Method and system for safe transmission of batch of data
A technology for batch data and secure transmission, applied in the field of information security, it can solve problems such as the inability to guarantee the security of batch data, the inability to know whether other target data has been tampered with or stolen, and the ease of use discount.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
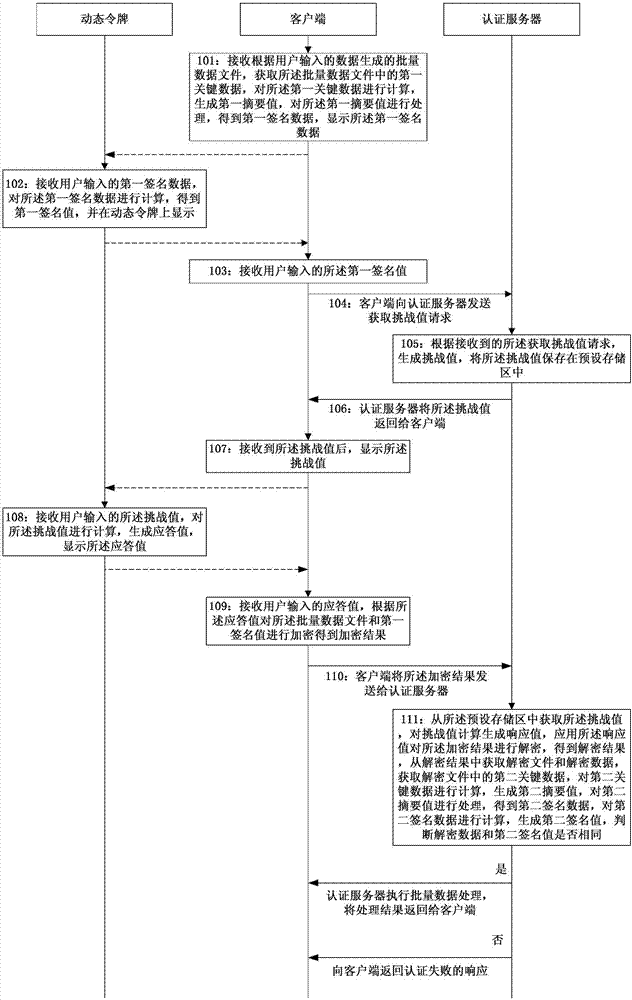
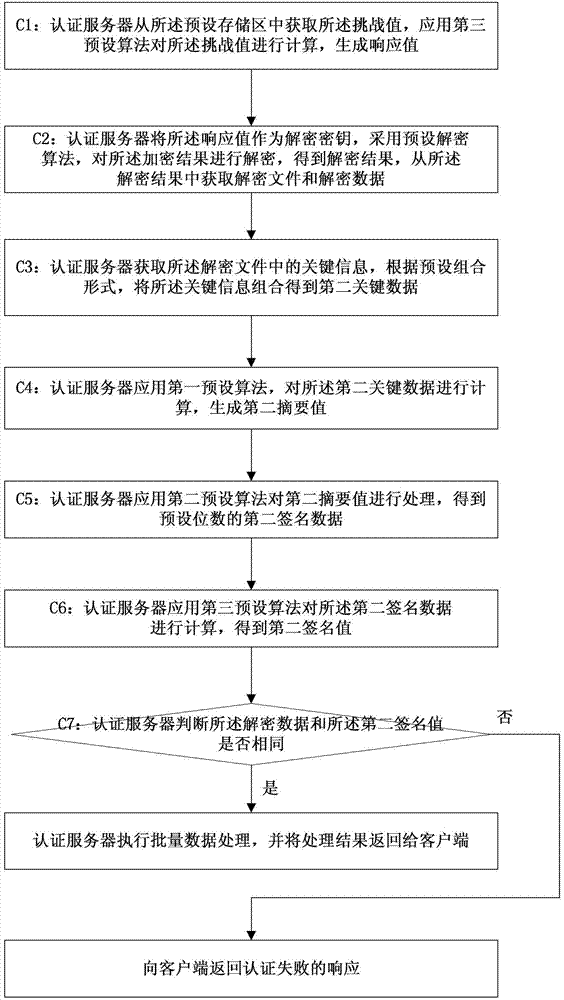
[0172] see figure 1 , Embodiment 1 of the present invention provides a method for secure batch data transmission. In this embodiment, preferably, the corresponding Corresponding default algorithm;
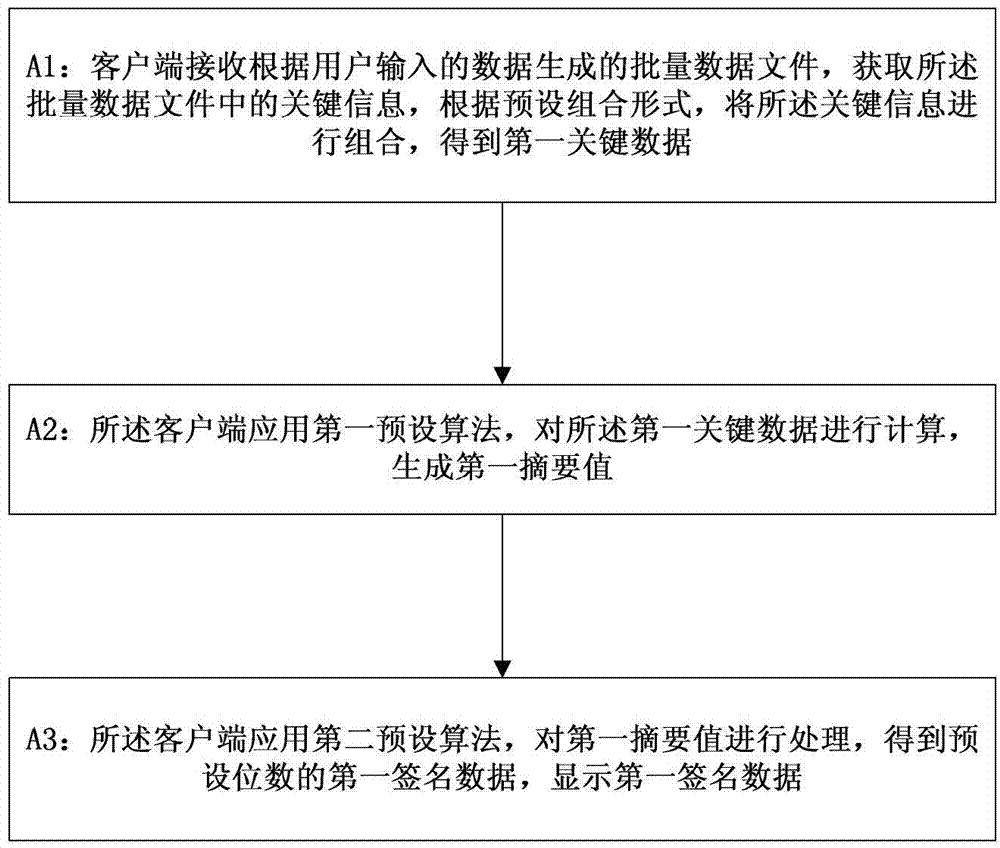
[0173] Step 101: The client receives the batch data file generated according to the data input by the user, obtains the first key data in the batch data file, calculates the first key data, generates a first summary value, and calculates the first key data in the batch data file. A summary value is processed to obtain the first signature data, and display the first signature data;
[0174] see figure 2 , the step 101 is specifically:
[0175] Step A1: The client receives the batch data file generated according to the data input by the user, obtains key information in the batch data file, and combines the key information according to a preset combination form to obtain the first key data;
[0176] In this embodiment, preferably, the batch data file can be a CSV file or a text f...
Embodiment 2
[0326] see Figure 4 , Embodiment 2 of the present invention provides a system structure diagram for secure batch data transmission, including: a client 100, an authentication server 200 and a dynamic token 300;
[0327] The client 100 includes:
[0328] The first receiving module 101: used to receive batch data files; used to receive the first signature value displayed on the dynamic token 300 input by the user; used to receive the challenge value sent by the authentication server 200; used to receive the user The input response value displayed on the dynamic token 300; used to receive the processing result or authentication failure response sent by the authentication server 200;
[0329] The first sending module 102: used to send a challenge value acquisition request to the authentication server 200; used to send the encrypted result encrypted by the first encryption module 107 to the authentication server 200;
[0330] The first obtaining module 103: for obtaining the fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com