Attack model library establishment method in quantum cryptographic protocol
An attack model and quantum cryptography technology, applied in key distribution, can solve problems such as information security threats, and achieve the effect of ensuring communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
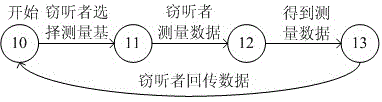
[0033] Such as figure 1 As shown, the method for establishing the attack model library in the quantum cryptography protocol includes the interception and retransmission attack model, the random replacement attack model, the general attack model, the Trojan horse attack model and the invisible photon attack model;
[0034] The interception and retransmission attack model is as follows: the sender sends the sequence A i Transmitted into the channel, the eavesdropper intercepts all of them and randomly selects the measurement base, measures each photon and records the result E i ; When all photons are measured, the eavesdropper gets a new sequence Ei' and sends it to the receiver, and the receiver gets the result B i . Such as figure 1 As ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com