Two-standard four-real data security access system based on 5G edge computing
An edge computing and data security technology, applied in the field of communication, can solve problems such as low data utilization, low efficiency, and difficulty in accessing data on 4G mobile terminals, and achieve efficient collection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
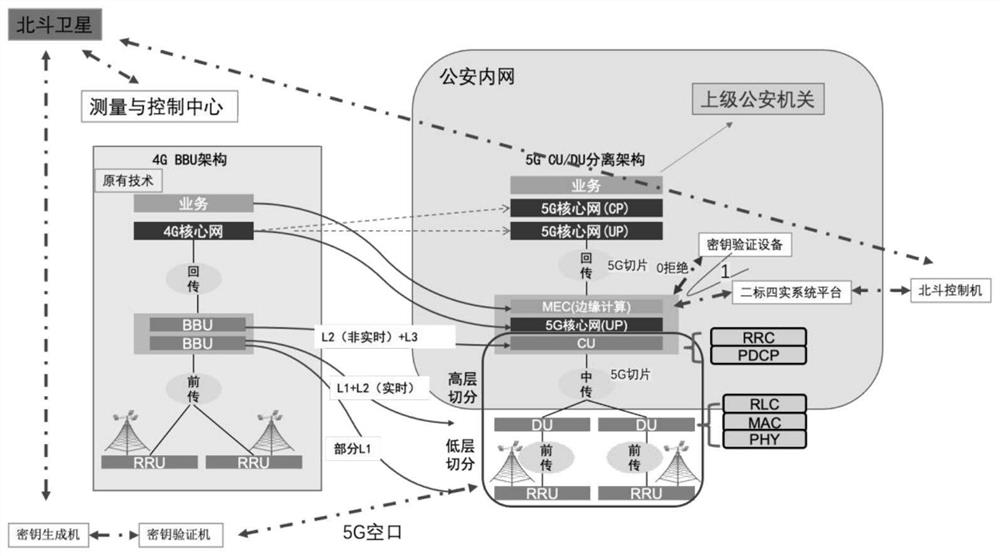
[0059] As a preferred embodiment of the present invention, the key generator specifically includes:
[0060] The face verification module is used to obtain the user's face information, and perform verification according to the user's face information to obtain the first result;
[0061] The ID card verification module is used to obtain the user's ID card information, and perform verification according to the user's ID card information to obtain the second result;
[0062] A key acquisition module, configured to acquire the third result, and send a request to the Beidou controller to acquire a key when both the first result and the second result pass.
[0063] As a preferred embodiment of the present invention, the 5G edge computing system also includes,
[0064] The front-end 5G core network is used to receive the verification result of the key verification device, and control and allow the key verification machine to access the two-standard four-real system platform accordin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com