Efficient searchable proxy privacy set intersection method and device
A collection and privacy technology, applied in the field of network security, can solve the problems of huge computing power and high communication complexity, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Embodiments of the present application are described in detail below, examples of which are shown in the drawings, wherein the same or similar reference numerals denote the same or similar elements or elements having the same or similar functions throughout. The embodiments described below by referring to the figures are exemplary, and are intended to explain the present application, and should not be construed as limiting the present application.
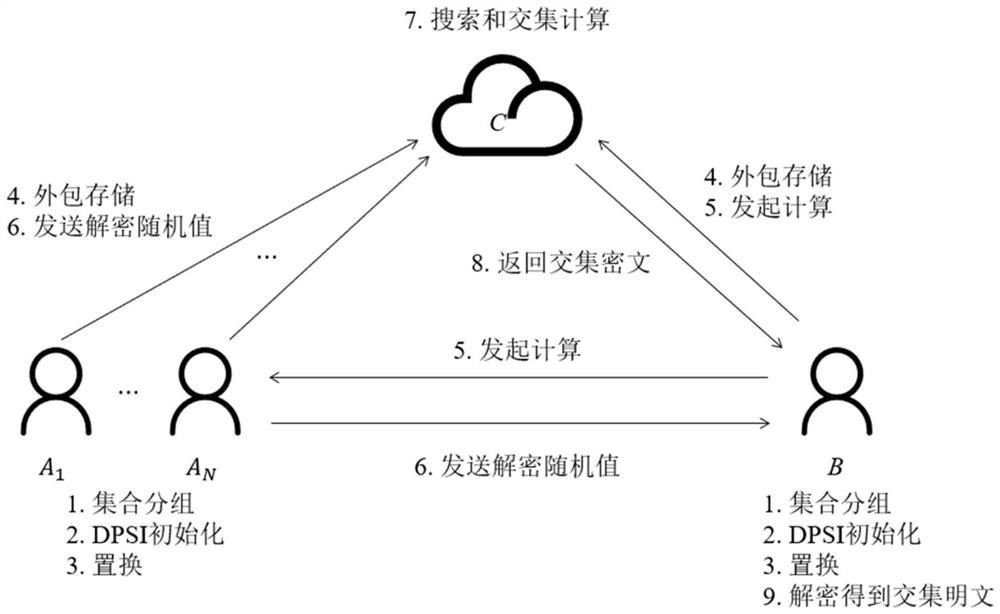
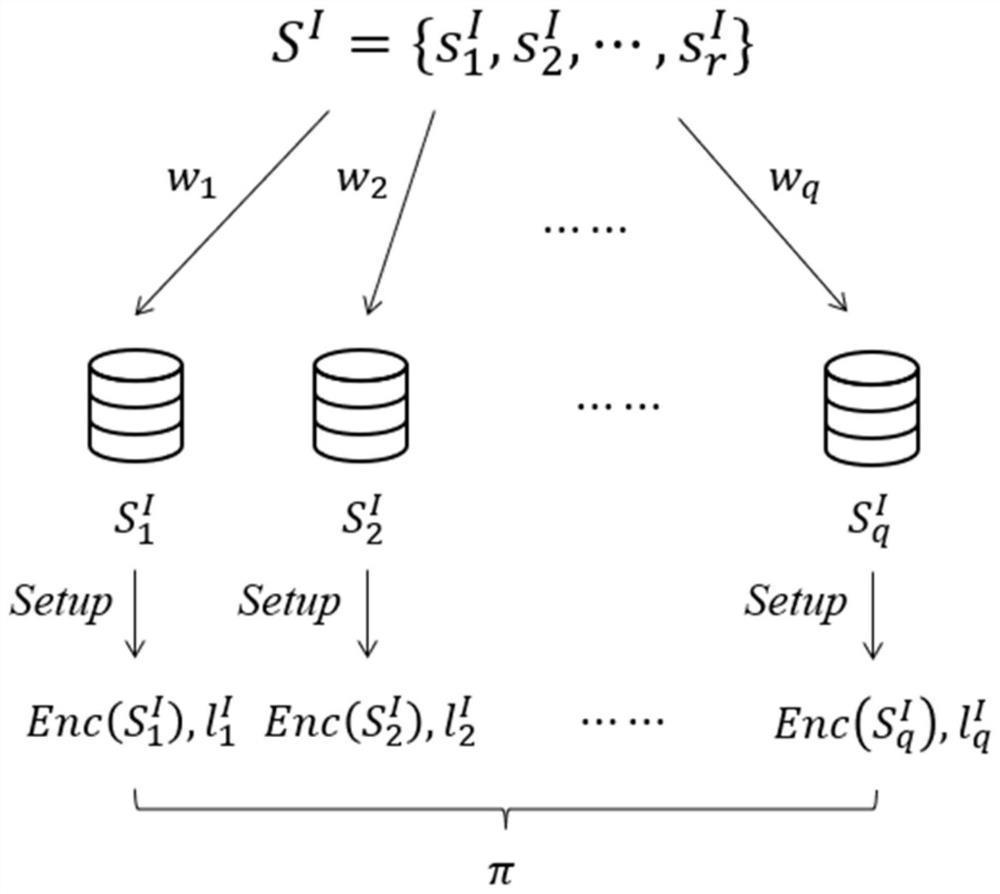
[0032] In the related technology, the user first needs to submit a search request to the cloud server, and the cloud server returns the result to the user after searching, and then the user decrypts the result, and then calculates the proxy PSI. This method has high communication complexity, and each calculation requires the user to decrypt and process the data of the proxy PSI, which consumes huge computing power. If the data can be processed well at the beginning, so that the encrypted data can not only be used for ciphert...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com