Handshake method and system based on datagram secure transmission protocol
A security transmission protocol and datagram technology, which is applied in the field of handshake methods and systems based on datagram security transmission protocol, can solve the problems of not supporting domestic commercial cryptographic algorithms, unable to meet the independent and controllable requirements of information security, etc., to facilitate horizontal extended effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0055] Assuming that the handshake method is performed between client 1 and server 1, client 1 requests to establish a data transmission link with server 1, and subsequent data transmitted between client 1 and server 1 needs to use a domestic Commercial encryption algorithm encryption, the handshake process between client 1 and server 1 is as follows:
[0056] S101. Client 1 sends a client greeting message to request server 1 to shake hands with server 1. The client 1 greeting message includes a list of all domestic commercial cipher suites supported by the client for the server. choose.
[0057] S102. The server 1 receives the client greeting message, and sends a server greeting message to the client 1 after authentication. The server greeting message includes one of the domestic commercial cipher suites selected by the server 1 from the domestic commercial cipher suite list. Matching domestic commercial cipher suites.
[0058] S103. Client 1 and server 1 replace the key sp...
Embodiment 2
[0079] Assuming that the handshake method is performed between the client 2 and the server 2, and the client 2 requests to establish a data transmission link with the server 2, the client 2 and the server 2 need to use a method to determine the subsequent data transmission. master key specifications, the handshake process between client 2 and server 2 is as follows:
[0080] S201. The client 2 sends a client greeting message to the server 2 to request the server 2 to shake hands with it. The client 2 greeting message includes a list of all domestic commercial cipher suites supported by the client for the server choose.
[0081] S202. The server 2 receives the client hello message, and sends a server hello message and a server key exchange message to the client 2 in sequence after authentication, wherein:
[0082] The server hello message includes one matching domestic commercial cipher suite selected by the server 2 from the list of domestic commercial cipher suites.
[0083...
Embodiment 3
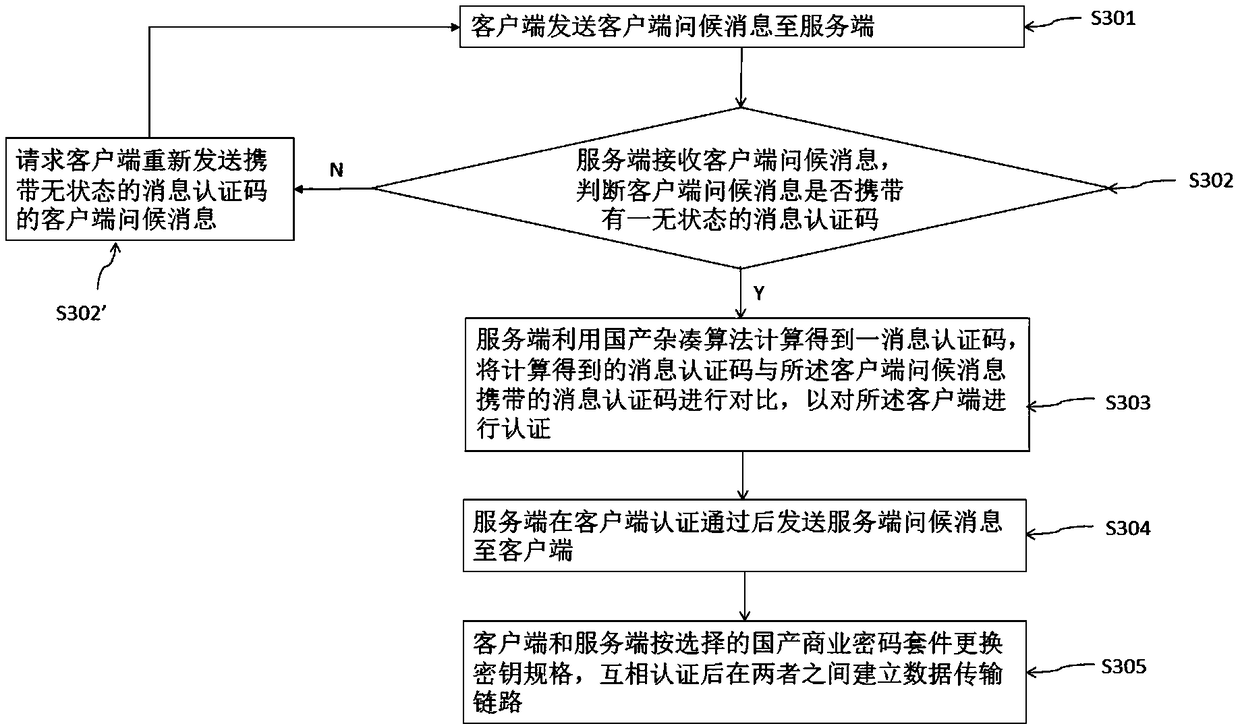
[0158]Assuming that the handshake method is performed between client 3 and server 3, the handshake process between client 3 and server 3 is as follows:
[0159] S301. The client 3 sends a client greeting message to the server 3 to request the server 3 to shake hands with it. The client 3 greeting message only includes a list of all domestic commercial cipher suites supported by the client for service terminal selection.
[0160] S302. The server 3 receives the client hello message, and determines whether the client hello message carries a stateless message authentication code.
[0161] S303. If the server 3 receives a message authentication code with or without status in the client greeting message, the server 3 calculates a message authentication code using a domestic hash algorithm, and combines the calculated message authentication code with the client greeting message. The carried message authentication codes are compared to authenticate the client 3.
[0162] S304. Afte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com