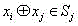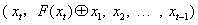Format-reserved encryption algorithm based on multi-segmented Feistel network
A format-preserving encryption and multi-segmentation technology, applied in encryption devices with shift registers/memory, digital transmission systems, electrical components, etc., can solve problems such as data being unable to be stored, corrupting data formats, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
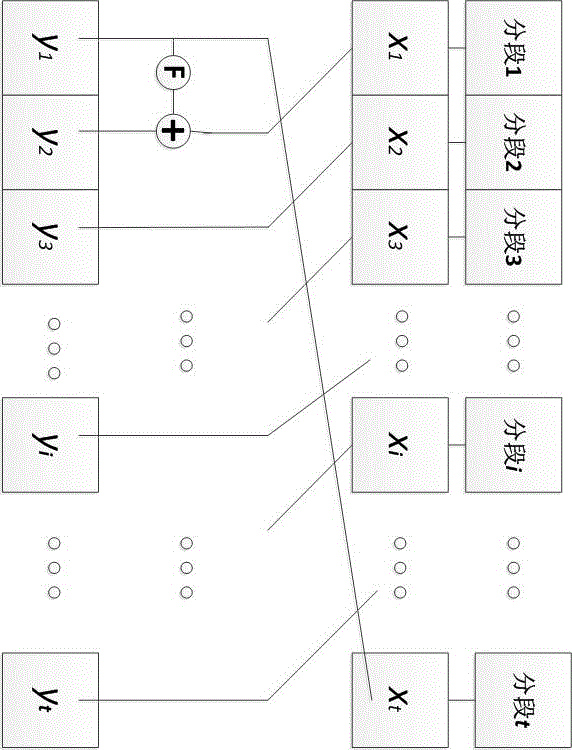
[0040] The format-preserving encryption algorithm based on the multi-segmented Feistel network of the present invention comprises the following steps:
[0041] 1. Divide a sensitive plaintext information, according to its given format, into t data segment. That is, the plaintext space S According to its own format, it is divided into t part: S 1 , S 2 , … ,S t . so, S It can be expressed as:
[0042]
[0043] Among them, if the collection S i is of size n i , then further S Expressed as:
[0044]
[0045] 2. OK t Number of rounds to split the Feistel network r , and the keys used in each round of the function
[0046] ,
[0047] The number of rounds r for t even multiples of
[0048] 3. use Represents a legitimate sensitive data where: x 1 ∈ S 1 ,x 2 ∈ S 2 ,… ,xt ∈ S t ; that is, respectively x 1 , x 2 , … ,x n as t Split the first round of the Feistel network t input.
[0049] 4. Execute the round operation of r rounds: i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com