Web communication encrypting method
An encryption method and cryptographic algorithm technology, applied in the field of encryption for Web communications, can solve the problems of difficult to effectively protect the confidentiality of sensitive data and user privacy, failure of handshake, and high cost of key negotiation, and achieve business flow optimization. And other web communication security applications, preventing third-party monitoring, easy to promote the effect of realization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
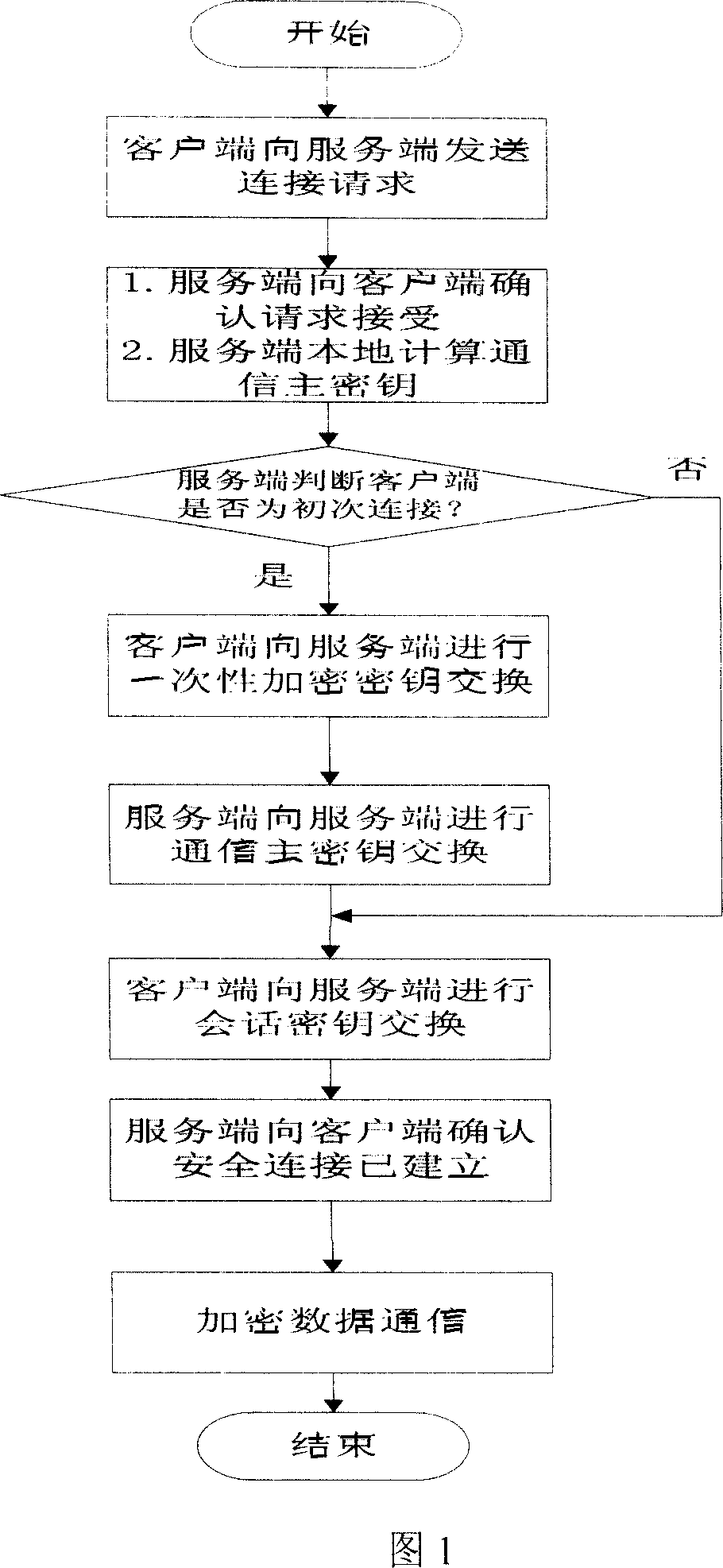
[0039] The specific implementation manner of the present invention will be described in more detail below in conjunction with the accompanying drawings.
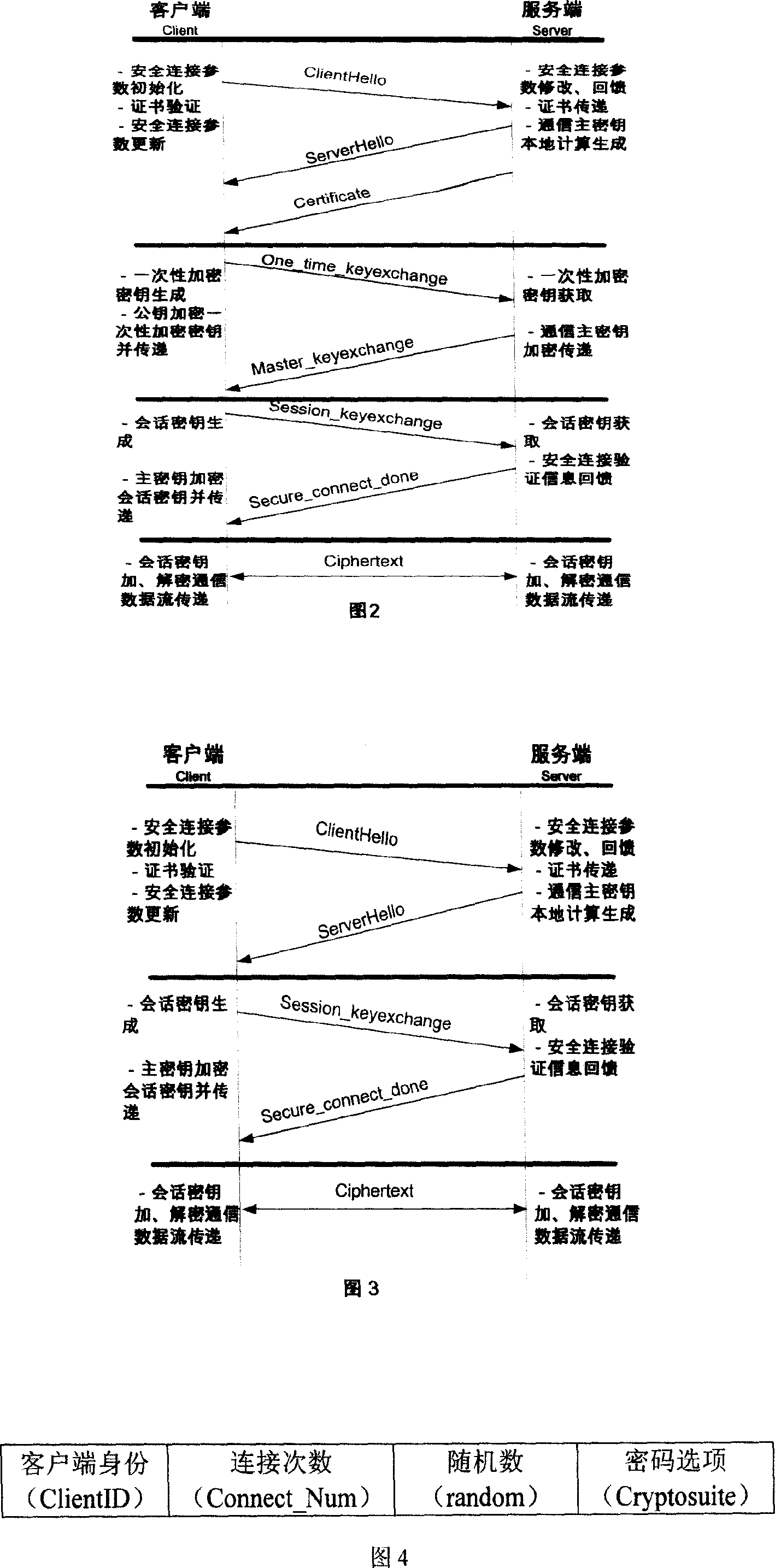
[0040] Referring to Figure 2, the communication encryption method between the client (Client) and the server (Server) for the first time access user is as follows:
[0041] Step 1: Client -> Server: The client sends a ClientHello message to initiate a session connection.
[0042] The fields contained in ClientHello are shown in Figure 4. The message contains fields "ClientID", "Connect_Num", "random", and "ciphersuite". The "ClientID" field is the client ID, and it is "Null" for the first login; the "Connect_Num" field identifies the connection times of the client, and the value is 0 at the first login; the "random" field contains a random number (a one-time random number is used as a communication freshness identification character), the data is randomly generated by the client, including time stamp Tc and random query va...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com