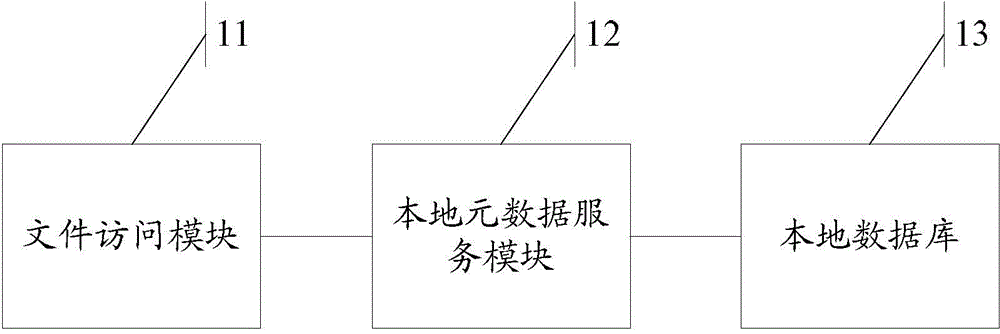
File writing method, file reading method, file deletion method, file query method and client
A client-side and file-writing technology, applied in electrical components, special data processing applications, instruments, etc., to solve problems such as the absence of metadata servers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
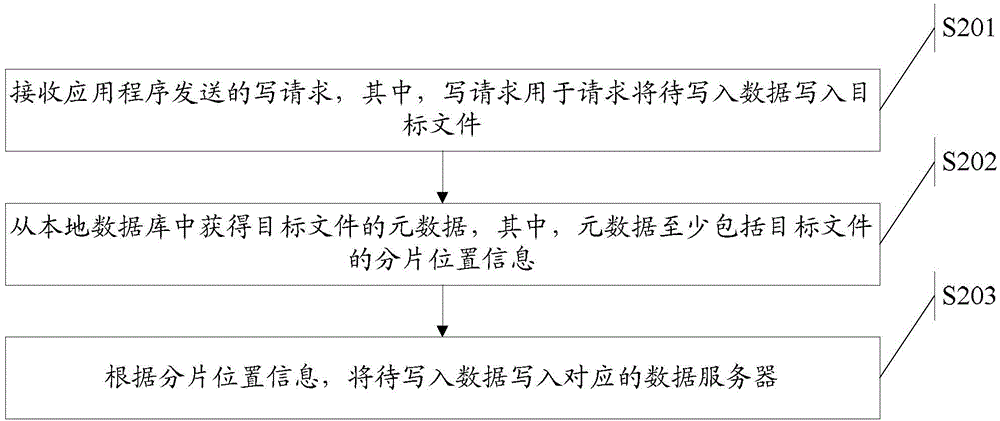
[0050] figure 2 It is a schematic flow chart of the method for writing files in the embodiment of the present invention, see figure 2 As shown, the method includes:
[0051] S201: Receive a write request sent by the application program, wherein the write request is used to request to write the data to be written into the target file;
[0052] In another embodiment, in order to enable the file access client to have the permission to write files, then, before S201, the method further includes: sending a write lock request to the remote metadata server, wherein the write lock request is used to request The remote metadata server writes lock metadata; receives a write lock response returned by the remote metadata server, wherein the write lock response carries a timestamp; saves the timestamp to a local database.
[0053] Specifically, the local metadata service module initiates a write lock request to the remote metadata server, and the remote metadata server responds to the ...
Embodiment 2
[0068] image 3 It is a schematic flow chart of the method for reading files in the embodiment of the present invention, see image 3 As shown, the method includes:
[0069] S301: Receive a read request sent by the application program, wherein the read request is used to request to read the data to be read in the target file;
[0070] Specifically, when the application program needs to read a certain part of data in the target file, it can send a read request to the file access module, requesting to read the data to be read in the target file.
[0071] Further, before reading the file, the file access client needs to obtain the permission to read the file, so before S301, the method also includes: receiving a read lock request sent by the application program, wherein the read lock request is used to request a read lock target file ;When the metadata is stored in the local database, return a read lock success response to the application; when the metadata is not stored in the...
Embodiment 3
[0081] Figure 4 It is a schematic flow chart of the method for deleting files in the embodiment of the present invention, see Figure 4 As shown, the method includes:
[0082] S401: Receive a file deletion request sent by an application program;
[0083] Specifically, when the application program needs to delete the target file, it can send a file deletion request to the file access module.
[0084] S402: Delete the metadata of the target file in the local database.
[0085] Specifically, in response to the request, the file access module invokes the local metadata service module to delete the metadata of the target file in the local database.
[0086] Further, after S402, the local metadata service module may also send a first deletion request to the remote metadata server, wherein the first deletion request is used to instruct the remote metadata server to delete the metadata; receiving the remote metadata server The delete reply sent.
[0087] Specifically, after the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com