Homomorphic encryption algorithm based on modulo-like operation
A technology of homomorphic encryption and modular operation, which is applied in the direction of homomorphic encryption communication, digital transmission system, electrical components, etc., can solve the problem of difficulty in ensuring data correctness, continuity of ciphertext, high complexity of fully homomorphic encryption algorithm and difficult practical application, Known problems such as poor resistance to plaintext attacks, to avoid leakage of plaintext information and algorithm structure, avoid consumption of computing resources, and improve execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be specifically introduced below in conjunction with the accompanying drawings and specific embodiments.
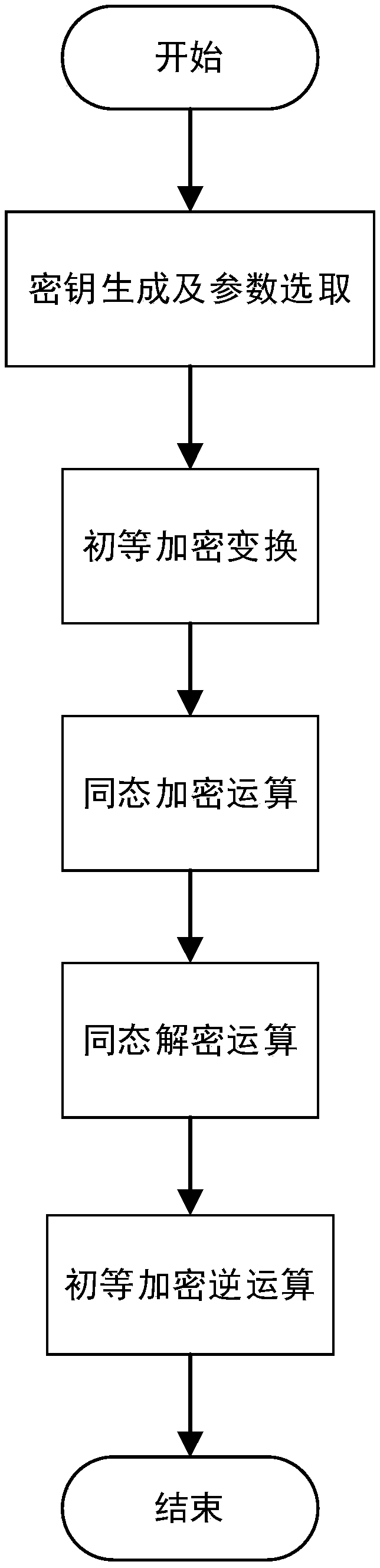
[0018] A homomorphic encryption algorithm based on modular operations, comprising the following steps:
[0019] Step 1, system initialization: generating keys and selecting parameters;
[0020] The specific steps of generating the key are as follows: the trusted third party TTP selects two prime numbers p and q such that |p|≈|q|, discloses their product N=pq, N is the algorithm public key, and p is the algorithm private key.
[0021] The specific steps for selecting parameters are as follows: a 0 and b 0 The encryption parameter selected for the elementary encryption transformation, Range is the fluctuation range of the expected maximum value of the input plaintext, Range≥|X| max ; sign(x) is the positive and negative sign function; [Range-|x|] is the self-interference function.
[0022] Step 2, encryption operation: perform homomorph...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com