Matrix type key management method for LoRaWAN
A key management, matrix technology, applied in the field of matrix key management for LoRaWAN, to achieve the effect of security improvement, efficient key update, and security improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
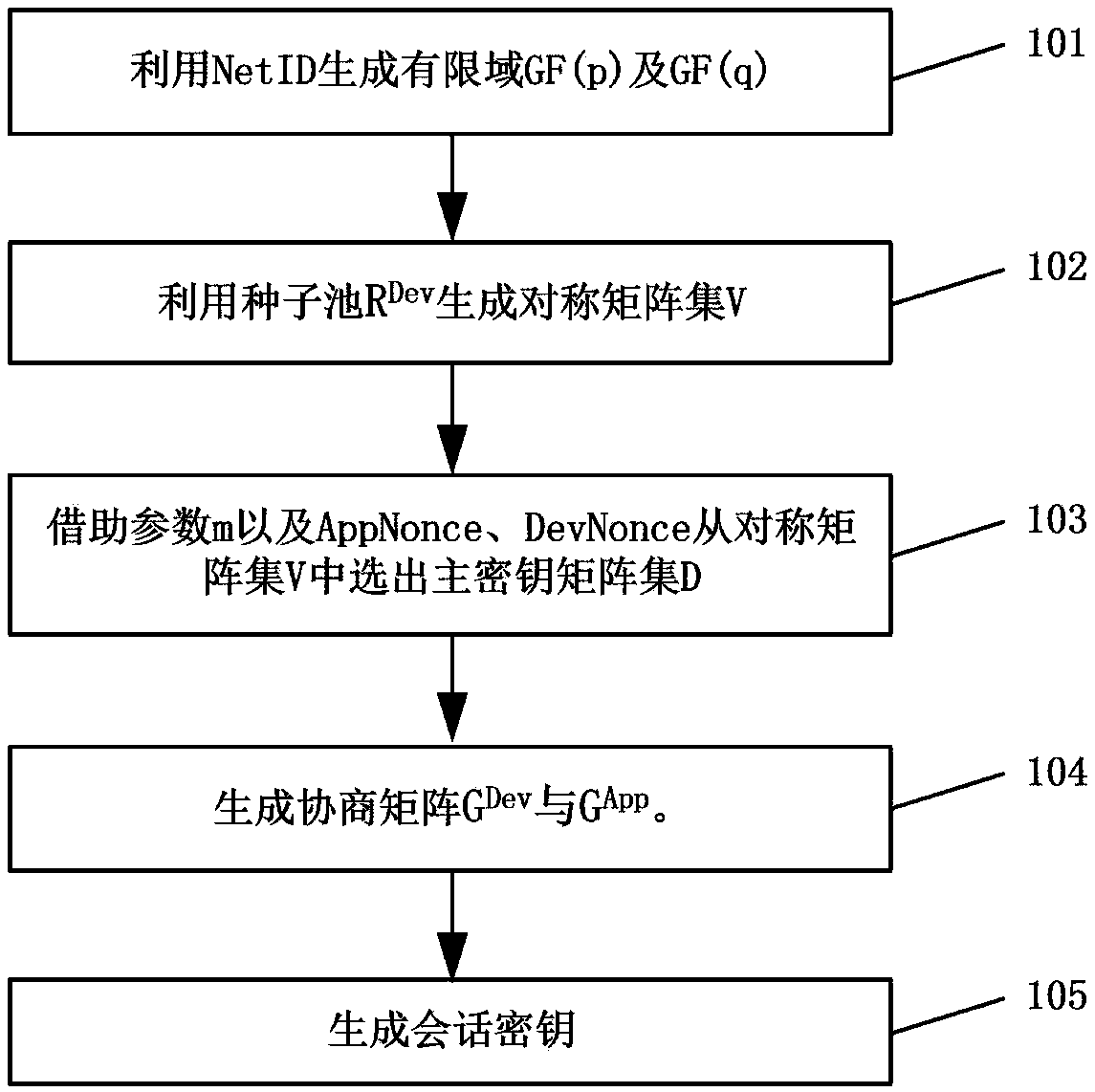
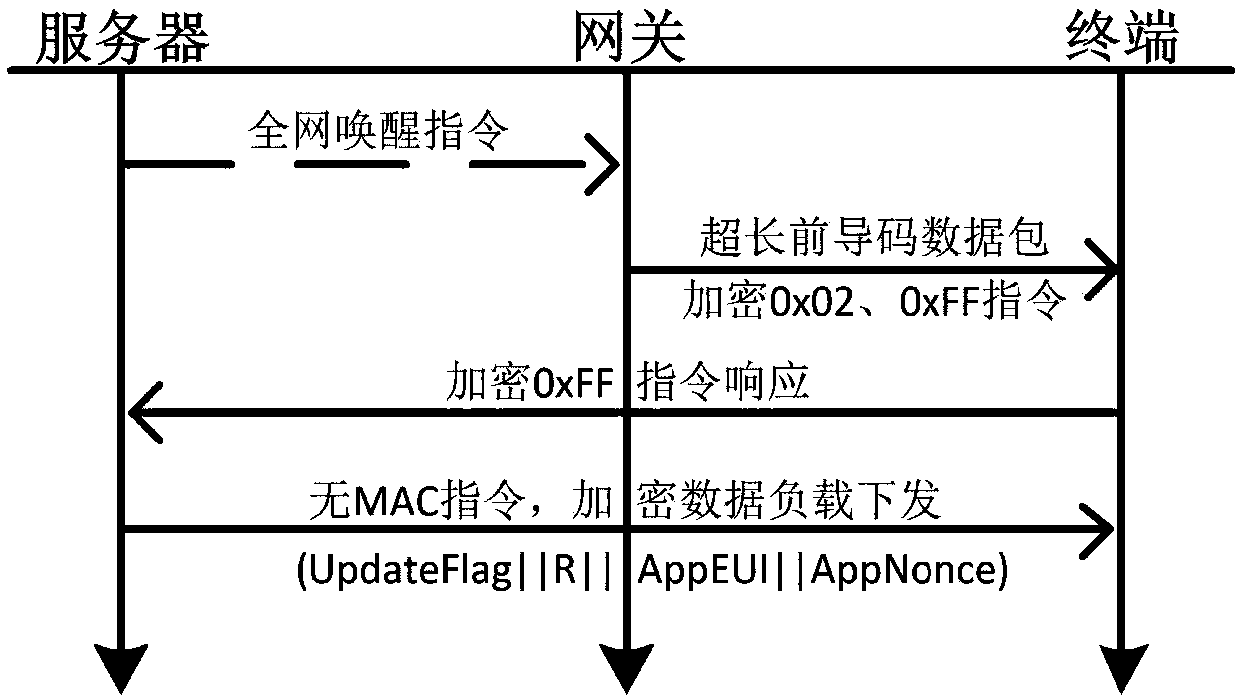
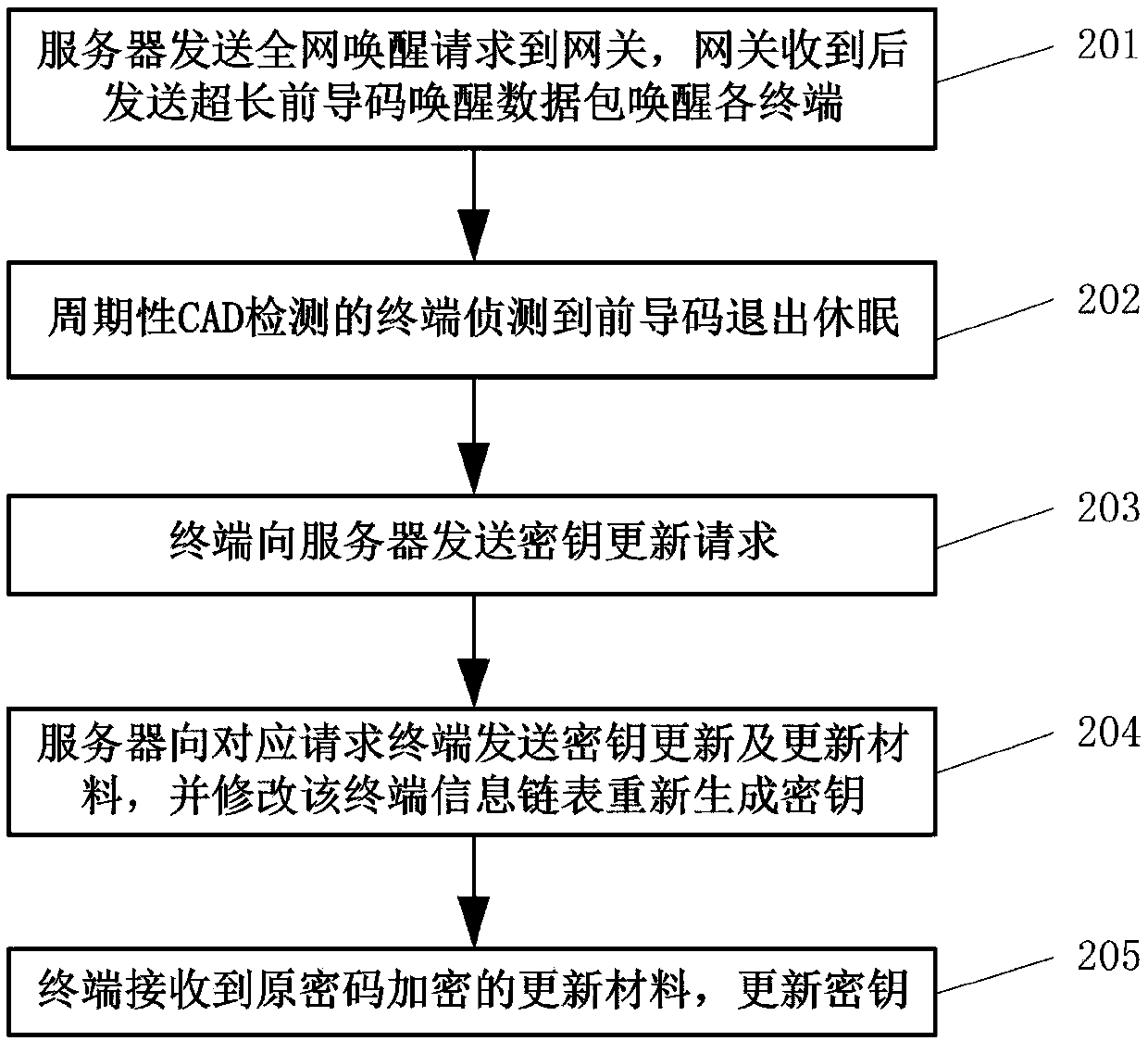
[0047]The embodiment of the present invention provides a matrix key management method for LoRaWAN, which solves the problem of using the matrix key management method in LoRa by combining the interaction data specified by LoRa during network access interaction and WOR technology. And it can efficiently update the key periodically. In an embodiment, the default network selects a 128-bit session key and stores it in an array of unsigned characters.
[0048] There are two message types in the LoRa protocol, one is the network message type, and the other is the data message type. The main message type related to the present invention is the network access message, and the network access message is divided into two types: the network access application message is shown in Table 1, and the network access reply message is shown in Table 2.
[004...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com