Message authentication code pre-computation with applications to secure memory
A message authentication code and message authentication technology are applied in the application field of pre-computed authentication codes in secure memory, and can solve the problem of not providing pre-computation and the like
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
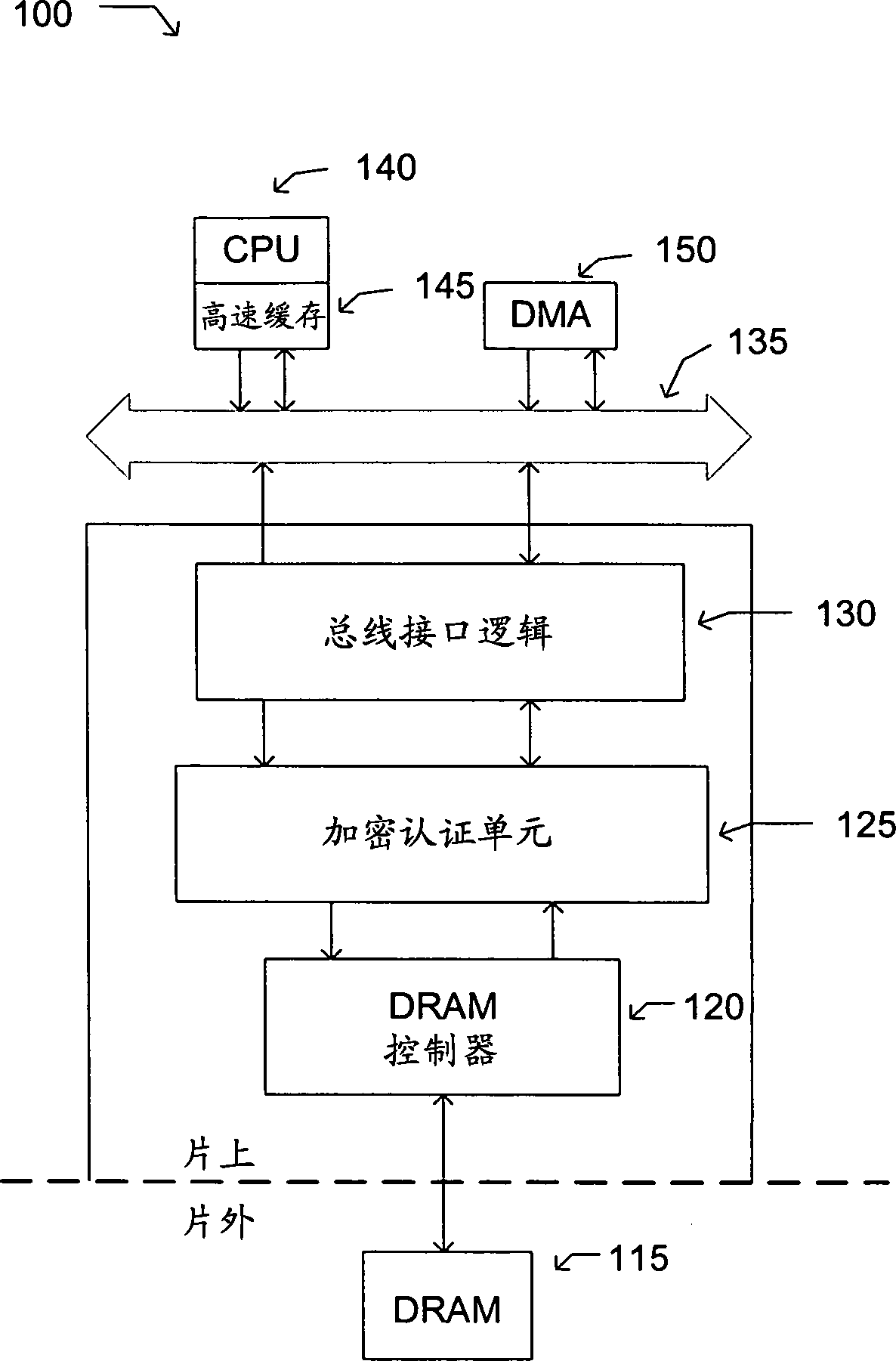
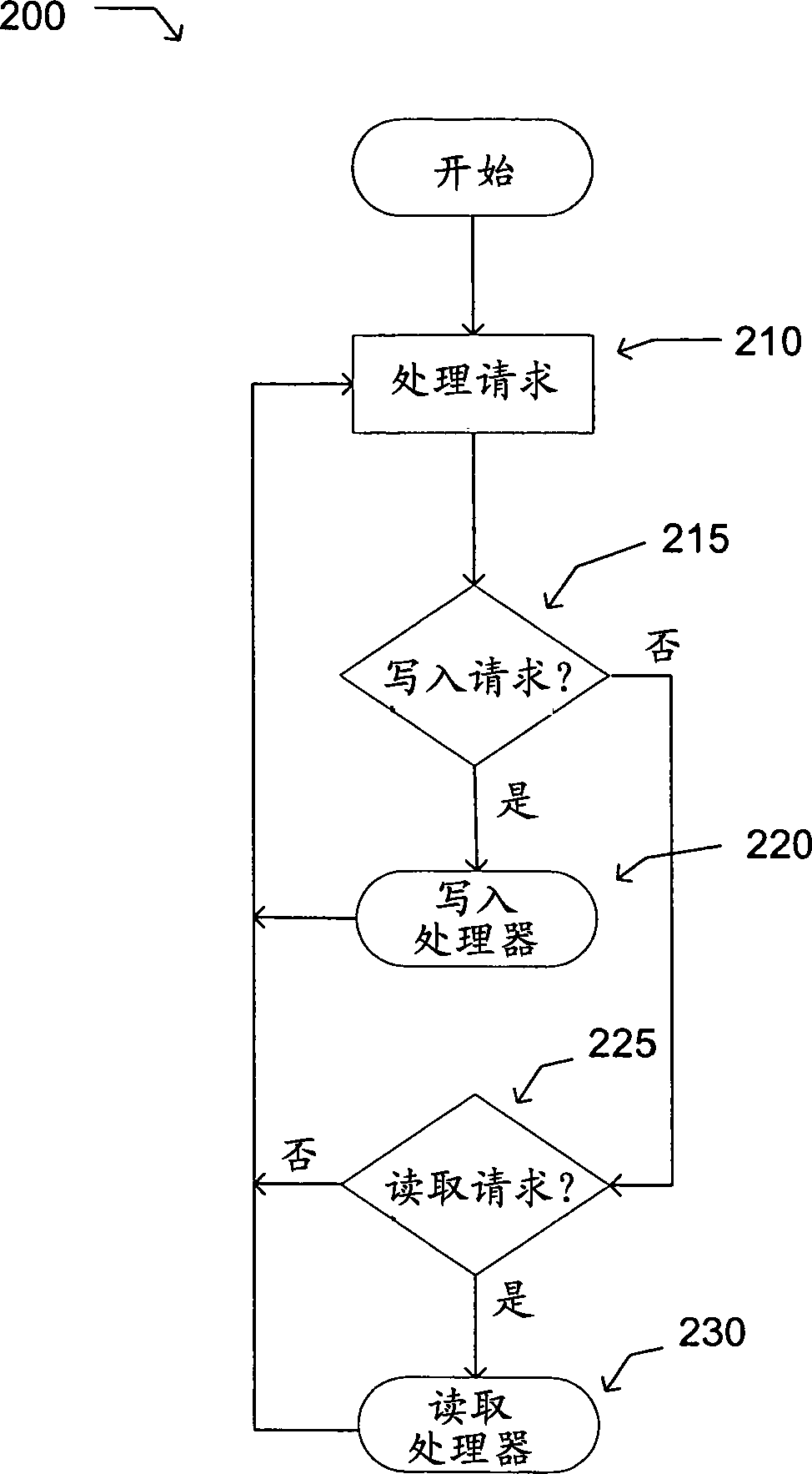
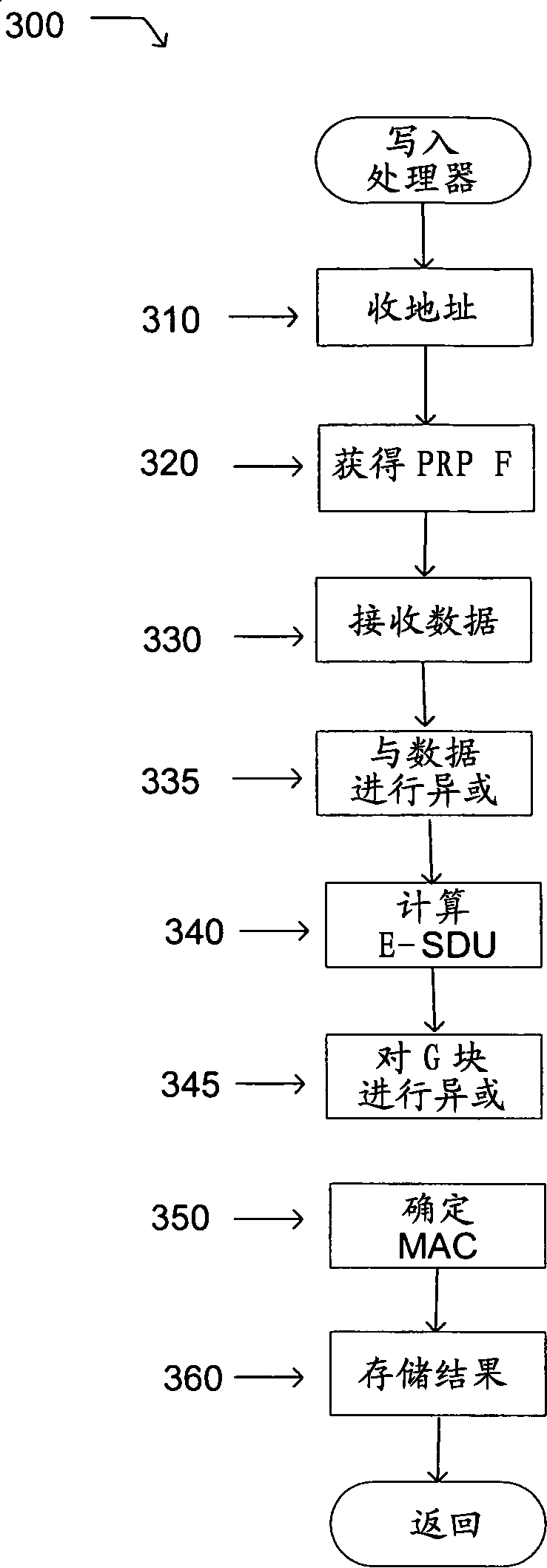
[0016] As discussed, the vulnerable area of computer security is off-chip memory. An adversary can alter or replay information contained in off-chip memory to compromise a computer system. One way to limit adversaries is to sign and encrypt off-chip memory. Computing the signature on memory may require generating a message authentication code (MAC). A MAC algorithm can be run with a secret key and a block of data or memory as input. The MAC algorithm can output a signature or a MAC. MAC can be a numeric value. MAC can be 16 bits or 32 bits. However, MAC can be larger or smaller. The first MAC is calculated using data written to the off-chip memory. The first MAC is stored along with the data. When data is read from the off-chip memory, a second MAC is generated from the read data. If the first MAC does not match the second MAC, the system can reset and / or discard the data.
[0017] turn to figure 1 , figure 1 is an example block diagram of a system 100 in which ap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com