Privacy protection method based on verifiable symmetric searchable encryption
A privacy protection and symmetric technology, applied in the privacy protection field of symmetric searchable encryption, it can solve problems such as data integrity cannot be guaranteed, and achieve the effect of ensuring freshness, improving efficiency, and preventing replay attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with specific examples.
[0032] A privacy protection method based on verifiable symmetric searchable encryption implemented based on the above system, which specifically includes the following steps:
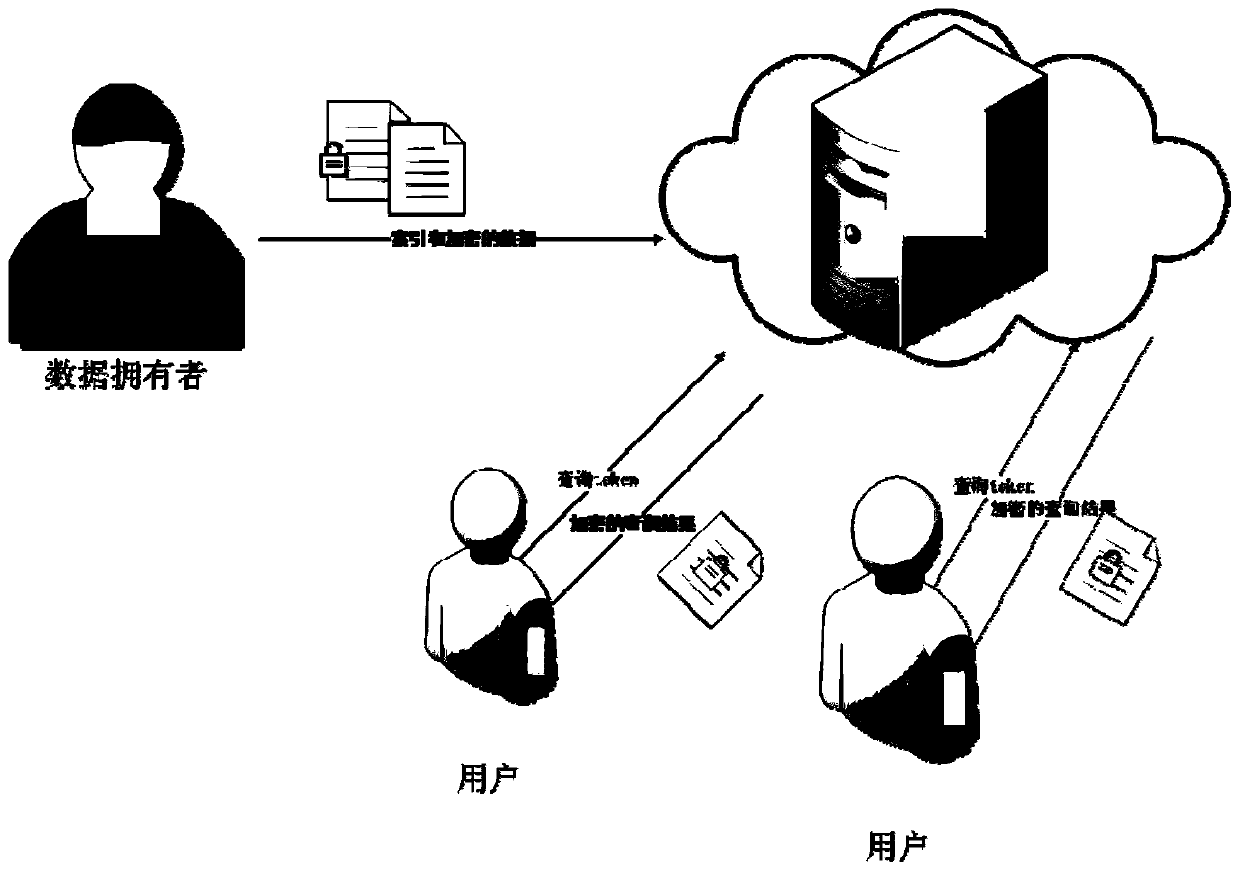
[0033] Step 1: Data owner establishment phase
[0034] The data owner generates 3 keys k according to the symmetric encryption key generation algorithm in cryptography 1 、k 2 、k 3 , generate a pair of keys (ssk, spk) (public key and private key) according to the asymmetric encryption key algorithm in cryptography.
[0035] The data owner creates a data reverse list △, that is, establishes the name identification (ID) of the document corresponding to each keyword, for example, word1 exists in document D 1 、D 2 , establish i ,D i > key-value pairs like this.
[0036] Step 2: Data owner initial...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com