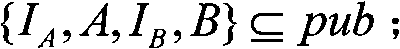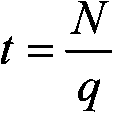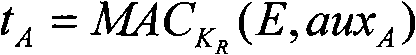Method for authentication for resisting secrete data disclosure and key exchange based on passwords
A secret data and key exchange technology, applied in the field of cryptographic protocols, can solve the problems of endangering the security of the protocol, leaking, combining, etc., and achieve the effect of improving online computing efficiency, protecting privacy, and ensuring high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0109] Password registration: user "B" can calculate and store B in advance -1 . When user "A" registers password w with user "B", user "B" calculates H(w, I A , I B ) and let β be H(w, I A , I B ) is a 32-bit prefix. User "B" calculates B -tbβ ∈ G′ and B tbβ ∈G′, delete β and make B -tbβ and / or B tbβ Stored in the entry for user "A" in the database.
[0110] Role marking: Suppose users "A" and "B" have exchanged two random numbers R during the parameter negotiation phase A and R B (and user "B"'s public key certificate), ie: user "A" sends R A , user "B" sends R B . Let the role of user "A" be denoted as: r A =R A ‖R B ; The role of user "B" is denoted as r B =R B ‖R A ; where "‖" is the string concatenation operator. R A The transmission of can be included in the following message sent by user "A" in ciphertext.
[0111] We give a specific implementation of the ECIES public key encryption algorithm based on standardization documents such as ANSI X9.63, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com