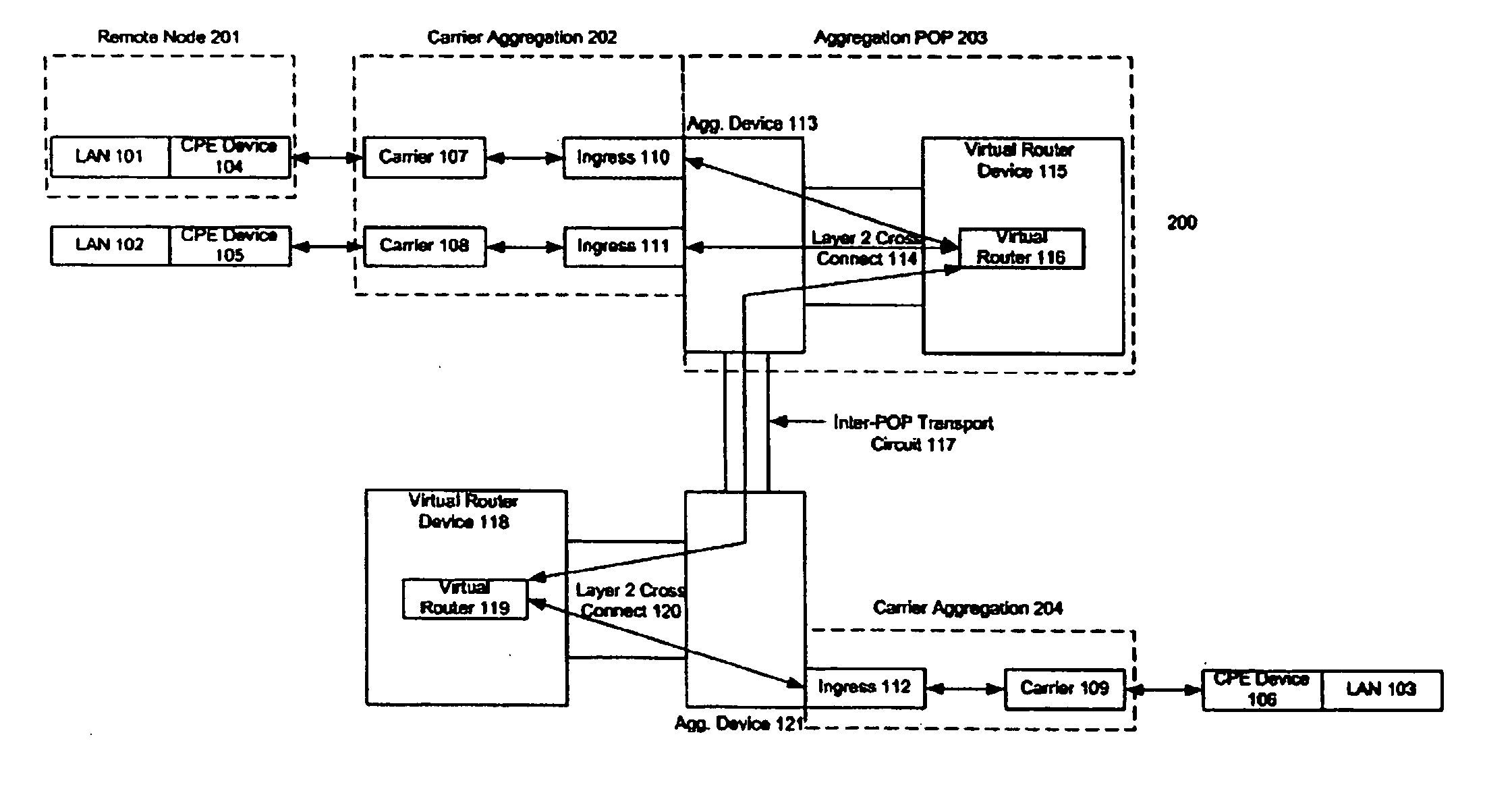
Private lines traversing a packet network and re-arrangement of channels among packet network connections
InactiveUS6882652B1Easy to adaptReduce needTime-division multiplexNetworks interconnectionPacket generatorNetwork connection
Techniques for providing communication services include provisioning a packet network connection that has packet channels, each of which is independently capable of carrying narrowband signals so as to emulate a private line circuit. A narrowband private line that traverses the packet network connection using a particular one of the packet channels is established. Delays that might otherwise be introduced as a result of packetizing the narrowband signals can be reduced. Private lines that traverse the packet network connection using other packet channels can be added or removed without adversely affecting the existing lines. Additionally, a narrowband communication line that traverses a channel in a first virtual circuit connection in a packet network can be rolled over to a channel in a second virtual circuit connection in the packet network. The latter technique can improve the use of available bandwidth and can be applied to non-private line applications as well.
Owner:TELLABS OPERATIONS
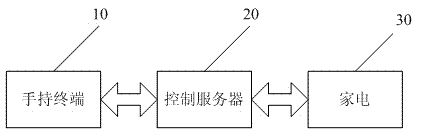
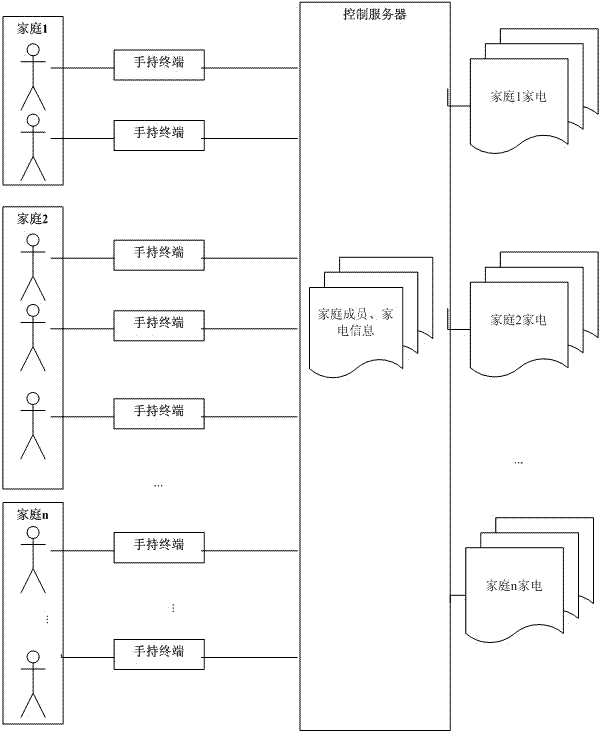
Method and system for remote control of household appliances
ActiveCN102789682ARemote control is safe and reliableSafe and reliable controlTransmission systemsTransmissionRemote controlHand held
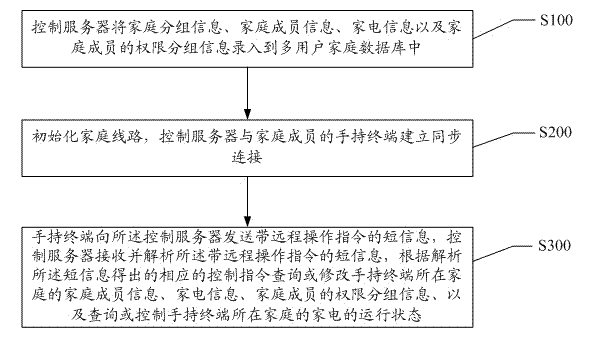
The invention discloses a method and system for the remote control of household appliances. According to the invention, by plugging private lines into homes, the household appliances of each home are managed uniformly; the interaction with a control server is realized by a hand-held terminal; the hand-held terminal sends a control message to the control server, the control server conducts analysis according to the message to set the user rights in the home, operate the household appliances according to the instructions and send messages to feed back the operation state of the household appliances, thus the remote control of household appliances is realized with low cost, safety and reliability, and simultaneously the invention provides the intelligent and templated control of household appliances with an enforcement base.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
Secure token access distributed database system
ActiveUS20040006699A1Digital data processing detailsUnauthorized memory use protectionEffective actionThe Internet
A secure token access distributed database system to provide verification of someone's or something's identity quickly and securely is provided, wherein such database and system is readily scalable from local to nationwide to worldwide use. The system specifically addresses the use of an authenticated user identification (ID) where any accepted authentication scheme can be employed in combination with a number of secure enabled databases connected by any means, including LAN, WAN, Internet, and dedicated lines, to provide value-added data in real-time at the main point of security contact. Furthermore, the instant invention provides a concept by which a potentially unlimited number of secure enabled databases containing various kinds of data potentially useful to a requesting entity, are either connected by some network means, or exposed to the Internet through a secure connection. Data transfer may also be bi-directional. As part of the security incident information exchange, data may not only be received by the requesting entity, but the provider database may also receive updated information. Requests may be progressive in nature. Data contained in a response from one database may cause the requesting application to send out a new, modified request for the ID based on that data. Moreover, continual update of the incident data may continue even after sufficient information has been received to make a security decision, e.g., grant entry. If subsequent data arrives that could affect that decision, it may provide authorities and security personnel with timely data and an opportunity for appropriate and effective action.
Owner:VERIFONE INC
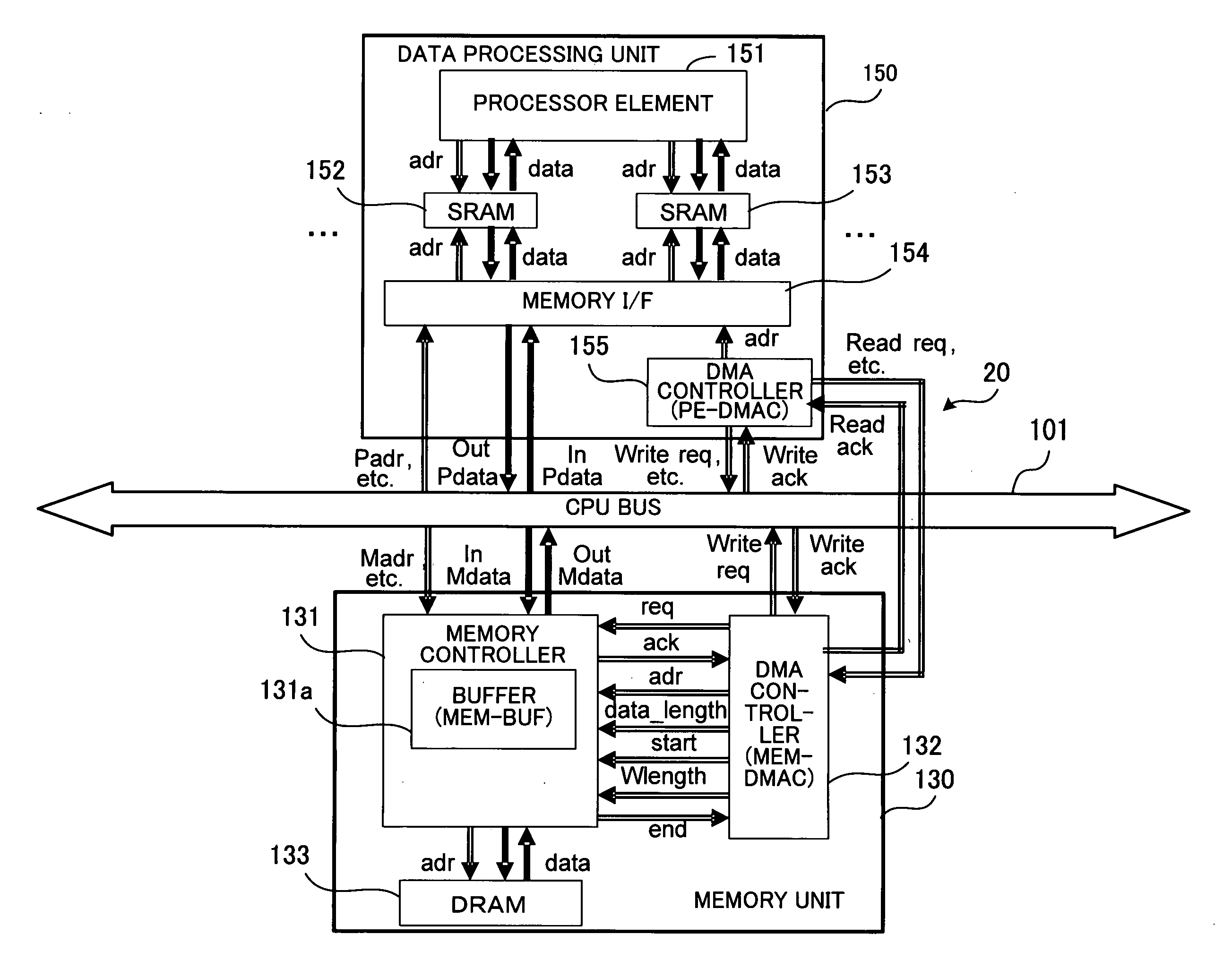
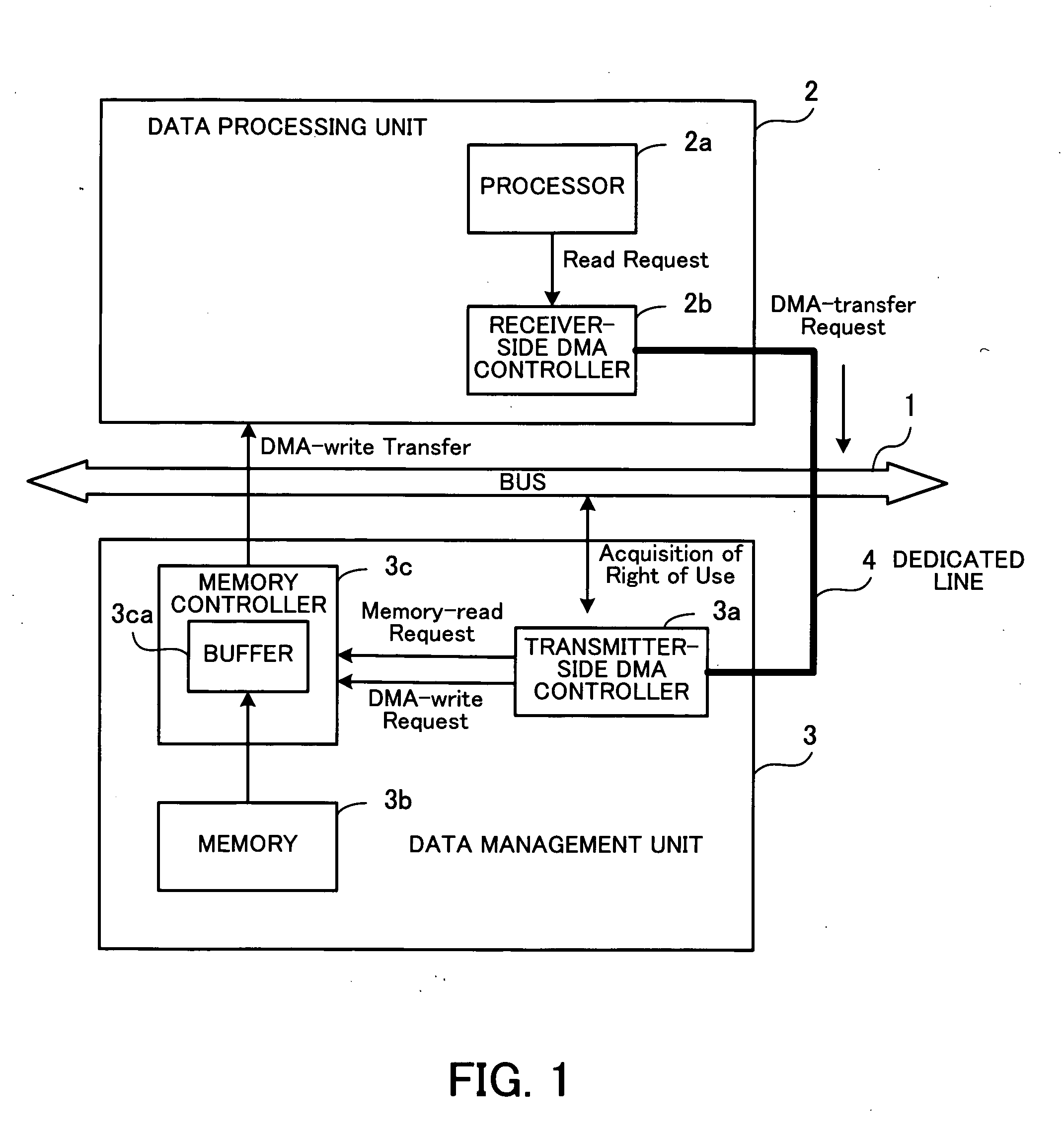
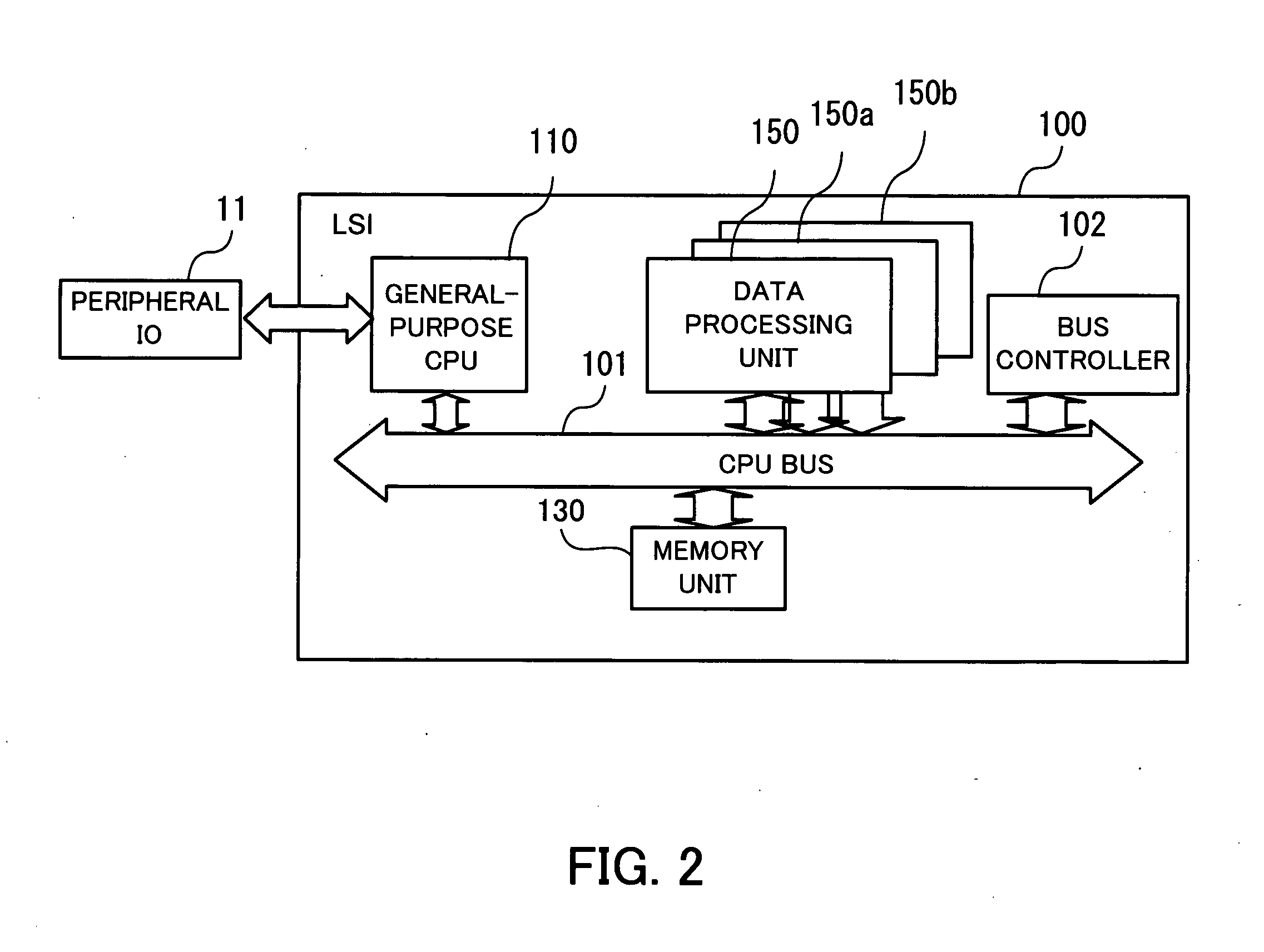
Data processing apparatus
InactiveUS20070174506A1Improve efficiencyElectric digital data processingManagement unitData management
A data processing apparatus in which DMA transfer is performed. When a processor in a data processing unit outputs a first request to read data managed by a data management unit, a receiver-side DMA controller outputs a second request for DMA transfer, from the data processing unit to the data management unit through a dedicated line. Next, a memory controller in the data management unit reads out from the memory the data designated by the second request, and stores the data in a buffer. Then, a transmitter-side DMA controller acquires a right of use of a bus, and the memory controller transfers the data stored in the buffer, through the bus by DMA, and writes the data in a data storage area in the data processing unit.
Owner:FUJITSU LTD
Automated delivery and inventory status notification system and method
InactiveUS6816074B2Frequency-division multiplex detailsNetwork topologiesMicrocontrollerRelational database
An automated, flexible and programmable system to update delivery and inventory status for an aggregate of remote mailboxes, bins, shelves, sorter bins, and / or a plurality of bins to distant customers and vendors through email, pager, personal digital assistant (PDA), cellular phone mail, voice mail at call centers and / or web site mailboxes. It can function as a delivery notice to mailbox recipients or as inventory stock management to store owners and vendors at remote locations. Various sensors mounted on flexible circuit boards located on the mailboxes, bins, or shelves together with distributed microcontrollers report status through a common bus to a master controller and then to a computer system. The computer in turn dispatches reports and information to various owners and vendors via a remote network operation center accessed through a dedicated line, a wireless service or an Internet Service Provider. The frequency of report update, changing of locations of update, and the relational database can also be reprogrammed at any time from a remote central service location.
Owner:WONG CHON MENG
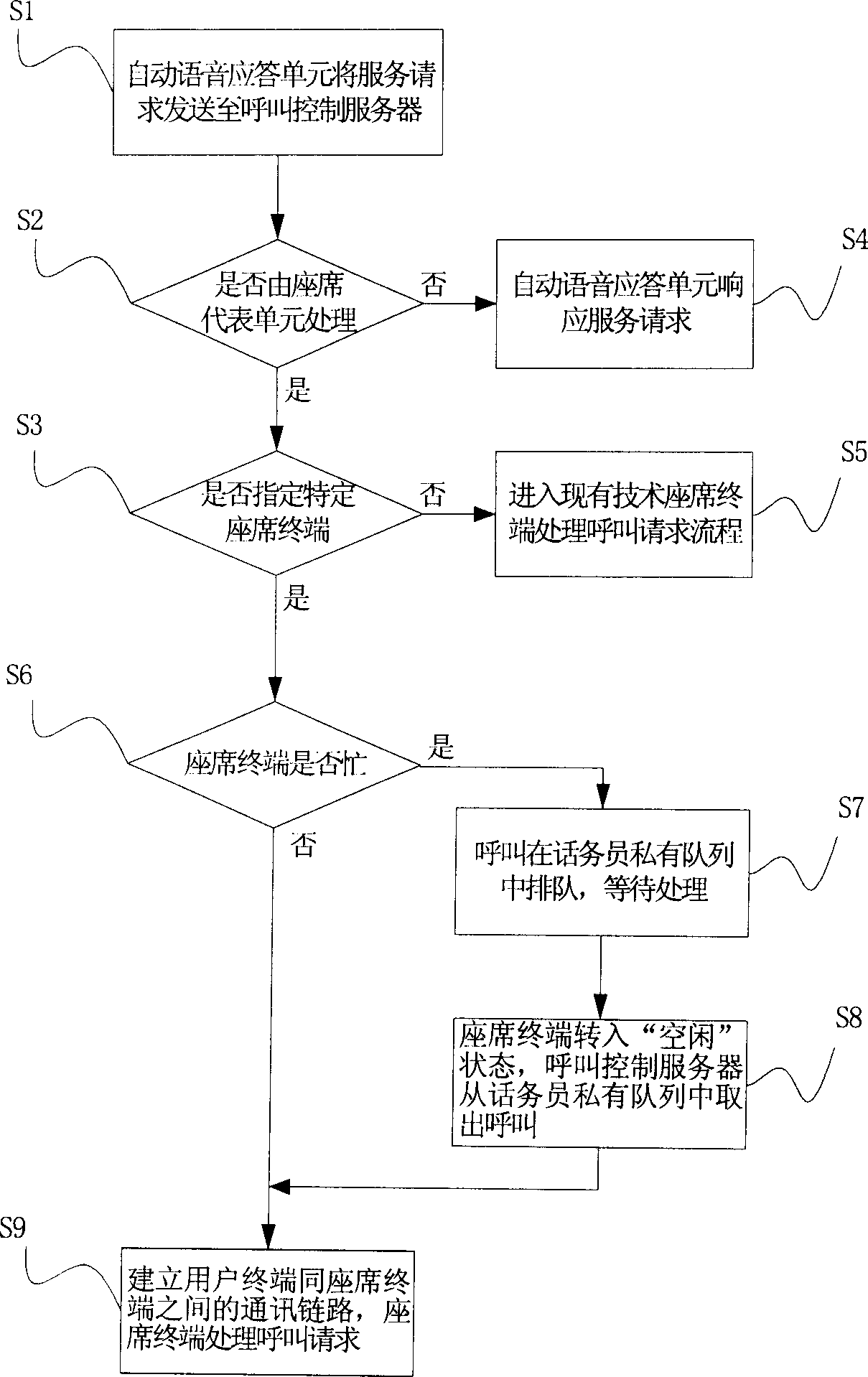
Call queuing method
InactiveCN1700716AShort response timeImprove work efficiencyAutomatic exchangesSelection arrangementsCall controlAutomatic call distribution
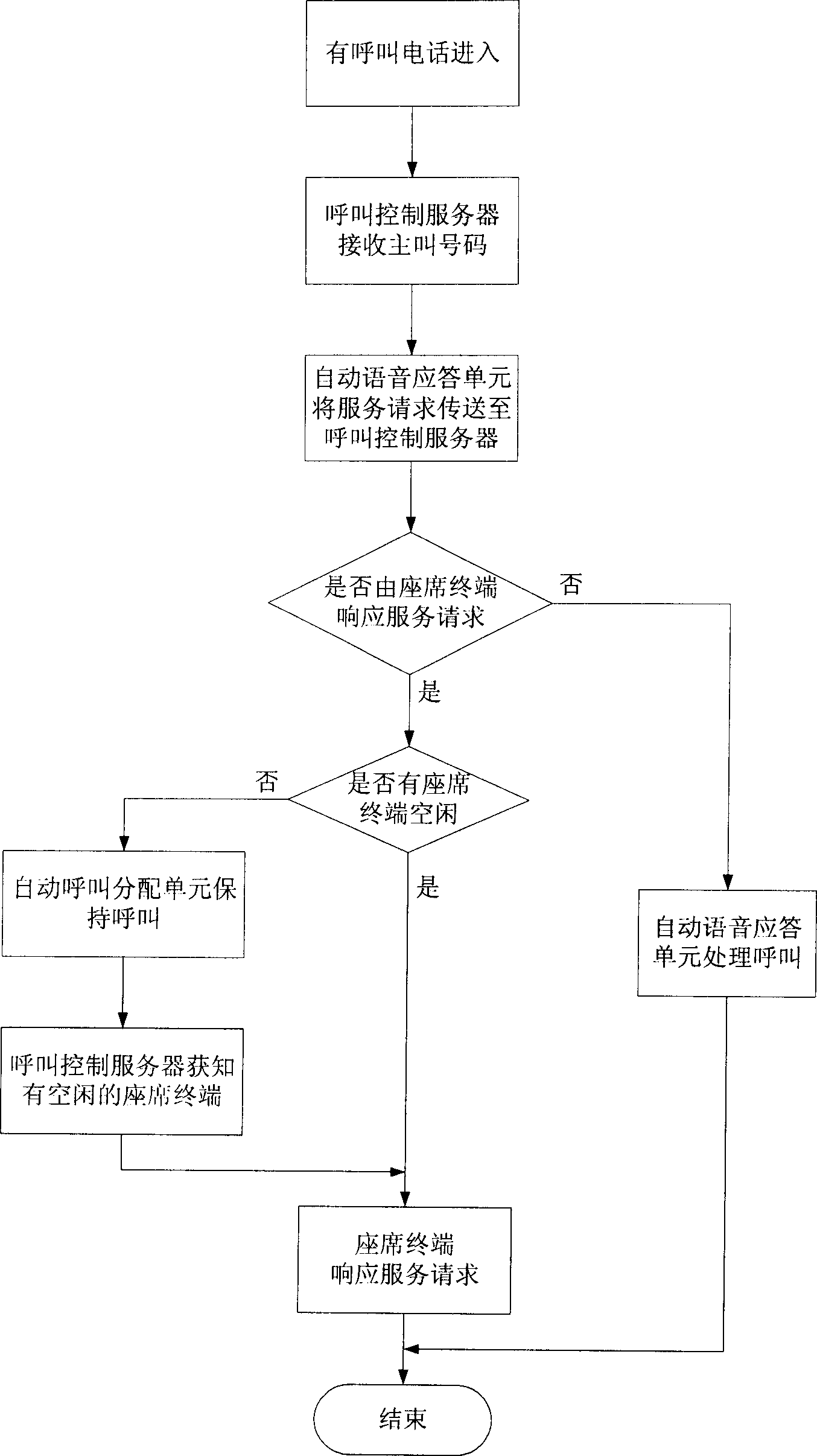
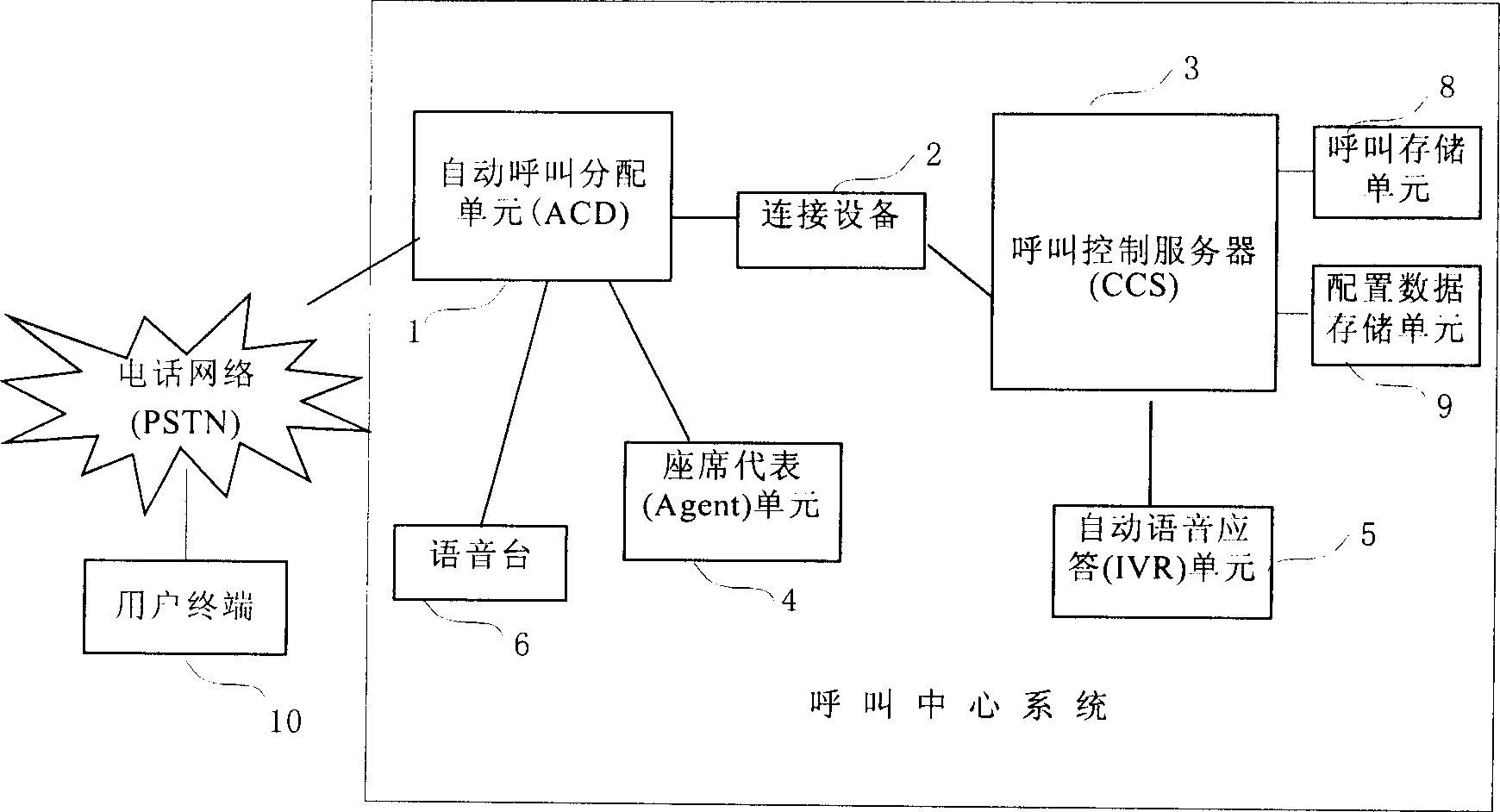
This invention discloses one calling and lining method, which comprises the following steps: a, the calling system receives the calls from user terminal; b, the call control servo judges whether the said requirements respond to the fixed terminal; c, call servo selects the fixed terminal and the automatic call alignment unit connects the call to the fixed terminal to respond the service requirement; d, the call control servo judges whether the set fixed terminal is at busy status; f, the said call waits in private line; g, the automatic call alignment unit connects the calls to the fixed terminal.
Owner:HUAWEI TECH CO LTD
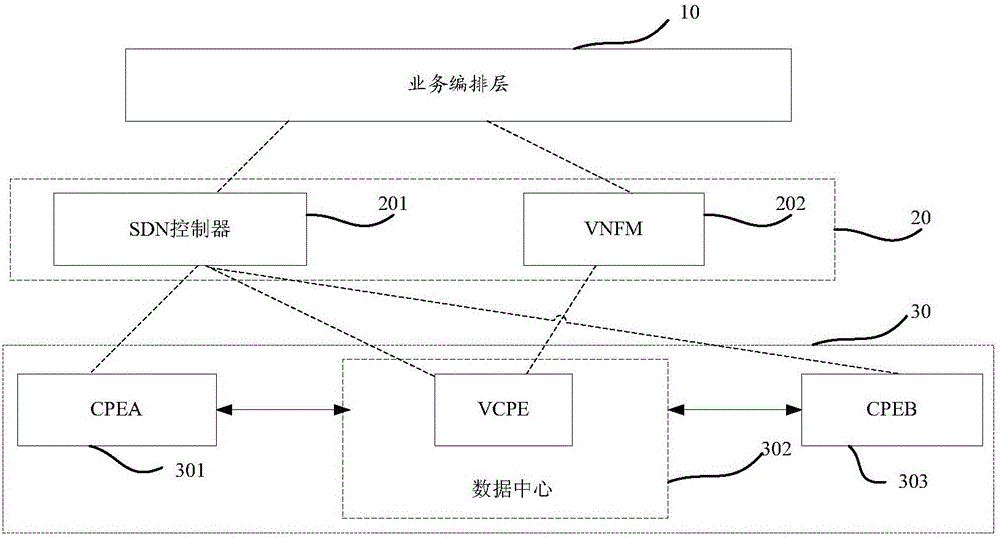
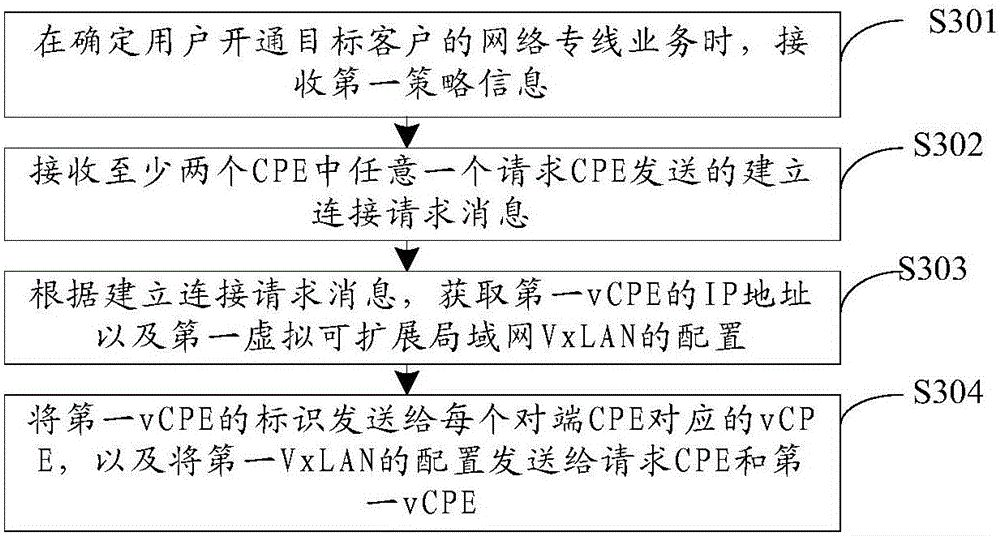
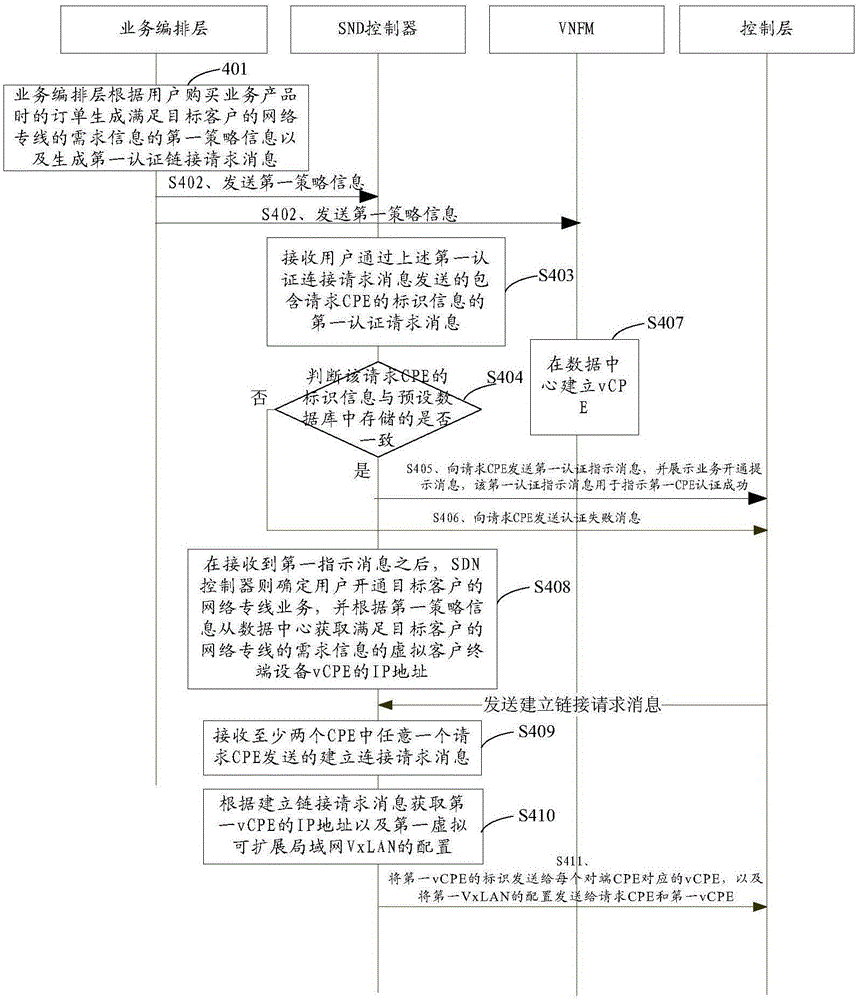
Network private line establishment method, apparatus and system
Embodiments of the present invention provide a network private line establishment method, apparatus and system, relating to the technical field of network communication. The network private line establishment method is low in operation complexity and comprises the steps of when a network private line service of a target client is opened, receiving first policy information; acquiring an IP address of virtual customer premise equipment (vCPE) meeting demand information of a network private line of the target client; receiving a request message for connection establishment that is sent by any request CPE of the at least two CPEs; and acquiring, according to the request message for connection establishment, an identifier of the first vCPE and configuration of a first virtual extensible local area network (VxLAN), sending the identifier of the first vCPE to the vCPE corresponding to each peer CPE, and sending the configuration of the first VxLAN to the request CPE and the first vCPE, so as to realize point-to-point communication of the network private line of the target client finally.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
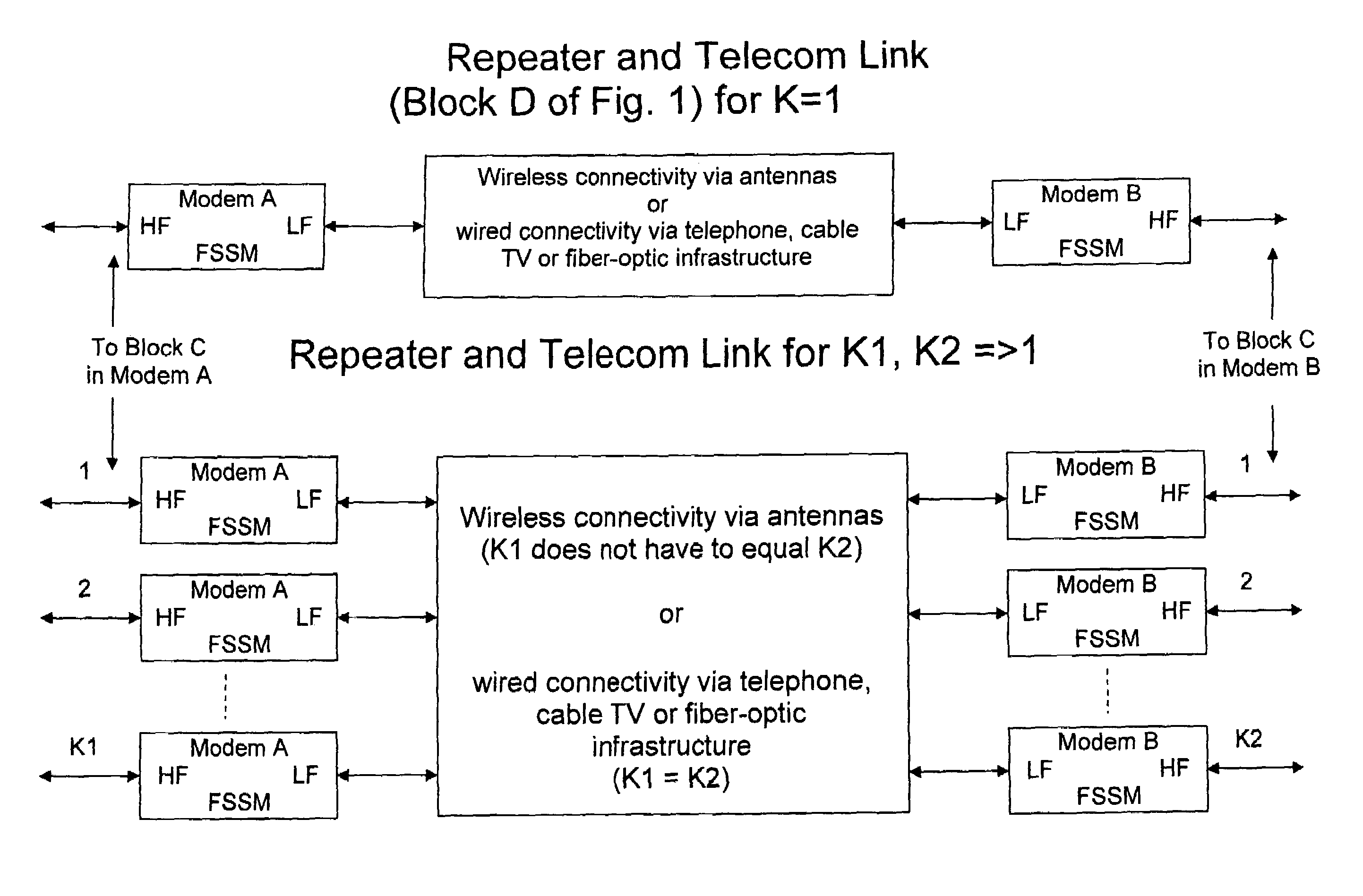
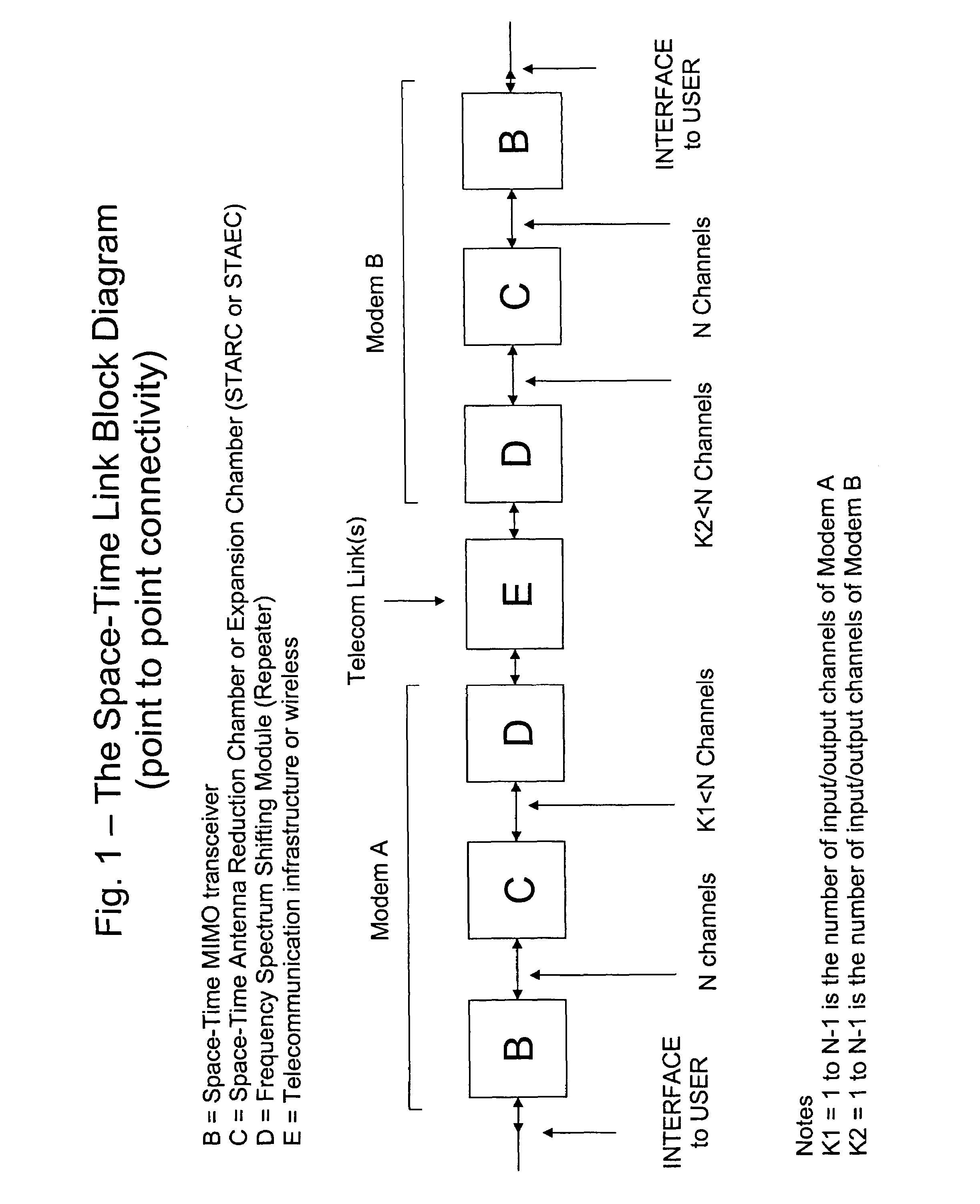
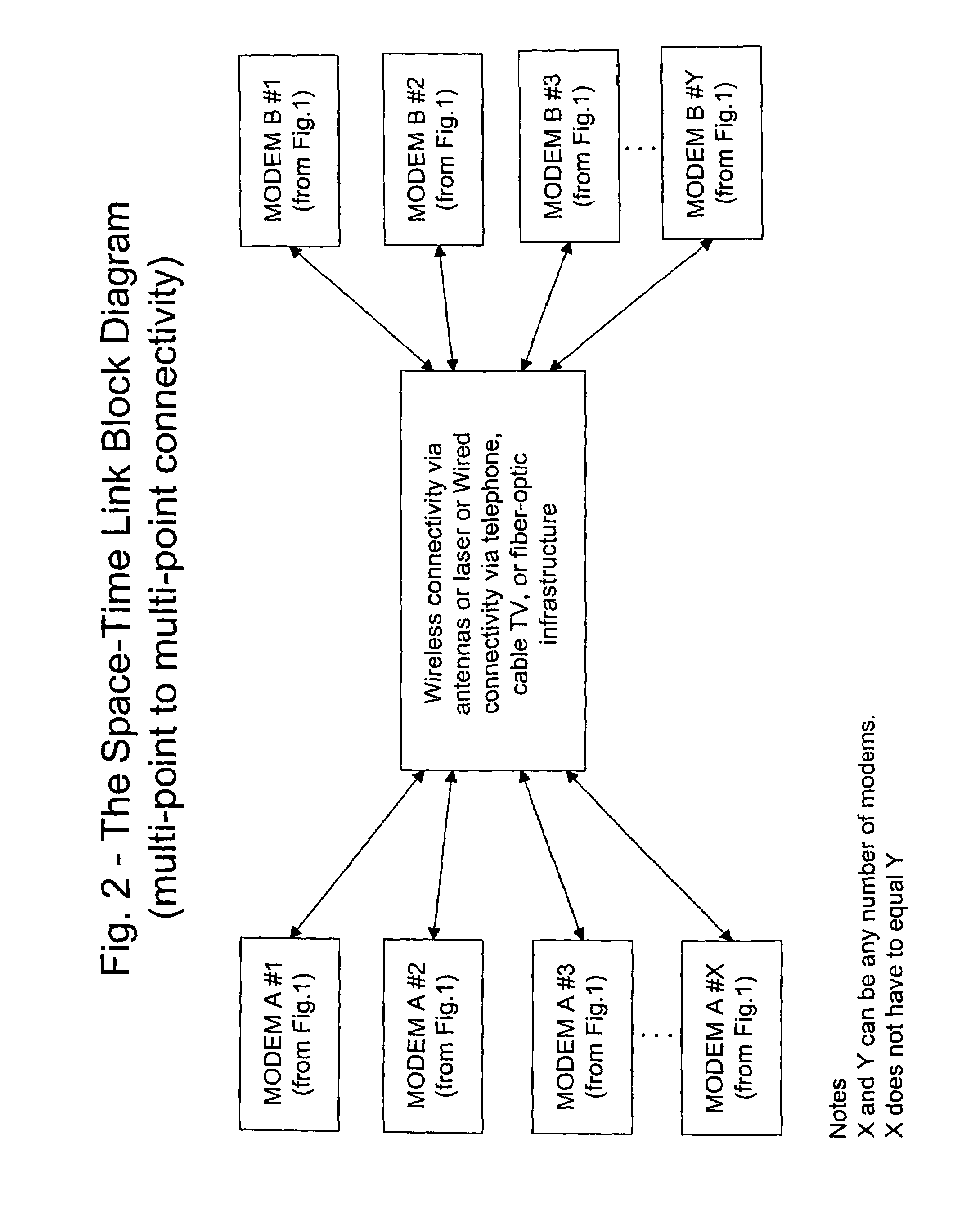
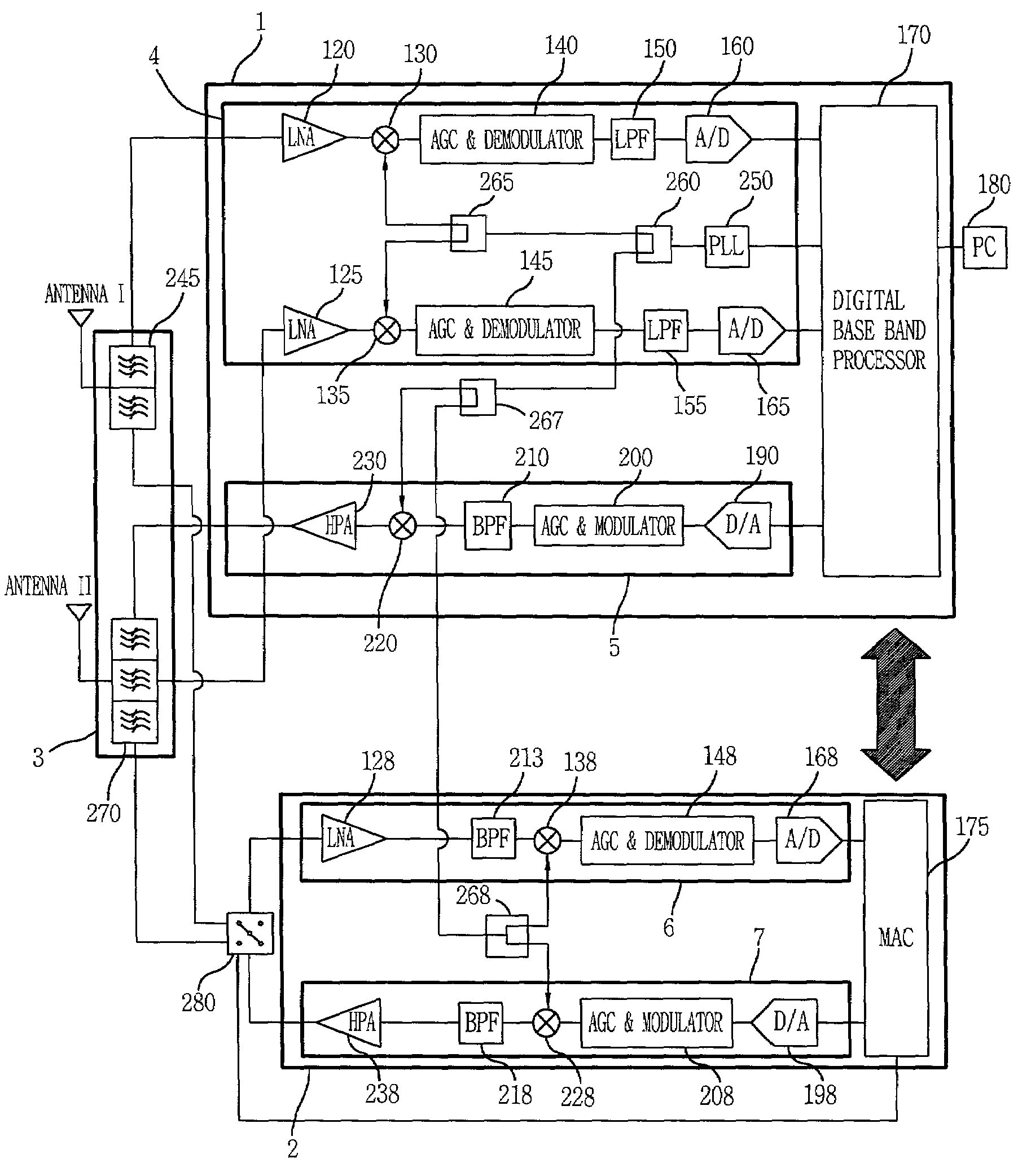
Providing a high speed data modem based on MIMO technology using a cable or single antenna
InactiveUS7346040B2High speed data transfer rateImprove data transfer rateBroadcast transmission systemsDiversity/multi-antenna systemsModem deviceTransceiver
A single cable or single antenna space-time fast modem system is described. Very high data transfer rates are accomplished using a space-time MIMO transceiver in combination with a unique space-time antenna reduction chamber and a frequency spectrum shifting module. The system readily connects to any existing communications infrastructure. The high speed data modem system incorporates a MIMO space-time wireless transceiver, yet unlike existing space-time wireless systems, requires only a single cable or antenna to achieve very high data transfer rates. Furthermore, this fast modem system achieves these very rapid data transfer rates, those comparable to a MIMO space-time wireless data link over existing wired or wireless infrastructure while operating at any carrier frequency, including base band, maintains data transfer rates during high speed motion, maintains a predictable separation factor “k” regardless of topographical limitations, is small in size, with no need for numerous cables or antennas, and can be produced at low cost. It is also possible, that the fast modem system described herein can be used with, or connected to any pre-existing communications means (e.g., LAN, WAN, Internet, dedicated lines, etc.) to provide very high speed data transfer rates.
Owner:AVALON RF
Integrated wireless local loop (WLL) and wireless local area network (WLAN) transceiver apparatus
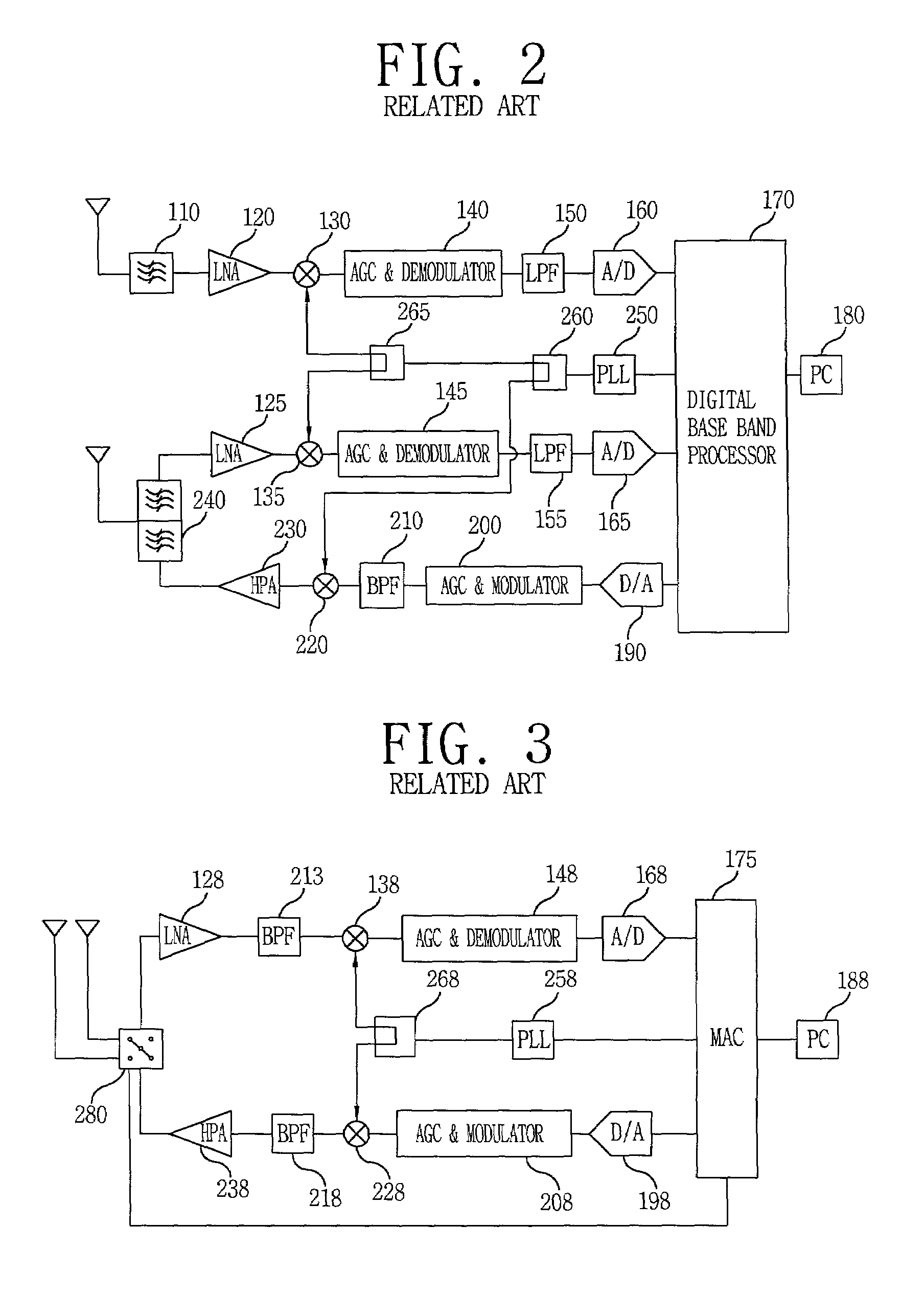
Disclosed is a integrated wireless local loop (WLL) and wireless local area network (WLAN) transceiver apparatus which connects a wireless local loop (WLL) base station and a plurality of wireless local area network (WLAN) terminals, including a WLL transceiver in communication with a WLL base station, a WLAN transceiver in communication with a plurality of WLAN terminals, and a specialized processing device which translates communications between WLL signaling protocol and WLAN signaling protocol. The apparatus allows a plurality of wireless terminals to simultaneously access the Internet without using a dedicated line or a cable line.
Owner:LG ERICSSON
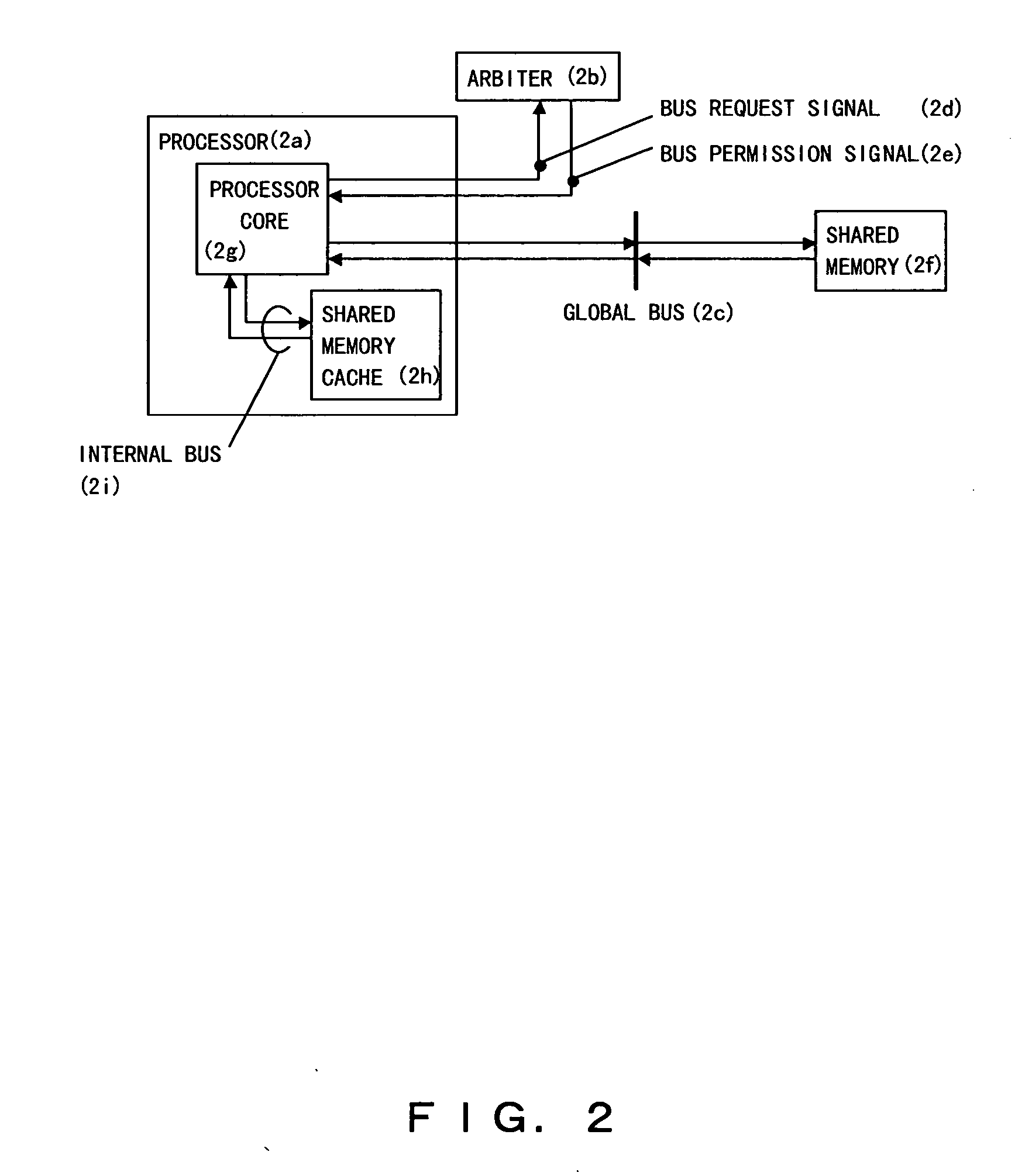
Multi-processor system
InactiveUS20060075197A1Lower performance requirementsHigh bandwidthMemory adressing/allocation/relocationMulti processorDedicated line
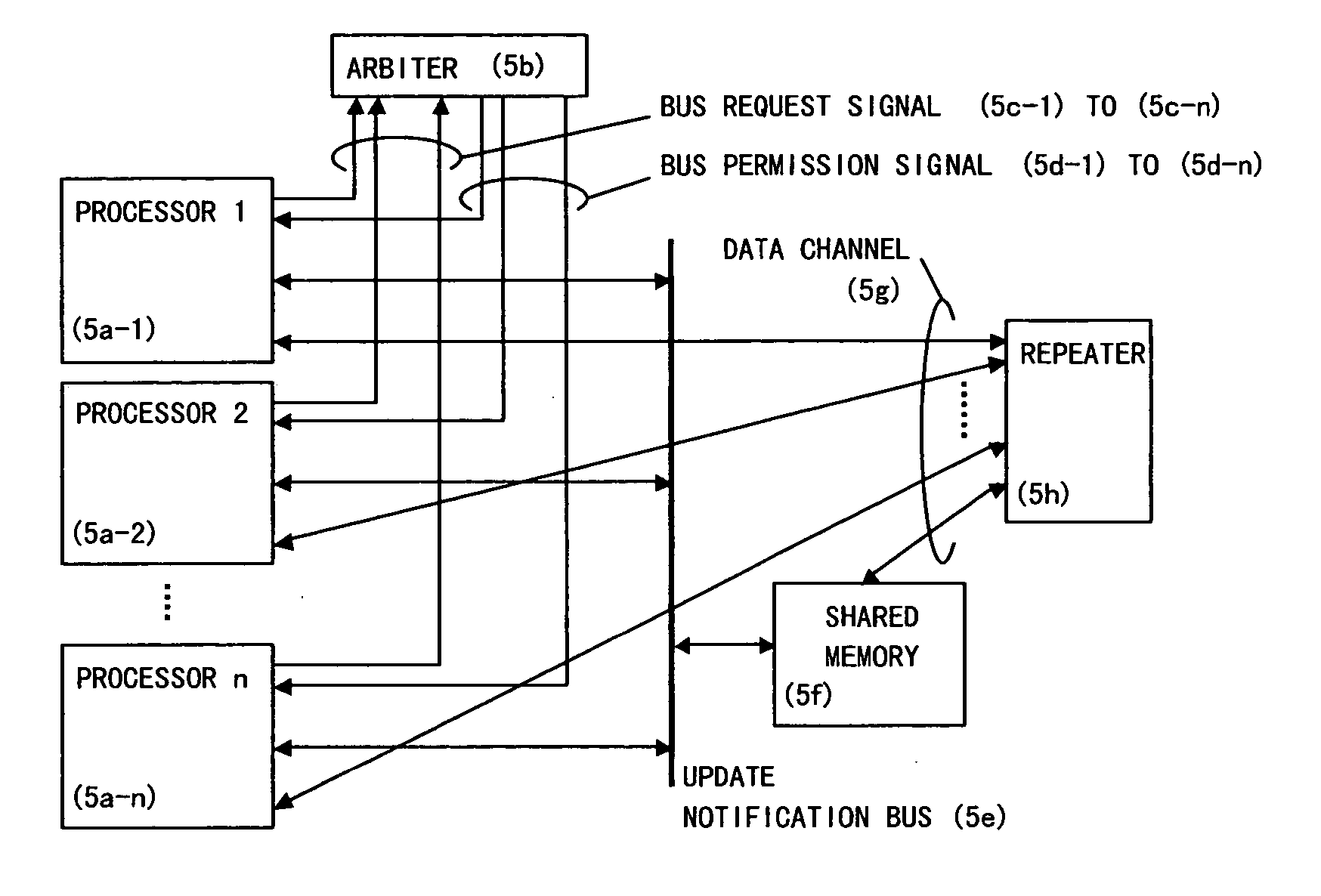
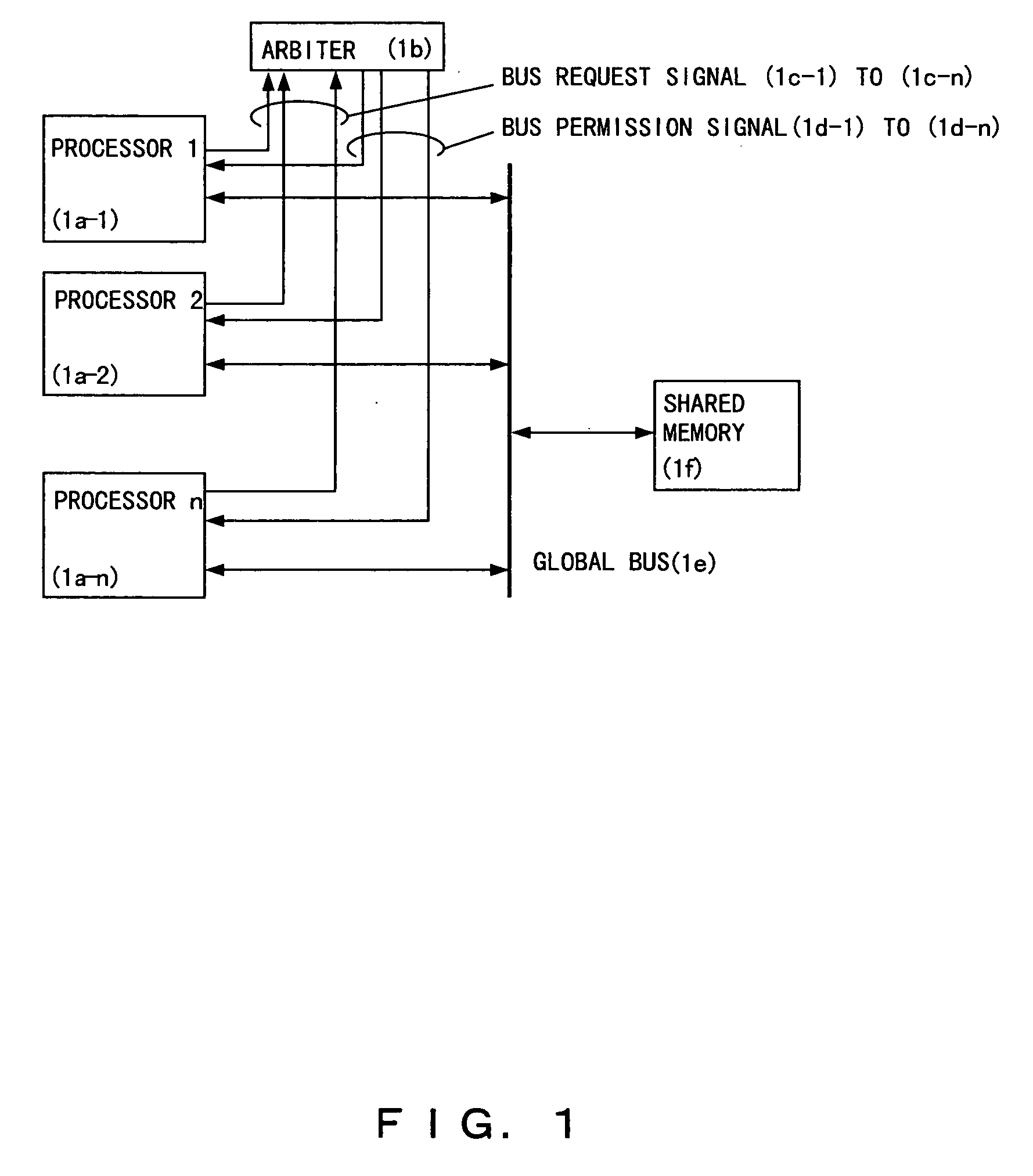
Data transmission for writing data into a shared memory is performed by a high-speed dedicated line provided between each processor and the shared memory. When a processor performs writing to a shared memory space, the processor notifies an update notification bus corresponding to the conventional global bus, to which address the update is to be performed. The other processors which have detected this notification inhibit access to that address and wait for the write data to be sent to the address via the dedicated line. When the data has arrived, the data is written into the corresponding address. Here, the data is also written into the corresponding address, thereby maintaining the cache coherency. Moreover, when transmitting a write address, it is necessary to acquire the bus use right while data transmission is performed by using the dedicated line, which significantly reduces the time required for acquiring the bus use right.
Owner:FUJITSU LTD
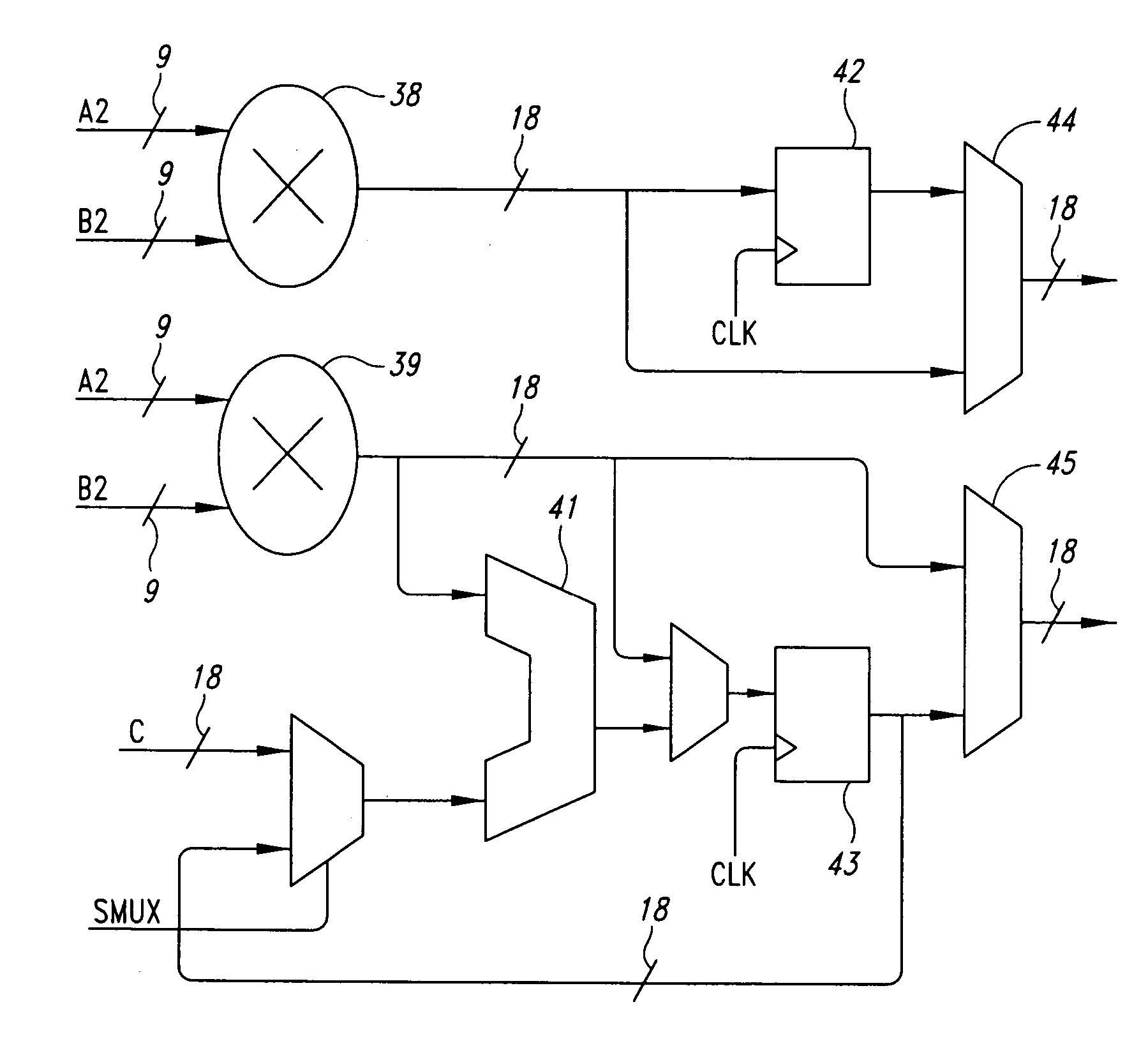
Efficient implementation of DSP functions in a field programmable gate array
ActiveUS20060075012A1Efficient cascadingLarge sectionDigital computer detailsComputation using denominational number representationMultiplexerParallel computing
An efficient implementation of DSP functions in a field programmable gate array (FPGA) using one or more computational blocks, each block having of a multiplier, an accumulator, and multiplexers. The structure implements most common DSP equations in a fast and a highly compact manner. A novel method for cascading these blocks with the help of dedicated DSP lines is provided, which leads to a very simple and proficient implementation of n-stage MAC operations.
Owner:MINERAL LASSEN
Method and system for communicating and isolating packetized data through a plurality of last-mile carriers to form a multi-node intranet
InactiveUS20060203820A1Reduce needEliminate needData switching by path configurationNetwork connectionsPrivate networkCarrier signal
The invention provides a system and method for transporting packetized data between remote geographic locations in a multi facilities-based carrier and multi-last mile access environment to form a multi-node intranet. The purpose of the invention is to implement a secure, private data service using disparate facilities-based carriers for last-mile connectivity to achieve cost reduction compared to single-carrier, private line or switched or routed private solutions. This is done by providing a system for increased data latency predictability, increased average data latency reduction, and end-to-end data prioritization compared to virtual private networking services utilizing tunneling protocols or public infrastructures for data switching or routing.
Owner:COLUCCIO MARC
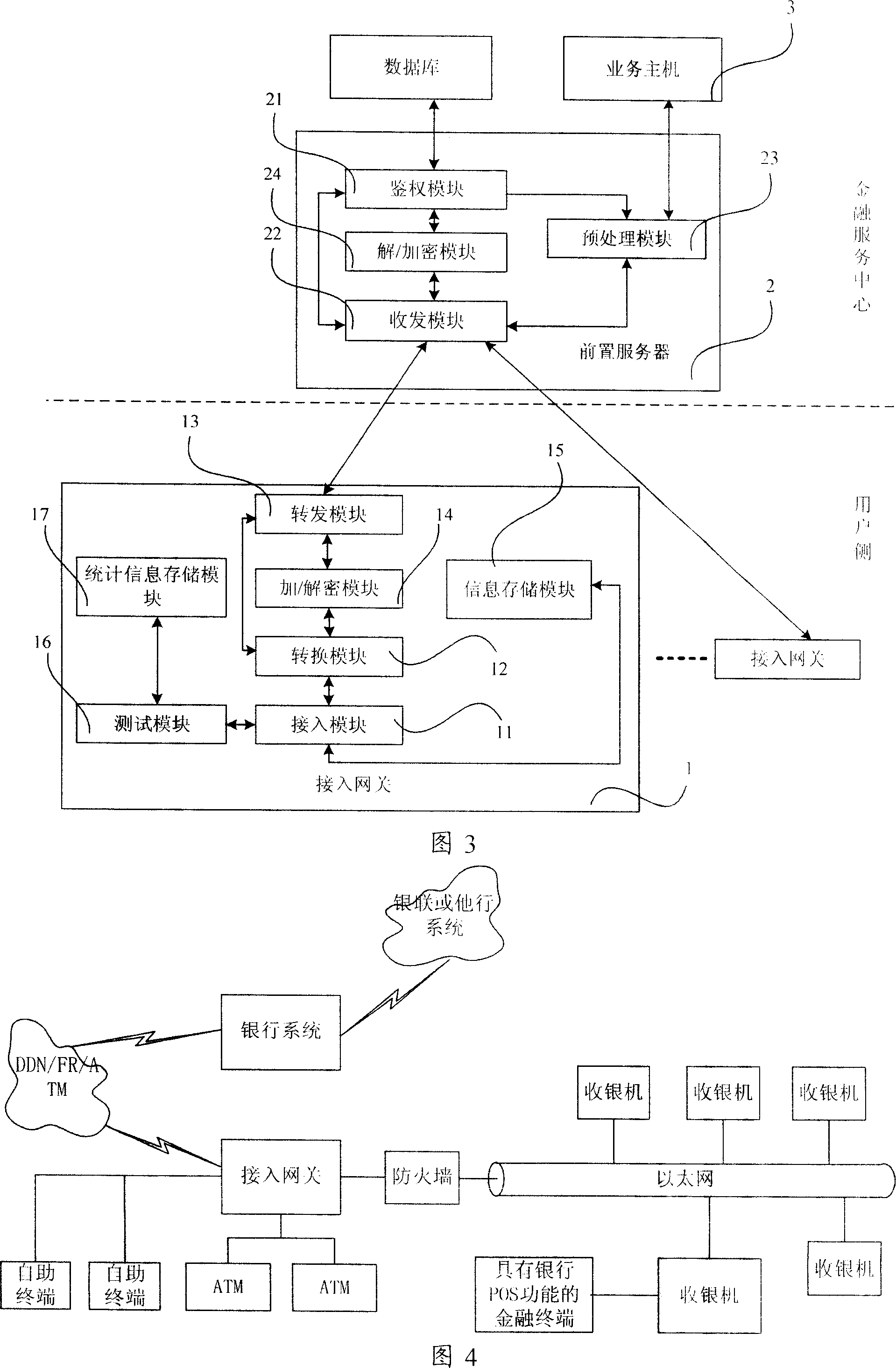
Finance business system and finance business processing method
InactiveCN101018130ALow costLower service costsComplete banking machinesFinanceProcess moduleNetwork structure
The disclosed financial business system comprises: a business host in service center, a front server with connected authorization module and transmitting-receiving module connected with a pre-process module, and a terminal access gateway including an access module and a conversion module and transmission module connected with a protocol conversion module. This invention reduces both service and hardware cost, and simplifies network structure.
Owner:WUFANG HENGDE BEIJING INVESTMENT CONSULTATION
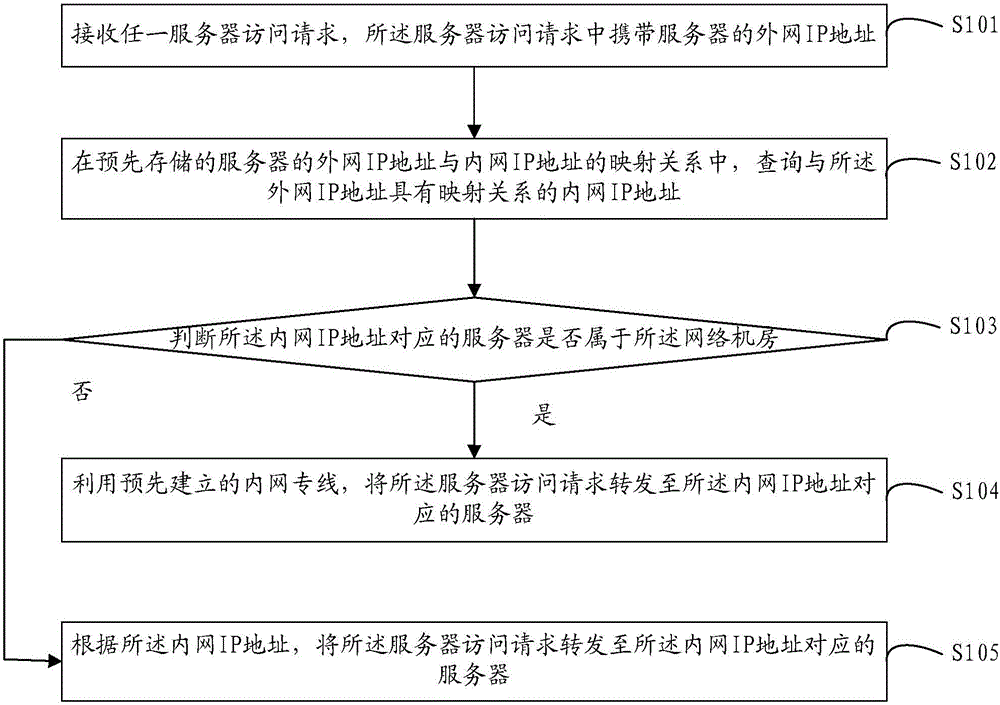
Inter-network communication method and device and load balancer
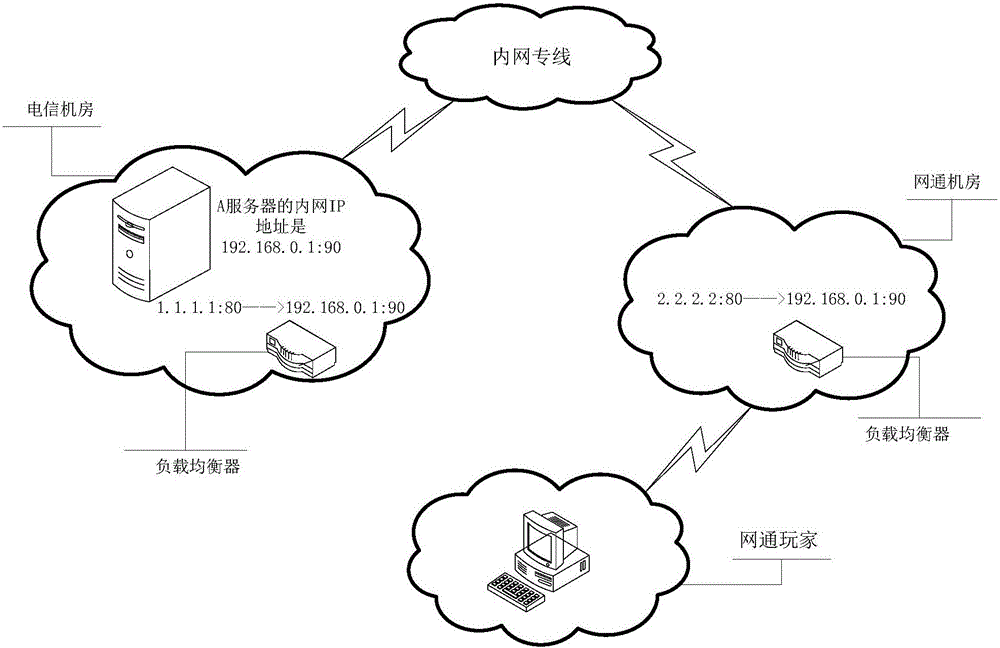
The present invention discloses an inter-network communication method and device and a load balancer. The inter-network communication method and device and the load balancer are applied to any one network machine room. The method comprises: receiving any one server access request, wherein the server access request carries the external network IP address of a server; inquiring an internal network IP address having a mapping relation with the external network IP address in the pre-stored mapping relation of the external IP address and the internal IP of the server; and if the server corresponding to the internal network IP address does not belong to the network machine room, employing an internal network private line built in advance, and forwarding the server access request to the server corresponding to the internal network IP address. The inter-network communication method and device and the load balancer can provide stability guarantee for an inter-network communication function with no need for employing a third-party proxy server. The inter-network communication method and device and the load balancer can realize inter-network communication through adoption of the internal network private line between the network machine rooms of each network supplier, and can solve the safety problem of the inter-network communication based on the safety of the internal network private line.
Owner:BEIJING AMAZGAME AGE INTERNET TECH CO LTD
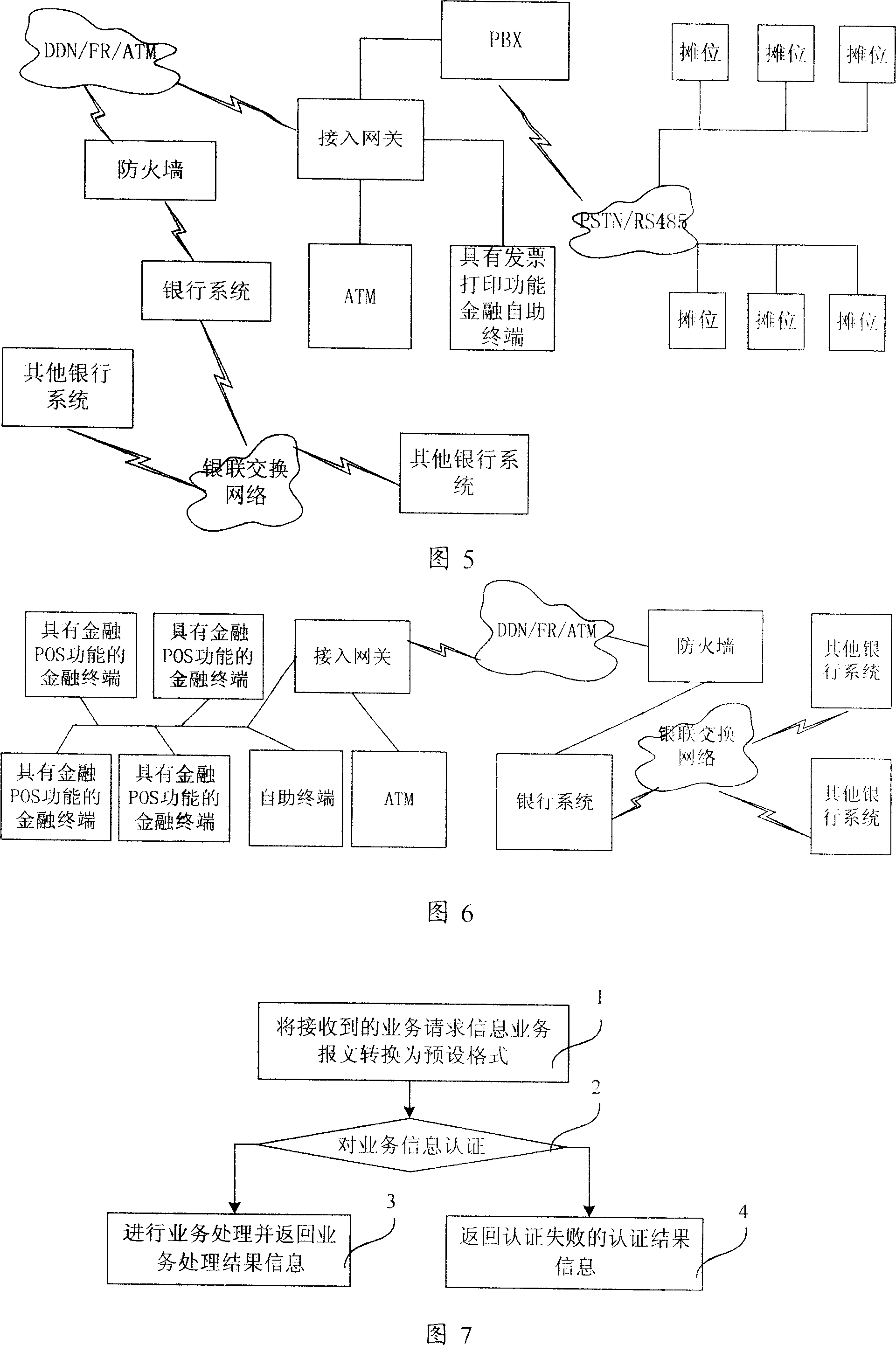
Method for access network to realize synthesis business access
InactiveCN101232460AImprove bandwidth utilizationIncrease incomeMultiplex system selection arrangementsNetworks interconnectionAccess networkLeased line
The invention relates to a broadband access network method for accessing integrated services. The invention includes the following steps: firstly, establishing at least one label switching path (LSP) in broadband access network based on multi-protocol label switching (MPLS); then, MPLS encapsulates the service to be transferred in the broadband access node equipment and transfer in the broadband access network through the LSP. As MPLS is a technology of providing a multi-level connection, the method, which takes MPLS as a private line means for broadband access network networking and traversing core network, can solve the problem faced by broadband access network as integrated services bearer network, thus realizing the bearing of integrated services like IP video, voice, data and private lines (including IP leased line and ATM private line of traditional asynchronous transmission mode, TDM private line and FR private line ).
Owner:HUAWEI TECH CO LTD
User private line communication method and equipment used in VPLS (Virtual Private LAN (Local Area Network) Service) network
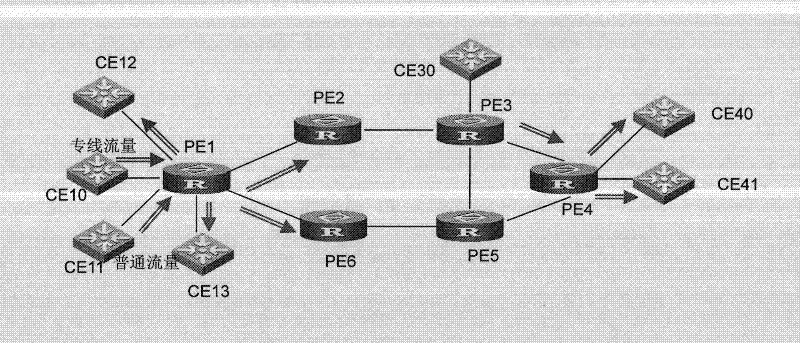
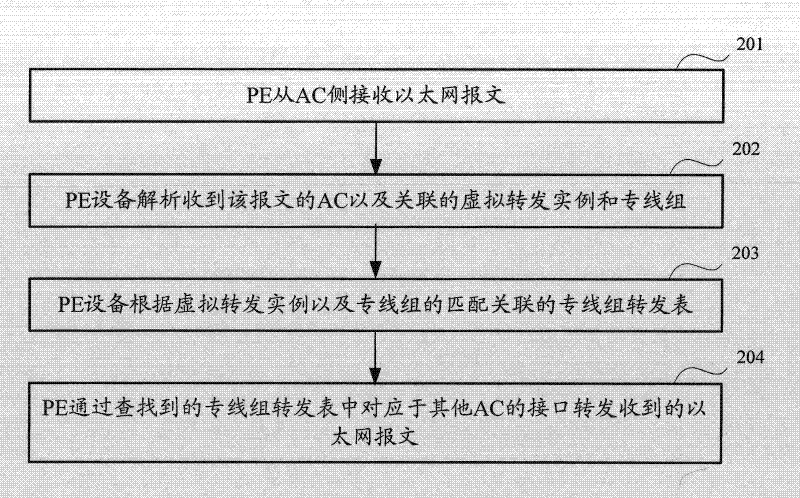
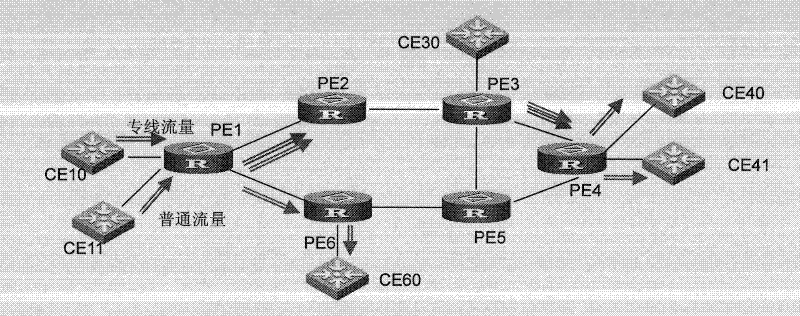
ActiveCN102413060APoint-to-point communication implementationData switching networksService provisionEthernet
The invention discloses a user private line communication method and equipment used in a VPLS (Virtual Private LAN (Local Area Network) Service) network, and the method equipment disclosed by the invention are applied to a service provider edge (PE). The method comprises: creating a virtual forwarding instance and setting access circuits (ACs) and opposite-end equipment which belong to the virtual forwarding instance by the service PE; configuring at least two ACs in the virtual forwarding instance into a private line group, and generating a private line group forwarding table associated with the virtual forwarding instance and the private line group, wherein the private line group forwarding table comprises an interface corresponding to each AC in the private line group; receiving an Ethernet message; analyzing the AC by use of the input interface for the Ethernet message and the associated virtual forwarding instance so as to determine the private line group to which the AC belongs; searching the associated private line group forwarding table according to the virtual forwarding instance and the private line group to which the AC belongs; and forwarding the Ethernet message through the interfaces corresponding to the other ACs in the searched private line group forwarding table. By adopting the user private line communication method and equipment disclosed by the invention, point-to-point user private line communication can be realized in the VPLS network.
Owner:XINHUASAN INFORMATION TECH CO LTD
Network system and network apparatus
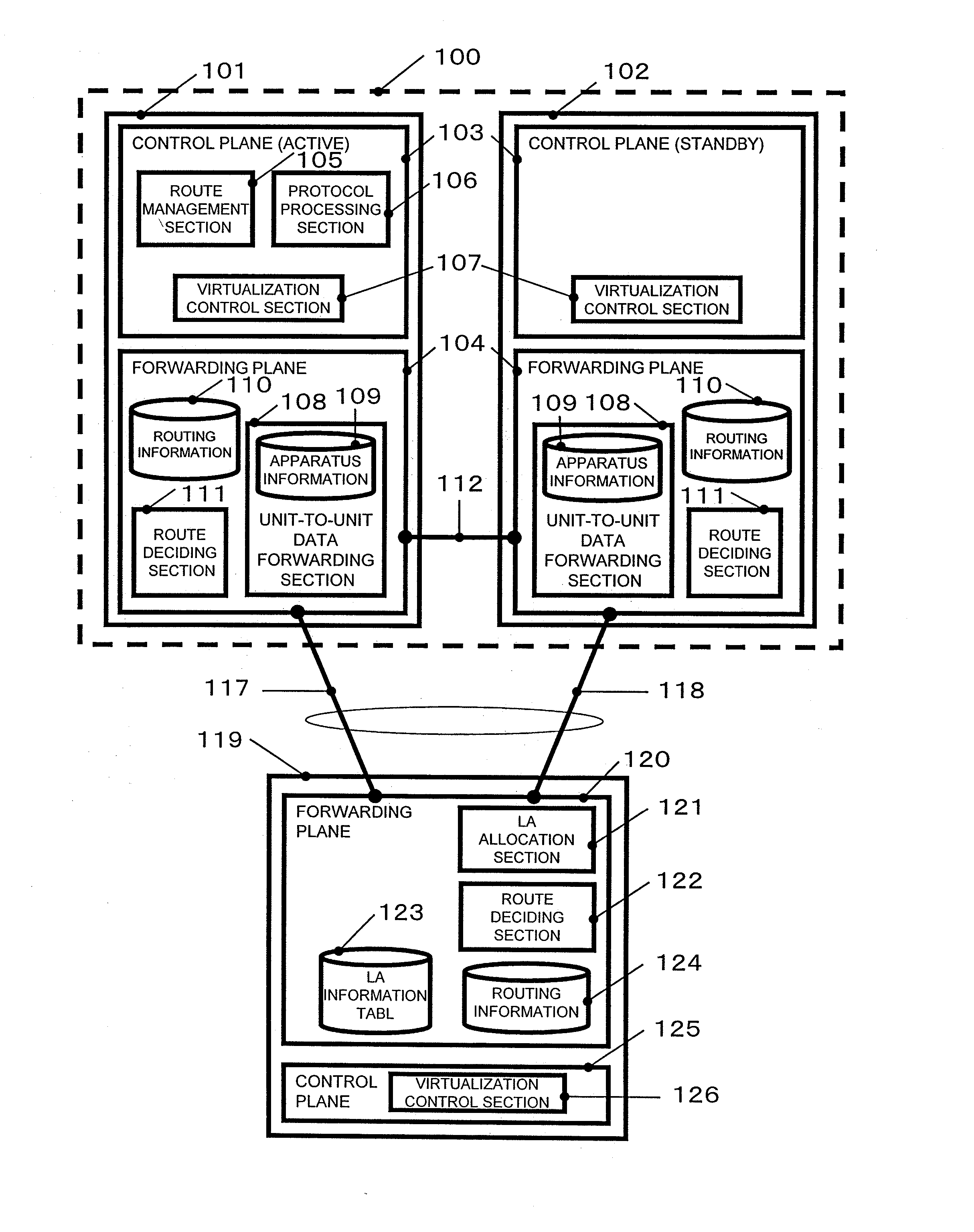
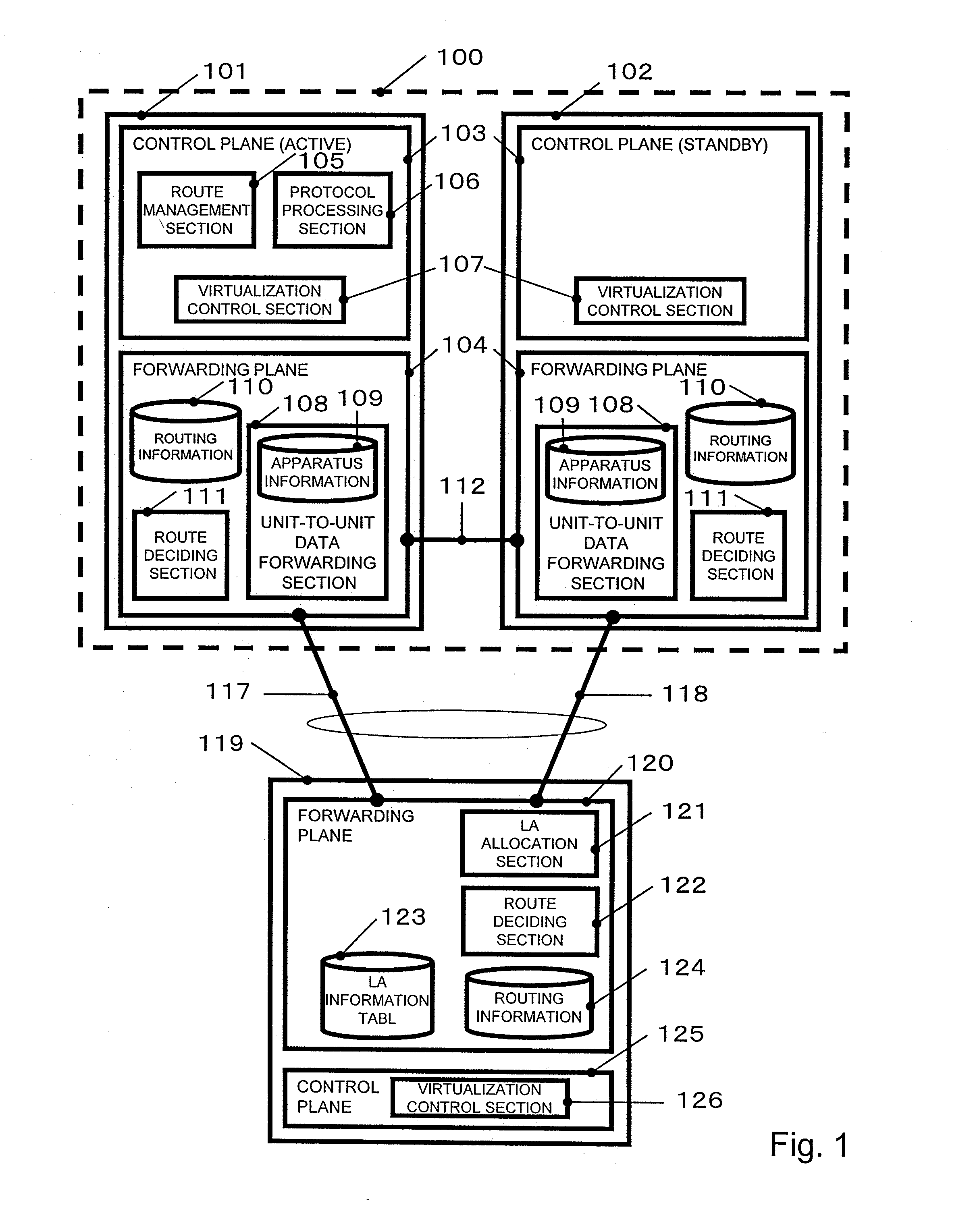
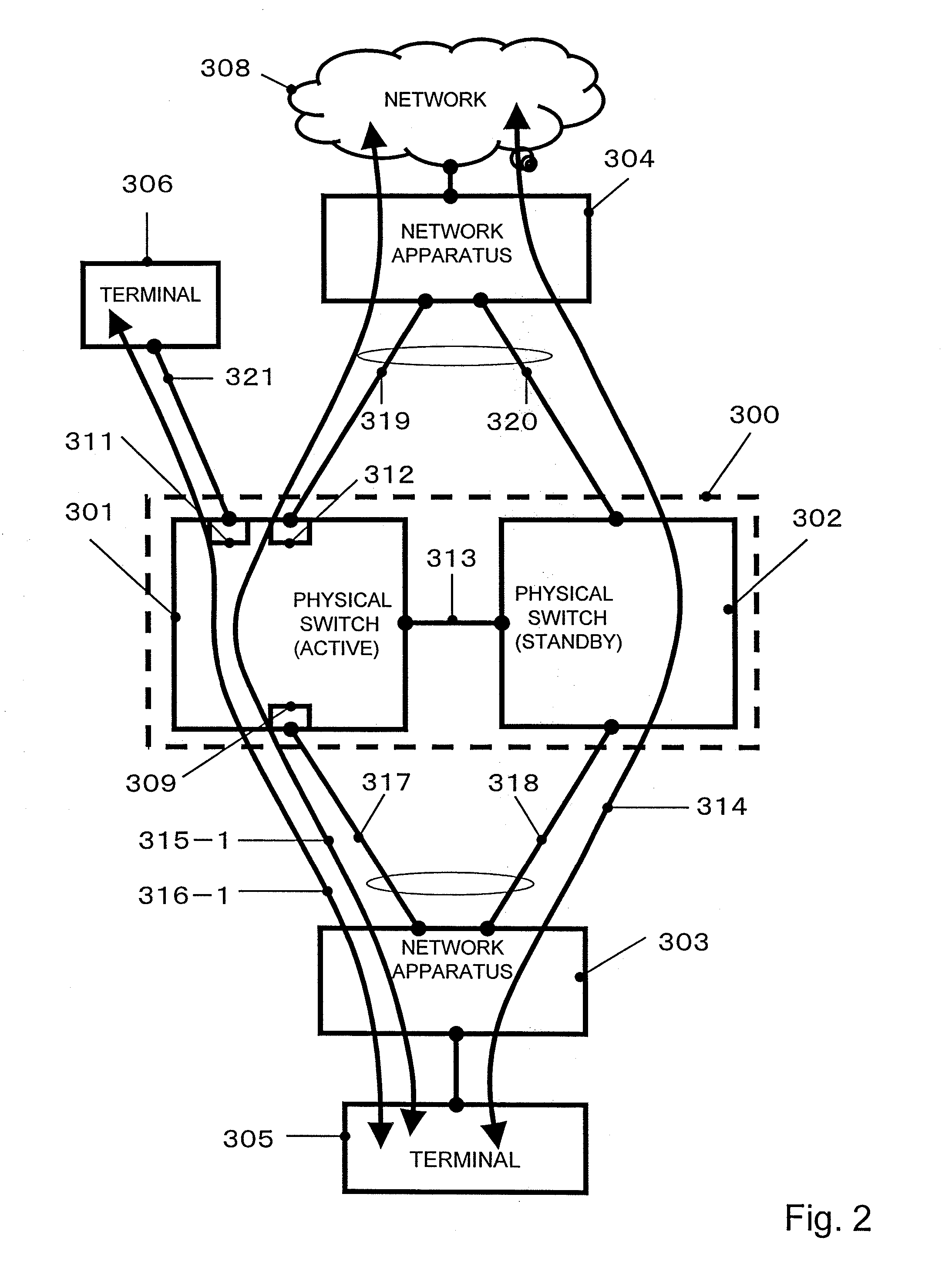
InactiveUS20110292931A1Forwarding capability can be improvedLower capability requirementsNetwork connectionsVirtualizationControl signal
In a virtual network apparatus, even when a fault occurs on a private line connecting plural physical network apparatuses to communicate a control signal, the redundancy is maintained, and the lower forwarding capability is prevented. In this network system, a control signal for virtualization to be transmitted and received between plural physical network apparatuses is relayed via a unit spanning LA connecting each physical network apparatus and an adjacent network apparatus in the adjacent network apparatus. Thereby, even when a fault occurs in the private line, it is possible to continue to communicate the control signal between the physical network apparatuses and continuously operate the virtual network apparatus.
Owner:ALAXALA NETWORKS
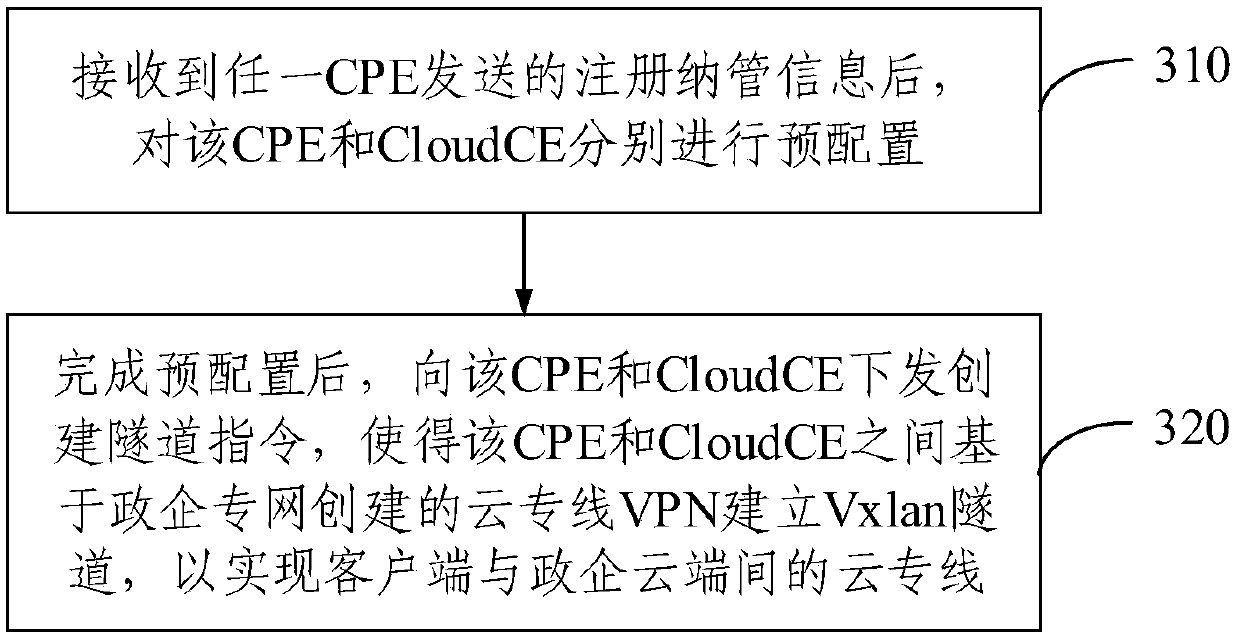
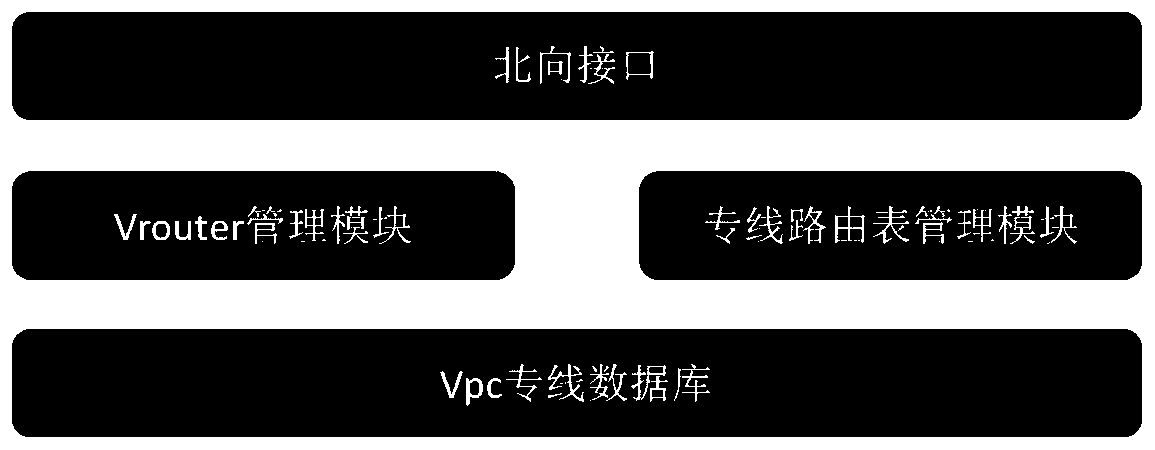
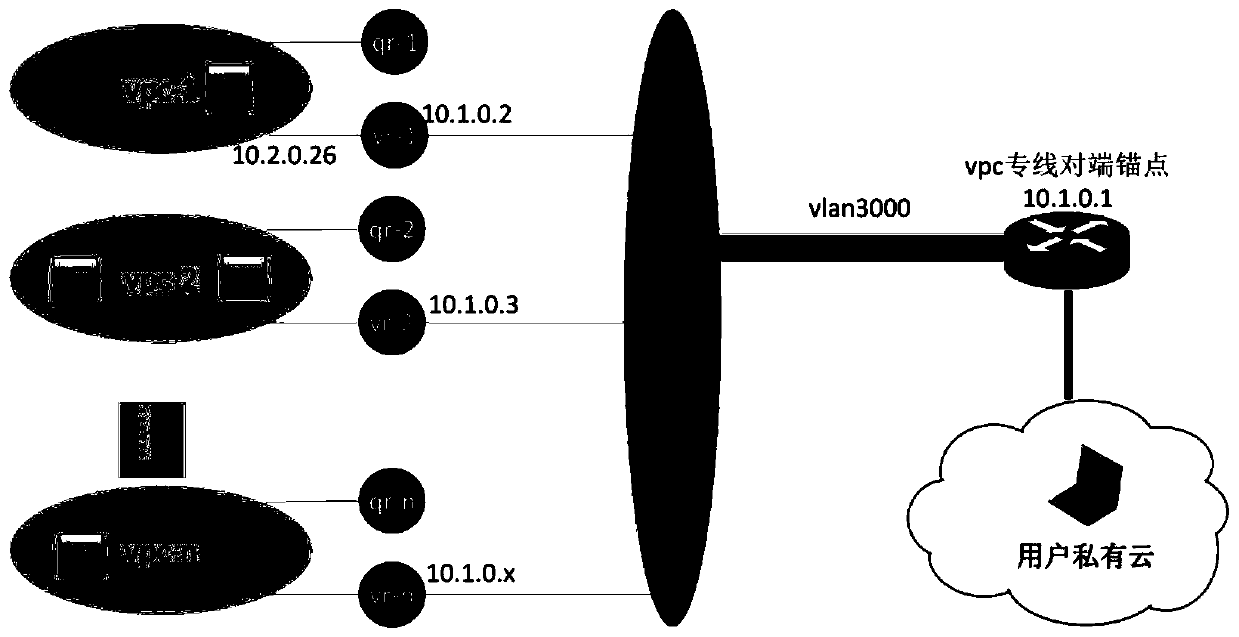
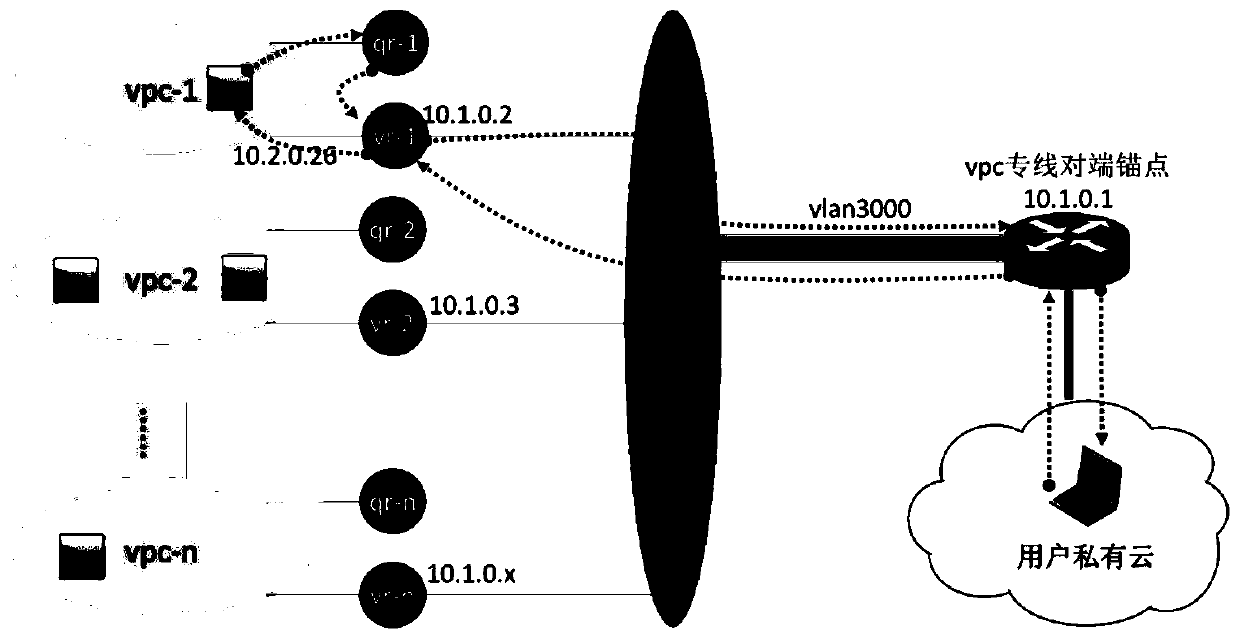
Cloud private line system and service issuing and opening method thereof
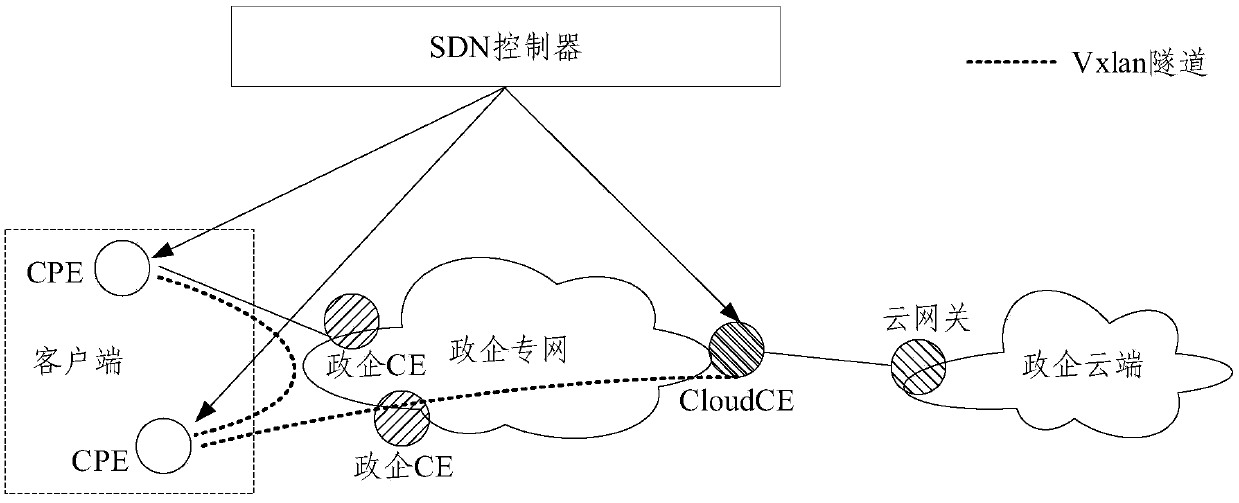
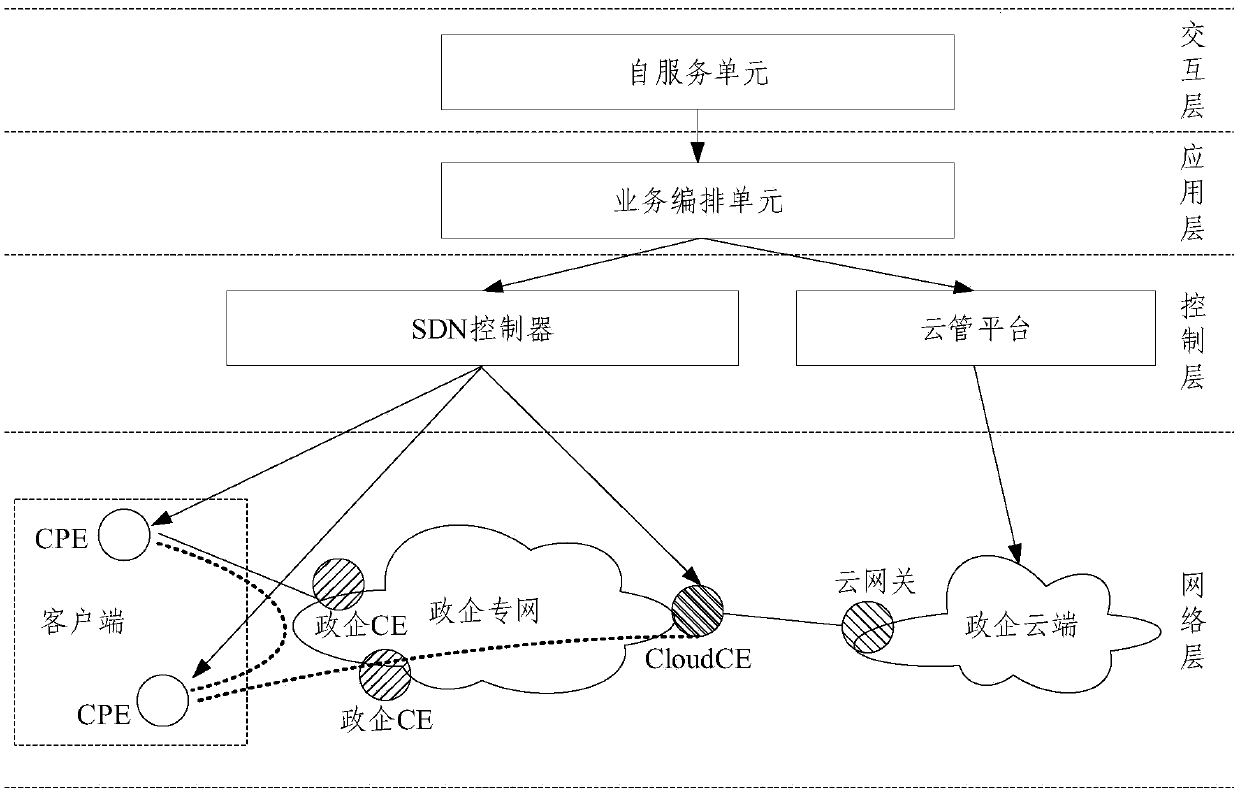
ActiveCN111106991AEnable secure accessSimplify the architecture processNetworks interconnectionCloud userTerminal equipment
The embodiment of the invention provides a cloud private line system and a service issuing and opening method thereof. The cloud private line system comprises a client, a government and enterprise private network, a government and enterprise cloud and an SDN controller. The client is deployed with a plurality of customer premise equipment CPE, the government enterprise private network is deployedwith a plurality of government enterprise CEs and a cloud user edge router Cloud CE, and the government enterprise cloud is deployed with a cloud gateway; the CPE is in butt joint with the governmentand enterprise CE, and the Cloud CE is in butt joint with the cloud gateway; and the SDN controller is used for controlling the client and the government and enterprise private network and establishing a Vxlan tunnel taking the CPE and the Cloud CE as end points so as to realize a cloud private line between the client and the government and enterprise cloud. According to the system and the methodprovided by the embodiment of the invention, safe access between the cloud on the local site and the sites is realized, the configuration process is simplified, the cost and equipment resources are saved, the problem of complex opening configuration is solved, and the opening process is simplified.
Owner:CHINA MOBILE GROUP ZHEJIANG
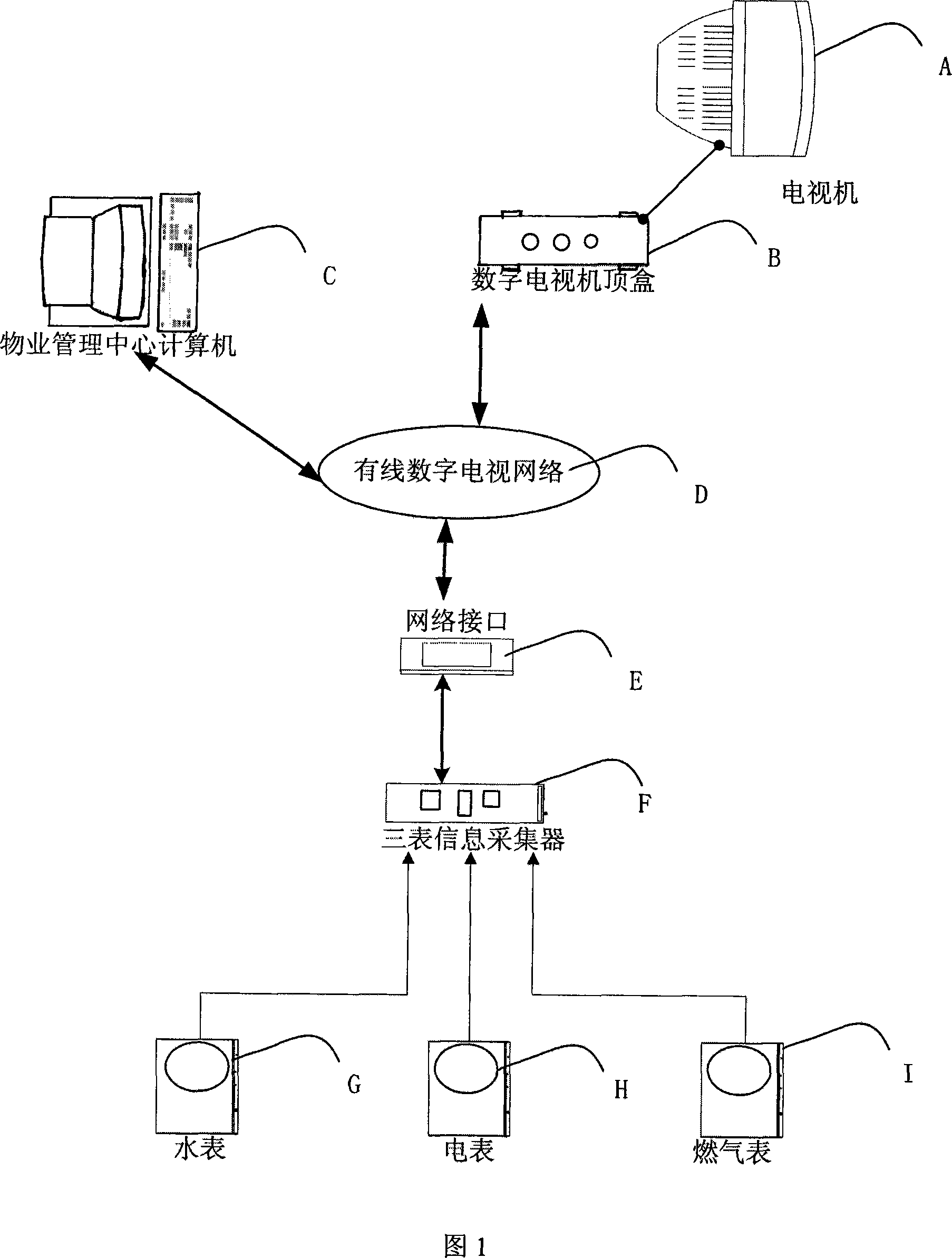
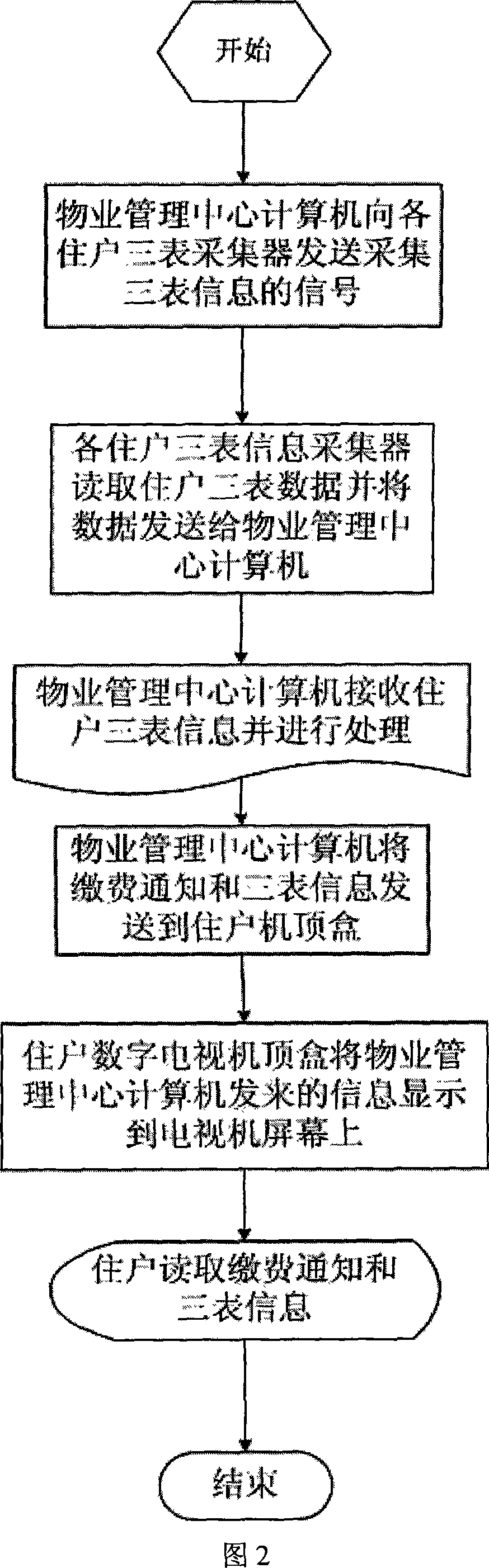
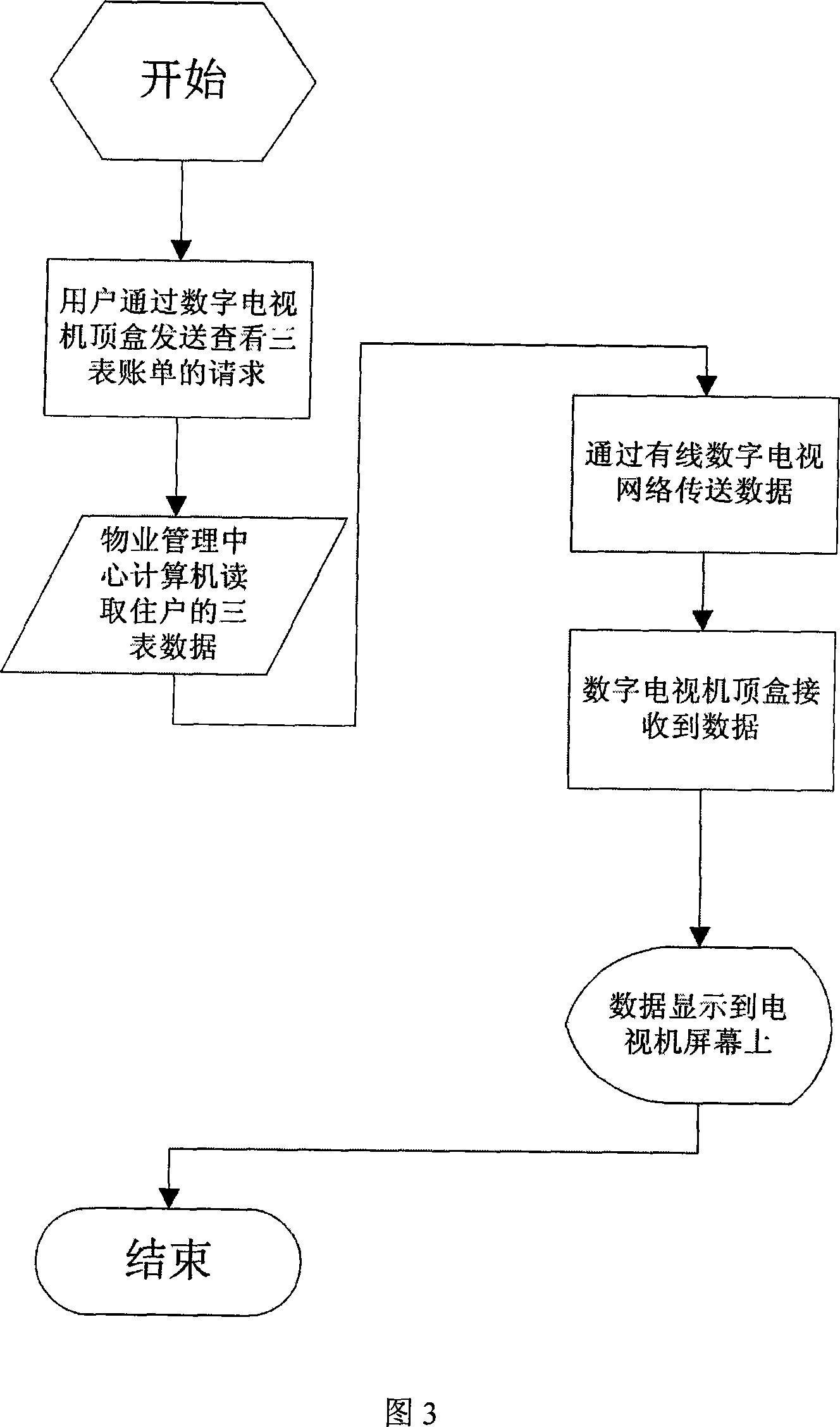
Water-electricity-gas three-meter remote intelligent centralized meter reading system based on digital TV set-top box
InactiveCN101246638ASimple structureEasy to installTelevision system detailsElectric signal transmission systemsElectricityLogistics management
The present invention provides a water-electricity-gas meter remote intelligent integrated meter reading system based on the digital television set top box, including: a three meters information search display subsystem for searching and output the searched three meters information, achieving by the set top box and the television of each user; a three meters information storage processing subsystem, for storage and processing three meters information of each user, achieving by the logistics management center computer; a three meters information collecting subsystem, for collecting the three meters information of each user, achieving by the three meters information collector of each user. The invention achieves the interactive communication based on the communication centrum of the Cable DTV web by the logistics management center computer, the three meters information collector and the Cable DTV web. The present Cable DTV web having high quality substitutes for the traditional complex bus or private line to achieve signal communication, this makes the system have simple structure, convenient for install and implement, reducing the fault latency at the same time, enhancing the credibility of system.
Owner:罗笑南
A hybrid cloud network interconnection method and system
ActiveCN109936629AGuaranteed reliabilityEnsure safetyNetworks interconnectionRouting tableNetwork on
The invention particularly relates to a hybrid cloud network interconnection method and system. The hybrid cloud network interconnection method comprises the following steps: firstly, purchasing a physical private line from an operator for hybrid cloud interconnection, and planning a vlan number of a private line internet; transmitting the private line vlan to a service network of the Openstack through an L2 link layer; creating a provider network of an Openstack, creating a special line forwarding router vrouter on the provider network, and adding a network card on the special line forwardingrouter vrouter; Special line interconnection routing entries reaching the opposite end of the hybrid cloud are added to a routing table query and a special line forwarding router query of the publiccloud VPC; and adding a special line interconnection routing entry reaching the home terminal at a special line Internet exit of the hybrid cloud opposite terminal and announcing the special line interconnection routing entry through an IGP. According to the hybrid cloud network interconnection method and system, a special line VPC interconnection mode is adopted, the safety of physical isolationis high, the reliability and safety of hybrid cloud interconnection are guaranteed, and the method and system can be used for special line interconnection of public cloud and private cloud, private cloud and private cloud, public cloud and public cloud and other scenes.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
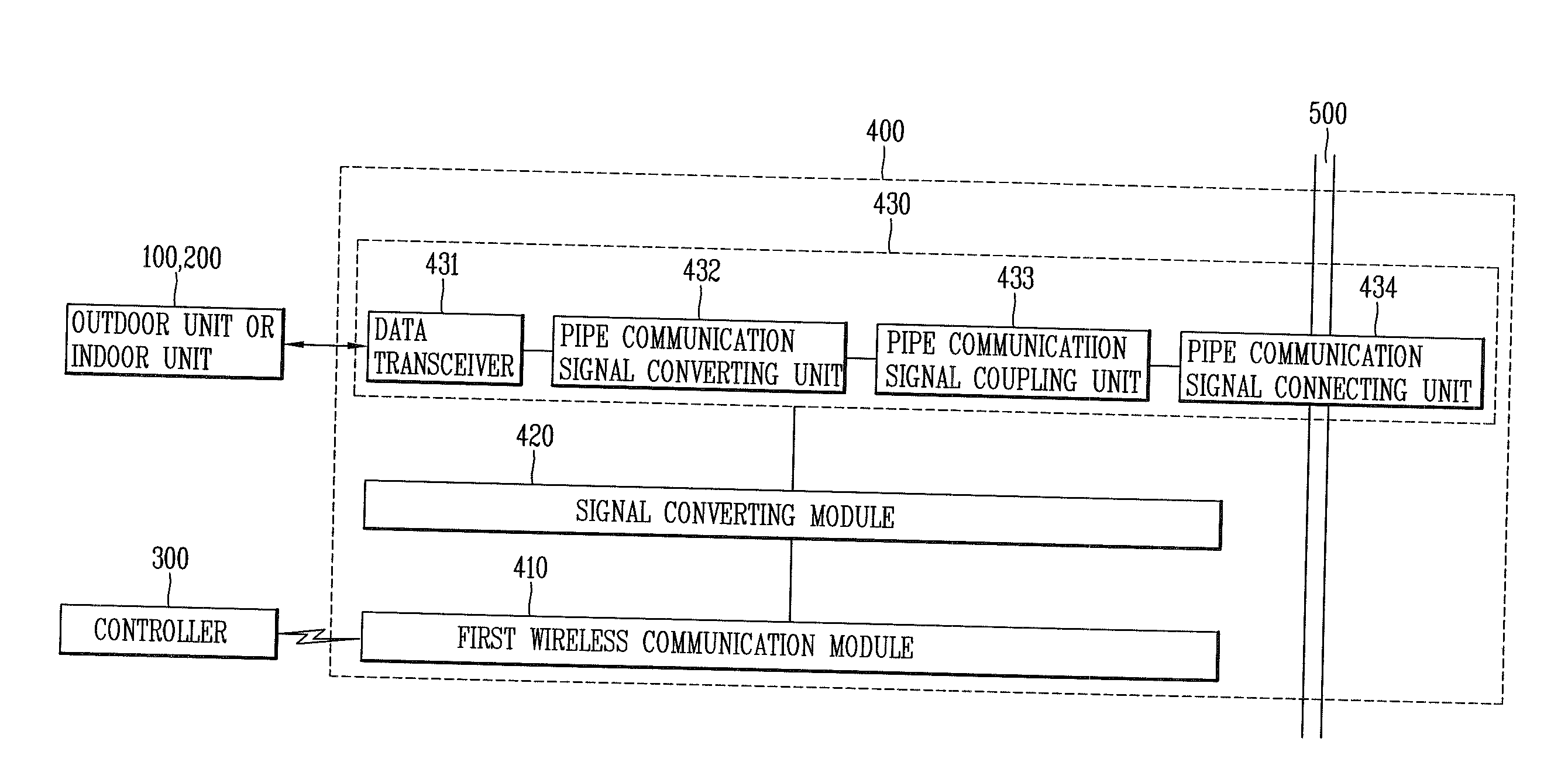
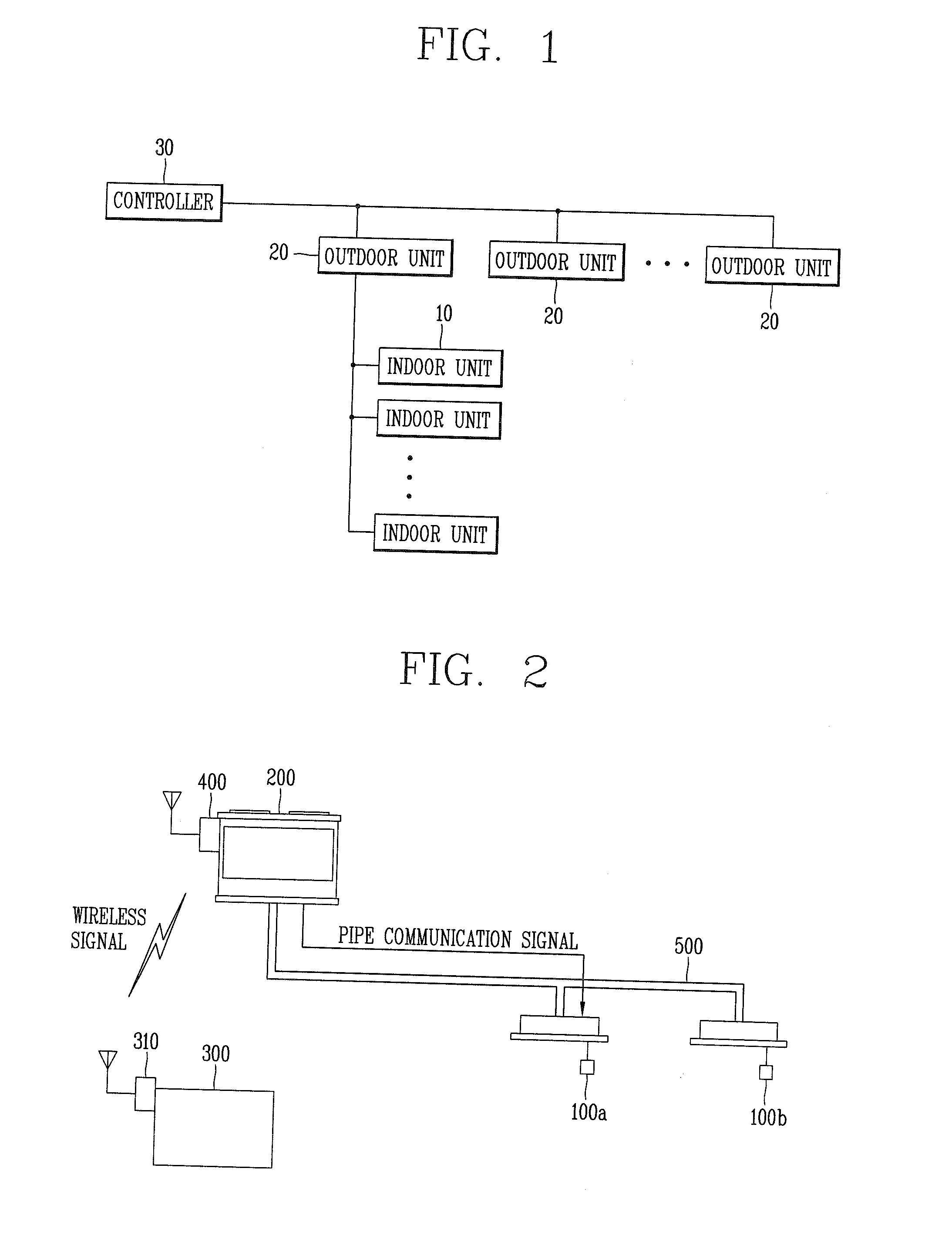
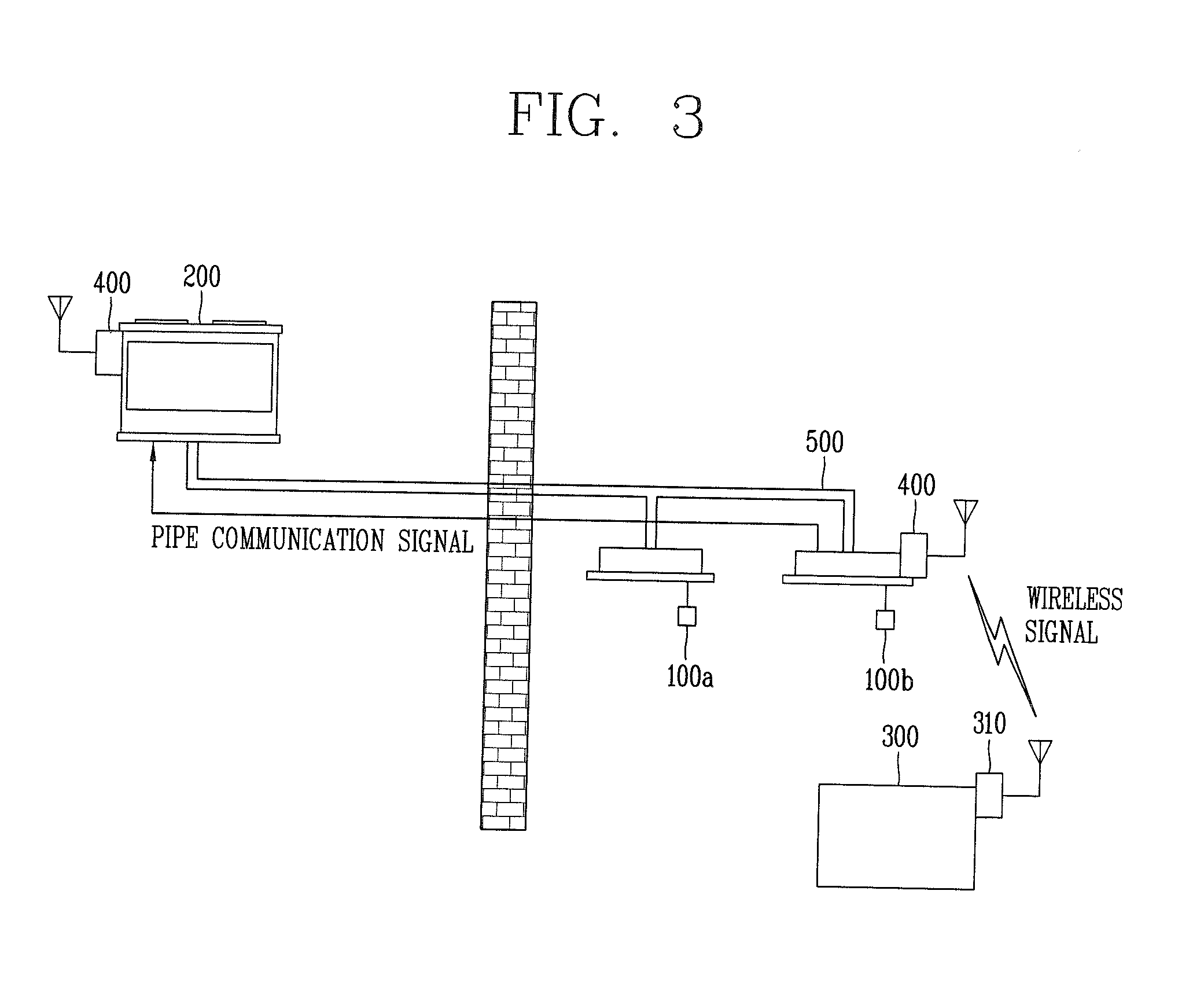
Air Conditioning System And Communication Method Thereof
ActiveUS20110224833A1Reduce installation costsReduce maintenance costsSampled-variable control systemsMechanical apparatusDedicated lineAir conditioning
In an air conditioning system and a communication method thereof a wireless network may be established between indoor units and a controller or between outdoor units so as to allow communications therebetween, thereby facilitating device addition or device deletion. Also, one or more outdoor units and a plurality of indoor units may be controlled without a dedicated communication line or with using a less mount of the dedicated communication line, and the outdoor units or indoor units may perform communications using one or more communication technologies, such as wireless communication and pipe communication technologies and wireless communication and dedicated line communication technologies, while performing communications with the controller using the wireless communication technology.
Owner:LG ELECTRONICS INC
Integrated information communication system
InactiveUS20030118034A1Interconnection arrangementsMetering/charging/biilling arrangementsCommunications systemCommunication quality
To provide an integrated information communication system without using dedicated lines or the Internet, ensuring communication speed, communication quality, communication trouble countermeasures in a unified manner, wherein security and reliability in communication is ensured. The system is comprised of an access control apparatus for connecting a plurality of computer communication networks or information communication equipment to each, and a relay device for networking the aforementioned access control apparatus, the system having functions for performing routing by transferring information by a unified address system, and is configured such that the aforementioned plurality of computer communication networks or information communication equipment can perform communications in an interactive manner.
Owner:THE DISTRIBUTION SYST RES INST
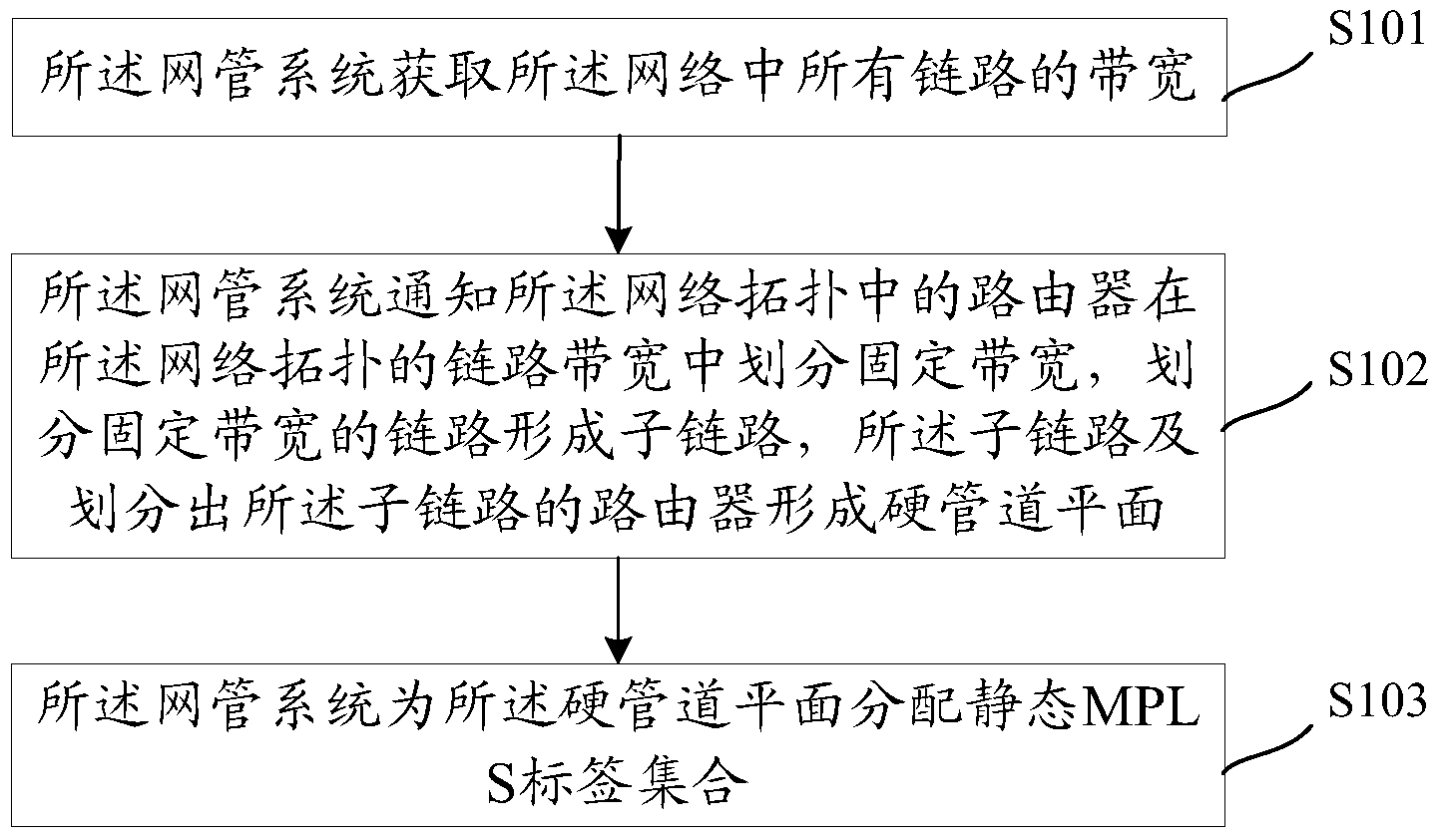
Method for establishing hard pipe as well as method and device for transmitting messages in network
The invention discloses a method for establishing hard pipe as well as a method and a device for transmitting messages in a network. The network comprises a plurality of routers and an NMS (network management system). The method comprises the following steps: the NMS acquires the bandwidths of all links in the network; the NMS informs the routers in a network topology of dividing fixed bandwidths in the link bandwidth of the network topology, a sublink is formed by the link for dividing into the fixed bandwidths, and a hard pipeline plane used for bearing a private line service is formed by the sublink and the routers which divide the sublinks; a static MPLS (Multi Protocol Label Switching) label integration is distributed to the hard pipeline plane by the NMS, and the label of the MPLS label in the static MPLS label integration can be transferred by the hard pipeline plane only, therefore, a private line service can be borne in the hard pipeline plane, the bandwidth of the private line service cannot be occupied by other non-private line services, and the private line service which ensures the bandwidth can be provided.
Owner:HUAWEI TECH CO LTD
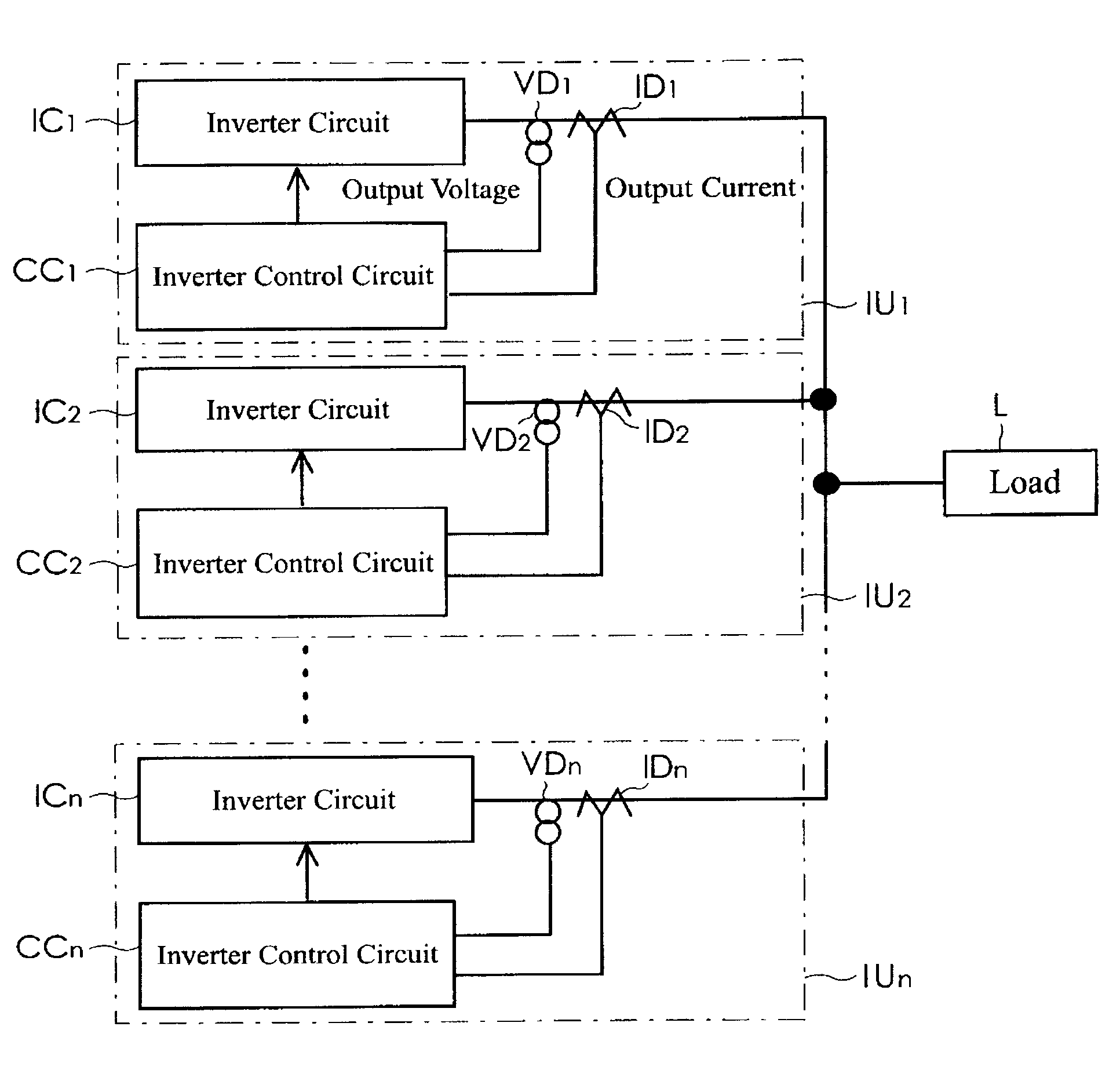
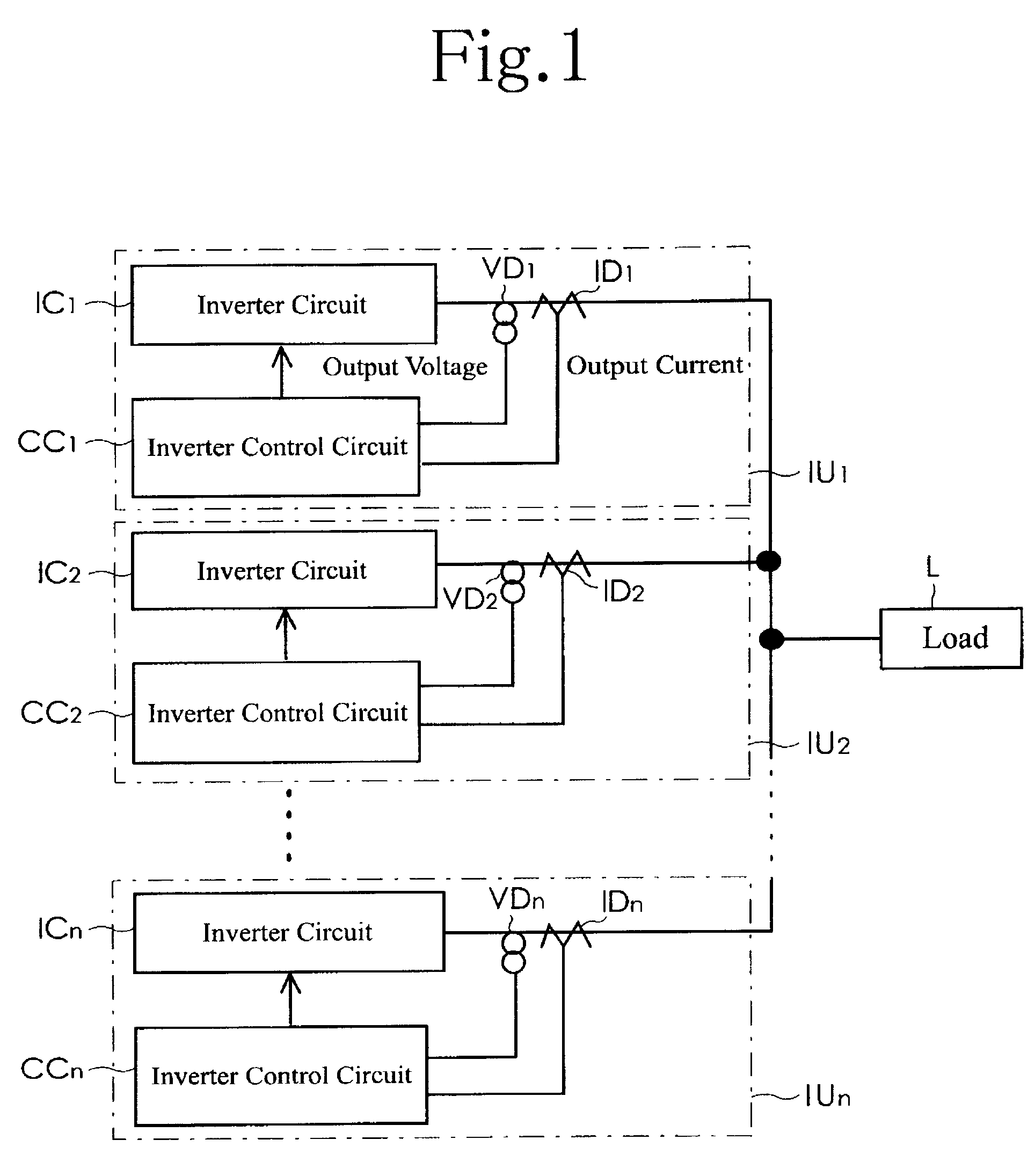
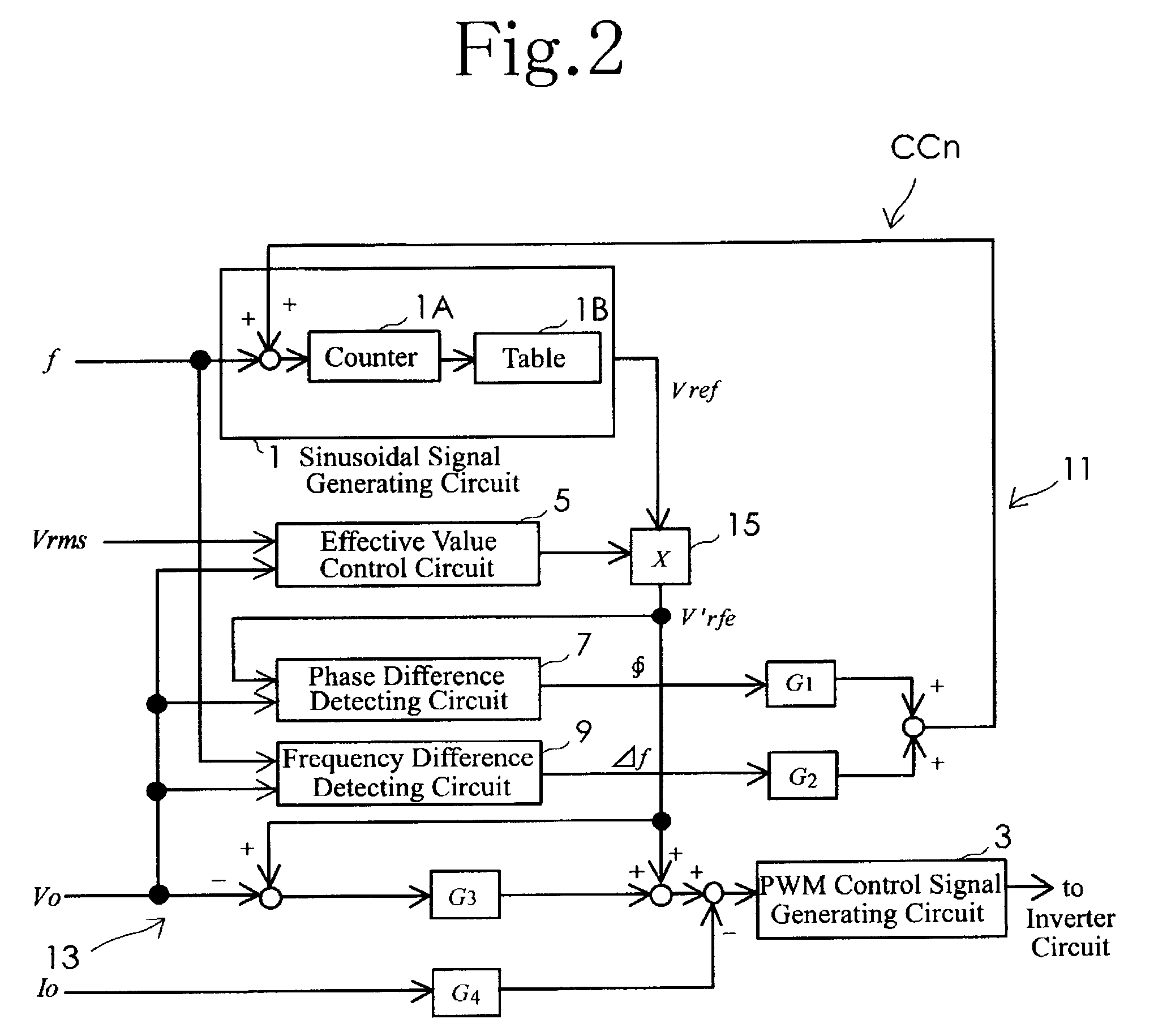
Parallel inverter system
ActiveUS20090185400A1High frequency accuracyBatteries circuit arrangementsDc source parallel operationPhase differenceControl signal
A parallel inverter system needs neither a dedicated line for synchronizing common portions nor switching operations, and includes a plurality of inverter units operating in parallel. An inverter control circuit of each inverter unit includes a sinusoidal signal generating circuit, a PWM control signal generating circuit, a phase difference circuit, a frequency difference circuit, and a feedback circuit. The feedback circuit inputs to the sinusoidal signal generating circuit an addition result value which is obtained by adding to a commanded value for reference frequency a value obtained from multiplication of a phase difference by a predetermined gain and a value obtained from multiplication of a frequency difference by a predetermined gain. The phase difference among outputs from the inverter units occurring in the parallel operation of the inverter units is reduced by changing the output frequencies of the inverter units. (140 word)
Owner:SANYO DENKI CO LTD
Disaster-tolerant system for processing telephone traffic data
ActiveCN101621394AReduce transfer dataReduce bandwidth requirementsData switching networksHardware structureNetwork connection
The invention relates to a disaster-tolerant system for processing telephone traffic data, which consists of a main operation system and a standby system. A synchronous private line is arranged between the main operation system and the standby system. The standby system and the main operation system have the same internal software and hardware structure and external network connection. The main operation system is an actual operation system, and the standby system synchronously operates with the main operation system. When normally processing data, the main operation system generates synchronizing information and transforms the synchronizing information to the standby system. The standby system receives the synchronizing information and implements the treatment process, but does not transmit the result. After the main operation system has system failure or disaster, the standby system temporarily takes over production, and after the acquired data is processed, the file is transmitted into the external network. The invention realizes disaster tolerance by adopting the mode that the systems are embedded into the processing flow and the transmitted data is greatly reduced. Moreover, the mode adopted by the invention has far lower requirement on bandwidth than the disaster-tolerant mode based on intelligent storage bottom copy. The standby system and the main operation system can complete switching over in a short time.
Owner:SHANGHAI POSTS & TELECOMM DESIGNING CONSULTING INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com