Method for implementing secret communication of wireless local area network
A technology of wireless local area network and secure communication, applied in the field of secure communication, can solve the problems such as the storage capacity of wireless access points cannot meet the requirements, and the key management tasks are heavy, and achieve a simplified structure, improved data security, and saved system resources. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
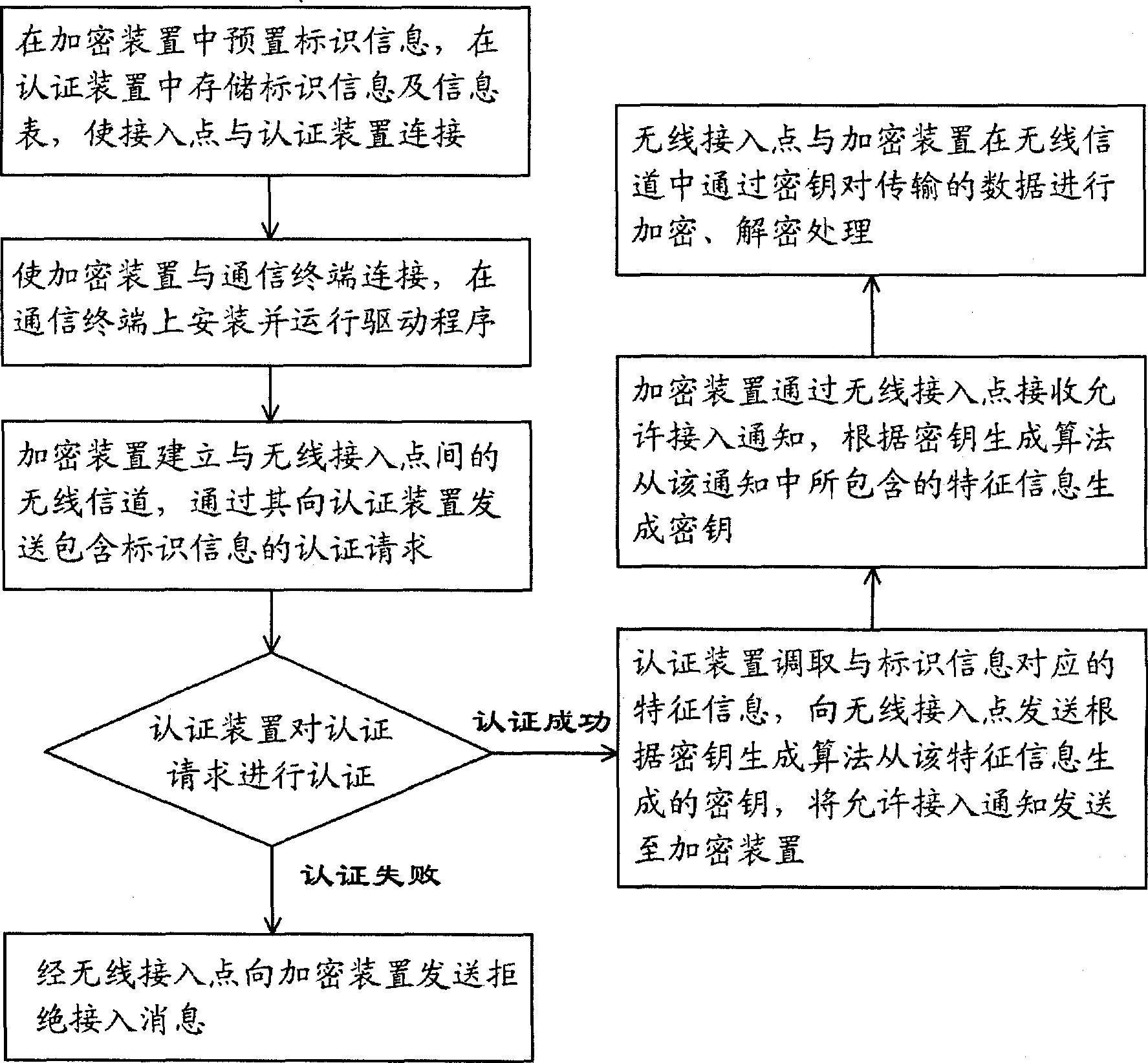
[0021] In order to further illustrate the technical means and functions adopted by the present invention to achieve the intended purpose, the detailed description is as follows in conjunction with the accompanying drawings and embodiments.
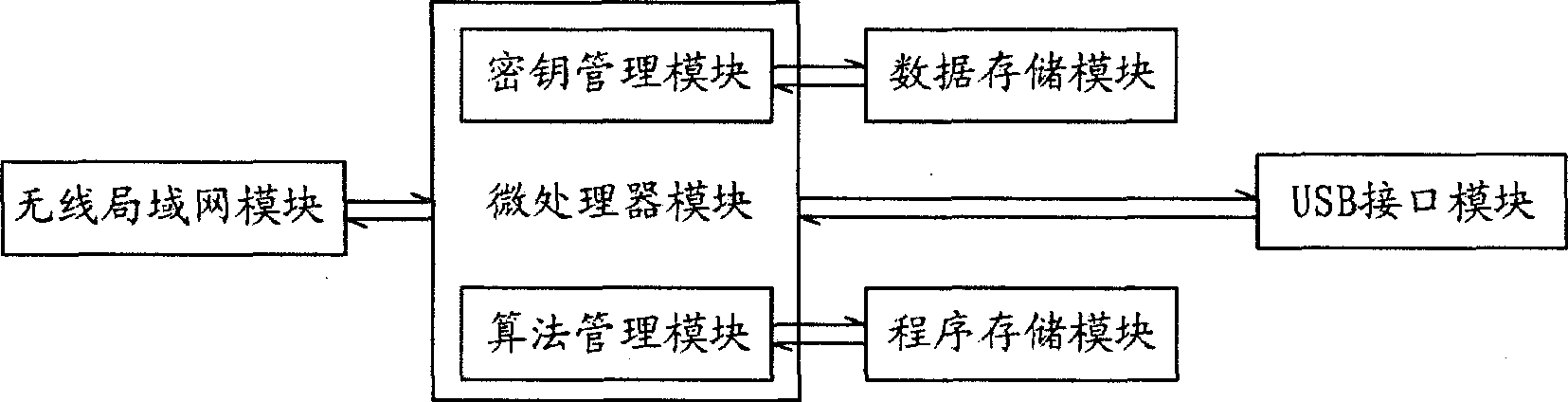
[0022] see figure 1 Shown is the structural block diagram of encryption device of the present invention, and this encryption device comprises:
[0023] Microprocessor module: responsible for data calculation, by calling the data and programs in the data storage module and program storage module, to perform encryption and decryption operations, to complete the encryption and decryption of the information transmitted in the communication, and to prepare to send it through the wireless LAN module The data is encrypted, and the data obtained through the wireless LAN module is decrypted. In addition, the microprocessor module can generate a key from the characteristic information using a key generation algorithm.
[0024] Program storage modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com