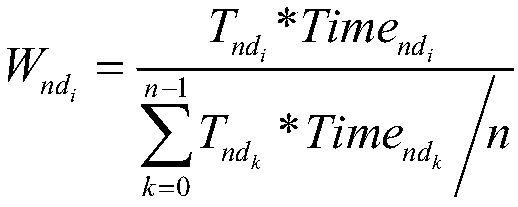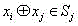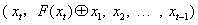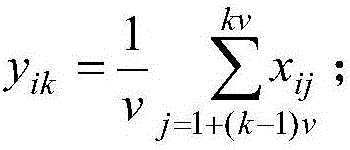Patents
Literature
74 results about "Randomization function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a randomization function or randomizing function is an algorithm or procedure that implements a randomly chosen function between two specific sets, suitable for use in a randomized algorithm.
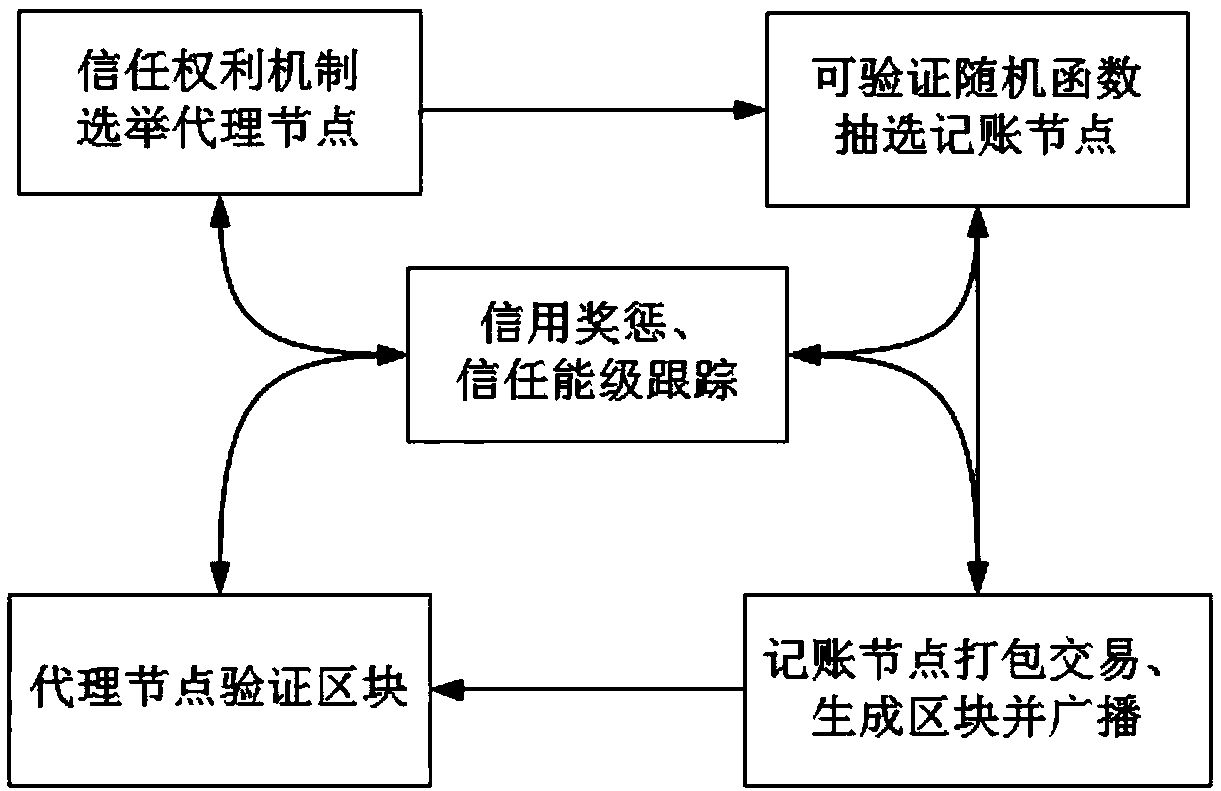
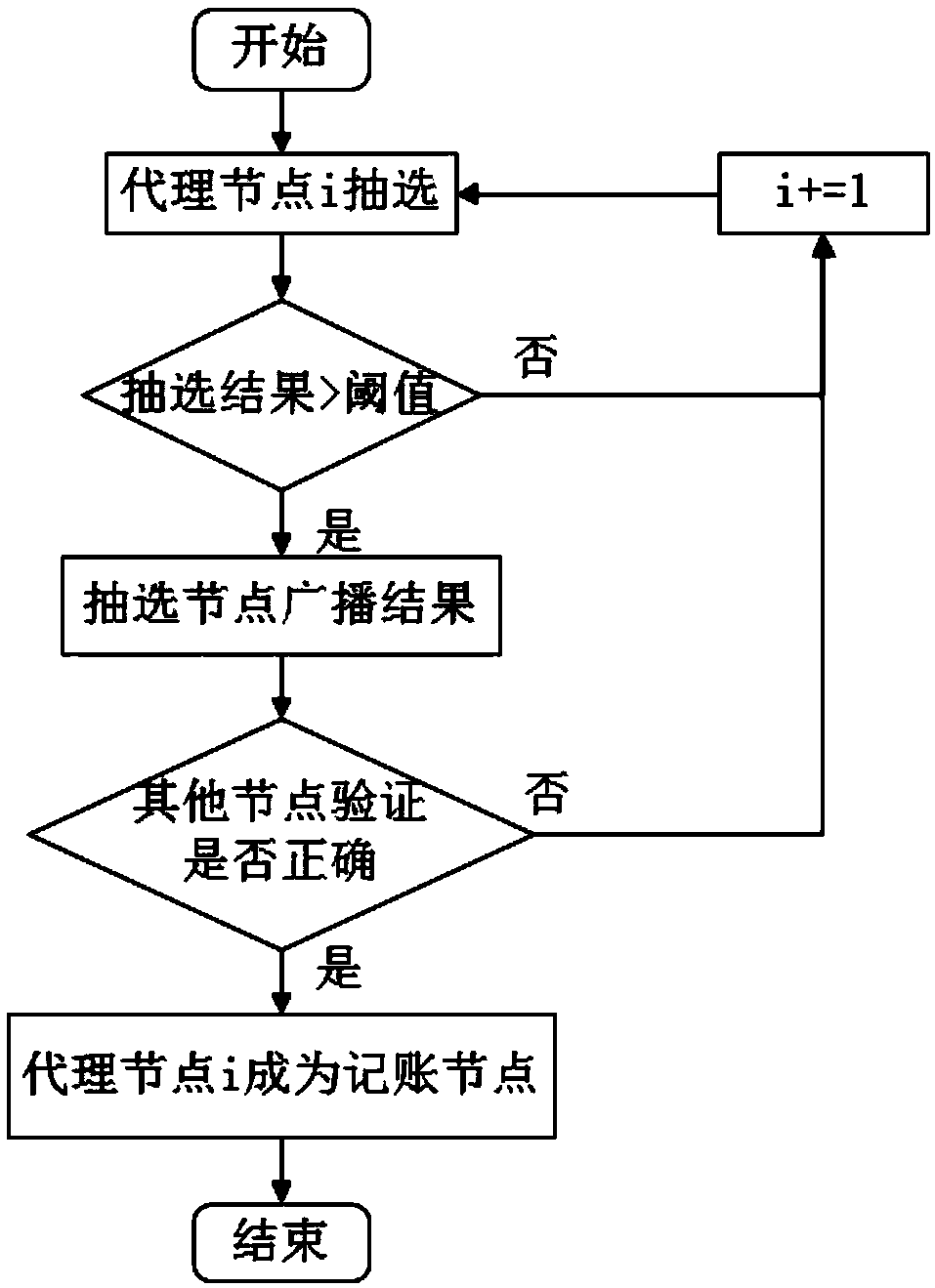
Block chain DPoS (Delegate Proof of Stake) consensus method based on trust mechanism
ActiveCN109639837ATimely exclusionIncrease engagementKey distribution for secure communicationPublic key for secure communicationChain networkProof-of-stake
The invention discloses a block chain DPoS (Delegate Proof of Stake) consensus method based on a trust mechanism. According to the method, concepts of trust degree and trust energy levels are importedfor nodes in a block chain system; the nodes with a trust energy level of error cannot participate in proxy node competitive election; proxy nodes are elected through utilization of a trust authoritymechanism; accounting nodes are extracted from the proxy nodes through adoption of a verifiable random function; and in a block chain network operation process, trust reward and penality are carriedout on node behaviors, and interruption and kickout policies employed for the accounting nodes of which trust energy level is reduced to the error energy level. According to the method, through tracking of the trust energy levels of the nodes and through trust reward and penality of the nodes, a probability that malicious nodes become the accounting nodes is reduced; participation active degree ofcommon nodes is improved; reliability of the whole consensus method is ensured; the trust degree is taken as a delegate proof of stake, so additional token money distribution is avoided.
Owner:SOUTHEAST UNIV
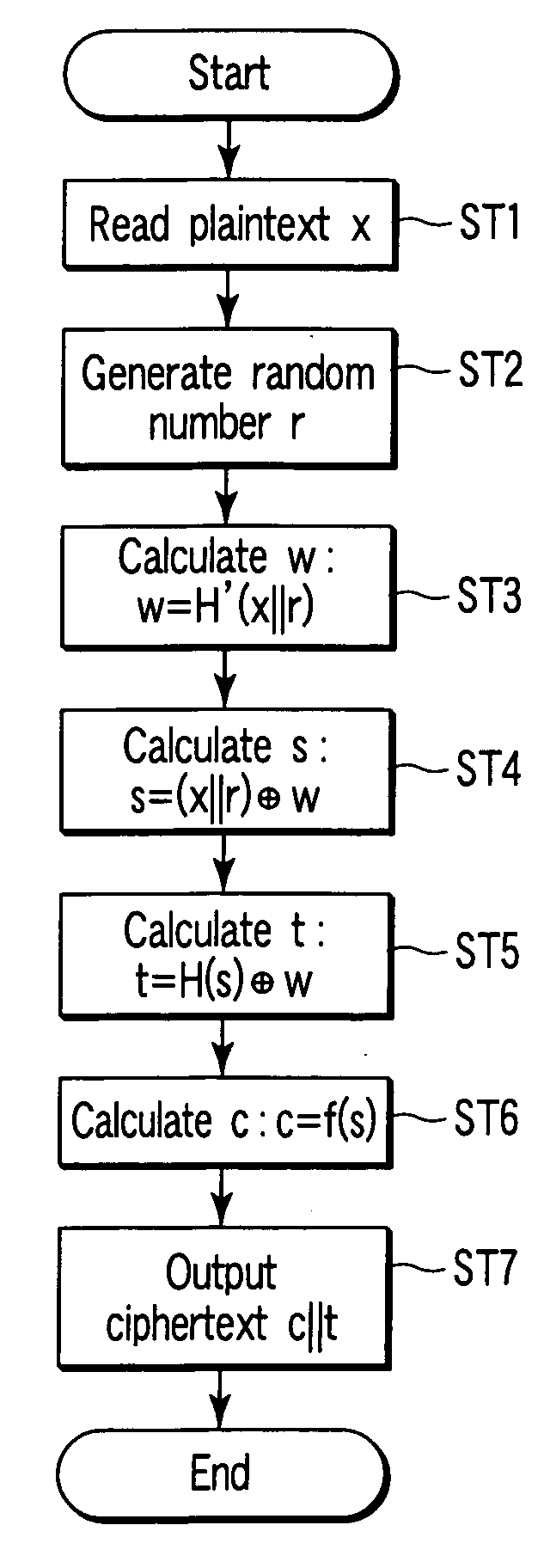
Encryption/signature method, apparatus, and program
InactiveUS20050157871A1Public key for secure communicationUser identity/authority verificationCiphertextTime of use
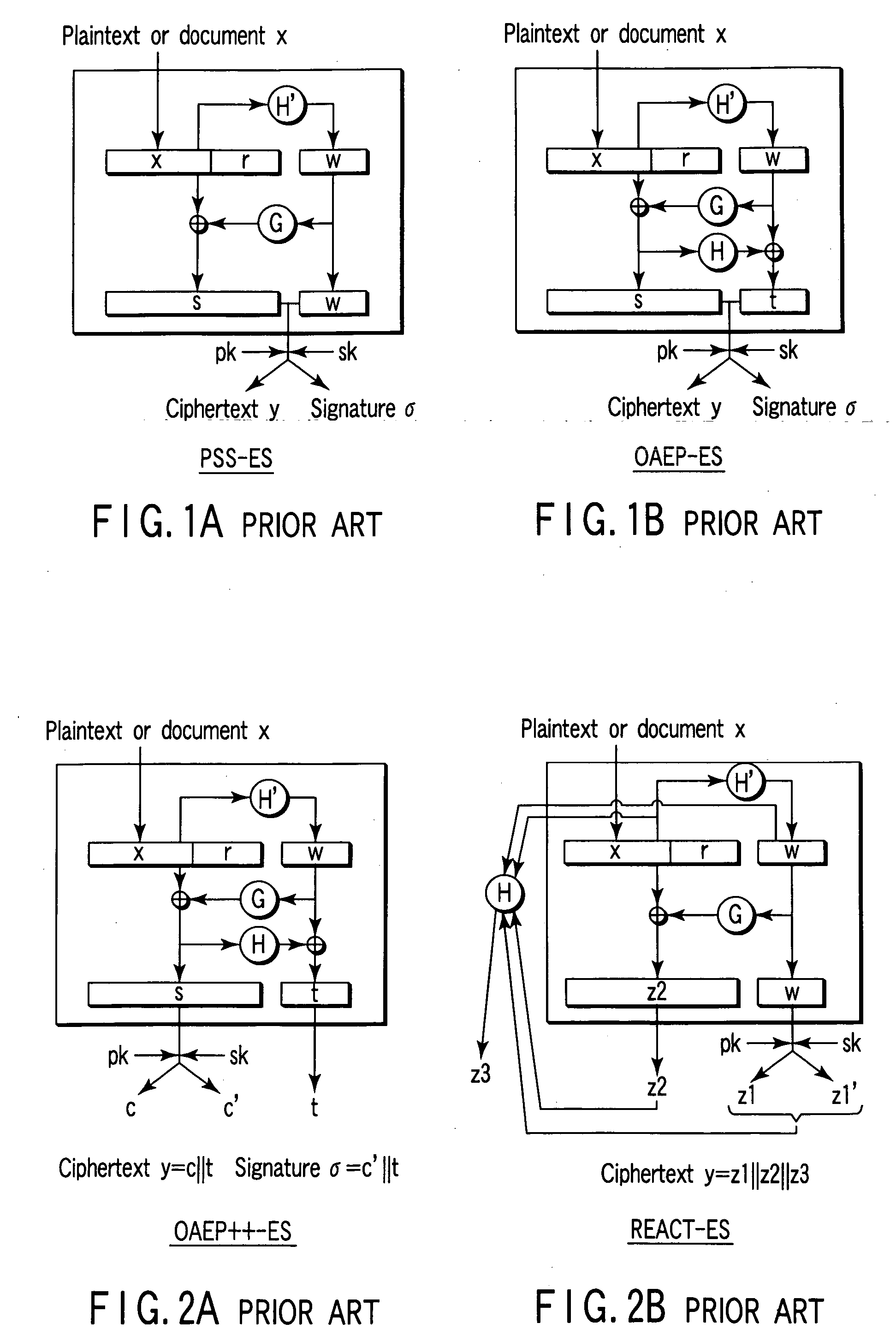
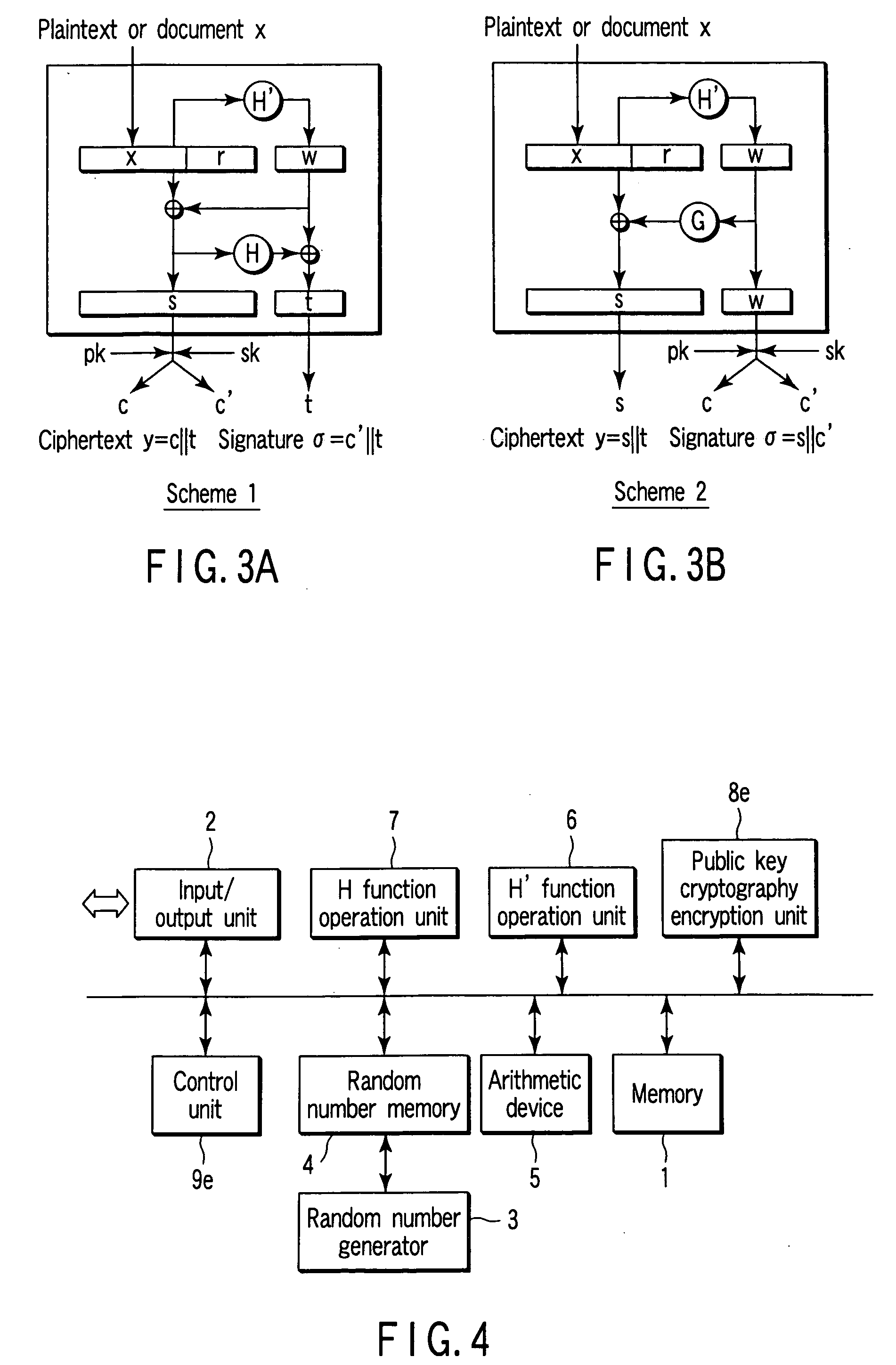
According to each embodiment of the present invention, random function operations less than three times and tight security can simultaneously be implemented. More specifically, a ciphertext y=c∥t or a signature σ=c′∥t is created as concatenated data of two data. The concatenated data is created by using a public key encryption scheme for only one (necessary part s) of the data. For this reason, tight security for the one-way characteristic of a trapdoor one-way function of the public key encryption scheme can be implemented. In addition, the output size of a first random function H′ is limited. Accordingly, a random function G for bit expansion in the conventional. OAEP++-ES scheme can be omitted. Hence, the number of times of use of random functions can be reduced to two.
Owner:KK TOSHIBA
Public key encryption system using error correcting codes
InactiveUS20120121084A1Improving information throughput efficiencyPublic key for secure communicationSecret communicationKey sizeCryptogram
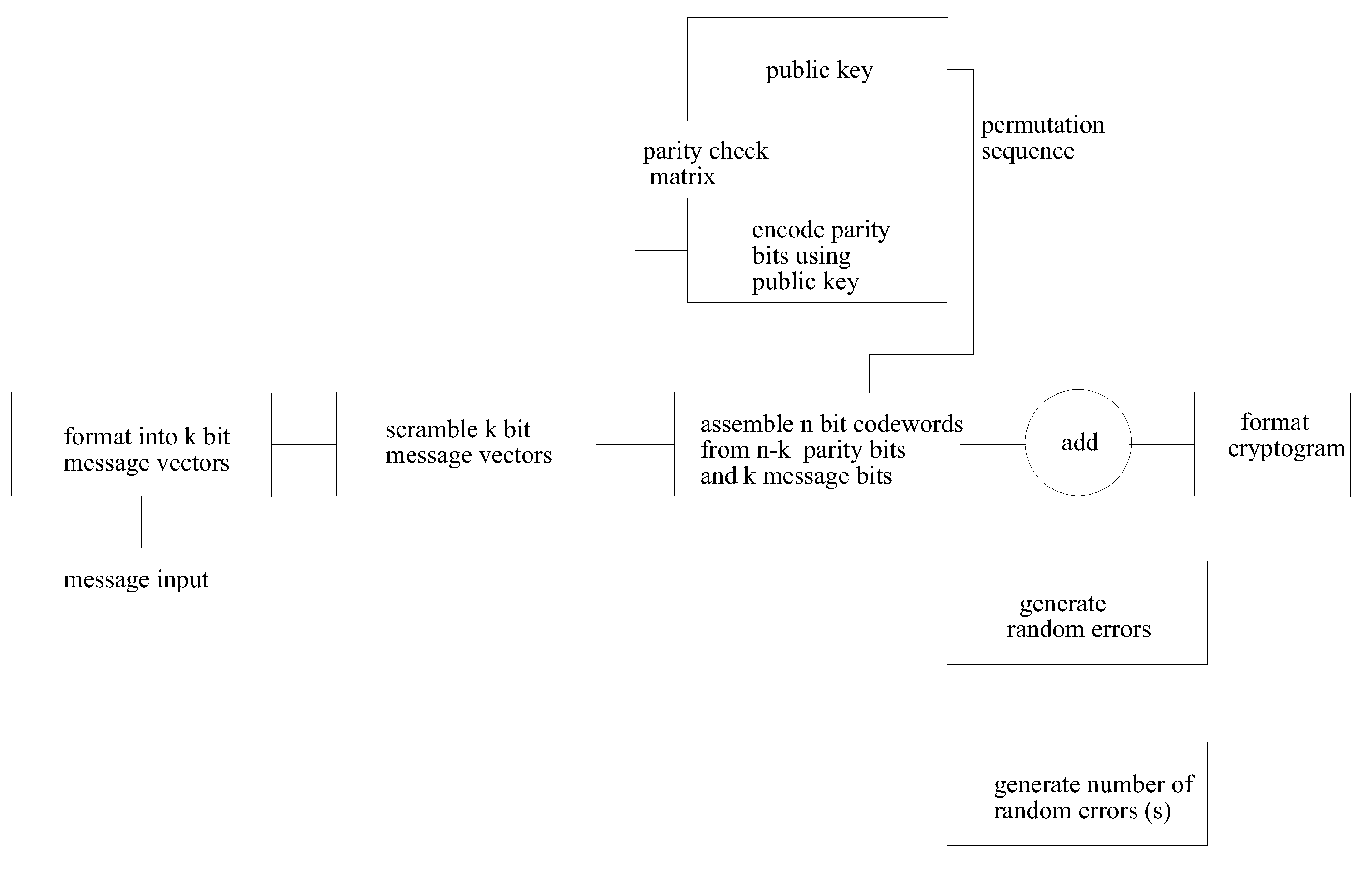
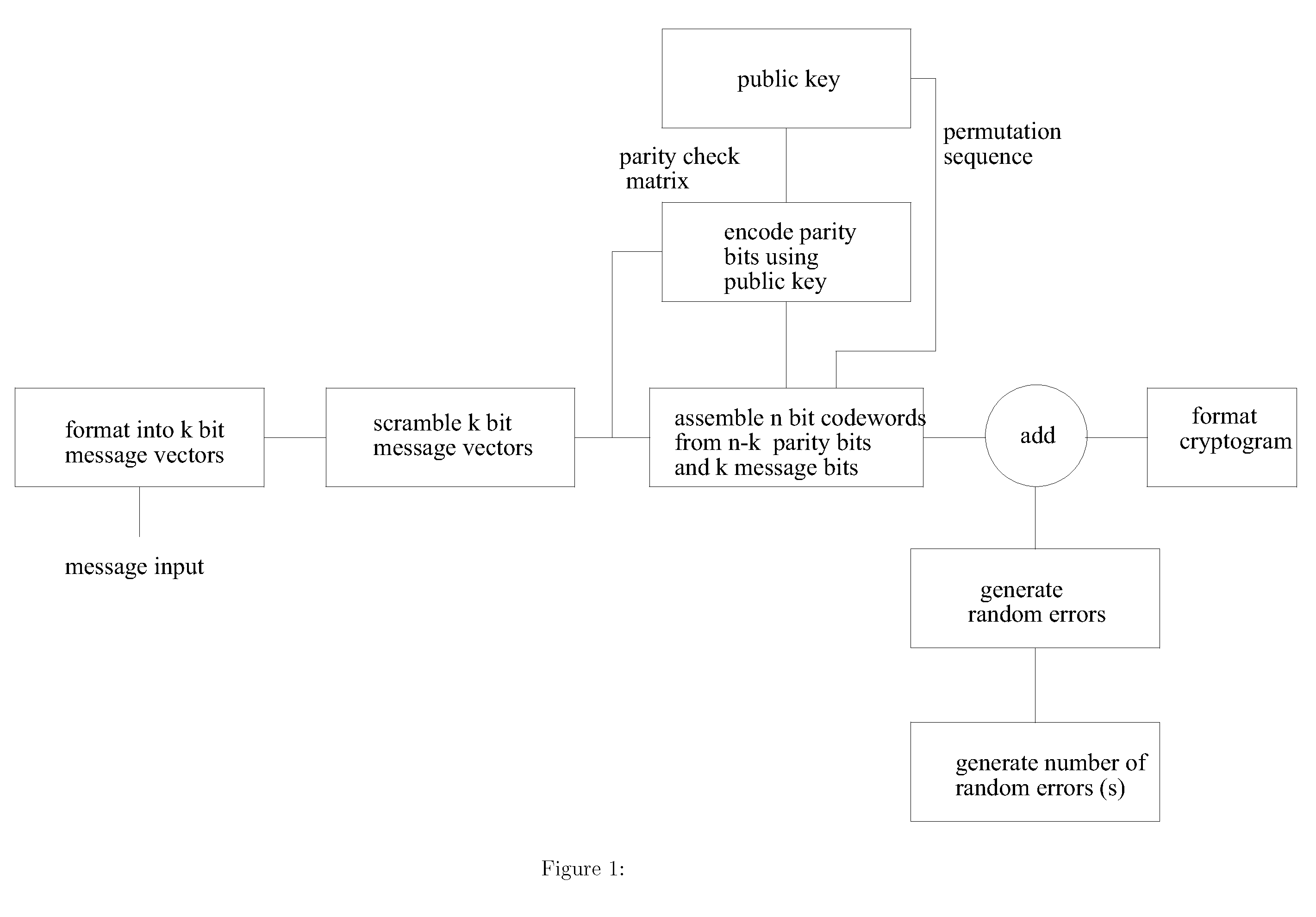
This invention provides improved security and improved throughput of the McEliece public key encryption system and reduces the public key size. Even though the public key is reduced, in some embodiments of the invention the ensemble of cryptograms produced is identical to the ensemble of cryptograms produced by the original system for a given Goppa code, and the same private key. It is possible using this invention that the encrypted message, the cryptogram is a truly random function, not a pseudo random function of the message so that even with the same message and the same public key, a different, unpredictable cryptogram is produced each time. Other embodiments of the invention use a shortened error correcting code allowing the length of the generated cryptogram to match exactly the available transmission or storage media such as is the case of RFID and packet based radio applications.
Owner:PQ SOLUTIONS LTD
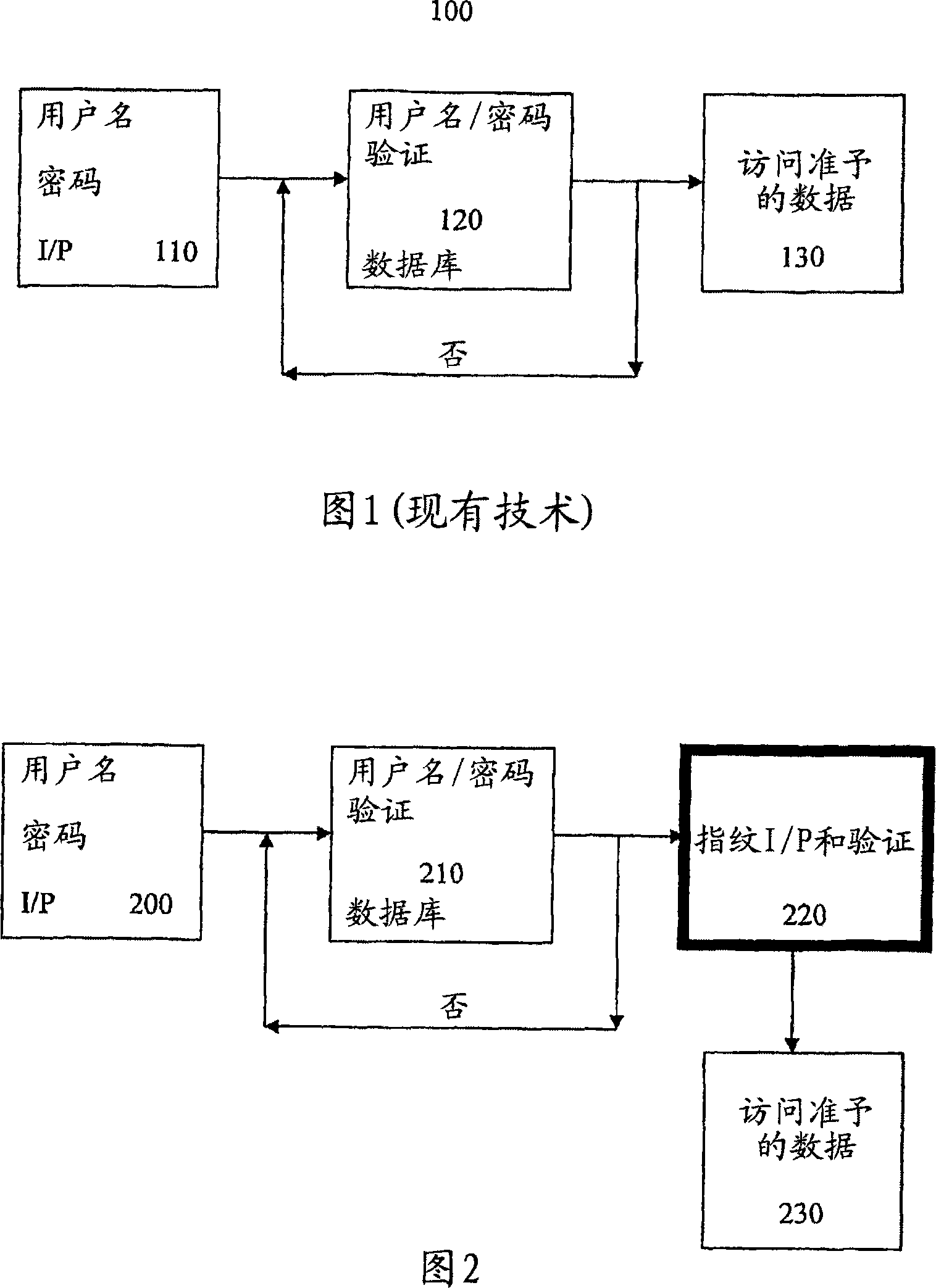
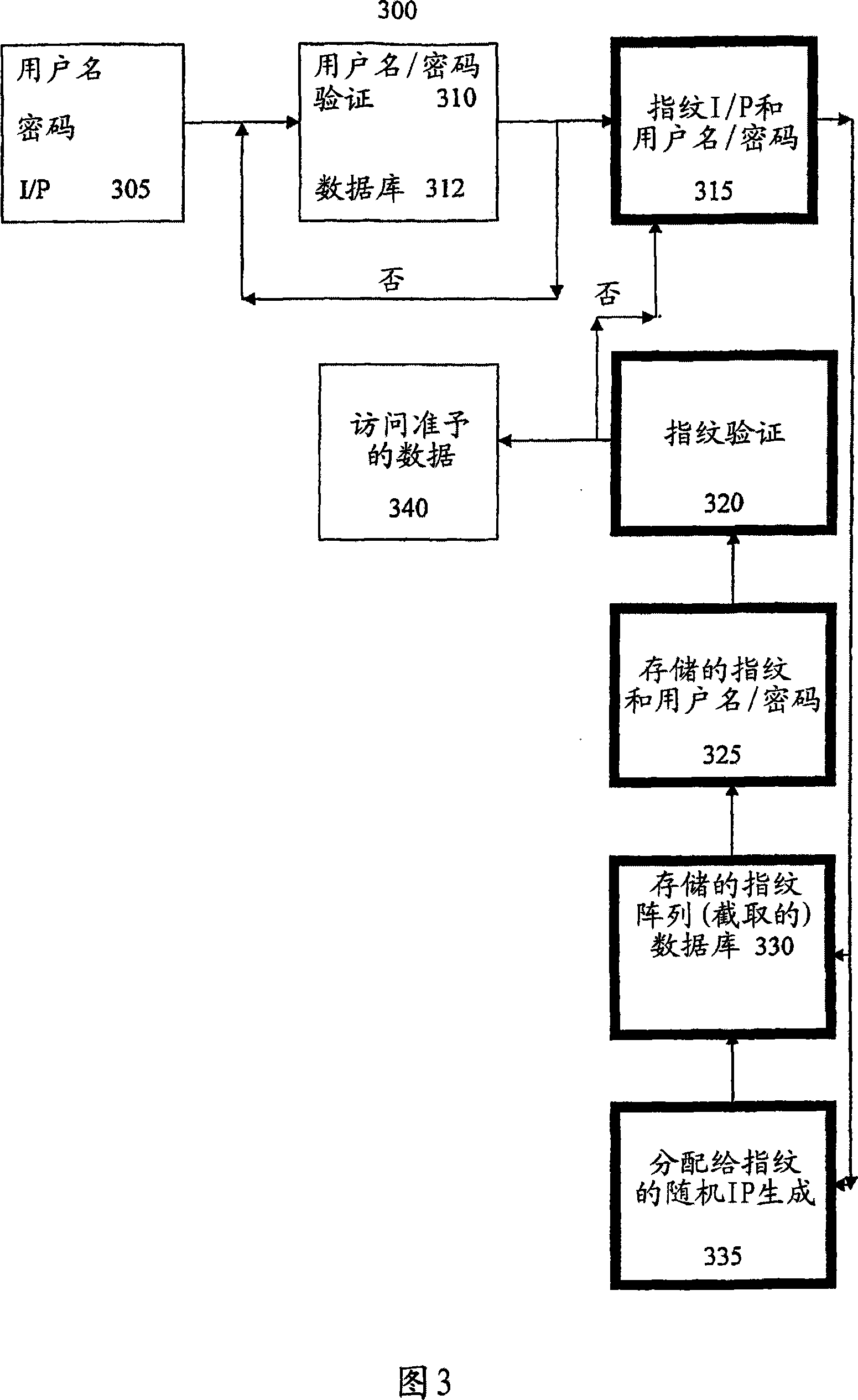
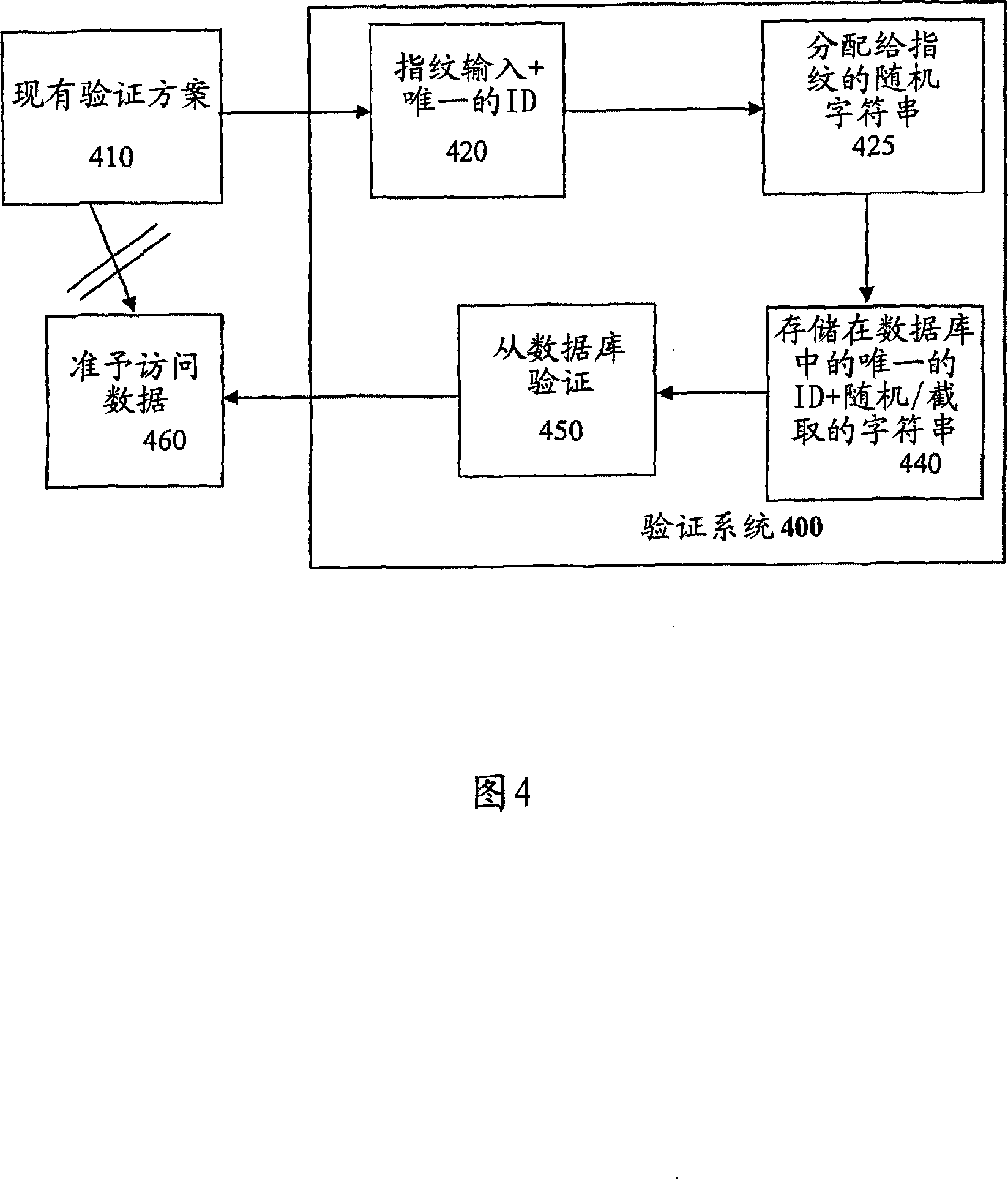
Method and system for string-based biometric authentication
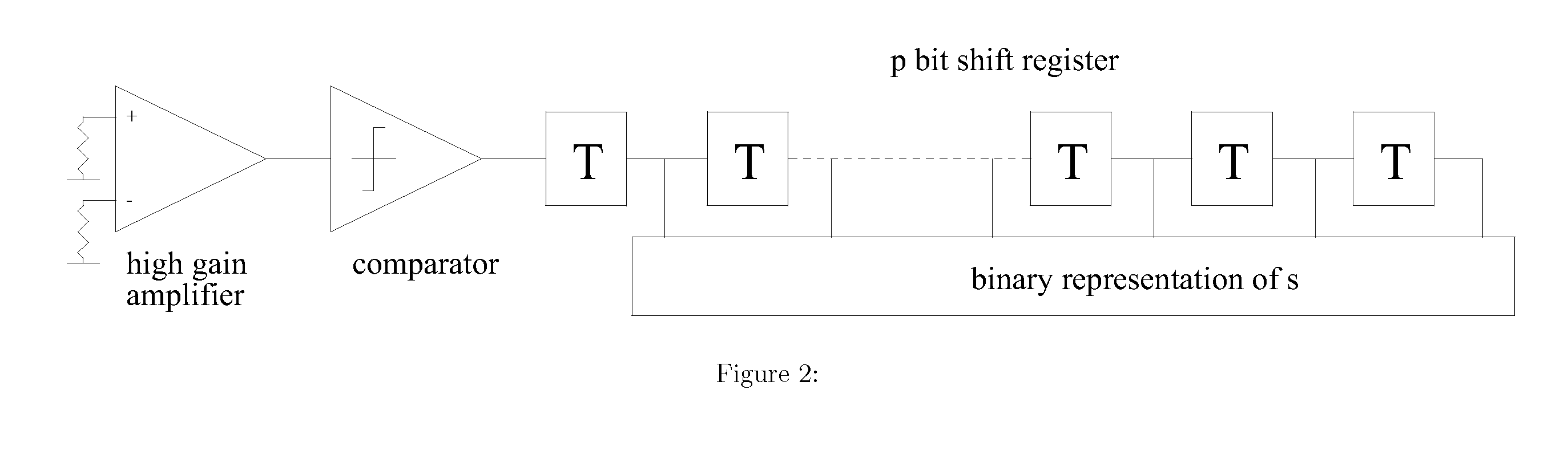
InactiveUS20070031009A1Programme controlElectric signal transmission systemsAuthorizationRandomization function
Techniques for string-based biometric authentication are described that includes a method for string-based biometric authentication provided that comprises the steps of receiving a username and password combination associated within a person, acquiring a biometric data from the person, generating a random string of biometric information based on the biometric data using a randomization function, truncating said random biometric string, and storing said truncated random biometric string along within the associated username and password combination of the person in a biometric database for future authorizations of the same person. To authenticate a user, the acquired biometric data is compared with a truncated biometric string in said biometric database searching for a match, and if a match is found, authorization of the person to access a resource is given.
Owner:MWALE JULIUS
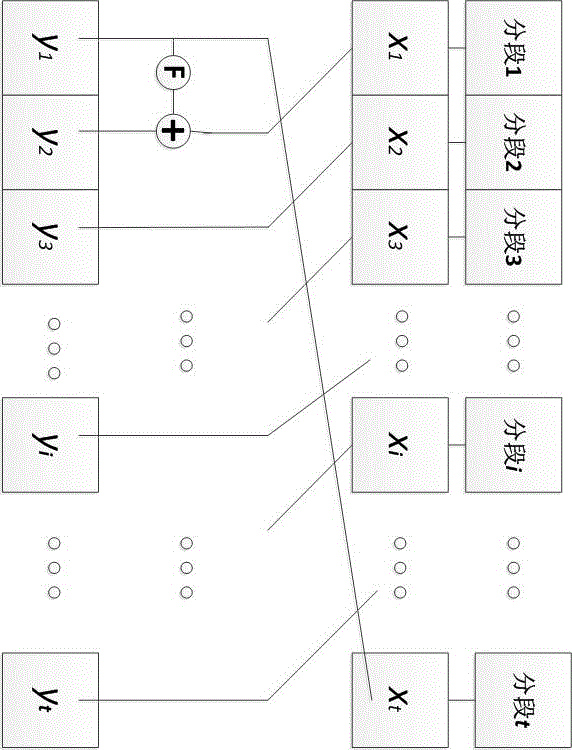
Format-reserved encryption algorithm based on multi-segmented Feistel network
InactiveCN105959098ADoes not affect compatibilityEncryption apparatus with shift registers/memoriesPlaintextComputer hardware
A format-preserving encryption algorithm based on a multi-segmented Feistel network, the method includes the following steps: S According to its own format, it is divided into t part: S 1 ,S 2 ,…,S t . where set S i is of size n i . Set the number of rounds for the Feistel network r and the key used by the round function k , where the number of rounds r for the number of divisions t associated even numbers; for a given plaintext m , format it as: m=x 1 || x 2 || … || x t ,in: x 1 ∈ S 1 ,x 2 ∈ S 2 ,…,x t ∈ S t ;Will x 1 ,x 2 ,…,x n as t Segmentation of the Feistel network t input, or input as ;Execute r rounds of round operations, and the final output ciphertext is c=y 1 || y 2 || … || y t ,in: y 1 ∈ S 1 ,y 2 ∈ S 2 ,…,y t ∈ S t , the advantages of the present invention are: by segmenting the sensitive data and defining the value domains of different segments, using self-defined pseudo-random functions, modulus addition and modulus subtraction operations, and using Feistel network to perform even-numbered rounds of round operations to achieve Encryption that preserves the format can support numerical data encryption schemes that retain any given format. After encryption, the data and database will not be affected, which provides the possibility for the encryption protection of numerical personal identification information in existing database application systems.
Owner:东港股份有限公司 +1
Method for constructing block encryption algorithm based on random function
ActiveCN102571330AImprove securityHeavy calculationKey distribution for secure communicationPlaintextPassword
The invention belongs to the field of information security and relates to construction of encryption algorithm. The password (encryption) algorithm is uncertain and random by using the random function to construct the block encryption method. The uncertainties are determined by partial data in the secret key and some information of plaintext. The encryption method has the advantage that the indeterminacy of the algorithm ensures that the password analysis becomes very difficult as a result of the lack of the information about the algorithm, so that a great amount of known (selected) plaintext ciphertext pair of the same algorithm and the same secret key cannot be acquired, and the condition for password analysis is destroyed to enhance the security. The existing abundant password analysis aims at determined algorithm, and the password analysis is difficult to perform when the algorithm is random. The uncertainty of the password system is increased through multiple ways. The encryption algorithm of the plaintext is uncertain, and the algorithms of different blocks are different, therefore, the secret key space can be increased so as to enhance the safety.
Owner:桂林碧琪信息科技有限公司
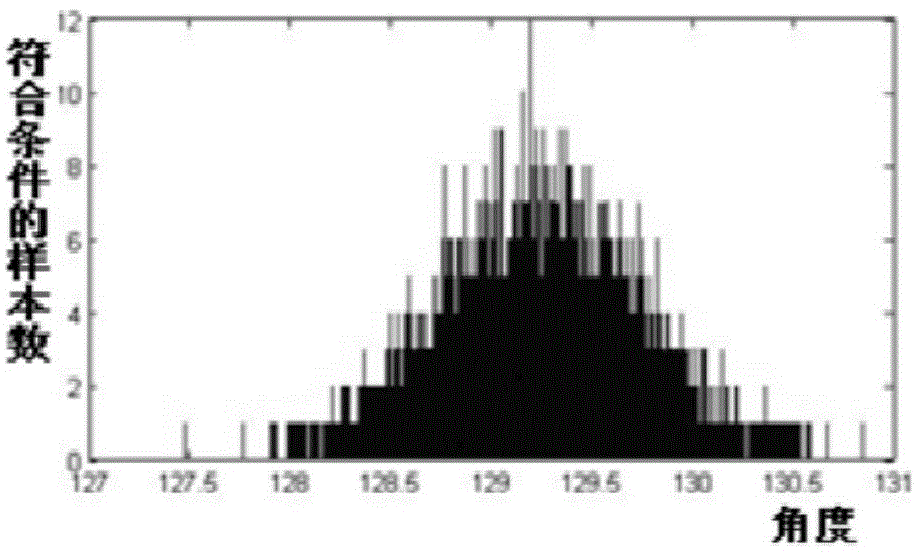
Partial discharging positioning method based on time delay error stochastic simulation and statistic analysis
ActiveCN103913680AImprove calculation accuracyTesting dielectric strengthTime delaysStatistical analysis
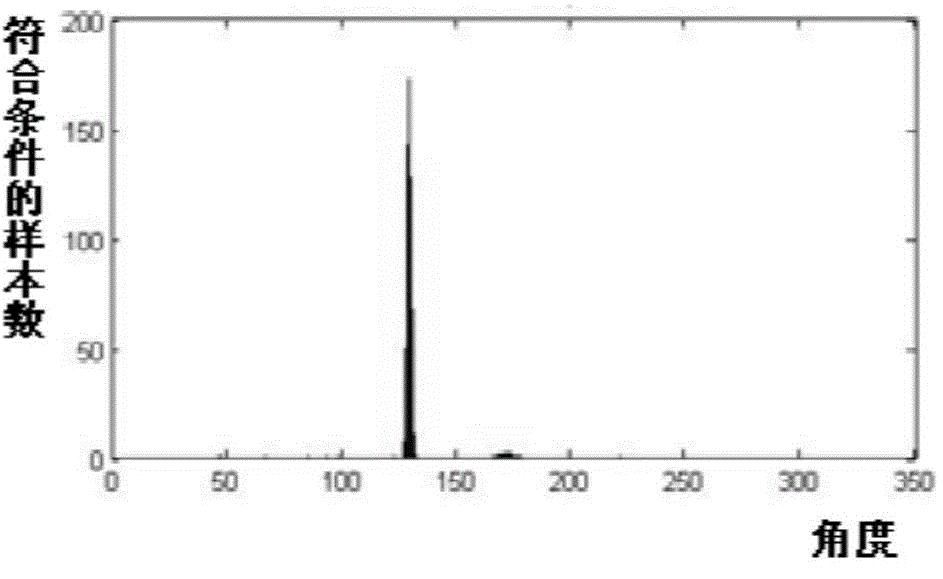
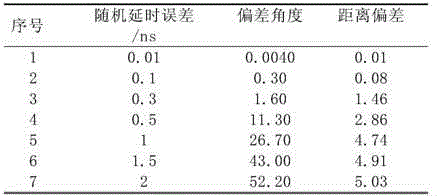
The invention provides a partial discharging positioning method based on time delay error stochastic simulation and statistic analysis. The partial discharging positioning method comprises the following steps that firstly, four time delays needed by positioning are obtained according to the generalized cross-correlation algorithm based on a set of waveforms received by a quaternary ultra-high frequency antenna array; secondly, the time delay error range is set with the time delays as base points, n sets of time delays are simulated in the time delay error range in a random mode, random functions are distributed in a normal mode, and the time delays worked out in the first step are adopted in the center; thirdly, the two-dimensional positioning information of a discharging source is calculated according to the n sets of time delays, and a direction angle distribution diagram is obtained; fourthly, the angle with the maximum angle distribution probability is set to be the positioning angle according to the statistical analysis method; fifthly, a search area is spread with the positioning angle as the center, grid searching is carried out, and the positioning angle and the radial distance of the discharging source are calculated. The partial discharging positioning method based on time delay error stochastic simulation and statistic analysis can improve the accuracy of partial discharging positioning.
Owner:SHANGHAI JIAO TONG UNIV
Method for distributing targets cooperatively attacked by unmanned aerial vehicle group
InactiveCN104950673ASolve the allocation problemMulti-target strikeAdaptive controlSimulationSingle vehicle
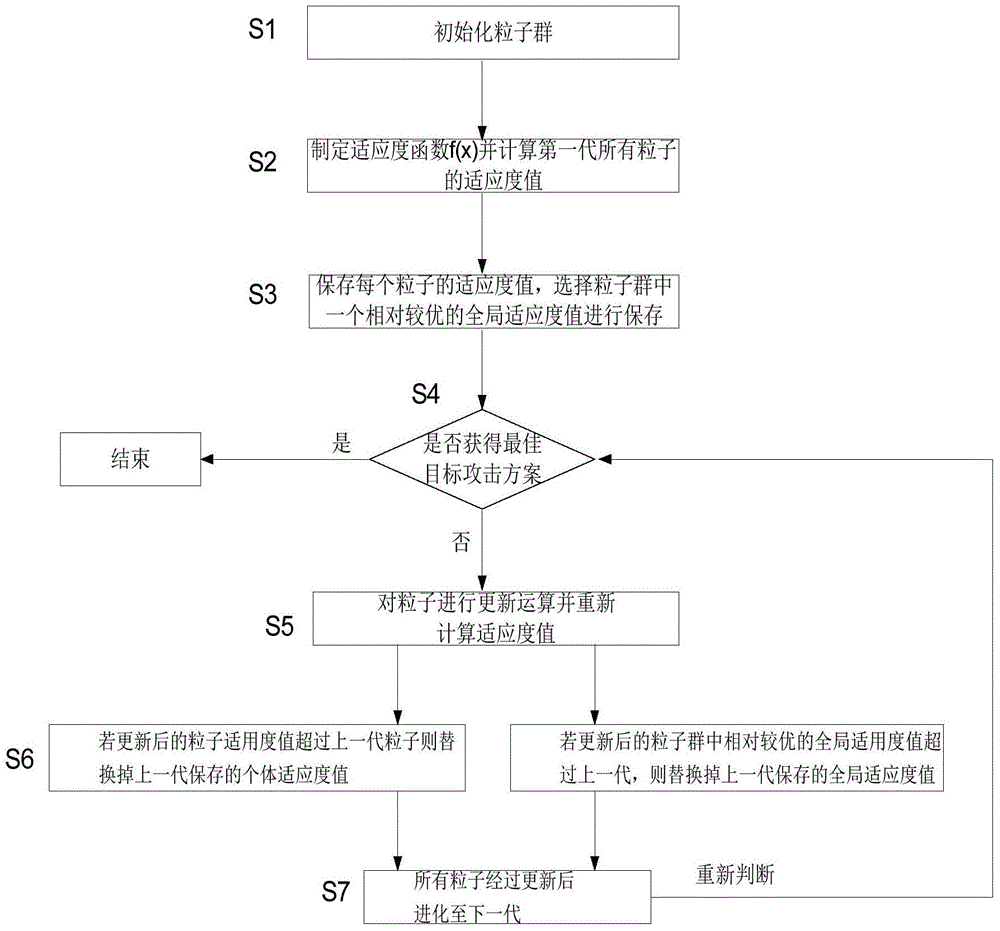
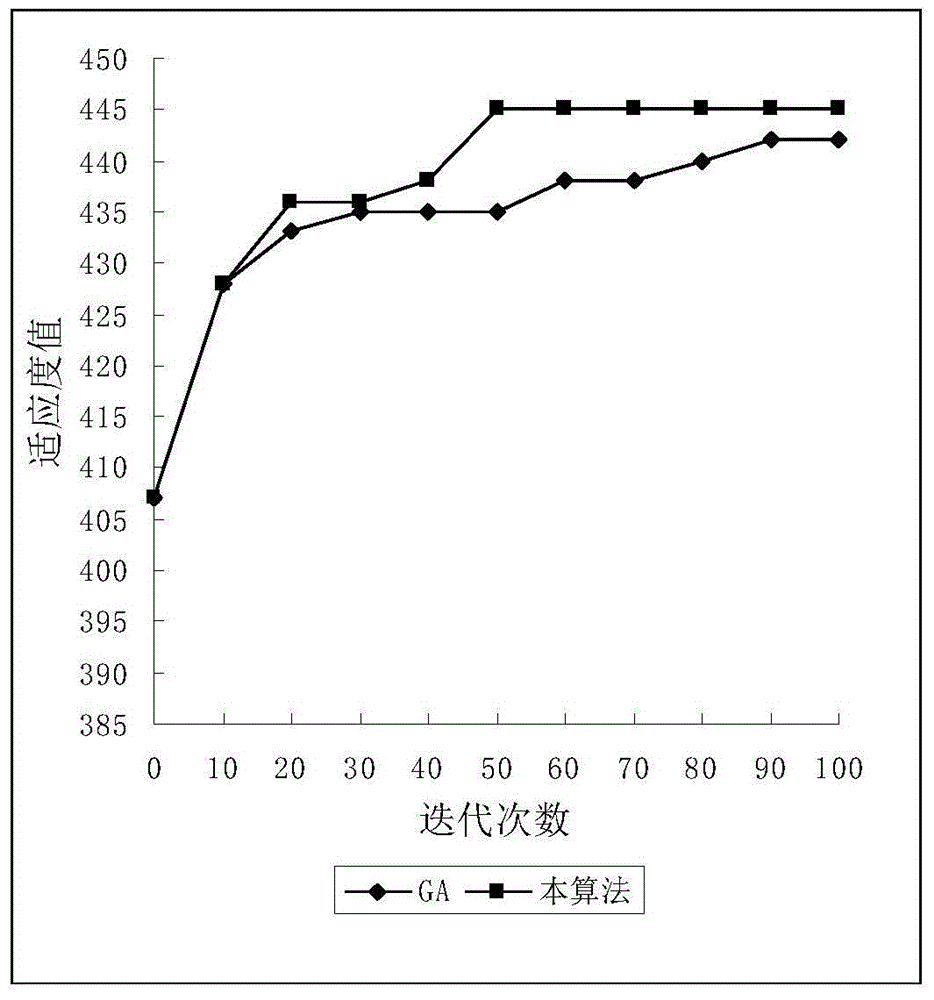
The invention relates to a method for distributing targets cooperatively attacked by an unmanned aerial vehicle group and belongs to the field of realtime embedding. The method includes: initializing a particle swarm, formulating a fitness function according to evaluation standards, storing fitness values of all particles, judging whether an optimal target distribution scheme is reached or not, and if not, using a random function, a cognitive function and a social function to update the particles, calculating fitness values of current particles, and updating a particle with individual optimal fitness and a particle with global optimal fitness; comparing particle individual fitness values after being updated and global fitness values after being updated with an initial individual optimal fitness value and a global optimal fitness value, evolving to a next generation after all particles are updated, and rejudging whether the optimal target distribution scheme is reached or not. A particle matrix between the unmanned aerial vehicle group and the targets is established, the problem of target distribution of the unmanned aerial vehicle group can be solved quickly and efficiently through constant self learning, single-vehicle to multiple-target attack can be realized, and the method is simple, convenient and quick.
Owner:KUNMING UNIV OF SCI & TECH
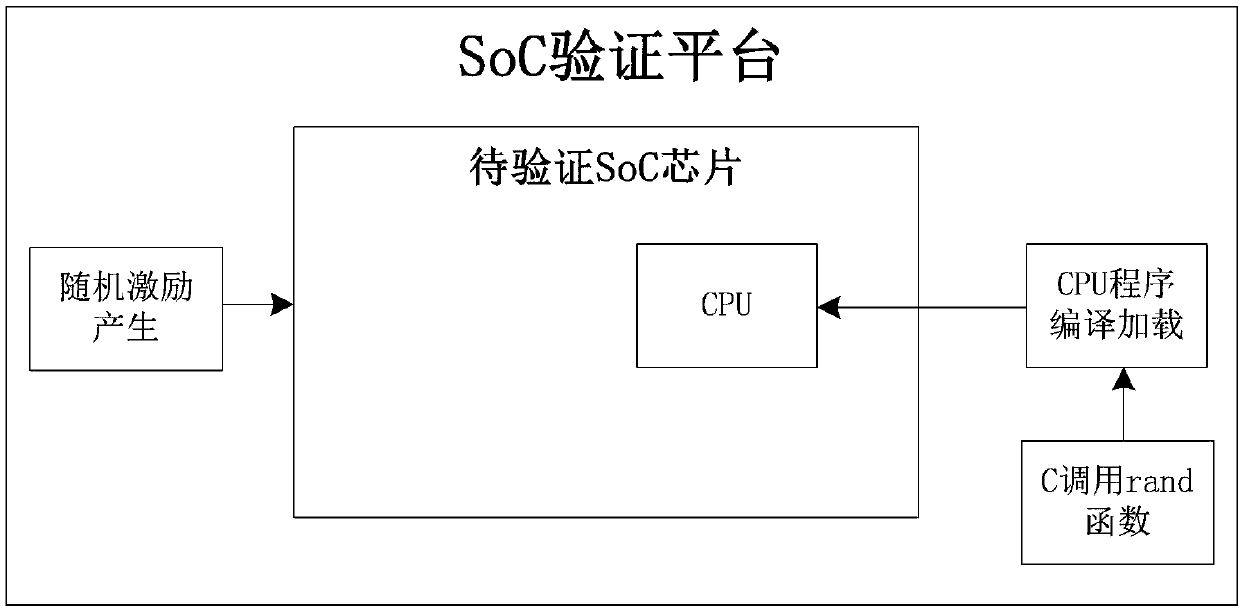
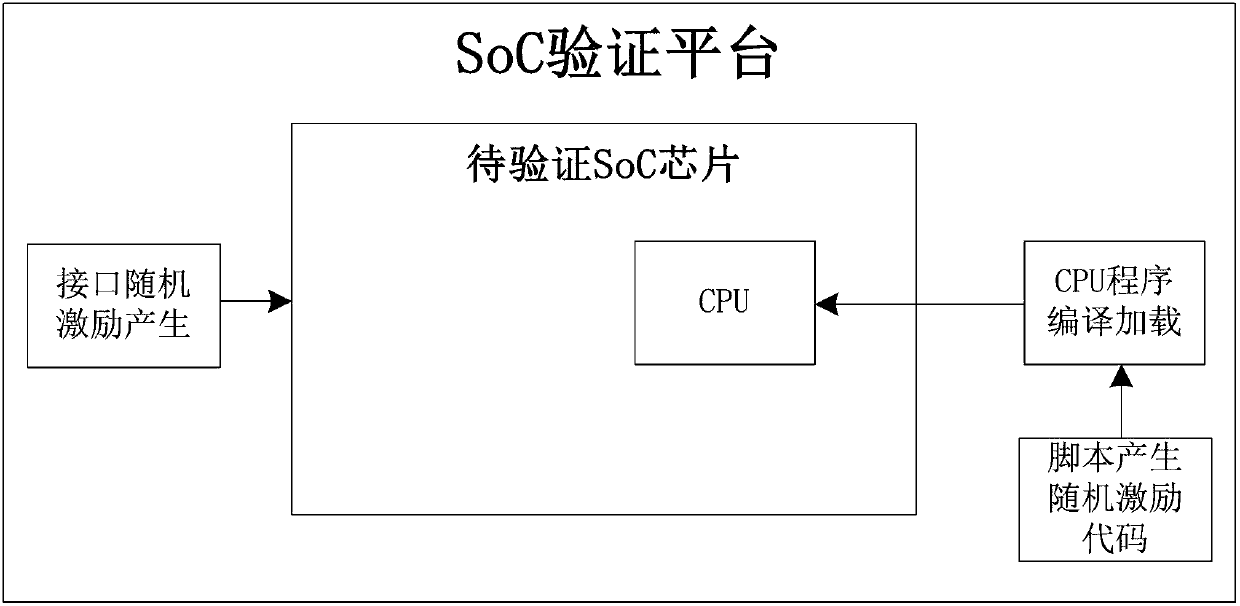
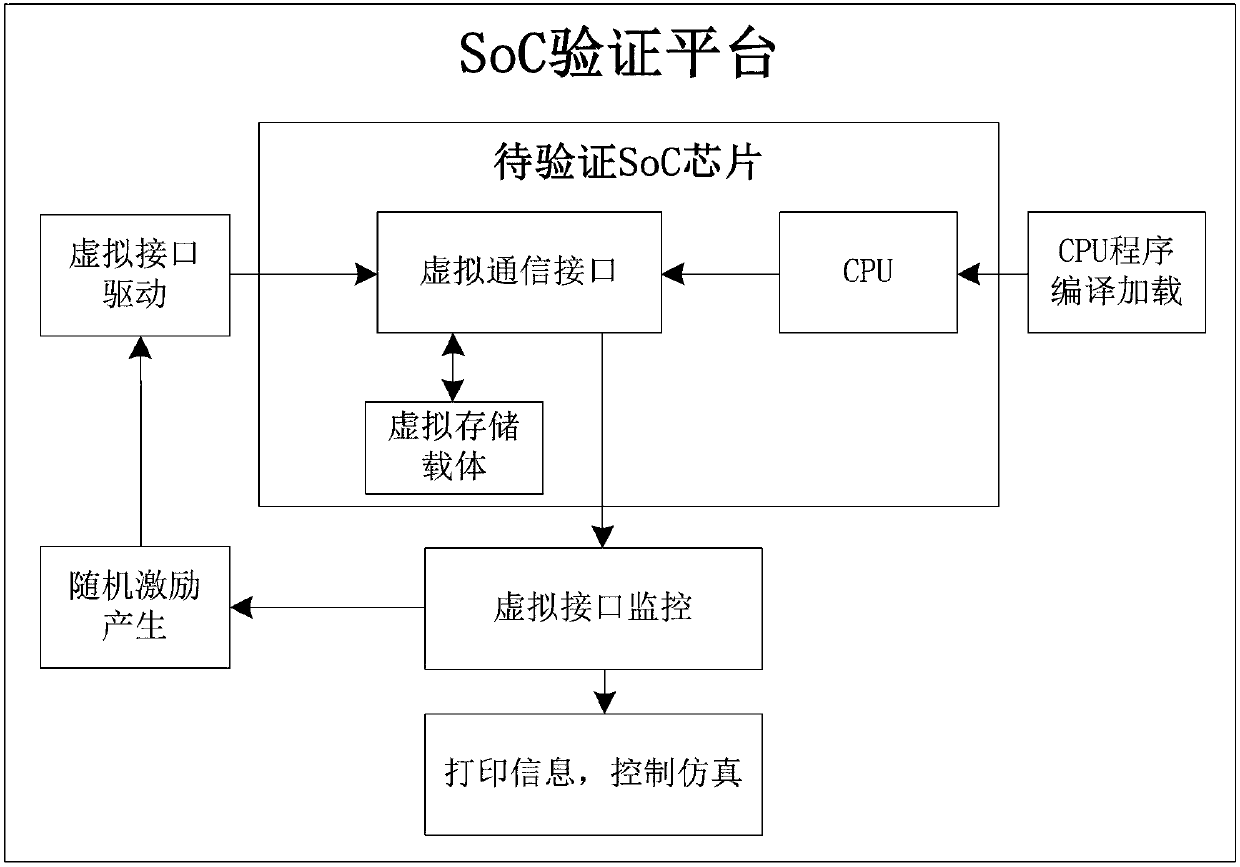
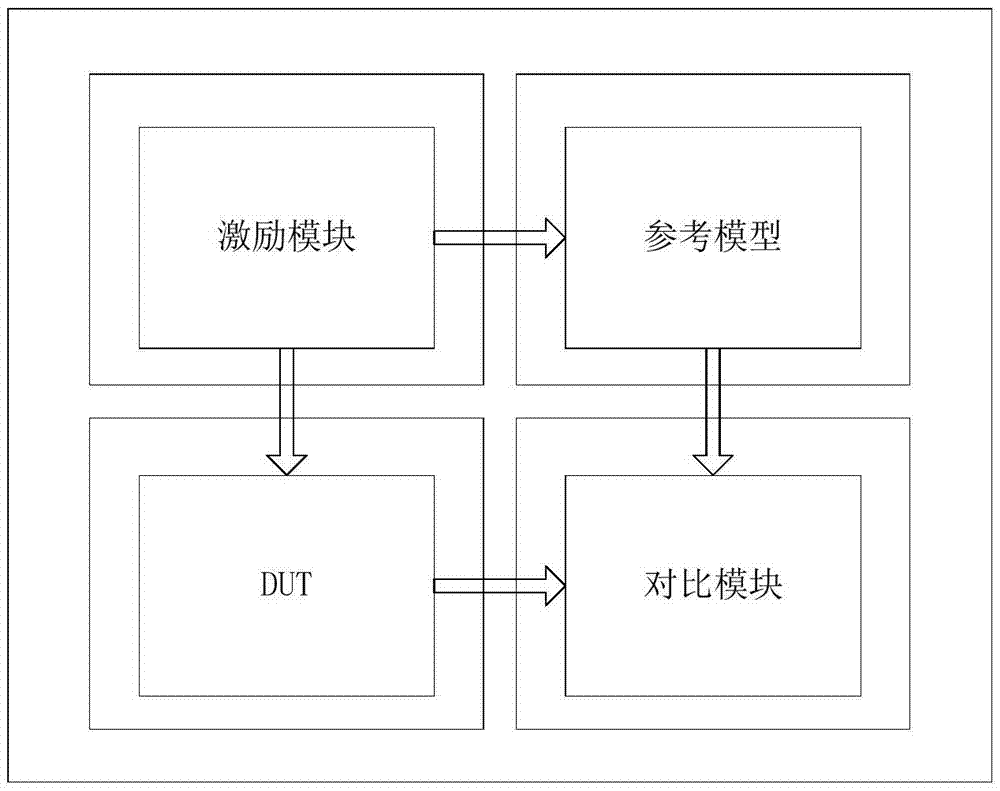
Soc (System-on-Chip) chip verification method
ActiveCN107797846AReal-time interactionRapid positioningSoftware simulation/interpretation/emulationValidation methodsComputer module
The invention discloses an Soc (System-on-Chip) chip verification method. The method is characterized in that one or more that two bus address space segments are obtained by dividing in address spaceinside a to-be-verified Soc chip to use the same as a virtual communication interface, and a virtual interface including an external driving module and a monitoring module is also mounted outside theto-be-verified Soc chip; random-number application is monitored by the monitoring module, random data are generated through a random function, and the generated random data are written into a virtualstorage carrier through the external driving module; and different addresses are defined as different communication requests in an address range of the virtual communication interface, and whether a communication request belongs to the pre-planned communication requests is recognized by the virtual interface through address information of data on a bus. Generation of random excitation is effectively controlled through introducing real-time monitoring of the virtual communication interface, real-time interaction between a CPU program and a hardware simulation program is realized through information printing and simulation process control, quick locating of a problem is facilitated, and verification is enabled to quickly converge.
Owner:RAMAXEL TECH SHENZHEN
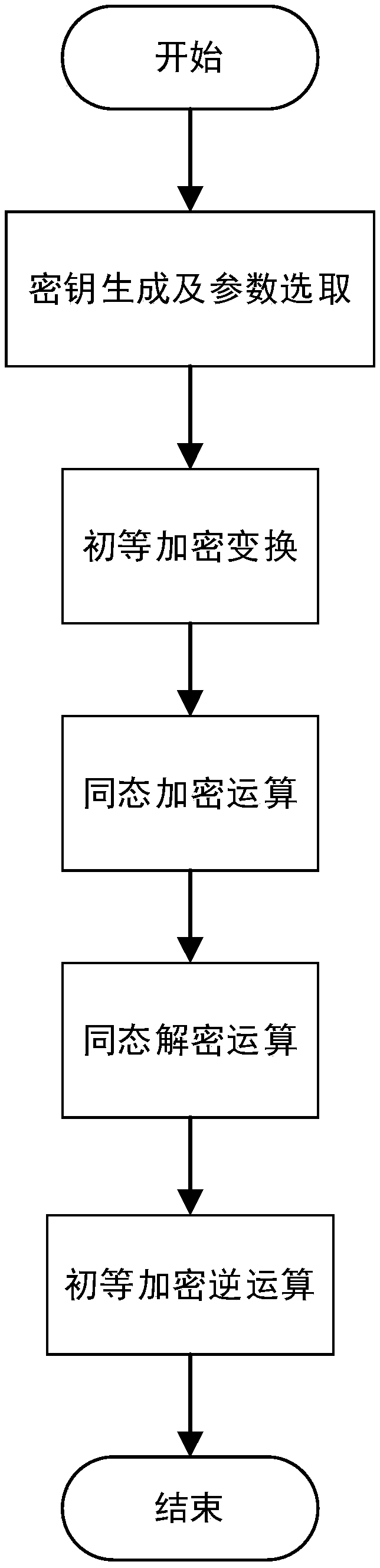
Homomorphic encryption algorithm based on modulo-like operation
ActiveCN108111295AImprove execution efficiencyPrevent leakageCommunication with homomorphic encryptionKey generationKnown-plaintext attack
The invention discloses a homomorphic encryption algorithm based on modulo-like oepration. The homomorphic encryption algorithm comprises following steps: step 1, system initialization: key generationand parameter selection; step 2, encryption operation: primary encryption transform and homomorphic encryption operation; and step 3, decryption operation: homomorphic decryption operation and primary encryption inverse transform. According to the homomorphic encryption algorithm, known plaintext attacks can be resisted, and the leakage of plaintext information and an algorithm structure can be effectively avoided; and a conventional random function is replaced by an interference function so that the consumption of computing resources caused by generation of random numbers is avoided, and theexecution efficiency of the algorithm on a cloud computing platform is effectively improved.
Owner:HOHAI UNIV
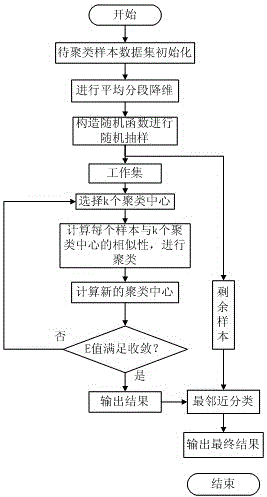
Data clustering method based on dimensionality reduction and sampling
InactiveCN105913077AReduce the numberReduce dimensionalityCharacter and pattern recognitionClustered dataNonlinear dimensionality reduction
The invention discloses a data clustering method based on dimensionality reduction and sampling, comprising steps of performing dimensionality reduction processing on a data set through a piecewise mean value algorithm, constructing a random function, performing random sampling from a large-scale clustering data set to obtain a working set with a relatively small scale, performing k-means clustering on the working set to obtain a random sampling clustering result, and performing classification on residual samples through measuring a relation between the residual samples and the obtained sampling clustering result. The data clustering method based on dimensionality reduction and sampling adopts the dimensionality reduction and sampling to reduce the number and dimensionalities of data samples which participate iteration, greatly reduces the complexity of the k-means algorithm under the condition that a good clustering effect is maintained, and realizes high efficiency clustering for big-scale data.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
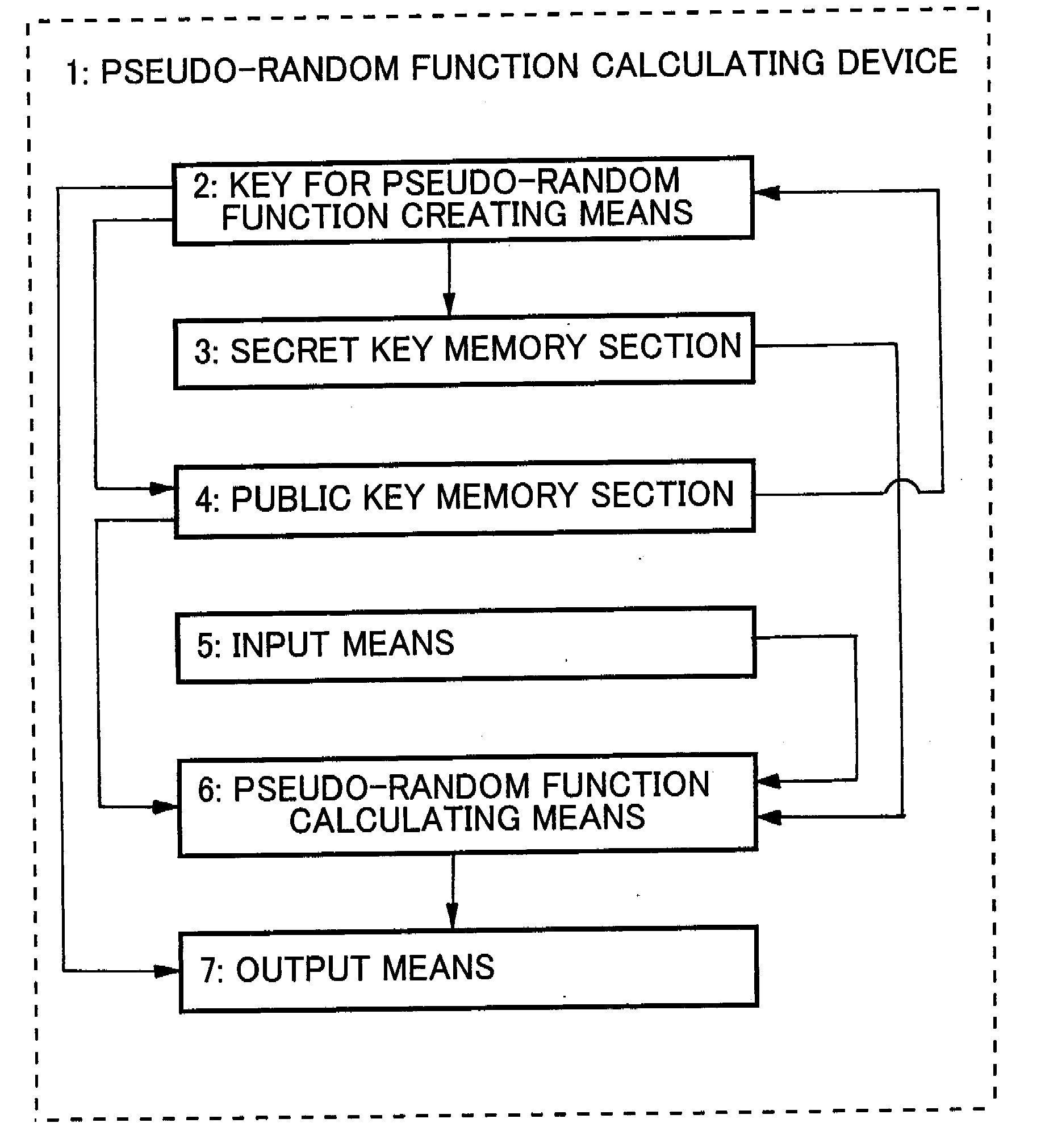
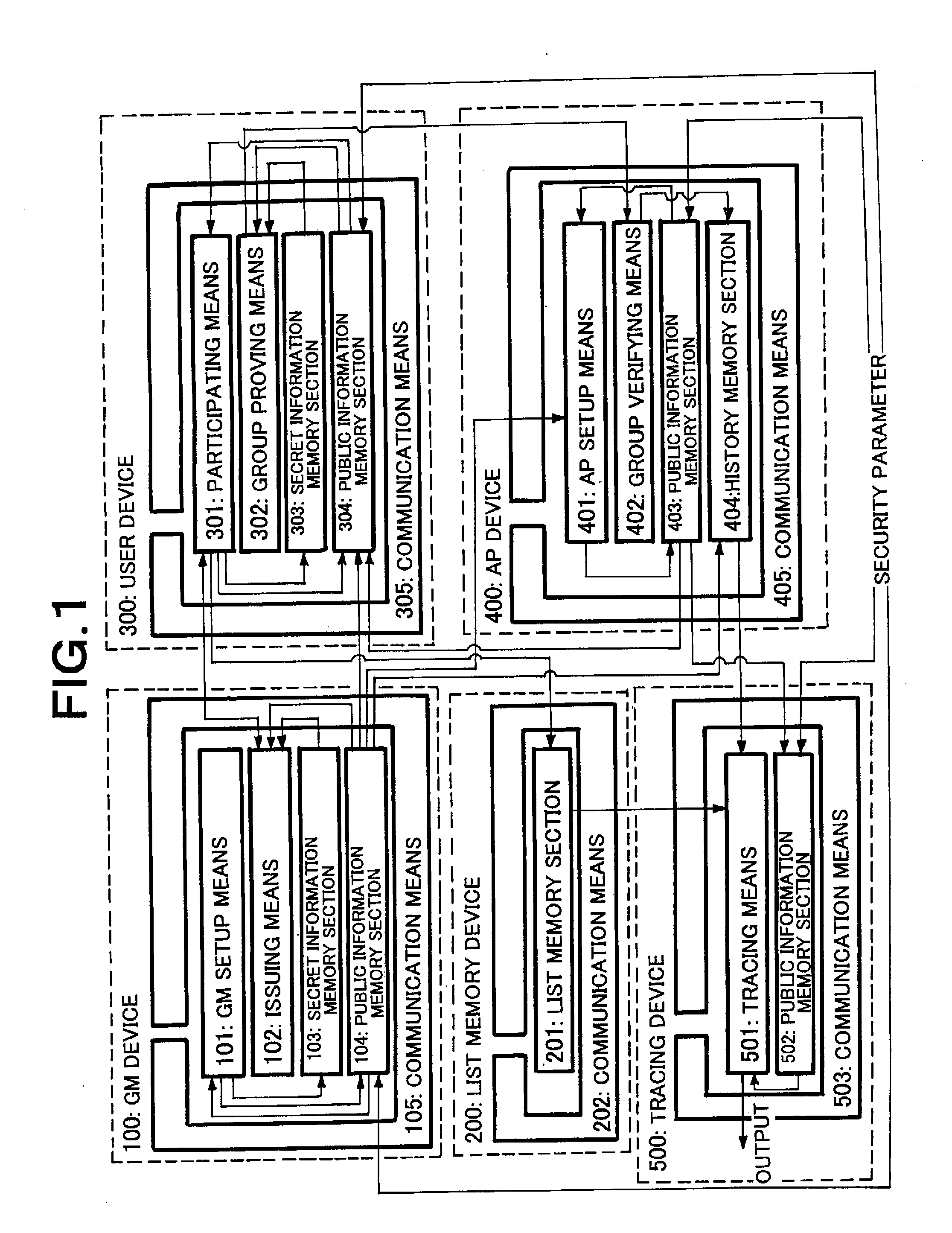
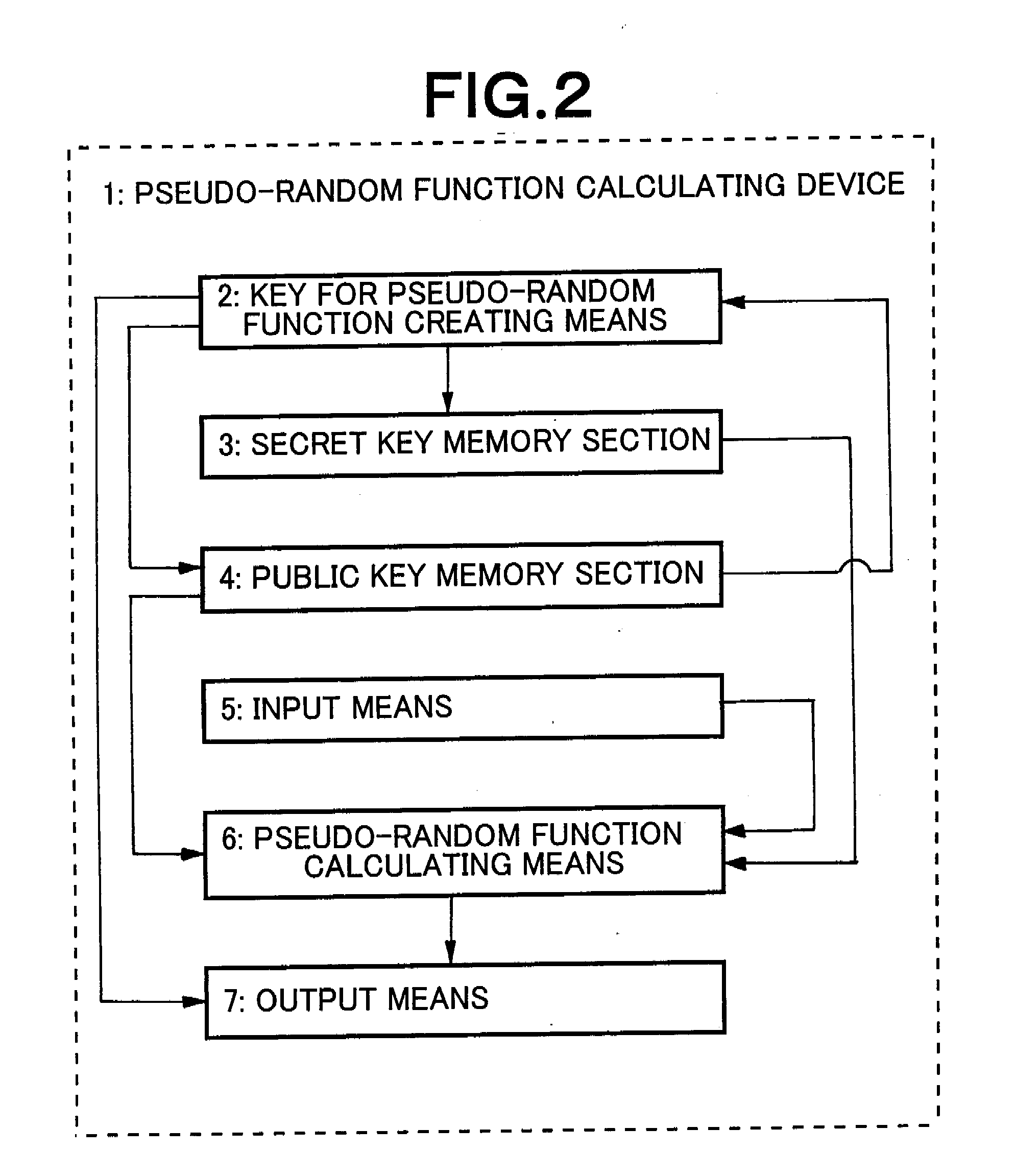
Pseudo-random function calculating device and method and number-limited anonymous authentication system and method
ActiveUS20090041239A1Simple calculationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTheoretical computer scienceModular exponentiation
An efficient pseudo-random function and an efficient limited number of times authentication system using such a function are realized. A pseudo-random function calculating device comprises a key creating means and a pseudo-random function calculating means. The key creating means creates a public key made of a set of at least a first component and a second component as components constituting an element of a finite group and a secret key made of an integer and secretly saves the created secret key in a secret key memory section but makes the public key public. The pseudo-random function calculating means outputs the element of a finite group as function value of the pseudo-random function upon receiving an integer as input. The pseudo-random function calculating means outputs the product of multiplication of the first element of the value obtained by calculating the modular exponentiation, using the first component of the public key and the input integer respectively as base and exponent, and the second element of the value obtained by calculating the modular exponentiation, using the second component of the public key and the reciprocal of the sum of the secret key and the input integer in a finite field respectively as base and component.
Owner:NEC CORP
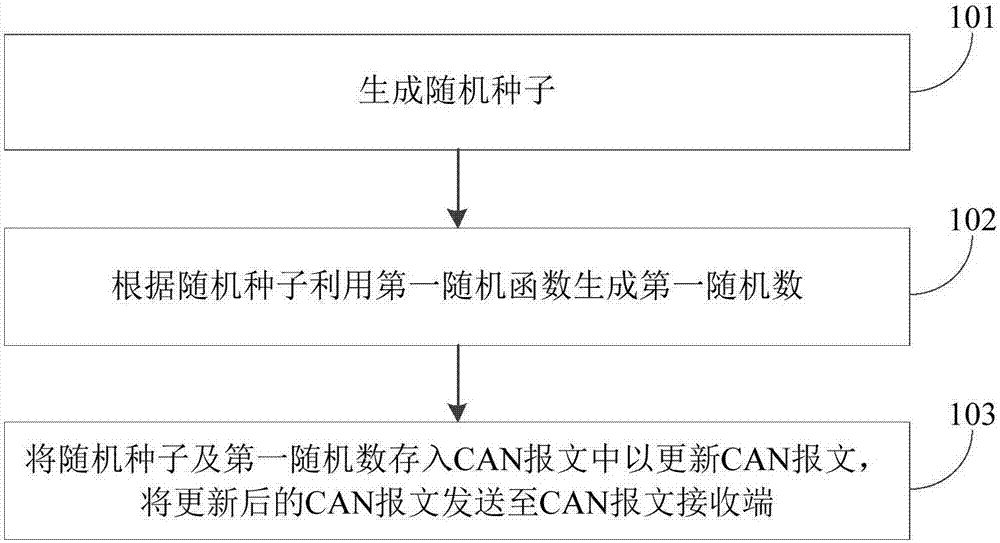
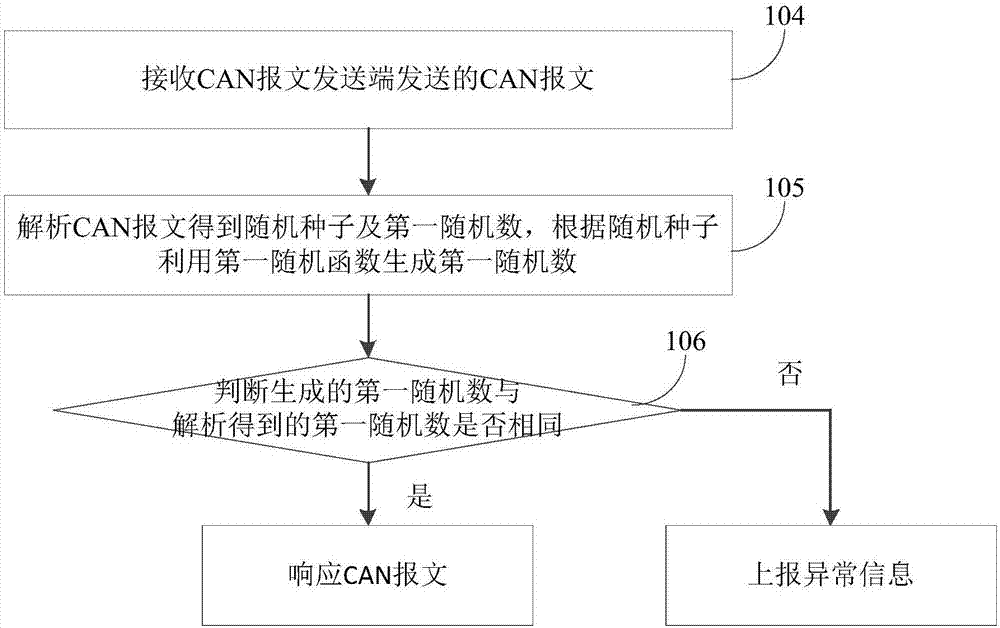
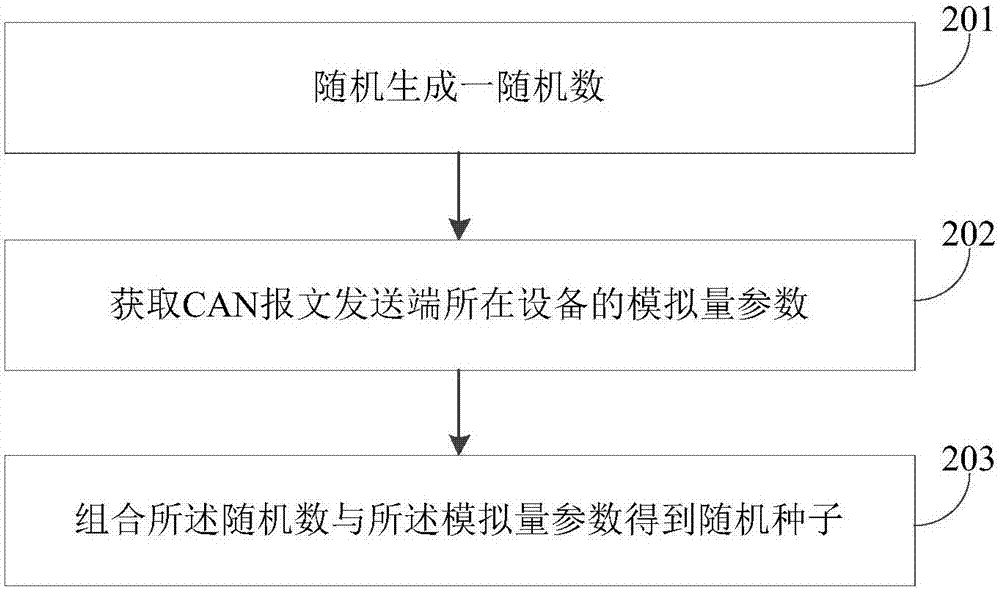
CAN bus communication method based on pseudo-random number
ActiveCN107547572ANot predictableNot pushableKey distribution for secure communicationBus networksComputer hardwareRandom seed
The invention provides a CAN bus communication method based on a pseudo-random number. The CAN bus communication method comprises the steps that a CAN message sending terminal is used for generating arandom seed; a first random function is utilized to generate a first random number according to the random seed; the random seed and the first random number are stored in a CAN message to update theCAN message, and the updated CAN message is sent to a CAN message receiving terminal; the CAN message receiving terminal is used for receiving the CAN message sent by the CAN message sending terminal;the CAN message is parsed to obtain the random seed and the first random number, and the first random number is generated according to the random seed by utilizing the first random function; whetherthe generated first random number is the same as the first random number obtained through parsing or not is judged, if yes, response is made to the CAN message. By storing the randomly generated random seed and the first random number in the CAN message, it can be ensured that CAN messages are different, accordingly the CAN messages do not have foreseeability, forgery attack can be prevented, andthe CAN bus communication method has the advantage of high safety.
Owner:BEIJING BANGCLE TECH CO LTD
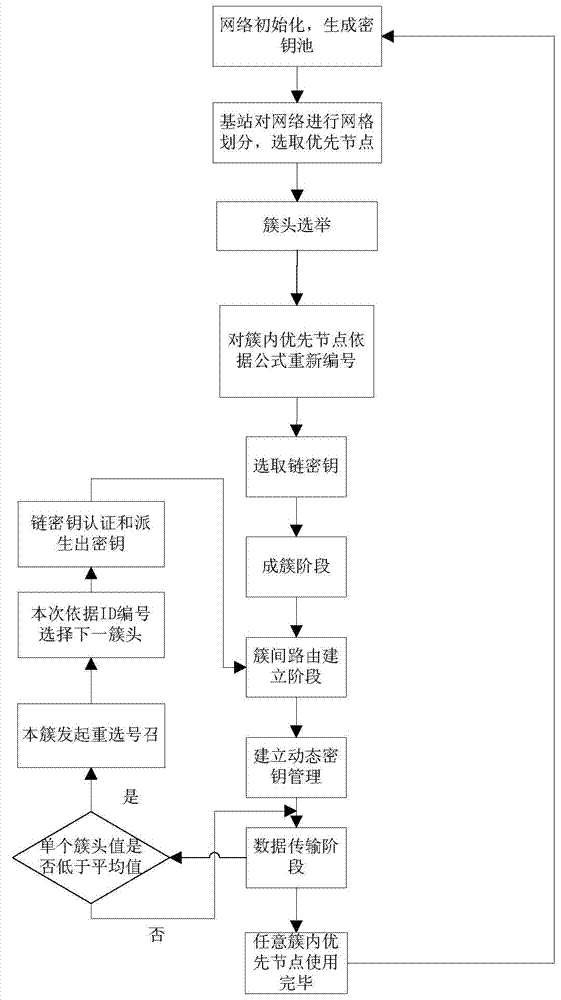
Self-adaptive grid safe routing method in wireless sensor network
InactiveCN103619016AReduce loadImprove relevancePower managementNetwork topologiesWireless mesh networkWireless sensor network
The invention relates to a self-adaptive grid safe routing method in a wireless sensor network, and belongs to the technical field of wireless sensors. The method is characterized in that grids are divided to perform redundancy control by using a base station so that the right that low-energy nodes are selected in a cluster head can be kicked, a cluster head election mechanism is improved, after a cluster head election is completed, each cluster head node randomly distributes a single chain secret key from a secret key pool composed of hash chains, other nodes use a one-way hash function and a pseudorandom function for generating communication secret keys, a secondary cluster head election mechanism is added, and after being attacked, the network is recovered by using a grid self-rule and the serial number of identification of the cluster head to be elected. The safe routing algorithm can effectively reduce the death rate of the nodes, enhance anti-attack capacity, improve the data fusion degree and prolong the lifetime of the network.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
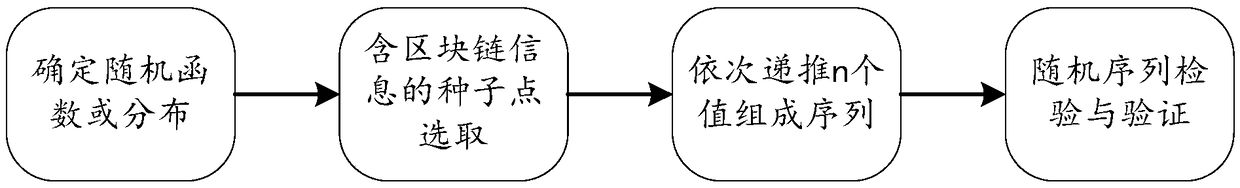
Blockchain-based random number generation method
PendingCN108733351ARelated to avoidGuaranteed randomnessRandom number generatorsRandom seedSignificant difference
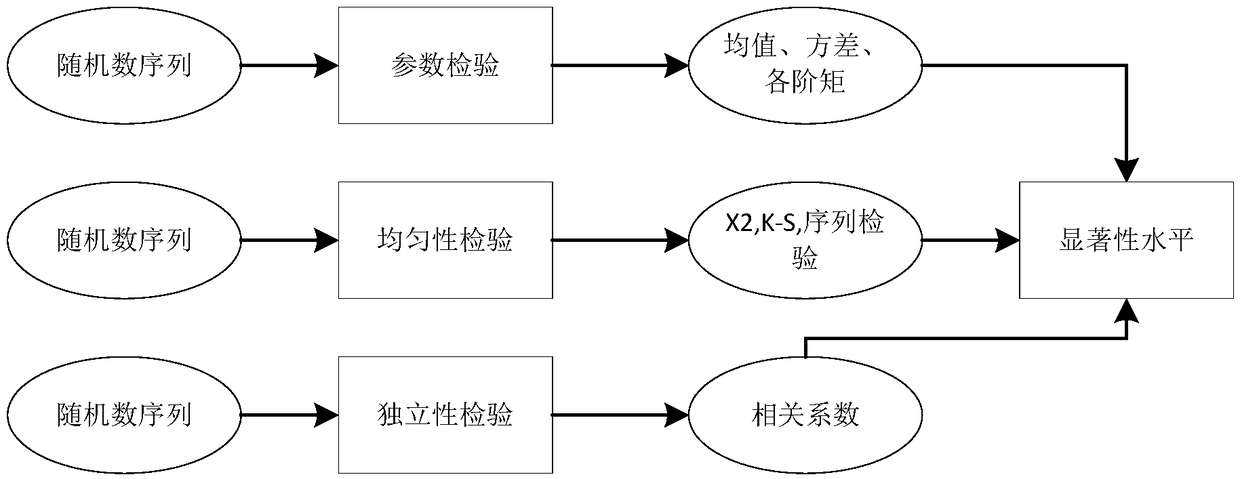
The present invention discloses a blockchain-based random number generation method. The method comprises: introducing a blockchain technology into a random number generation process; assigning a random function of a random number purposefully to each node of the blockchain; and while the node performs its own maintenance, accepting random seeds from other nodes to generate new random numbers. By using the random number generation method disclosed by the present invention, the generated random number has the characteristics of independence, uniformity, and the like, is reasonable through theoretically analysis, is correct through analysis and verification, and has no significant differences in uniformity, parametric tests, independence, combinational rules, and other inspection aspects withthe real random number.
Owner:北京泛融科技有限公司
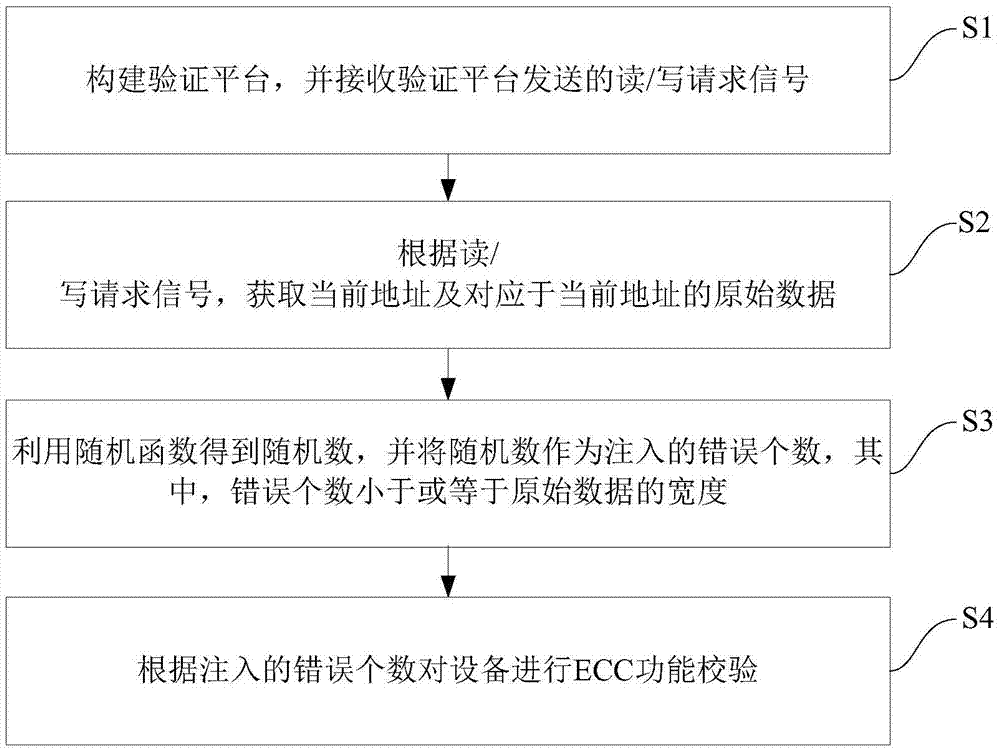
ECC function verification method
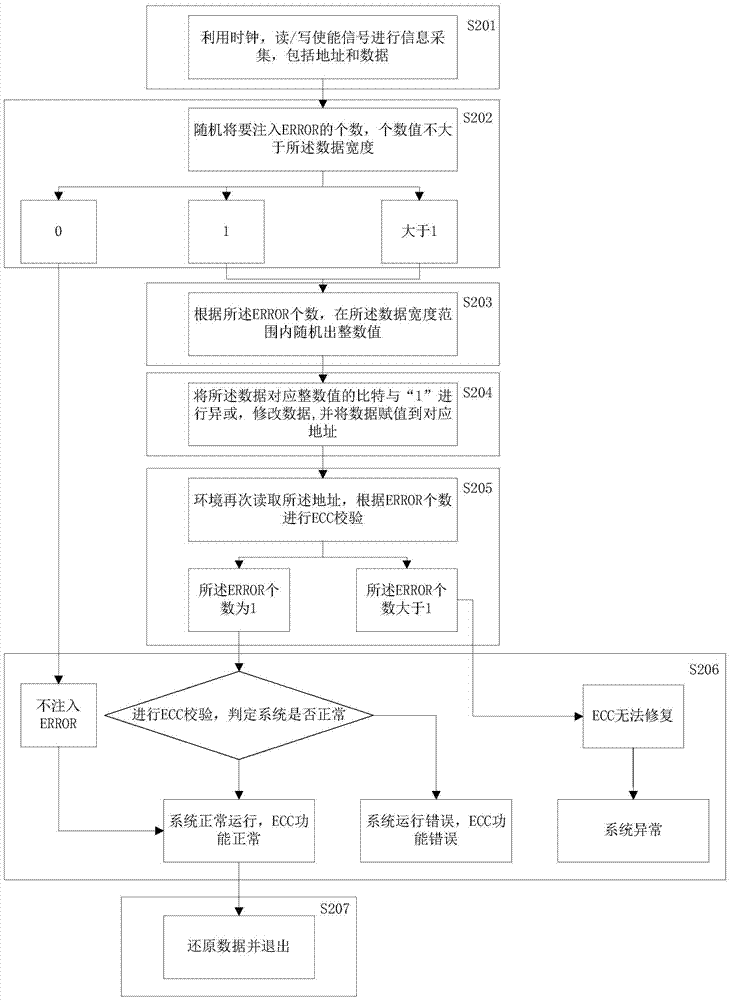
InactiveCN106933696AStrong randomnessImprove controllabilityRedundant data error correctionOriginal dataValidation methods
The invention provides an ECC function verification method. The method comprises the following steps of constructing a verification platform and receiving a reading / writing request signal sent by the verification platform; according to the reading / writing request signal, obtaining a current address and original data corresponding to the current address; obtaining a random number by utilizing a random function, and taking the random number as an injected error number, wherein the error number is smaller than or equal to the width of the original data; and performing ECC function verification according to the injected error number. The method has the advantages of strong controllability, strong randomness, high verification flexibility and comprehensive verification functions.
Owner:北京国睿中数科技股份有限公司 +1
Method and apparatus for enhanced randomization function for personal media
InactiveUS20070143526A1Different experienceMetadata audio data retrievalSpecial data processing applicationsWorld Wide WebThreshold number
A method of playing media files is provided. A plurality of media files is stored. A commonality input that indicates a criterion for commonality is received. Further, a quantitative input is received. The quantitative input indicates a threshold number of the plurality of media files associated with the criterion for commonality. The quantitative input is a number of two or more. The common media files are randomly selected from the plurality of media files according to the commonality input and the quantitative input. The media files are played consecutively within the context of an overall randomized playback context.
Owner:GENERAL INSTR CORP
Grouping encryption method based on random functions and resisting to known plaintext cipher attacks
ActiveCN103607276AReduce workloadEncryption apparatus with shift registers/memoriesPlaintextComputer hardware
The invention belongs to the field of information safety and relates to a grouping encryption method. Random functions are used for constructing the grouping encryption method. The code (encryption) algorithm is uncertain and random, encrypts through the random functions. The specific mode of the functions is determined by secret keys, parameters shared secretly by two parties and other parameters. The secret keys influence the specific mode of the functions and are input parameters of the functions, thus, a code analyzer is made to be incapable of determining the algorithm when not knowing the secret keys and the secret parameters, so that effective code analysis cannot be conducted through known plaintext cipher. Different function specific modes of different groups are used, so that potential attacks can be effectively resisted to.
Owner:GUILIN UNIV OF ELECTRONIC TECH
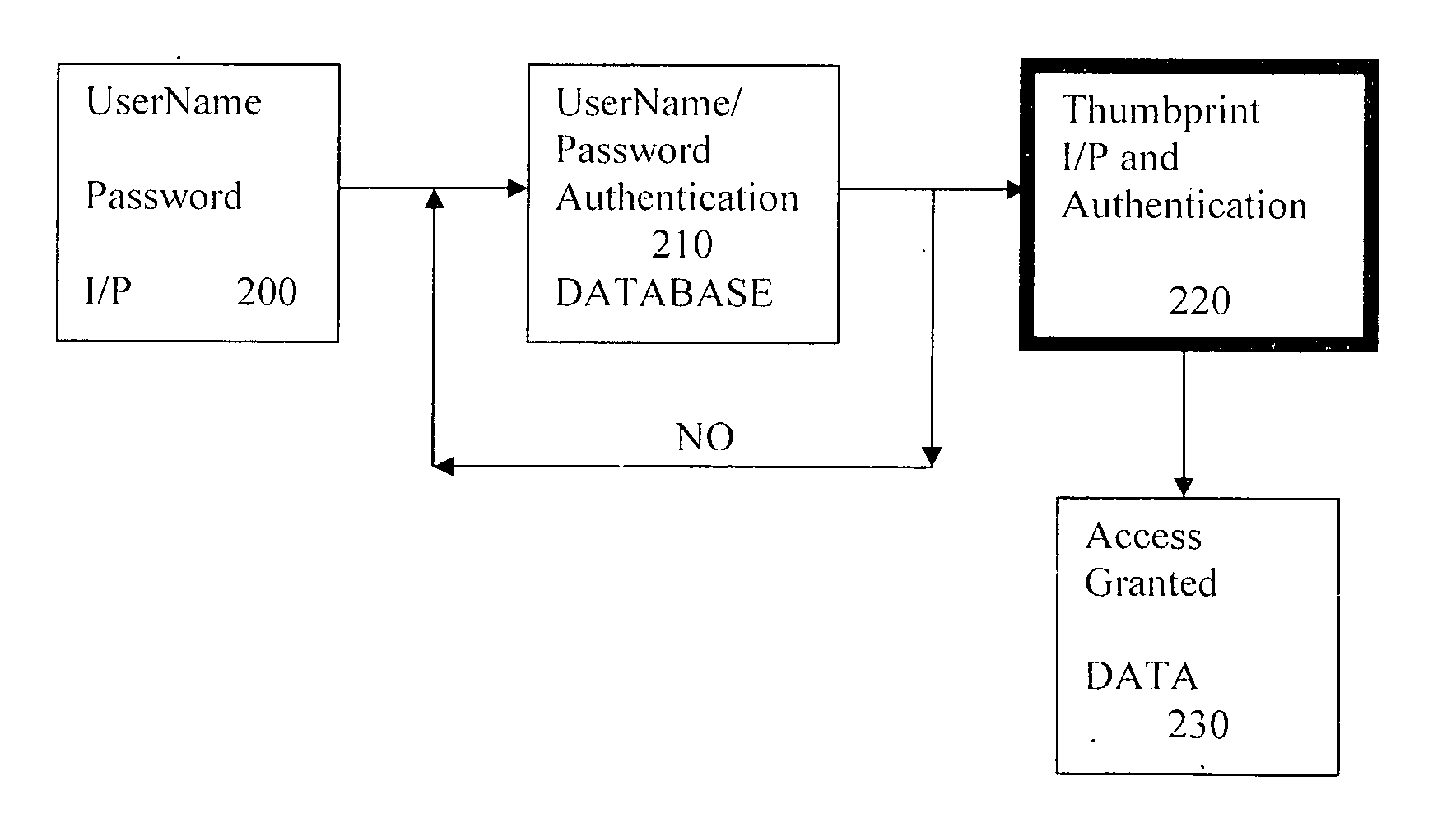
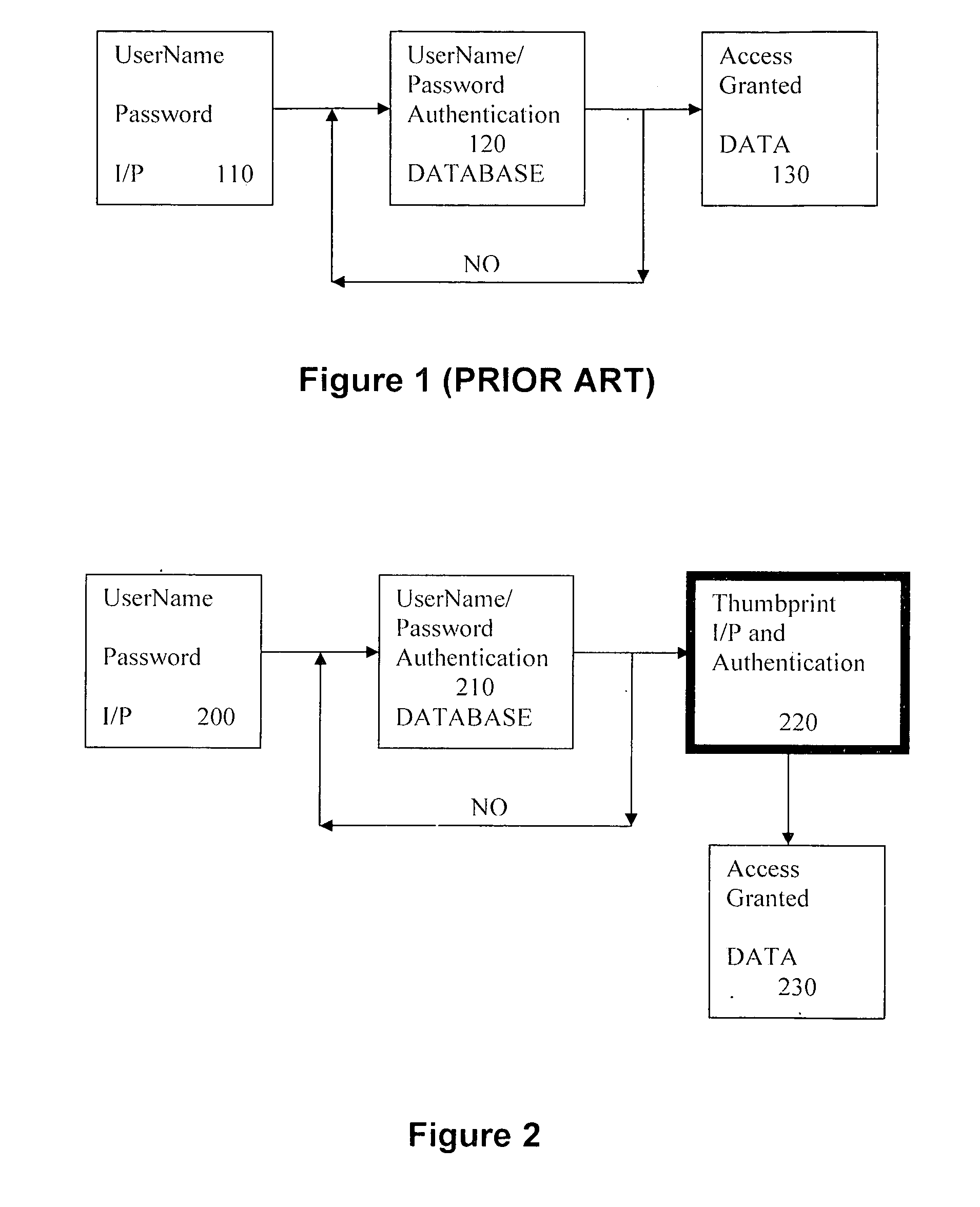
Method and system for string-based biometric authentication
InactiveCN101199160APublic key for secure communicationUser identity/authority verificationBiometric dataPassword
Techniques for string-based biometric authentication are described that includes a method for string-based biometric authentication provided that comprises the steps of receiving a username and password combination associated with a person, acquiring a biometric data from the person, generating a random string of biometric information based on the biometric data using a randomization function, truncating said random biometric string, and storing said truncated random biometric string along with the associated username and password combination of the person in a biometric database for future authorizations of the same person. To authenticate a user, the acquired biometric data is compared with a truncated biometric string in said biometric database searching for a match, and if a match is found, authorization of the person to access a resource is given.
Owner:朱利叶斯·穆瓦勒
Block ciphering method based on random function to resist against known plaintext-ciphertext pair attack
The invention belongs to the field of information security, and relates to a block ciphering method. The block ciphering method is constructed by a random function. The cryptographic (encryption) algorithm is uncertain and random, when the random function is used to encrypt, the concrete form of the function is determined by a secrete key which also determines the concrete form of the function and is an input parameter of the function, so an analyzer cannot think about the whole situation. By virtue of the design, a cipher analyzer cannot determine the algorithm when the analyzer does not know the secrete key, thus the analyzer cannot effectively analyze the cipher through the known plaintext-ciphertext pair.
Owner:GUILIN UNIV OF ELECTRONIC TECH
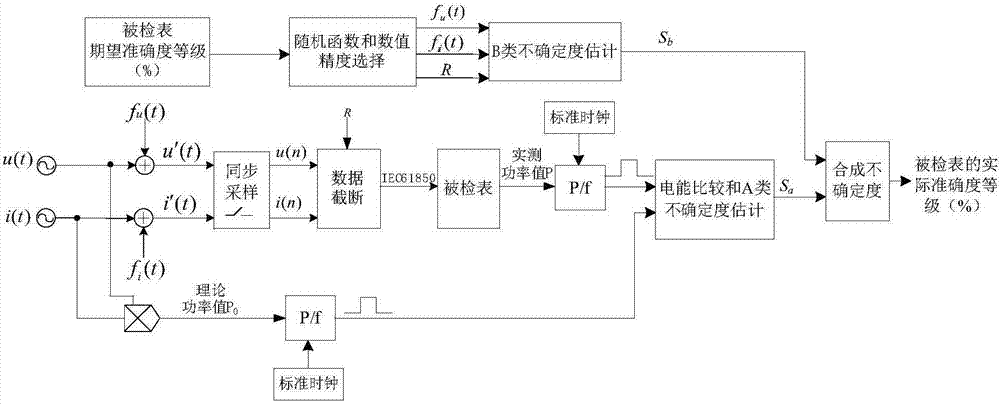
Digitization electric energy meter detection and traceablility method based on standard digital power source
ActiveCN106918797ASolve the confusion of traceabilityAvoid confusionElectrical measurementsTruth valueComposite function
The present invention discloses a digitization electric energy meter detection and traceablility method based on a standard digital power source. According to opinions that a standard digitization electric energy meter only can perform numerical value traceablility and does not has physical quantity traceablility and a theoretical value is namely a true value, an output mode is provided that a composite function obtained through addition of Fourier series in a trigonometric function mode and a random function is taken as a standard digital power source. In a given power theoretical value condition, appropriate value precision and parameters of the random function are determined according to the expected accuracy level of the detected digitization electric energy meter to configured the standard digital power source, obtain the voltage and current discretization data with given precision and send the voltage and current discretization data to a detected table; and the actual accuracy level of the detected table is determined through assessment of the uncertainty between the measurement result of the detected table and the theoretical value. The digitization electric energy meter detection and traceablility method based on the standard digital power source realizes detection and traceablility of the digitization electric energy meter.
Owner:STATE GRID CORP OF CHINA +1
Testing method and device of memory
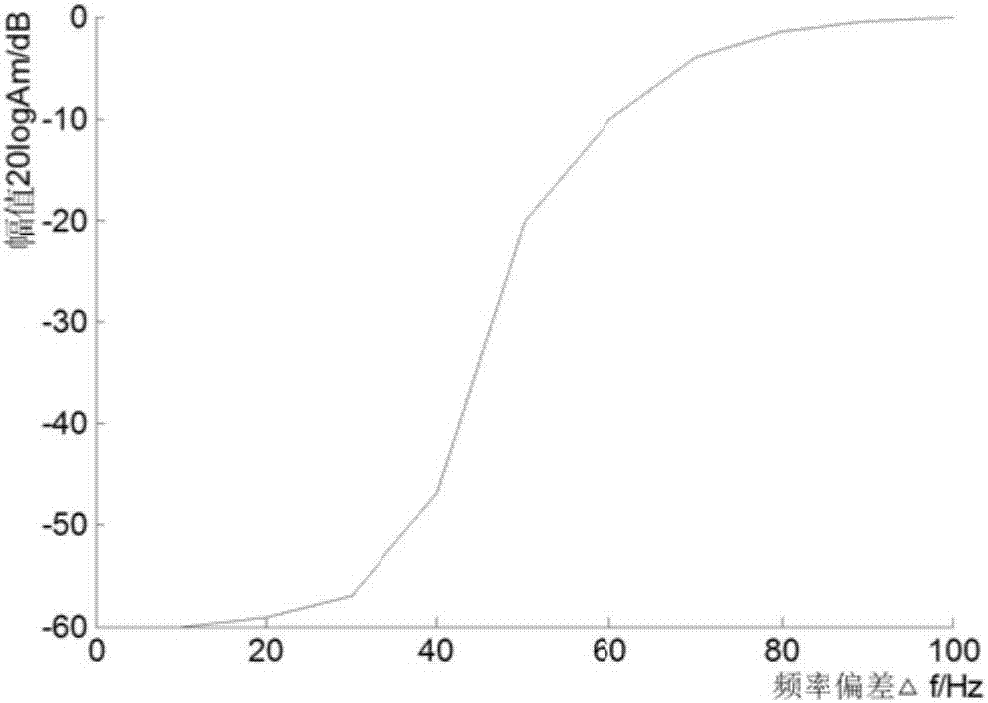
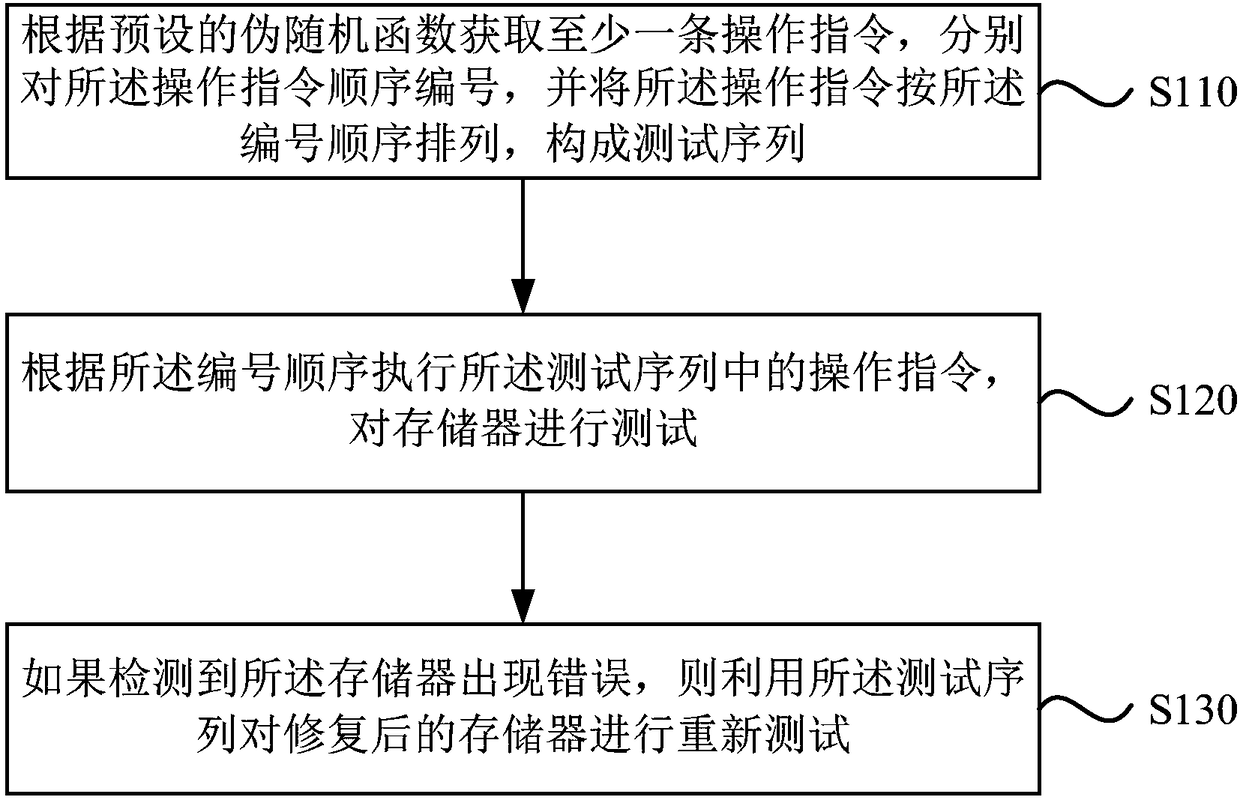
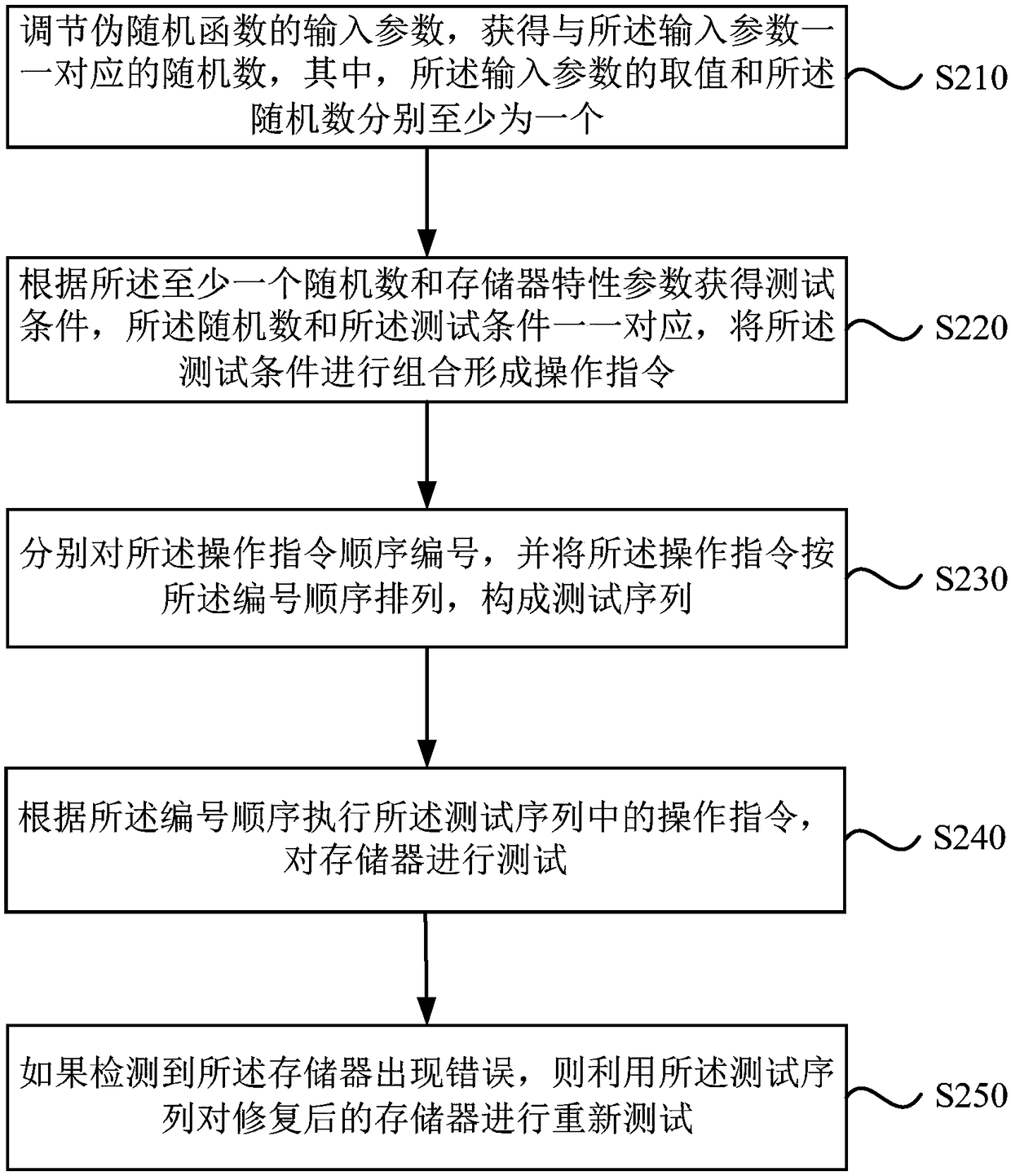
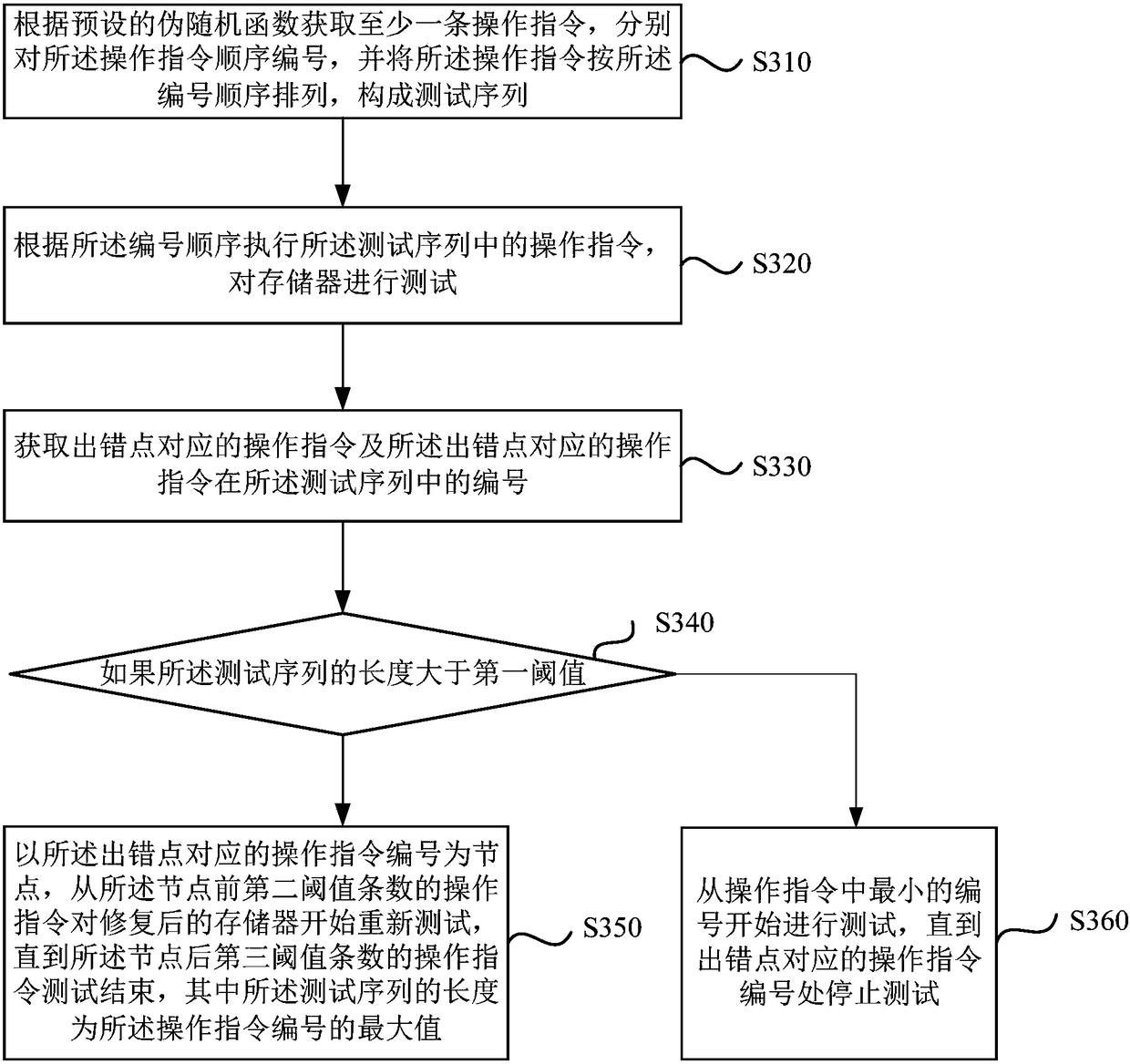
ActiveCN108122596AImplement random testingEnsure comprehensivenessStatic storageInstruction sequenceRandomization function
The embodiment of the invention discloses a testing method and device of a memory. The method includes: acquiring at least one operation instruction according to a preset pseudo-random function, respectively numbering the operation instruction in an orderly manner, and arranging the operation instruction according to a number order to form a testing sequence; executing the operation instruction inthe testing sequence according to the number order to test the memory; and utilizing the testing sequence to retest the repaired memory if occurrence of an error of the memory is detected. Random testing on memory programs and / or data is realized, comprehensiveness of testing is guaranteed, and accuracy and efficiency of testing are improved.
Owner:GIGADEVICE SEMICON (BEIJING) INC
Question type picture verification code generation method
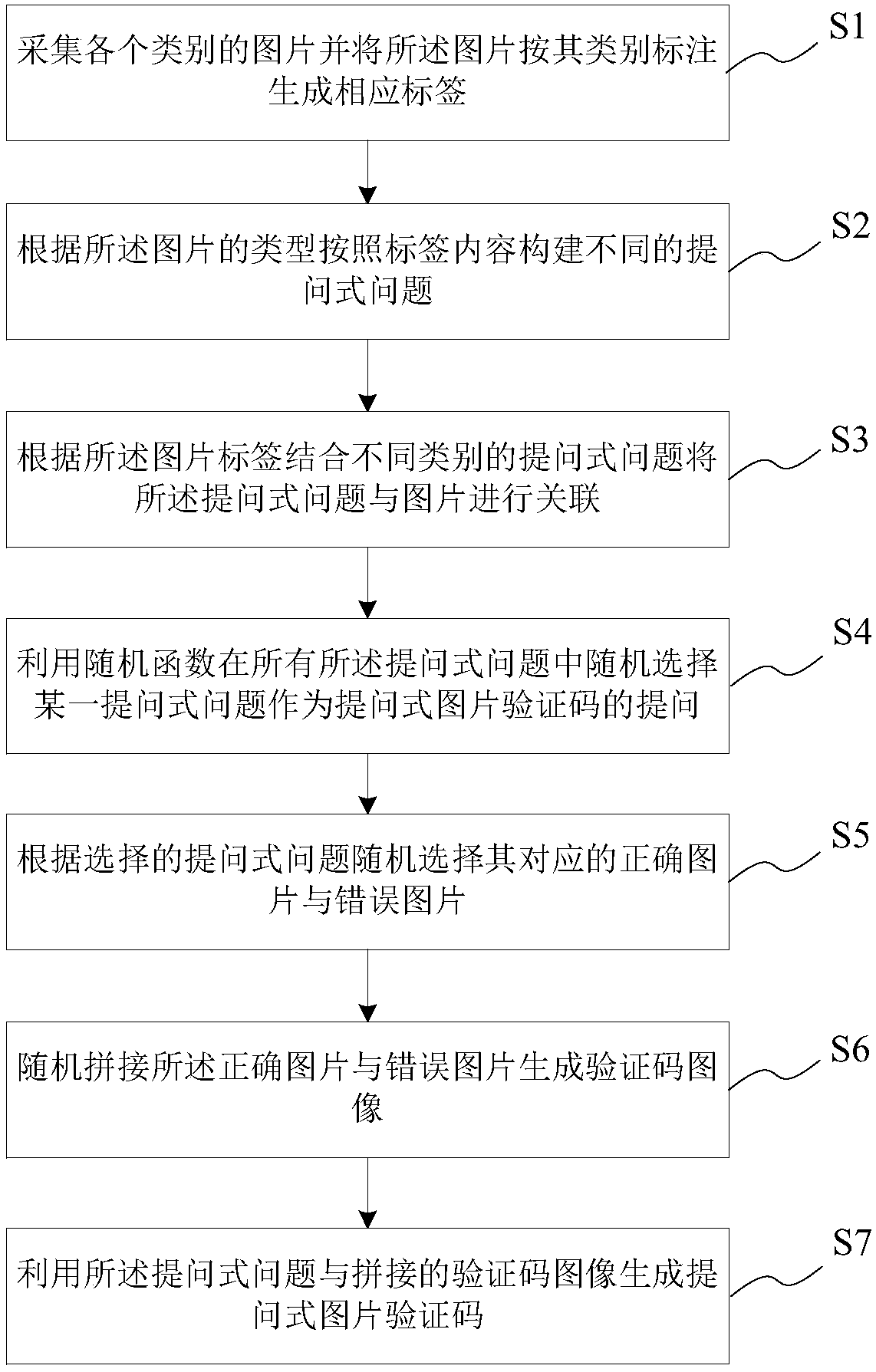
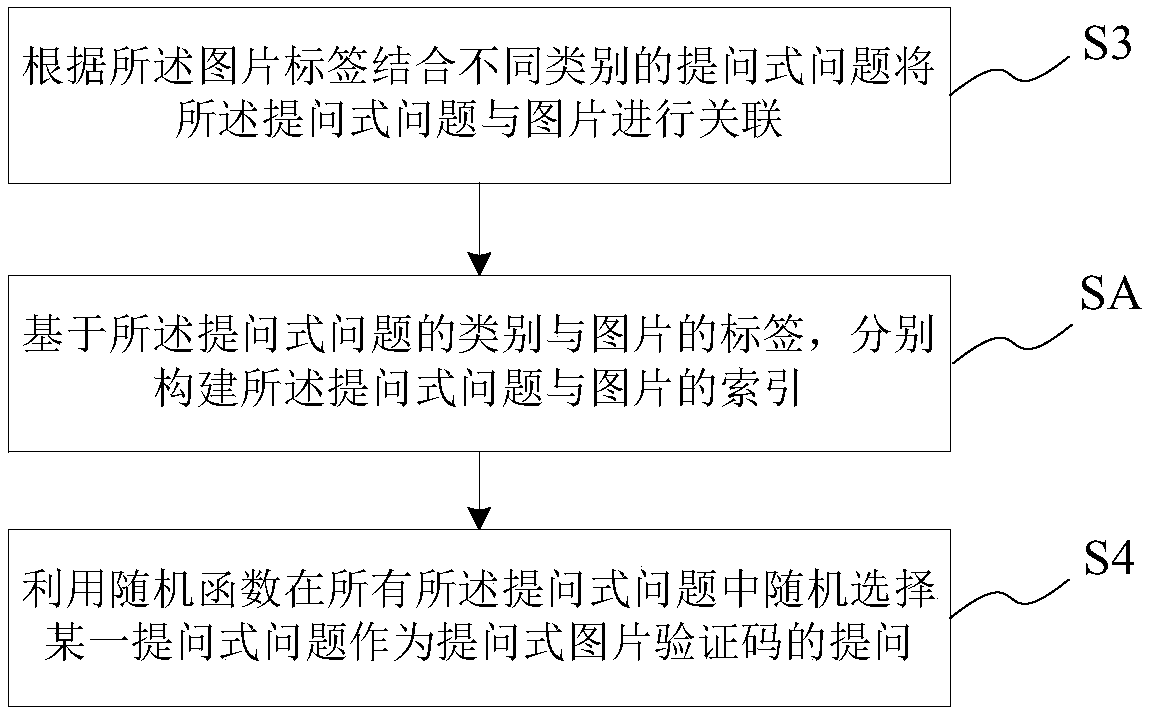
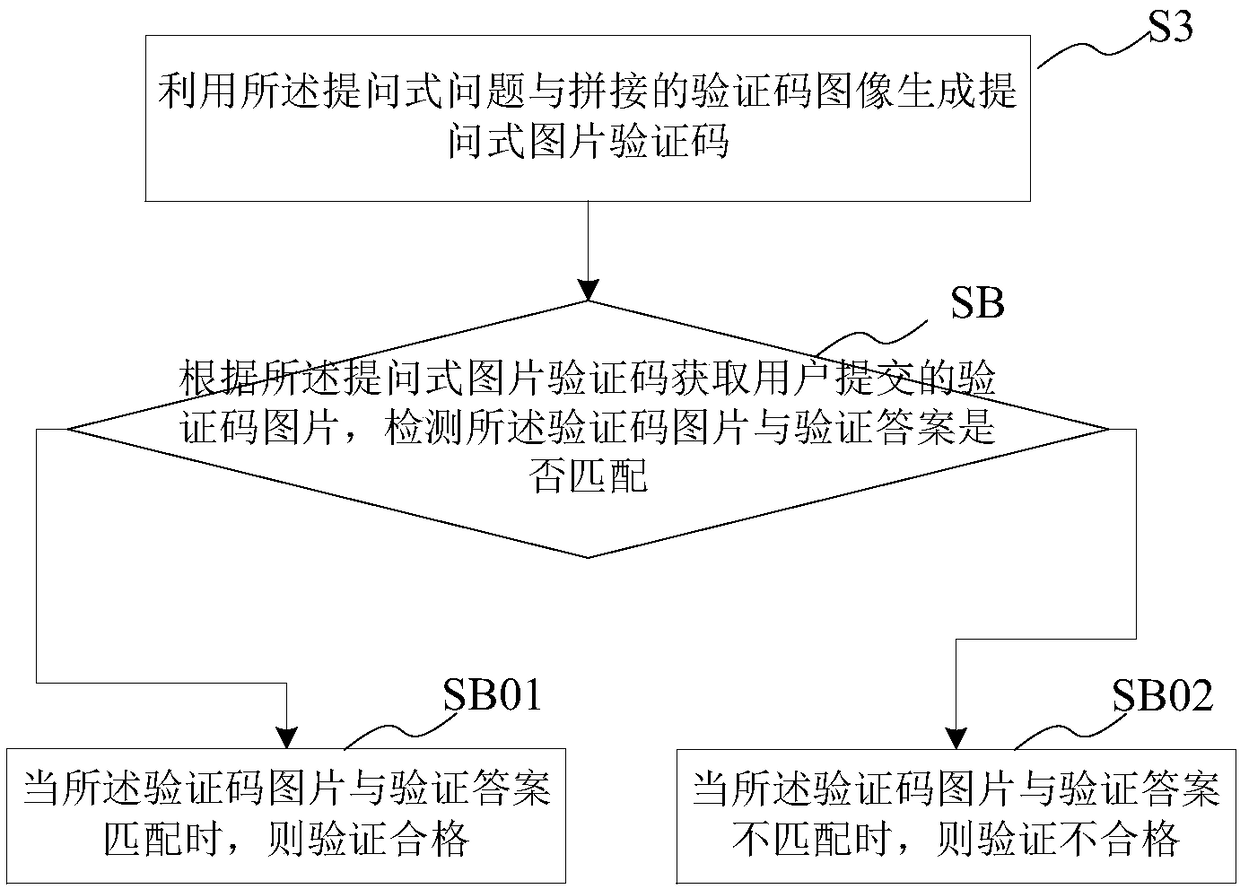
InactiveCN108123806APrevent intelligent recognitionImprove securityUser identity/authority verificationProgramming languageRandomization function
The invention provides a question type picture verification mode generation method. The question type picture verification mode generation method comprises the steps of collecting all kinds of pictures and labeling the pictures according to the type to generate corresponding labels; building different question type questions based on the picture types and label content; associating the question type questions with pictures by combining the picture labels with different types of question type questions; selecting one question type question randomly from all the question type questions as a question of a question type picture verification code by utilizing a random function; selecting corresponding correct pictures and wrong pictures randomly based on the selected question type question; splicing the correct pictures and the wrong pictures randomly to generate a verification code image; and generating the question type picture verification code by utilizing the question type question andthe spliced verification code image. The question type picture verification mode generation method can increase the difficulty which is easily cracked in a verification process efficiently and can guarantee verification safety; and the user experience is improved.
Owner:重庆亚凡科技有限公司
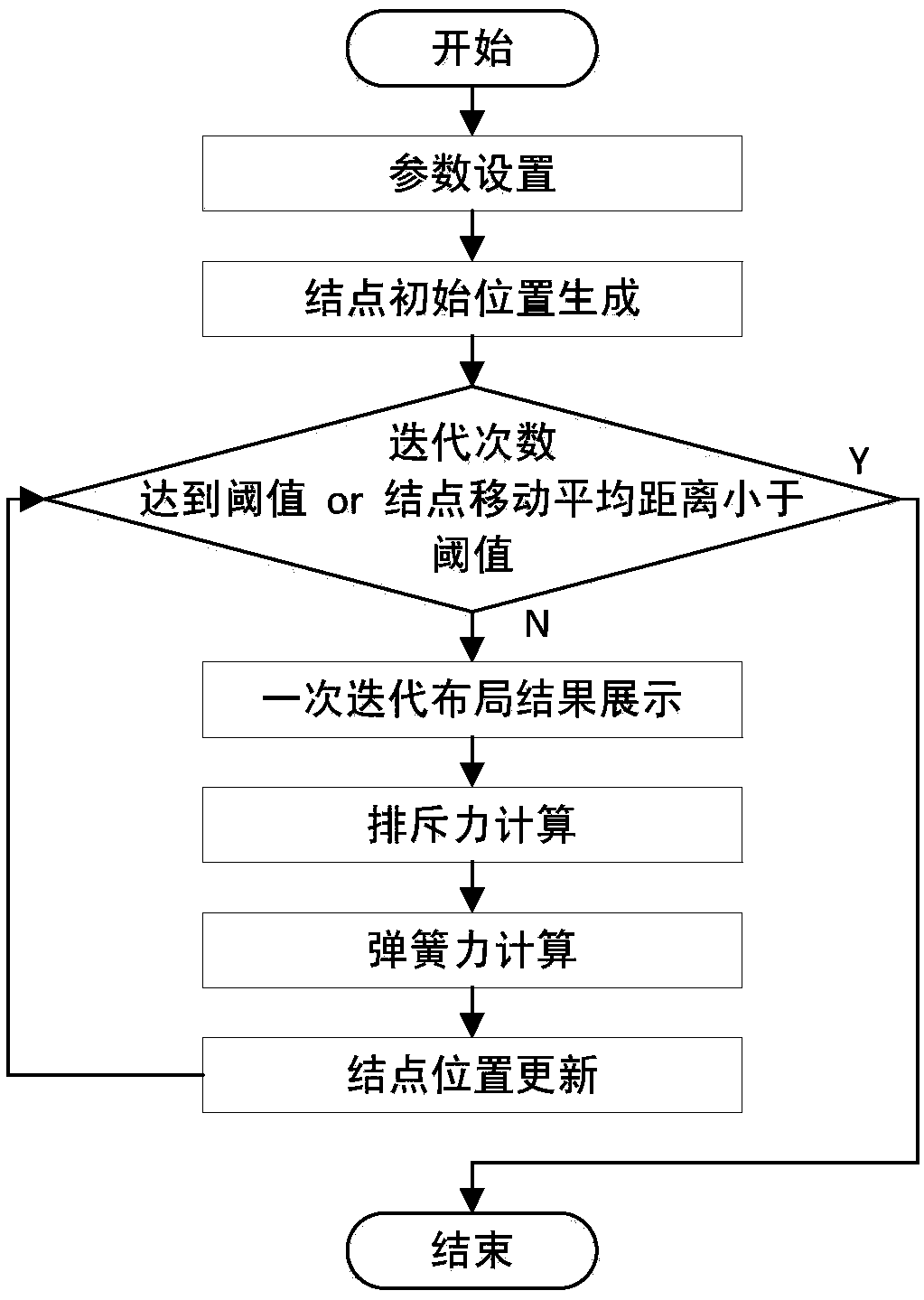
Method for visualizing layout optimization of graph data based on force guiding algorithm
ActiveCN107818149AEasy to separateLayout improvementDrawing from basic elementsOther databases browsing/visualisationAlgorithmData visualization
The invention relates to a method for visualizing layout optimization of graph data based on a force guiding algorithm. The method, to optimize the visual layout of the graph data, in the loop iteration process of the force guiding algorithm, adds the following processing step that in the case of node adhesion, the position of the pop-up of nodes and the direction of the pop-up of the nodes are given by a random function, so that the adhesive nodes are separated from each other by a certain distance, and the attracting force and the repulsive force in the case of node adhesion can be calculated. Further, the method adopts a gradient setting for parameter delta values in the displacement calculation of the force guiding algorithm, so that the visualization process of the graph data reducesthe shock and quickly converges. The method can solve the above problems in the basic force guiding layout algorithm and improves the layout efficiency of the algorithm while optimizing the layout effect of the algorithm.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
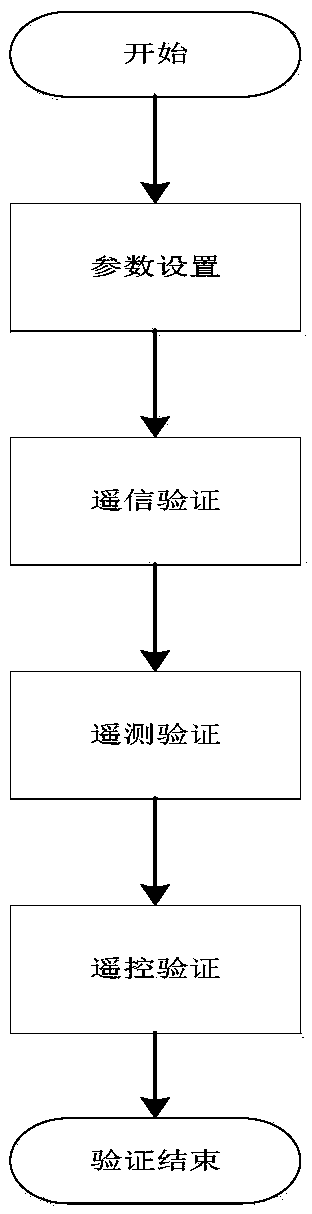
Method for testing new system through simulation four-remote signal generator
InactiveCN108918997AAccuracy Limit ImprovementReduce error rateElectrical testingFunctional testingComputer module
The invention relates to a method for testing a new system through a simulation four-remote signal generator. The method refers to a four-remote signal simulation system. The four-remote signal simulation system comprises a remote signaling verification module, a remote measuring verification module and a remote control verification module. The four-remote signal simulation system simulates a PC into the situation that a substation communicates with an automatic system, change remote signaling parts and remote measuring parts are generated in batch, and remote control and remote regulating commands issued by the automatic system are recorded. The method comprises the following four testing steps of parameter setting, remote signaling verification, remote measuring verification and remote control verification. The remote signaling deflection generated by the hardware test environment is simulated through the four-remote signal simulation system, and batch generation of the change remotesignaling parts in a short time is achieved; the random function is adopted to generate the remote measuring parts within the reasonable range, and after communication is established, the remote measuring parts are uploaded to a testing system; and remote control commands issued by the testing system are recorded, the time of a functional test is shortened from at least five hours in the past to0.1 hour, the accuracy limit is increased, and the error rate is nearly decreased to be zero.
Owner:GUANGDONG POWER GRID CO LTD +1
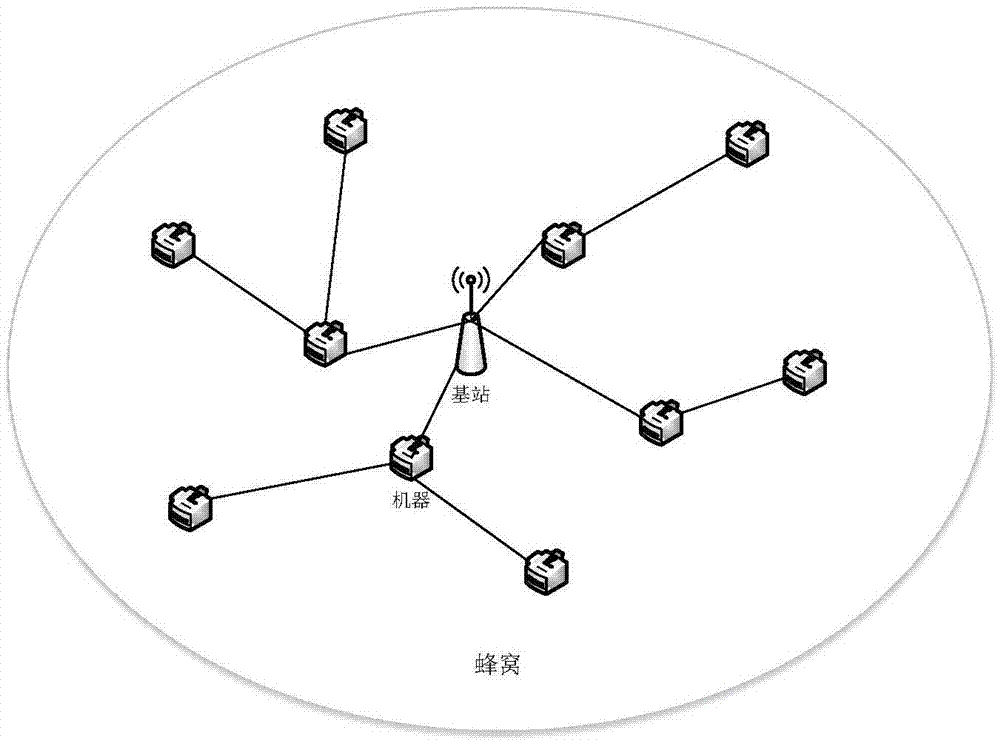
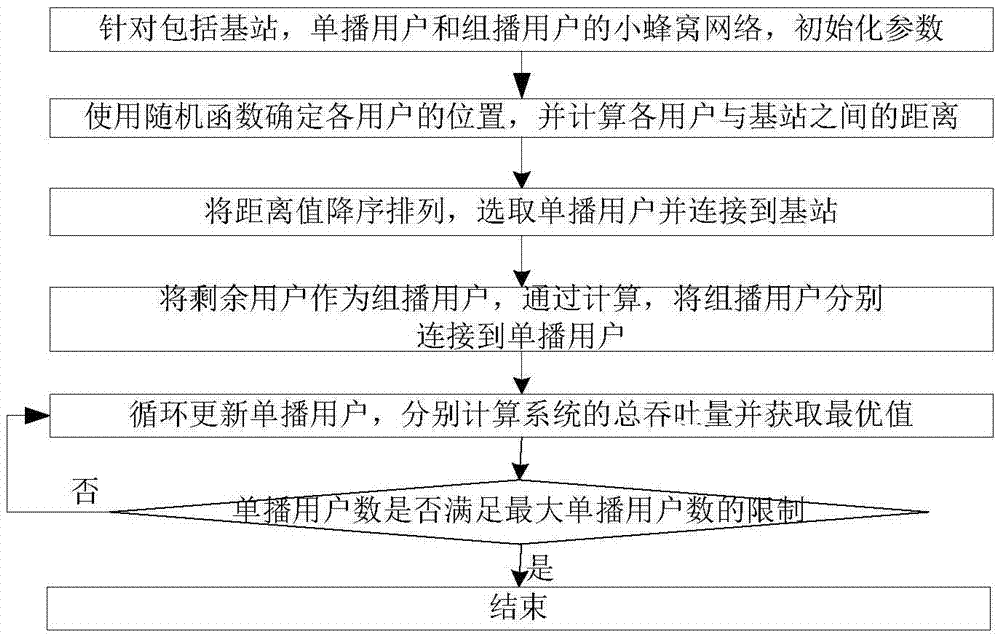
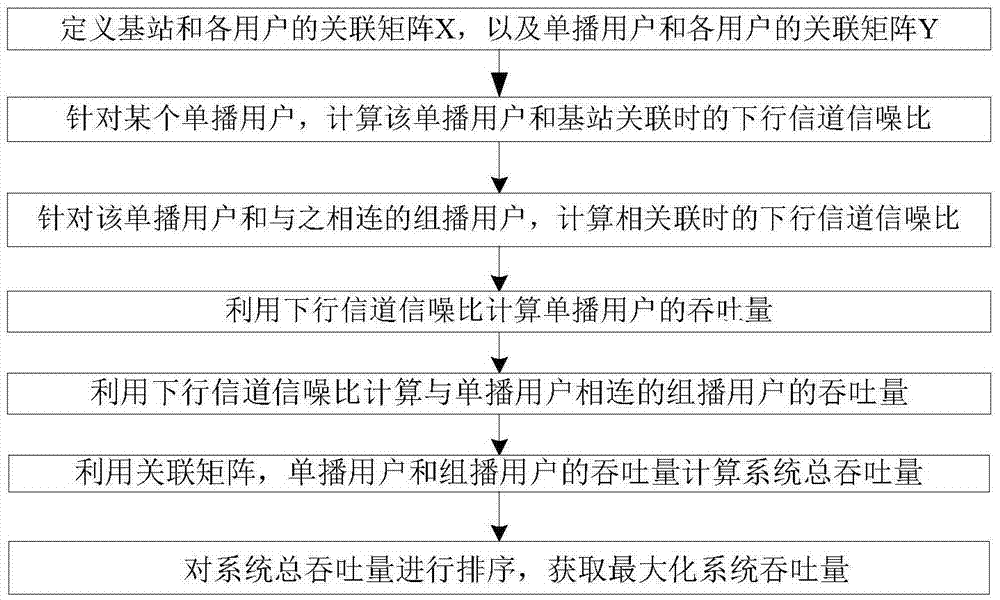
Combined unicast and multicast mechanism-based resource allocation method
ActiveCN105451350AGuaranteed QoS requirementsAlgorithm with few parametersBroadcast service distributionMachine-to-machine/machine-type communication serviceRound complexityFirefly algorithm
The invention discloses a combined unicast and multicast mechanism-based resource allocation method. The method specifically comprises the steps of 1, initializing parameters; 2, determining the location of each user by a random function and calculating distance values; 3, arranging the distance values in a descending order, selecting unicast users and connecting the unicast users with a base station respectively; 4, for each rest multicast user, respectively calculating the distance between the above multicast user and each unicast user respectively, and connecting according to the minimum value of the distance values; 5, circularly updating the number value of unicast users, and respectively calculating a system total throughput and a maximum value; 6, judging whether the number value of unicast users meets the restriction requirement on the maximum value of unicast users or not; if yes, outputting the maximized system throughput; if not, returning to conduct the step 5. According to the technical scheme of the invention, the characteristics of the firefly algorithm are fully utilized, so that the method has the advantages of fewer parameters, easy implementation, reduced complexity of system resource allocation and less computation time. Meanwhile, the system throughput is maximized while the QoS requirements of system users can be met at the same time.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Mode of implementing desktop random animation of embedded system platform
InactiveCN102541545AThe animation process is rich and variedEasy to makeAnimationSpecific program execution arrangementsAnimationTimer
The invention relates to presentation of animation information, in particular to a mode of presenting a desktop animation implemented on an embedded system platform. The mode of implementing the desktop random animation of the embedded system platform comprises the following processes: A) decomposing the animation and constructing animation elements; B) defining change attributes of all the related animation elements; and C) carrying out the following processes of: C1) carrying out initialization on the change attribute of each animation element in an initialization interface by calling a random function; C2) calling animation calculation interfaces at regular intervals by a timer, transferring time variables into an action equation and calculating the animation element for drawing an animation picture at a specific moment and corresponding specific attribute parameters of the change attribute of the animation element; C3), carrying out presentation on the action pictures by calling animation drawing interfaces; and C4) waiting for the next moment of the timer in the process C2) to arrive and carrying out the process C2), wherein each animation element is provided with three basic interfaces for being called by a main control program for presenting the animation. The mode is used for implementing the desktop random animation of the embedded system platform.
Owner:XIAMEN YAXON NETWORKS CO LTD
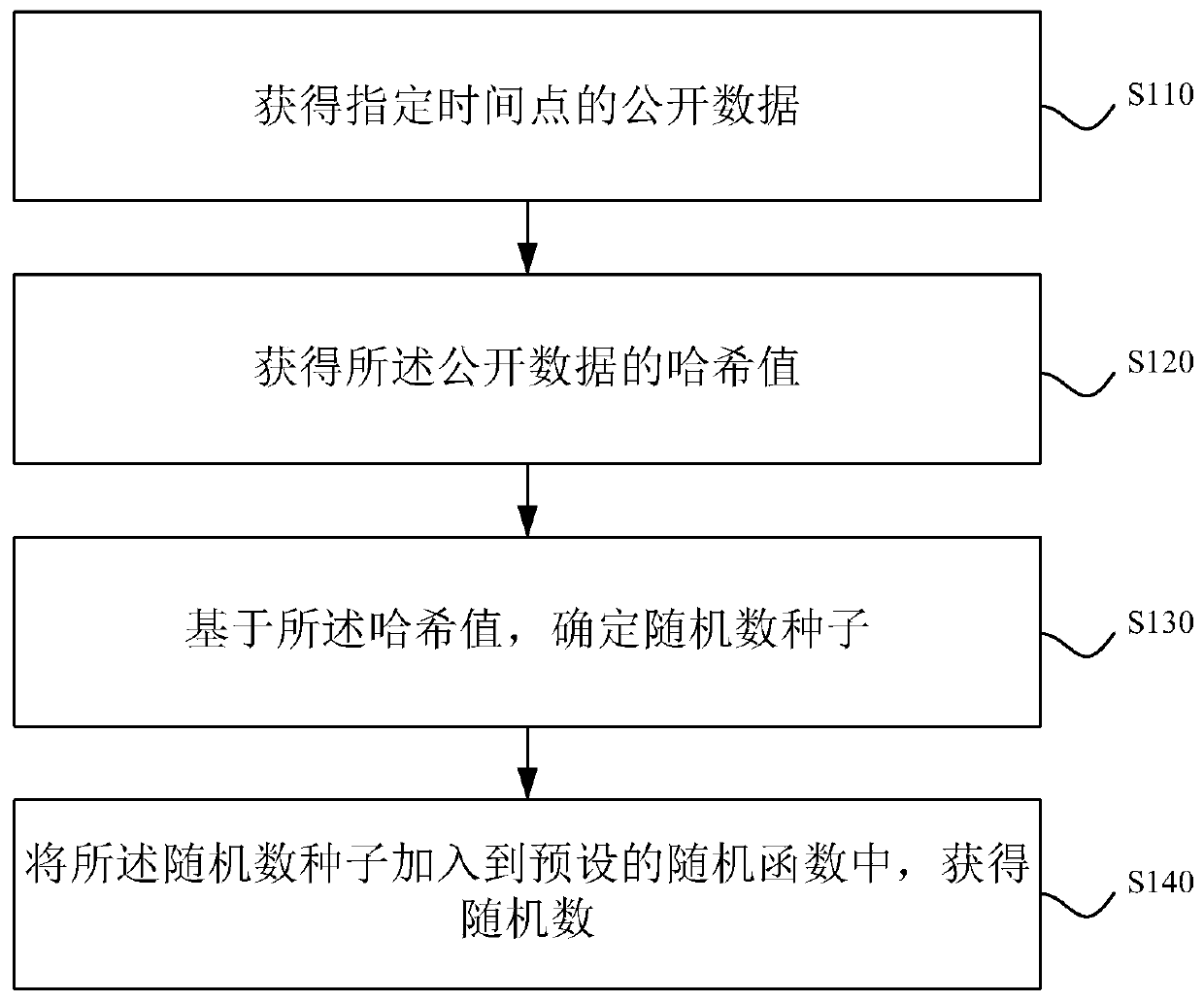
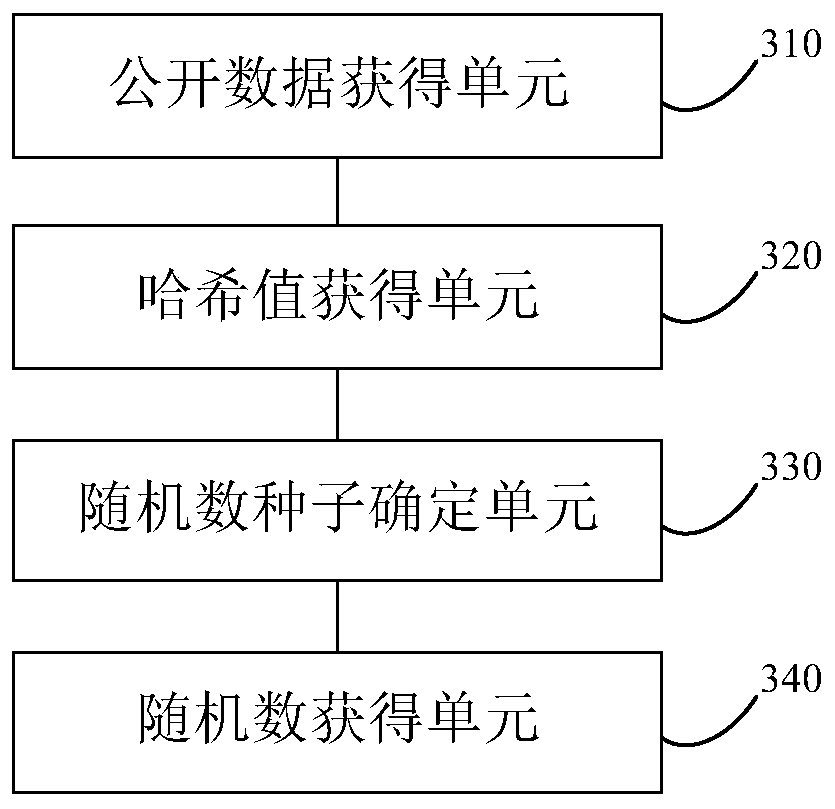
Random number acquisition method, random number acquisition device, random number acquisition system and storage medium
The invention discloses a random number acquisition method. The random number acquisition method includes the steps of acquiring public data at a specified time, wherein the specified time is pre-specified before itself; acquiring the hash value of the public data; based on the hash value, determining a random number seed; adding the random number seed to a preset random function to obtain a random number. The invention also discloses a random number acquisition device, a random number acquisition system and a storage medium. By the random number acquisition method, the public data of the specified time are random with time, and before the specified time, no one can predict the public data at the specified time; the public data of the specified time are subjected to hash calculation to obtain the hash value, and the random number obtained according to the random number seed determined by the hash value is open and fair; after the specified time, all persons can verify the random numberbased on the acquired public data of the specified time.
Owner:SHENZHEN THUNDER NETWORK TECH +1
Processing of data sets in a computer network
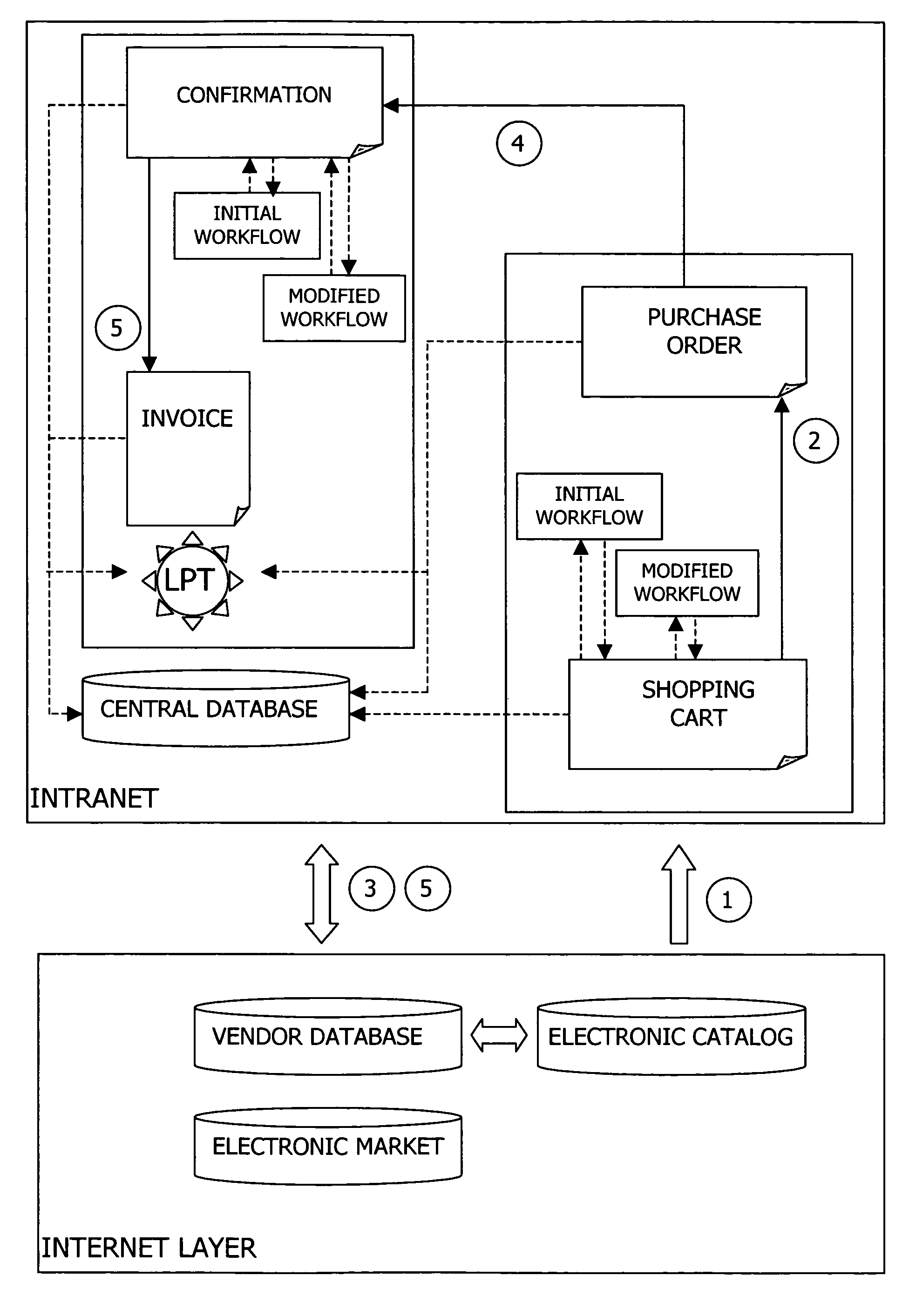
ActiveUS7917467B2Smooth transmissionReduce access latencyFinanceDigital data processing detailsData setResource saving
A system and method for the resource-saving collaborative handling of data sets in a computer network is described. The method comprises the steps of providing a data set having an initial collaborative workflow, determining if the data set satisfies a set of one or more first start conditions to trigger a random function query, providing the data set to a random function if the random function query is triggered, stochastically determining, by the random function, whether or not to assign a modified collaborative workflow to the data set, and replacing the initial workflow with the modified workflow for the data set if the random function determines to assign the modified workflow.
Owner:SAP AG
Real-time video transmission method based on forward error correction encoding window expanding
InactiveCN102710943AImprove error correction performanceAccurate decodingTelevision systemsSelective content distributionGroup of picturesVideo decoding
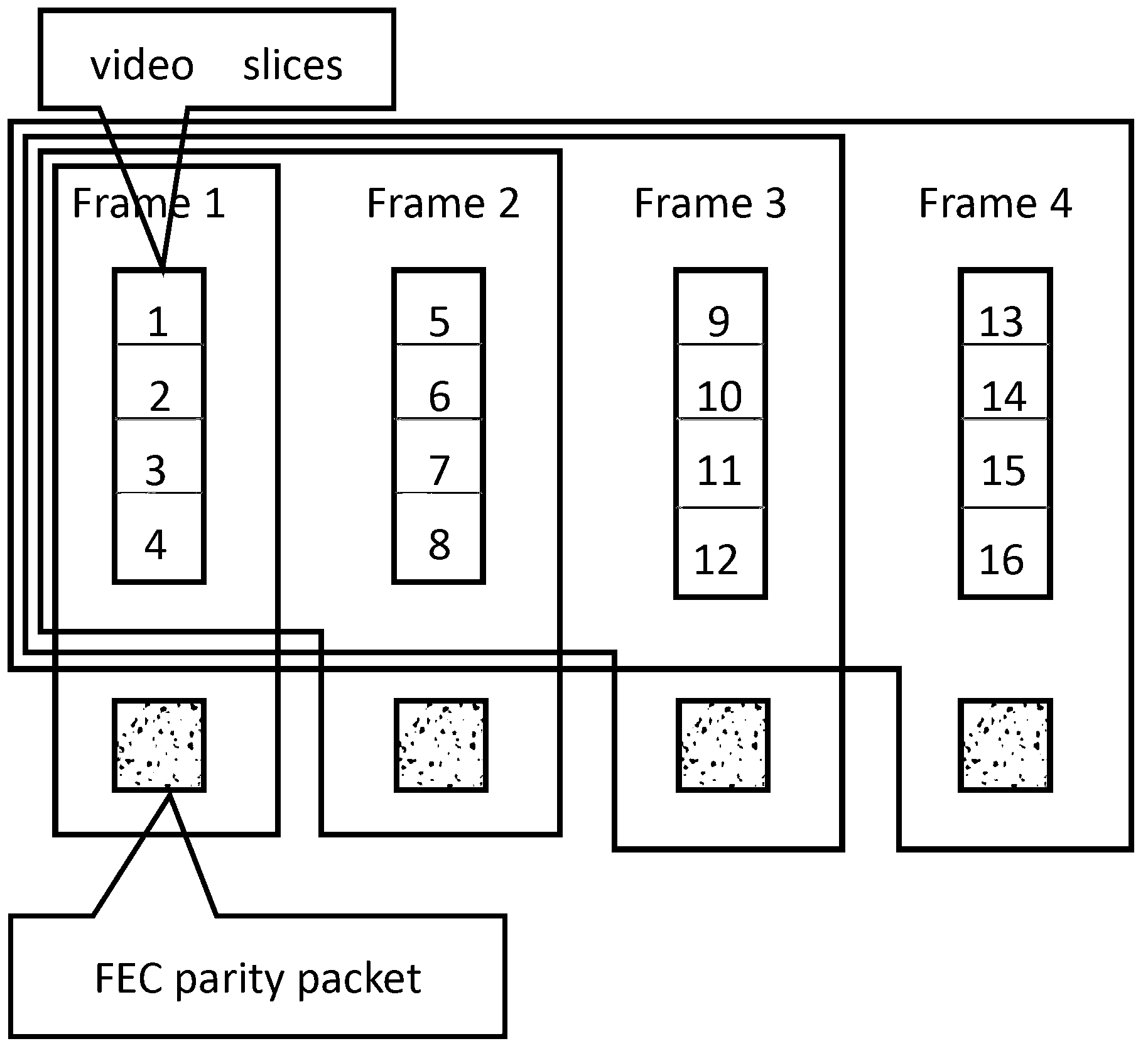
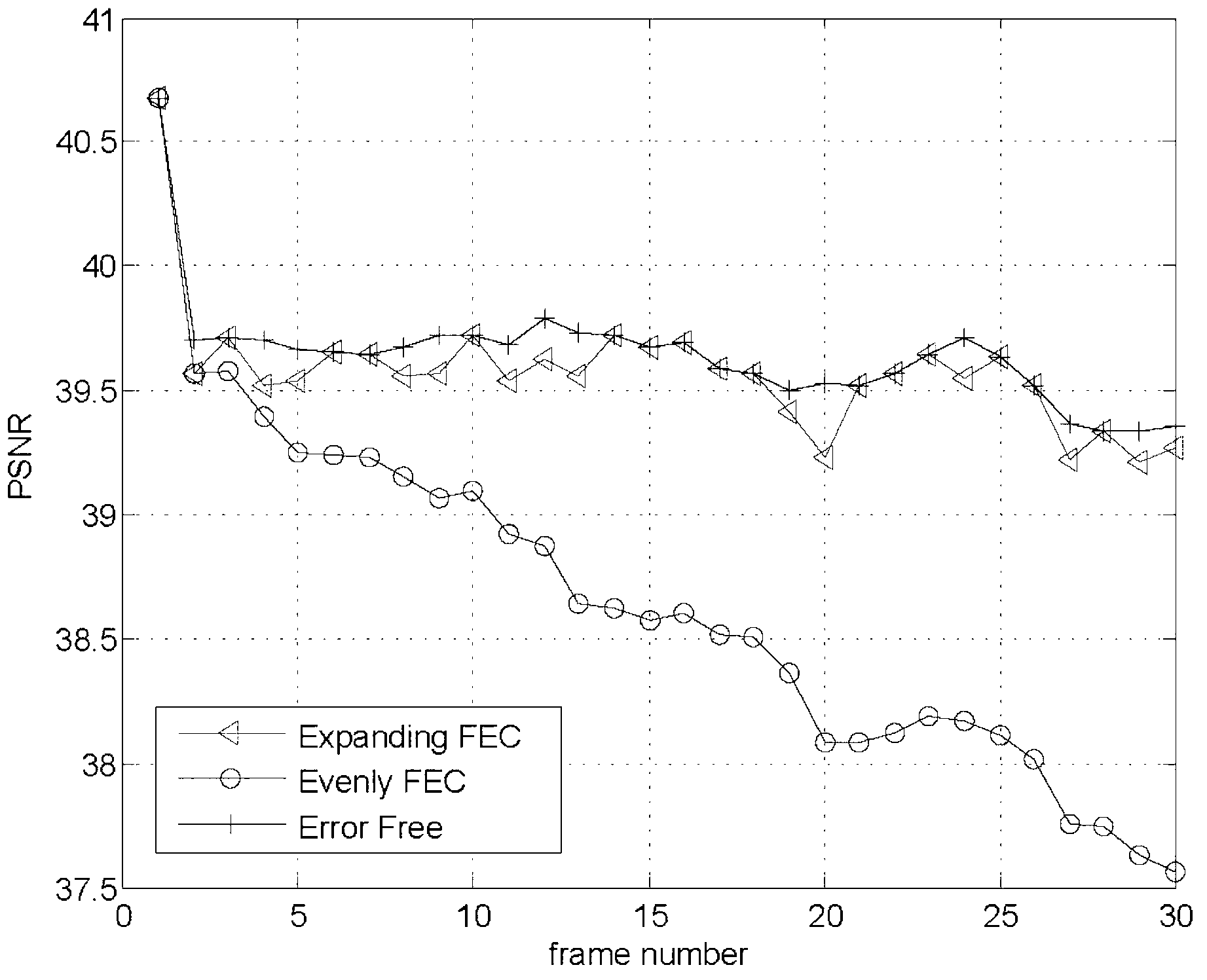
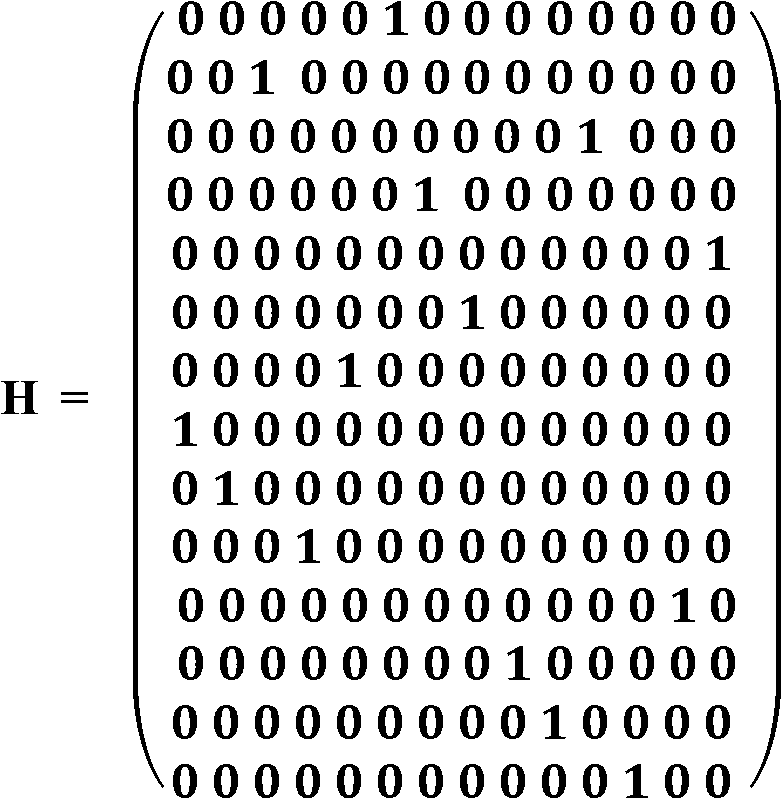
The invention discloses a real-time video transmission method based on forward error correction encoding window expanding. According to the method, video signals are encoded by a forward error correction encoder (FEC). The method has the following characteristics: (1) when encoding current image frame data, the forward error correction encoder uses all video data (including the video data of the current frame) before the current frame in GOP (Group Of Picture) as encoding data to generate check data packet; (2) in order to improve the error correction performance of a system to the maximum degree, the used video data packets are multiplied with a certain transformation matrix before the forward error correction encoding, so that a linear system of equations can be linearly independent at the utmost extent, and the decoding can be conducted correctly furthest; and (3) one of the realization of a transformation matrix is to rearrange the video data packets, and according to the method for rearranging the video data packets, the invention provides a method obtained by a random function, so that different random sequences can be used by different frames, and meanwhile, the extra information needs to inform a video receiving end (a video decoding end).
Owner:罗天明 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com