Ad Hoc network key node identification method fused with deletion method
A key node and identification method technology, applied in the field of network security, can solve problems such as many key nodes, high algorithm time complexity, and difficult to distinguish node criticality, and achieve good adaptability, accurate identification results, and low time complexity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
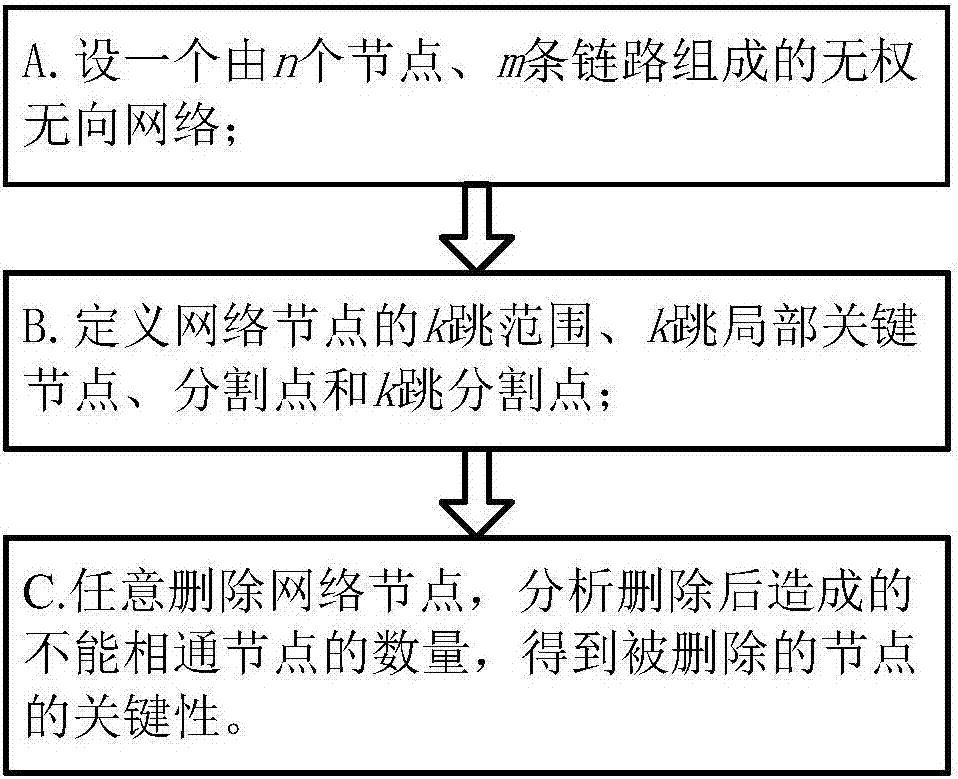
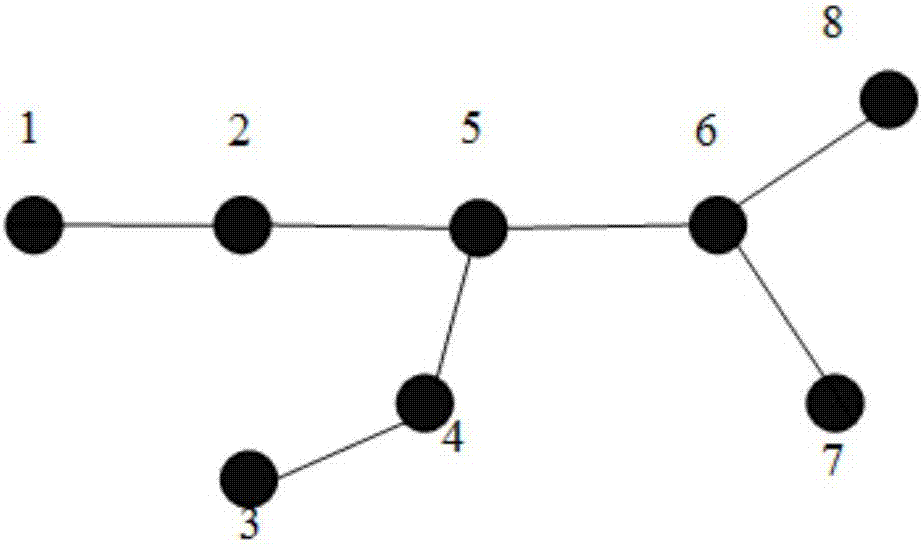
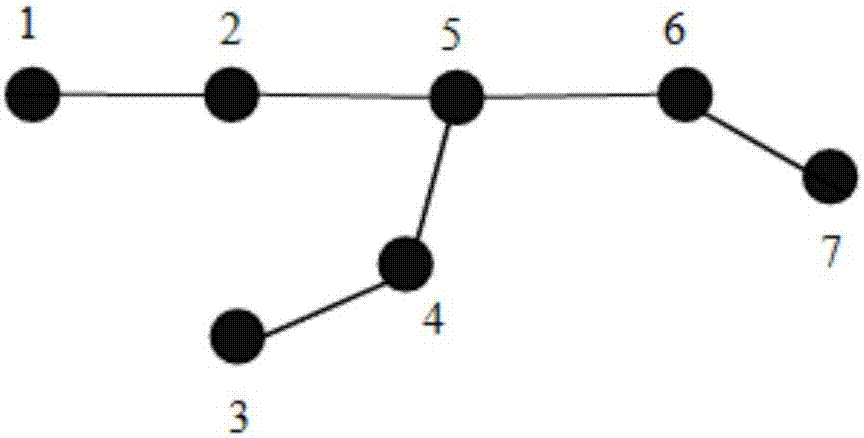
[0041] Example 1: see Figure 1 to Figure 5 , a kind of Ad Hoc network key node identification method of fusion deletion method, comprises the following steps:
[0042] A. Let the graph G=(V,L) be an unweighted and undirected network composed of n nodes and m links, where V={v 1 ,v 2 ,...,v n} is the set of all nodes in the network, L={l 1 , l 2 ,...,l m} is the set of links between all nodes;
[0043] B. Define the k-hop range of network nodes, k-hop local key nodes, split points and k-hop split points;
[0044]The k-hop range of a node refers to the range of all nodes that can be reached by the node in its shortest path less than or equal to k hops, and its topology includes all nodes within the k-hop range of the node and all links between these nodes road;
[0045] The k-hop local key node refers to the key node within the k-hop range, and when the number of nodes contained in the k-hop range is equal to n, this type of key node is called a global key node; if the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com