Identity authentication method, device and system
A technology of identity authentication and equipment, applied in the field of communication, can solve problems such as compatibility problems, and achieve the effect of avoiding compatibility problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
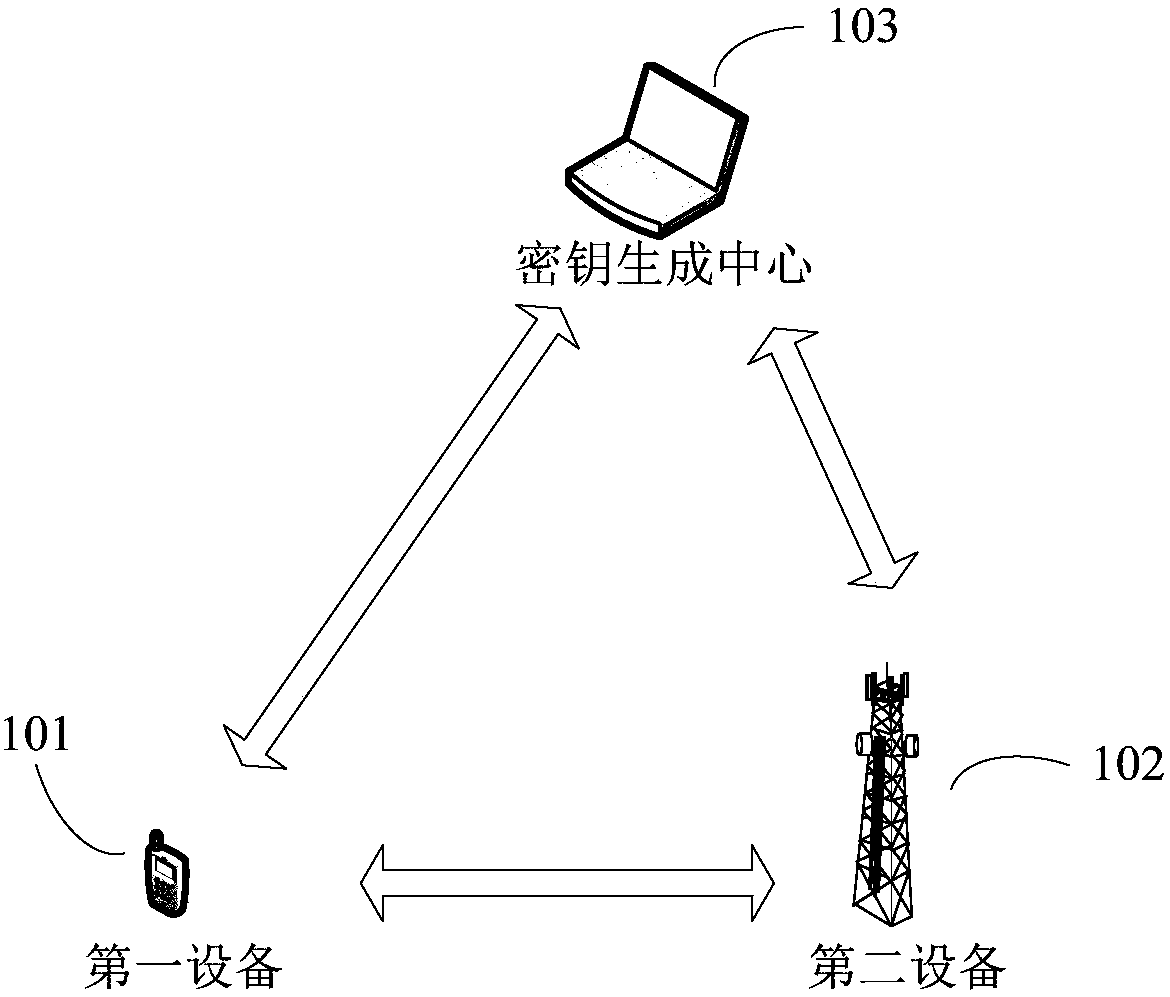
[0052] see figure 1 , is a schematic structural diagram of an embodiment of the communication system of the present application.
[0053] Such as figure 1 Said, the communication system may include a first device 101 , a second device 102 , and a key generation center 103 .
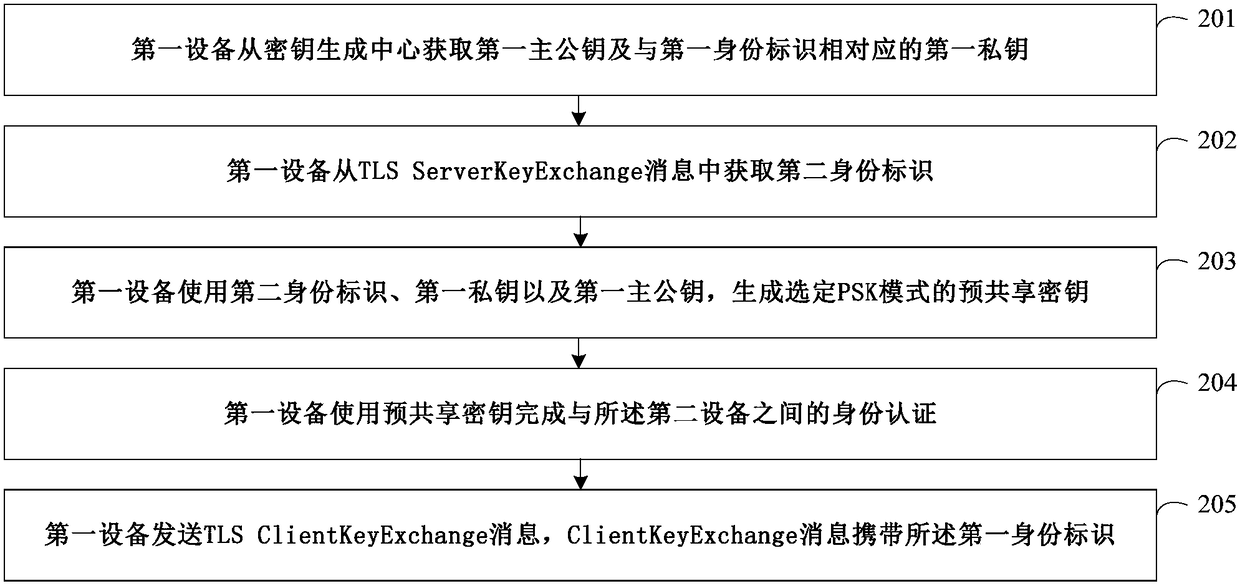
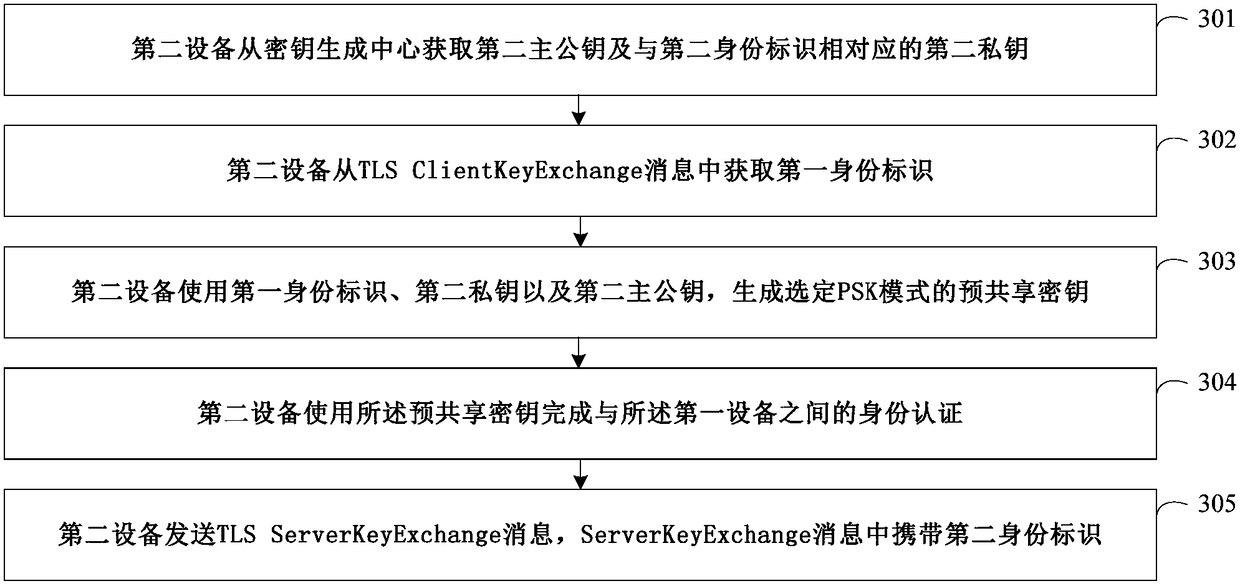
[0054] Wherein, encrypted data transmission may be performed between the first device 101 and the second device 102 . The cryptographic algorithm protocol, authentication and key agreement process required for encrypted data transmission between the first device 101 and the second device 102 can all be completed by using the TLS protocol.
[0055]The TLS protocol is composed of two layers: TLS record protocol (TLS Record) and TLS handshake protocol (TLS Handshake). The handshake protocol is the core part of TLS. It completes functions such as cryptographic algorithm protocol, authentication, and session key generation between the client and server, and is the prerequisite for secure data transmission b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com