Message identification method and electronic device
An electronic device and message authentication technology, which is applied in the fields of information security and cryptography, can solve the problems of decreasing the accuracy of message authentication and affecting the security of encryption schemes, and achieve the effects of reducing computational complexity, improving efficiency, and ensuring accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
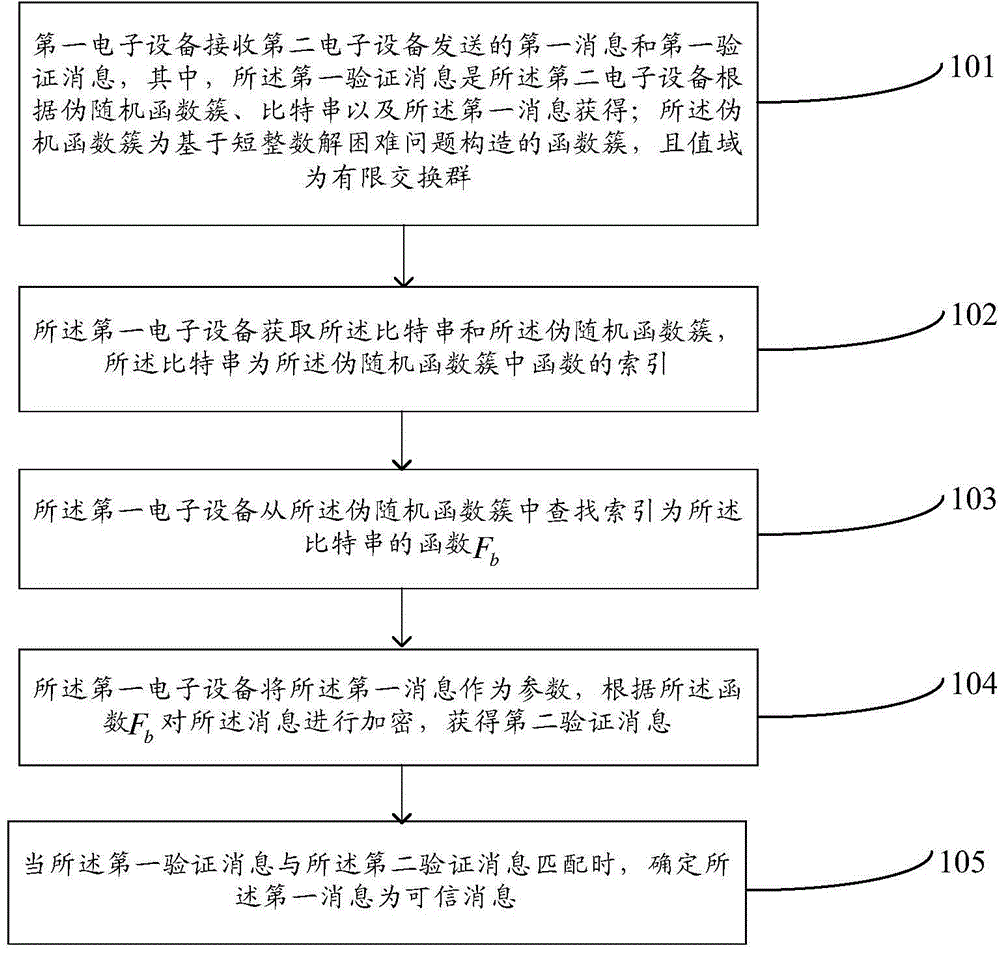
[0060] The embodiment of the present invention provides a pseudo-random function construction method, such as figure 1 As shown, the method includes the following steps:
[0061] 101. The first electronic device receives the first message and the first verification message sent by the second electronic device, wherein the first verification message is the second electronic device according to the pseudo-random function cluster, the bit string and the first obtained from the message; the pseudo-machine function cluster is a function cluster constructed based on solving difficult problems with short integers, and the value domain is a finite commutative group.
[0062] Wherein, the second electronic device may obtain the pseudo-random function cluster from the first electronic device, obtain it from a preset server, or construct it by itself.
[0063] During the communication process, any attacking adversary may tamper with the message sent by the sender, so that the receiver c...
Embodiment 2
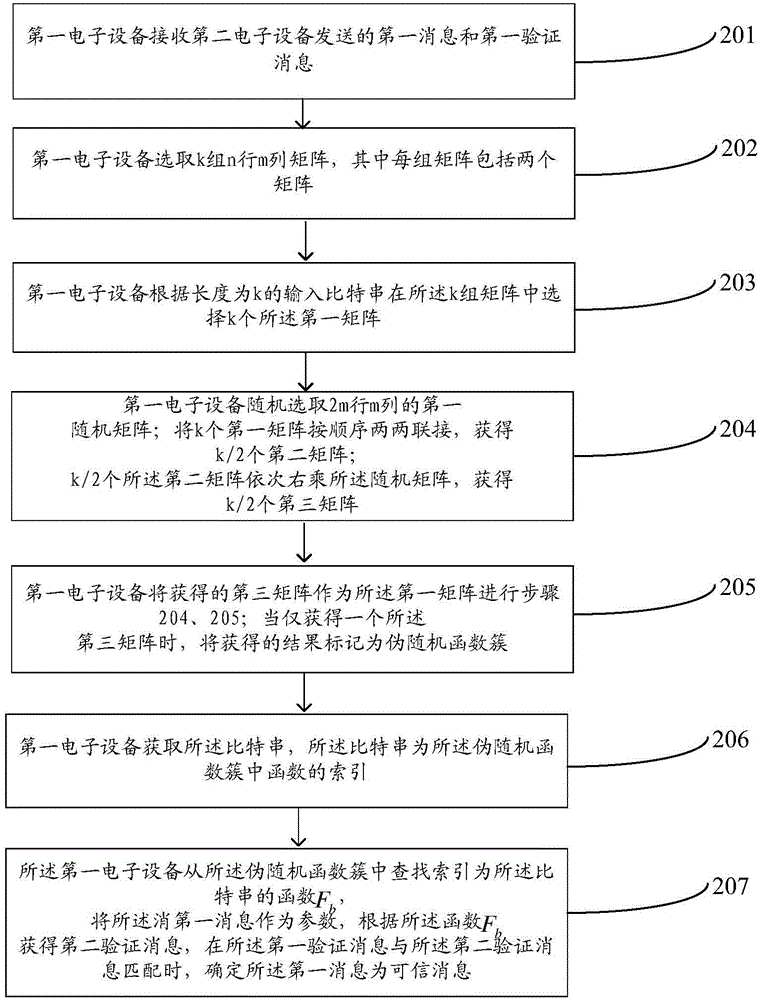
[0125] The embodiment of the present invention provides a method for message identification, which constructs a pseudo-random function based on solving difficult problems with short integers, such as figure 2 As shown, the method includes the following steps:
[0126] 201. The first electronic device receives a first message and a first verification message sent by a second electronic device.
[0127] Wherein, the first verification message is obtained by the second electronic device according to a pseudo-random function cluster, a bit string, and the first message; the pseudo-machine function cluster is a function cluster constructed based on short integers for solving difficult problems, and The range of values is a finite commutative group.
[0128] During the communication process, any attacking adversary may tamper with the message sent by the sender, so that the receiver cannot receive the correct message. In addition, either the sender or the receiver can obtain an...
Embodiment 3
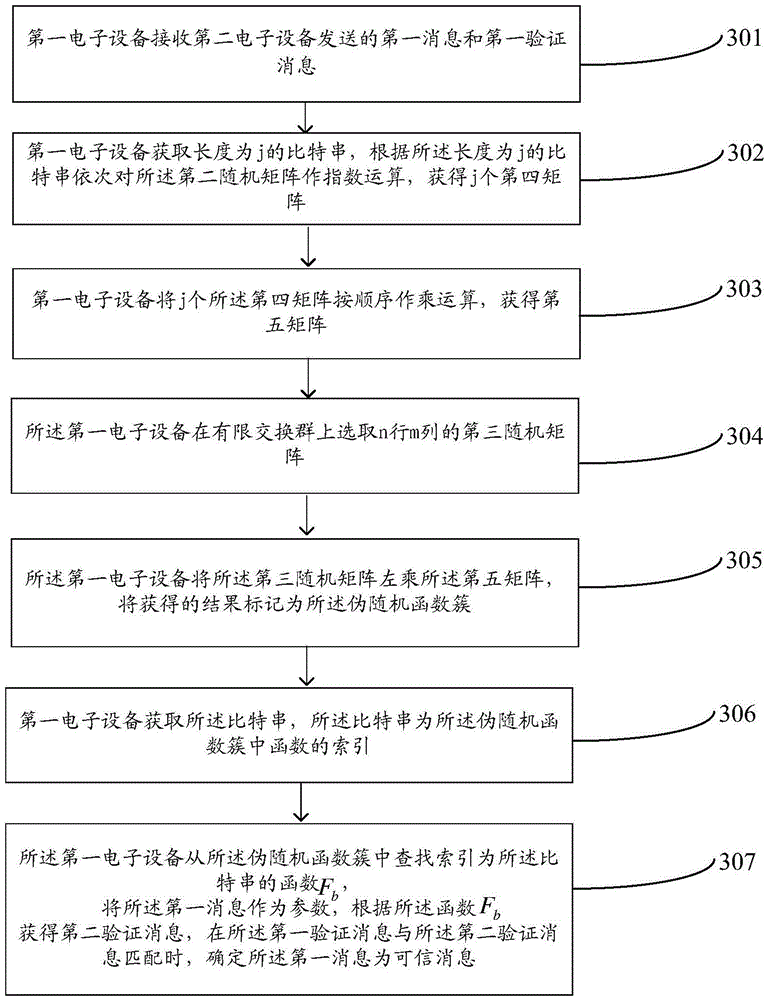
[0156] The embodiment of the present invention provides a method for constructing a pseudo-random function, which constructs a pseudo-random function based on solving difficult problems with short integers, such as image 3 As shown, the method includes the following steps:
[0157] 301. The first electronic device receives a first message and a first verification message sent by a second electronic device.
[0158] Wherein, the first verification message is obtained by the second electronic device according to a pseudo-random function cluster, a bit string, and the first message; the pseudo-machine function cluster is a function cluster constructed based on short integers for solving difficult problems, and The range of values is a finite commutative group.
[0159] Wherein, the elements in the first random matrix all obey the χ (chi-square distribution) distribution, and the second random matrix is a matrix with m rows and m columns.
[0160] In the pseudo-random funct...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com