Cloud data protection method for data hierarchical encryption and segmentation
A technology of data classification and data protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The content of the present invention is described in more detail below:
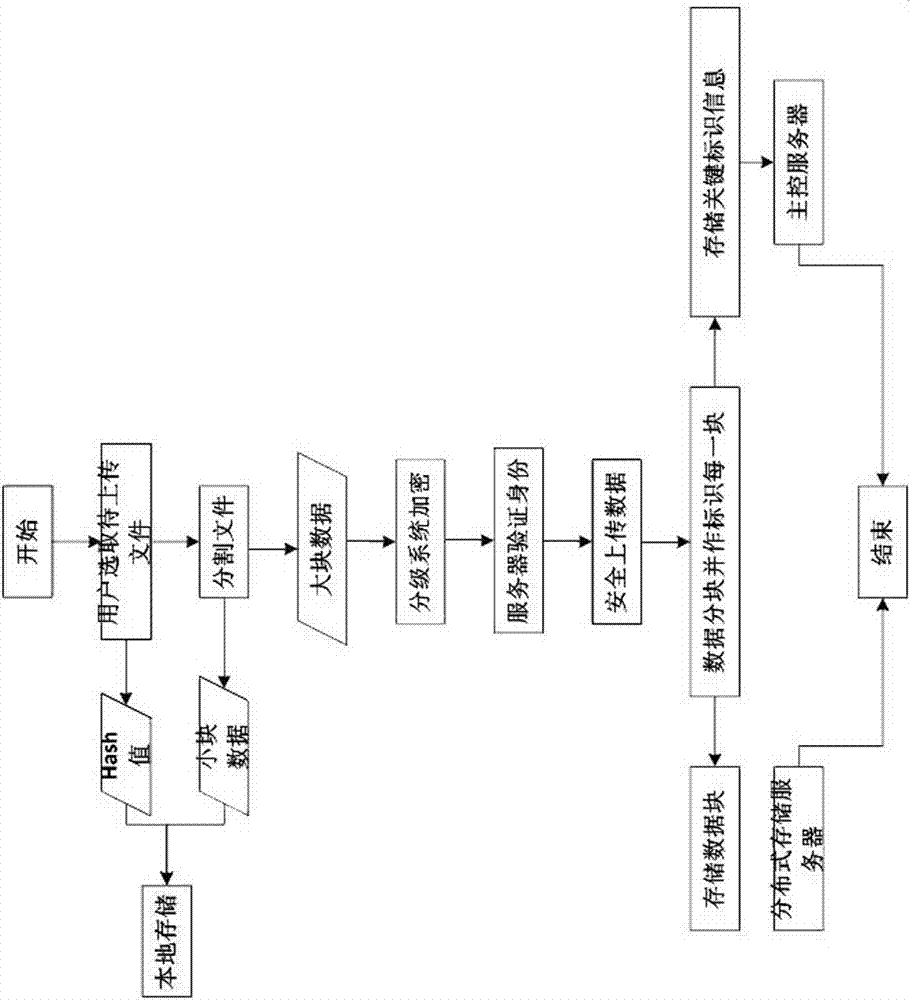
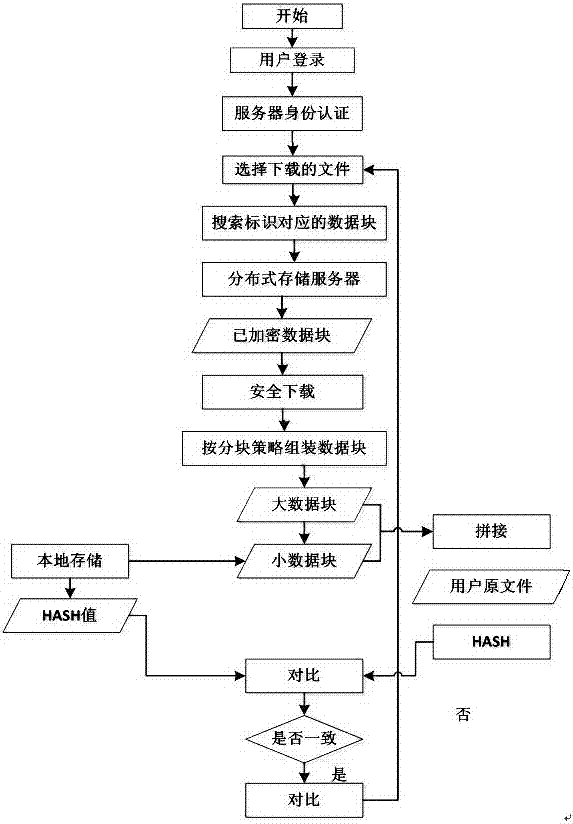
[0032] The solution divides the security implementation of cloud storage into the following three parts:
[0033] 1) Client system: The client system consists of a file system filter driver in the kernel state and a control program in the user state. It is responsible for monitoring and capturing local system operations, dividing the obtained data into large and small blocks, and performing hash operations (Hash), and then saving small data blocks and hash values locally, using data coloring and different intensities Data encryption technology to encrypt.
[0034] 2) Master control server system: The master control server system mainly performs data block and metadata processing services, and performs authentication and access control on data requests from clients.
[0035] 3) Storage server system: The storage server system is mainly responsible for the actual managed data storage. When the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com