Method and system for evaluating network safety situation
A network security and situation assessment technology, applied in the field of network security, can solve problems such as potential safety hazards, poor real-time performance of tools, and single data source
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
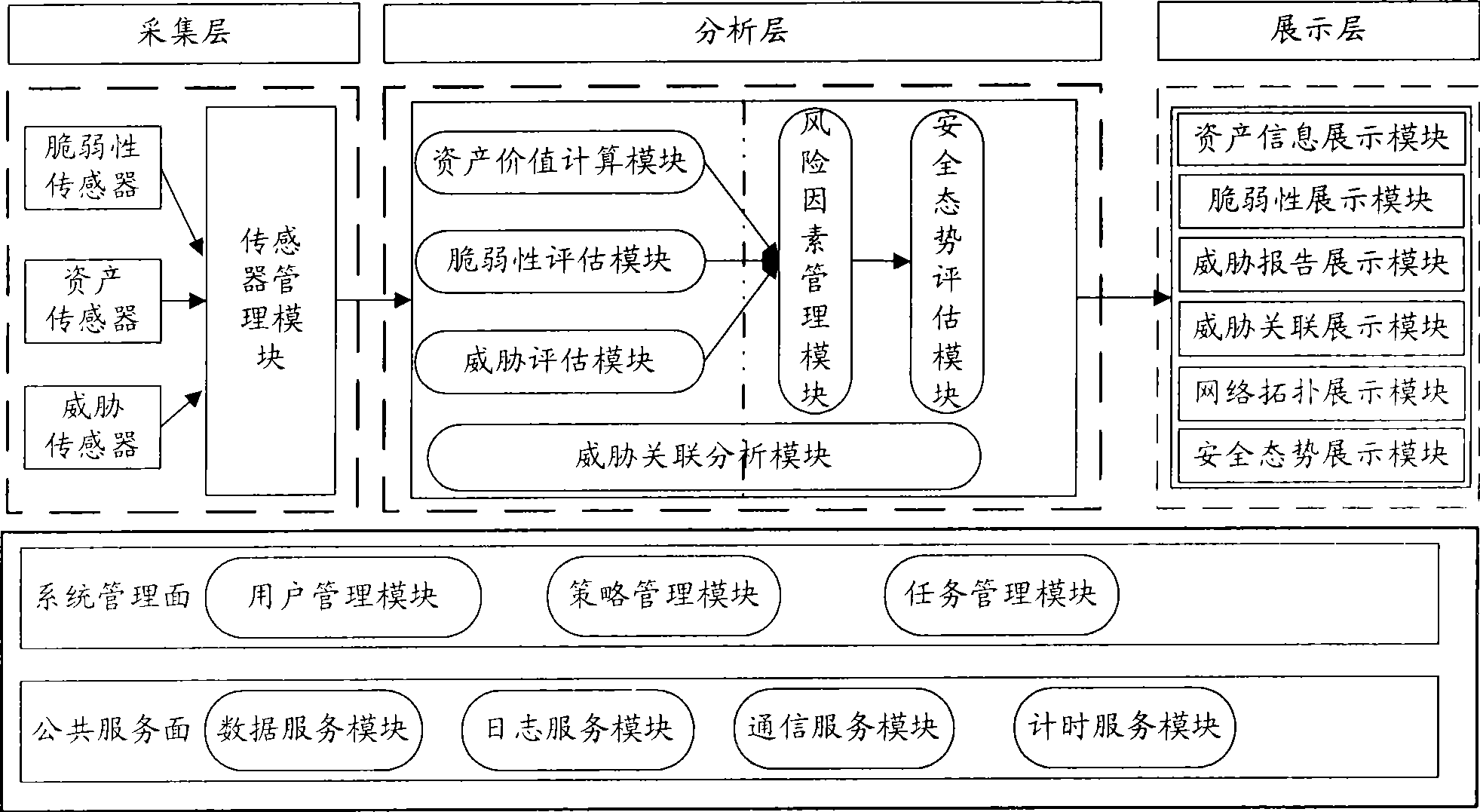
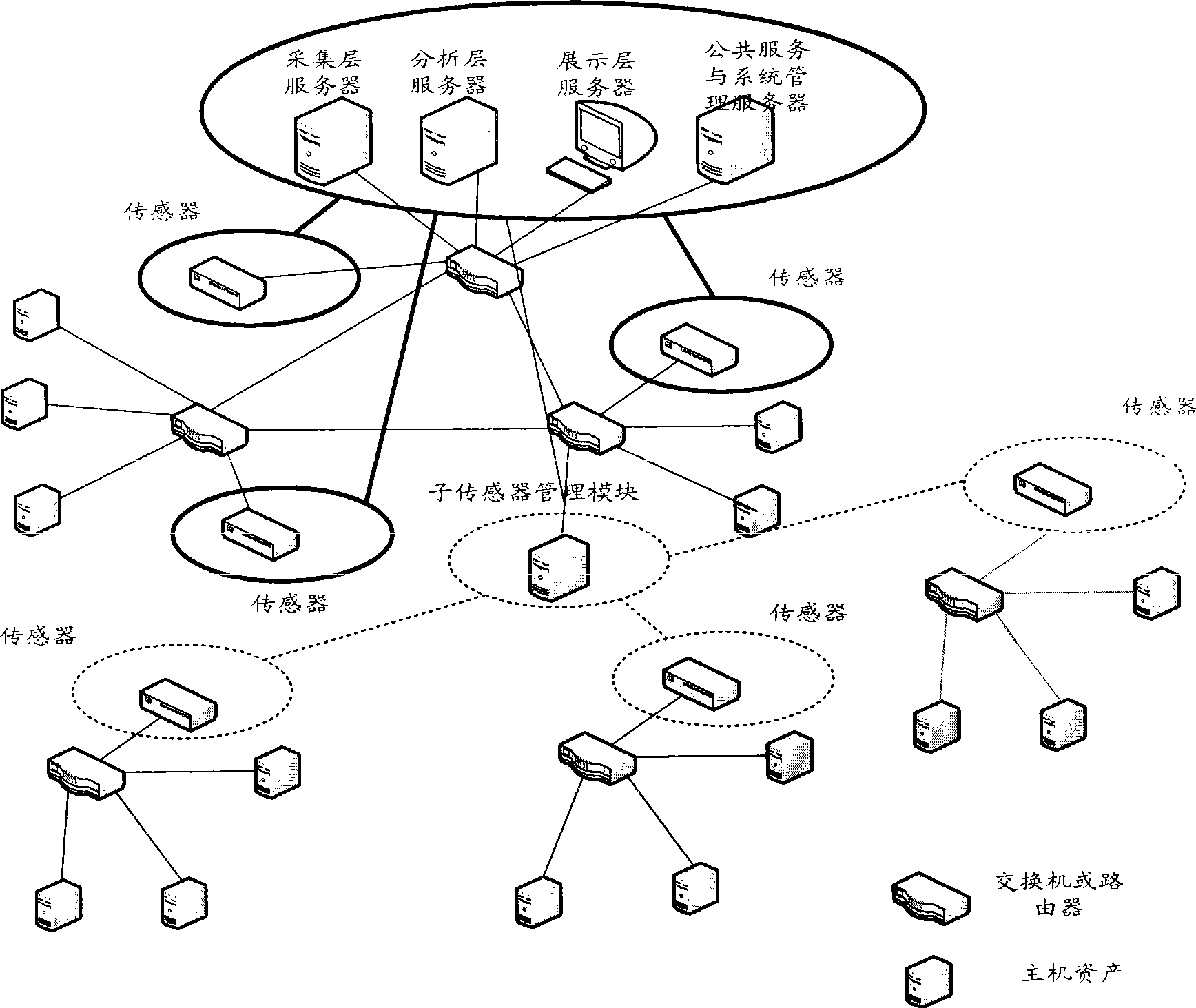
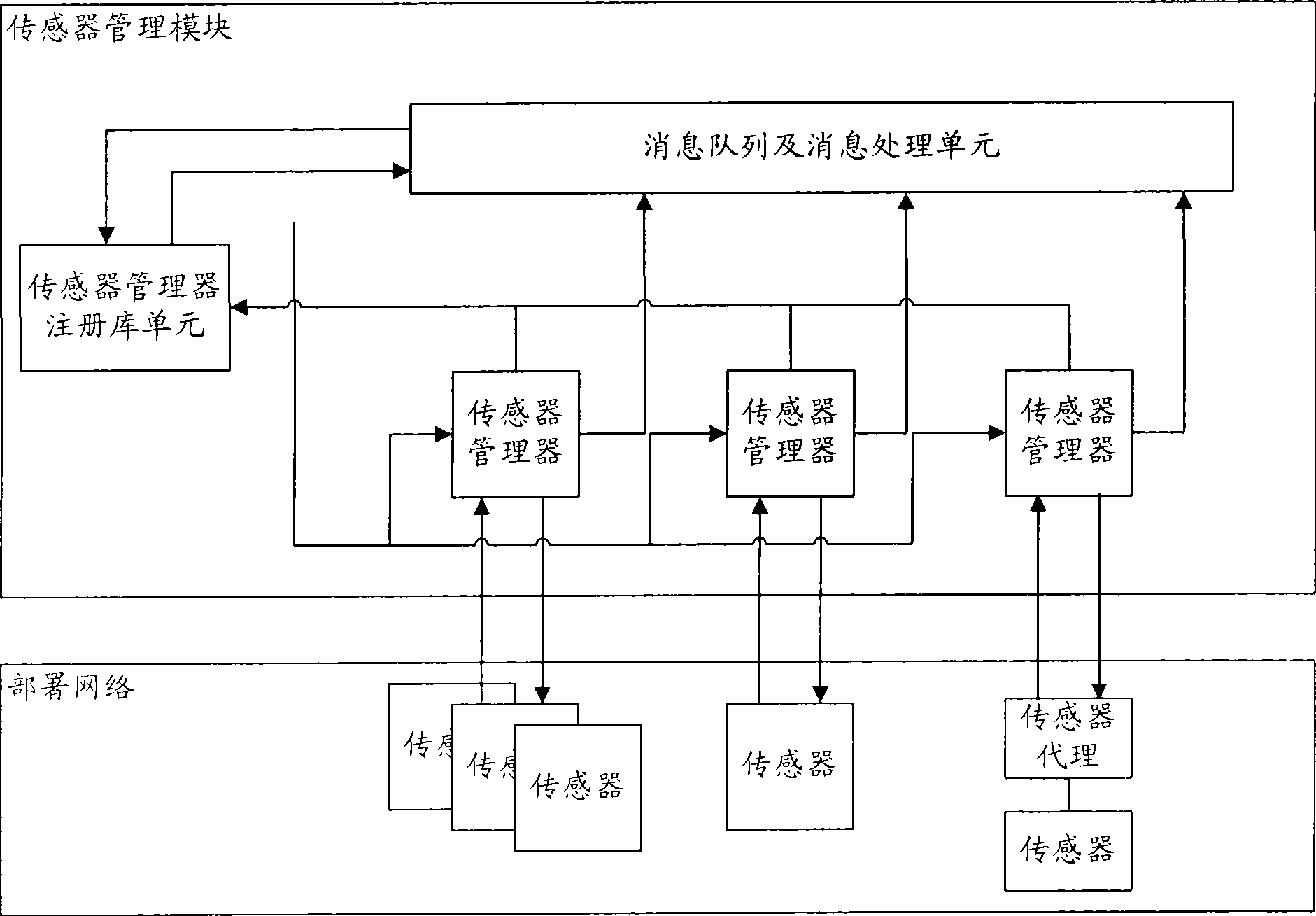
[0062]First explain the definitions of several terms in the present invention: assets are tangible and intangible assets accumulated through information construction, including information equipment, information, production or service capabilities and social reputation; asset value is based on the value of assets in business The value estimated by importance and other relevant factors, the larger the value, the more important the asset is. Vulnerability refers to the deficiencies, loopholes or weaknesses in the security defense of information or assets and their protective measures. The vulnerability value is the vulnerability value evaluated based on the vulnerabilities discovered in the assets. The larger the value, the more important the asset is; the threat It...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com