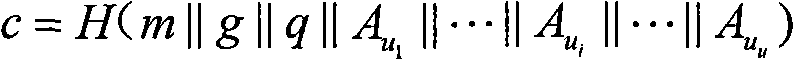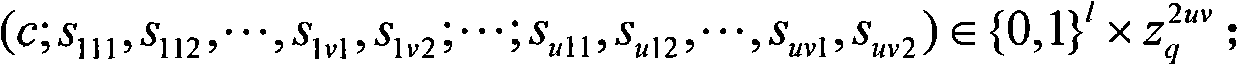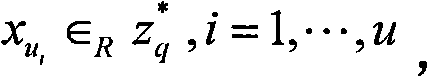Method for protecting security of digital signature documents of multiple verifiers strongly designated by multiple signers.
A technology of digital signature and security protection, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] Three designers A, B, and C have completed the review of an electronic drawing and need to sign the document together. The designated supervisor D and supervisor E can verify the digital signature.
[0066] Step 1. Generate system parameters: Let the public parameters established by the system be the cyclic group G whose order is a prime number q g,q , and the secure Hash function H=SHA-1.
[0067] Step 2. User key establishment:
[0068] The private keys of users A, B, C, D, and E are x A , x B , x C , x D , x E , these private keys are kept secretly by each user, correspondingly, their public keys are y A ,y B ,y C ,y D ,y E .
[0069] Three designers A, B, and C want to calculate the digital signatures of two strongly designated verifiers D and E for the message m, so u=3, v=2.
[0070] Step 3. Signing process:
[0071] Signer A randomly chooses r AD 1 ,...
Embodiment 2
[0088] There are four staff members A, B, C, and D who have completed the work report and need to sign the report together, and designate supervisor E, supervisor F and supervisor G to verify the digital signature.
[0089] Step 1. Generate system parameters: Let the public parameters established by the system be the cyclic group G whose order is a prime number q g,q , and the secure Hash function H=MD5.
[0090] Step 2. User key establishment:
[0091] The private keys of users A, B, C, D, E, F, and G are x A , x B , x C , x D , x E , x F , x G , these private keys are kept secretly by each user, correspondingly, their public keys are y A ,y B ,y C ,y D ,y E ,y F ,y G .
[0092] Workers A, B, C, and D want to jointly digitally sign message m and designate three verifiers E, F, and G to verify, so u=4, v=3. Let A be the person in charge of the signers, that is, the signature collector, and E be the person in charge of the verifiers, tha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com