Patents
Literature
436 results about "Use of services" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Use of the Services. The Services are designed to be used through a supported modern web browser and an Internet connection. You are responsible for controlling access to your account, including by creating a strong password, protecting that password, and preventing unauthorized account usage.
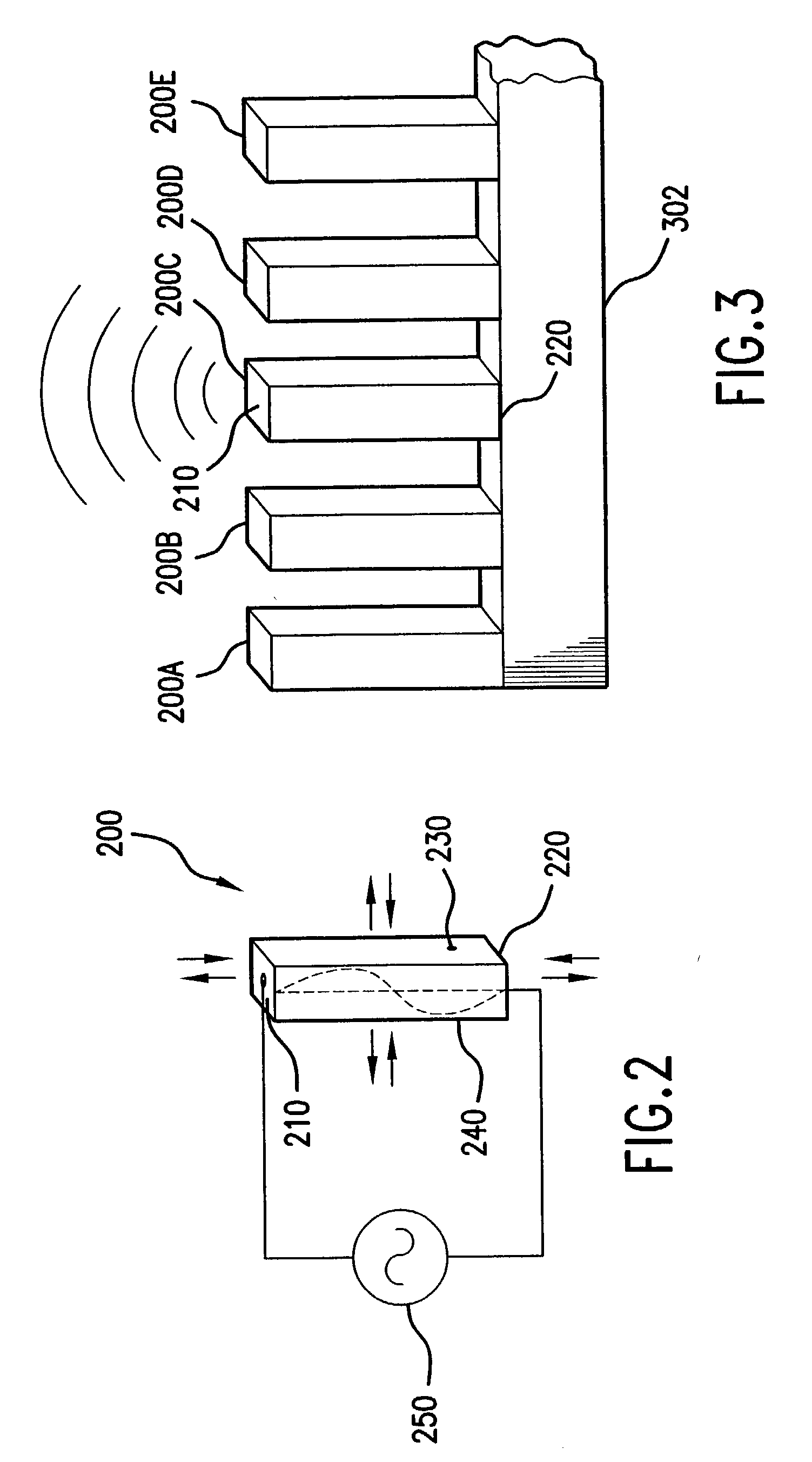
Systems and methods for allocation of classes of service to network connections corresponding to virtual channels
ActiveUS20110276699A1Multiple digital computer combinationsTransmissionInternet trafficClass of service
A system for allocating a different class of service to each network connection in a plurality of network connections, where each network connection corresponds to one or more virtual channels. The system can include a plurality of virtual channels that connect a first computer and a second computer. Each virtual channel can service at least a portion of the network traffic generated using a remote-display protocol. The system can also include a plurality of network connections, where each network connection corresponds to at least one of the virtual channels. Each network connection of the system can have an assigned port number and an assigned class of service that corresponds to a transmission priority level. The class of service assigned to each network connection can be unique from the classes of service assigned to other network connections.
Owner:CITRIX SYST INC
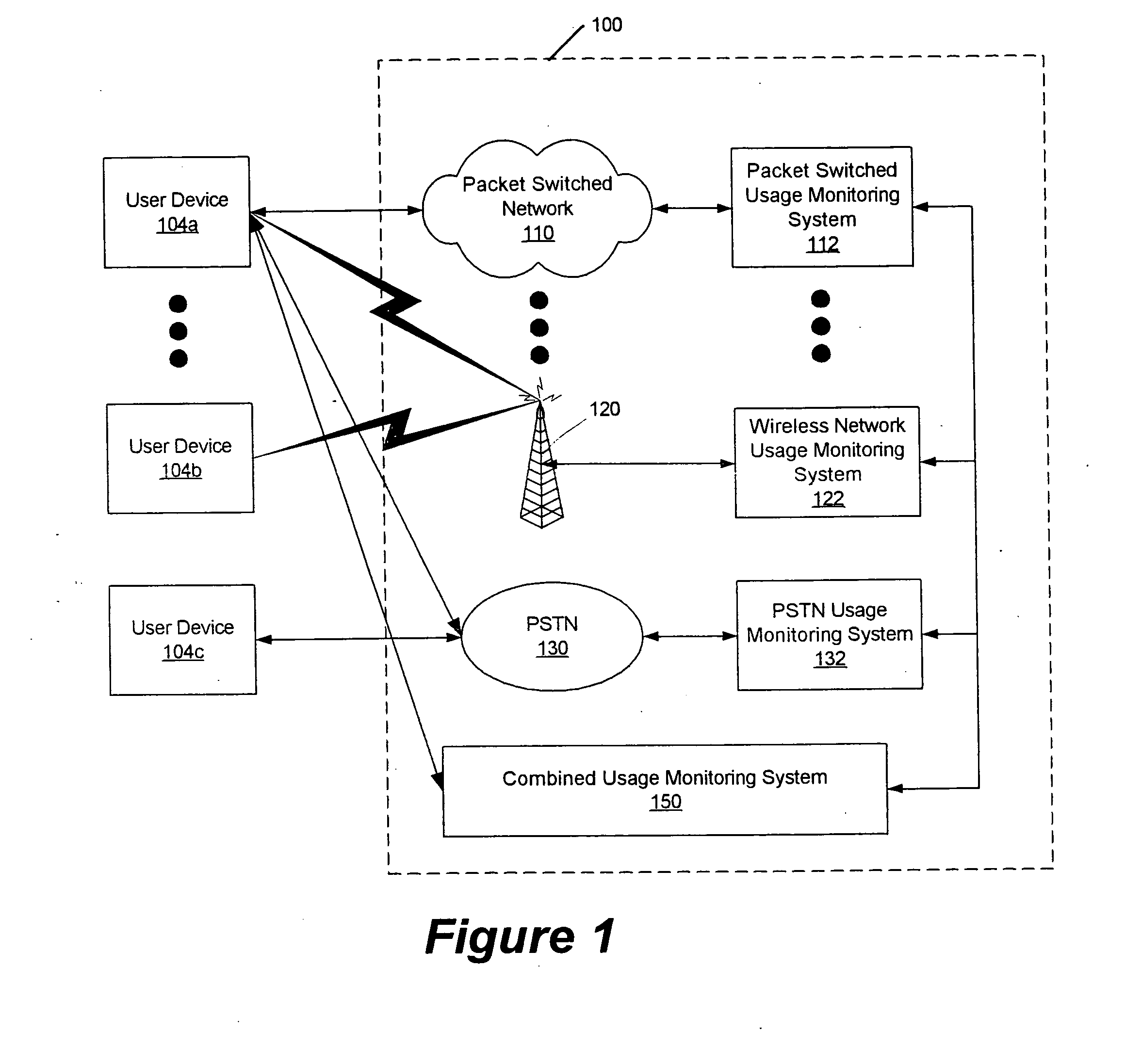
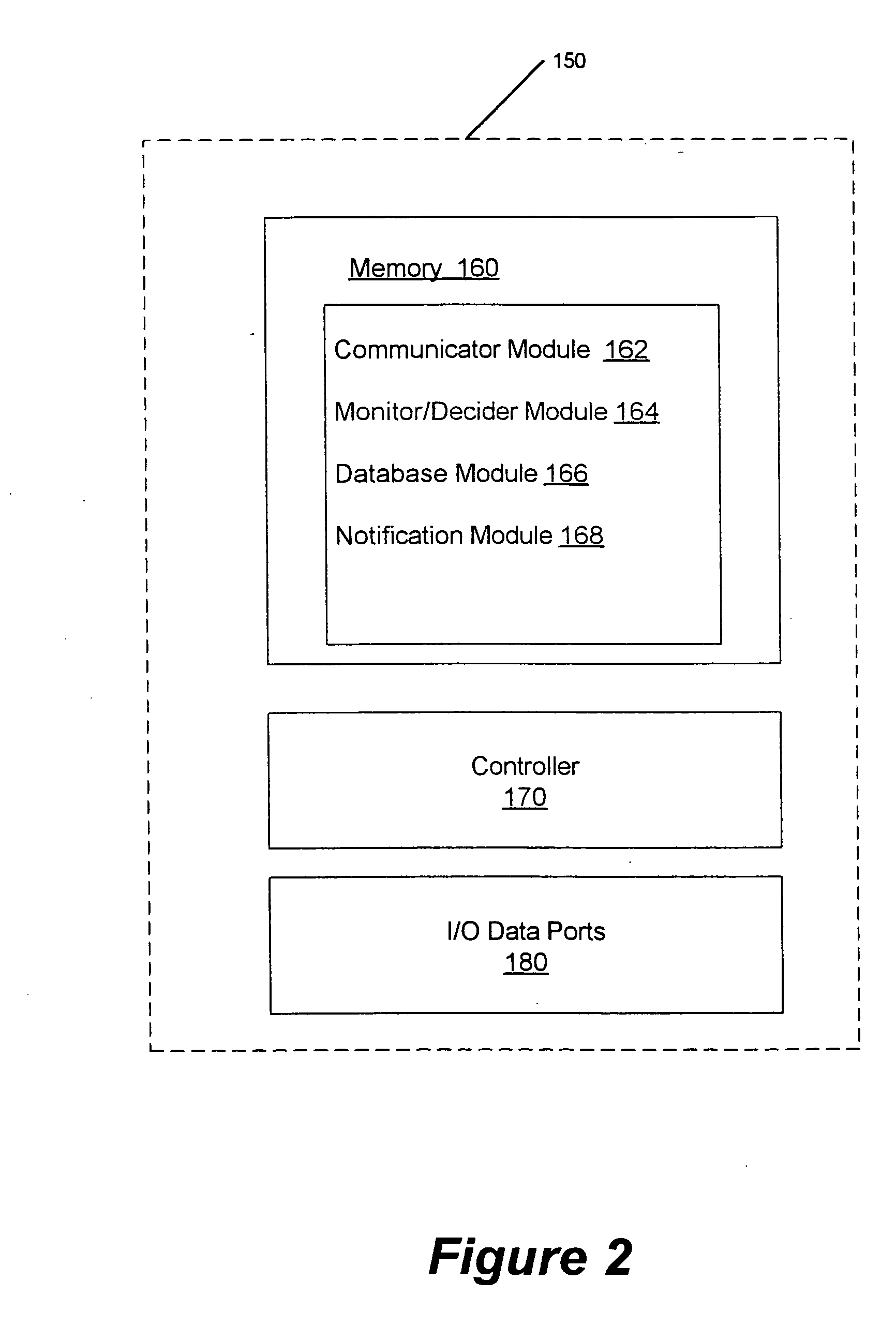
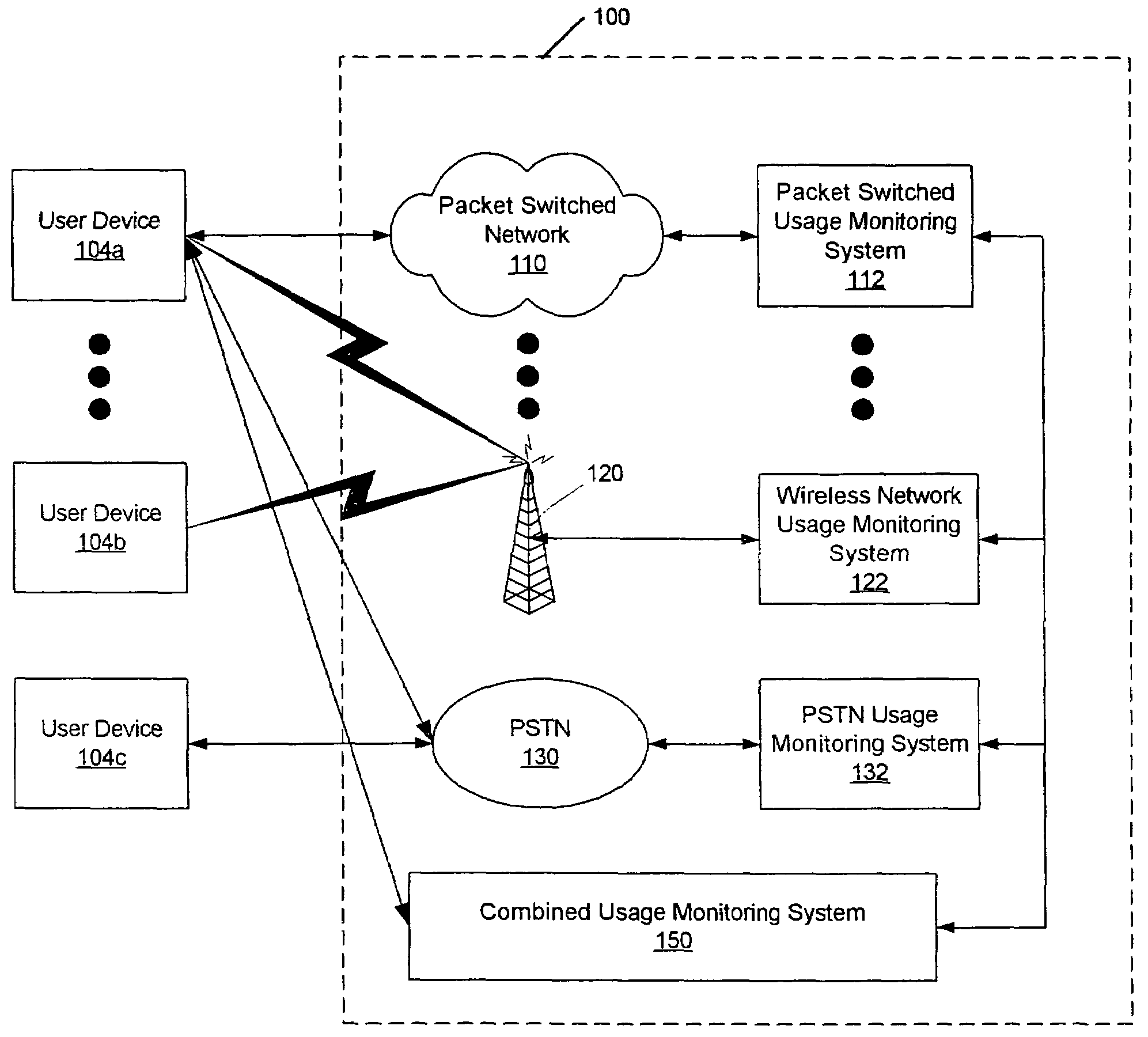
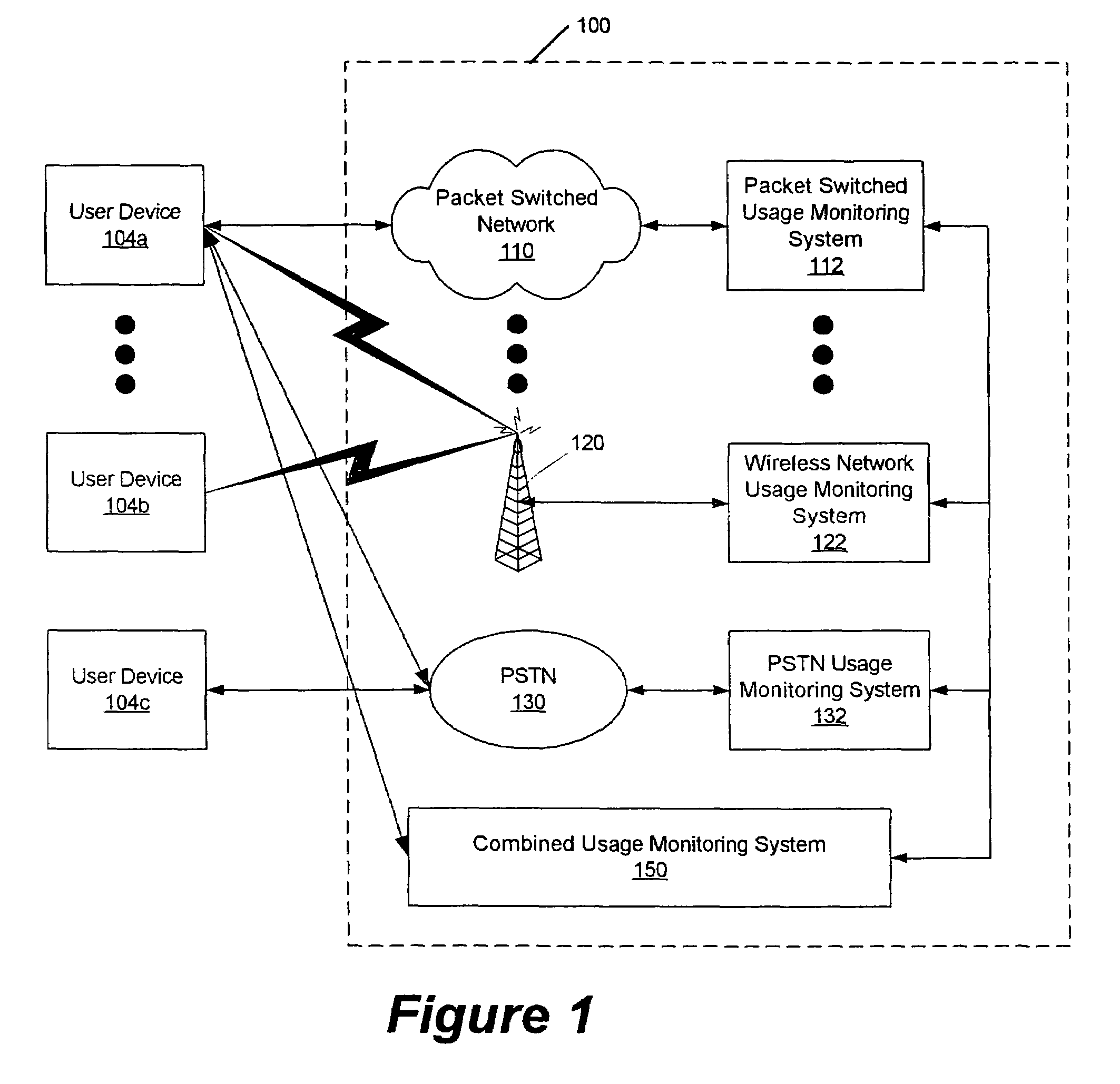
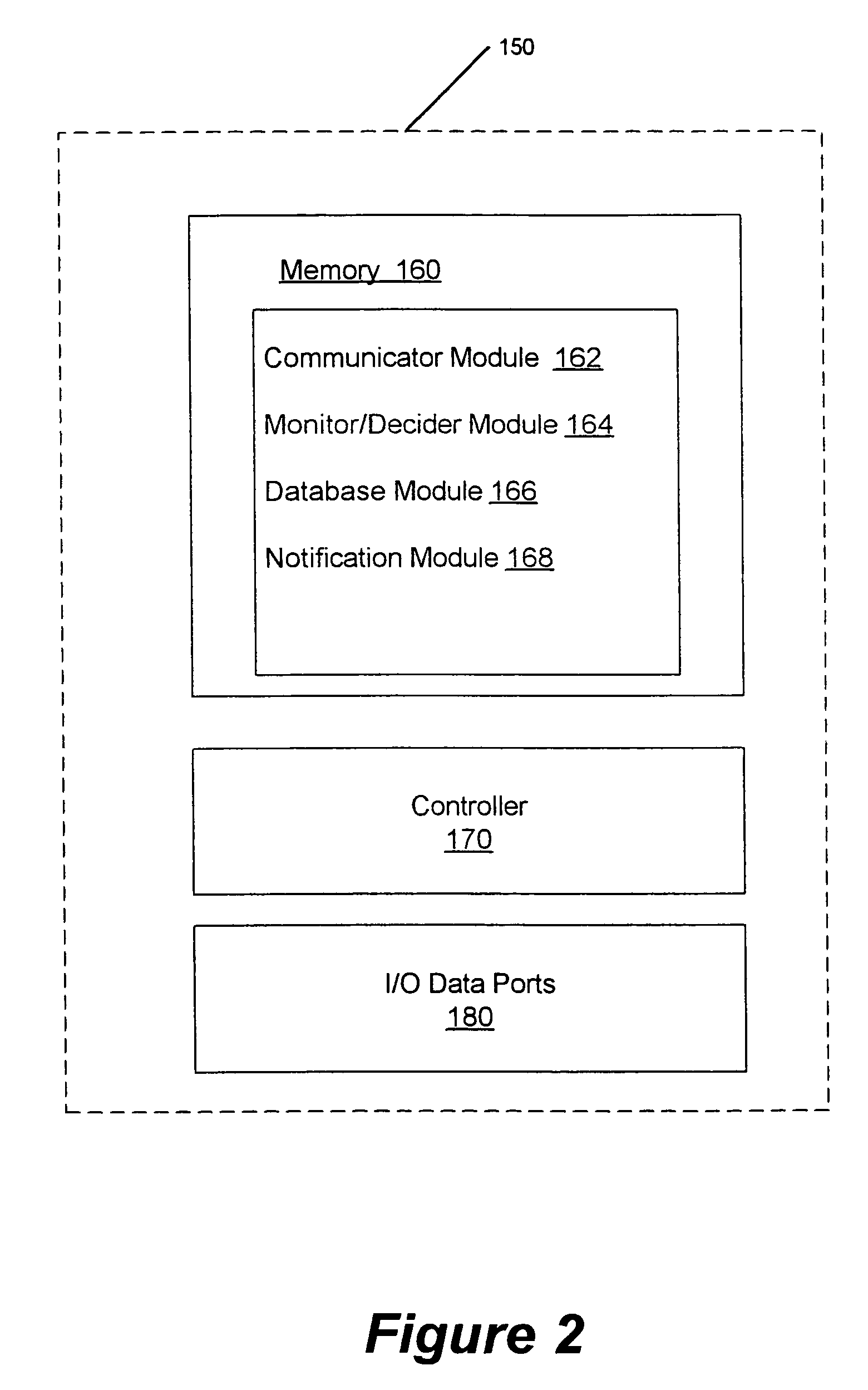
Methods, systems and computer program products for monitoring service usage
InactiveUS20060045245A1Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemUse of services
Monitoring criteria is received that corresponds to a usage quantity for a plurality of services. Each of the plurality of services is provided over ones of a plurality of different communication systems. Actual service usage information is received for the plurality of services. The actual service usage information and the monitoring criteria are compared. An electronic notification message is sent when the monitoring criteria for one or more of the plurality of services is satisfied.
Owner:AT&T INTPROP I L P
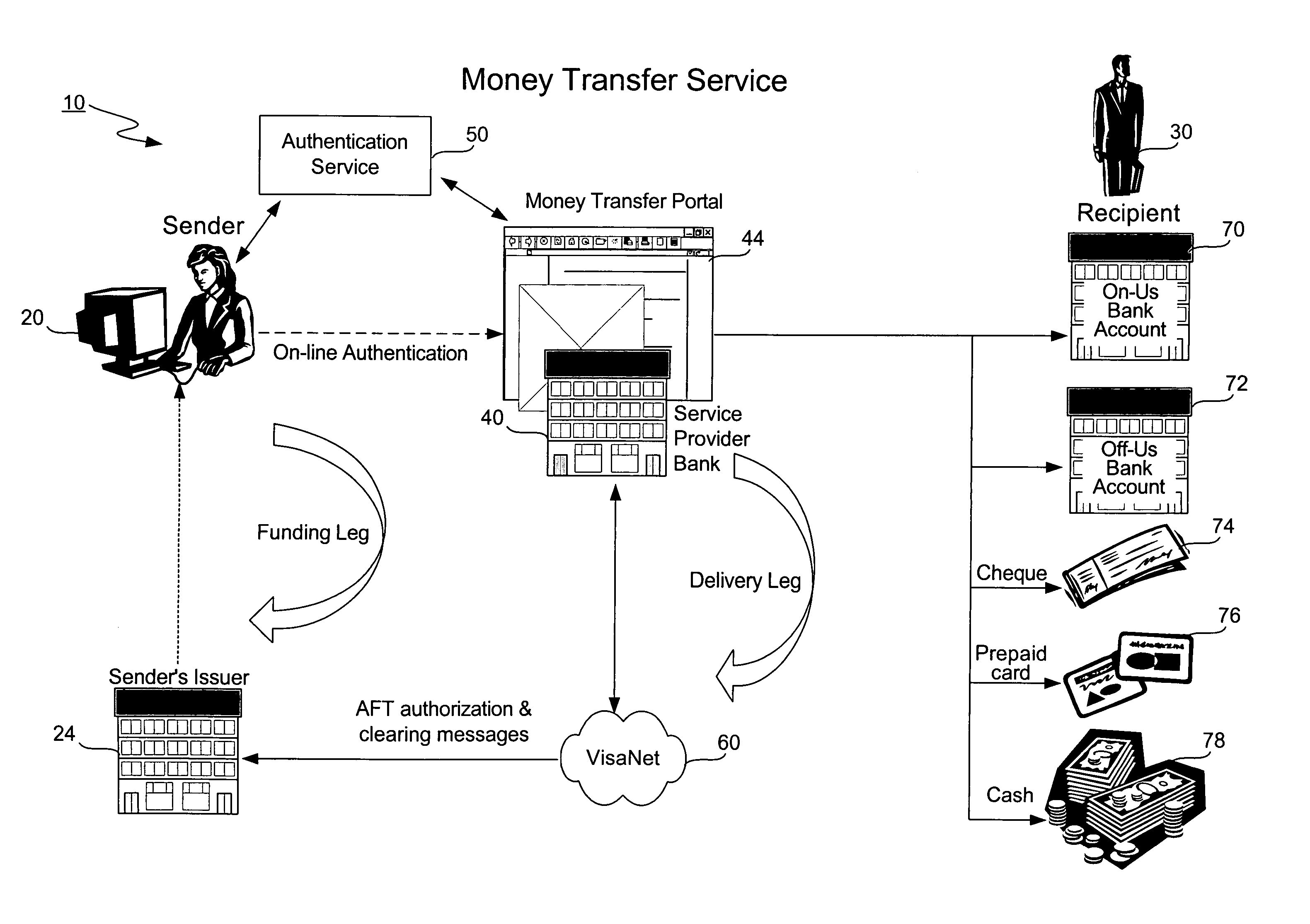
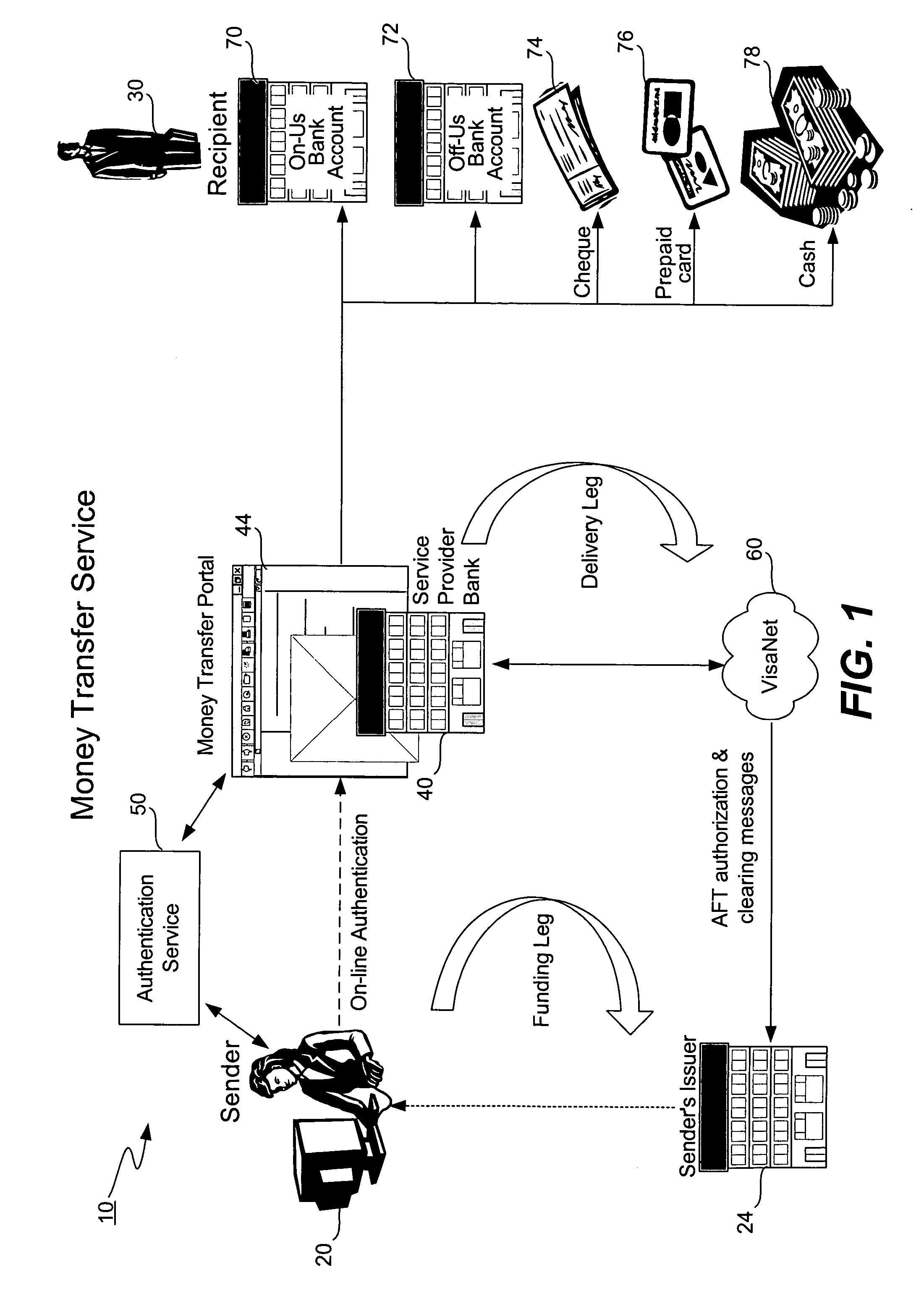
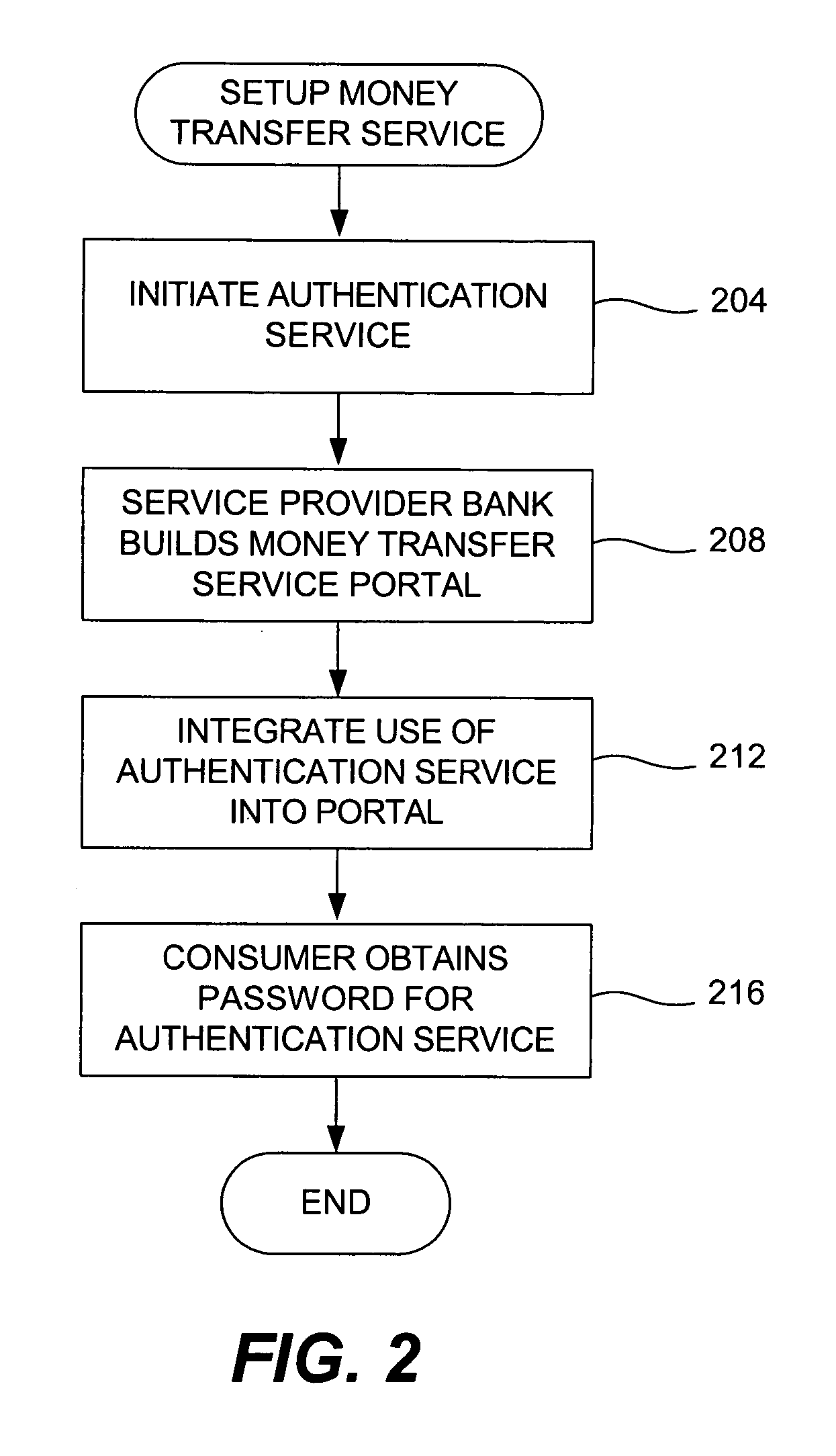
Money transfer service with authentication
ActiveUS20060006224A1Good serviceAvoids cash handling costComplete banking machinesFinancePasswordUse of services
A bank (or merchant) hosts and operates an online money transfer service (or “portal”). A sender logs into the portal and enters payment card and money transfer details and then submits the transaction. An authentication window appears displaying the sender's transaction details and the sender is prompted to enter his or her password. Upon successful authentication, the bank seeks authorization from the card issuer. Upon successful authorization, the bank credits the recipient's local bank account or existing payment card. The recipient can also receive a check, a draft, a prepaid card or cash. The money transfer service is used both cross-border and domestic to effect person-to-person money transfer. The money transfer service uses the “Verified by Visa” authentication service and VisaNet for authorization. Messages over VisaNet are used to deliver funds to a recipient.
Owner:VISA INT SERVICE ASSOC
Methods, systems and computer program products for monitoring service usage
InactiveUS7620162B2Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemUse of services
Monitoring criteria is received that corresponds to a usage quantity for a plurality of services. Each of the plurality of services is provided over ones of a plurality of different communication systems. Actual service usage information is received for the plurality of services. The actual service usage information and the monitoring criteria are compared. An electronic notification message is sent when the monitoring criteria for one or more of the plurality of services is satisfied.
Owner:AT&T INTPROP I LP
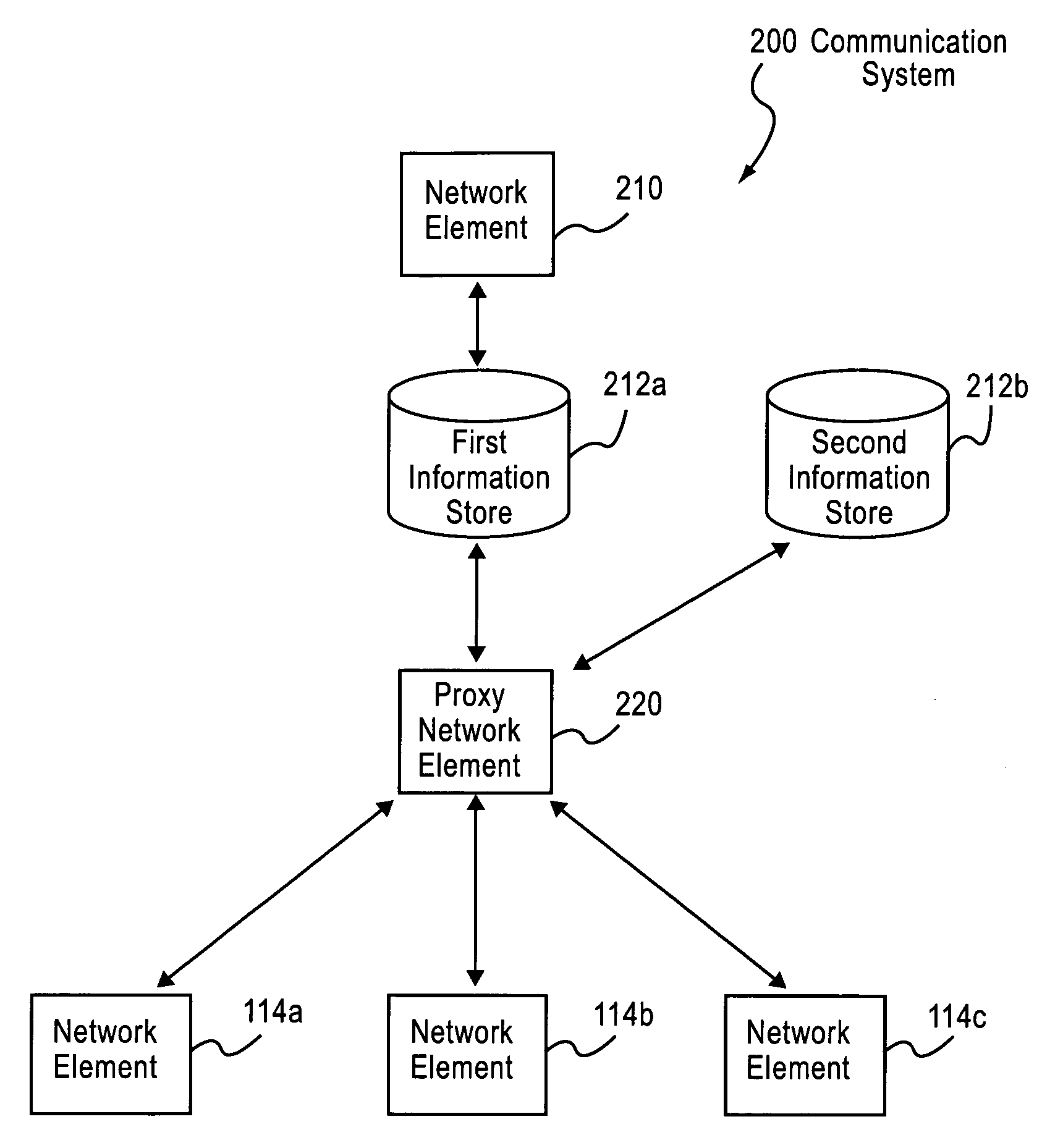
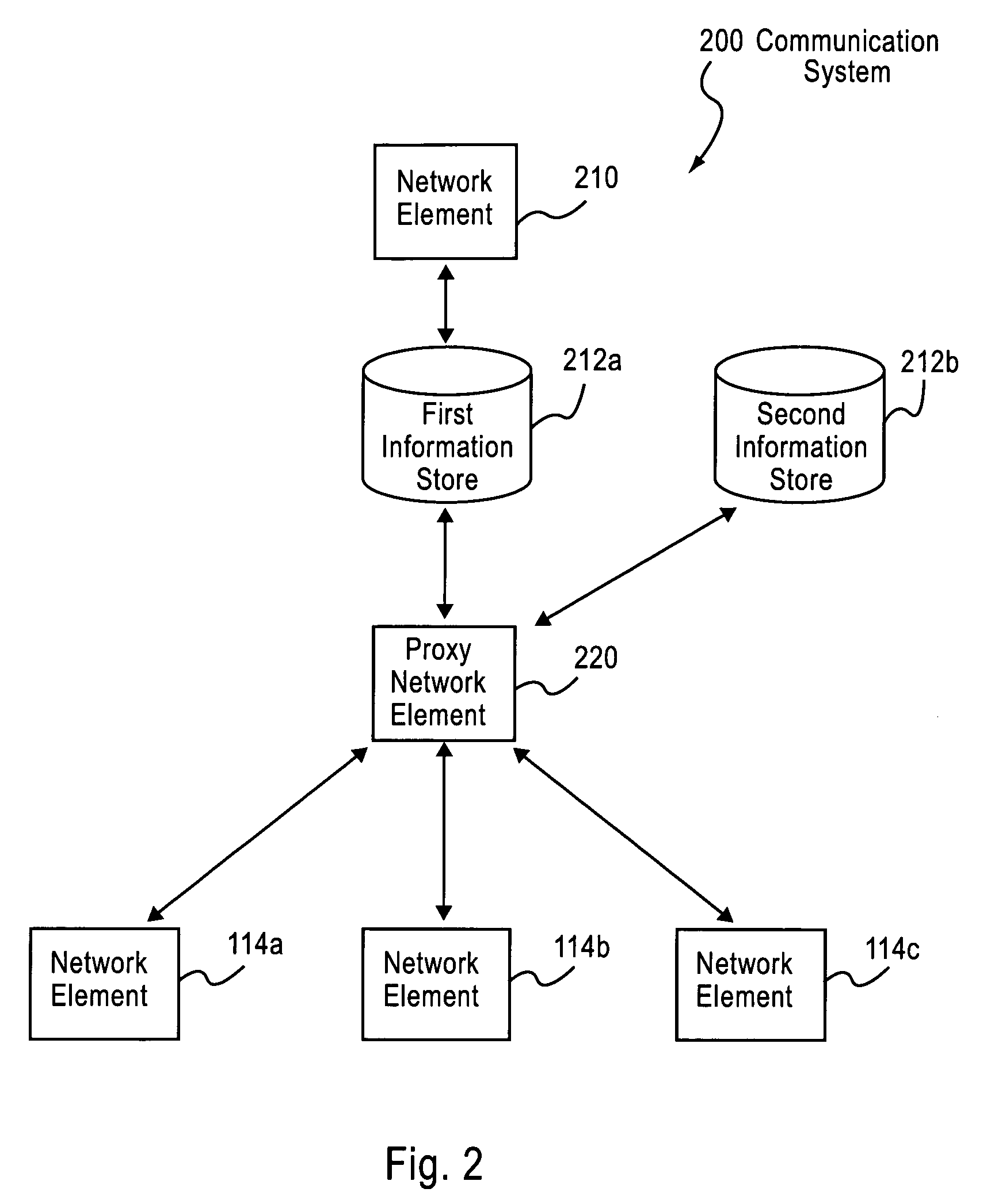
Controlling access to services in a communications system
ActiveUS7644267B2Digital computer detailsTelephonic communicationCommunications systemUse of services
Owner:WSOU INVESTMENTS LLC
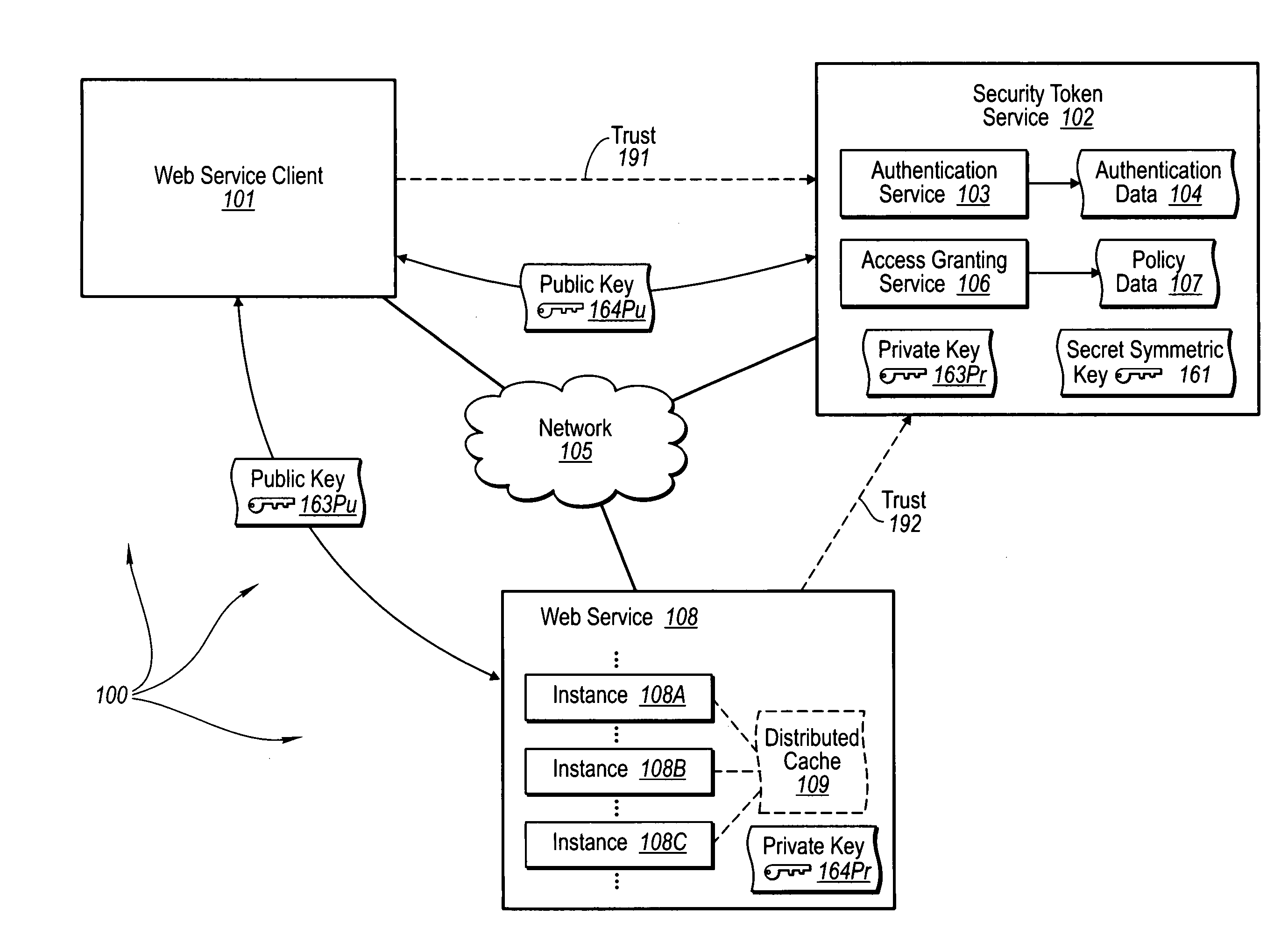
Trusted third party authentication for web services
InactiveUS20060206932A1Communication securityDigital data processing detailsUser identity/authority verificationWeb serviceInternet privacy
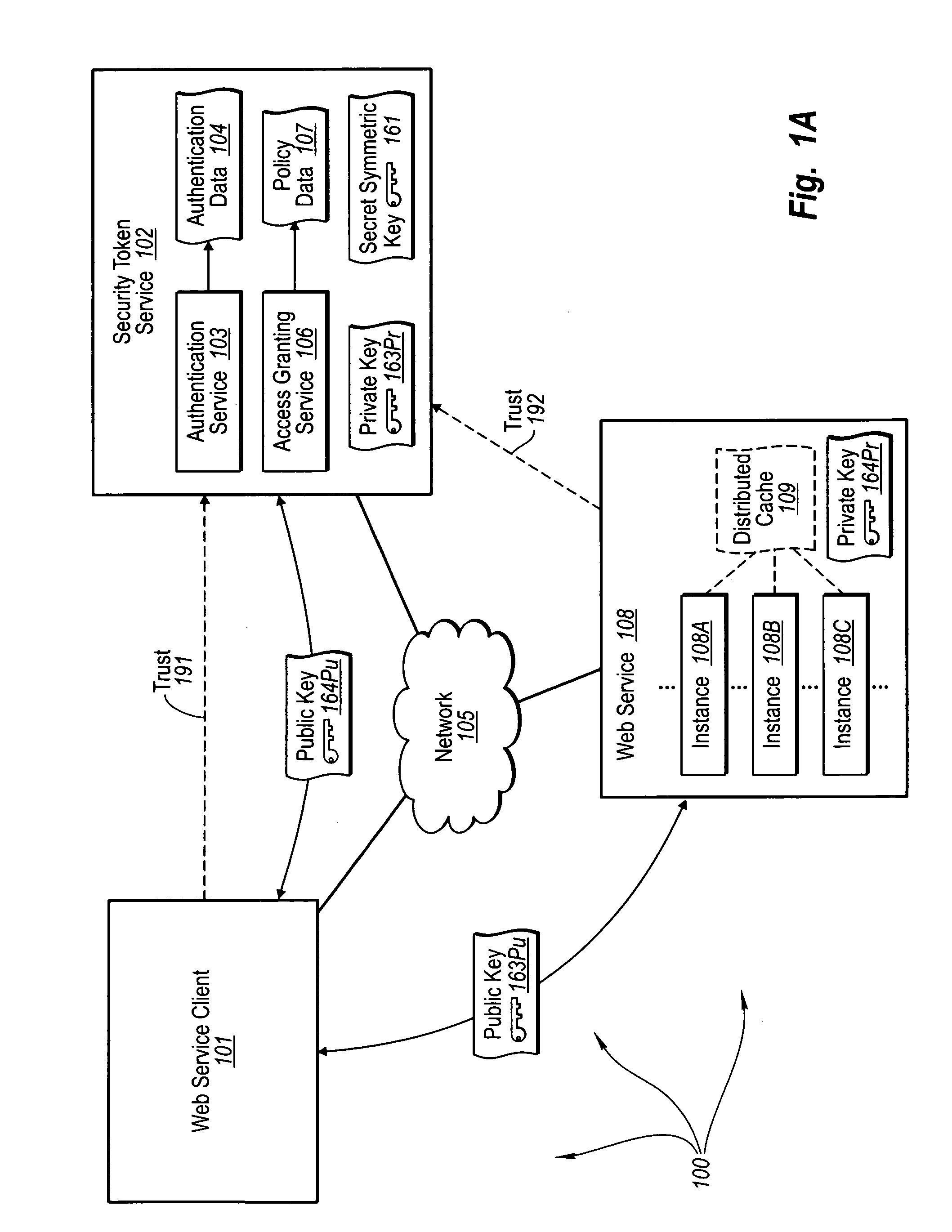
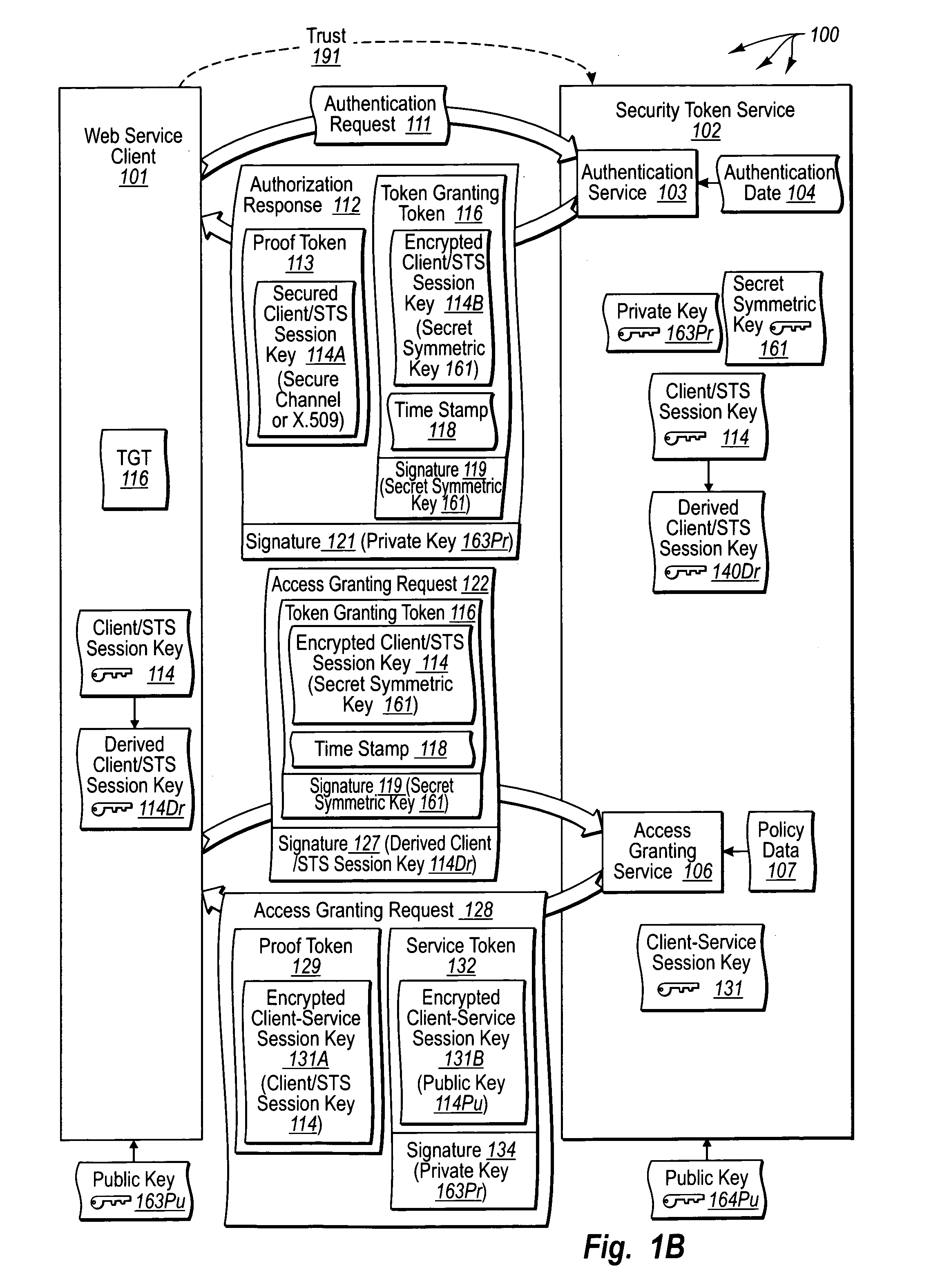
The present invention extends to trusted third party authentication for Web services. Web services trust and delegate user authentication responsibility to a trusted third party that acts as an identity provider for the trusting Web services. The trusted third party authenticates users through common authentication mechanisms, such as, for example, username / password and X.509 certificates and uses initial user authentication to bootstrap subsequent secure sessions with Web services. Web services construct user identity context using a service session token issued by the trusted third party and reconstruct security states without having to use a service-side distributed cache.
Owner:MICROSOFT TECH LICENSING LLC
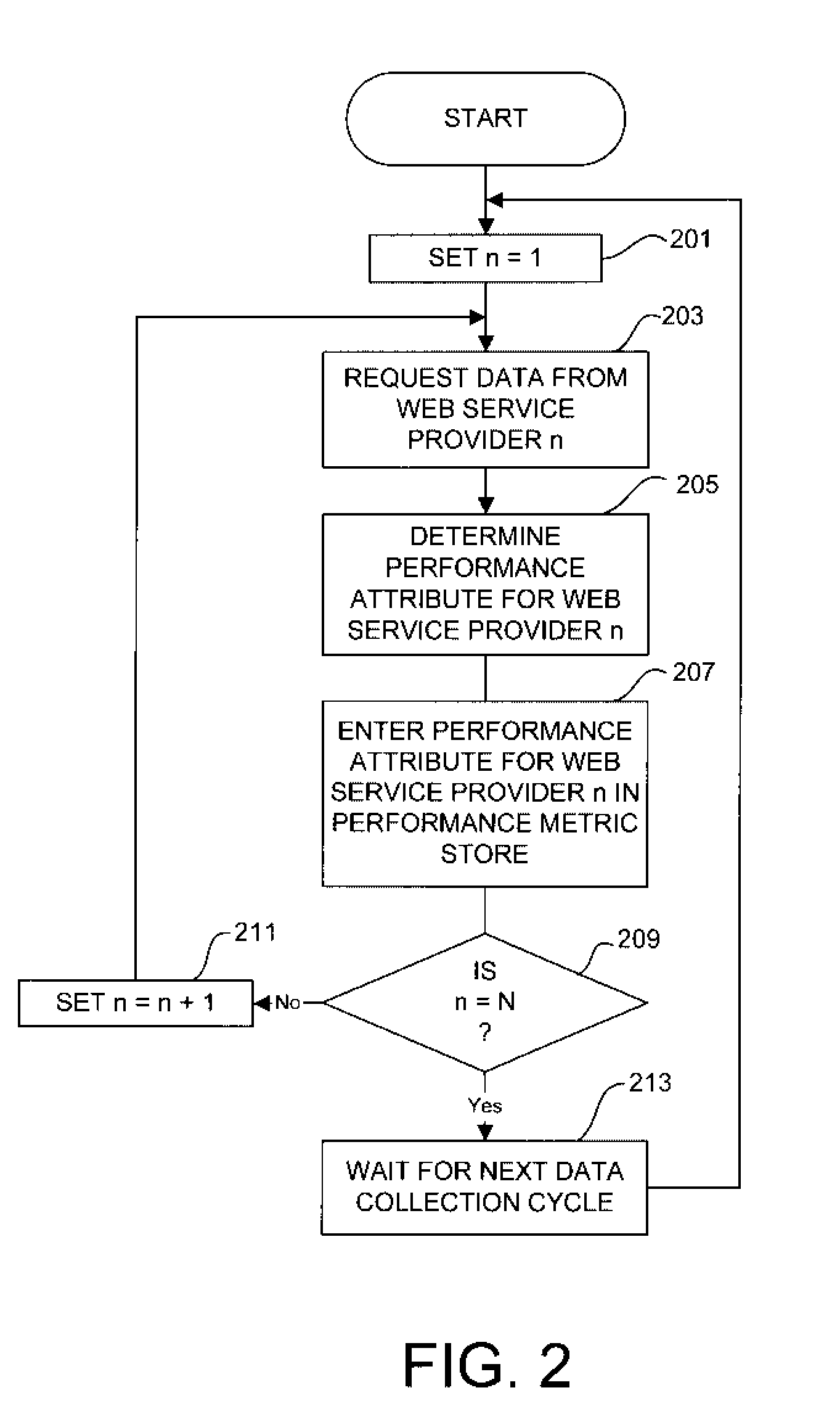
Method of and System for Providing Performance Information in a UDDI System
InactiveUS20070250611A1Update performanceWeb data retrievalDigital computer detailsWeb serviceUse of services
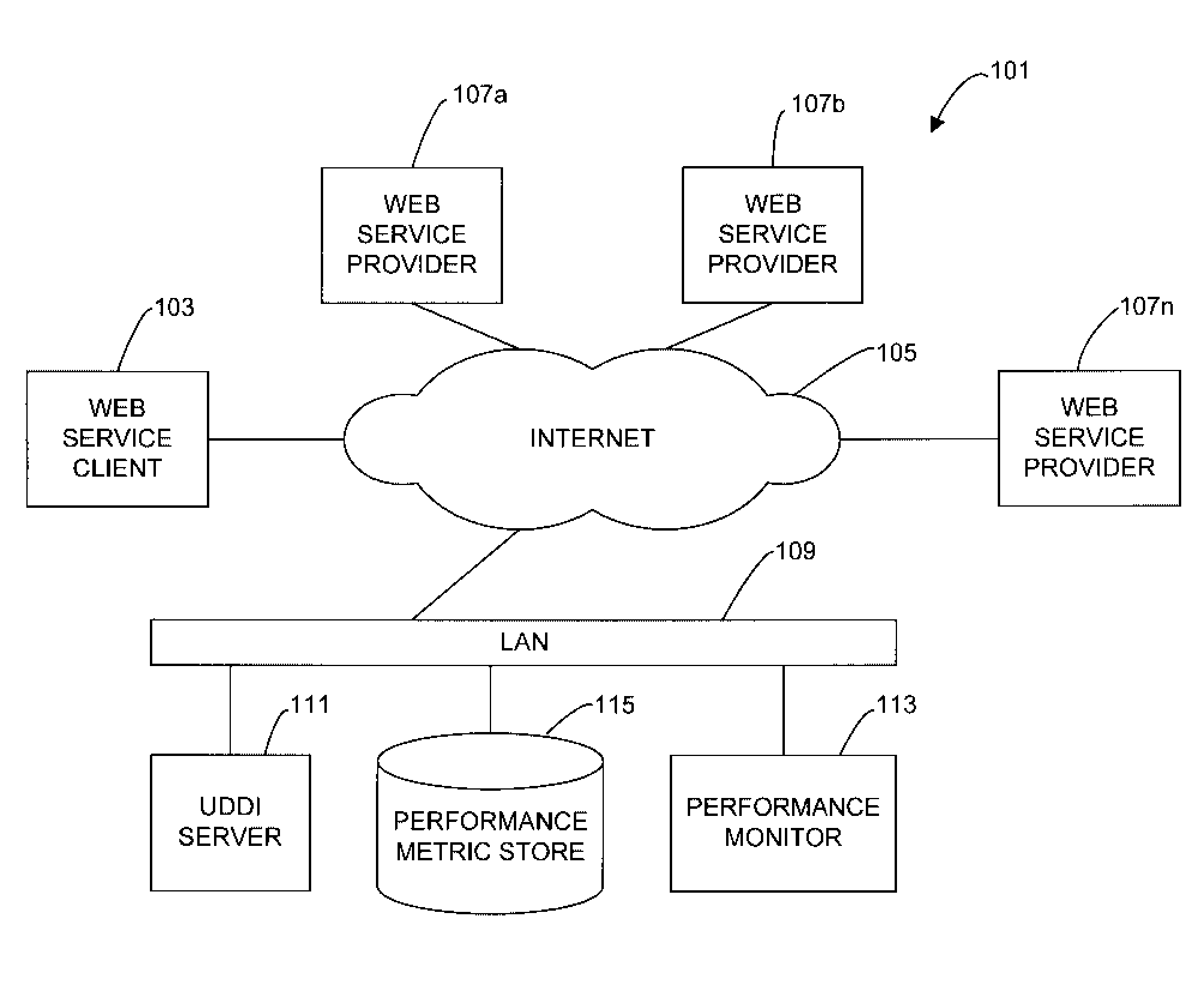
A method of and system for providing performance information in a Universal Description, Discovery and Integration (UDDI) system periodically requests data from Web service providers that are registered in a UDDI registry. The method and system determine performance attributes for the Web service providers based upon the requested data. The method stores the latest, or most current, performance attributes in a performance metric store that is accessible by the UDDI registry. The UDDI registry services requests from Web service consumers for performance attributes of service providers that provide specified Web services. The UDDI registry accesses the performance metric store to obtain current performance attributes for the Web service providers and returns the performance attributes to the Web service consumer. The Web service consumer can use the performance attributes to select a Web service.
Owner:IBM CORP
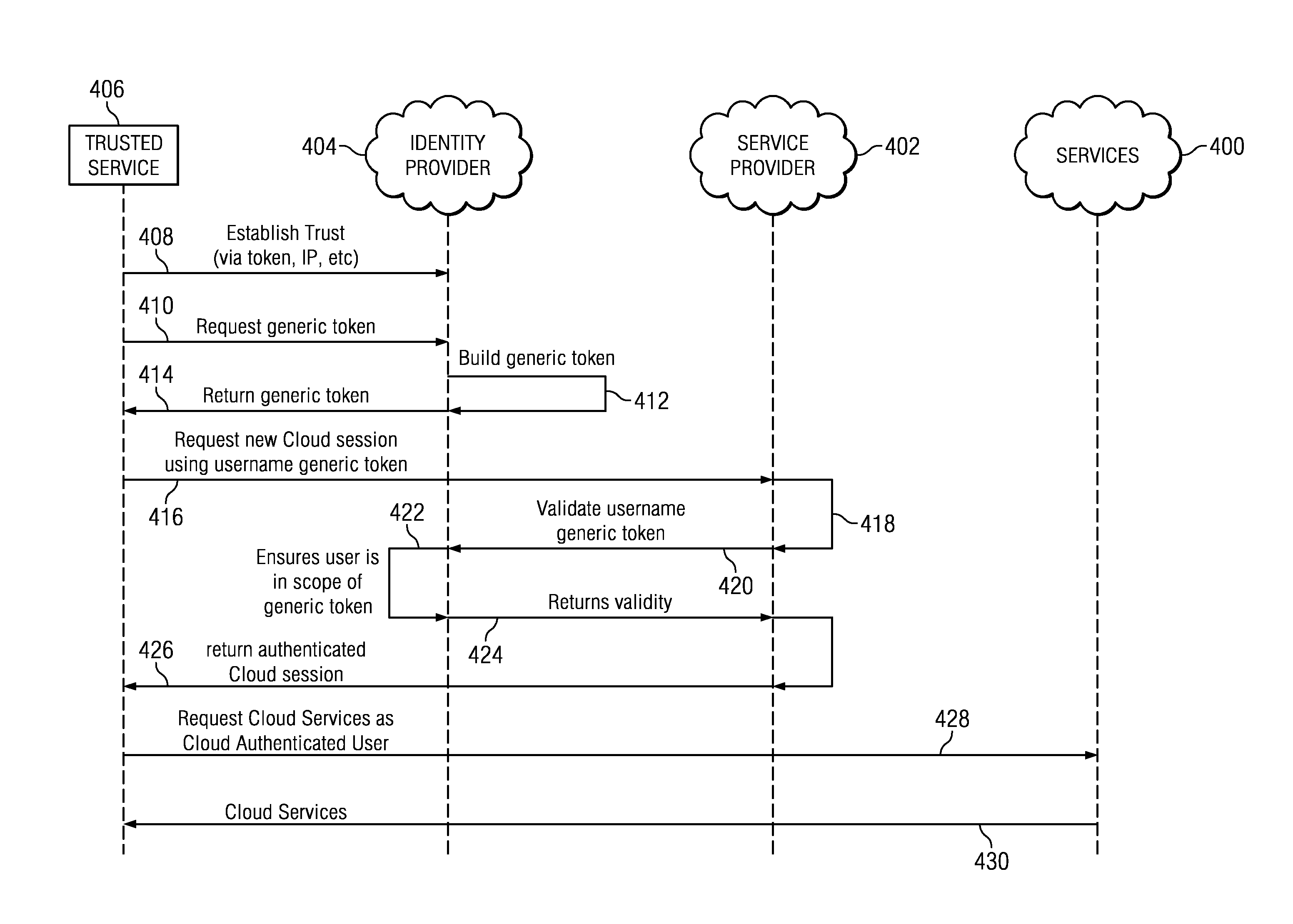
User impersonation/delegation in a token-based authentication system
ActiveUS20120254957A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust relationship
A “trusted service” establishes a trust relationship with an identity provider and interacts with the identity provider over a trusted connection. The trusted service acquires a token from the identity provider for a given user (or set of users) without having to present the user's credentials. The trusted service then uses this token (e.g., directly, by invoking an API, by acquiring another token, or the like) to access and obtain a cloud service on a user's behalf even in the user's absence. This approach enables background services to perform operations within a hosted session (e.g., via OAuth-based APIs) without presenting user credentials or even having the user present.
Owner:IBM CORP
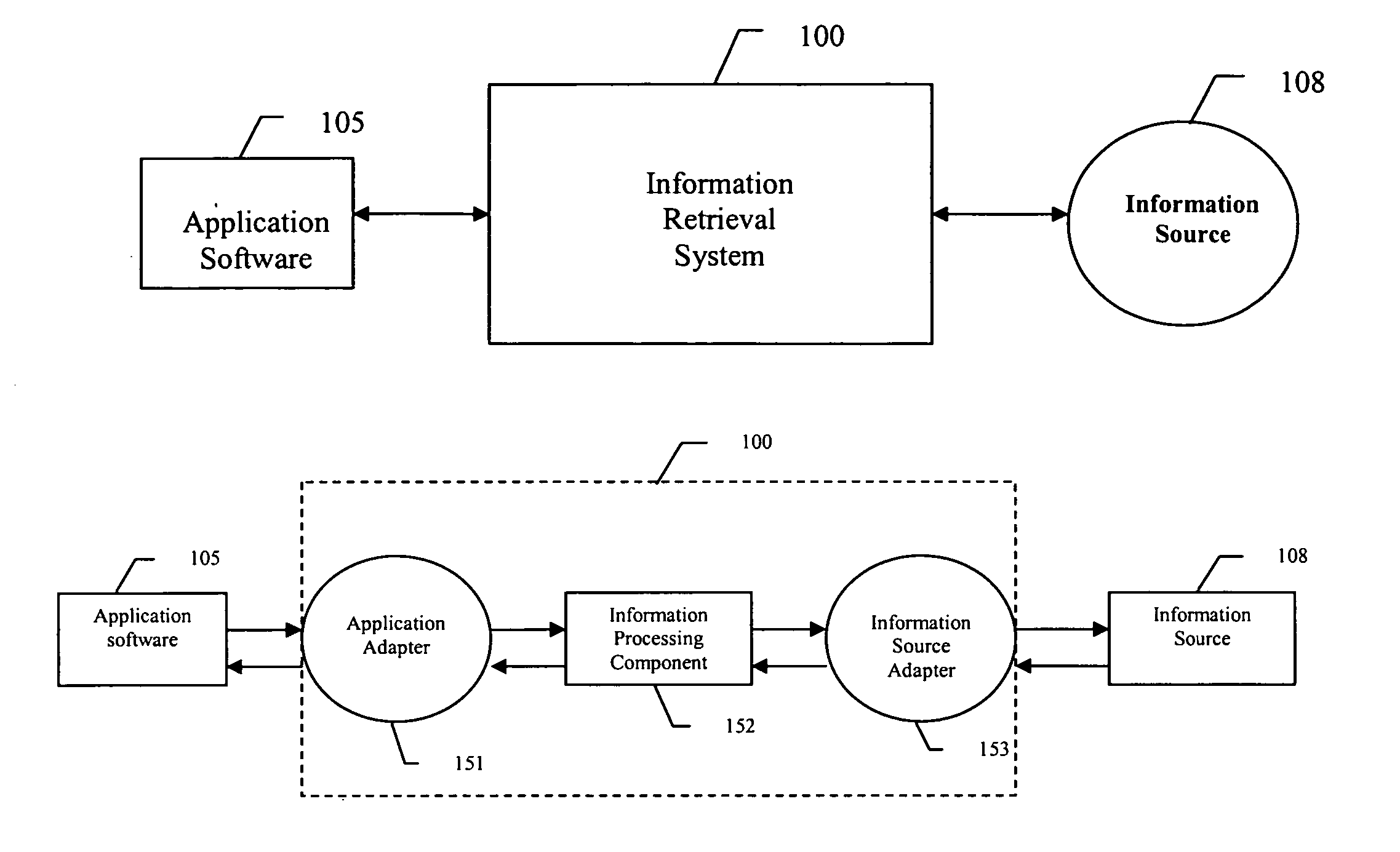
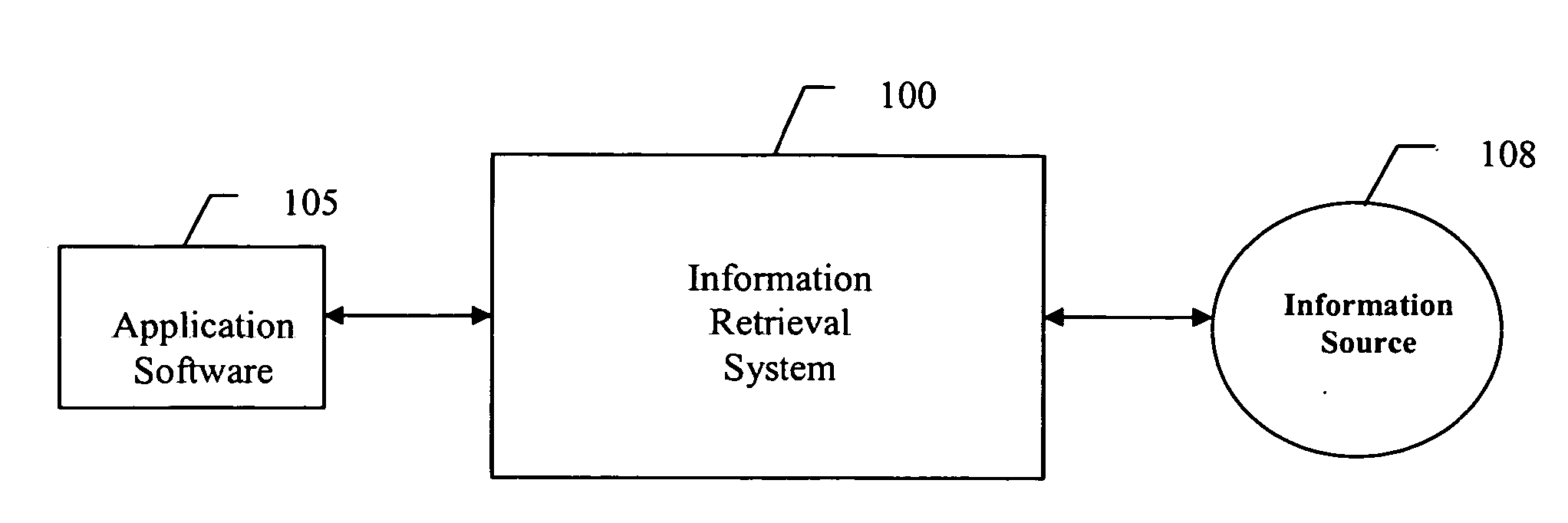
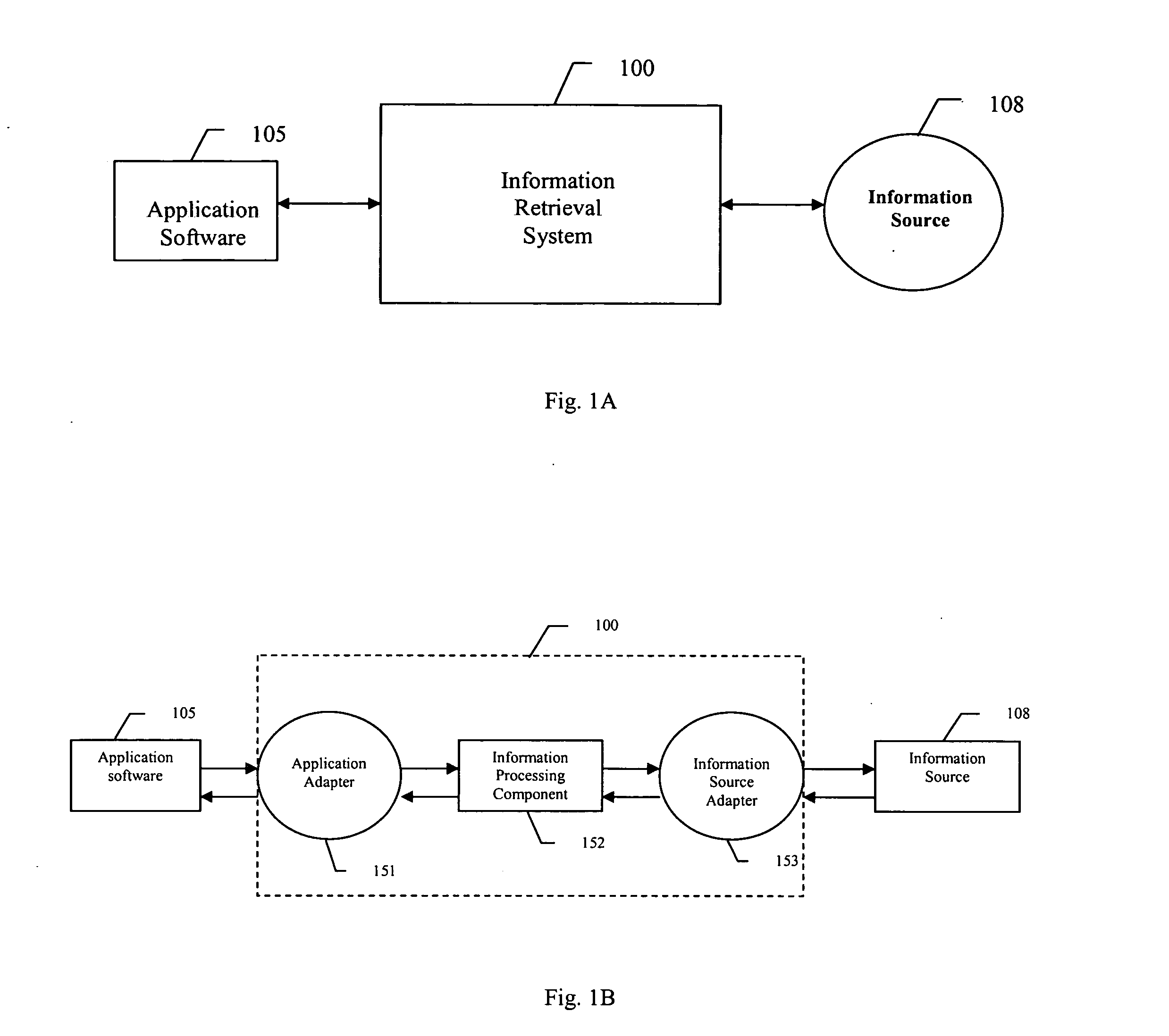
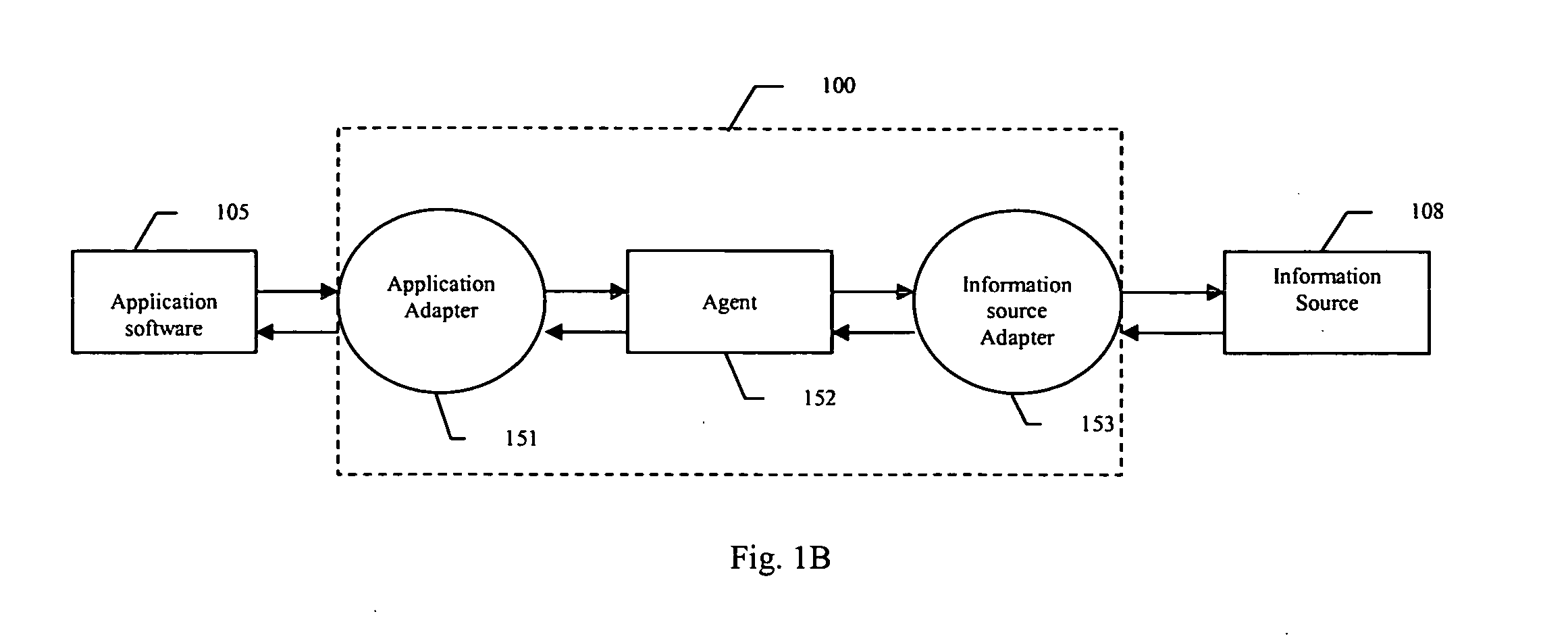
Method and system for assessing relevant properties of work contexts for use by information services
InactiveUS20050027704A1Weight increaseHeavy weightWeb data indexingDigital data processing detailsAdaptive weightingData source
An information retrieval system for automatically retrieving information related to the context of an active task being manipulated by a user. The system observes the operation of the active task and user interactions, and utilizes predetermined criteria to generate context representation of the active task that are relevant to the context of the active task. The information retrieval system then processes the context representation to generate queries or search terms for conducting an information search. The information retrieval system determines the relevance of a word to the context by utilizing an adaptive weighting system. The information retrieval system assigns varying weights to different attributes of a word and calculates an accumulated weight of the word by accumulating all weights assigned to the word. The attributes may include word size, style, location of the word, etc. The system then ranks the importance of words based on their respective accumulated weight, and chooses words that rank within a predetermined number from the top to form search terms to conduct an information search using various data sources.
Owner:NORTHWESTERN UNIV
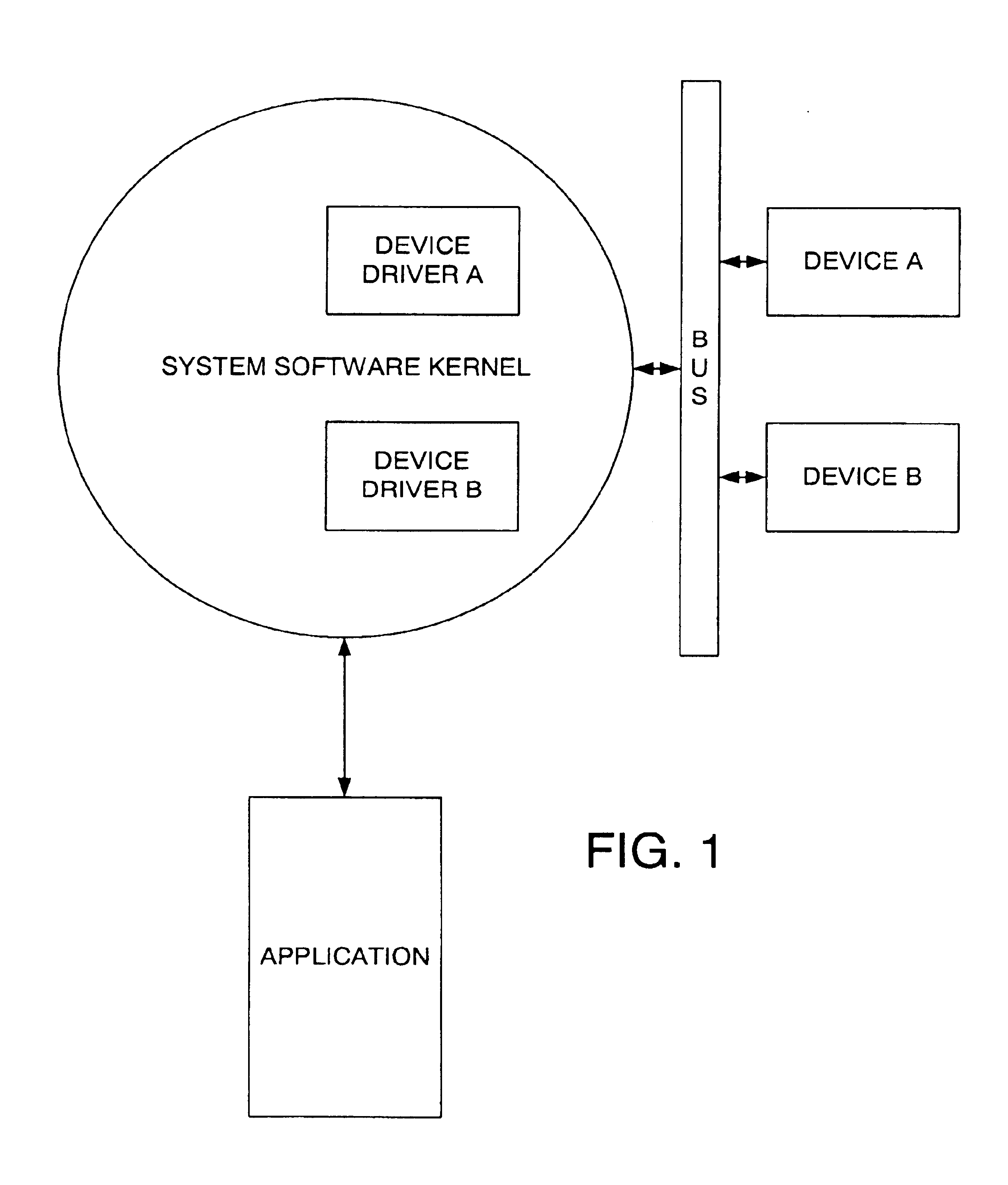
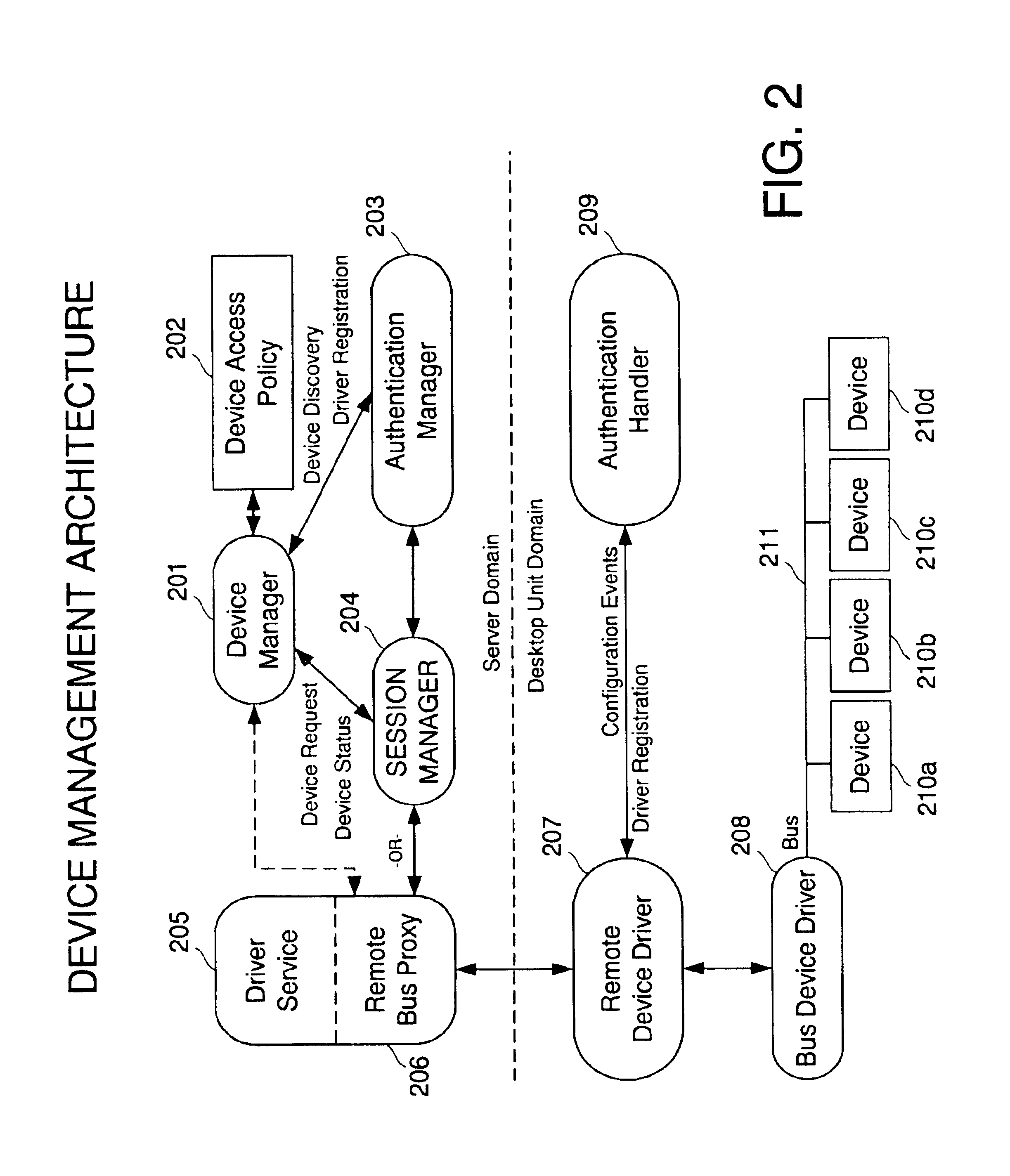
Remote device access over a network
The present invention provides a method for devices to be remotely accessed over a network. A remote device drive is coupled to a bus device driver at a network client. The remote device driver communicates to a remote bus proxy to a driver service in the server domain. A device manager provides responsibility for discovering services on network clients, enabling driver services to use the devices, notifying other driver services of the availability of devices, notifying clients of the permission to use a device by a service, and tracking connected devices.
Owner:ORACLE INT CORP
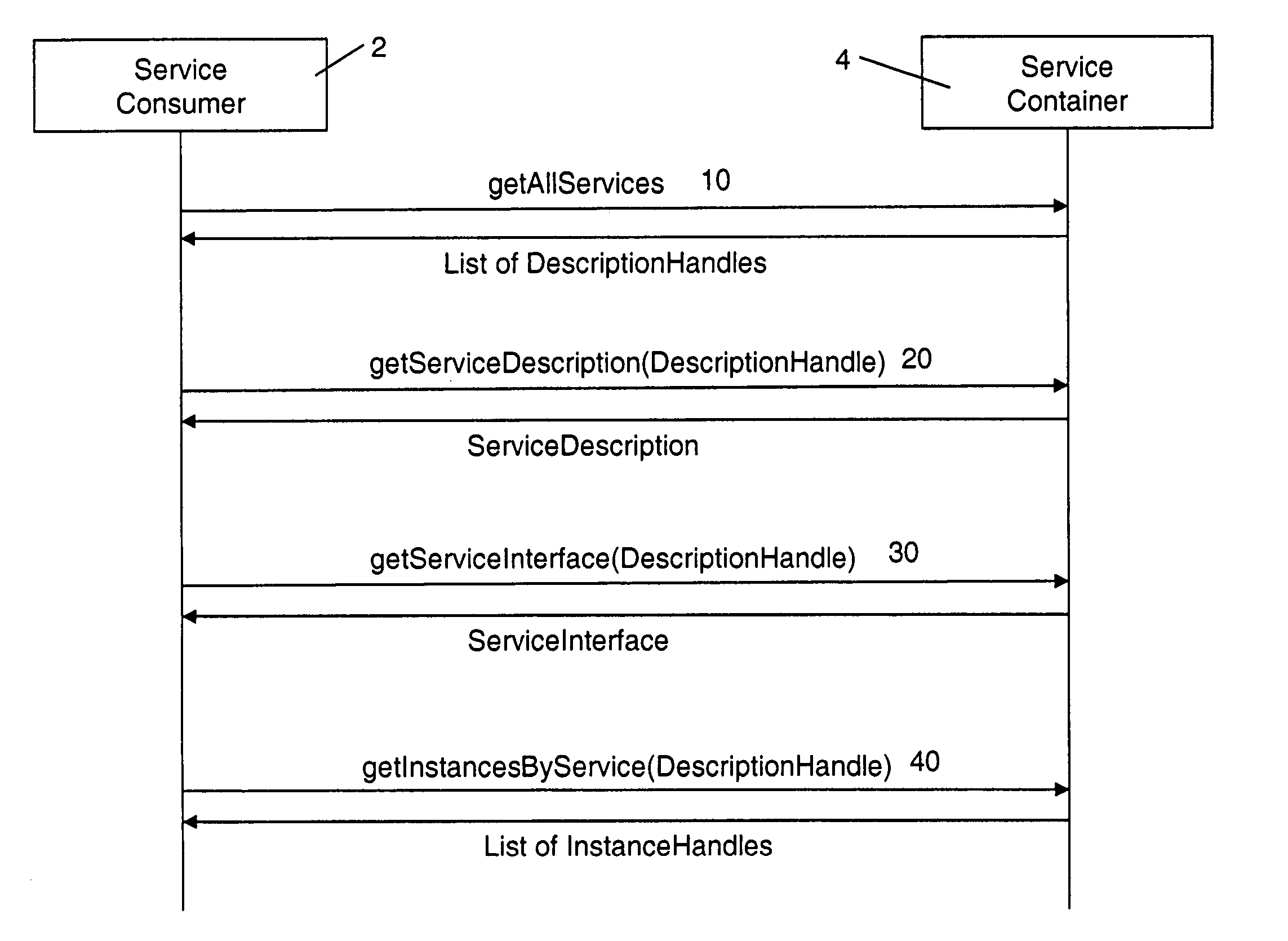
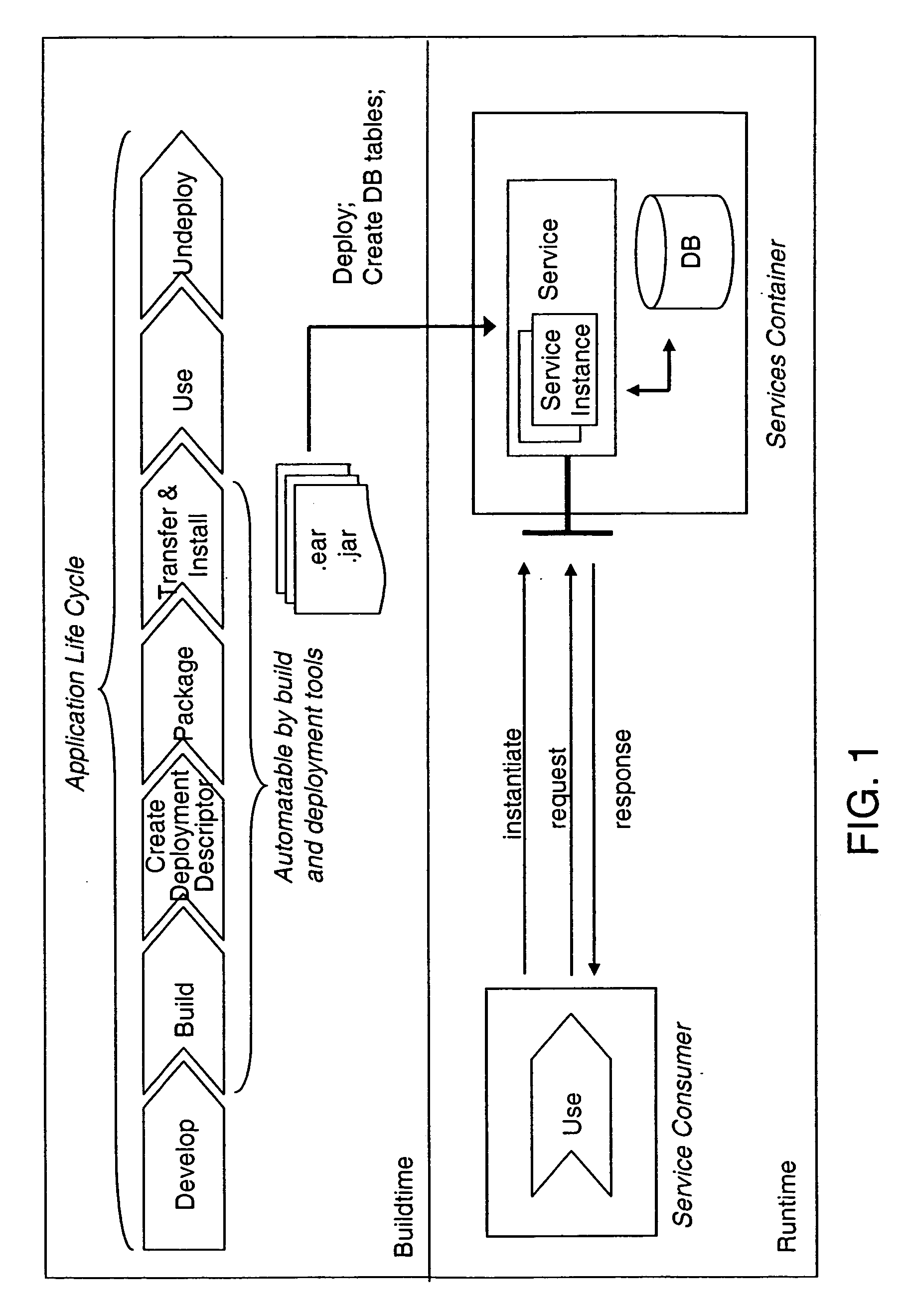
System and method for modeling and dynamically deploying services into a distributed networking architecture
InactiveUS20060029054A1Avoid disadvantagesMultiplex system selection arrangementsCircuit switching systemsHosting environmentNetwork architecture
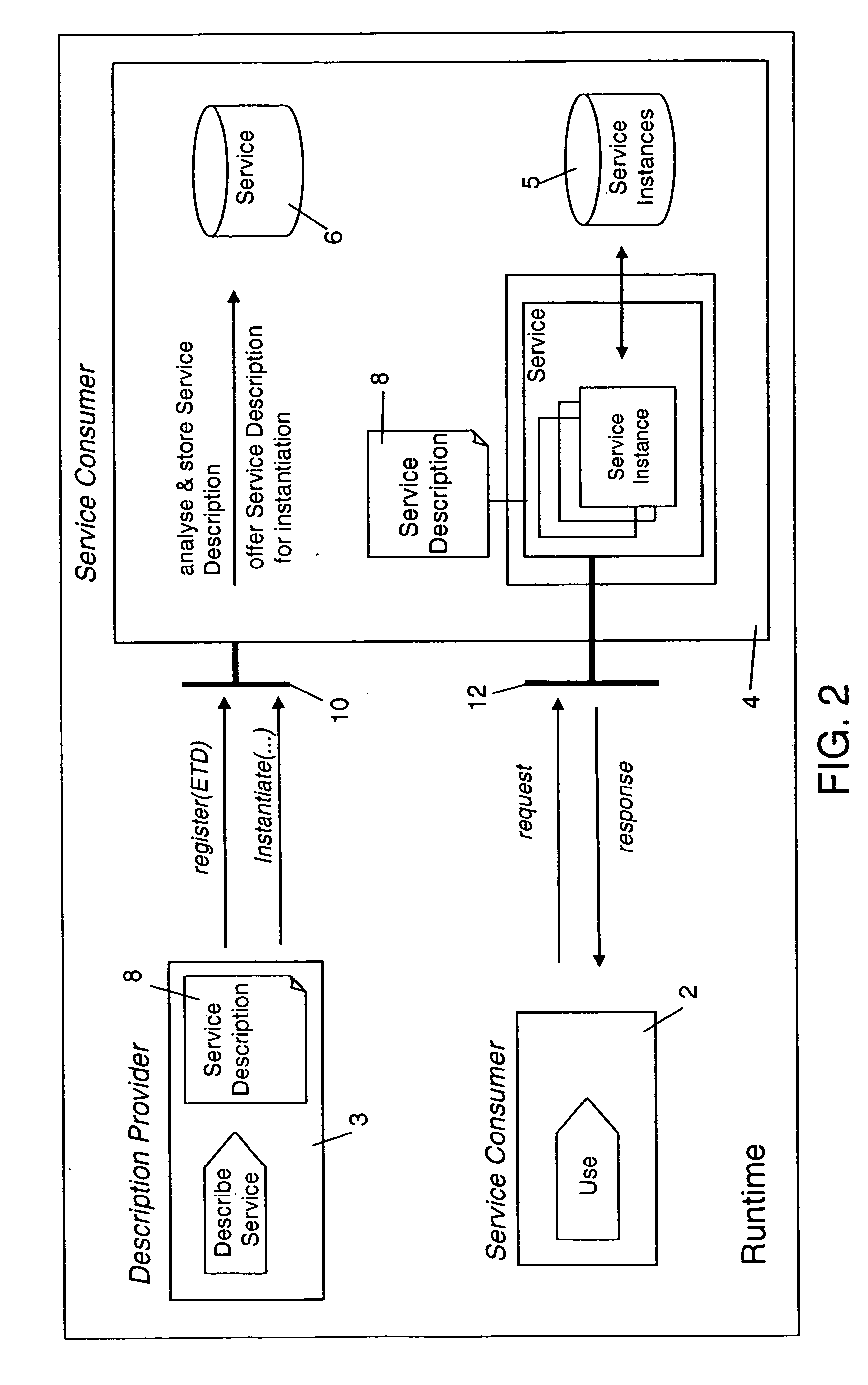
The present invention describes a new system and method for modeling and dynamically deploying services into a distributed networking architecture, especially in a service-oriented architecture. The service container being part of distributed networking architecture exposes its functionality as services. It provides a registration service for deploying service descriptions. Having created a new service description in any declarative description language (i.e. a description of a (stateful) service e.g. a stateful Web service), the description provider invokes the registration service at the service container that allows to register (i.e. deploy) that new service description during runtime without restarting service container. The service container is responsible to analyze and check the submitted new service description for validity, to store the service description and to make it available for interested services consumers for instantiation. If a new service has been successfully registered, a new service interface for accessing that new service is automatically created by the service container. Interested services consumers may query the hosting environment for the available services being hosted and to subsequently instantiate a new service. A service consumer may then invoke any exposed service operation on a given service instance which generally follows a request response pattern.
Owner:IBM CORP
Apparatus and methods for correlating messages sent between services
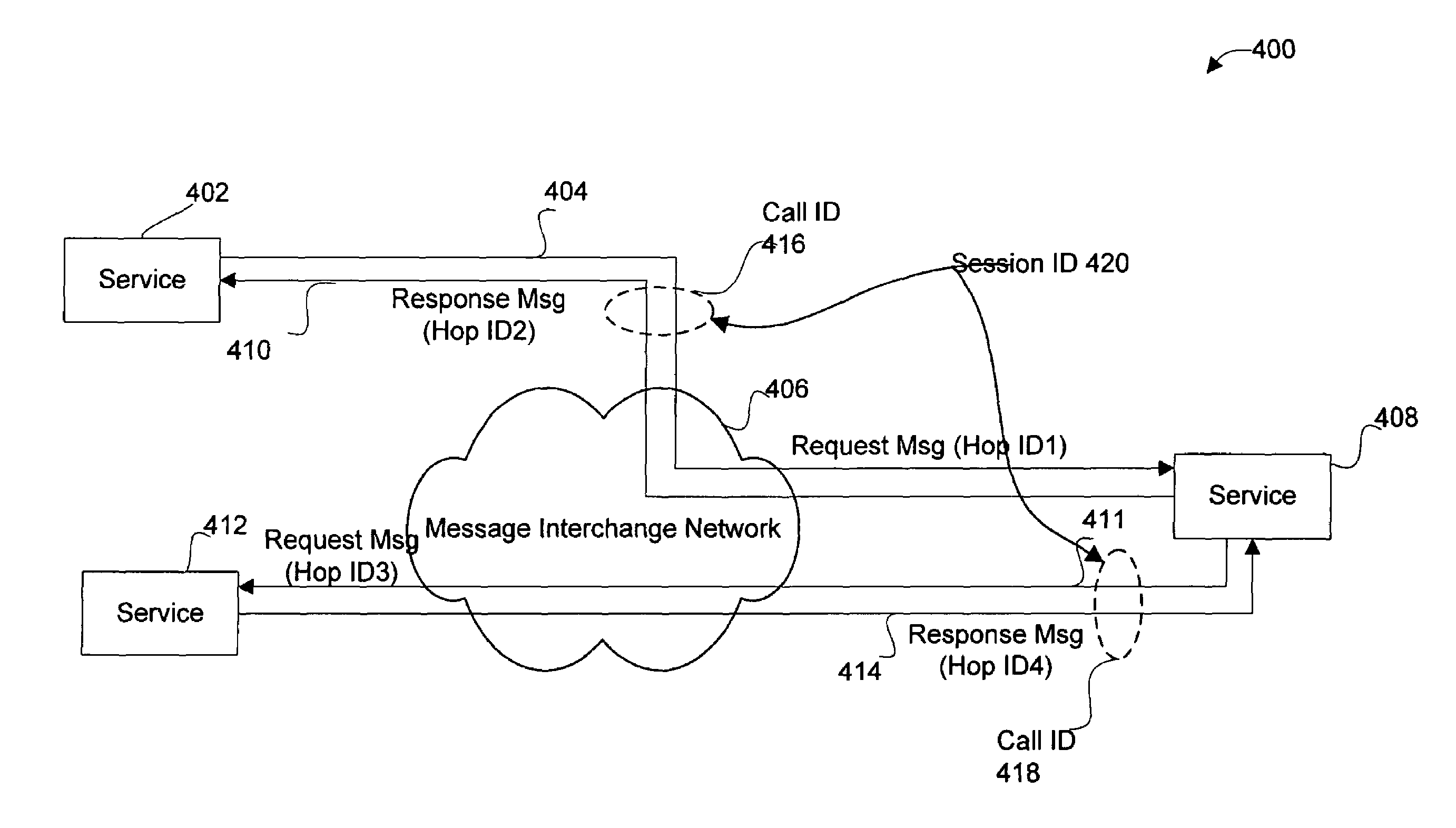
InactiveUS7249195B2Efficiently correlatedMultiplex system selection arrangementsInterprogram communicationRelevant informationUse of services
Disclosed are methods and apparatus for effectively correlating messages sent between services. In general, a message interchange network is configured to manage the use of services by remote entities or services within a computer network. In general terms, correlation information is stored for each message. The correlation information includes information for correlating each message with a specific call between two services and a specific session between two or more services.
Owner:SALESFORCE COM INC
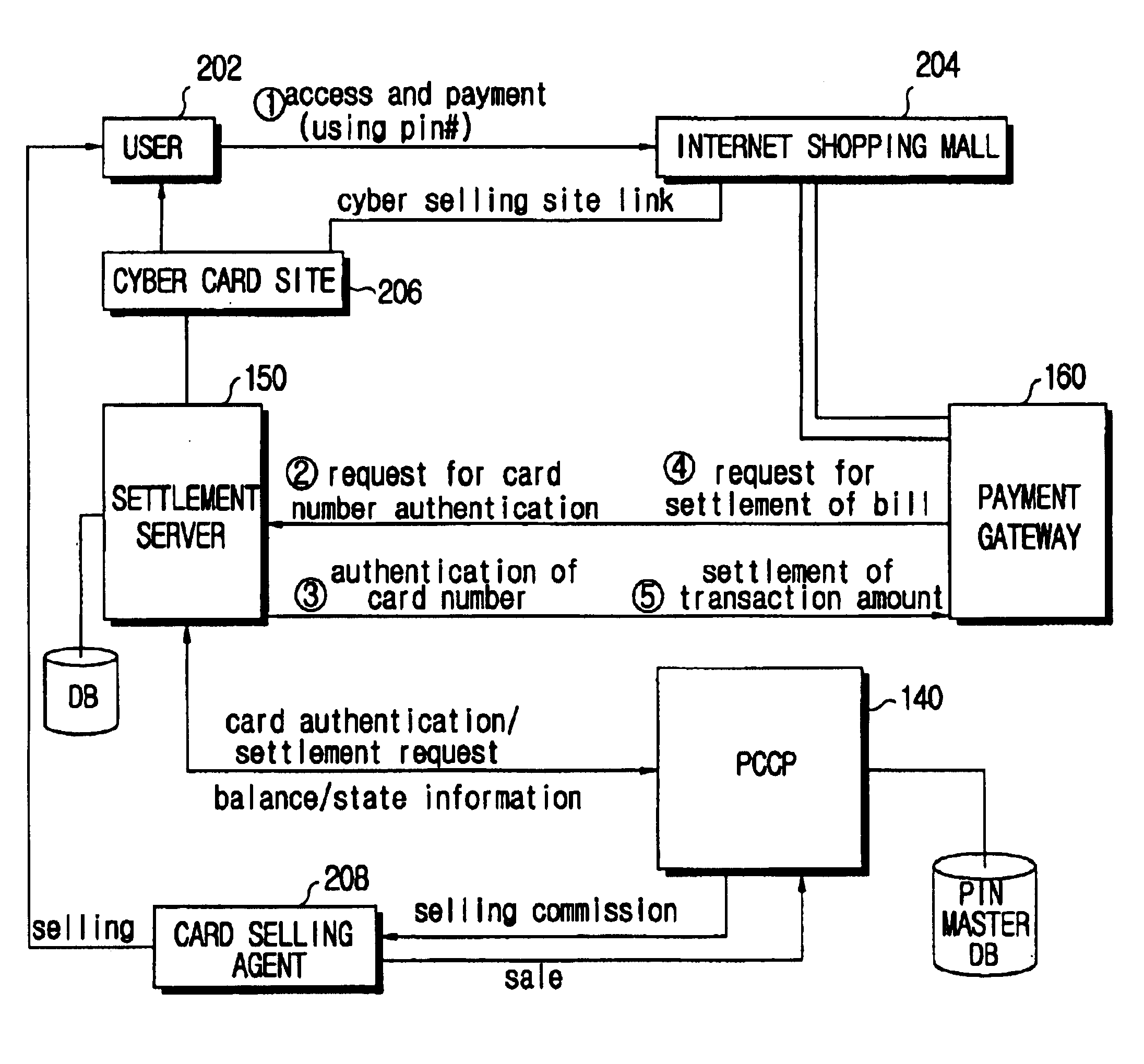
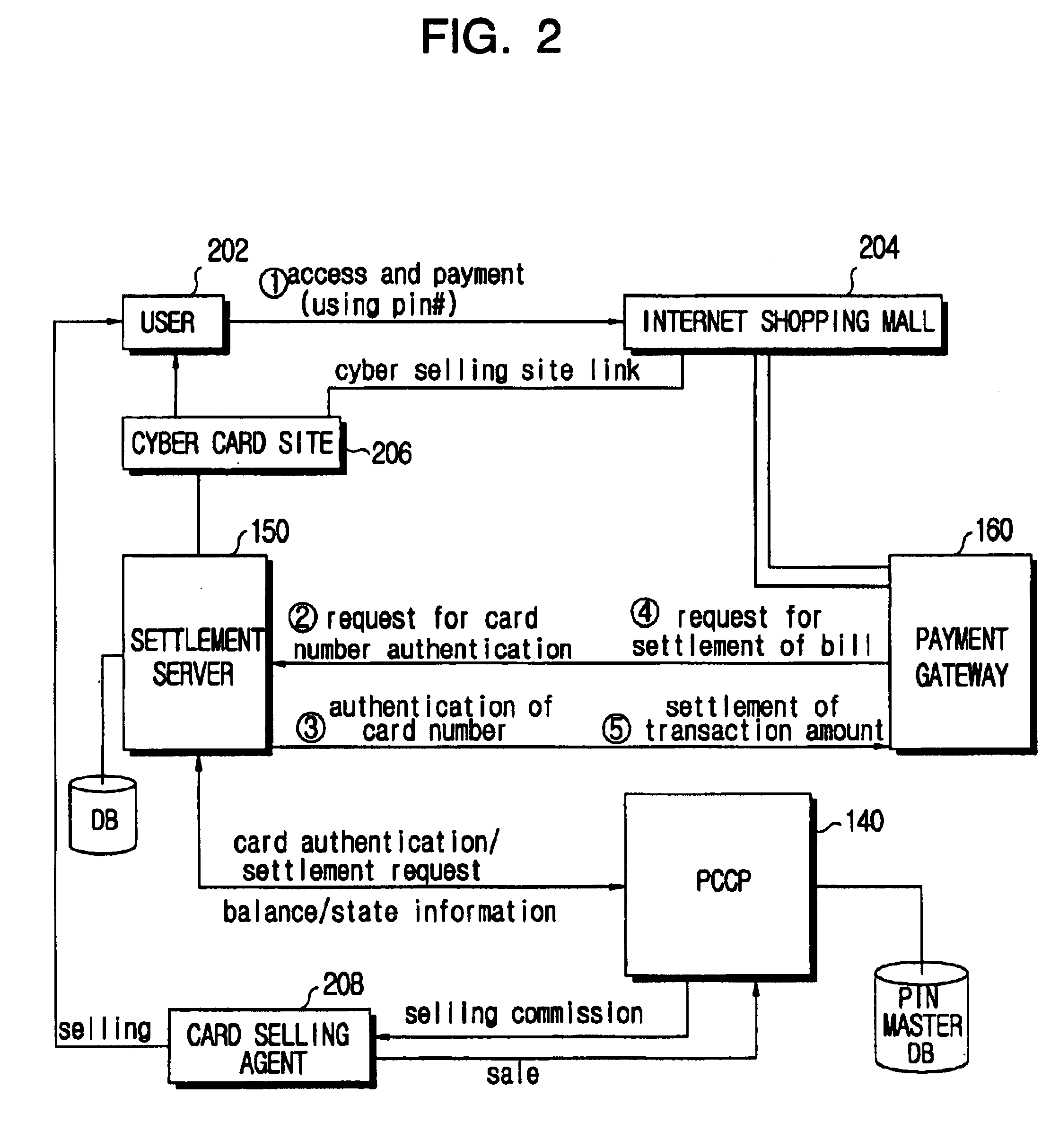
Electronic payment system using multifunctional prepaid cards and method of selling prepaid cards
InactiveUS6793135B1Pre-payment schemesVisual presentationComputer hardwarePersonal identification number
There are provided an electronic payment system using a multifunctional prepaid card which is commonly used in payment for use of services and purchase of goods, and a method of selling the multifunctional prepaid card. The electronic payment system includes a multifunctional prepaid card having a predetermined Personal Identification Number (PIN), shopping / service providing means for providing services and goods to a user of the multifunctional prepaid card and requesting the PIN of the multifunctional prepaid card for payment, and a prepaid card management system for managing state / balance information for PIN for the multifunctional prepaid card on a database, making a settlement by referring to the balance amount of the corresponding PIN if payment for a specific PIN is requested by the shopping / service providing means, and updating the settlement result on the database. Thus, according to the electronic payment system, a single multifunctional prepaid card can be comprehensively used in payment for use of various services and for purchases of goods.
Owner:GALAXIA COMM
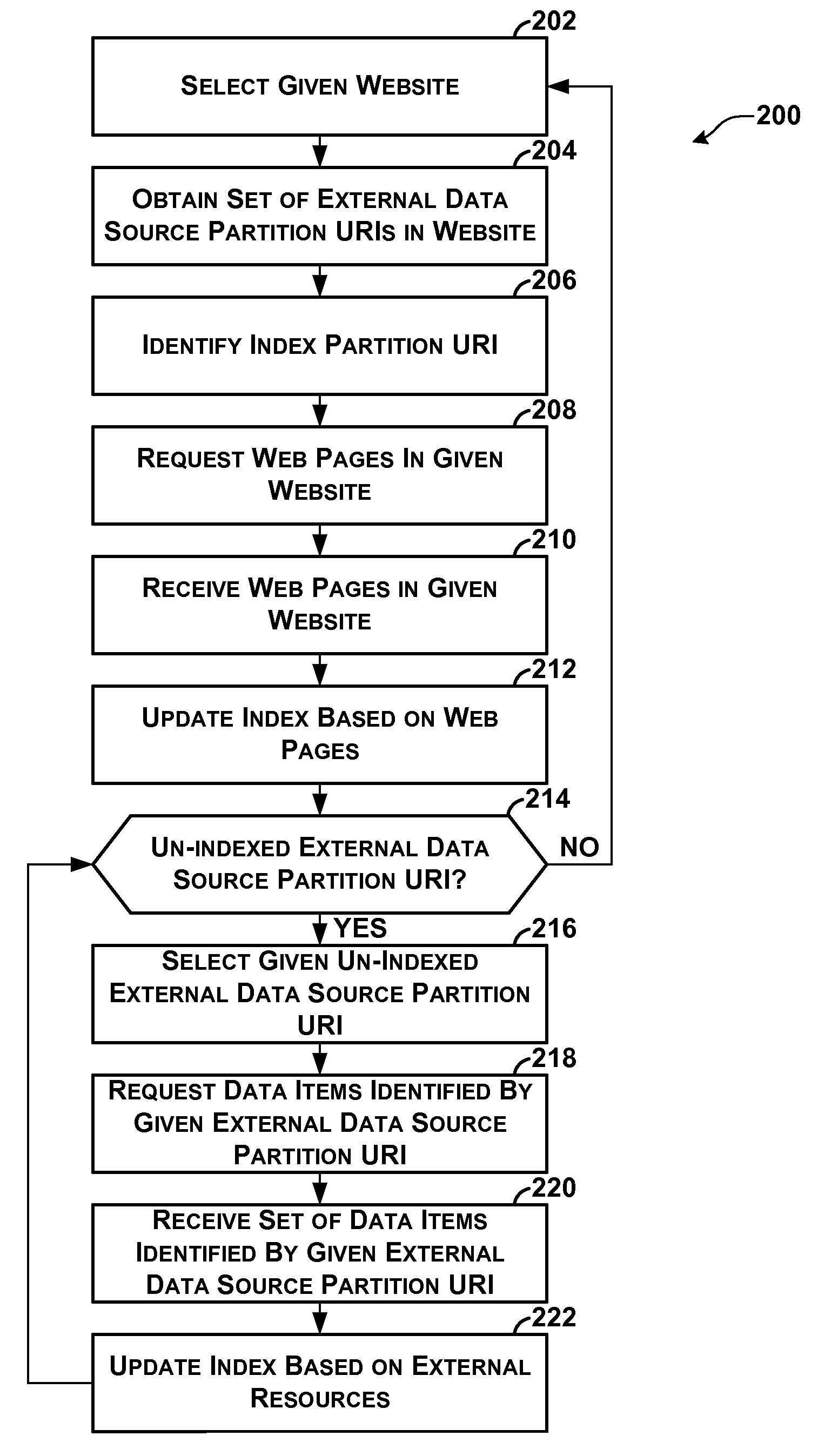
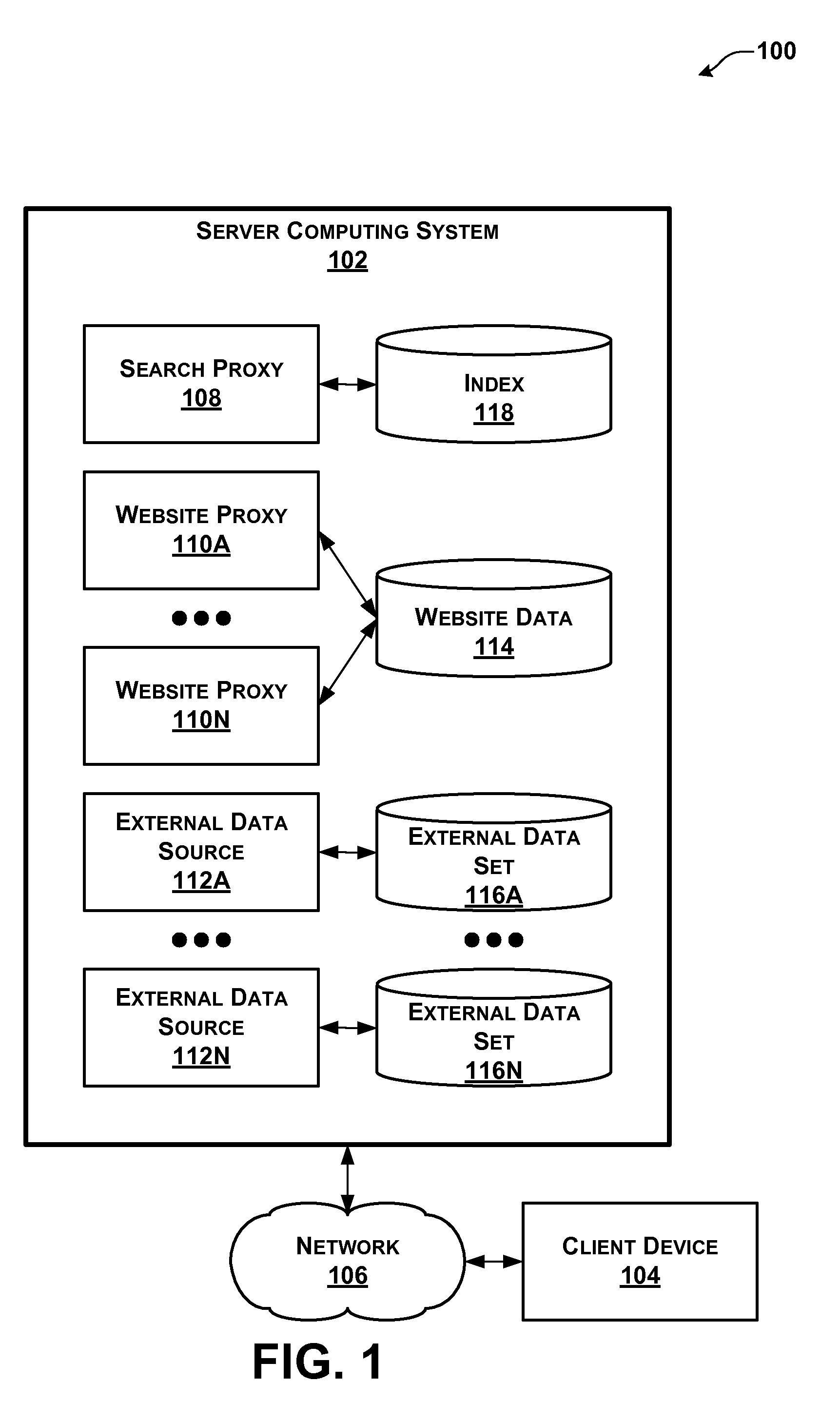
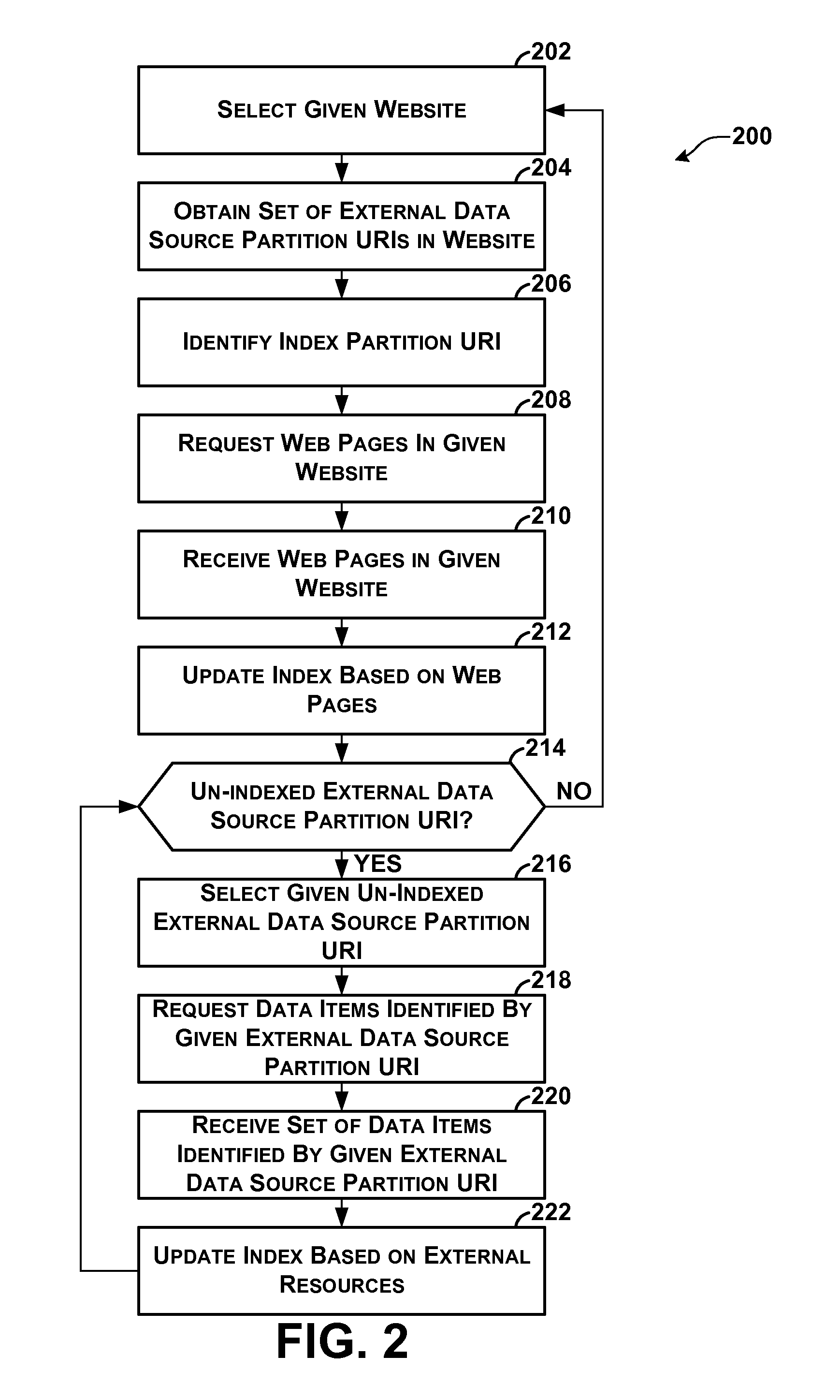
Indexing of Partitioned External Data Sources
ActiveUS20110022582A1Well formedWeb data indexingDigital data processing detailsWeb siteExternal data
A computing system hosts a plurality of websites, a plurality of external data sources, and a search service. External resources in each of the external data sources are partitioned among a plurality of external partitions. The search service automatically generates an index comprising index entries. The index entries are partitioned among a plurality of index partitions, each associated with one or more of the websites. For each given index partition, the index entries in the given index partition map terms to resources in the given set of resources that contain the terms. The given set of resources includes web pages in a given set of websites associated with the given index partition and external resources in external partitions used by the given set of websites. The search service uses the index entries in given index partition to identify resources in the given set of resources containing query terms.
Owner:MICROSOFT TECH LICENSING LLC
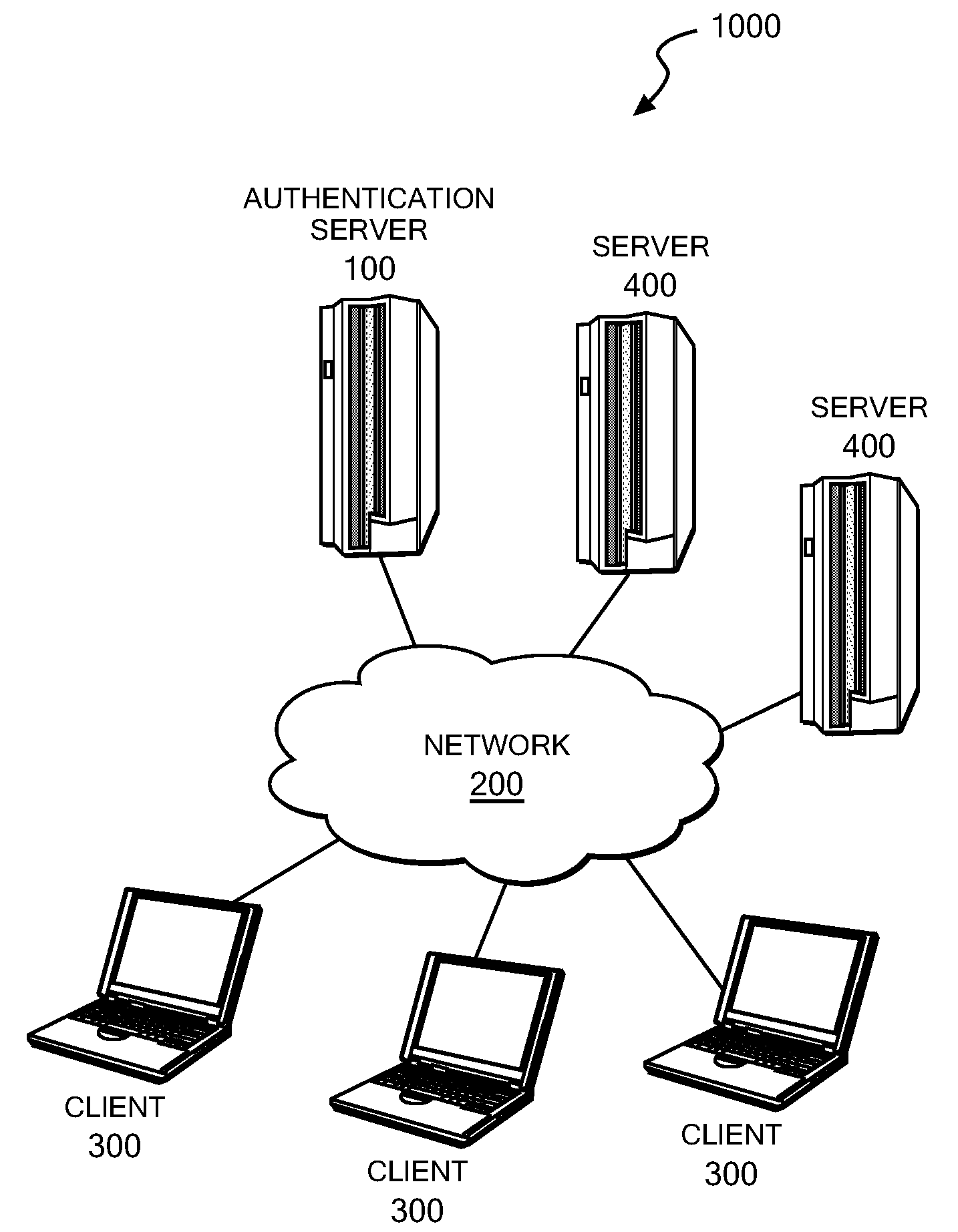
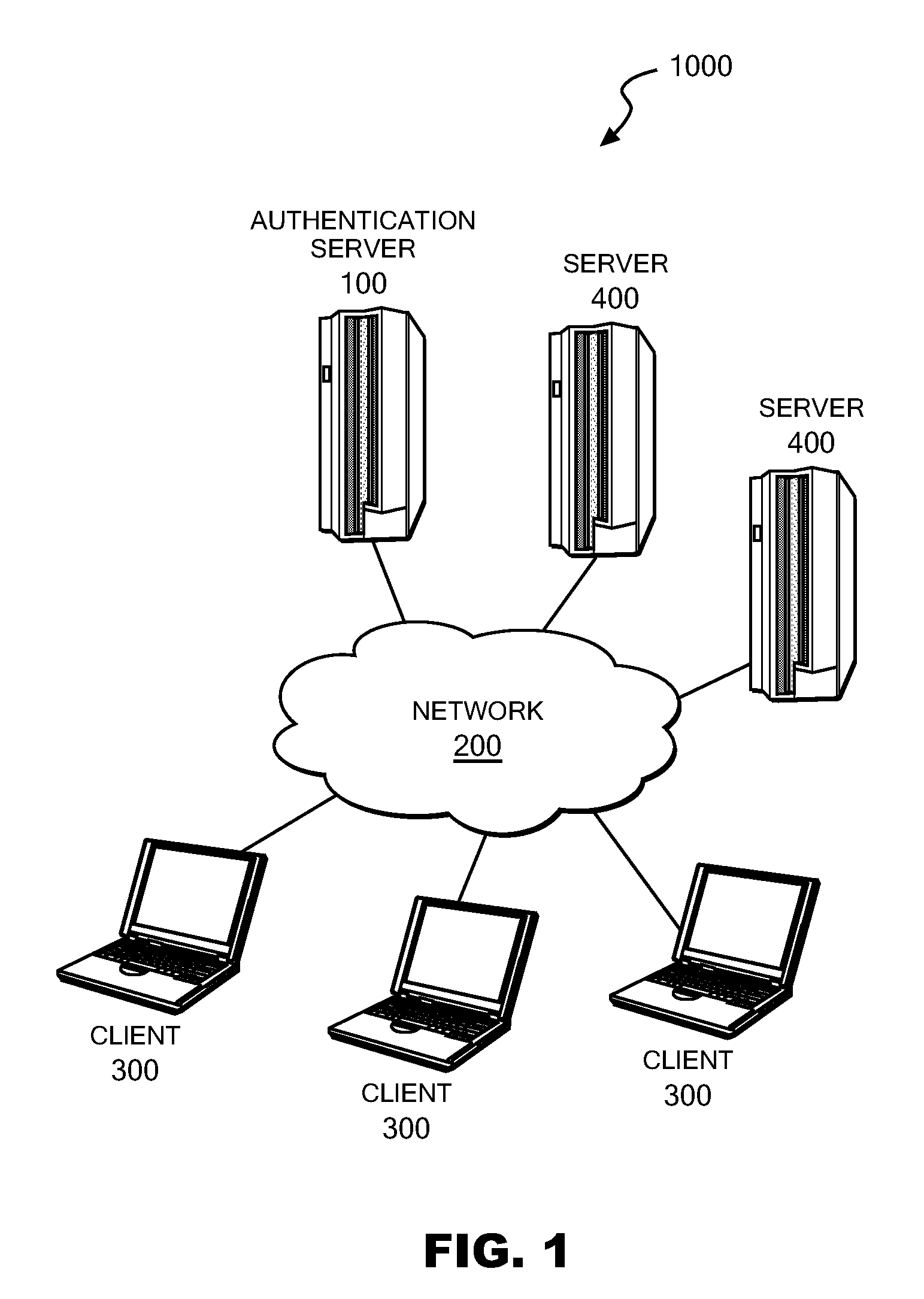
Authentication server, authentication method and authentication program
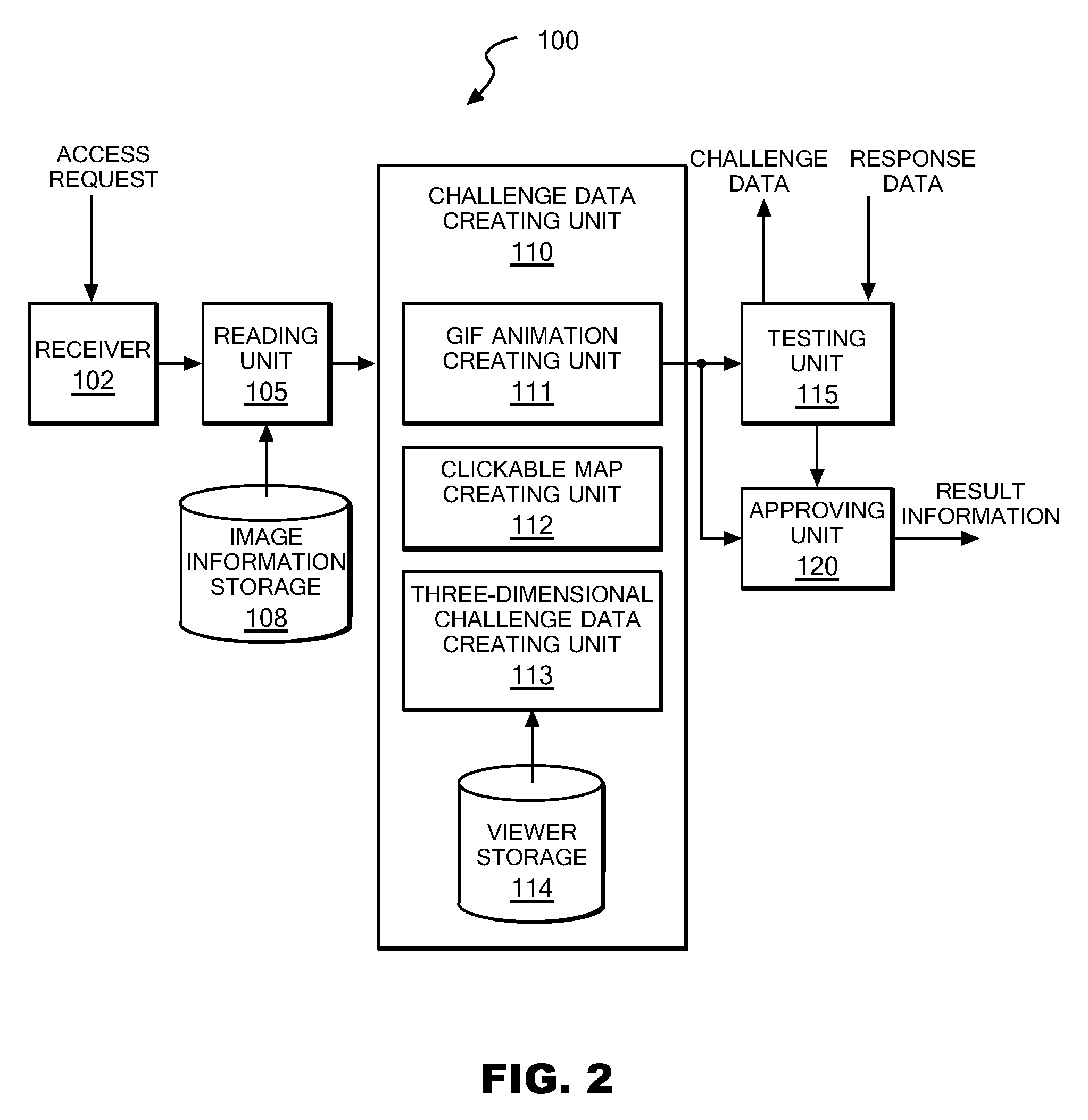
ActiveUS20090187986A1Digital data processing detailsUser identity/authority verificationUse of servicesAuthentication server
Upon receipt of a service use request from a client, an authentication server device reads one or more image information pieces from an image information storage storing multiple image information pieces each containing one or more known symbols, one or more dummy symbols, or both of them, and thereafter creates challenge data using the one or more read image information pieces so that one or more two-dimensional images each containing one or more of the known symbols and one or more two-dimensional images each containing one or more of the dummy symbols can be presented to the user of the client, one image at a time. Upon receipt of response data, the authentication server device judges whether or not the received response data matches the one or more known symbols contained in the challenge data, and approves the service use of the client device if the match is confirmed.
Owner:IBM CORP
Web service provider and authentication service provider
InactiveUS20050015585A1Simple and efficient authenticationEffective serviceUser identity/authority verificationWeb serviceService provision
A Web service providing method of a Web service provider providing a Web service comprises a decoding request transmission step transmitting, in response to a request from a client, a decoding request of Web service use permission information related to permission of use of the Web service, to an authentication service provider that provides a service related to authentication, and a decode response reception step, receiving a decode response of the Web service use permission information issued in response to said decoding request of the Web service use permission information, from the authentication service provider.
Owner:RICOH KK
Payment service capable of being invoked from merchant sites
A computer-implemented service acts as an intermediary between merchant sites and users thereof, and enables the users to purchase items on the merchant sites without having to create accounts with such sites. A user may invoke the service from a web page of a merchant site, and complete a purchase transaction, without having to browse away from the merchant site. The service may either forward the user's payment information to the merchant's system to enable the merchant to charge the customer, or may charge the user on behalf of the merchant. In some implementations, the service enables users to make single-action purchases from the merchant sites.
Owner:AMAZON TECH INC
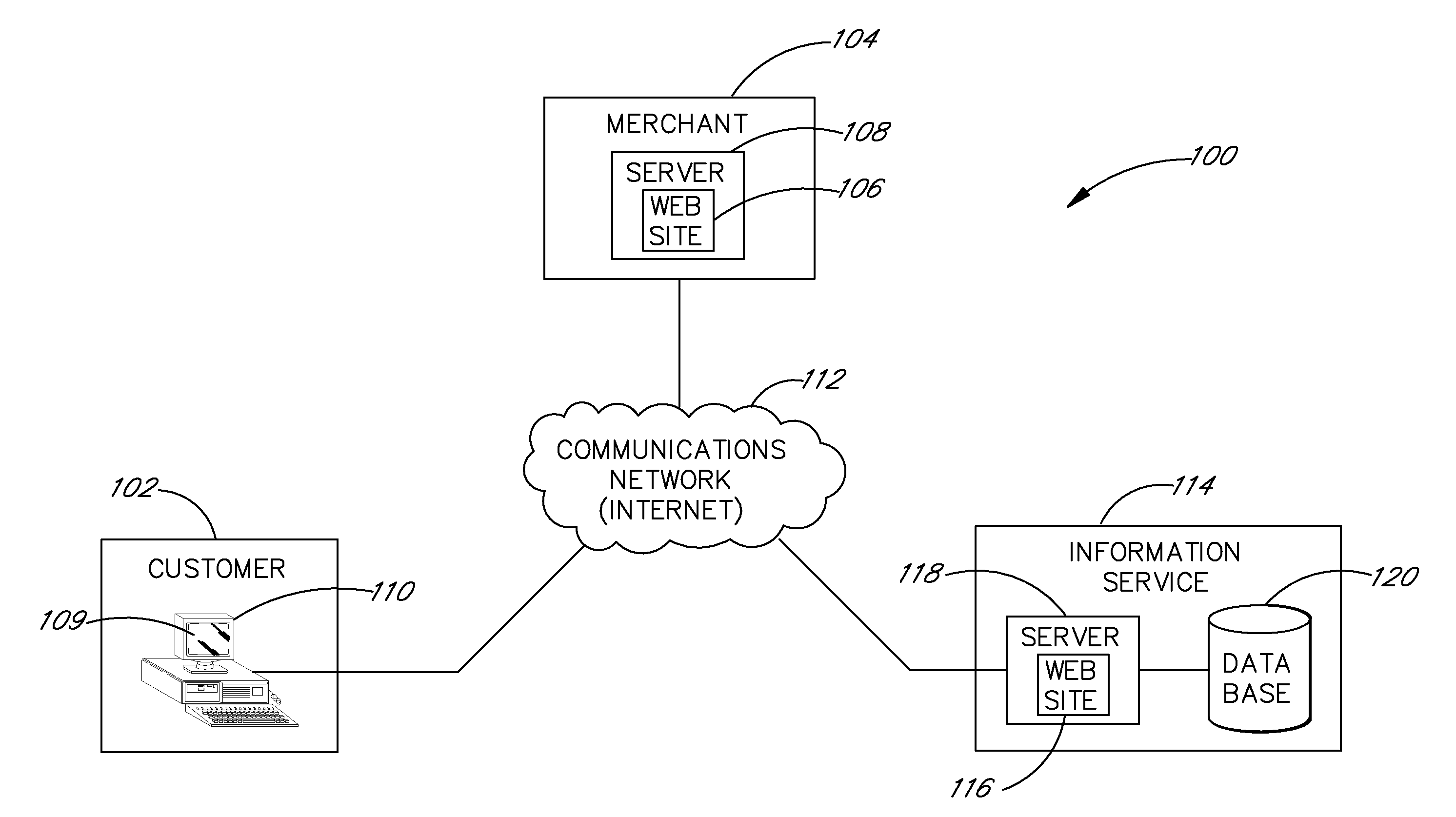
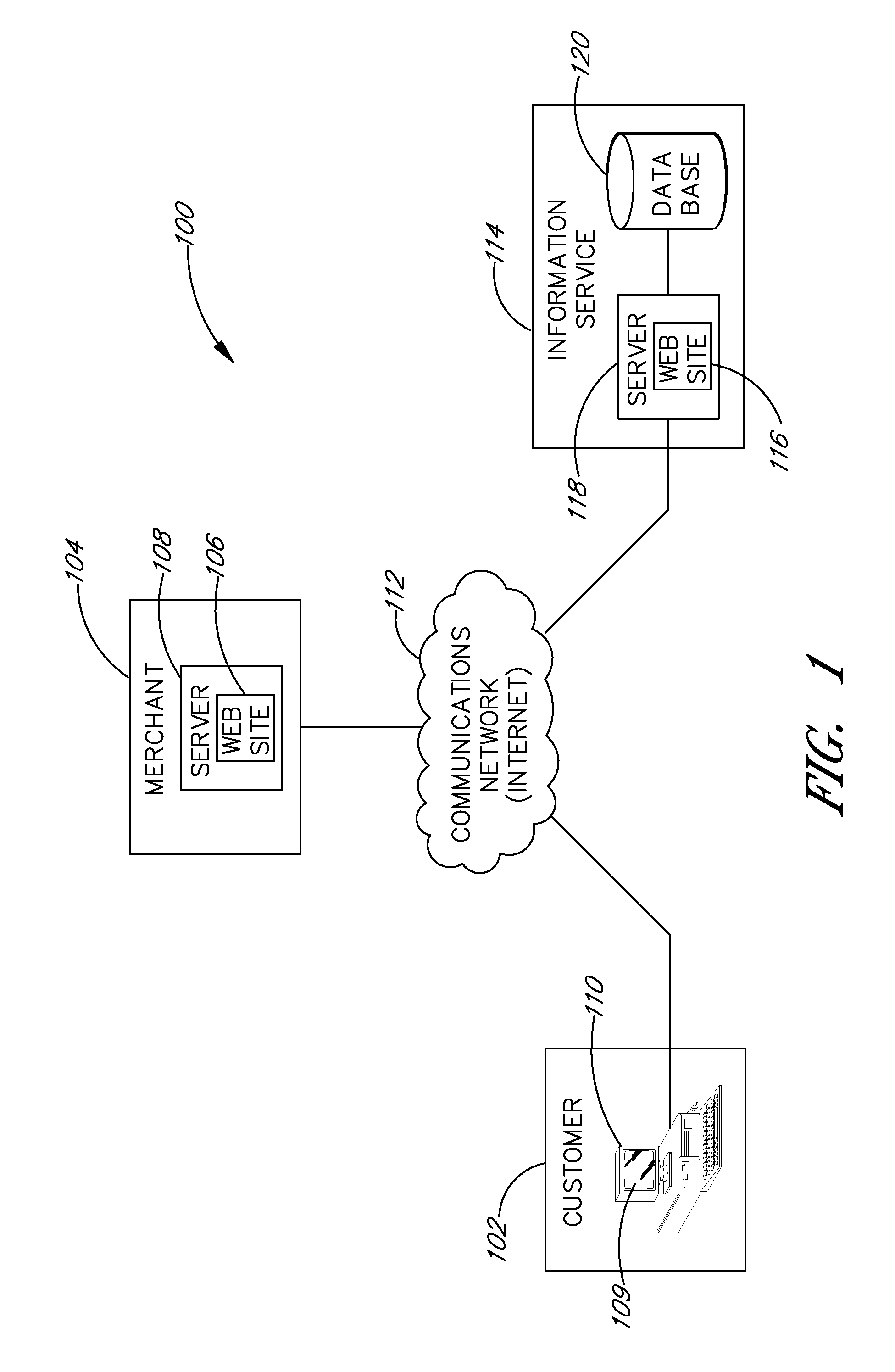
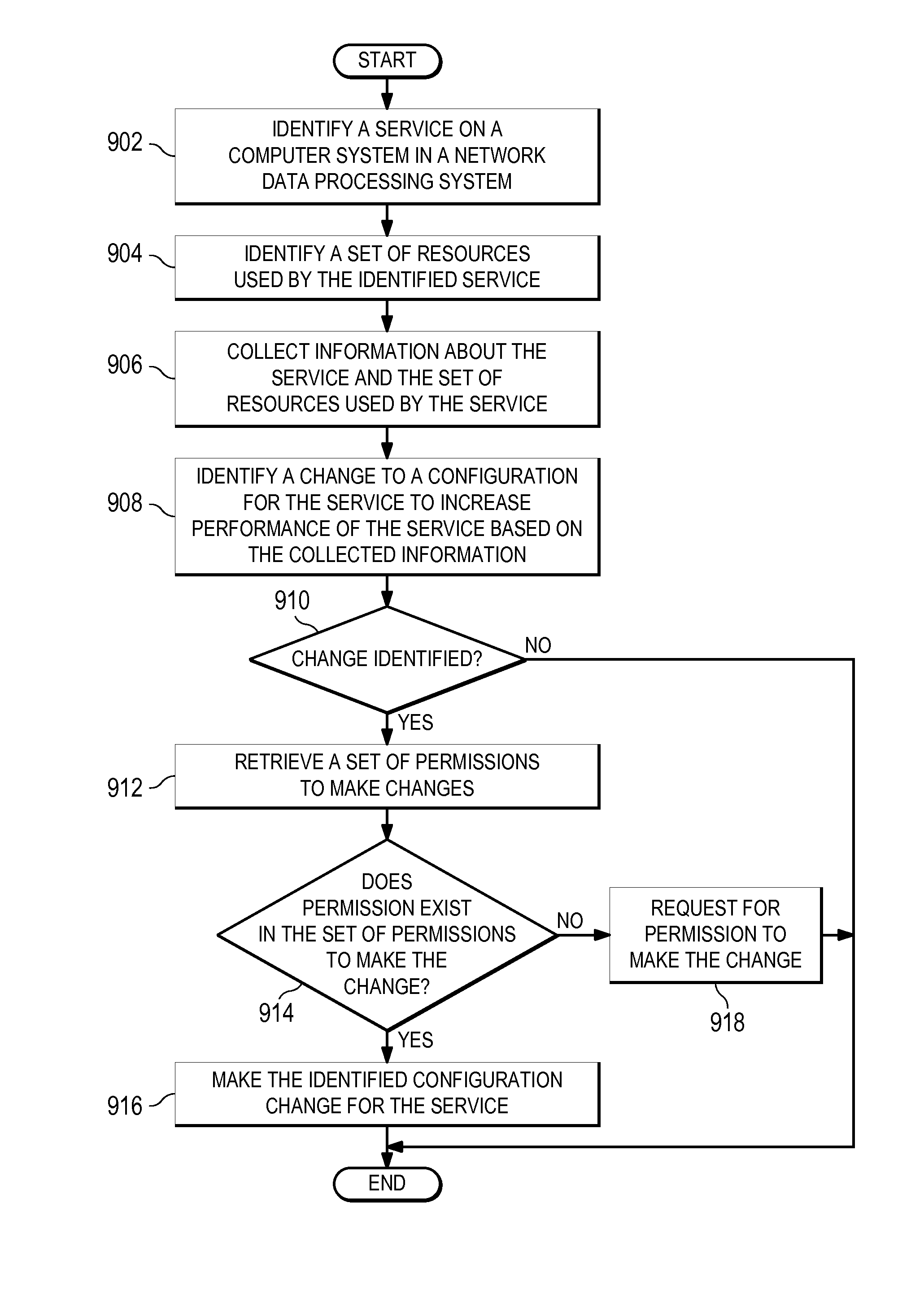
Resource configuration for a network data processing system
ActiveUS20130326032A1Improve service performanceDigital computer detailsProgram controlData processing systemComputerized system
A method for managing a service is disclosed. A program system running on a computer system in a network data processing system identifies the service on the computer system and a set of resources used by the service. The program system collects information about the service and the set of resources used by the service. The program system uses the information collected to identify a change to a configuration for the service which will increase performance of the service. The program system then makes the identified change to the configuration for the service.
Owner:IBM CORP
Secure wireless sales transaction using print information to verify a purchaser's identity
InactiveUS20030001459A1Reduce credit fraudPiezoelectric/electrostriction/magnetostriction machinesBiometric pattern recognitionThird partyWireless transceiver
A wireless transceiver device is used to conduct a secure electronic sales transaction. In an embodiment, the wireless device is used to obtain a fingerprint of the individual wanting to make a purchase. The wireless device then transmits the fingerprint to a device coupled to a cash register, which sends the fingerprint to a third party verification service. The third party verification service uses the received fingerprint to verify the identity of the purchaser by matching the received fingerprint to fingerprint data stored in a database. The identity of the purchaser can then be sent to the cash register and to a credit service. The credit service uses the data from the third party verification service to approve sales information received from the cash register and to prevent the unauthorized use of a credit account.
Owner:SONAVATION INC
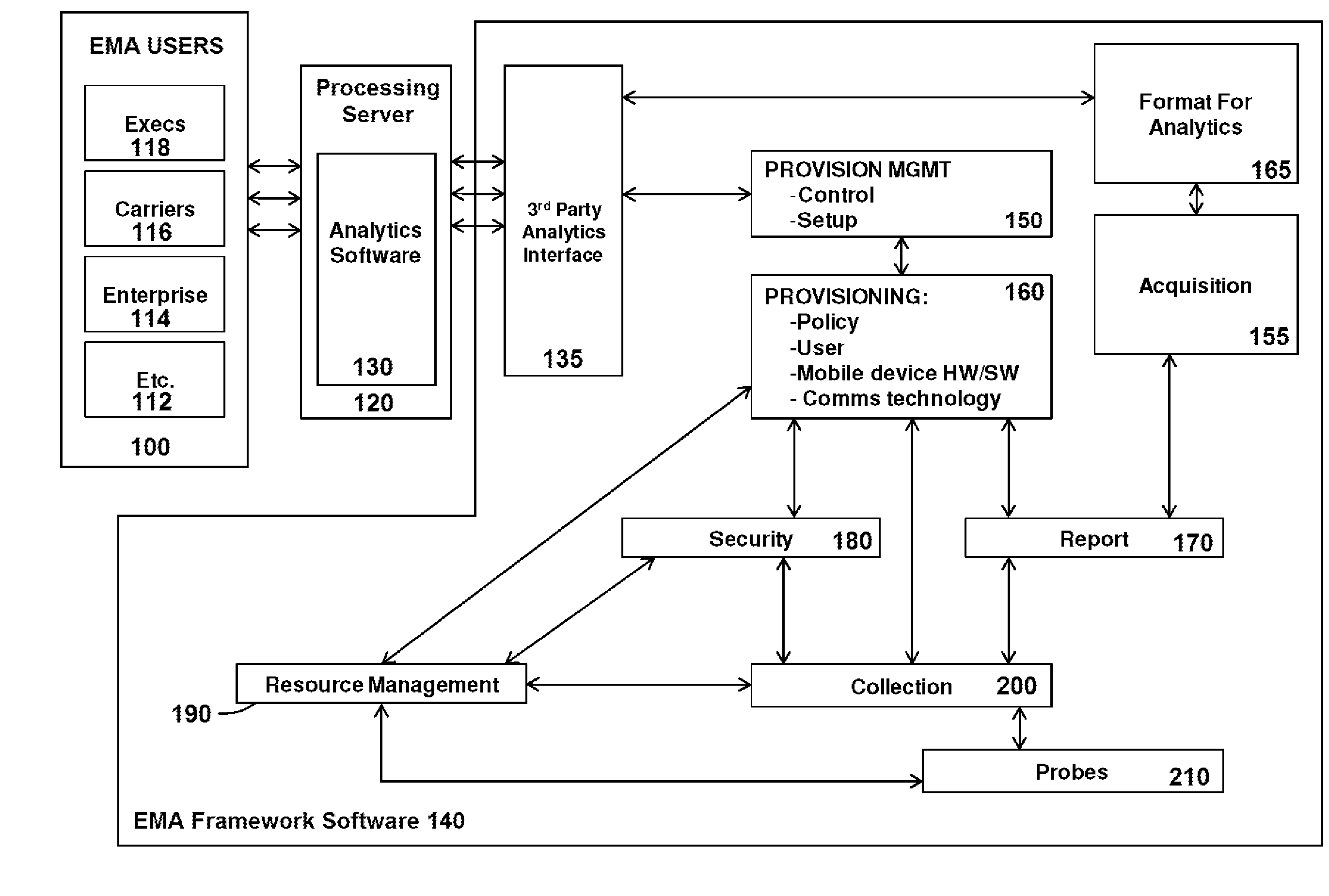
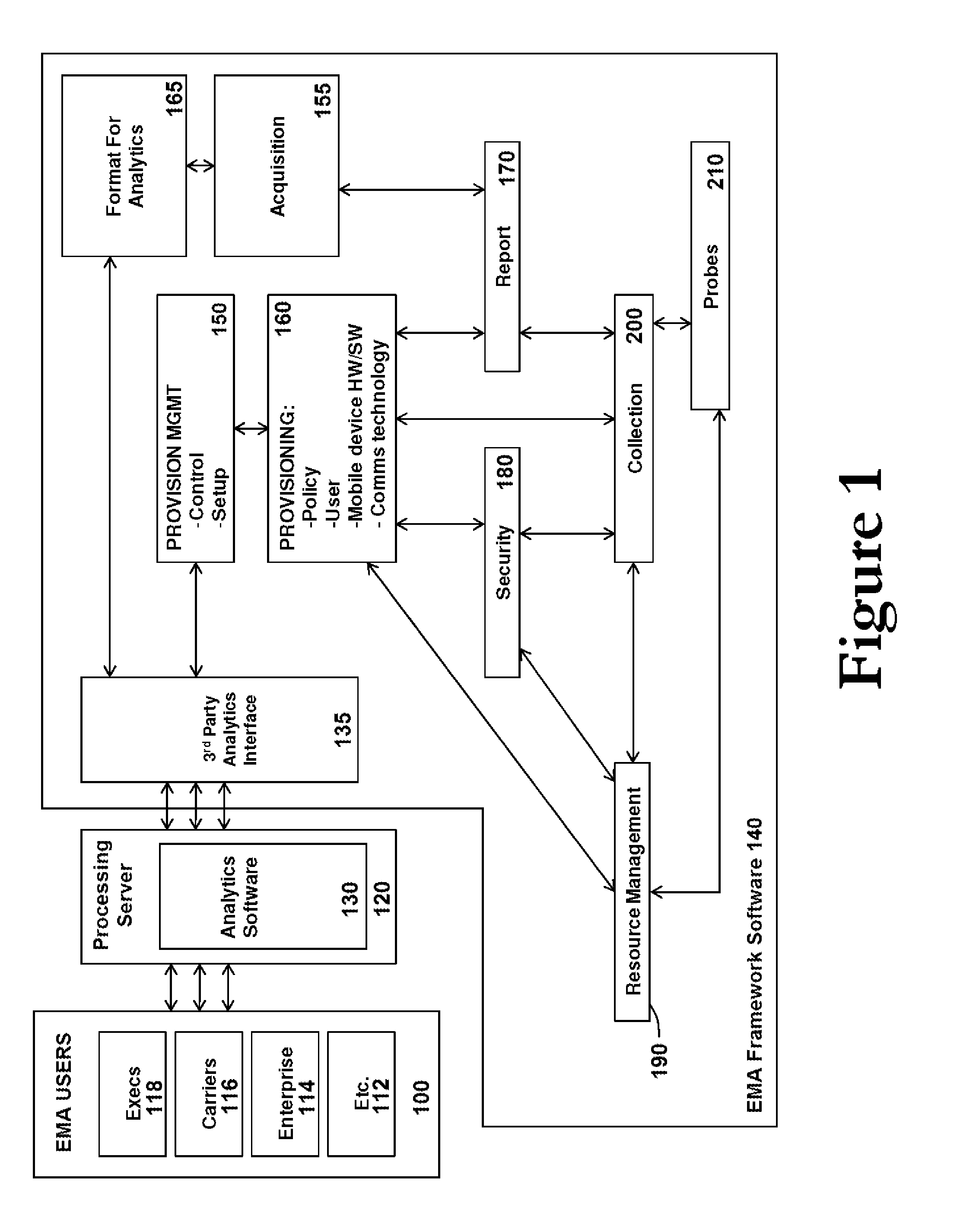
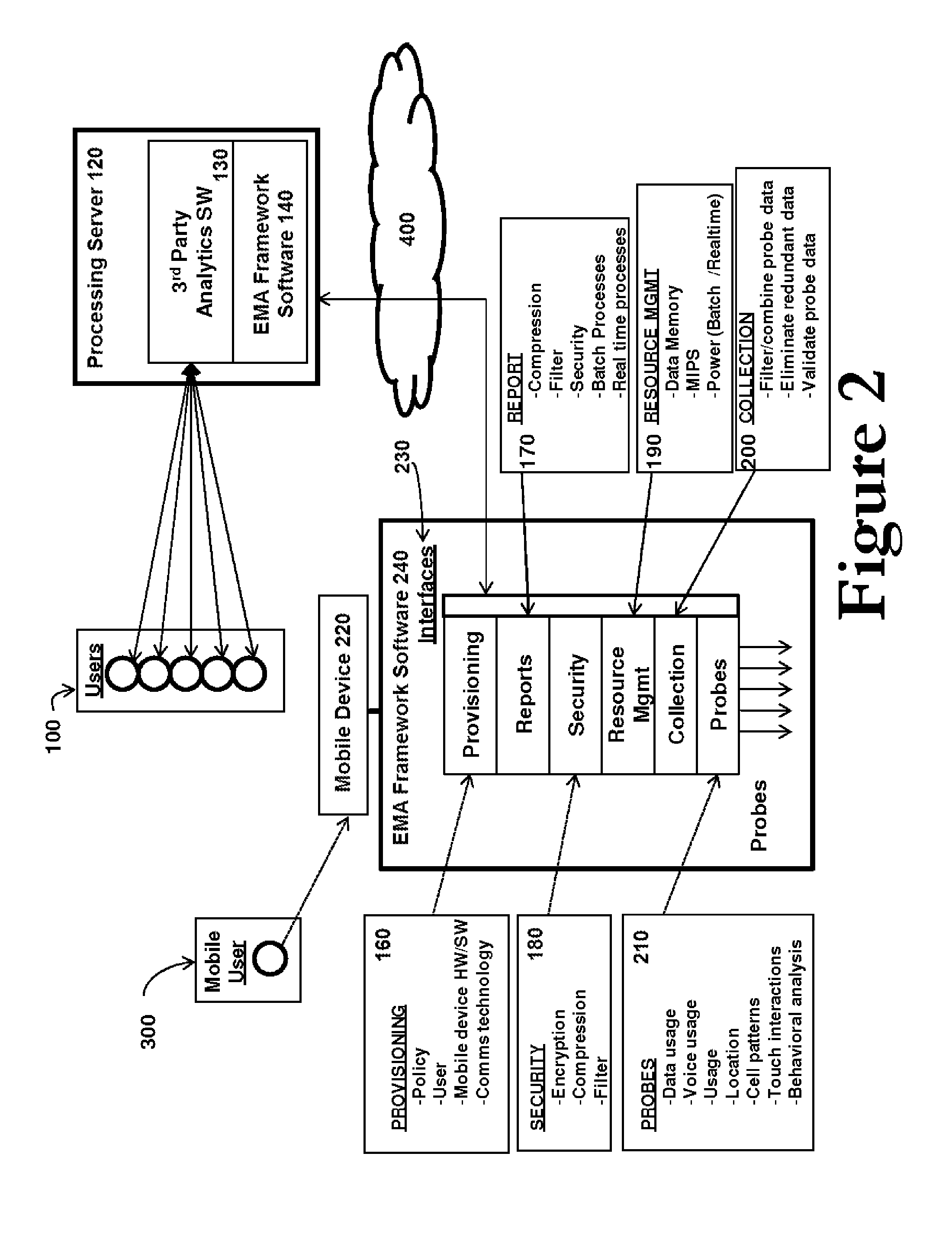
Embedded mobile analytics in a mobile device
InactiveUS20100041391A1Provide informationReduce in quantitySecurity arrangementThird generationUse of services
A method or process enables the collection of data from mobile devices and mobile networks using filtering, compression, encryption, memory management, and power management technologies to collect mobile device metrics at the mobile device (client side), and then transmit these metrics from the mobile device to a server for processing by analytics software. The analytics processing may also occur directly on the mobile device. Policies are determined and configured at the processing server to drive and control the mobile device metrics captured, which may include but are not limited to, data usage (e.g. time of day, amount of data sent / received), voice usage (e.g. time of day, calls in / out of network, dropped calls, call duration), the location of the mobile device, cell patterns (e.g. problem cells, roaming), touch interactions, behavioral analysis (programs used, services uses), battery performance, CPU usage, memory usage, network usage (e.g. 2G, 3G, 3.5G, 4G, Wi-Fi, WiMAX), and the like.
Owner:TAPROOT SYST
Multiple Data Services Over a Distributed Antenna System
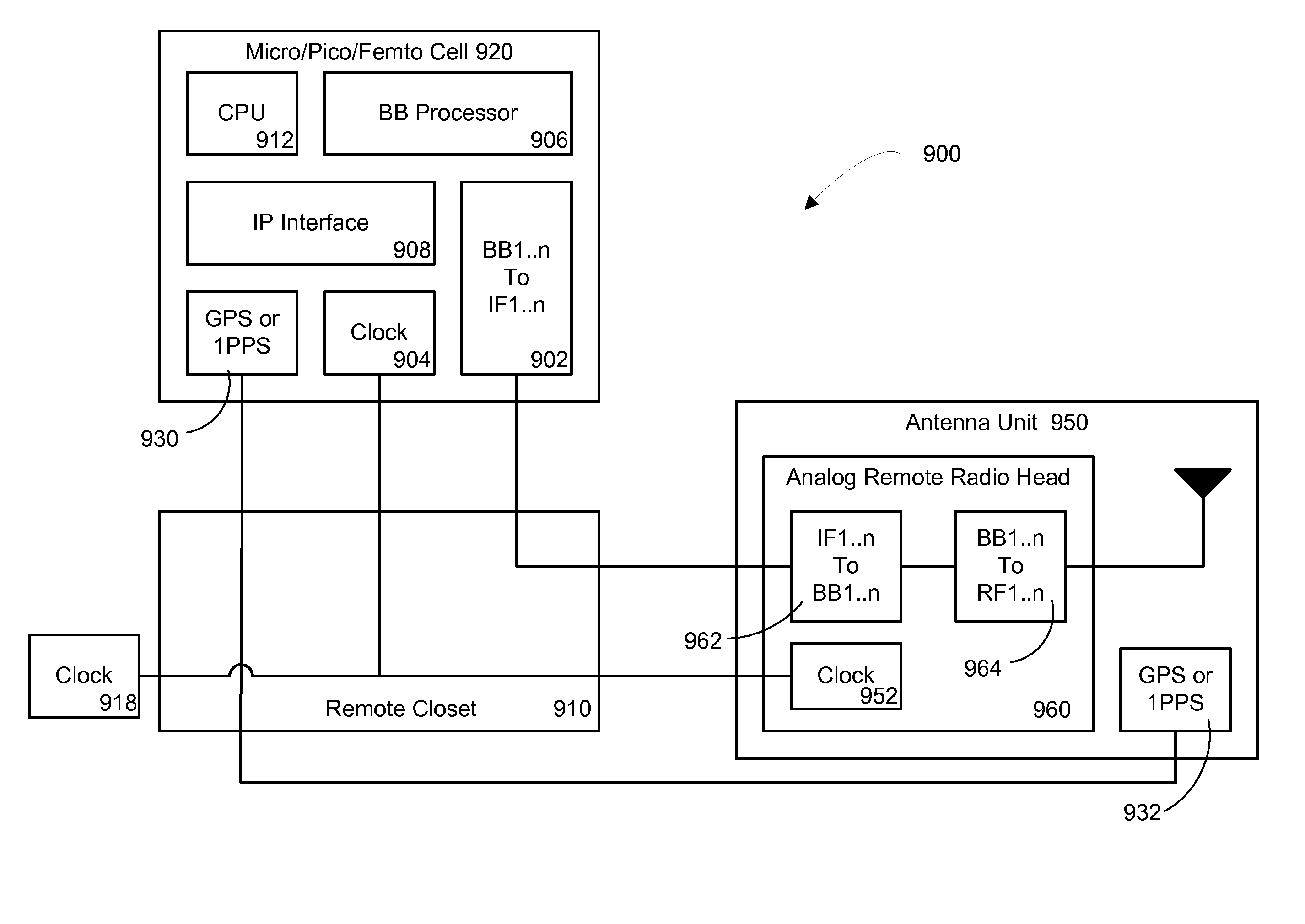
InactiveUS20100093391A1Avoid spendingReduce energy costsSite diversityNetwork traffic/resource managementDistributed antenna systemGps receiver
The invention is directed to a method and system for supporting multiple time division duplexed (TDD) based wireless services or frequency division duplexed (FDD) wireless services on a Distributed Antenna System (DAS). A DAS can support a many wireless services, including voice and data services using the same physical equipment. TDD based services use a common clock signal to synchronize the components of the DAS for transmission and reception of TDD signals. In accordance with the invention, the DAS can include a GPS receiver which can extract a timing signal (such as a 1 pps signal) from a GPS signal and distribute the timing signal to any and all components of the DAS to enable synchronization of the components for transmitting and receiving TDD signals. The GPS receiver can be part of the interface that connects a TDD based service to the DAS or separate component of the DAS. In accordance with the invention, the DAS can distribute a reference clock signal to all of the components of the DAS in order to maintain zero frequency shift while manipulating with the carrier frequencies of the various wireless services carried by the DAS. In addition, and in accordance with the invention, two analog architectures for better integration between the services sources (BTS) and the DAS are disclosed.
Owner:CORNING OPTICAL COMM WIRELESS
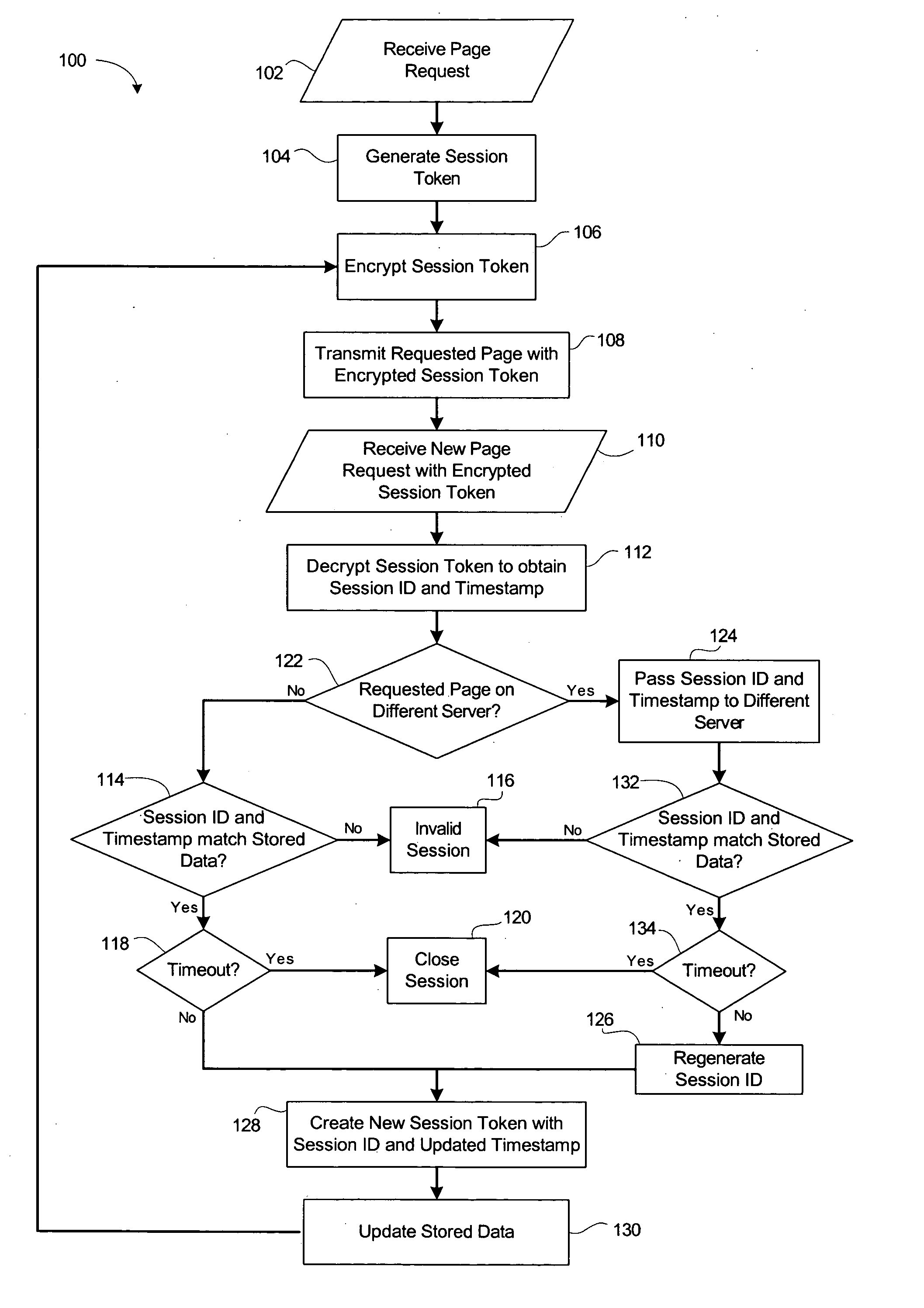
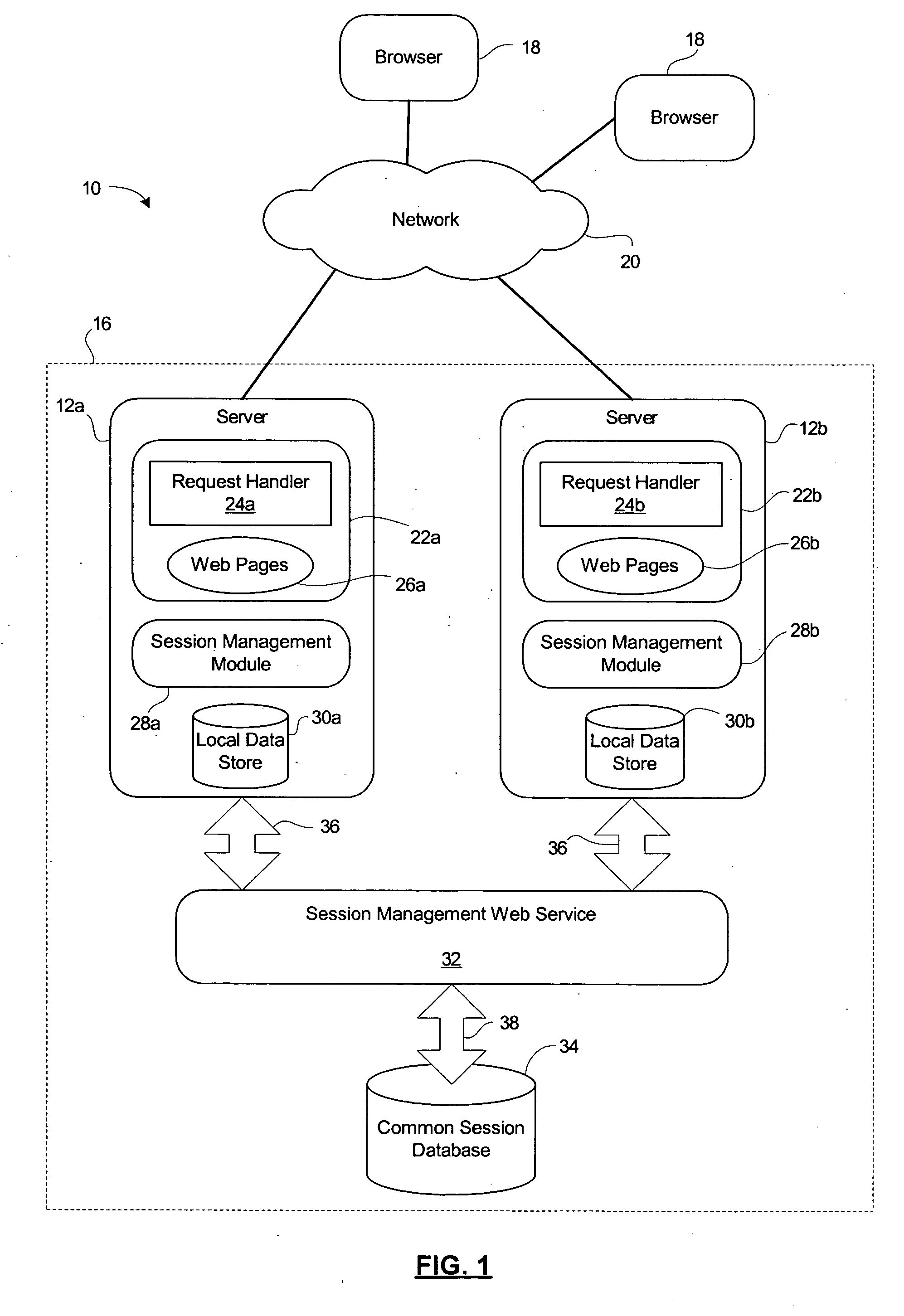
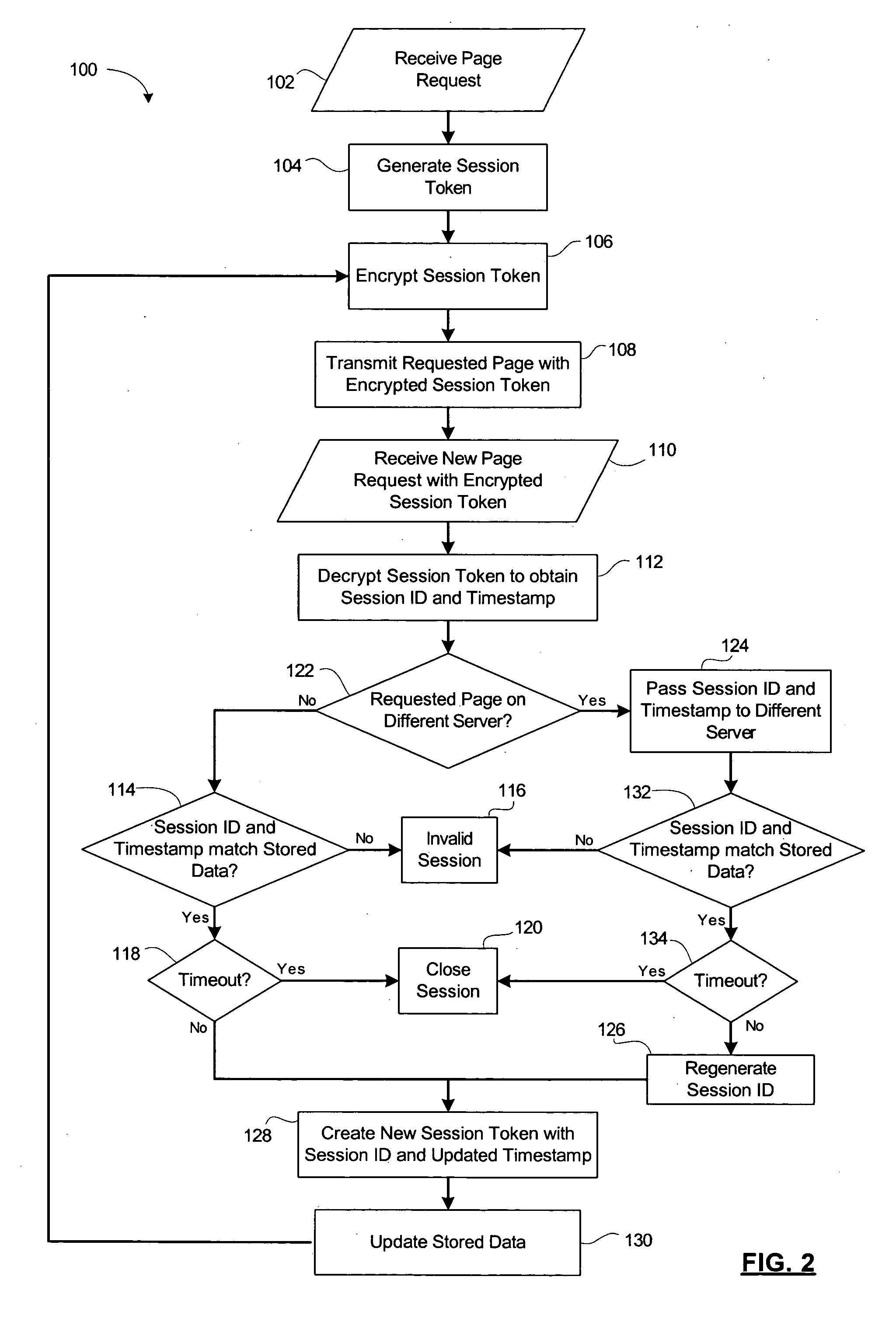
Method and system for secure session management in a web farm
ActiveUS20050132222A1Digital data processing detailsUser identity/authority verificationSession managementWeb service
A system and method for secure session management in a web farm using a session token. A session management web service updates the session token with each request received from a browser. If the request must be redirected to a new server where the requested resource is located, then the decrypted session token is transmitted to the new server and the session management web service generates a new session token to be used in place of the previous session token. The new session token is transmitted to the browser with the requested web resource.
Owner:AVAYA INC
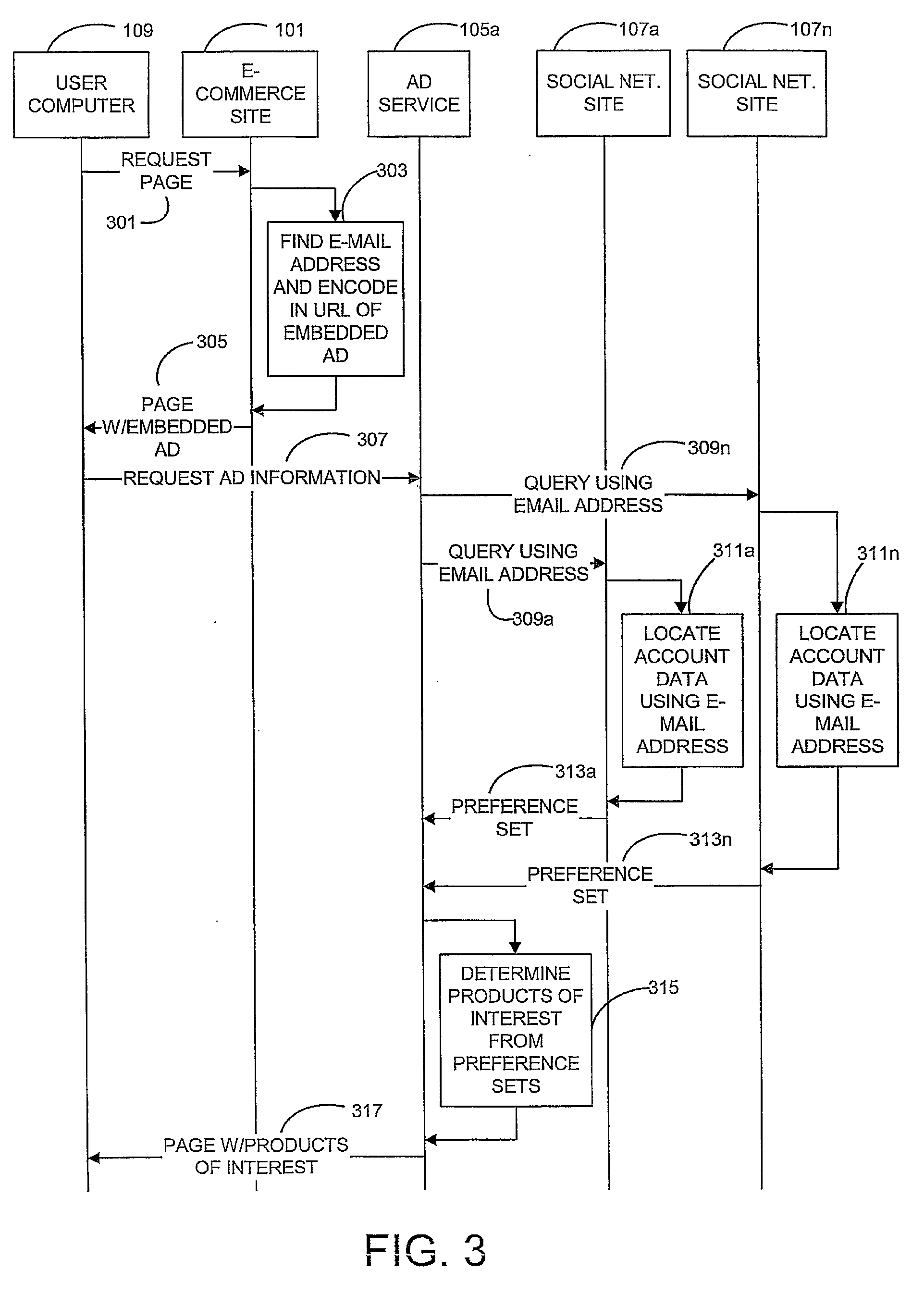
Adaptive Advertising Based On Social Networking Preferences
A method of providing targeted advertising includes an electronic commerce site that receives a request from a user for a webpage. The electronic commerce site determines an identifier, such as email address, for the user. The electronic commerce site encodes the identifier in a request, such as a universal resource locater (URL), associated with an advertisement. The electronic commerce site embeds the advertisement in the requested webpage and sends the webpage to the user. When an advertising service receives the URL from the user, the advertising service sends a query to a social networking site. The query includes the identifier. Upon receiving preference information for the user from the social networking site in response to query, the advertising service uses the preference information to determine products of interest to the user. The advertising service sends a webpage to the user. The webpage from the advertising service includes information on the products of interest.
Owner:IBM CORP
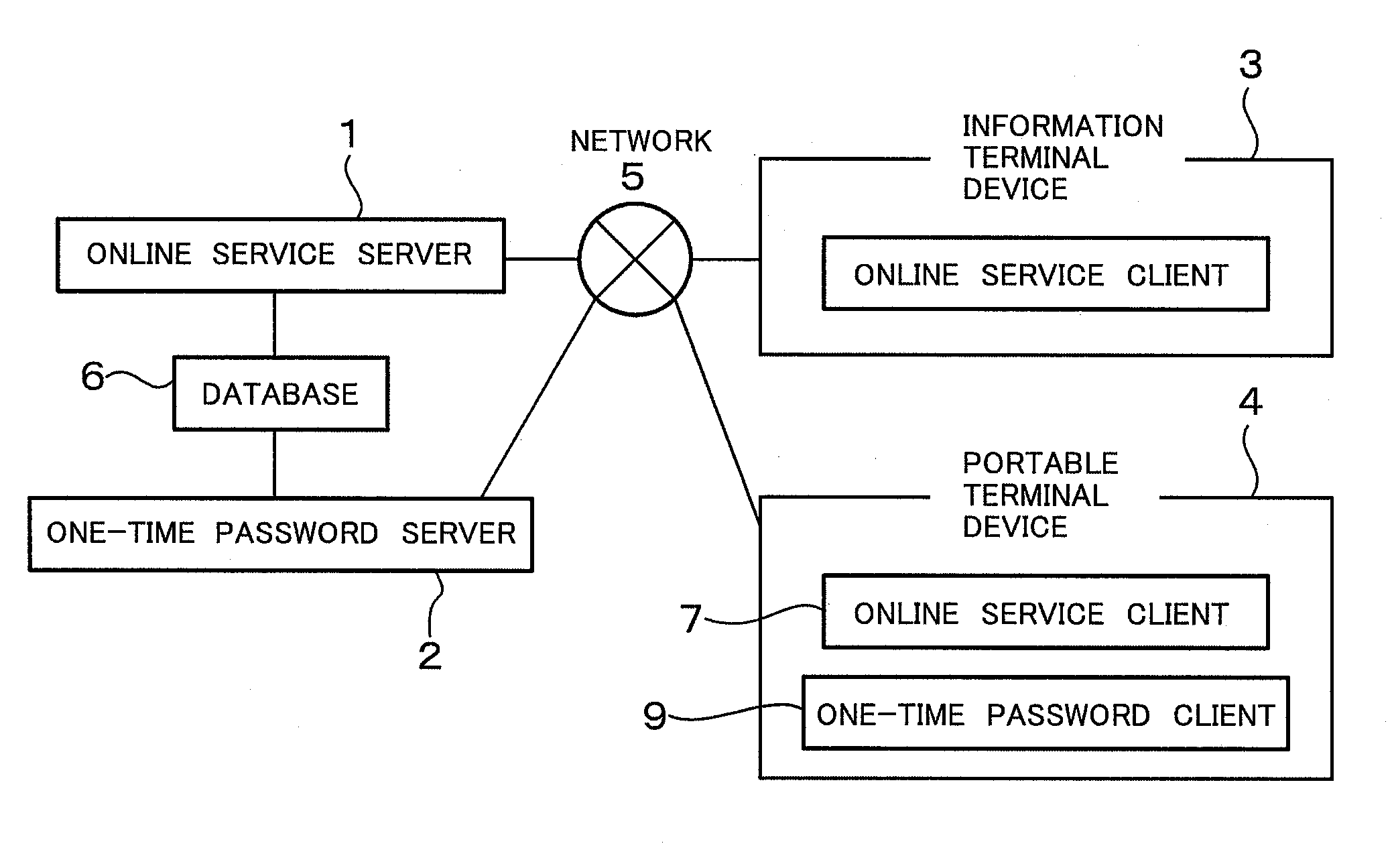
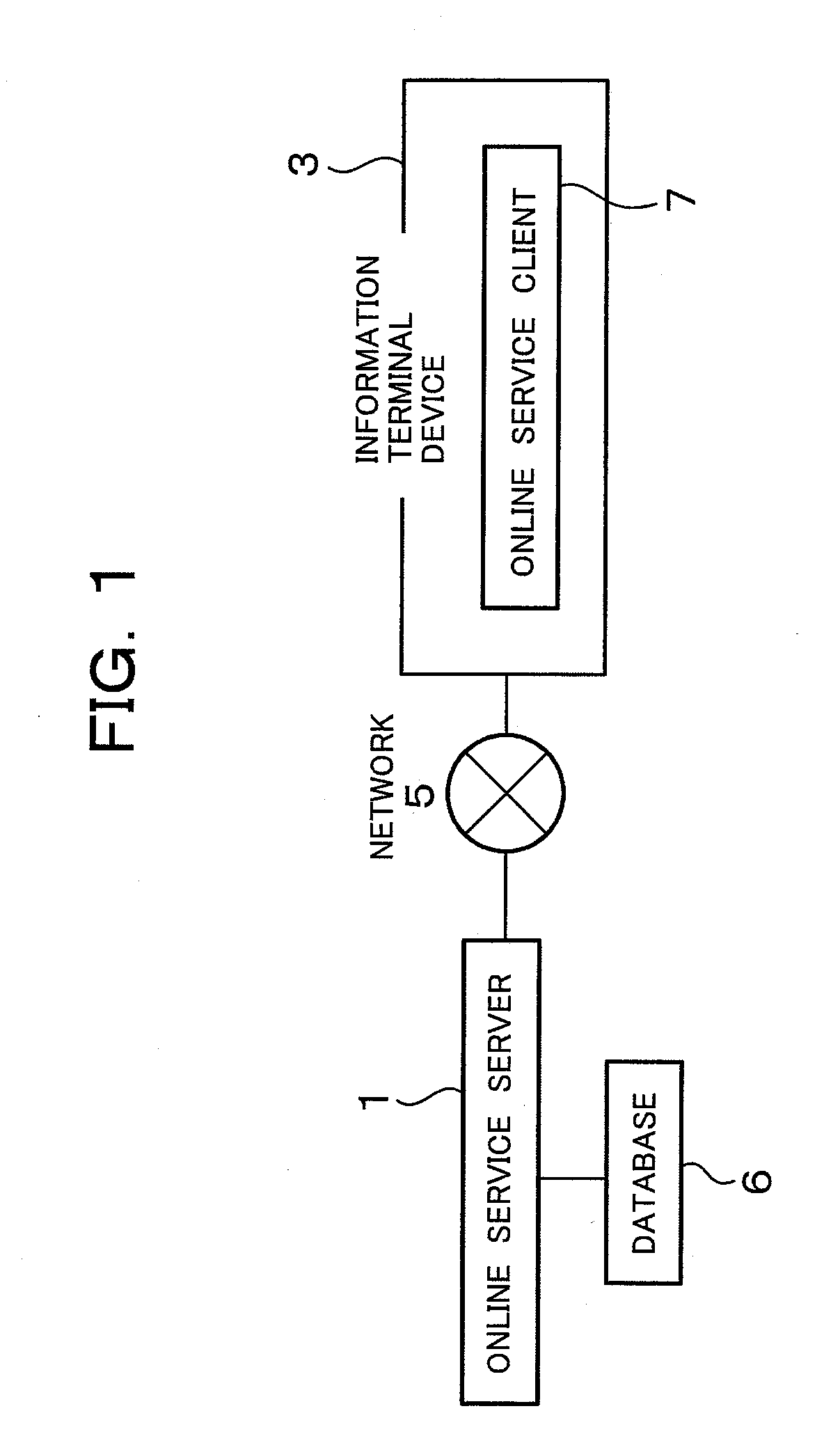
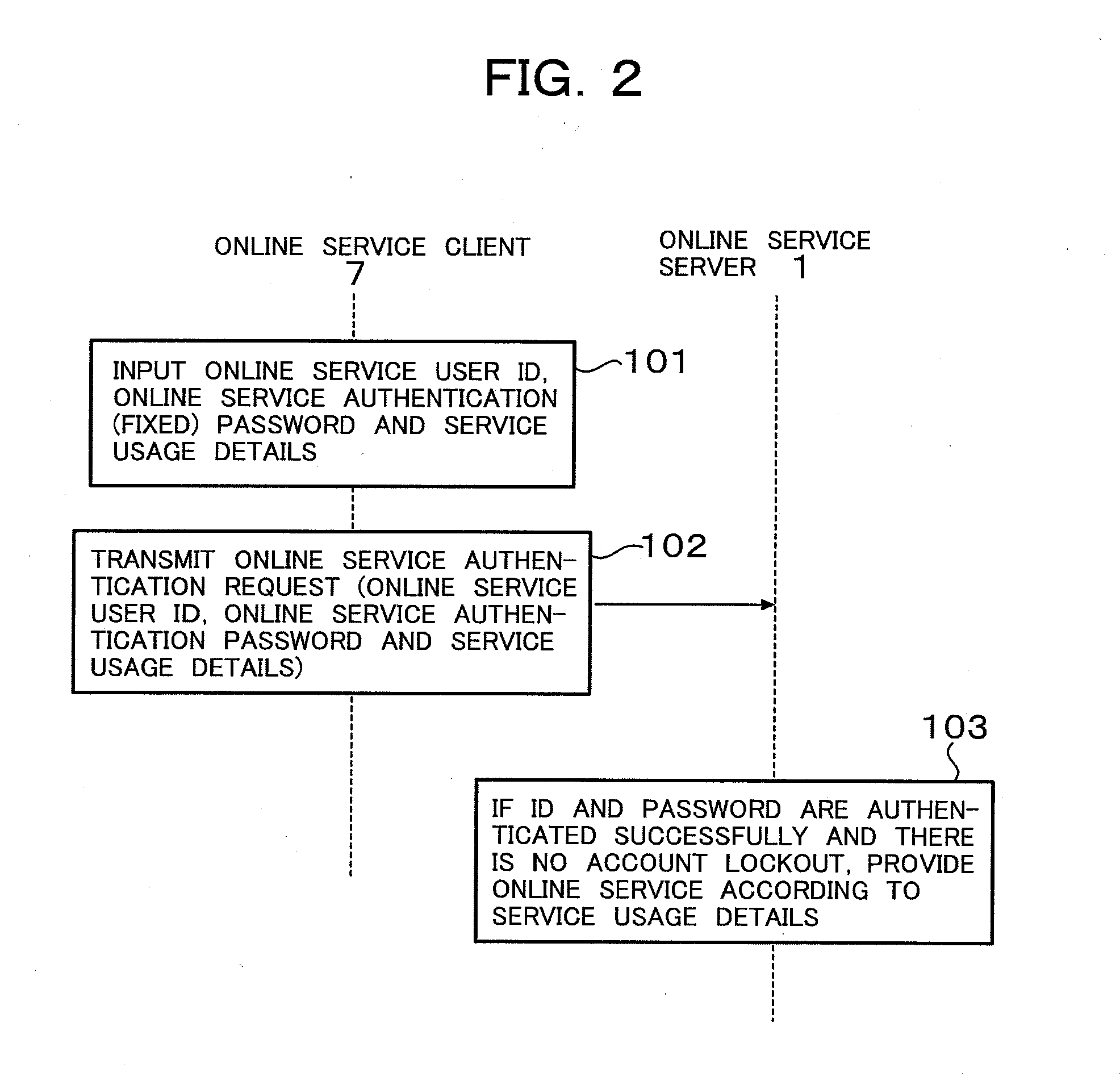
Authentication system and authentication method
InactiveUS20100017860A1Easy transferEasy to useDigital data processing detailsUser identity/authority verificationUse of servicesAuthentication server
The security of an authentication system using a one-time password is increased, a shift from an authentication system using a fixed password is simplified, and a range of use is increased. An authentication system wherein a one-time password is synchronized with time, or an authentication system wherein a one-time password is synchronized with the number of online service authentication requests, is provided. When a one-time password client 9 downloads a one-time password for online service authentication from a one-time password server 2, current time information or a current value of the number of online service authentication requests is made to coincide between the client and server, and an online service authentication request is authenticated as long as the downloaded one-time password for online service authentication is valid. The one-time password may also be synchronized with service usage details contained in the online service authentication request.
Owner:HITACHI LTD
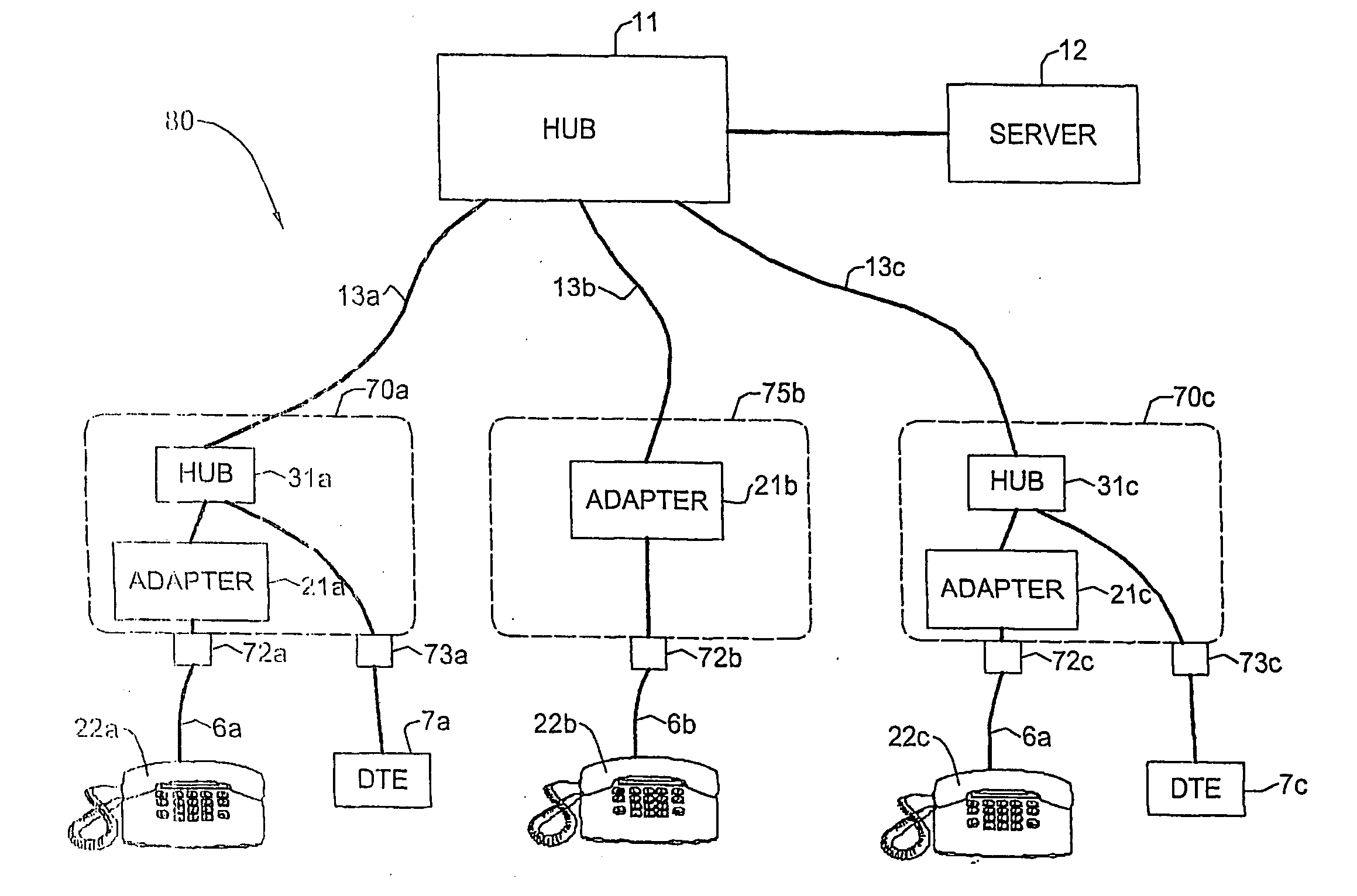
Telephone outlet with packet telephony adapter, and a network using same
InactiveUS20050083959A1Easy to useMultiplex system selection arrangementsSpecial service provision for substationNetwork connectionUse of services
An outlet for a Local Area Network (LAN), containing an integrated adapter that converts VoIP to and from analog telephony, and a standard telephone jack (e.g. RJ-11 in North America) for connecting an ordinary analog (POTS) telephone set. Such an outlet allows using analog telephone sets in a VoIP environment, eliminating the need for an IP telephone set or external adapter. The outlet may also include a hub that allows connecting both an analog telephone set via an adapter, as well as retaining the data network connection, which may be accessed by a network jack. The invention may also be applied to a telephone line-based data networking system. In such an environment, the data networking circuitry as well as the VoIP / POTS adapters are integrated into a telephone outlet, providing for regular analog service, VoIP telephony service using an analog telephone set, and data networking as well. In such a configuration, the outlet requires two standard telephone jacks and a data-networking jack. Outlets according to the invention can be used to retrofit existing LAN and in-building telephone wiring, as well as original equipment in new installation.
Owner:CONVERSANT INTPROP MANAGEMENT INC +1
Method and system for assessing relevant properties of work contexts for use by information services
InactiveUS20060271535A1Weight increaseHeavy weightWeb data indexingSpecial data processing applicationsAdaptive weightingData source
An information retrieval system for automatically retrieving information related to the context of an active task being manipulated by a user. The system observes the operation of the active task and user interactions, and utilizes predetermined criteria to generate context representation of the active task that are relevant to the context of the active task. The information retrieval system then processes the context representation to generate queries or search terms for conducting an information search. The information retrieval system determines the relevance of a word to the context by utilizing an adaptive weighting system. The information retrieval system assigns varying weights to different attributes of a word and calculates an accumulated weight of the word by accumulating all weights assigned to the word. The attributes may include word size, style, location of the word, etc. The system then ranks the importance of words based on their respective accumulated weight, and chooses words that rank within a predetermined number from the top to form search terms to conduct an information search using various data sources.
Owner:NORTHWESTERN UNIV
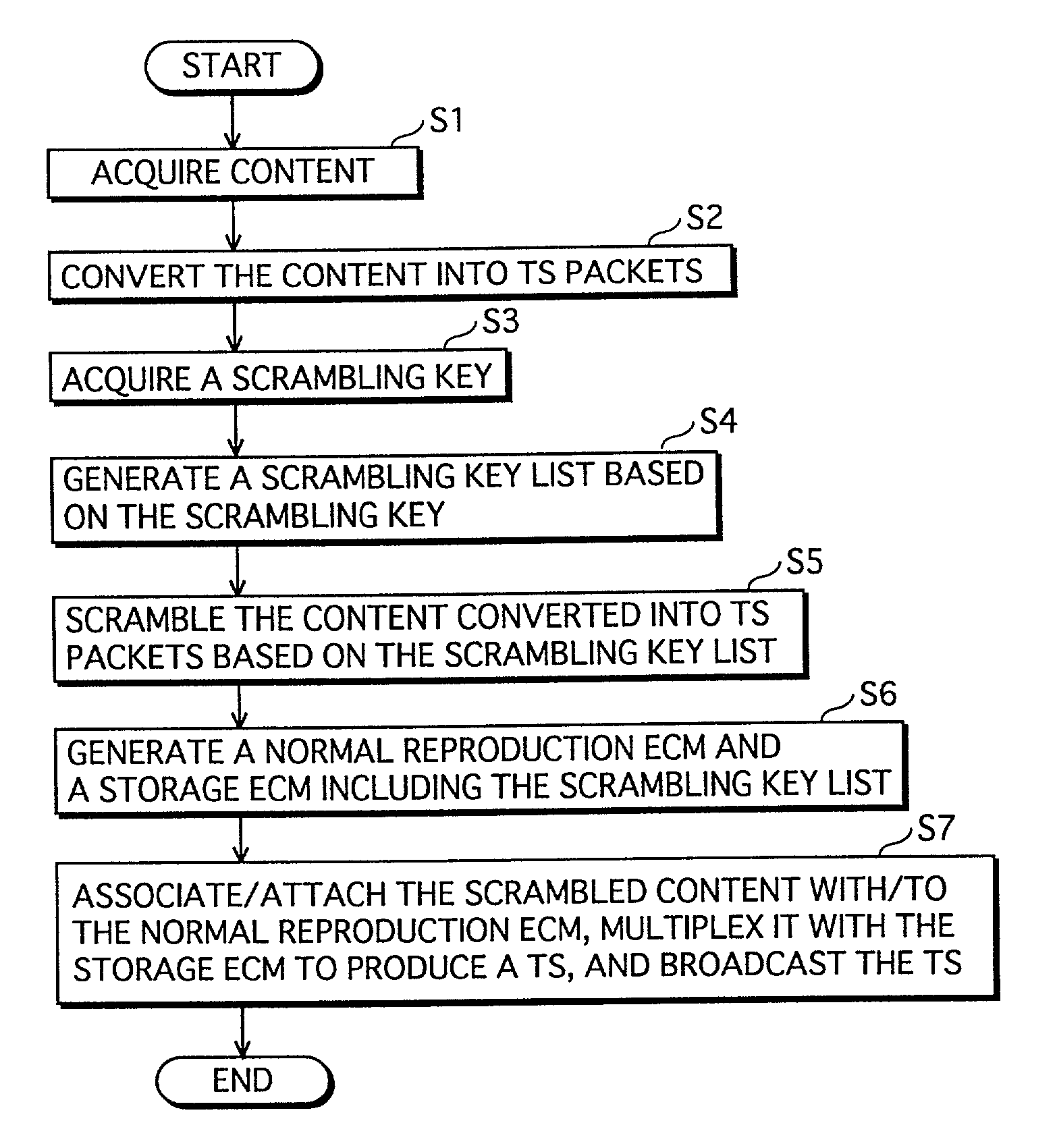
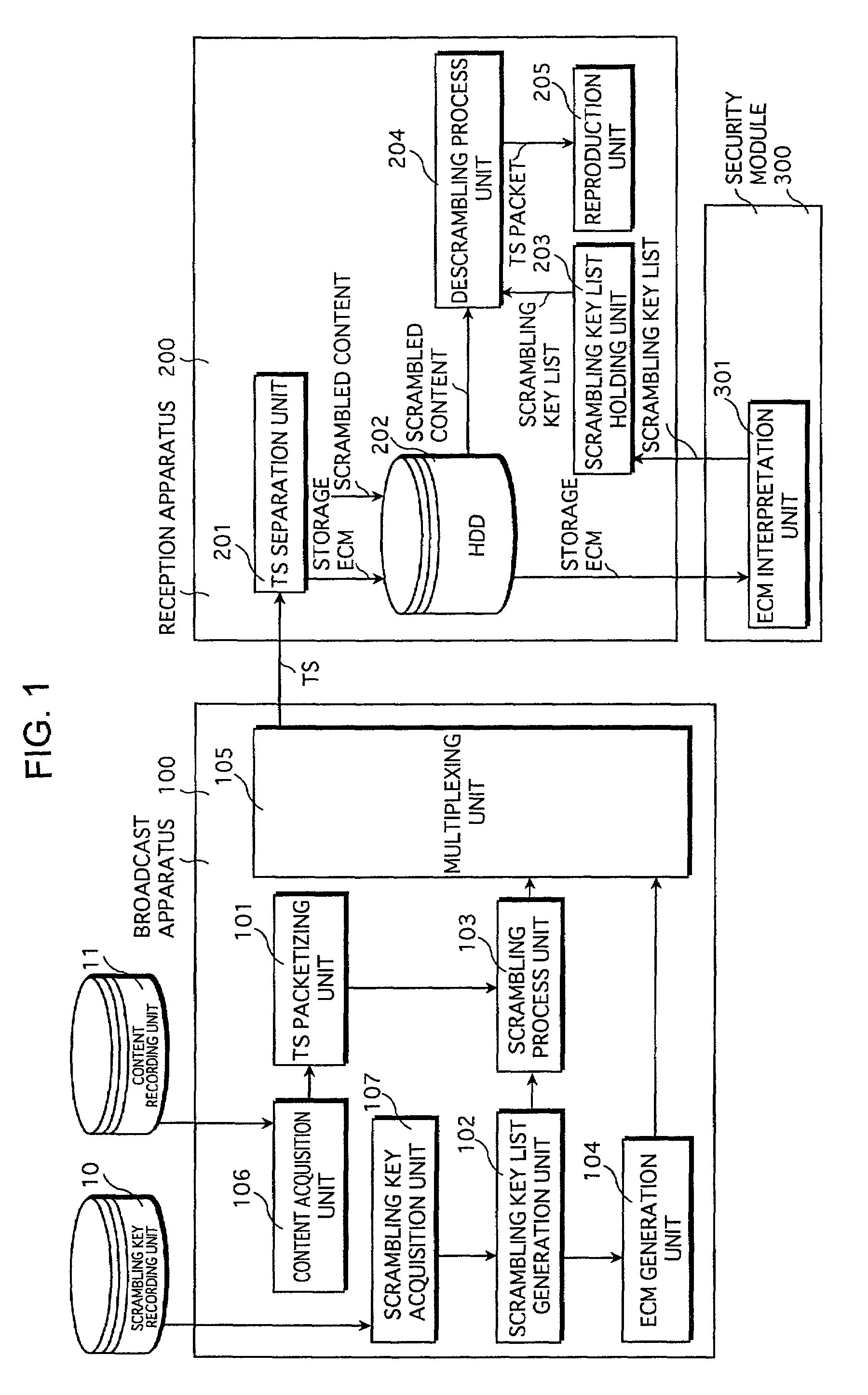
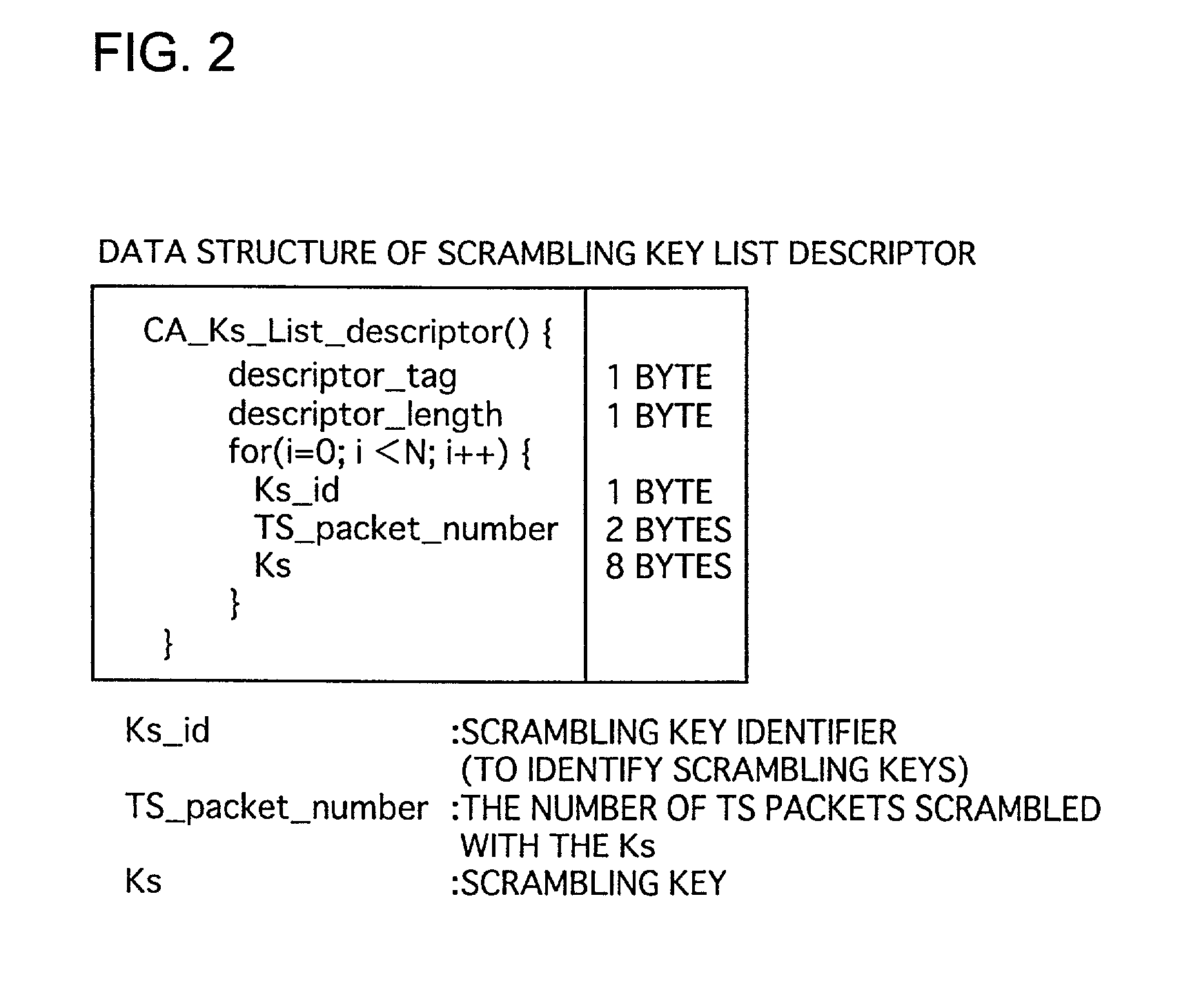
Broadcast apparatus and reception apparatus for providing a storage service by which scrambled content is stored and descrambled using scrambling key list
InactiveUS7391866B2Improve performanceBroadcast with distributionTelevision system detailsComputer hardwareUse of services
A reception apparatus includes: a reception unit for receiving the scrambled content, the scrambled content being scrambled so that a predetermined unit of scrambled content is descrambled using a descrambling key corresponding to the predetermined unit of scrambled content, and at least one piece of storage information in which a list including all descrambling keys used for descrambling the scrambled content is embedded; storage unit for storing the received scrambled content and the storage information; list extraction unit for extracting the list from the stored storage information; descramble processing unit for extracting the predetermined unit of scrambled content from the stored scrambled content, extracting a descrambling key corresponding to the predetermined unit of scrambled content from the extracted list, and descrambling the extracted predetermined unit of scrambled content using the extracted descrambling key; and reproduction unit for reproducing the predetermined unit of descrambled content in the descrambled order.
Owner:SOVEREIGN PEAK VENTURES LLC
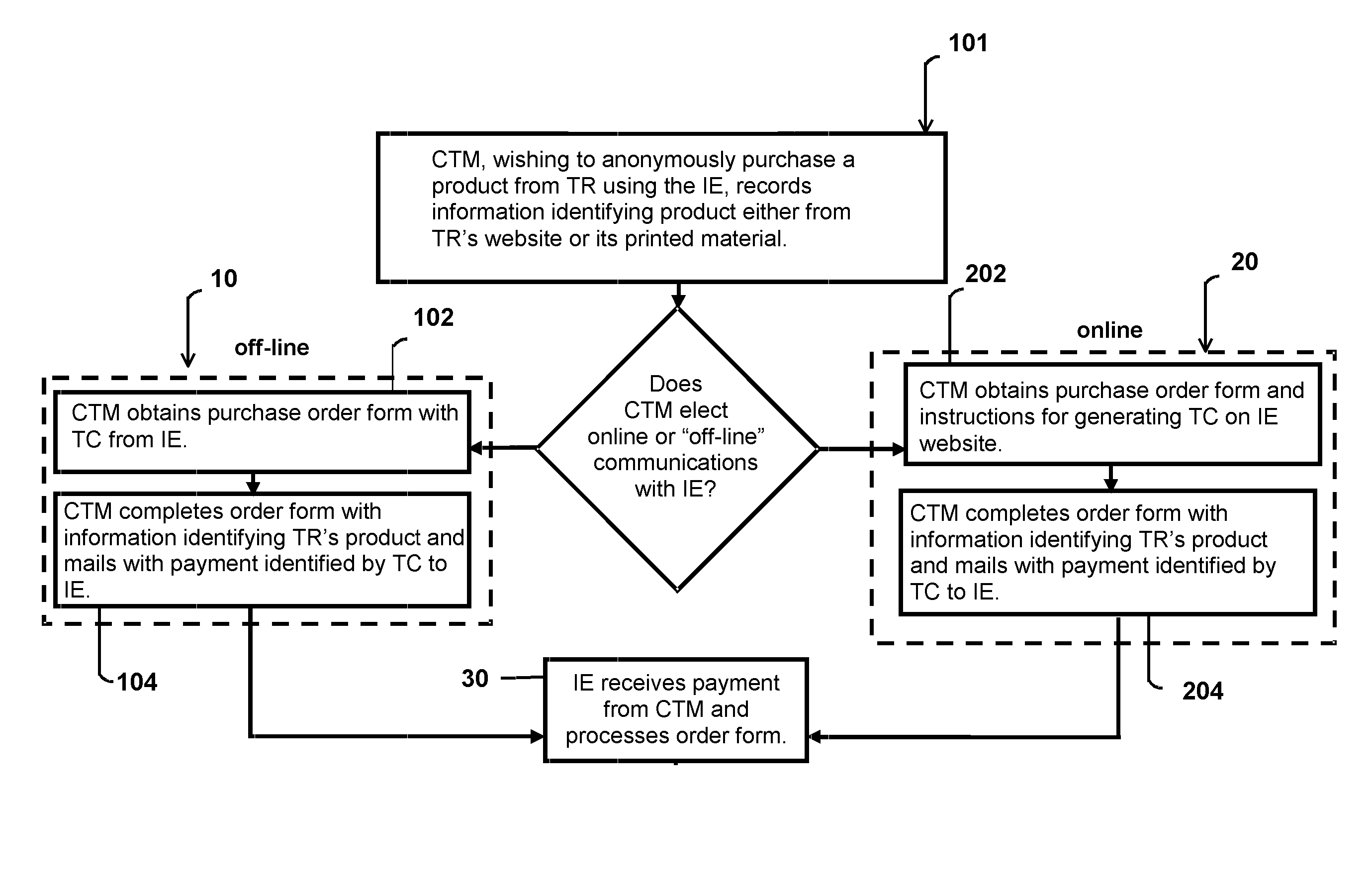
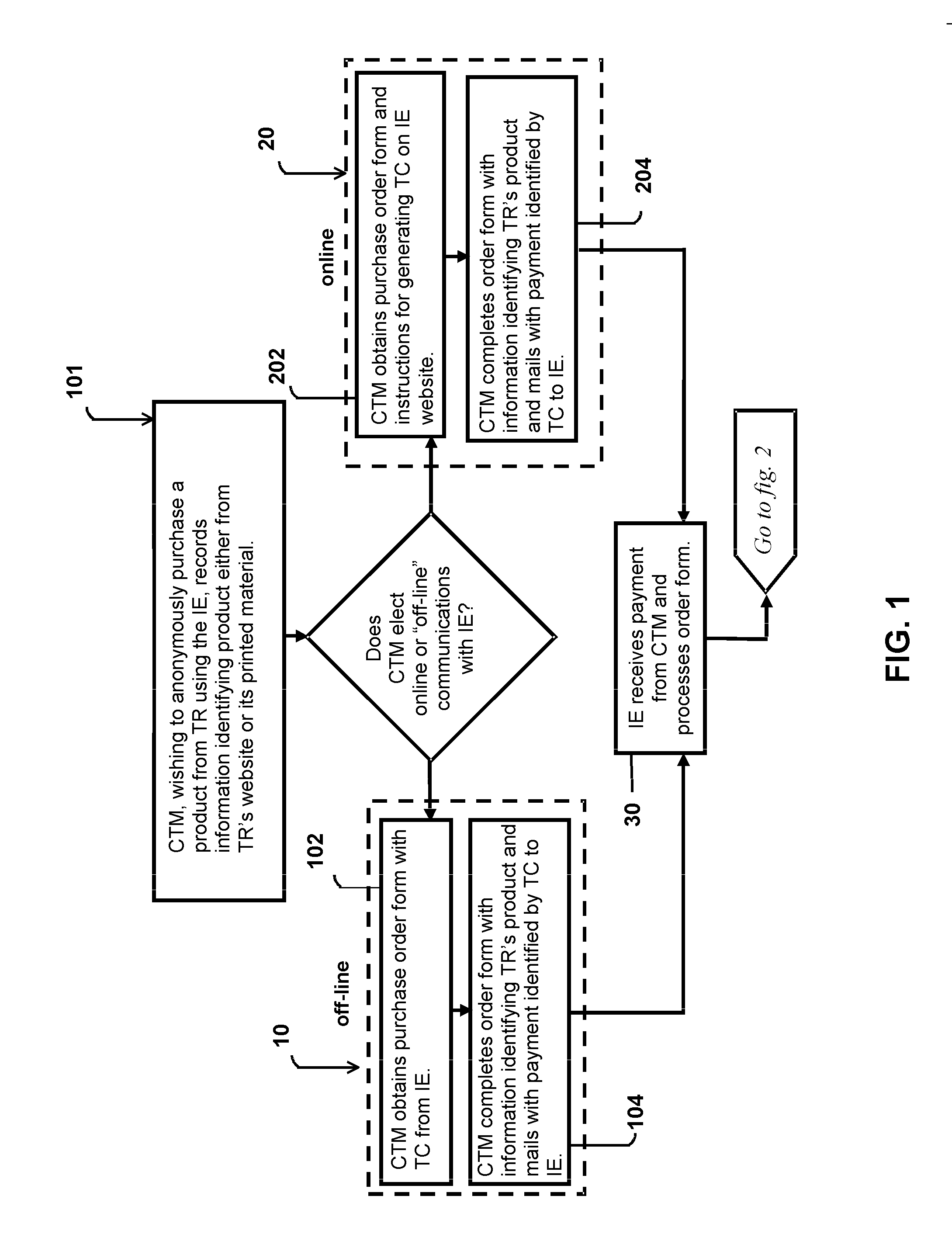
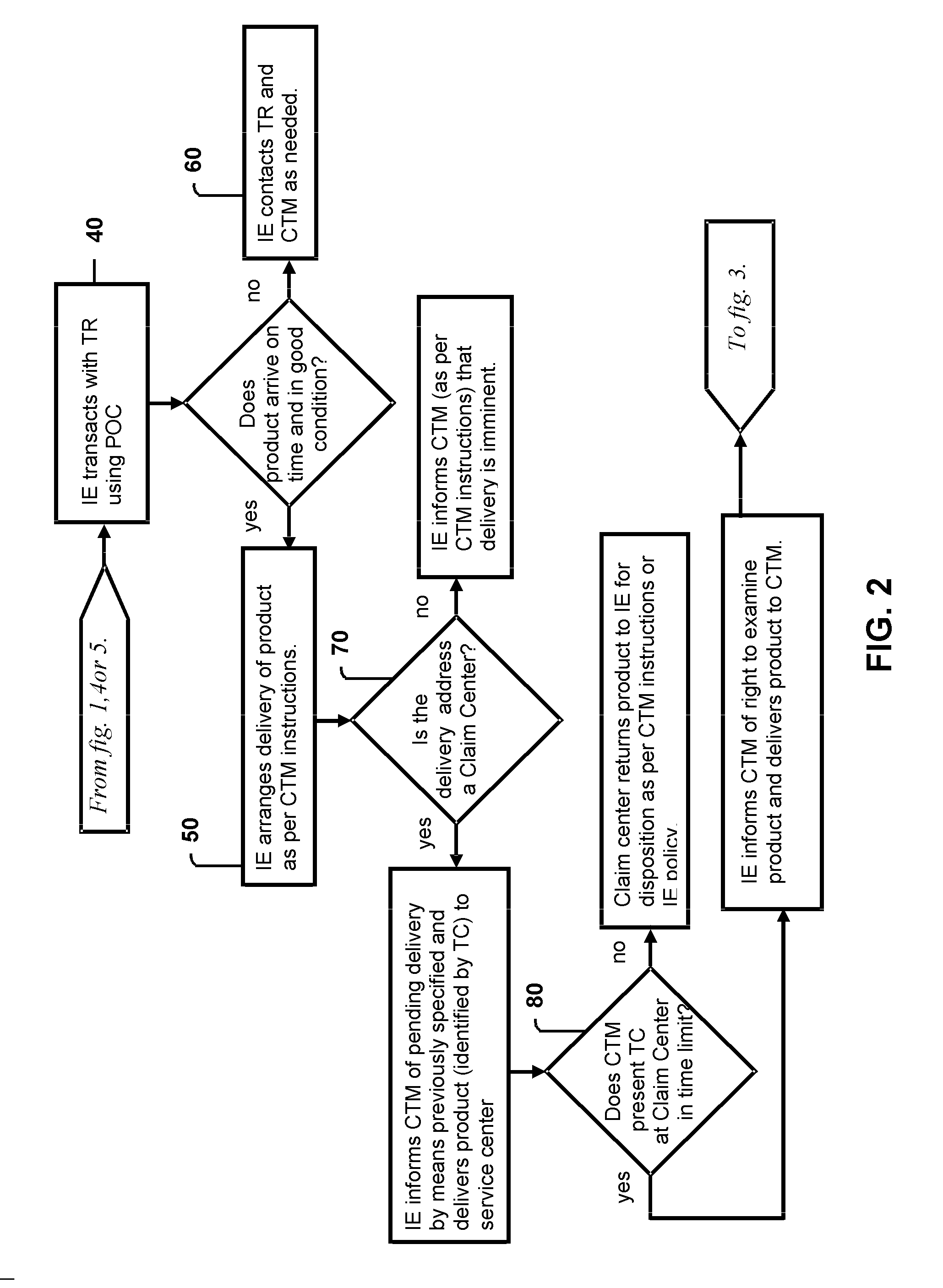
System and method for anonymous transactions and conveyances
A system and associated methods enabling a customer or transferee to acquire a product or service from a merchant, vendor or transferor through the services of an intermediate entity using a transaction protocol that shields the customer's name or other identifying information from the intermediate entity, the merchant, vendor or transferor, the delivery agent, and other agencies that may be ancillary to the transaction. The system and method is also useful for allowing anonymous sales from a seller to a buyer and conveyances from a transferor to a transferee.
Owner:JONES AUSTIN
Method and system for assessing relevant properties of work contexts for use by information services
InactiveUS20060212446A1Weight increaseHeavy weightWeb data indexingSpecial data processing applicationsAdaptive weightingData source
An information retrieval system for automatically retrieving information related to the context of an active task being manipulated by a user. The system observes the operation of the active task and user interactions, and utilizes predetermined criteria to generate context representation of the active task that are relevant to the context of the active task. The information retrieval system then processes the context representation to generate queries or search terms for conducting an information search. The information retrieval system determines the relevance of a word to the context by utilizing an adaptive weighting system. The information retrieval system assigns varying weights to different attributes of a word and calculates an accumulated weight of the word by accumulating all weights assigned to the word. The attributes may include word size, style, location of the word, etc. The system then ranks the importance of words based on their respective accumulated weight, and chooses words that rank within a predetermined number from the top to form search terms to conduct an information search using various data sources.
Owner:NORTHWESTERN UNIV
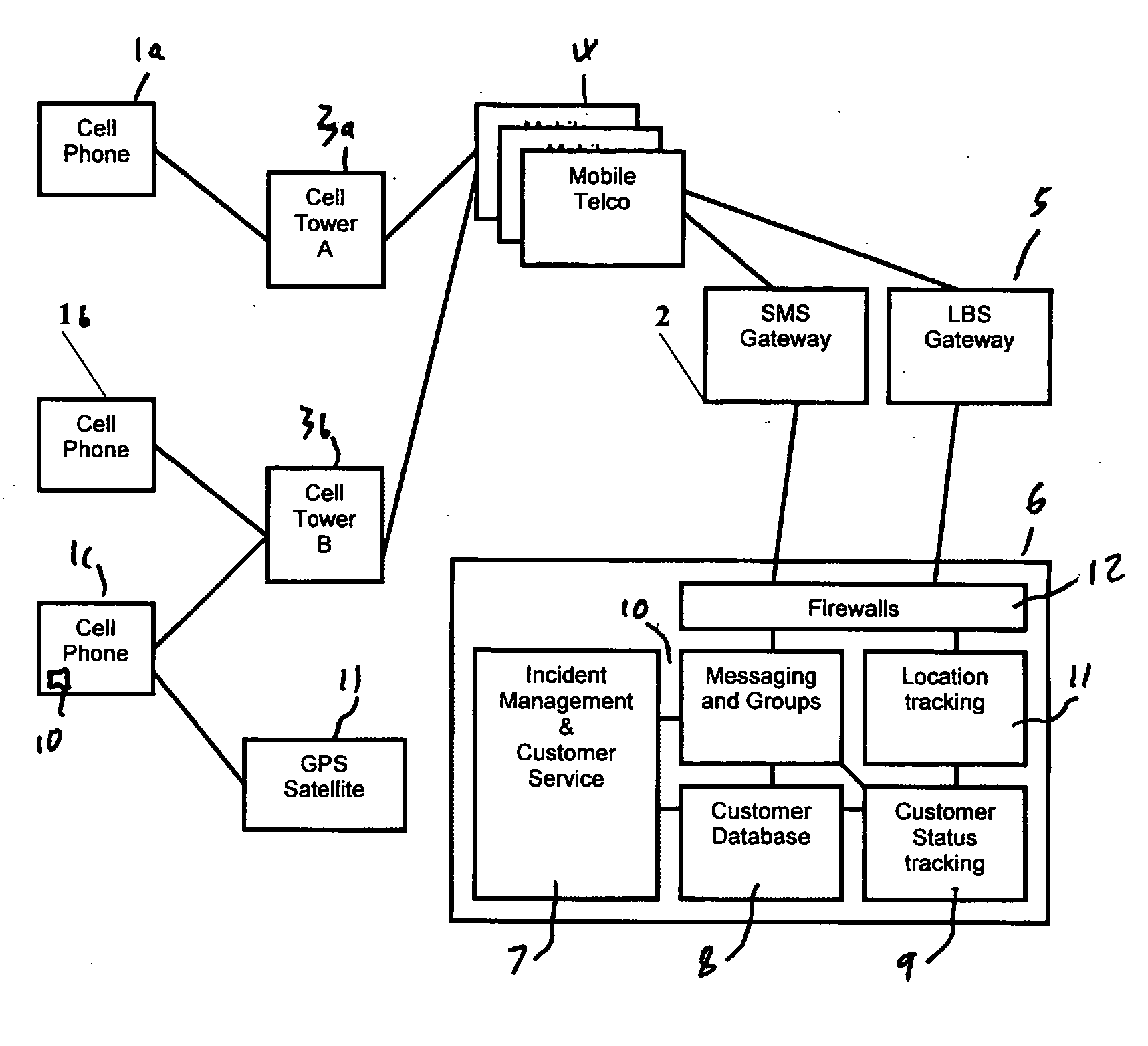
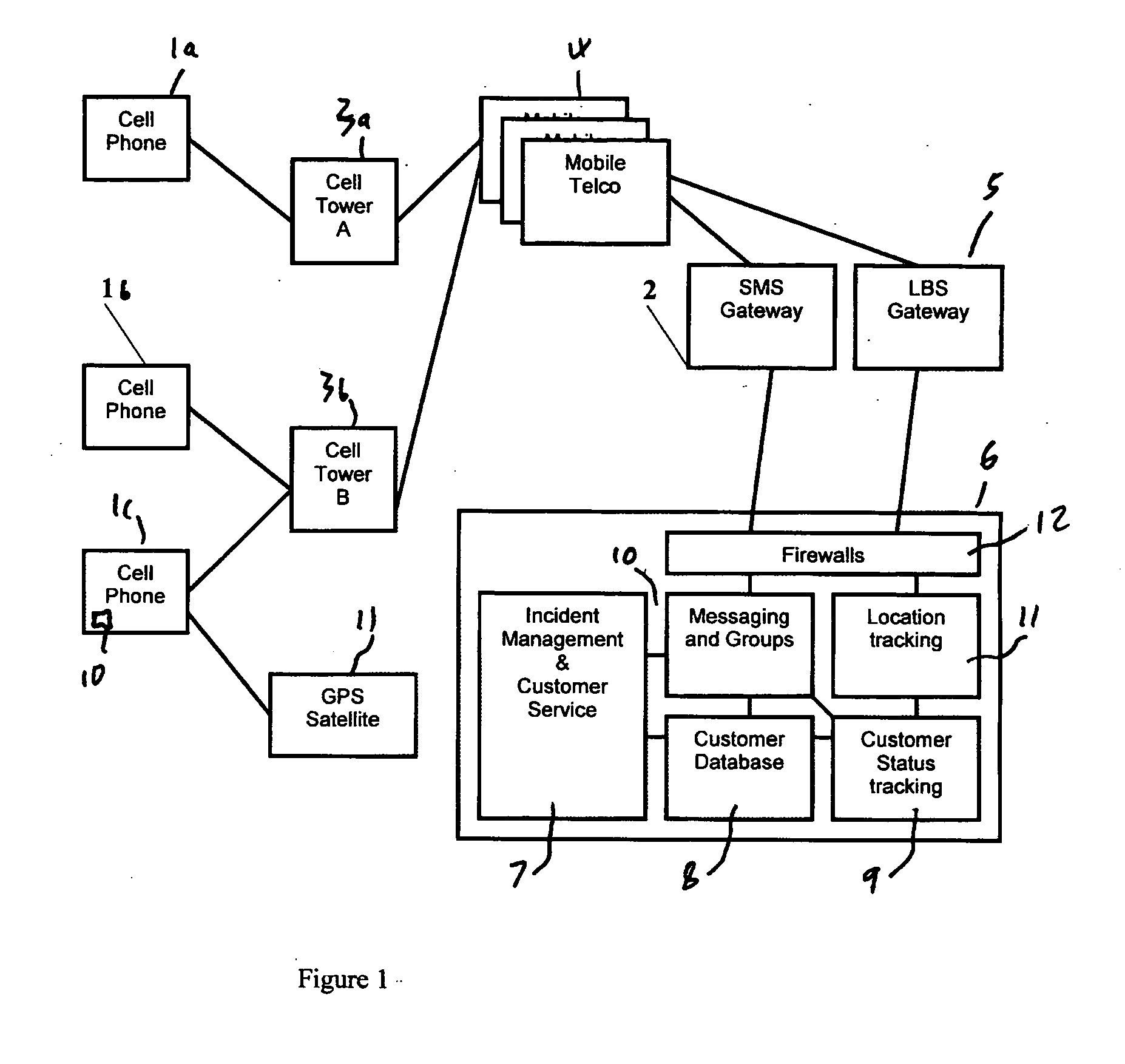
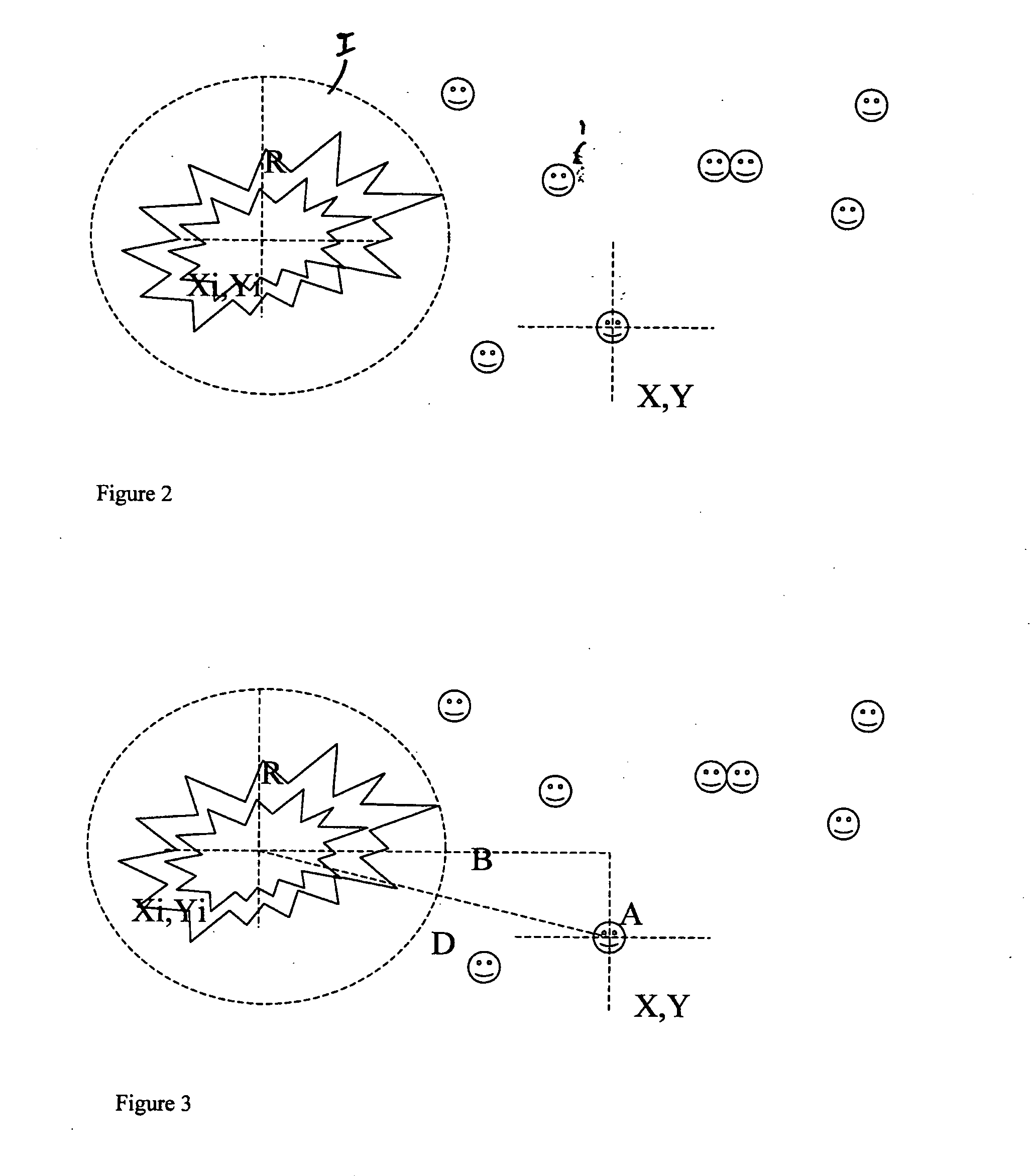
Location, tracking and alerting apparatus and method
InactiveUS20070159322A1Position fixationRadio/inductive link selection arrangementsExtreme weatherIndustrial Accident
This invention describes a product that is used during emergency incidents where the location of people can be used to track who could have been involved in the incident for example Industrial Accidents, Extreme Weather, Natural Disasters, Terrorist Attacks etc. The service locates people using devices they carry with them typically their mobile phone (1). The people's locations are compared to the location and radius of the incident and the probability that they may have been involved in the incident is determined (possible or low probability). People are also automatically contacted by a verity of means for example SMS (2) to their mobile and asked to confirm their status. Their status is automatically updated and available to people who they have linked themselves to via the service.
Owner:GRIFFIN IAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com