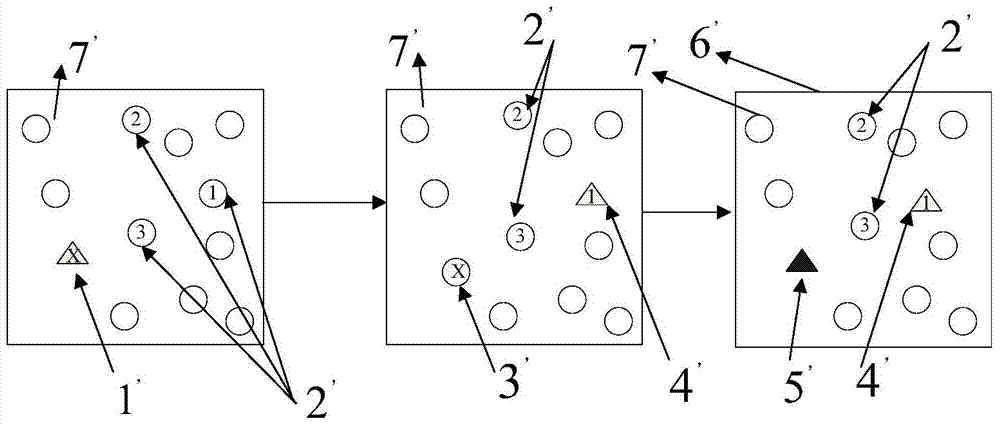
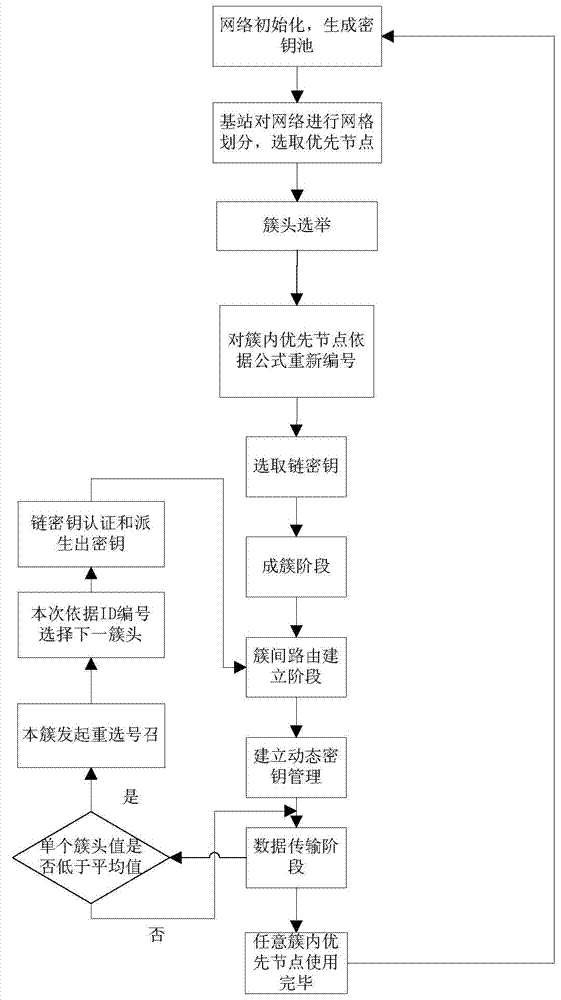
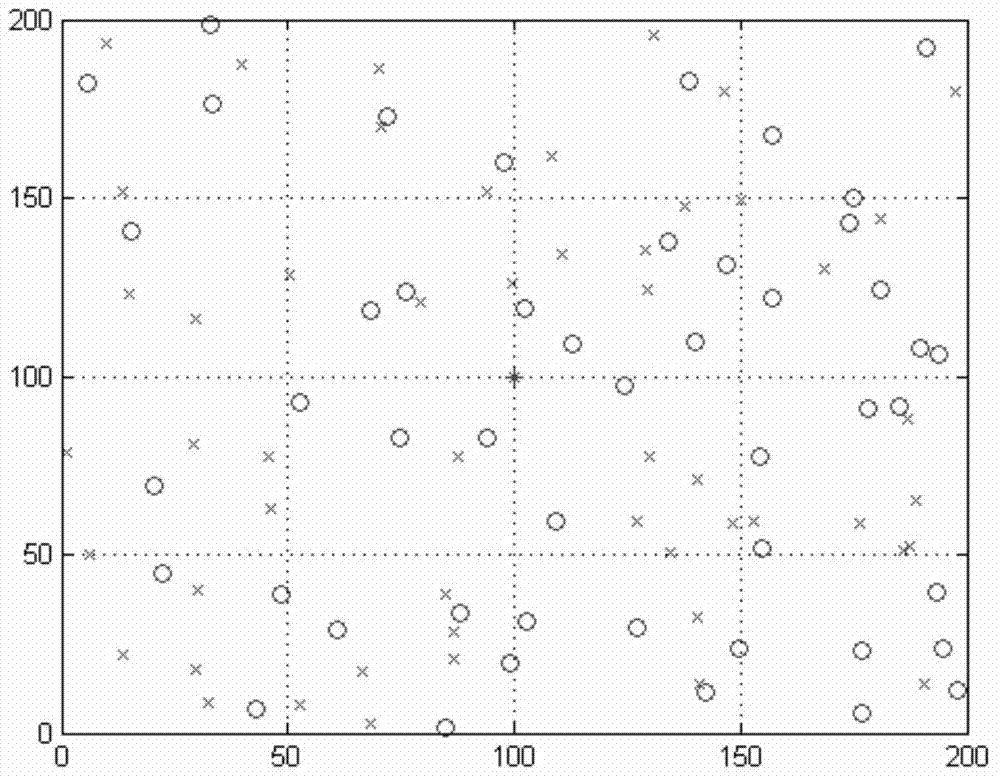
Self-adaptive grid safe routing method in wireless sensor network
An adaptive grid, wireless sensor technology, applied in security devices, network topology, wireless communication and other directions, can solve the problem of not fully adapting to the WSN random topology environment, key distribution scheme without routing protocols combined, etc., to avoid The effect of cluster head reselection, prolonging network survival time, and enhancing correlation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] specific implementation
[0055] The wireless sensor network self-adaptive grid security routing method of the present invention will be introduced in detail below.
[0056] In terms of signal transmission, the present invention adopts a free space model and a multipath fading model. When the distance between the sending node and the receiving node is less than a certain value, the free space model is used, otherwise the multipath fading model is adopted. According to the energy consumption mentioned in the literature The formula, the energy consumed by a node sending out information of size K-bit is:
[0057] E send = k * E elec + k * ξ fs * ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com