Negotiation method for cryptographic algorithm of data transport services in distribution network
A cryptographic algorithm and data transmission technology, which is applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems that cannot meet the negotiating requirements of cryptographic algorithms in distribution networks, and meet the needs of easy upgrade and maintenance, prevention of network attacks, and fast matching Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
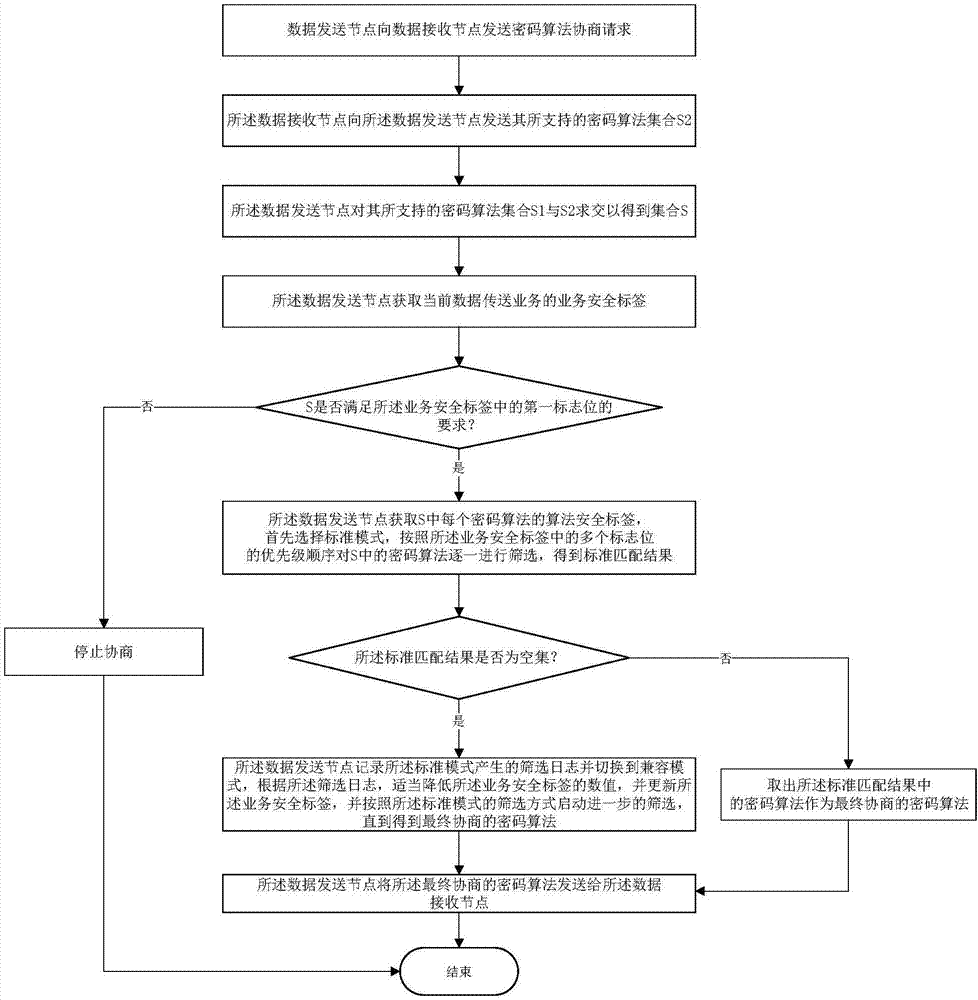
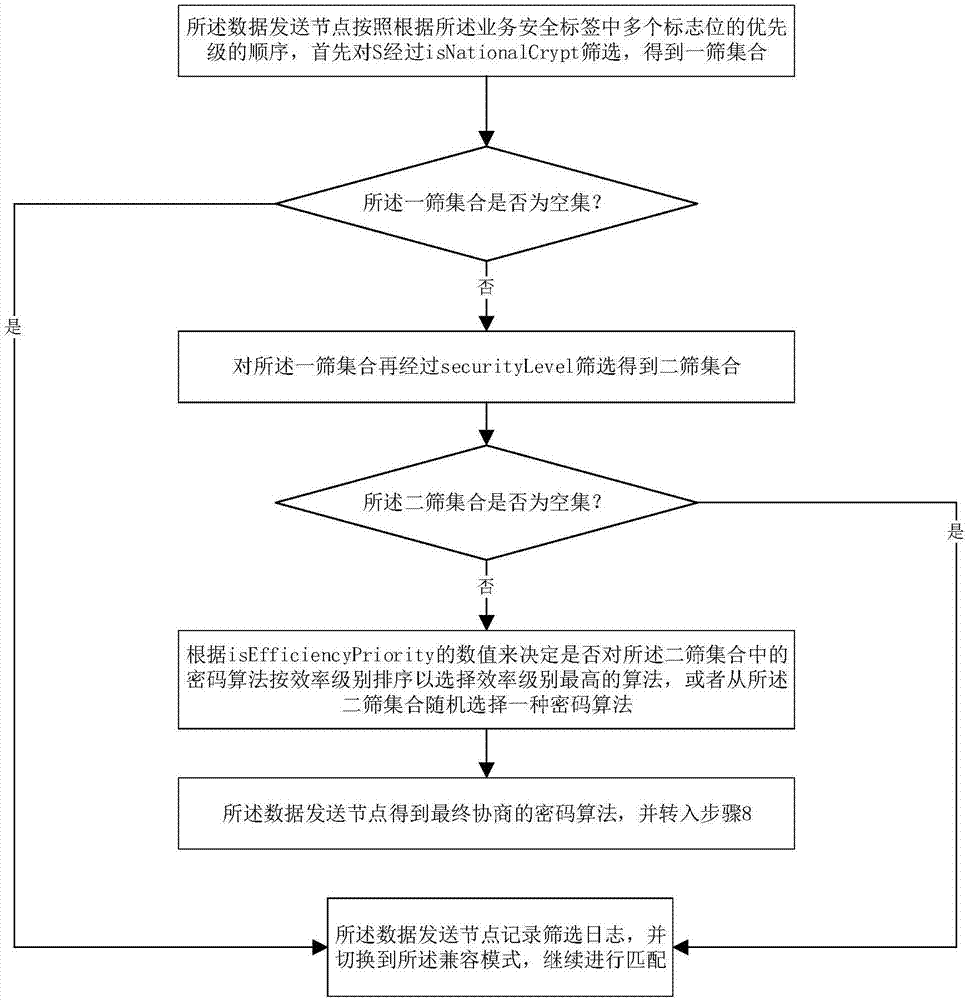
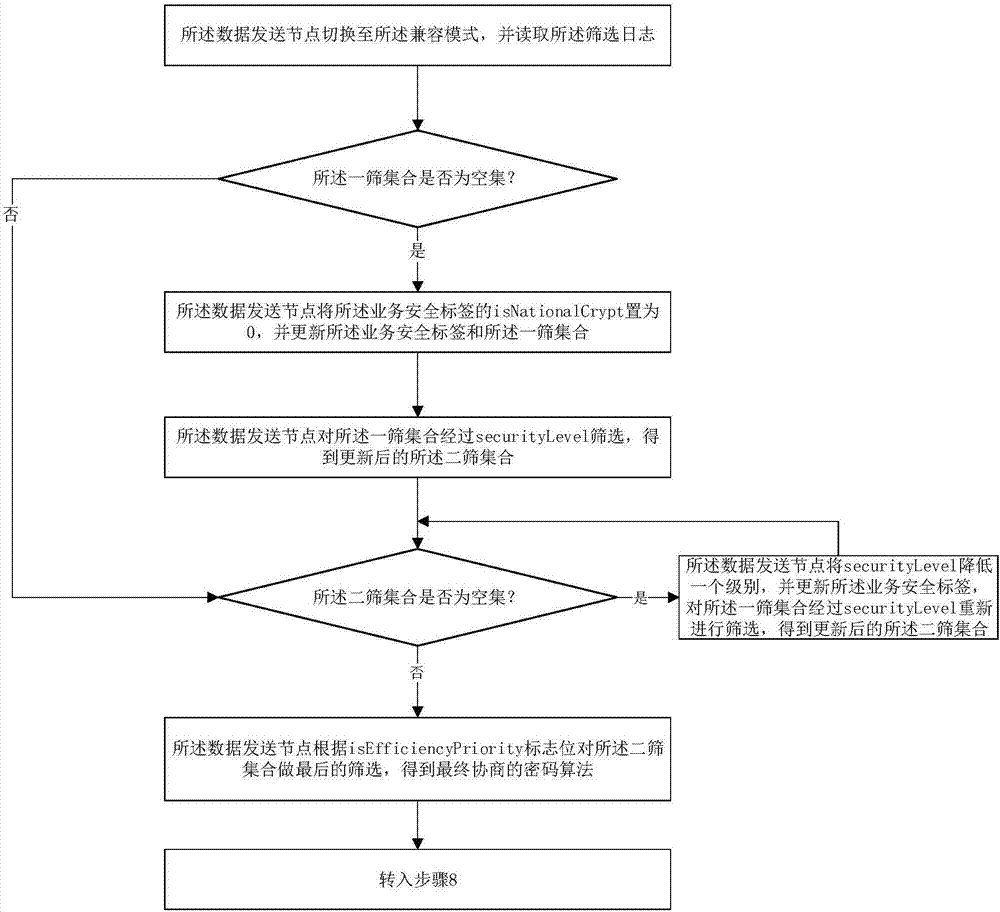
[0040] After the preparations are completed, the following will refer to the attached figure 1 , 2 and 3 to describe a specific implementation of the negotiation method of the cryptographic algorithm of the data transmission service in the distribution network according to the present invention, the negotiation method includes the following steps:
[0041] Step 1: the master station sends a cryptographic algorithm negotiation request to the terminal;
[0042] Step 2: The terminal sends a list of supported cryptographic algorithms to the main station, including a signature algorithm set SS21={SA1, SA2, SA3, SA4, SA5} and an encryption algorithm set SS22={EA1, EA2, EA3, EA4,EA5};
[0043] Step 3: The master station intersects the supported signature algorithm set SS11 and encryption algorithm set SS12 with SS21 and SS22 respectively to obtain SS1 and SS2. Since it is assumed that the master station supports all cryptographic algorithms, SS1=SS21, SS2 = SS22;
[0044] Step 4:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com