Realization method for reasonable construction and correct parse of communication data package based on alarm system
An implementation method and an alarm system technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as unsound communication protocols, difficulty in realizing correct data encapsulation and analysis, and easy leakage of data transparent transmission, etc., to achieve The effect of increasing time complexity and improving transmission speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
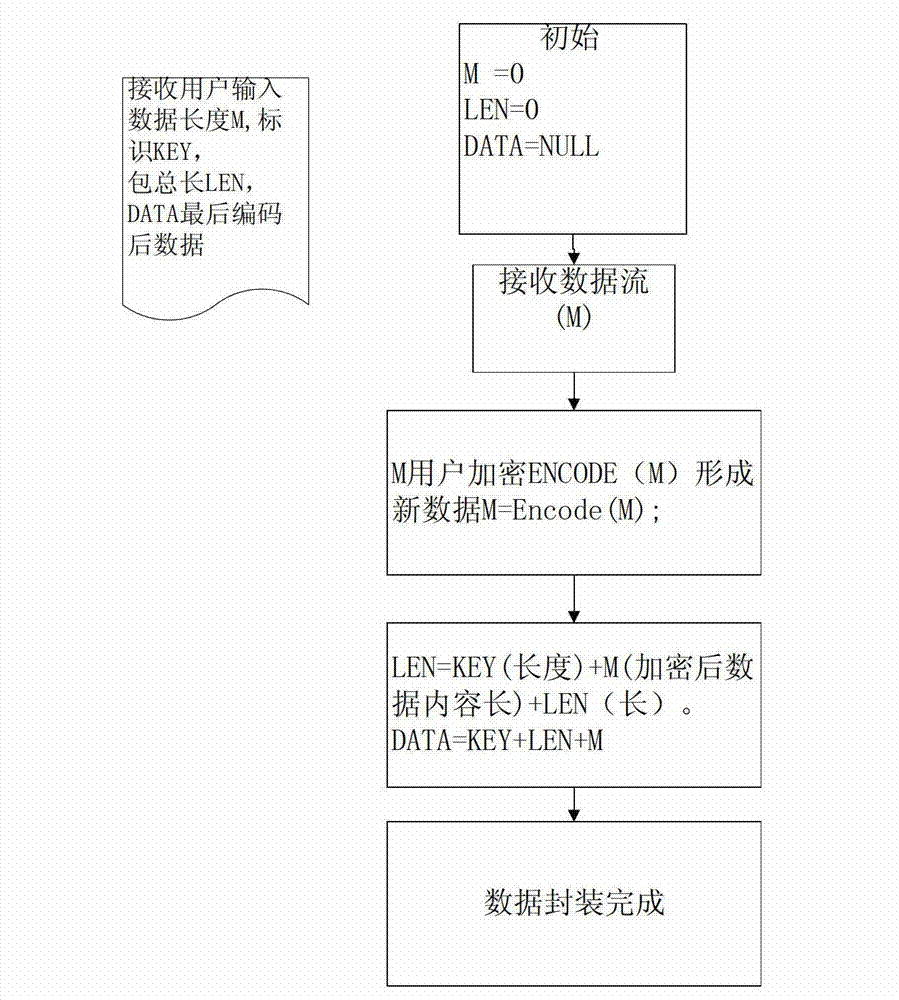
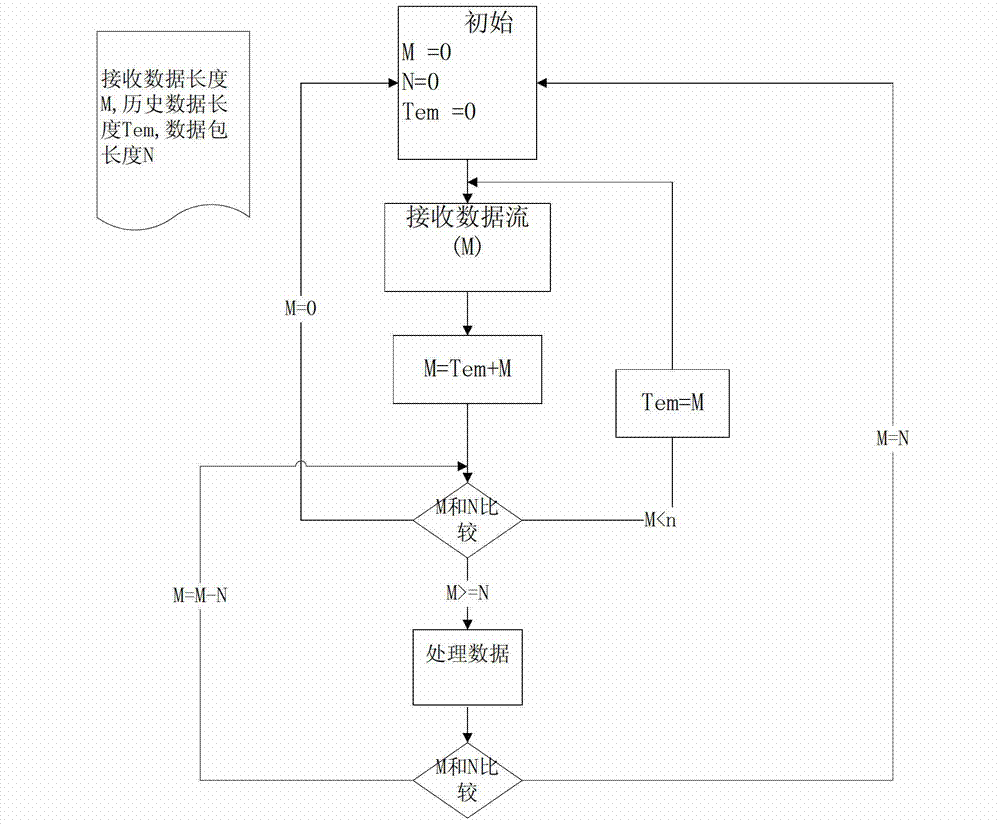
[0039] ILD encoding refers to encoding Key, Length, Cmd, and Value to form a bit stream data packet; decoding is the inverse process of encoding, which is to parse and restore the original data from the bit stream buffer. Specific examples are as follows:
[0040] 1 Packet format:
[0041] Baotou (Headkey)
Packet length (Len)
Command (Cmd)
content
Byte 1~2
Byte 3~6
Byte 7~8
[0042] in:
[0043] Baotou (Headkey): fixed to 0x3995
[0044] Packet length (Len): the length of the entire data packet header, 2+4+2+content length
[0045] Command (Cmd): used to indicate the type of content contained in the packet
[0046] Content: the actual data content
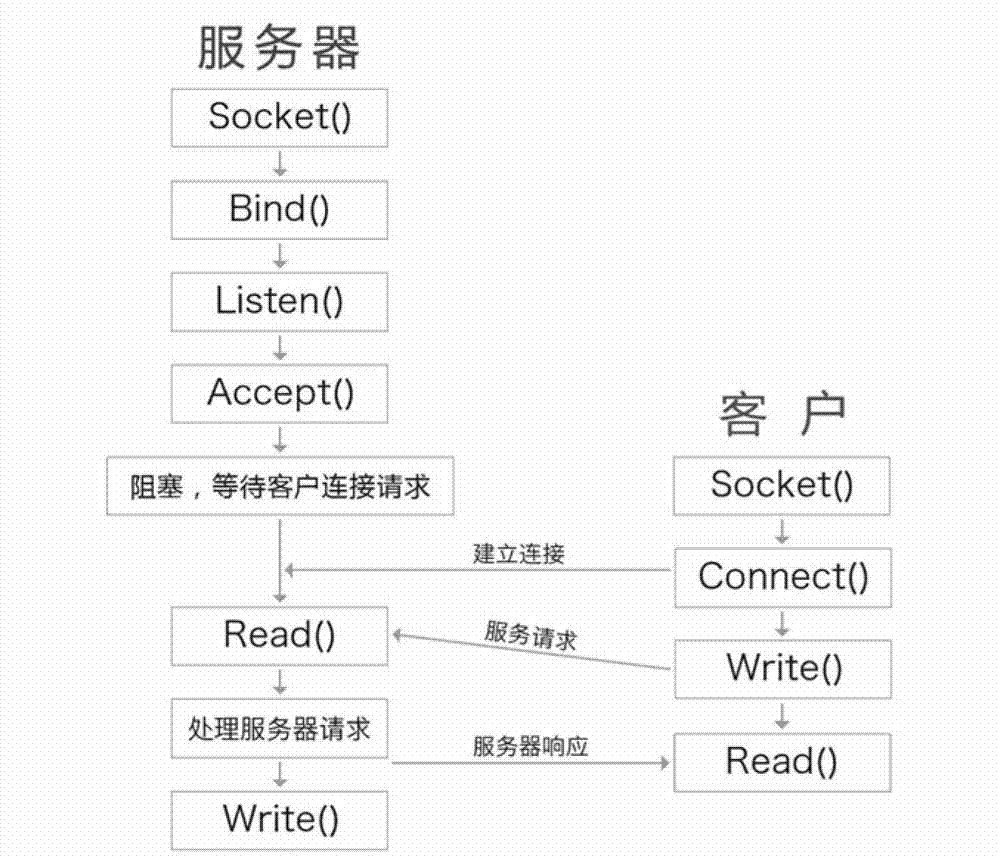
[0047] 2 center login:
[0048] It is used for each center to connect to the designated server and obtain the information of the equipment under the jurisdiction of the center from the server.
[0049] Center→Server: Cmd=10001
[0050]
[0051]
[0052] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com