Method for safely and efficiently fusing data
A data fusion and high-efficiency technology, which is applied to the public key and key distribution of secure communication, can solve the problems of limited communication capacity, computing power, and storage space, and achieve energy saving, integrity assurance, and data flow reduction. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0039] The query base station BS has private parameters l, θ, private key sk, and public key pk. Among them, l, θ, sk are kept secret, and pk is made public. For node i participating in data fusion, it has a unique identifier s i , the private parameter θ i , private key a i , public key α i , the private validation parameter γ i = l i alpha i , node i shares the key sn with the querying base station i , l i . where s i , θ i 、a i , γ i , sn i , l i kept secret, i open to the public.
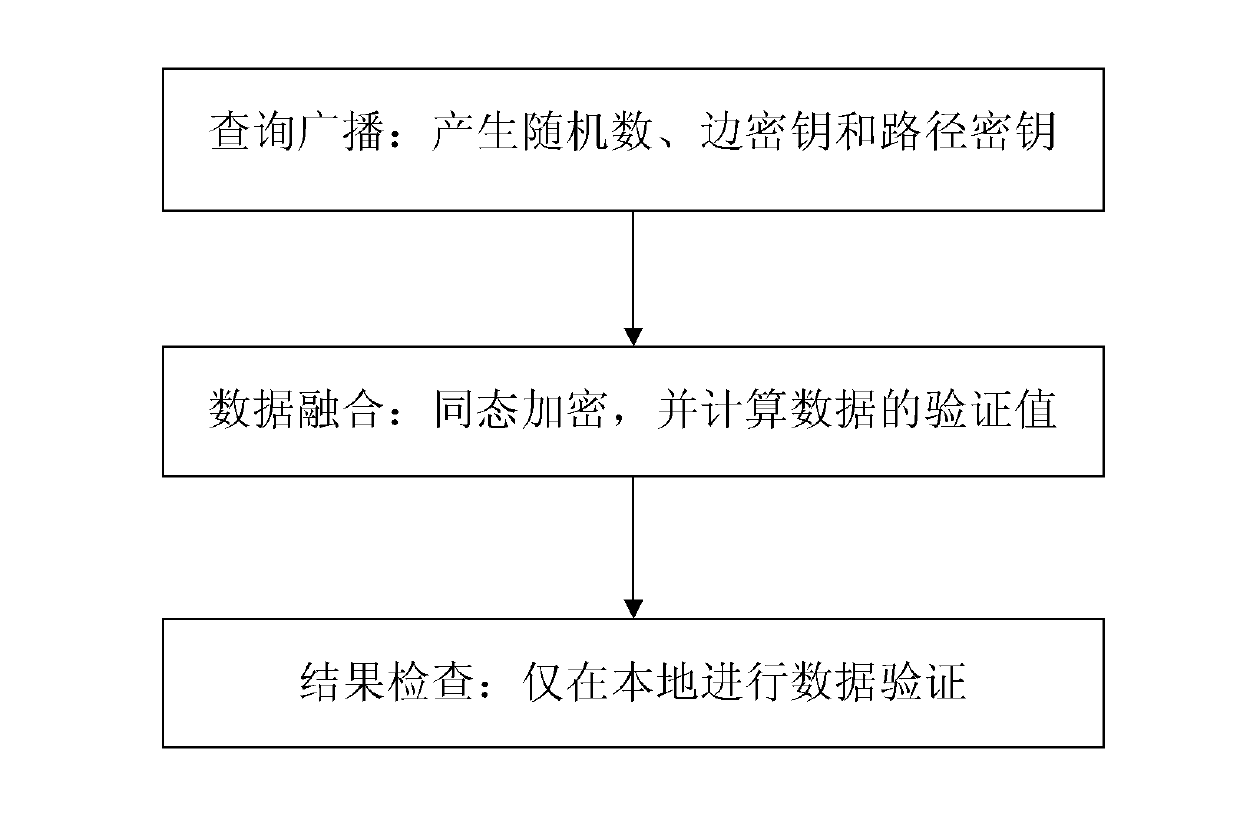
[0040] Step 1. Query Broadcast:
[0041] Step (1): query the base station BS to generate a random number N;
[0042] Step (2): The query base station calculates an edge key (edge-key) and a path key (path-key) according to the network topology of the nodes participating in data fusion. Among them, for leaf nodes, only path keys are calculated; for intermediate nodes, path keys and edge keys are calculated. For any intermediate node i, the edge key is obtained using the key ge...
Embodiment
[0077] Step 1, query broadcast
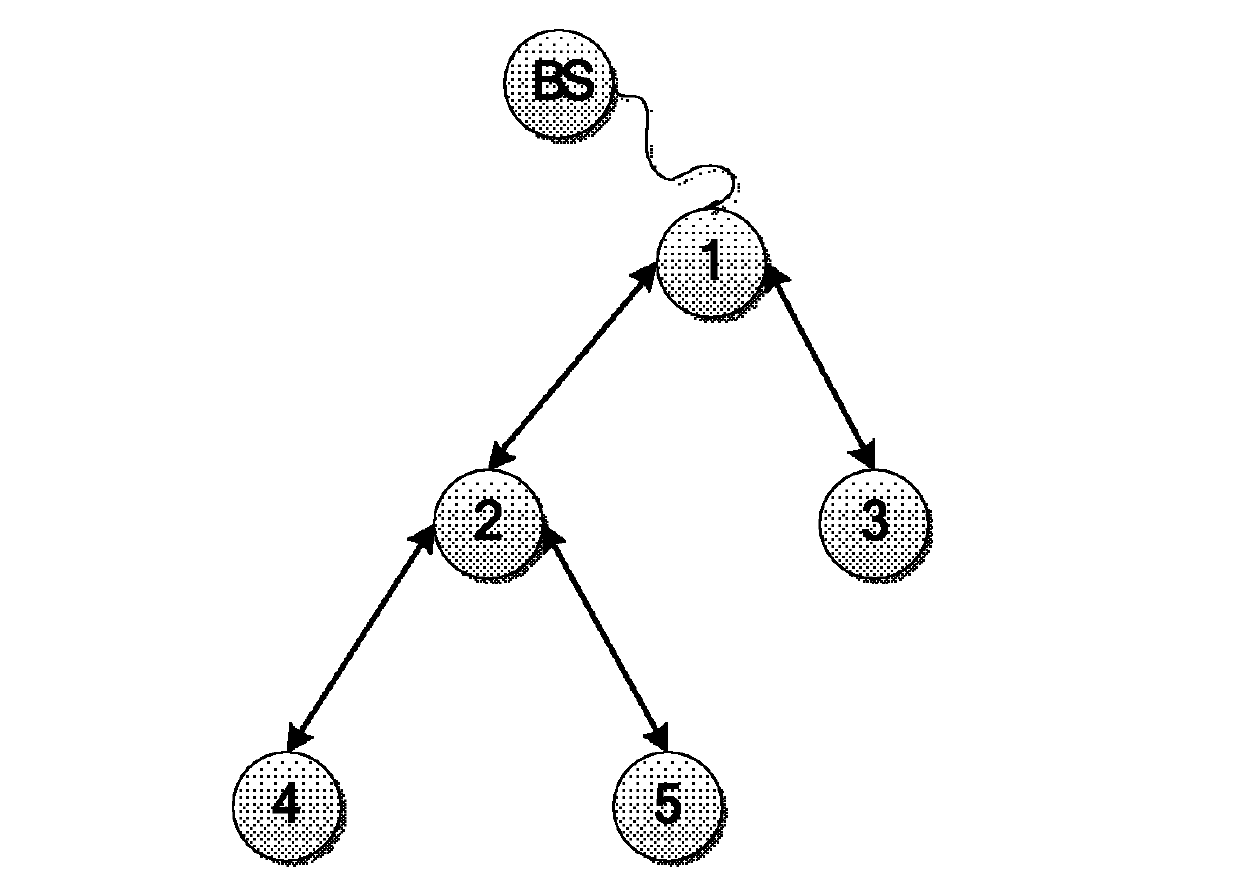
[0078] Step (1): Query the base station to generate a random number 0x92572DACAB723B6BC901B2788C4AF933D675329C;
[0079] Step (2): Query the base station according to figure 2 According to the network topology structure, calculate the path key of leaf node 4 as 0x2EF9446CB80040C855DE14FC5A79A8ECB2B8258A, and perform the same operation for leaf nodes 3 and 5; calculate the path key of intermediate node 2 as 0x21994C1C4A4D530D4BD3914A2428C699DA6878E9; node 2 has child nodes 4 and 5, so its edge density The keys are 0x988E82EB9D3DCC742E7D1985C3D8A209856193CC, 0x8468347EB5D4F765EC3CB2BDCD583A27C1BE921F, and the same operation is performed for node 1;
[0080] Step (3): For node i, the query base station uses the key sn i Encrypt and send to node i.
[0081] Step (4): Node i decrypts the information after receiving the information sent by the base station. Save the random number N, edge key and path key.
[0082] Step 2, data summation and fus...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com