Security configuration method of Tomact cipher suite of SSR
An encryption suite and security configuration technology, applied in computer security devices, electrical components, instruments, etc., can solve serious and high-impact problems, achieve safe operation, use with confidence, and ensure safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The content of the present invention is described in more detail below:
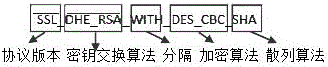
[0018] A security configuration method for the tomcat cipher suite of SSR, by selecting or adding the default cipher suite, disabling insecure encryption, the format and components of the cipher suite are as follows figure 1 As shown, each suite begins with "SSL" or "TLS", followed by the key exchange algorithm. Use the word "With" to separate the key exchange algorithm, encryption algorithm, and hash algorithm (the separation may not exist), for example: SSL3_DHE_RSA_WITH_DES_CBC_MD5, which means that DHE_RSA (temporary Diffie-HellMan with RSA digital signature) is defined as the encrypted Key exchange algorithm; define DES_CBC as encryption algorithm; define MD5 as hash algorithm.
[0019] But the format is not fixed. For example, there is a writing method like TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, but you can understand its meaning after you are familiar with it. More than 128 refers to the key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com