Secret communication method based on fraction order Fourier transform order-multiplexing
A technology of fractional Fourier transform and secure communication, which is applied in the field of information security and can solve the problem that the order of fractional Fourier transform is not fully utilized.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
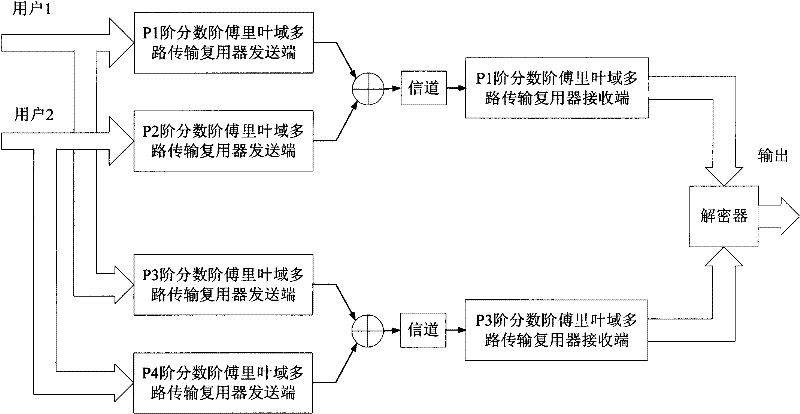
[0036] The secure communication method based on fractional Fourier transform proposed by the present invention comprises the following steps
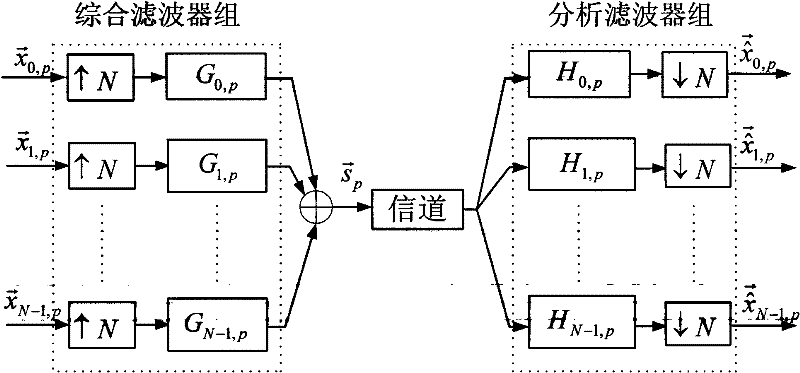
[0037] 1. Design of Fractional Fourier Domain Multiplexer
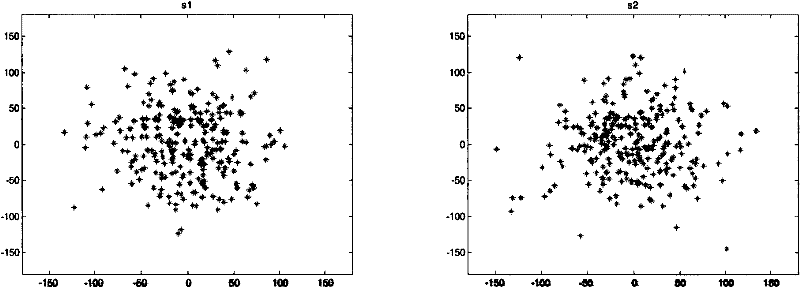
[0038] (1) According to the number M of users in the designed system, select M that satisfies the invertibility condition of matrix C in formula (3) 2 fractional Fourier transform order, and the multiplexing order p is discussed below i The selection method of , the determinant value of matrix C in formula (3) can be expressed as the form shown in formula (8)
[0039] | C | = Π i = 0 M - 1 e - j · 1 2 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com