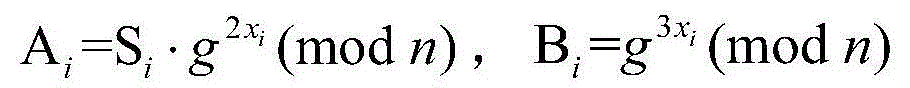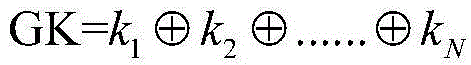Message authentication and group key negotiation method based on vehicle-mounted short distance communication network
A technology of group key negotiation and message authentication, applied in user identity/authority verification, electrical components, transmission systems, etc. Security, the effect of realizing confidential communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
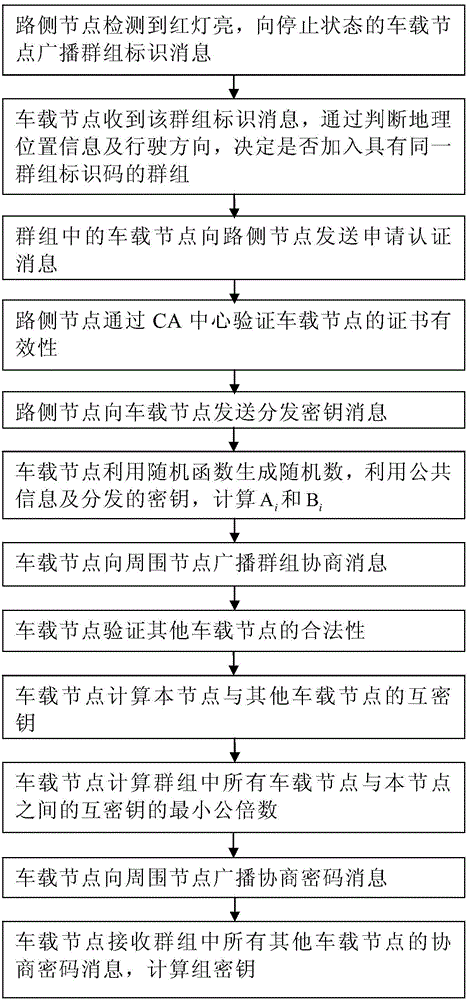
[0039]In the V2X network, the vehicle node regularly broadcasts heartbeat information including its own unique identification, geographical location information, driving direction and other information. At the same time, the vehicle node receives the heartbeat information of surrounding nodes, and can communicate with the vehicle nodes within its communication range. On urban roads, roadside nodes are installed at intersections and other places with heavy traffic flow, and have the characteristics of high installation location, large coverage area, high bandwidth and reliable connection.
[0040] figure 1 It is a schematic flow chart of the method of the present invention. As shown in the figure, the message authentication and group key negotiation method based on the vehicle-mounted short-distance communication network of the present inventi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com