Identity authentication and secret key negotiation method and device in communication network
A technology of communication network and key negotiation, applied in the direction of public key of secure communication, user identity/authority verification, data exchange network, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
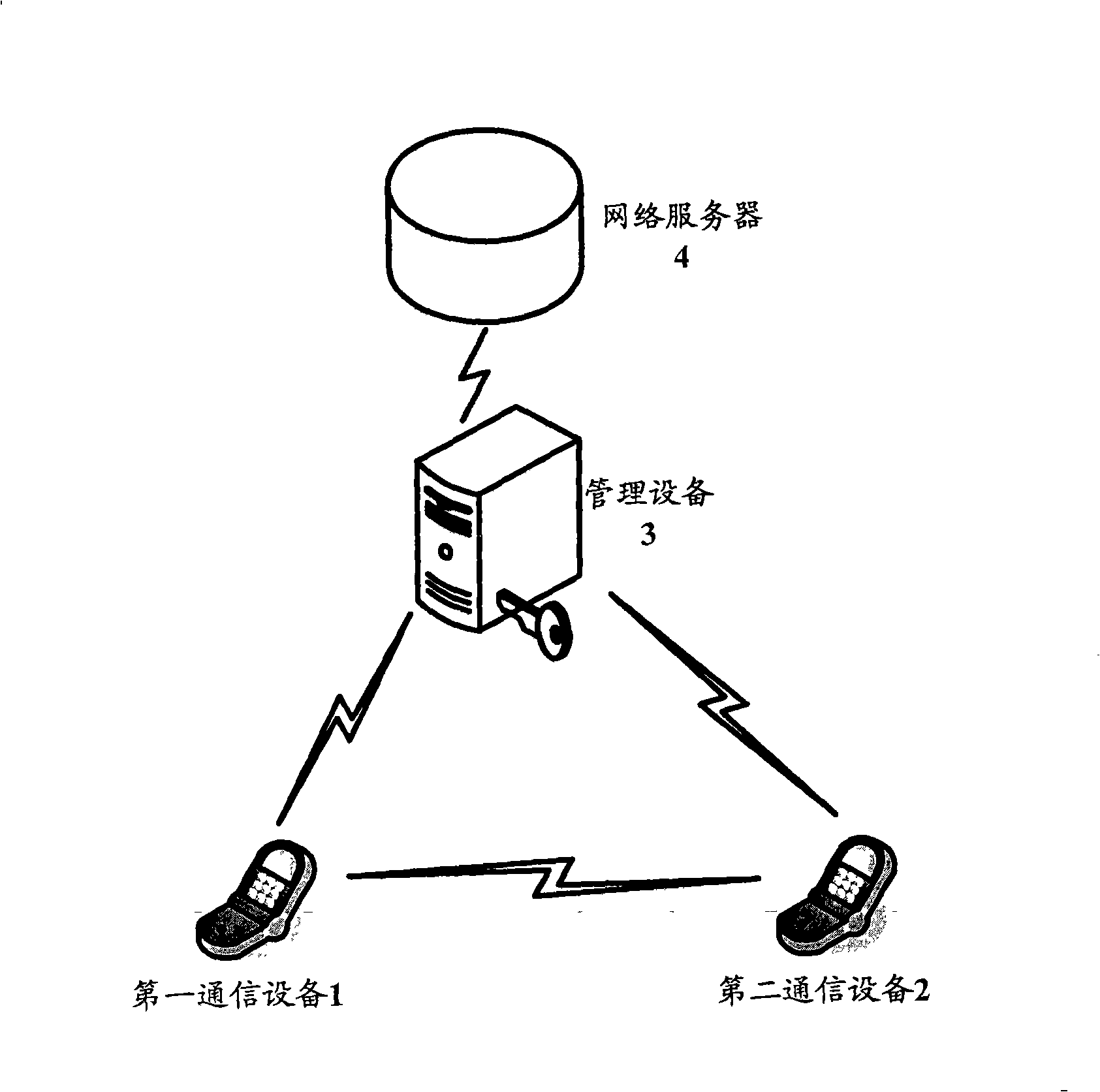
[0030] figure 2 It is a schematic diagram of a communication network for implementing identity-based encryption technology according to a specific embodiment of the present invention. The communication network shown includes: a management device 3 (to avoid confusion, hereinafter referred to as KMC 3 ), a network server 4 and a plurality of communication devices (for simplicity, only the first communication device 1 and the second communication device 2 are shown). where the KMC shown 3 Including the first safety auxiliary device provided by the first aspect of the present invention; the first communication device 1 and the second communication device 2 shown both include the safety communication device provided by the second aspect of the present invention; the network server 4 shown includes the present invention The second safety auxiliary device provided by the third aspect.
[0031] Before describing specific embodiments in conjunction with the accompanying drawings, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com