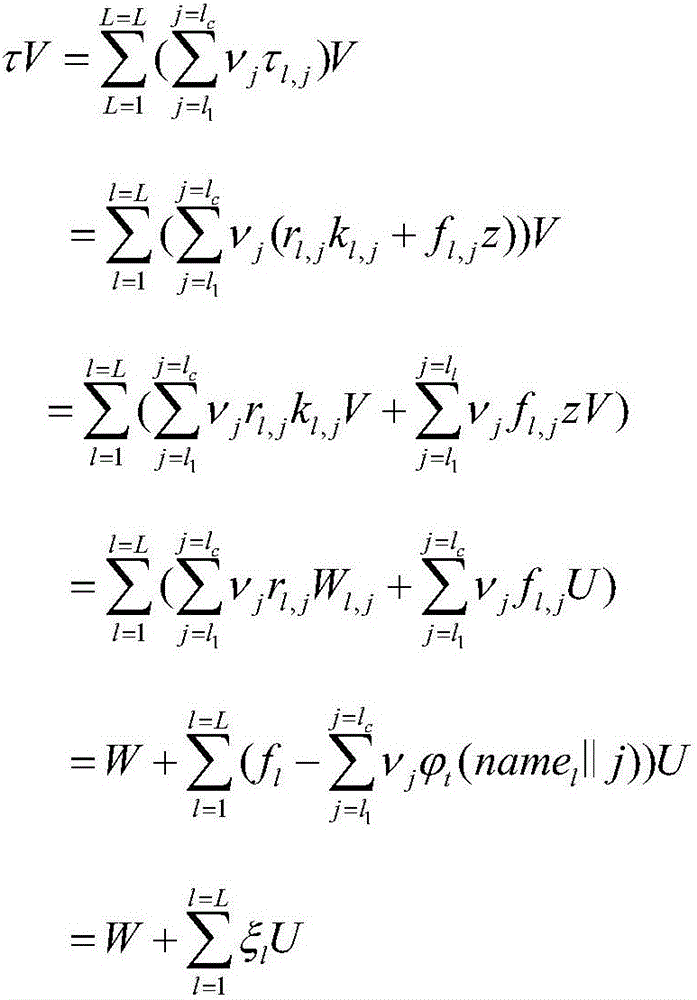Batch self-auditing method for cloud storage data
A cloud storage and data technology, applied in the field of information security, can solve problems such as data leakage of cloud users, and achieve the effect of ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Describe technical scheme of the present invention in detail below:
[0030] The steps of the present invention are divided into four parts:
[0031] System initialization: The system generates a public-private key pair based on an elliptic curve digital signature algorithm, a public-private key pair for lightweight signatures on file names, and a secure lightweight symmetric encryption algorithm.
[0032] Signature generation steps: the user uses the improved Elliptic Curve Signature Algorithm (ECDSA) to calculate their digital signatures for multiple data files, and at the same time digitally signs different data file names to generate data file labels, and stores these multiple sensitive data files Perform symmetric encryption. Finally, these signatures and the ciphertext of the data file are sent to the cloud server, and these data are deleted on the local client.
[0033] Audit proof generation steps: In order to batch audit the integrity of the outsour...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com