Method and system for realizing network identity authentication based on two pieces of isolation equipment
A network identity and device isolation technology, applied in the field of secure transactions, can solve problems such as poor user experience, limited storage capacity, hardware cost barriers, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
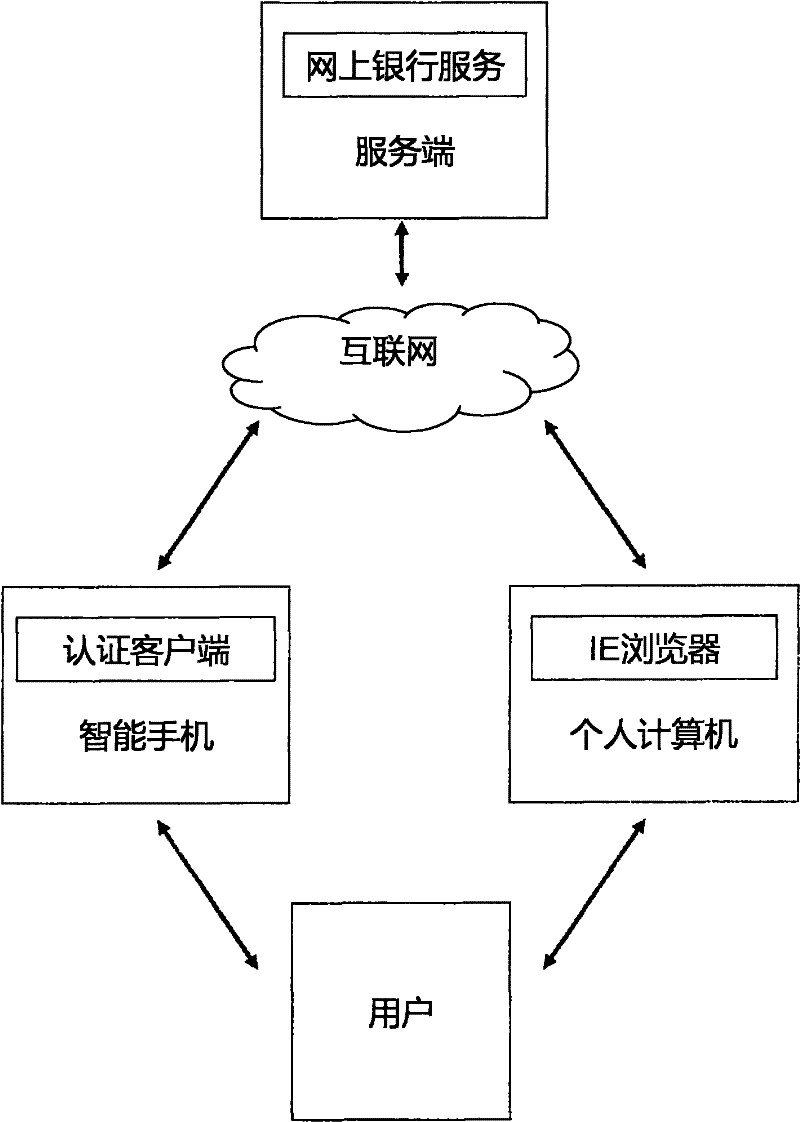
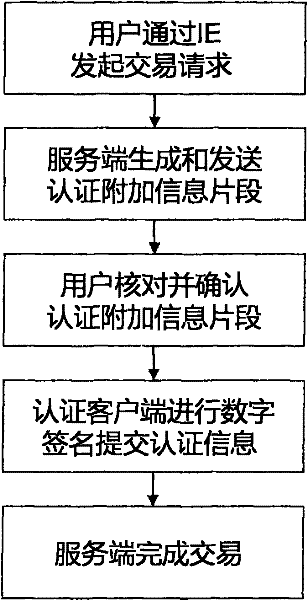
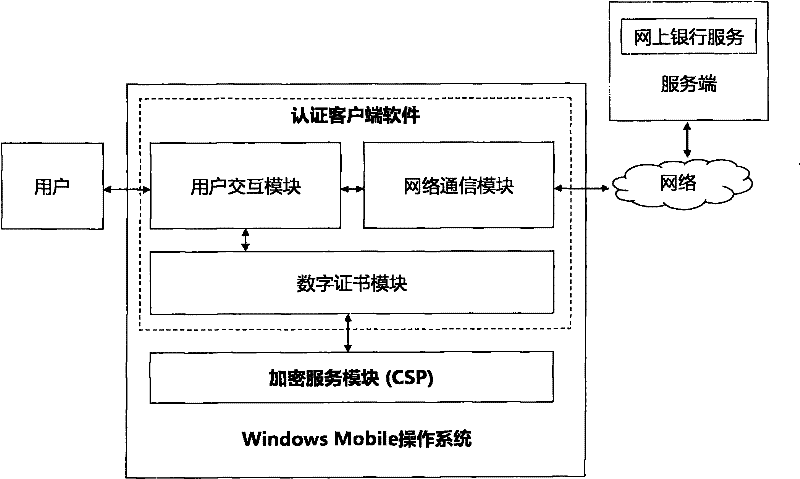
[0031]To facilitate an understanding of the principles and features of the present invention, the following description refers to the implementation of an exemplary embodiment. Specifically, the present invention is aimed at installing Windows 2000 and above operating systems, IE browsers and computers that can access the Internet as ordinary clients, and installing Windows Mobile operating systems that can access Internet smart phones as authentication clients terminal, and an ordinary server connected to the Internet as the server. In addition, the present invention is combined with the PKI public key infrastructure system, and is illustrated for online banking services.
[0032] It should be understood, however, that this is not the only embodiment in which the invention may be practiced. On the contrary, the present invention can be applied to various operating systems, such as Linux, Android, Symbian, Mac OS, Chromc OS operating systems, etc.; can be applied to different ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com