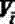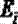Grid structure vulnerability node identification method
A technology of power grid structure and identification method, applied in the direction of instrument, data processing application, calculation, etc., can solve the problems of poor identification performance of vulnerable nodes, insufficient consideration of calculation and identification, and no dynamic consideration of node vulnerability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
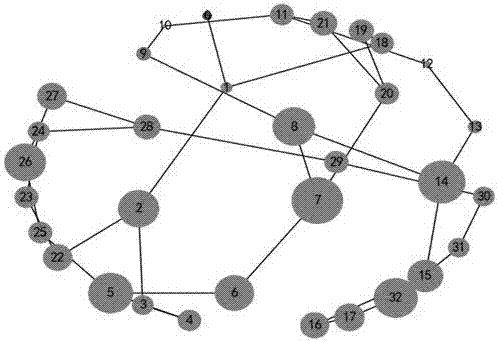
[0025] A method for identifying vulnerable nodes of a power grid structure, comprising the following steps:
[0026] 1) Read in the grid topology node connection relationship data (if there is a connection between two nodes, there will be a record), and configure the number k of nodes to be attacked or destroyed;
[0027] 2) Based on the network topology, calculate the shortest path between two nodes , the shortest path is the least number of edges from node i to node j. The average path length L of the network is defined as the average value of the shortest distance between any two nodes. The calculation formula is as follows:
[0028] (1)
[0029] in, is the shortest path between two nodes, and N is the number of nodes;
[0030] 3) Based on the shortest path between two nodes , according to formula (2) to calculate the network efficiency E,
[0031] (2);
[0032] 4) On the basis of the original input node pair data, delete the relevant paths connected to the n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com