Secure data transmission method and device of middleware based on hybrid cipher suite
A hybrid cipher and cipher suite technology, applied in the field of information security, can solve the problems of uncontrollable data transmission security and uncontrollable security strength of foreign standard cipher algorithms.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0095] In order to enable those in the technical field to have a better understanding of the use of mixed cipher suites for middleware and clients to securely transmit data, first introduce in detail how middleware and clients generate symmetric keys according to the SSL / TLS handshake protocol in the embodiment of the present invention process.
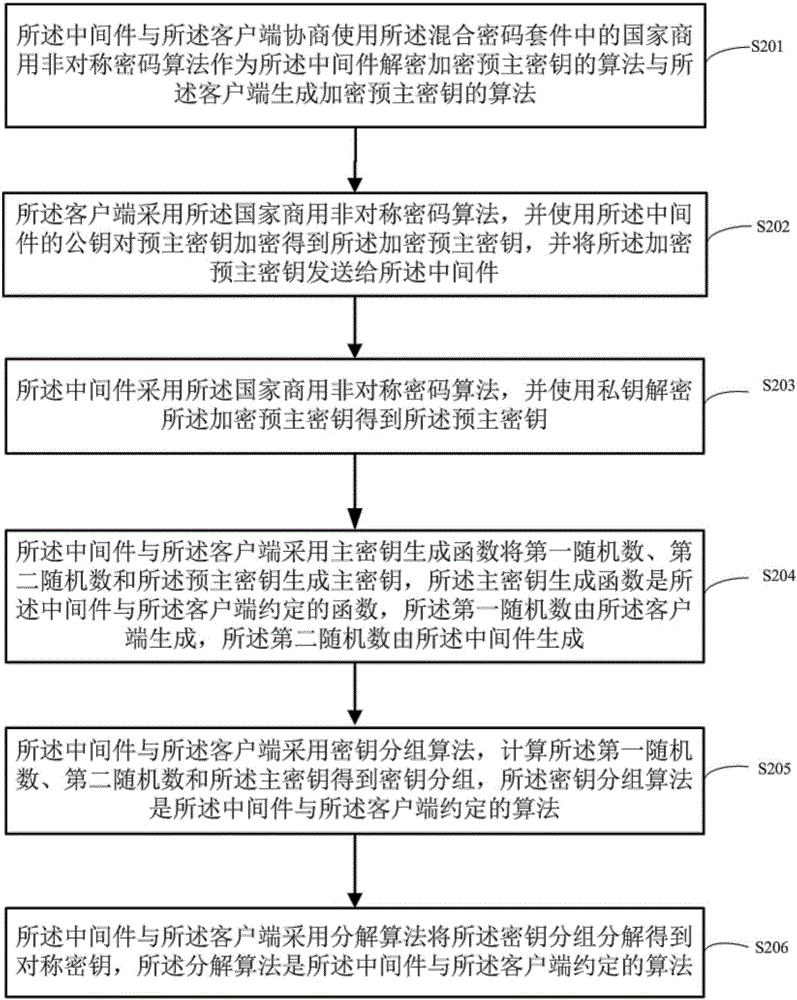
[0096] see figure 2 , is a flow chart of the middleware and the client using a mixed cipher suite to generate a symmetric key in the embodiment of the present invention, and the specific steps may include:
[0097] Step S201: The middleware negotiates with the client to use the national commercial asymmetric encryption algorithm in the mixed cipher suite as the algorithm for the middleware to decrypt and encrypt the pre-master key, and generates an encrypted pre-master key with the client key algorithm.
[0098] In order for the middleware and the client to generate a symmetric key, both the middleware and the client must obtain th...
Embodiment 2
[0135] A secure connection needs to be established between the middleware and the client using a mixed cipher suite for secure data transmission. The embodiment of the present invention introduces in detail the process of establishing a secure connection between the middleware and the client. The embodiment of the present invention is based on Embodiment 1, namely On the basis that both the middleware and the client have obtained the symmetric key, the middleware and the client establish a secure connection according to the SSL / TLS handshake protocol.
[0136] see Figure 4 , is a flow chart of establishing a secure connection between the middleware and the client on the basis of obtaining a symmetric key in the embodiment of the present invention, and the specific steps may include:
[0137] Step S400: The middleware decapsulates the encapsulated encrypted data request information sent by the client, and securely connects with the client at the SSL / TLS layer.
[0138] When t...
Embodiment 3
[0149] The embodiment of the present invention introduces in detail the process of establishing a secure connection between the client and the middleware. The embodiment of the present invention is based on Embodiment 1, that is, on the basis that both the client and the middleware have obtained a symmetric key. The SSL / TLS handshake protocol specifies the secure connection established with the middleware.
[0150] see Figure 5 , is a flow chart of the client establishing a secure connection with the middleware on the basis of obtaining the symmetric key in the embodiment of the present invention, and the specific steps may include:
[0151]Step S500: the client sends encapsulated encrypted data request information to the middleware, wherein the key used in the encrypted data request information is the symmetric key obtained by the method in Embodiment 1.
[0152] The client encapsulates the encrypted data request information according to the HTTPS protocol, and sends the en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com