TLS handshake protocol for identity-based cryptosystem
A technology of identity password and handshake protocol, which is applied in the field of basic communication, can solve problems such as high delay and large amount of calculation, and achieve the effects of reducing network delay, high security, and saving network traffic and memory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The specific embodiment of the present invention is described in detail below in conjunction with accompanying drawing;
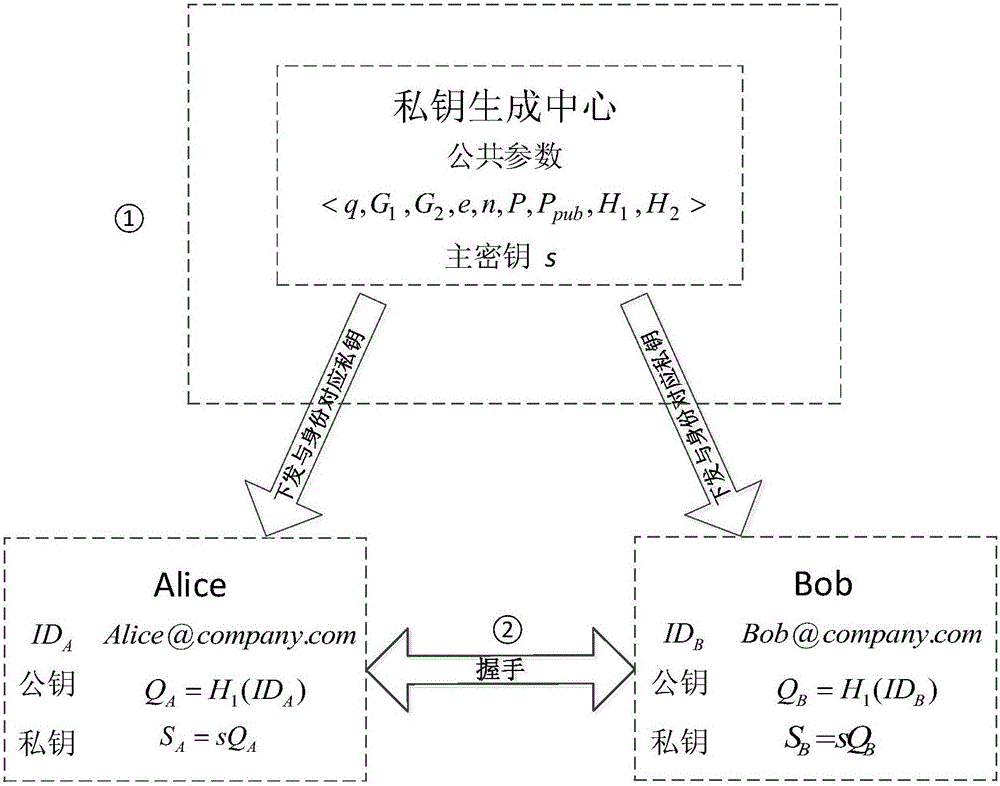
[0058] The purpose of the present invention is to propose an identity-based TLS handshake protocol, which can get rid of the troubles of certificate transmission and verification, simplify the handshake process, complete the authentication of both parties at the same time, and establish a secure session. The present invention will be described below in conjunction with a specific embodiment in which a user Alice (abbreviated as A) in the same domain initiates a secure connection to a user Bob (abbreviated as B). In this embodiment, a credible self-trust authority (Self-Trust Authority, STA) in the domain completes the task of the PKG.
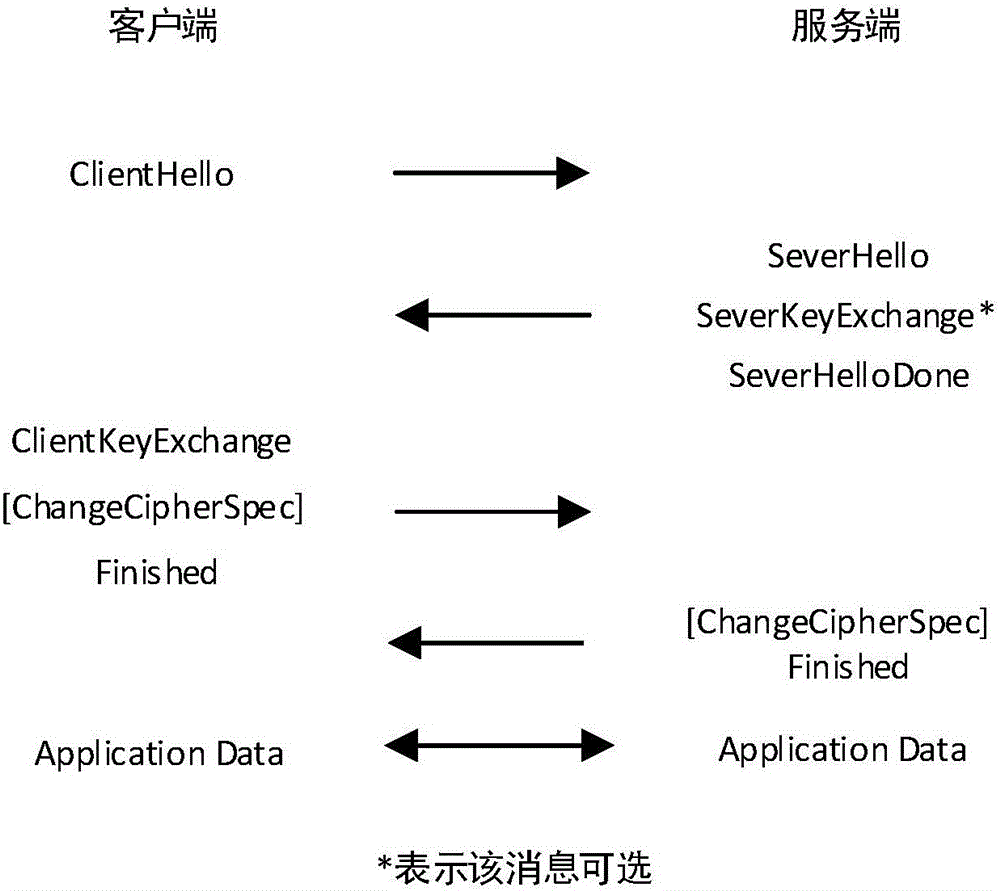
[0059] Such as Figure 1-2 Shown, overall process of the present invention comprises the following steps:
[0060] 1) Establishment of an identity-based cryptographic system and distribution of private keys;
[006...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com