Method and device for generating symmetric block ciphers
A block cipher, symmetric technology, applied to the public key and key distribution of secure communication, can solve the problems of high cost and large chip area, achieve high cost performance, realize the effect of area and speed, and reduce the area
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
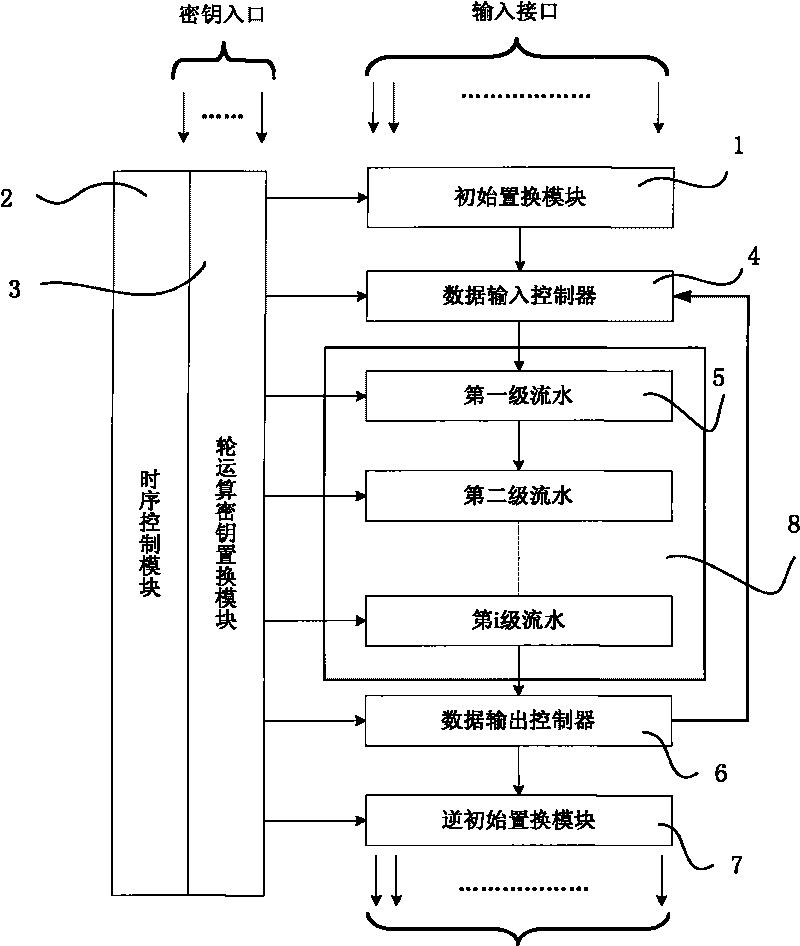
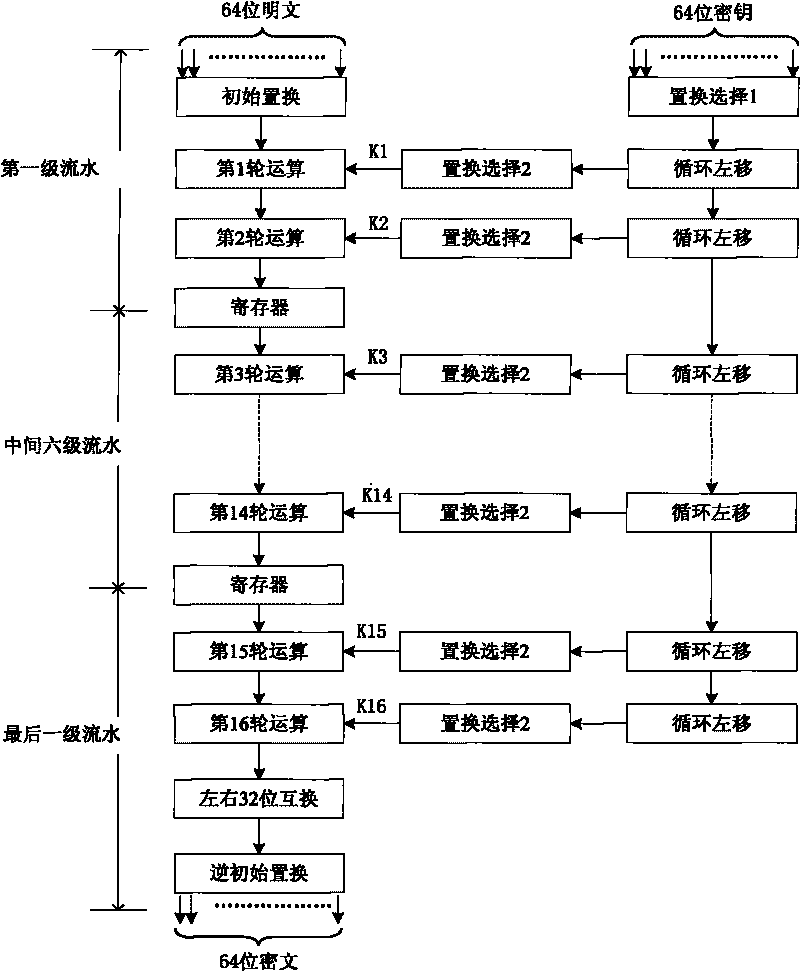
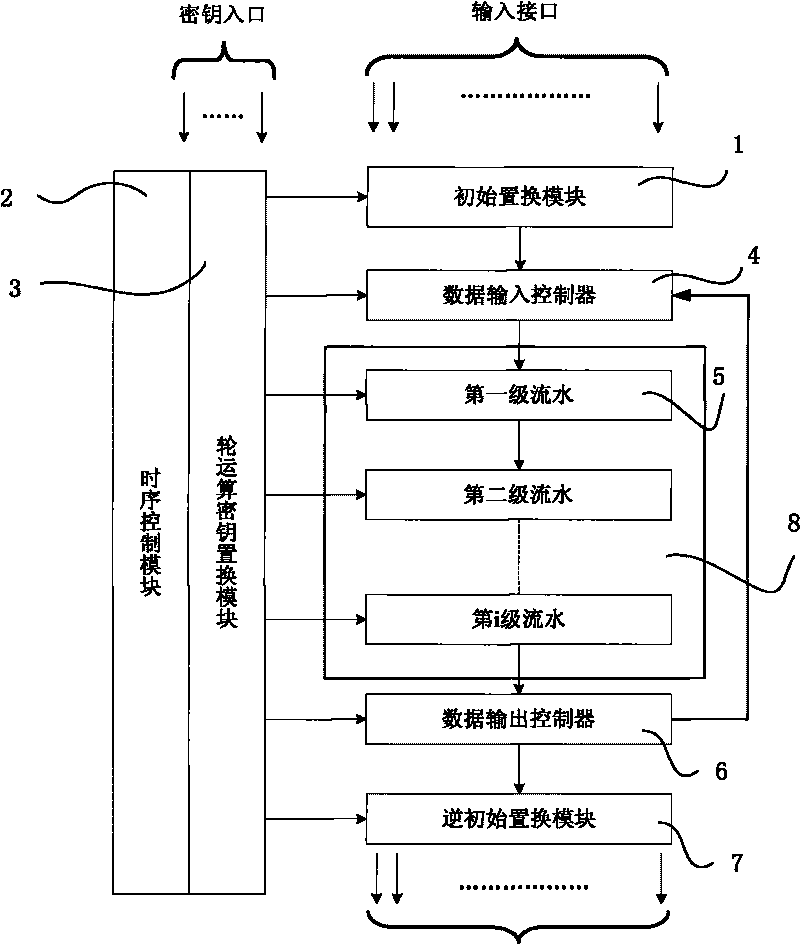
[0032] Such as figure 1 , figure 2 The device for generating a symmetric block cipher as shown is particularly characterized in that it at least includes an initial replacement module 1, a timing control module 2, a round operation key replacement module 3, a data input controller 4, a data output controller 6, an inverse initial Replacement module 1 and a pipeline composed of several stages of pipeline modules.
[0033] Specifically, the timing control module 2 is the core of the device, and it controls the round operation key replacement module 3 to replace the round key needed for the round operation; meanwhile, its output port is also connected with the initial replacement module 1, data input control The controller 4, the data output controller 6, and the control input port of the inverse initial replacement module 7 are connected to control the flow direction of data, coordinate the function operation of each level of data in the pipeline, and make the data complete th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com