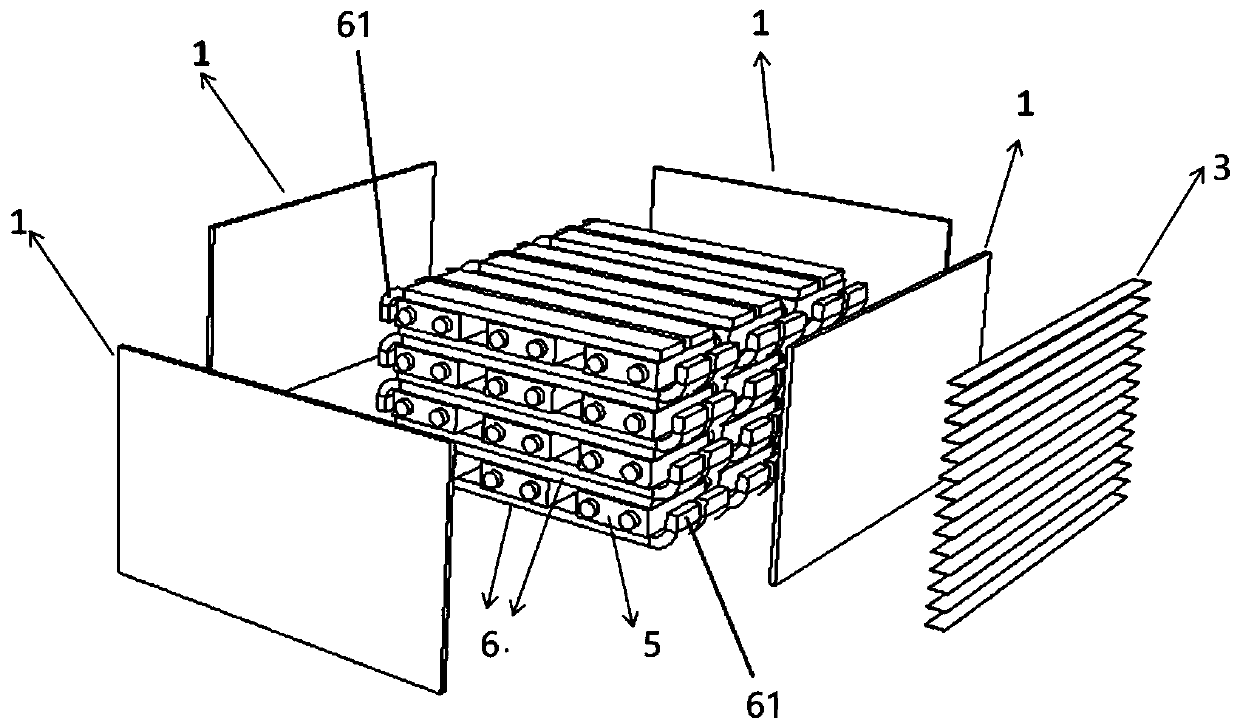
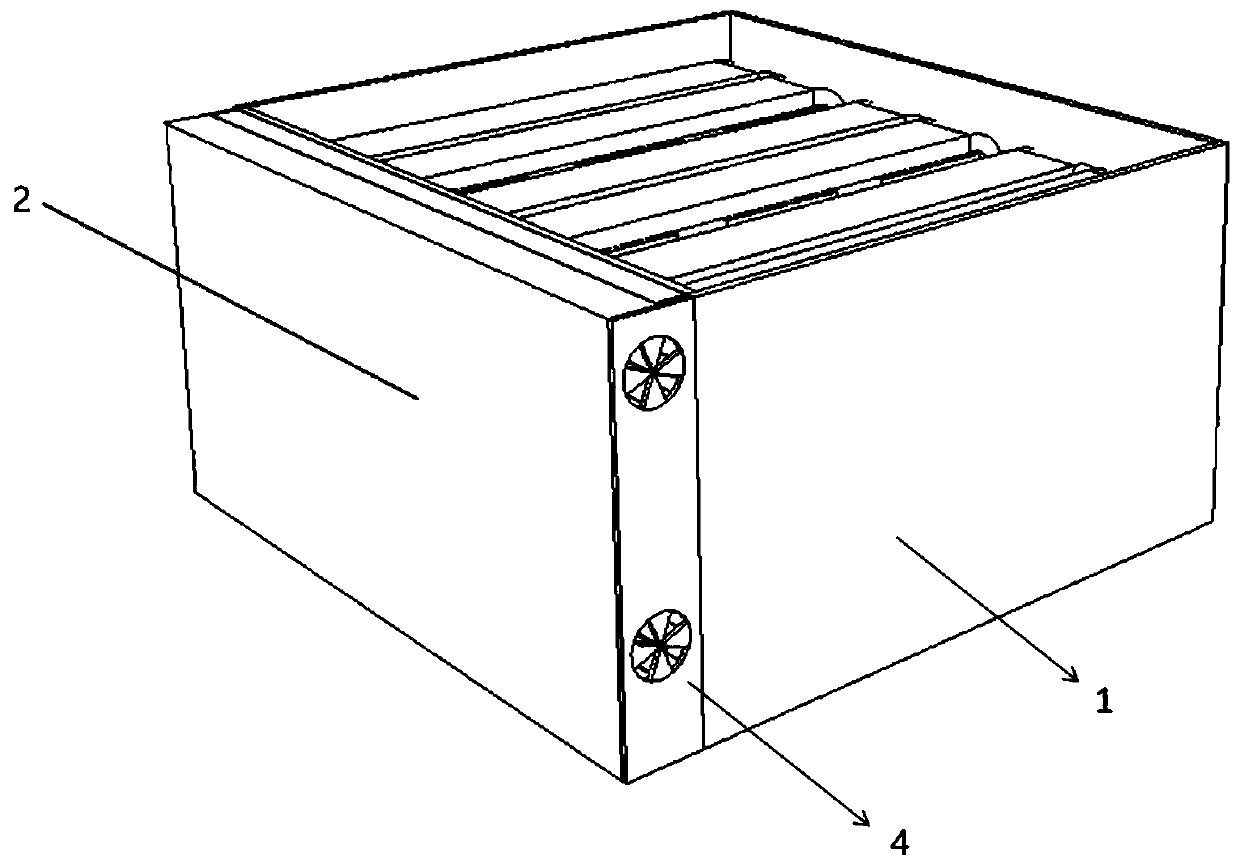
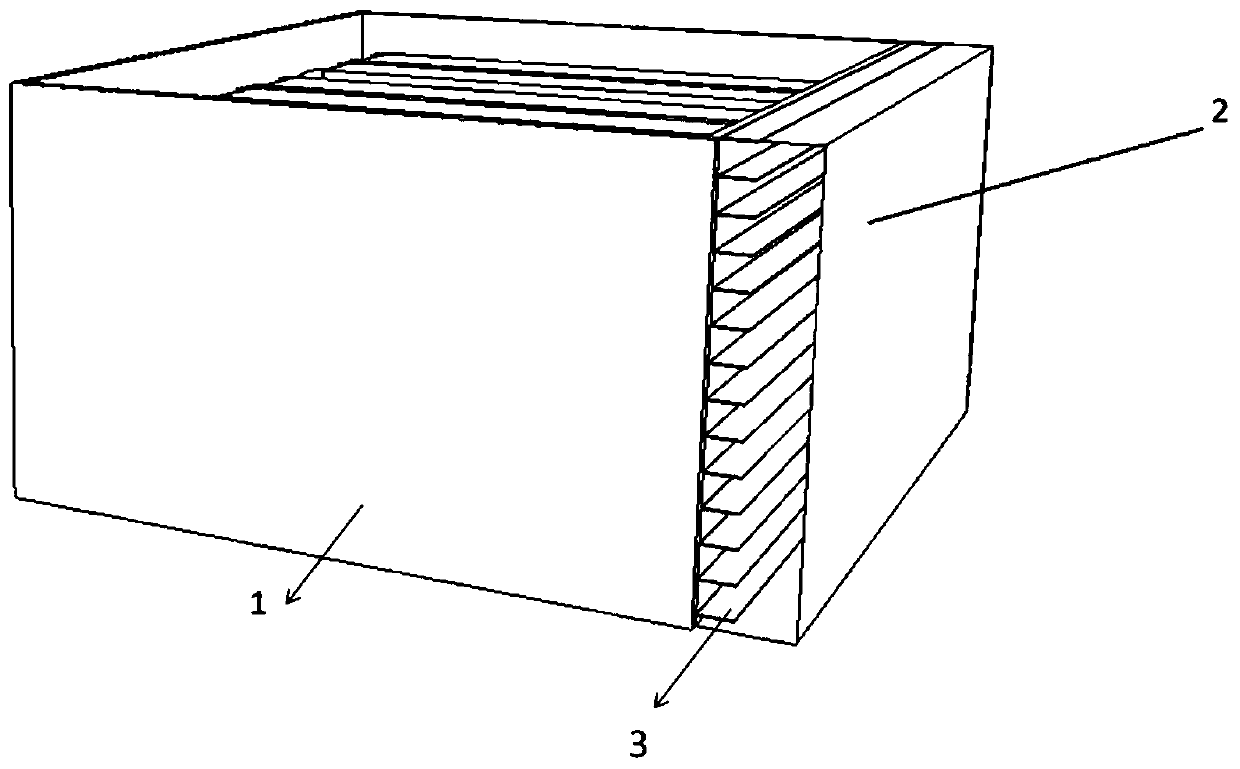
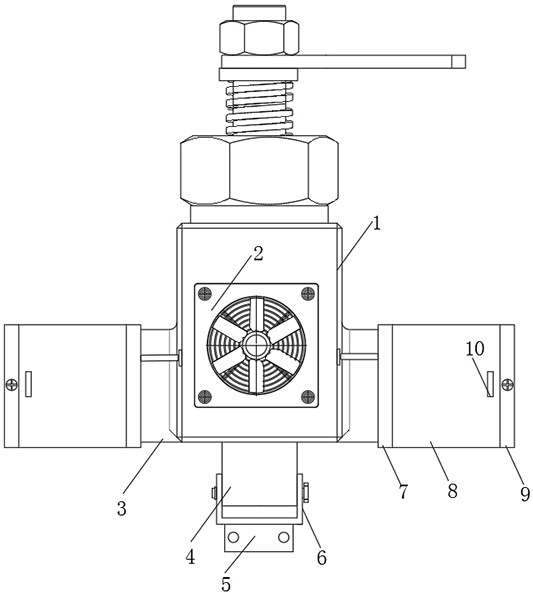
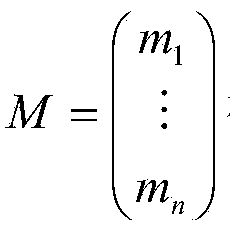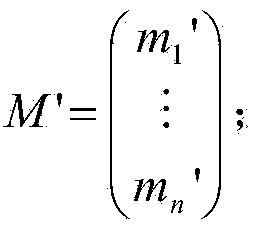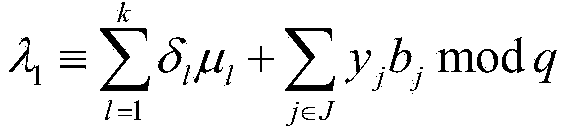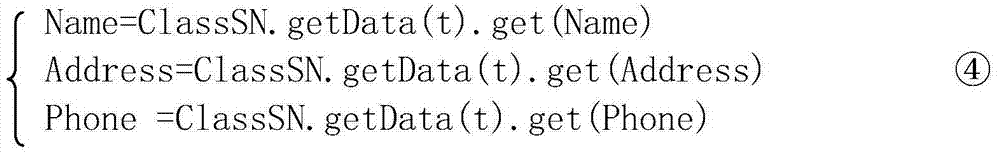Patents
Literature
48results about How to "Leak will not" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
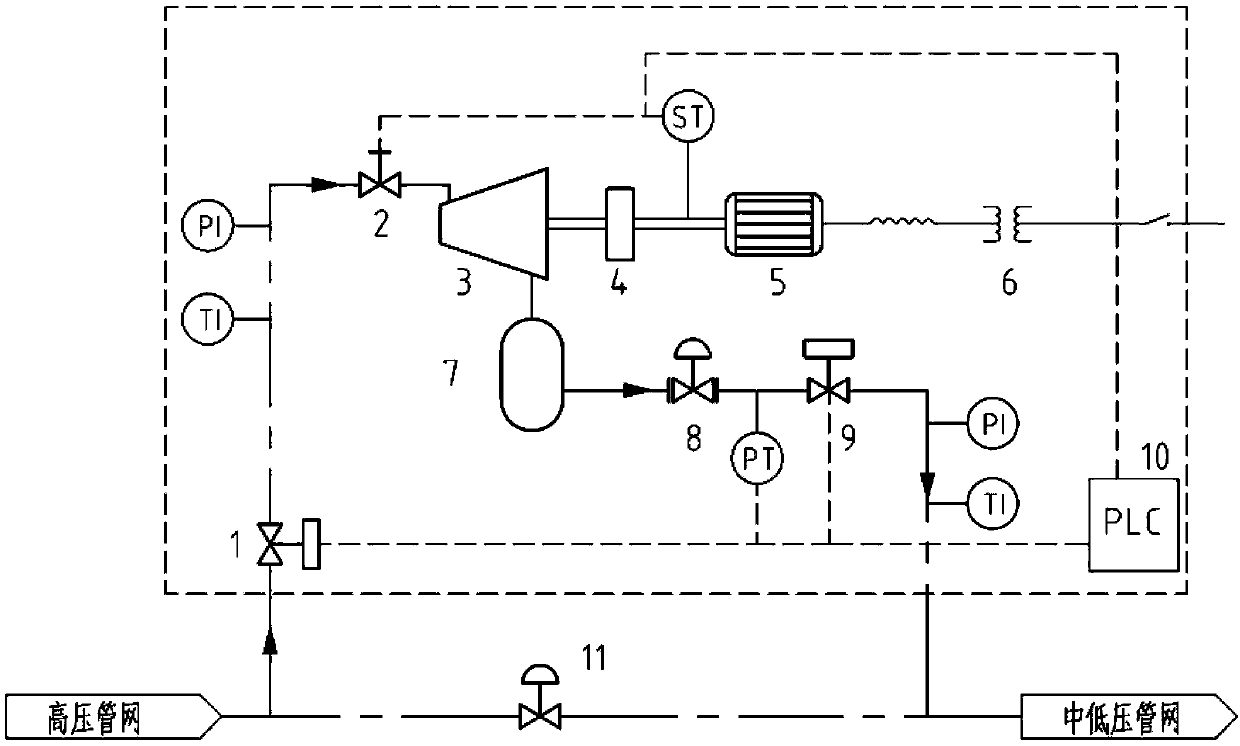
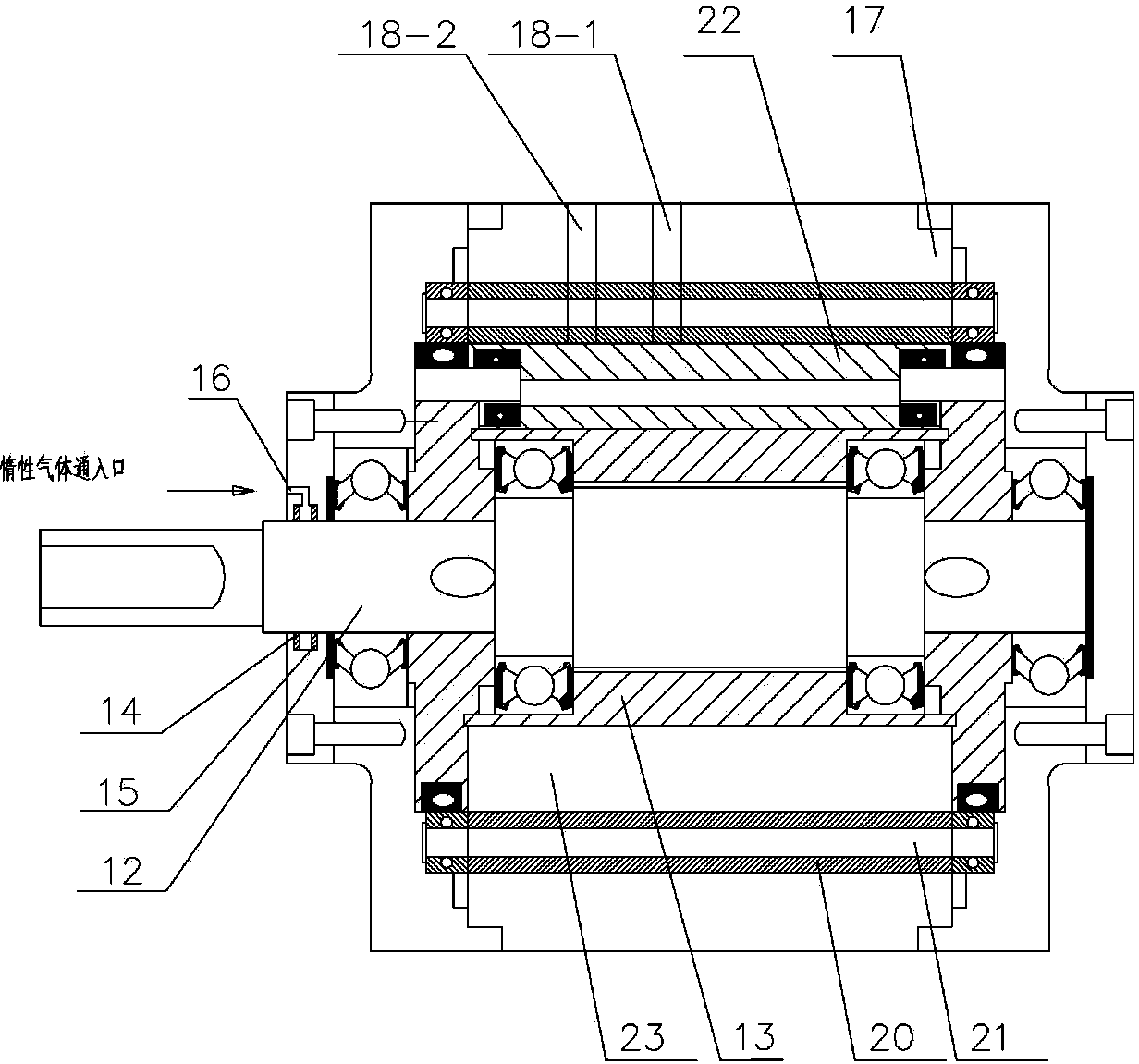
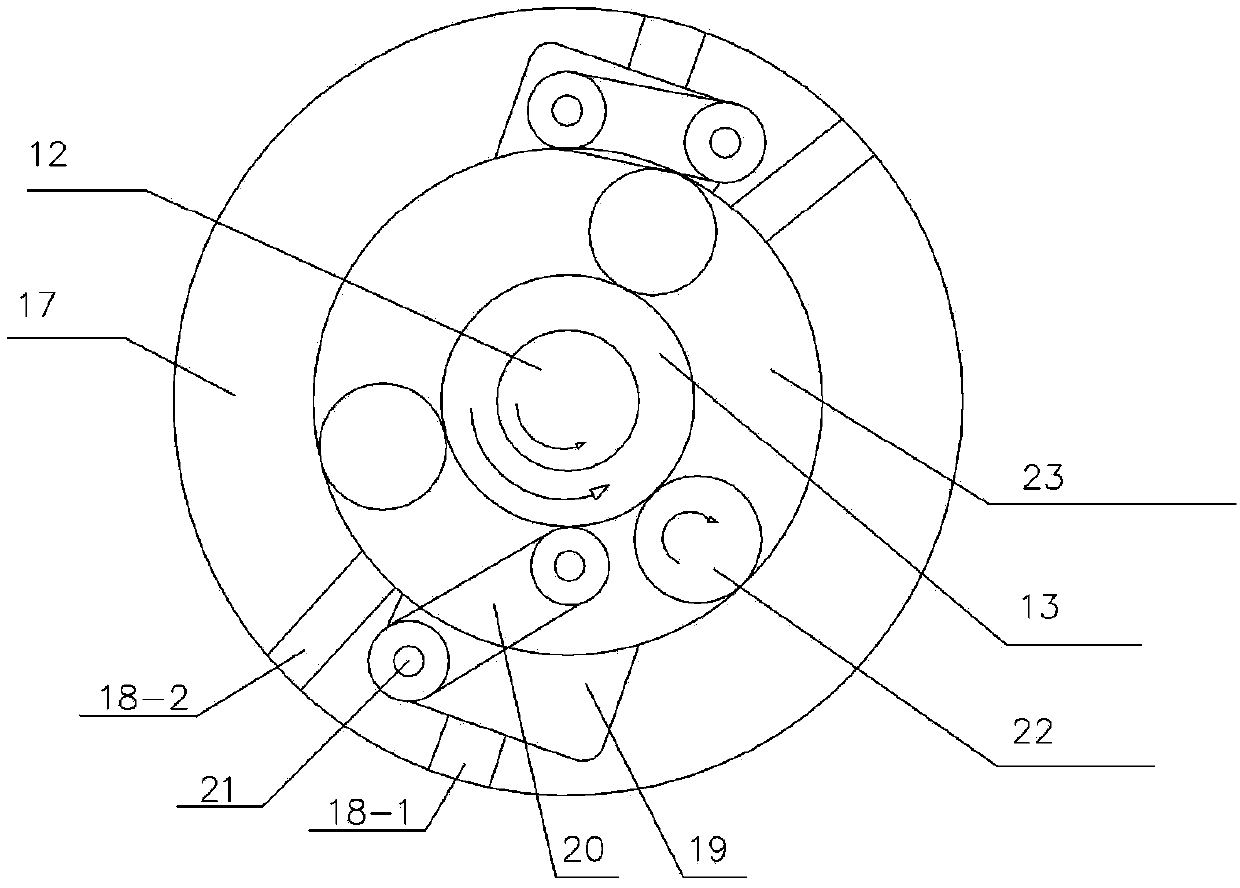
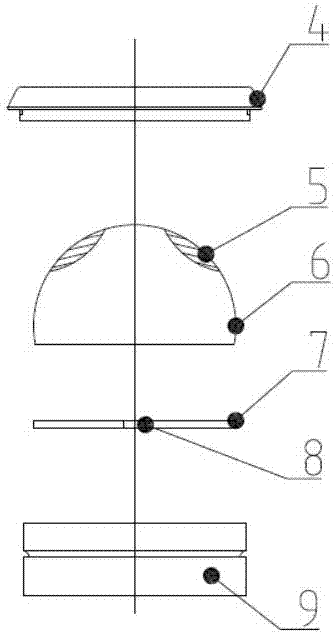
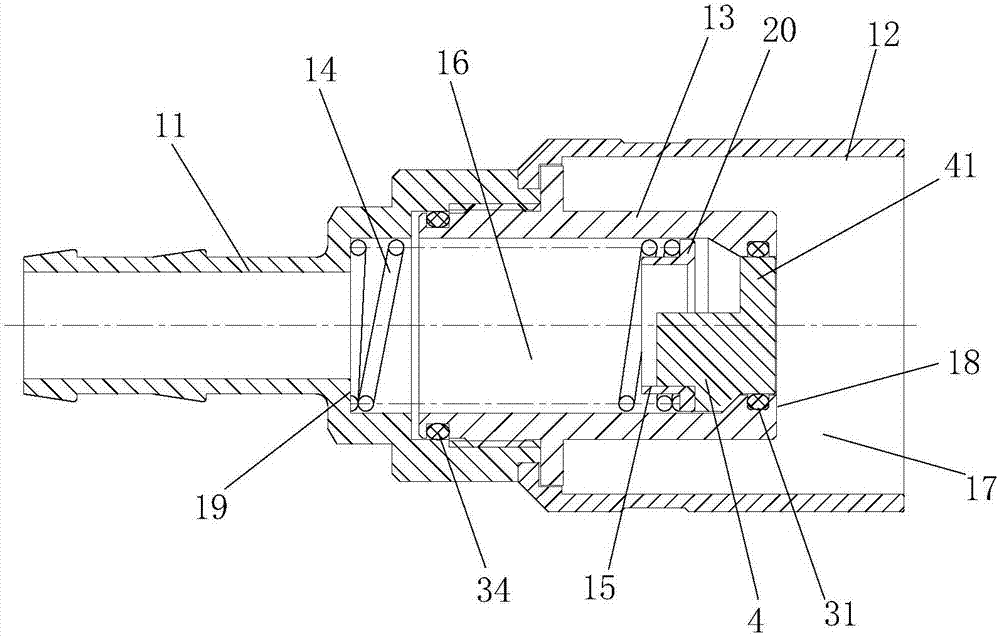
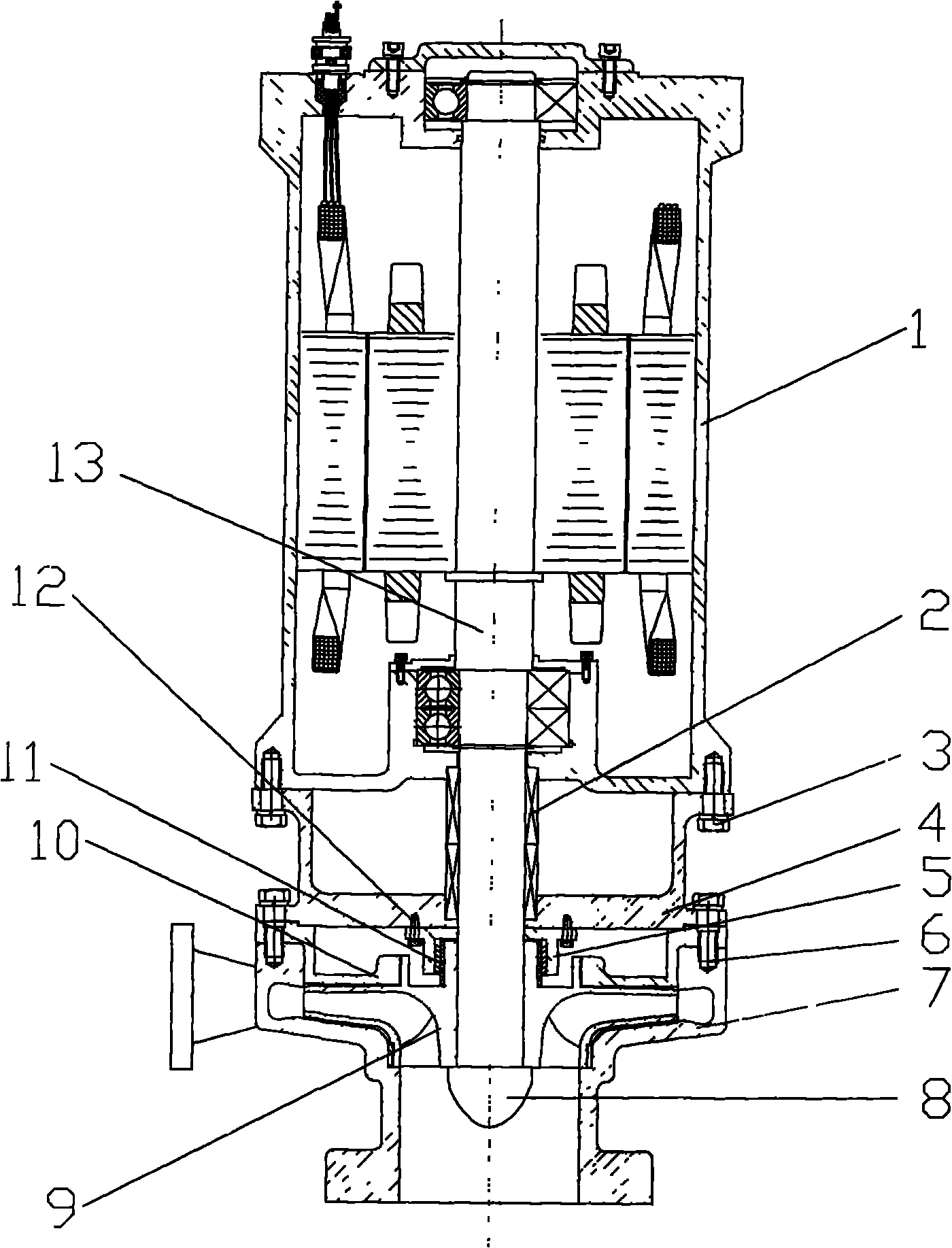
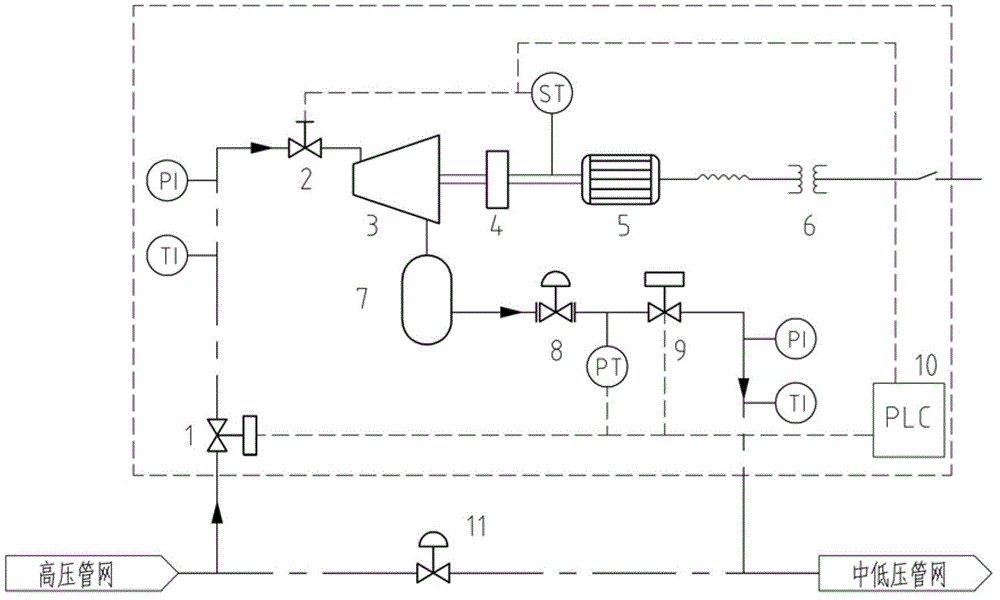
Process and device for generating power by pressure energy of small natural gas pipeline network
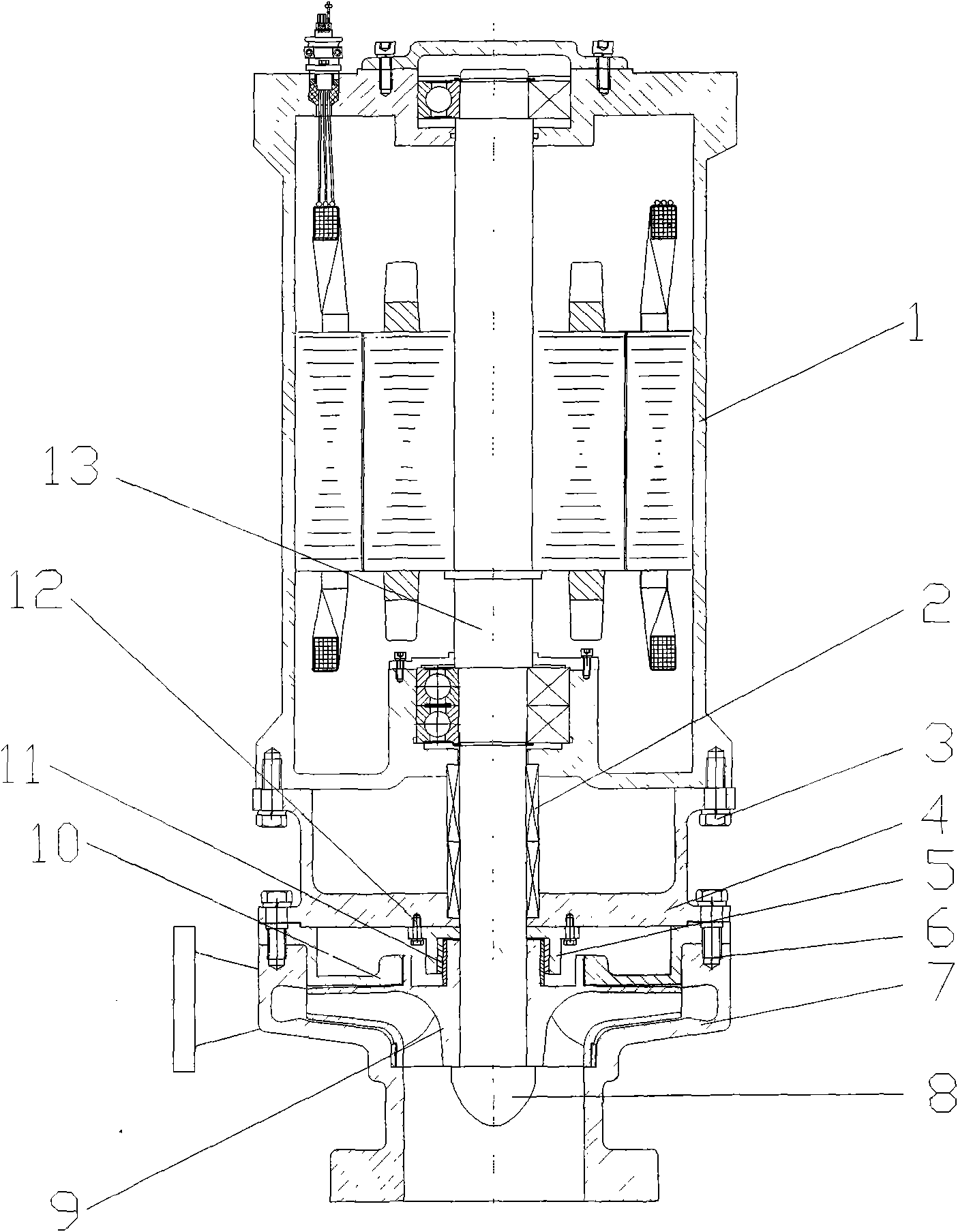
InactiveCN103422899ALeak will notSolve the problem that cannot be explosion-proofSealing arrangements for enginesMachines/enginesGas cylinderPower user
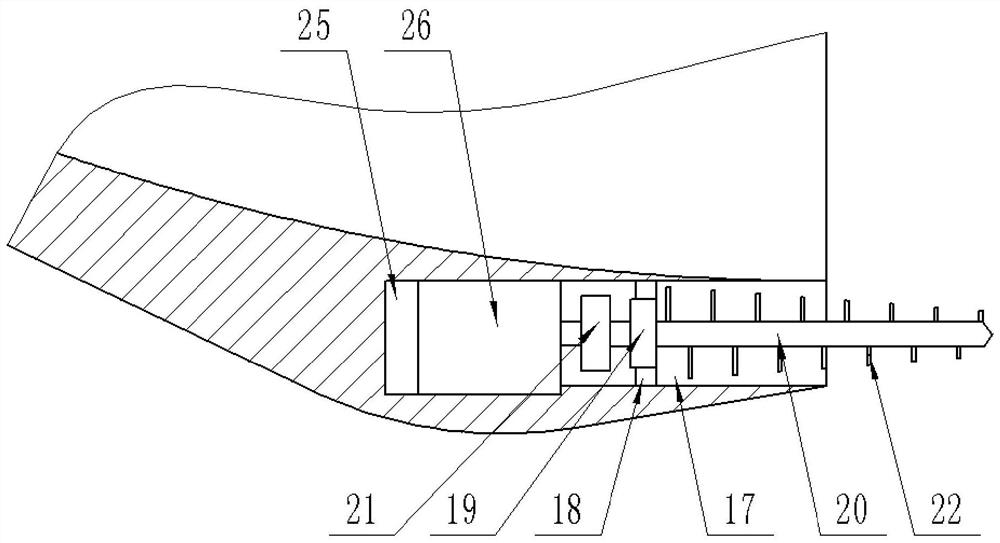
The invention discloses a process and a device for generating power by pressure energy of a small natural gas pipeline network. A high-pressure pipeline network of the device is connected with a gas inlet of an expansion machine through a pipeline; a gas outlet of the expansion machine is connected with a gas inlet of a temperature balancer through a pipeline; an outlet of the temperature balancer is connected with a low and medium-pressure gas pipeline network through a pipeline; a main shaft of the expansion machine is connected with a gearbox; the gearbox is connected with a power generator; the power generator is connected with a transformer synchronizer; the expansion machine adopts an improved AT15-65 type gas expansion machine; one end of the main shaft is connected with an air cylinder in a totally-closed way; a first seal ring and a second seal ring, which have sealing effects, are arranged between the other end of the main shaft and a wheel drum; a flow guide pipe is arranged in a closed cavity between the two seal rings; the flow guide pipe is connected with an inert gas bottle. The device can be used for continuously and stably providing a 220 V / 380 V stable power supply for an interruptible and closed 1-5 kW low-power user.
Owner:SOUTH CHINA UNIV OF TECH +1
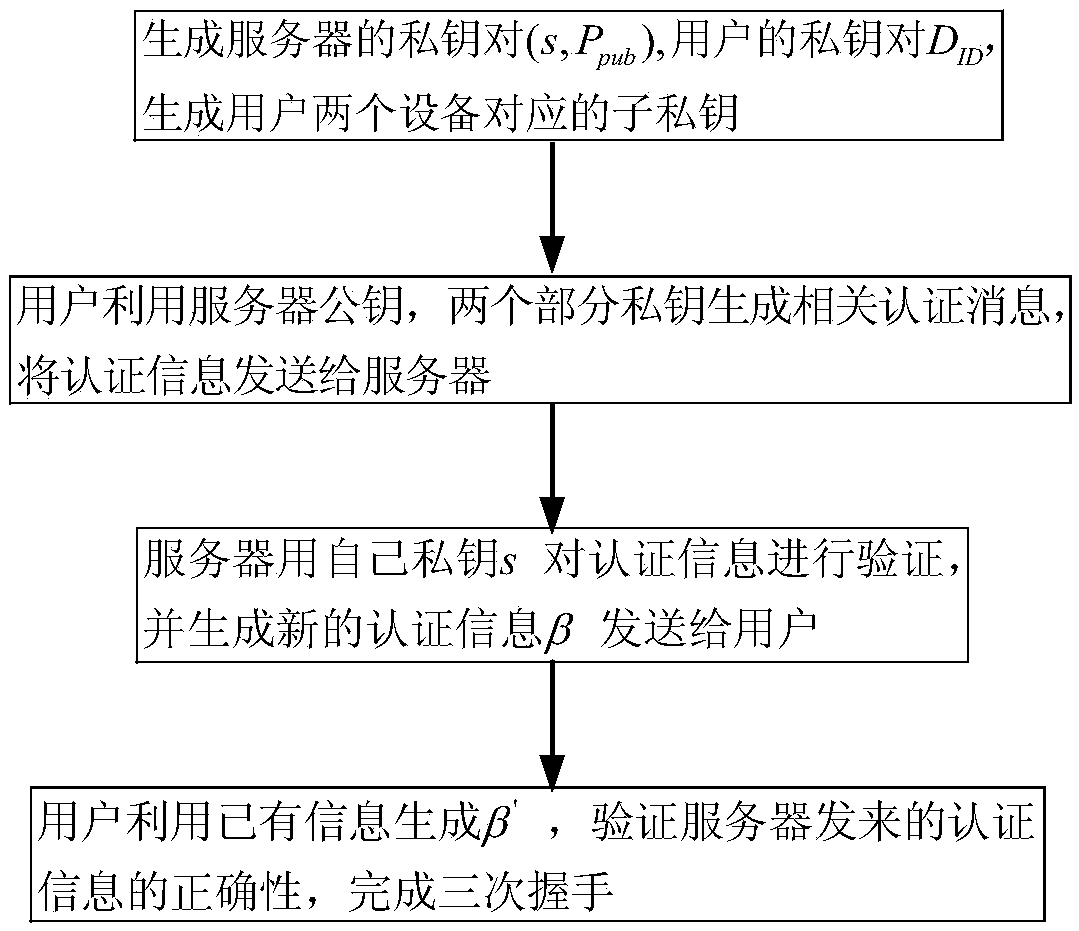
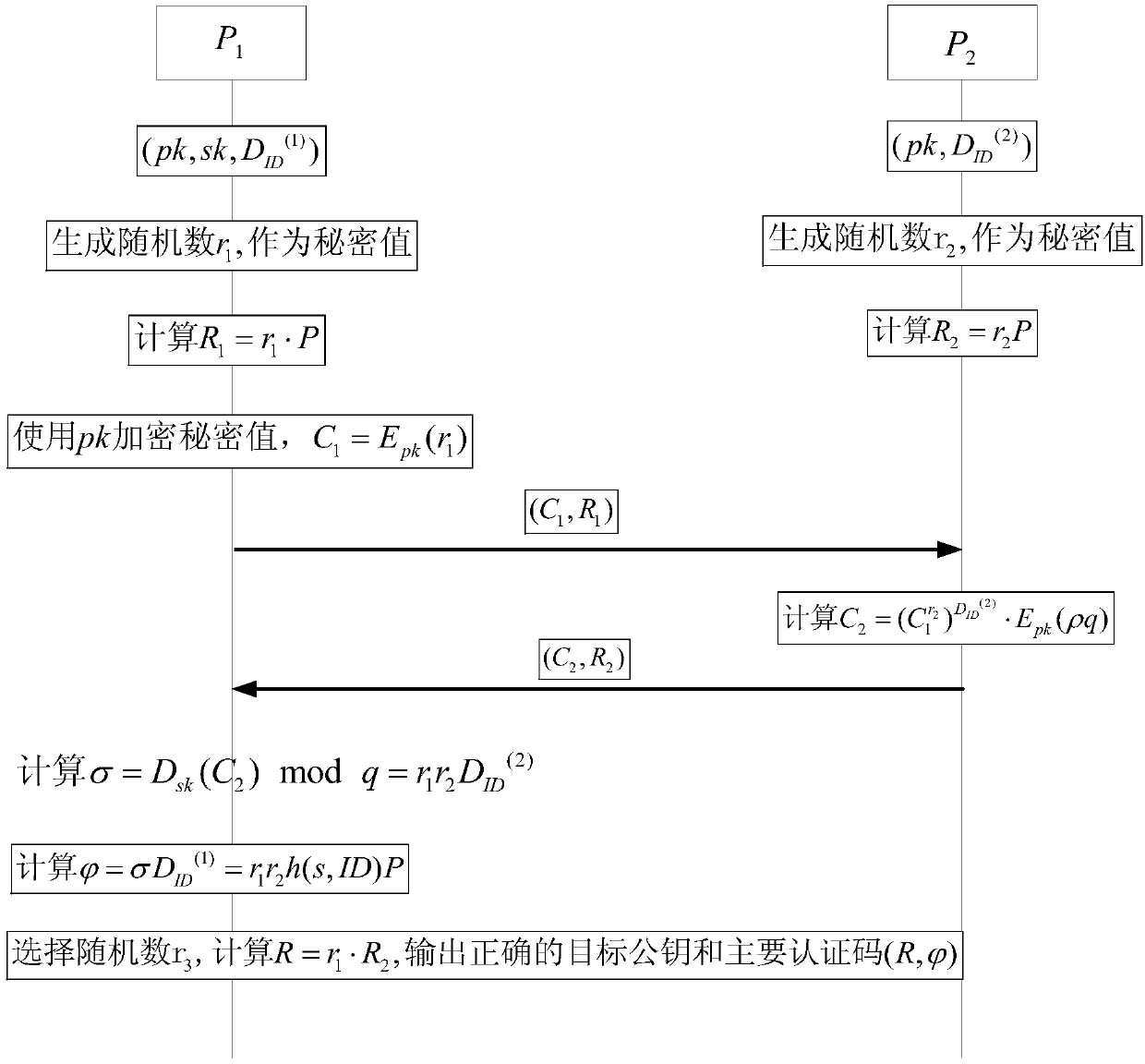
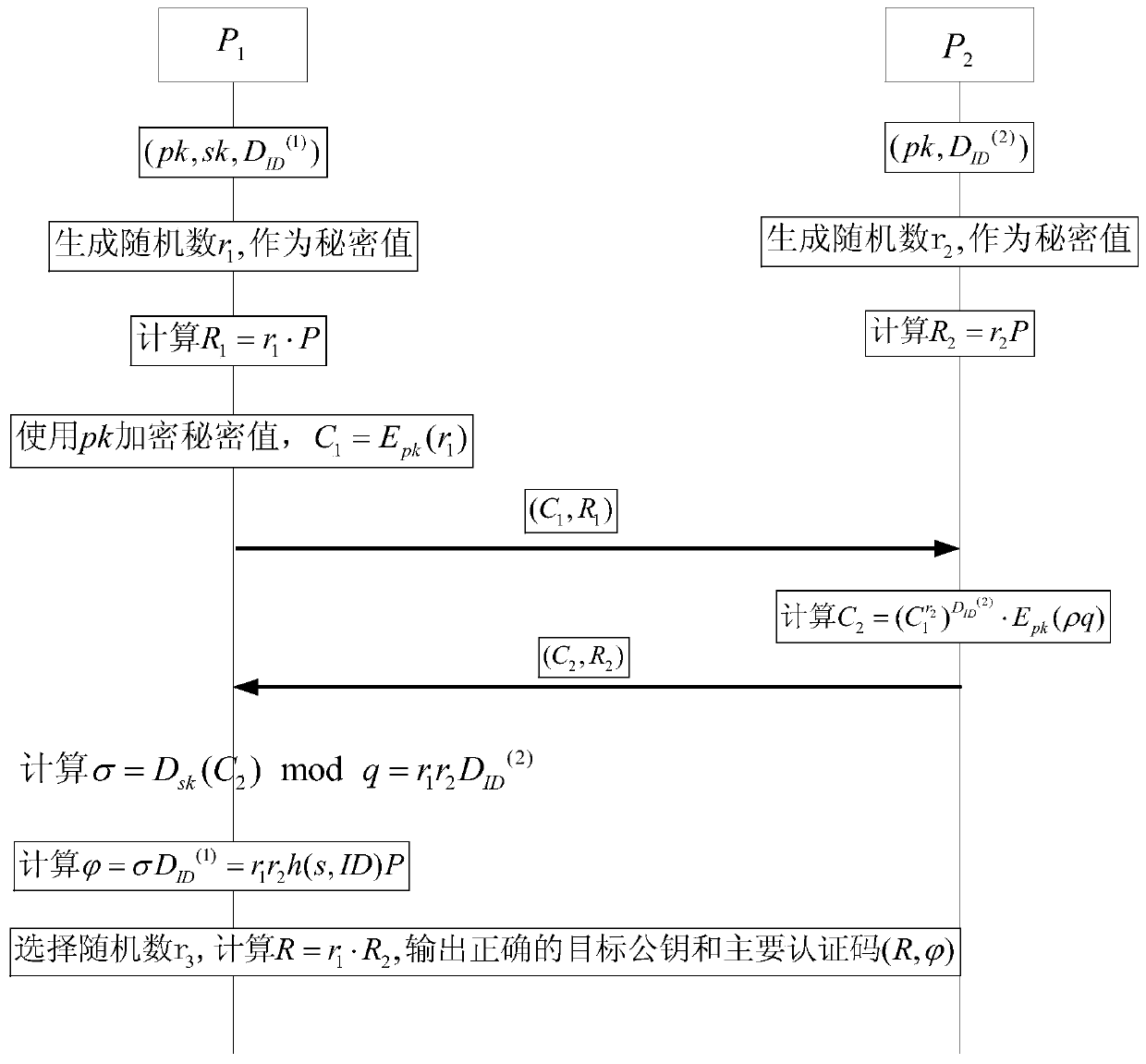
RSA digital signature generation method and system based on identity
ActiveCN107733648AImprove securityLess fairnessKey distribution for secure communicationPublic key for secure communicationCiphertextDigital signature
The invention relates to a RSA digital signature generation method and a RSA digital signature generation system based on an identity. The method specifically comprises the steps as follows: a secretkey generation center generates a public and secret key pair of a pair of RAS and a pair of random numbers; one part of a signature secret key is sent to P1, and the other part of signature secret keyis sent to P2; the two parties P1 and P2 participating into generation of a digital signature separately generate a random number r1 and a random number r2; the P1 firstly computes r1, encrypts the r1 to acquire C1, and then sends the C1 and r1 to the P2; the P2 computes r2 and returns the same to the P1; meanwhile, the P2 a ciphertext C2; the P2 sends the ciphertext C2 to the P1; And the P1 decrypts the C2, and computes to acquire signatures S and R by using one part of own signature secret key, and after the signatures pass authentication, the P1 publishes the complete RAS digital signature(R, S) based on the identity. According to the method and the system provided by the invention, security of the signature secret key is ensured, and the fairness of the two parties participating intothe digital signature is improved.
Owner:WUHAN UNIV
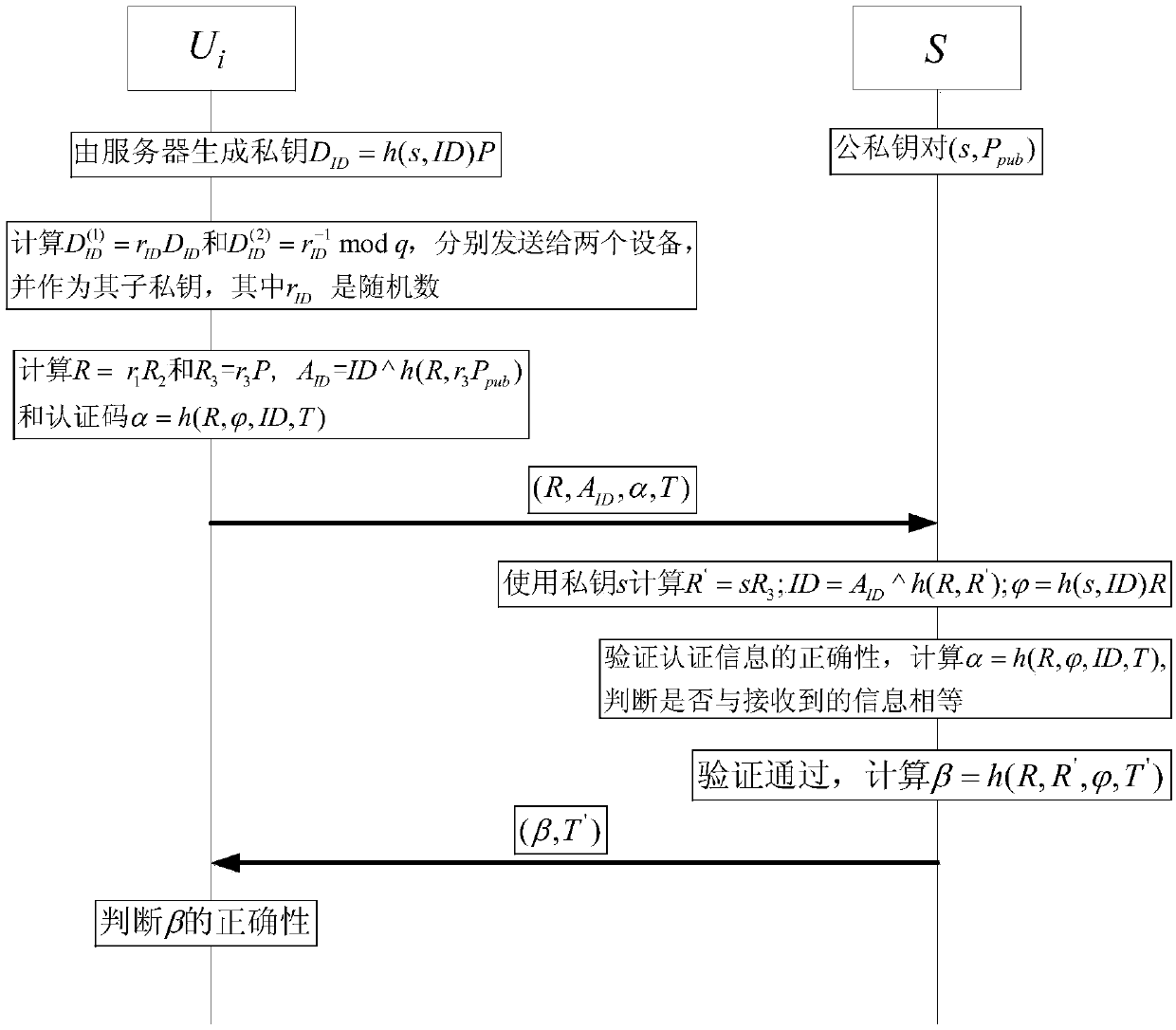
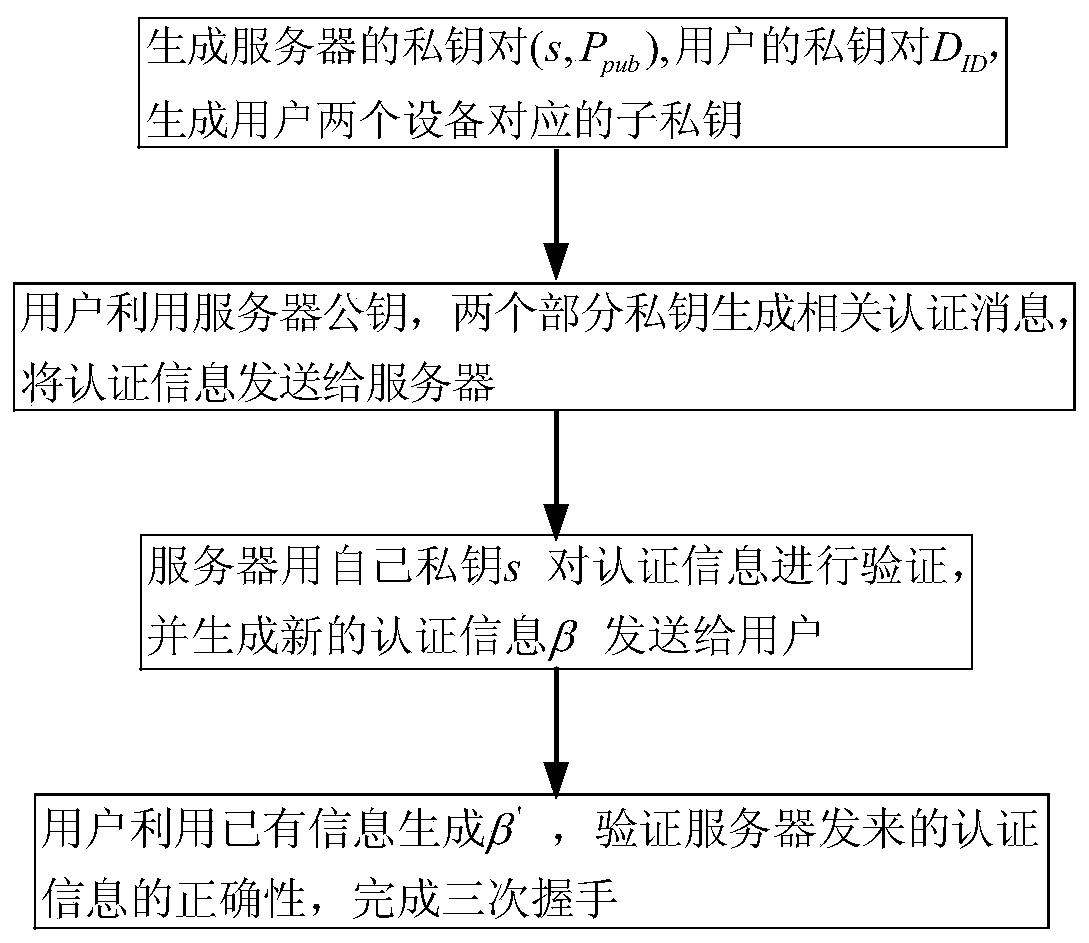
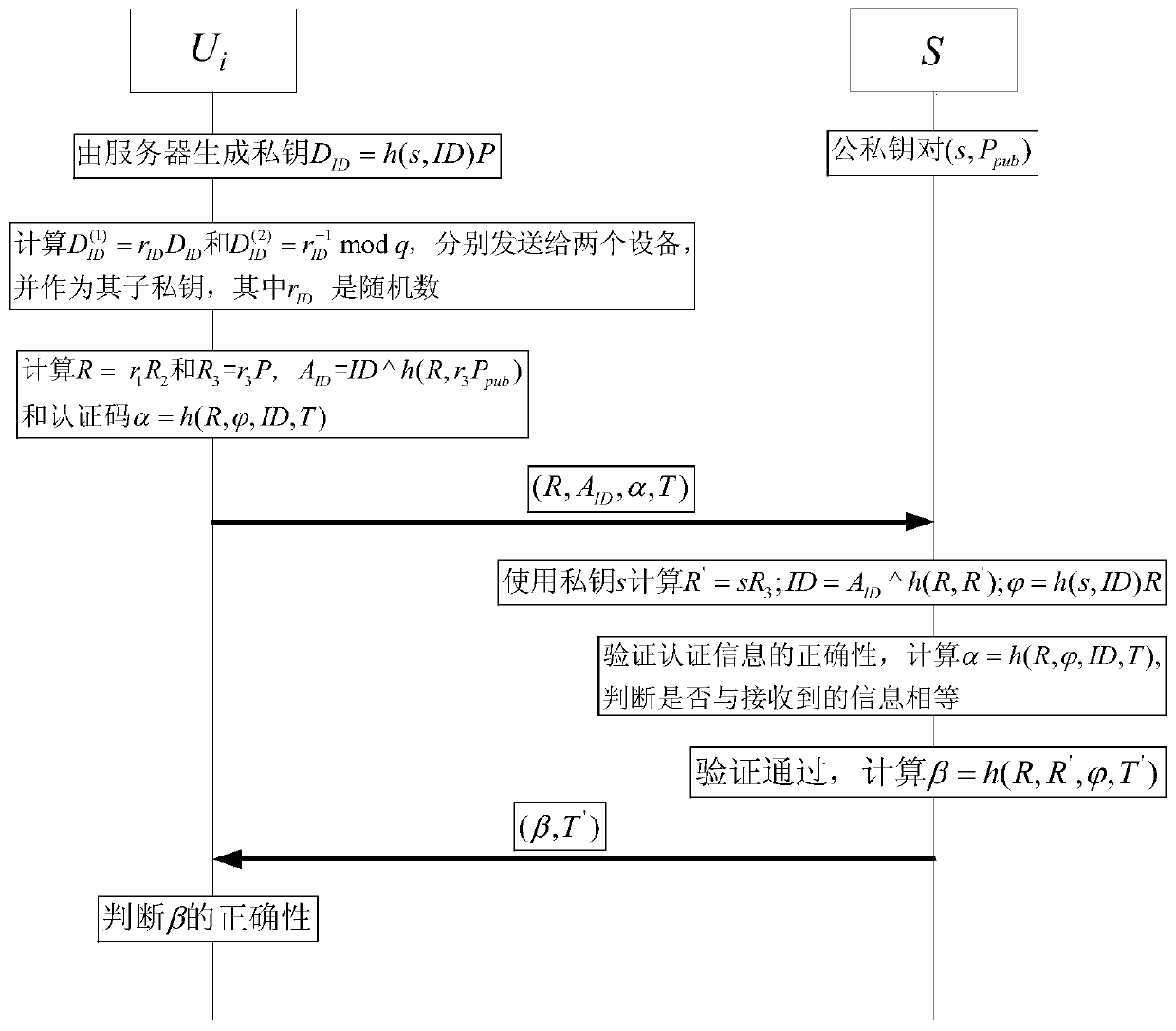
Identity-based anonymous authentication method and system
ActiveCN107947913AImprove securityLess fairnessKey distribution for secure communicationUser identity/authority verificationZero-knowledge proofSecure communication
The invention relates to an identity-based anonymous authentication method and system. The method comprises the following steps: a server generates two partial private keys and sends the same to double parties P1 and P2 participating in the authentication respectively, wherein P1 and P2 generate a main authentication code (the formula is described in the specification) and R in an authentication process, and the privacy and reliability of the interactive information between P1 and P2 are ensured by using zero knowledge proof; after the P1 obtains the main authentication code, the P1 generatesa pseudo-address AID, generates a third temporary public key R3, calculates a final authentication code alpha, and sends the authentication information (AID, R, R3, alpha, T) the server, and the server verifies the authentication information and feeds back the authentication information to a user, after the successful completion of three times of handshake, the server can establish secure communication with the user. The identity-based anonymous authentication method and system are suitable for jointly completing identity-based distributed anonymous authentication without exposing the respective partial authentication private keys of the both parties together, the both parties holding the partial private keys must participate in the authentication at the same time, and the complete authentication private key does not need to be restored.
Owner:WUHAN UNIV
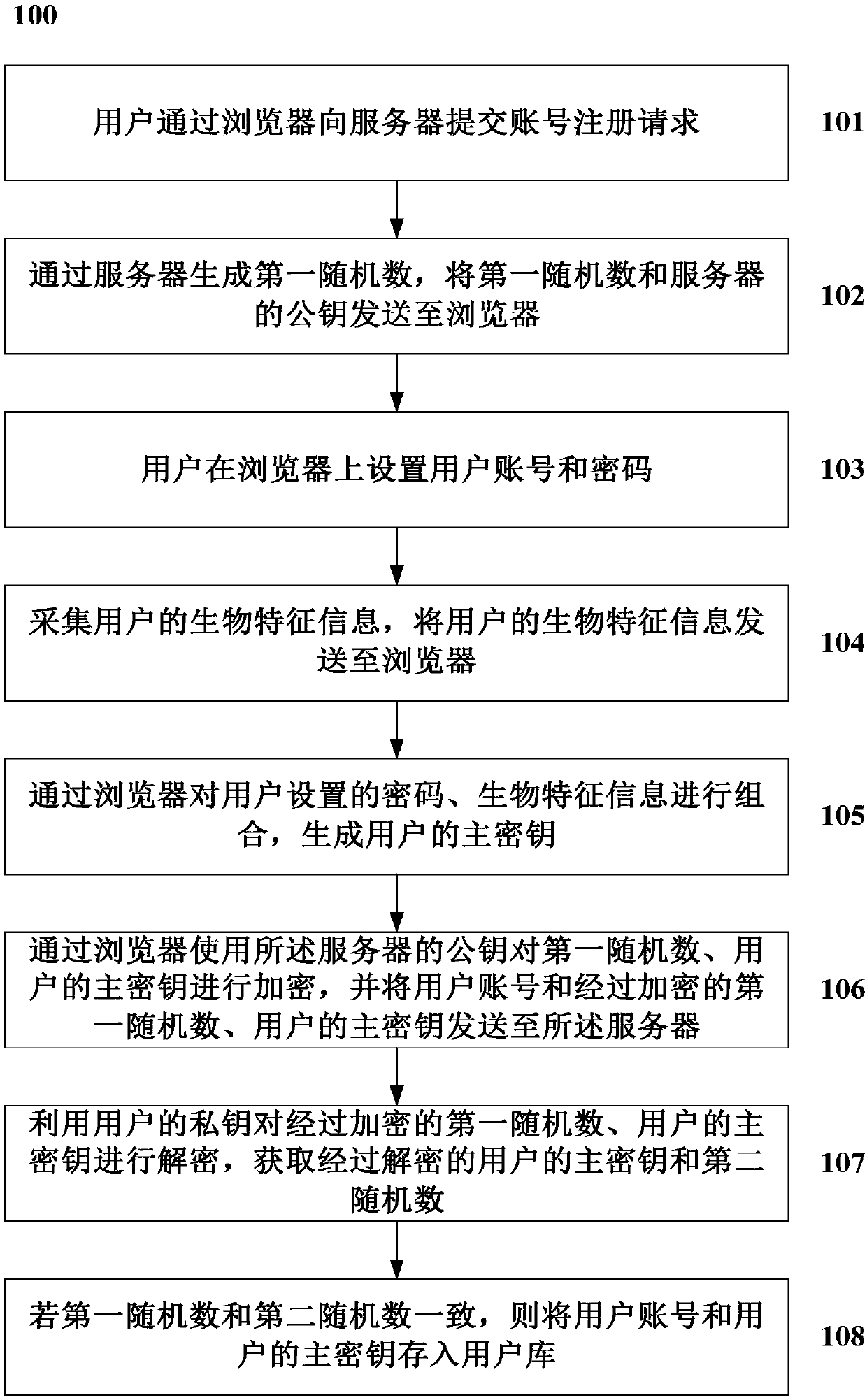
Double-factor identity authentication method and system based on biological identification technique
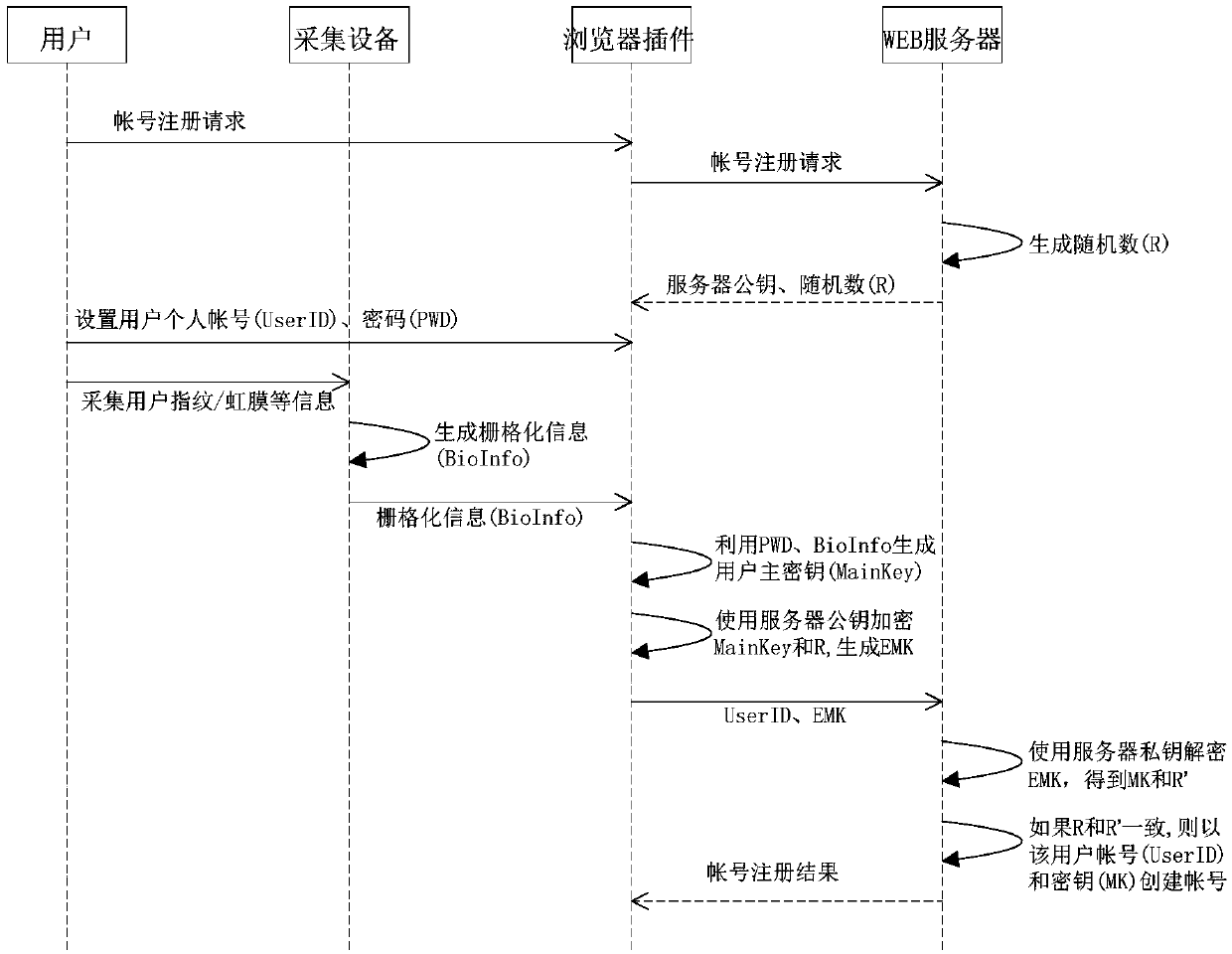
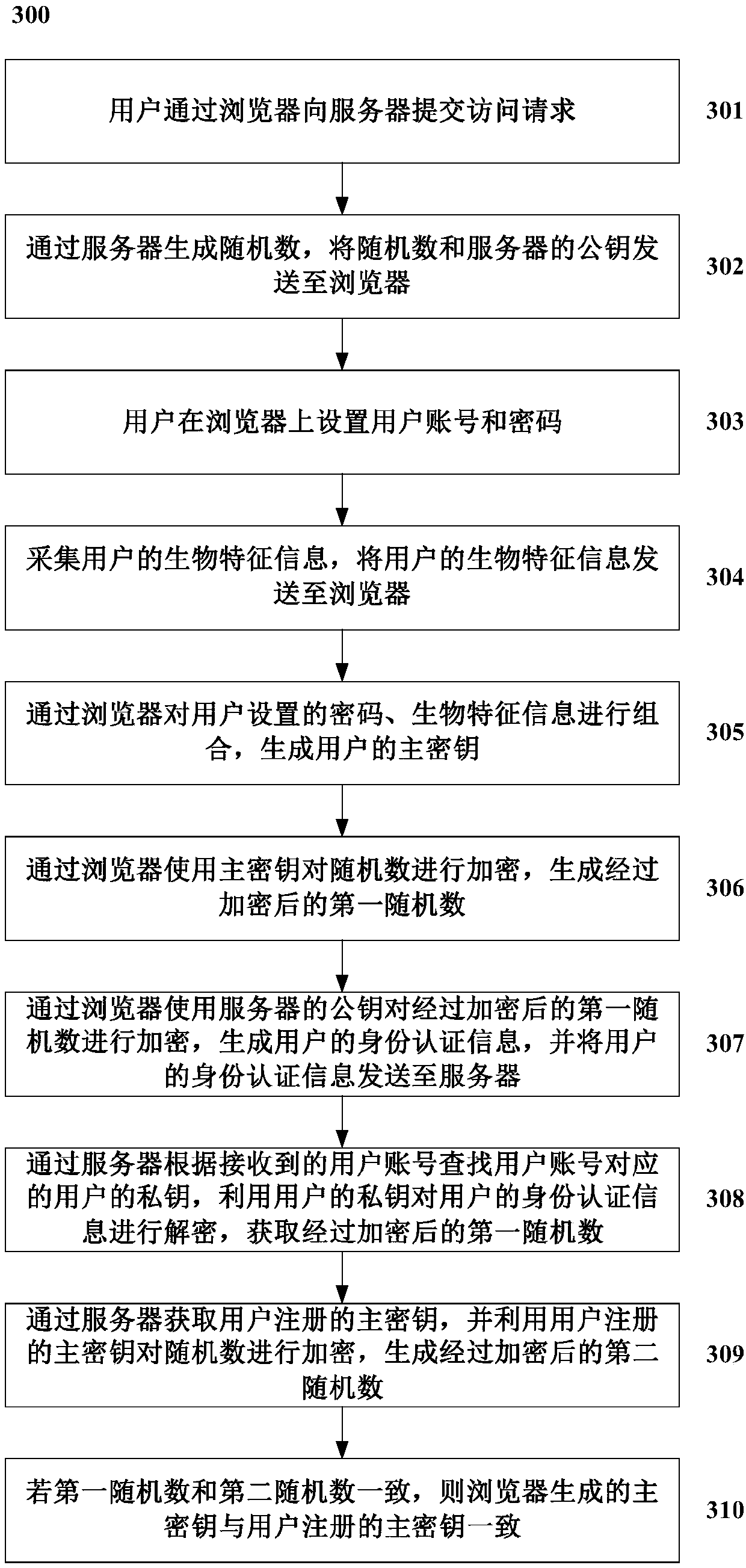
ActiveCN107733933AAddress vulnerable security issuesWon't spreadKey distribution for secure communicationMaster keyBiometric trait
The invention discloses a double-factor identity authentication method based on a biological identification technique. The method includes the steps that a user submits an account registration requestto a server through a browser; a first random figure is generated by the server, and the first random figure and a public key of the server are sent to the browser; the user sets a user account and acode on the browser; the biological feature information of the user is collected and sent to the browser; the code set by the user is combined with the biological feature information through the browser, and a master key of the user is generated; the public key of the server is used for conducting encryption on the first random figure and the master key of the user through the browser, and the user account, the encrypted first random figure and the encrypted master key of the user are sent to the server; the server searches for a user's private key corresponding to the user account accordingto the received user account, utilizes the user's private key to decrypt the encrypted first random figure and the encrypted master key of the user, and obtains the decrypted master key of the user and a second random figure.
Owner:CHINA ELECTRIC POWER RES INST +1
Platy heat pipe and processing technology thereof
InactiveCN102506597AImprove structural strengthWith ultra-thinSolar heating energyIndirect heat exchangersTrunk structureEngineering
The invention provides a platy heat pipe, comprising a platy heat pipe frame, wherein the platy heat pipe frame is internally provided with a microporous pipe trunk structure which is formed by a group of microporous pipes, side walls of the microporous pipes are connected to mutually enhance the strength of each microporous pipe, each microporous pipe is filled with a working medium with a phase inversion heat exchange effect, two ends of the platy heat pipe are sealed, and at least one end is provided with a gradually contractive sealing belt formed by cold welding. The platy heat pipe provided by the invention has the characteristics of high strength, super thinness, high efficiency and high heat transportation volume and can substitute an oscillation heat pipe and a common heat pipe.
Owner:赵耀华
Bilinear pairing-free cloud storage data security audit method
The invention provides a bilinear pairing-free cloud storage data security audit method. A user uploads own data blocks to a cloud server after encrypting in order to prevent data information from being leaked. Meanwhile, the user allows a trustable auditor to audit data, and makes sure that the data information is not leaked to the trustable auditor. According to the data audit scheme, the cloud storage data can be audited safely without great bilinearity.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Anonymous authentication method and system
InactiveCN101867587APrivacy protectionLeak will notUser identity/authority verificationService provisionPrivacy protection
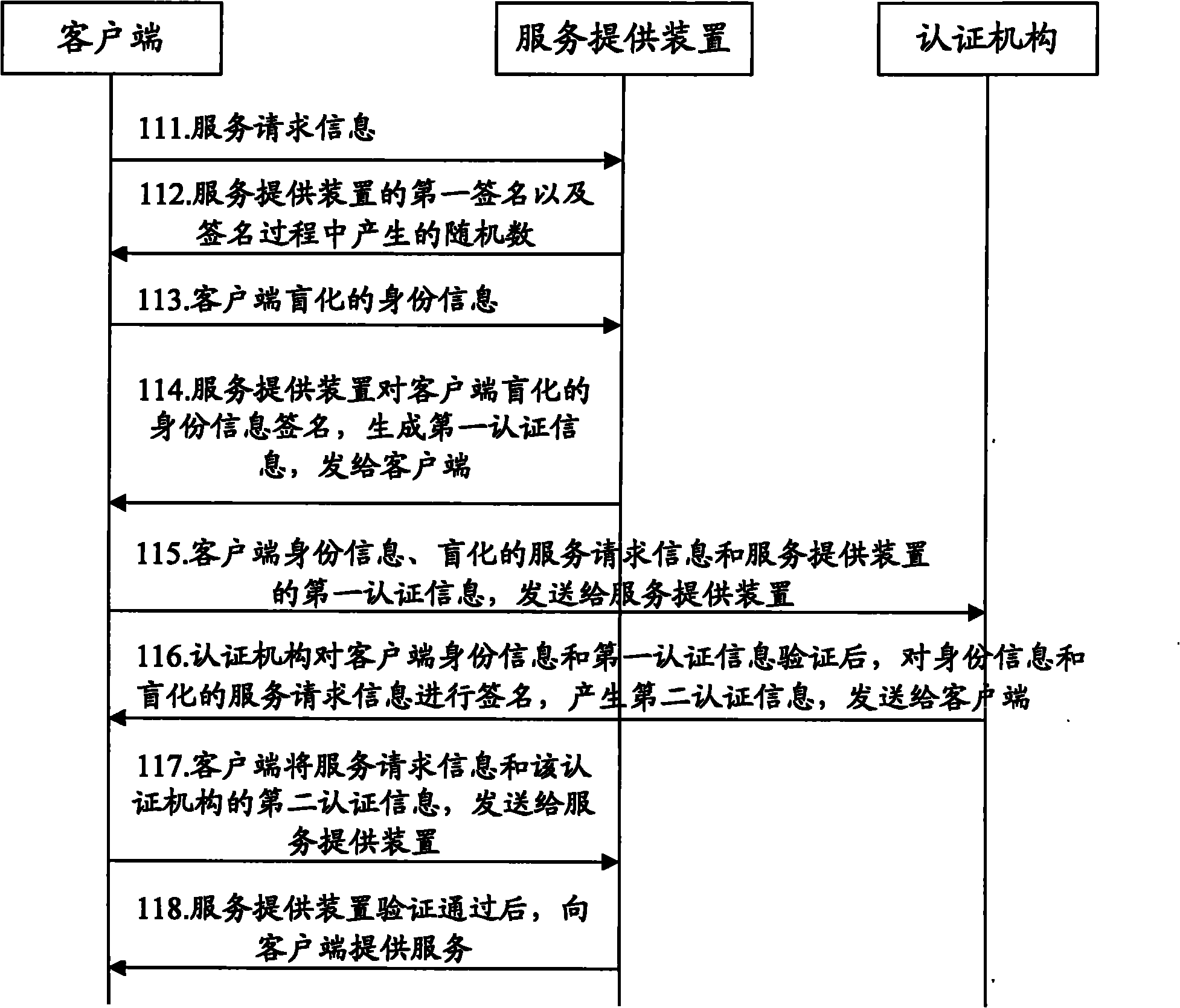
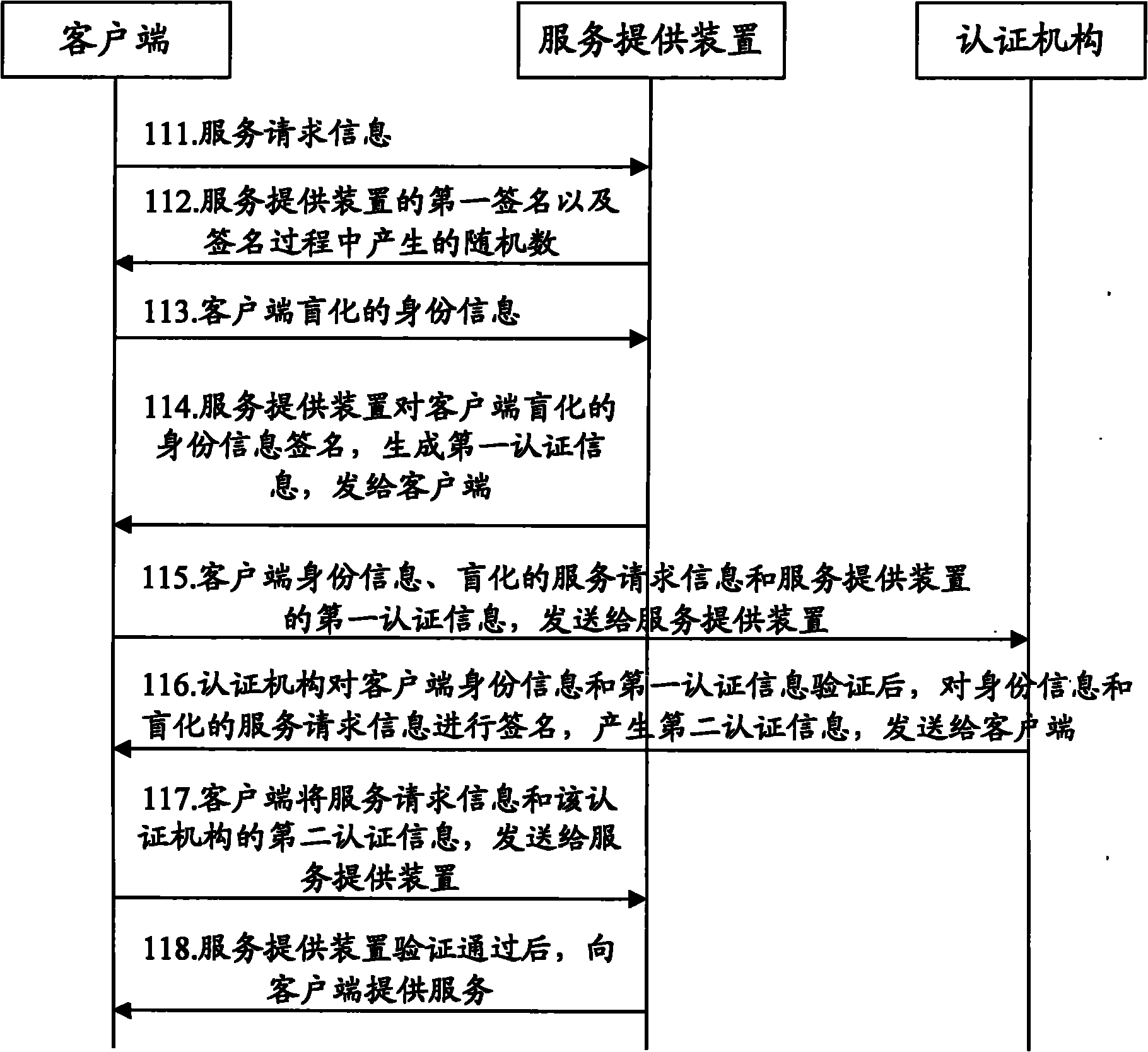
The invention discloses an anonymous authentication method and an anonymous authentication system. The method comprises the following steps that: a client generates blind identity information according to the identity information of the client per se and sends the blind identity information to a service provider; the client receives first authentication information generated after the service provider signs the blind identity information; the client generates blind service request information according to the service request information of the client to the service provider and sends the blind service request information to an authentication institution; the client receives second authentication information generated after the authentication institution signs the blind service request; and the client sends the service request information and the second authentication information to the service provider, and receives service content information provided according to the service request information after the service provider authenticates and passes the second authentication information. The scheme can realize authentication with a privacy protection function and anonymous authentication is controllable.
Owner:BEIJING JIAOTONG UNIV
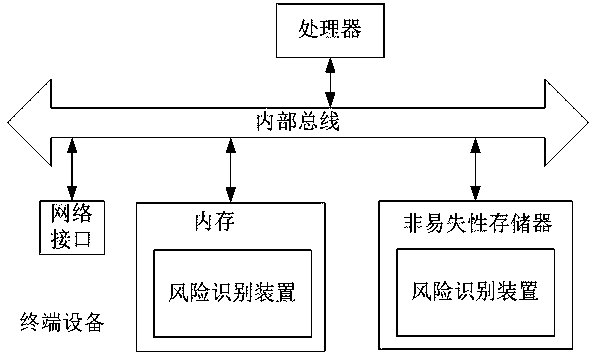
Risk identification method and device and electronic equipment
ActiveCN111310196AReduce the stress of risk identificationLeak will notPlatform integrity maintainanceValue setStatistical analysis
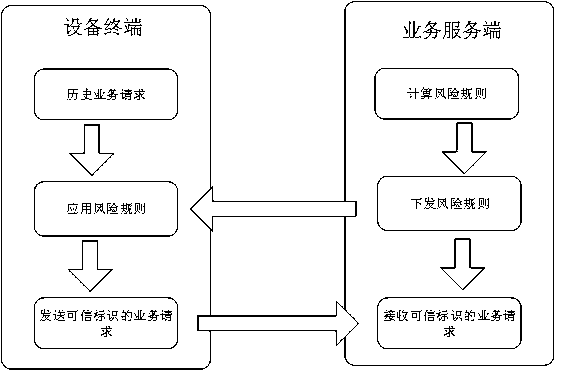
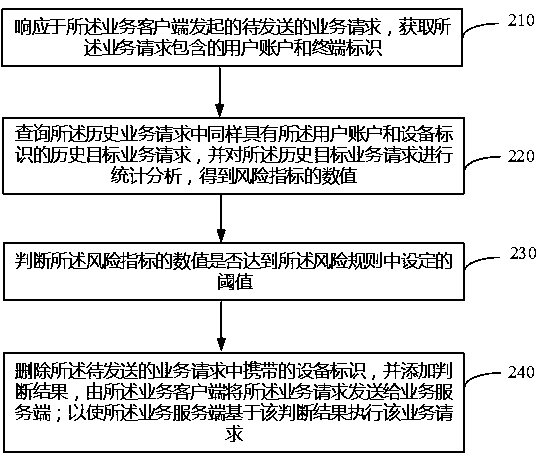
The invention provides a risk identification method and device and electronic equipment. The risk identification method and device are applied to a trusted execution environment of terminal equipment,wherein historical business requests and risk rules are stored in the trusted execution environment. The method comprises the following steps: in response to a to-be-sent service request initiated bya service client, obtaining a user account and a terminal identifier contained in the service request; querying a historical target service request which also has the user account and the equipment identifier in historical service requests, and performing statistical analysis on the historical target service request to obtain a numerical value of the risk index; judging whether the numerical value of the risk index reaches a threshold value set in a risk rule or not; deleting an equipment identifier carried in the to-be-sent service request, adding a judgment result, and sending the service request to a service server by the service client; and sending the business request to the business server to enable the business server to execute the business request based on the judgment result. The personal information of the user can be protected due to the fact that the device identifier is not sent outwards.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
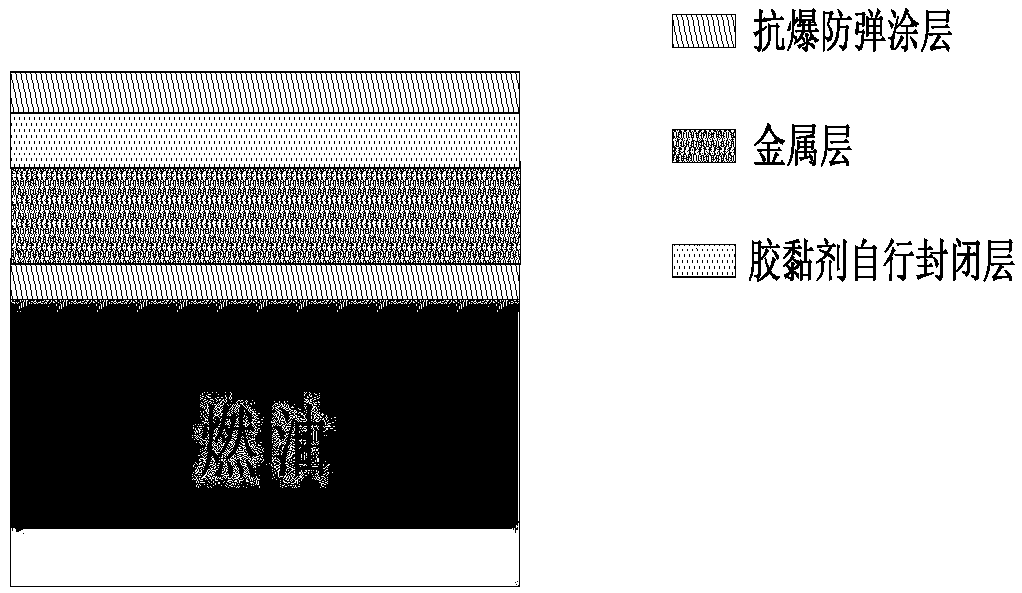
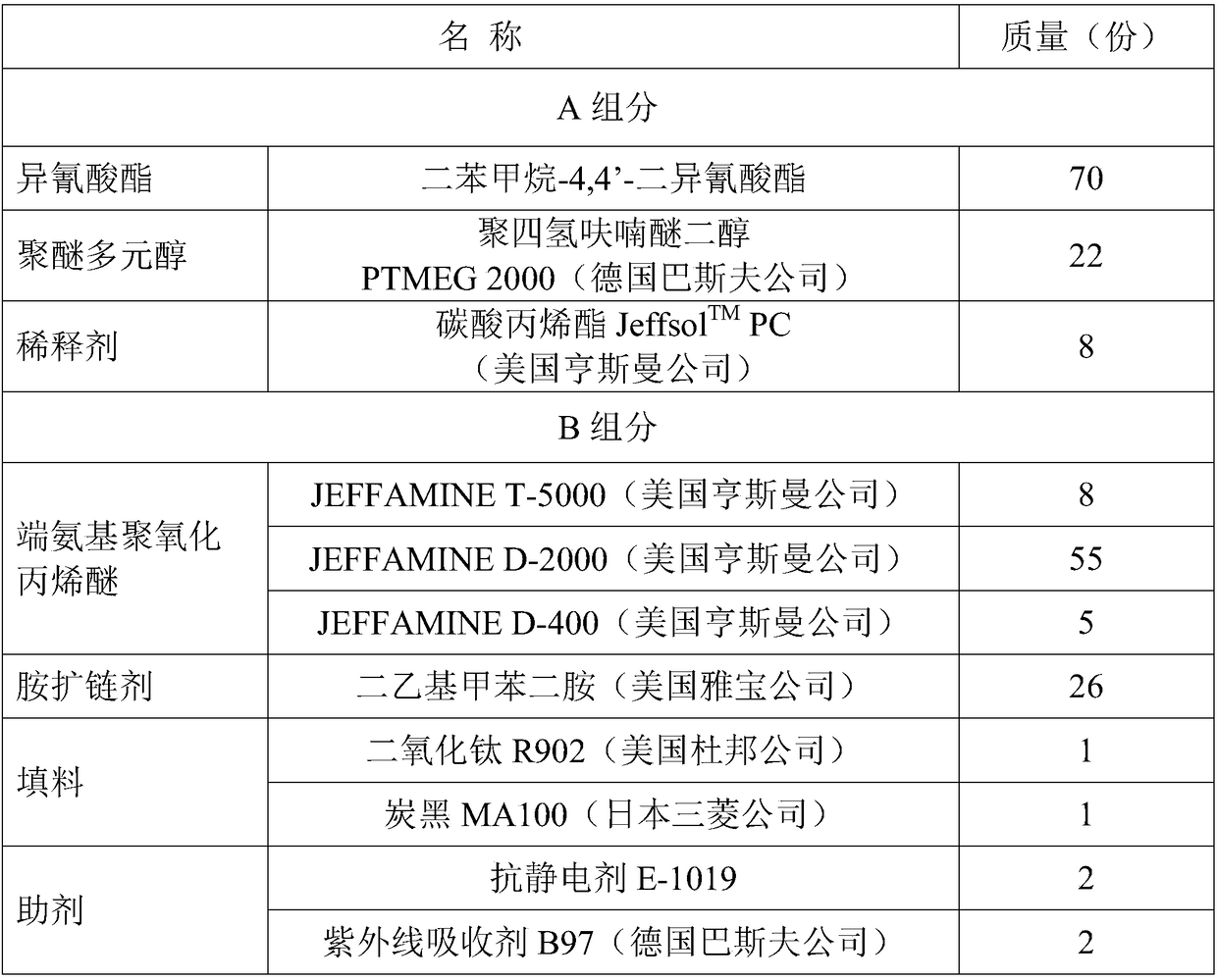
Anti-knock bulletproof coating material and preparation method and application thereof
InactiveCN108707415AImprove antiknock performanceSelf-enclosedPolyurea/polyurethane coatingsPolyolDiluent
The invention relates to an anti-knock bulletproof coating material and a preparation method and application thereof and belongs to the technical field of protective materials. The anti-knock bulletproof coating material comprises a component A and a component B; the component A comprises 40-80 parts of isocyanate, 20-55 parts of polyether polyol and 0-10 parts of diluent; the component B comprises 50-88 parts of amine-terminated polyether , 25-50 parts of amine chain extender, 0-5 parts of packing and 0-5 parts of additives. The volume ratio of the component A to the component B is 1 to 0.97-1.03. The component A and the component B are prepared respectively, and are mixed and sprayed to the surface of the base body of an oil tank or oil box by a double-component high-temperature high-pressure impact mixing airless spraying equipment so as to form the anti-knock bulletproof coating. The unique strain rate sensitivity of the anti-knock bulletproof coating can improve the dynamic mechanics performance of the oil tank / oil box under explosive load, and anti-knock anti-impact performance can be improved by reducing structural transformation of the oil tank / oil box.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Broadband terahertz mixer with low frequency conversion loss
ActiveCN112332780AStreamlined and Simplified SizeShorten the lengthMulti-frequency-changing modulation transferenceLow-pass filterIntermediate frequency
The invention discloses a broadband terahertz mixer with low frequency conversion loss, and aims to achieve high isolation, simple structure, high working frequency, low frequency conversion loss andwide working bandwidth. According to the technical scheme, a quartz circuit cavity penetrates through a radio frequency height reduction waveguide and a local oscillation height reduction waveguide, an anti-parallel terahertz Schottky diode is arranged between a radio frequency direct current ground microstrip line and a radio frequency matching branch knot on the upper surface of a quartz substrate, and the radio frequency direct current ground microstrip line and the radio frequency matching branch knot sequentially pass through a radio frequency transition suspension microstrip line; a local oscillator low-pass filter and a local oscillator matching network are connected in series, the local oscillator transition microstrip penetrates through the local oscillator height reduction waveguide and is connected with the intermediate frequency low-pass filter in series, and finally a frequency mixing signal is output through an intermediate frequency port.
Owner:10TH RES INST OF CETC
Anonymous transaction method in e-commerce
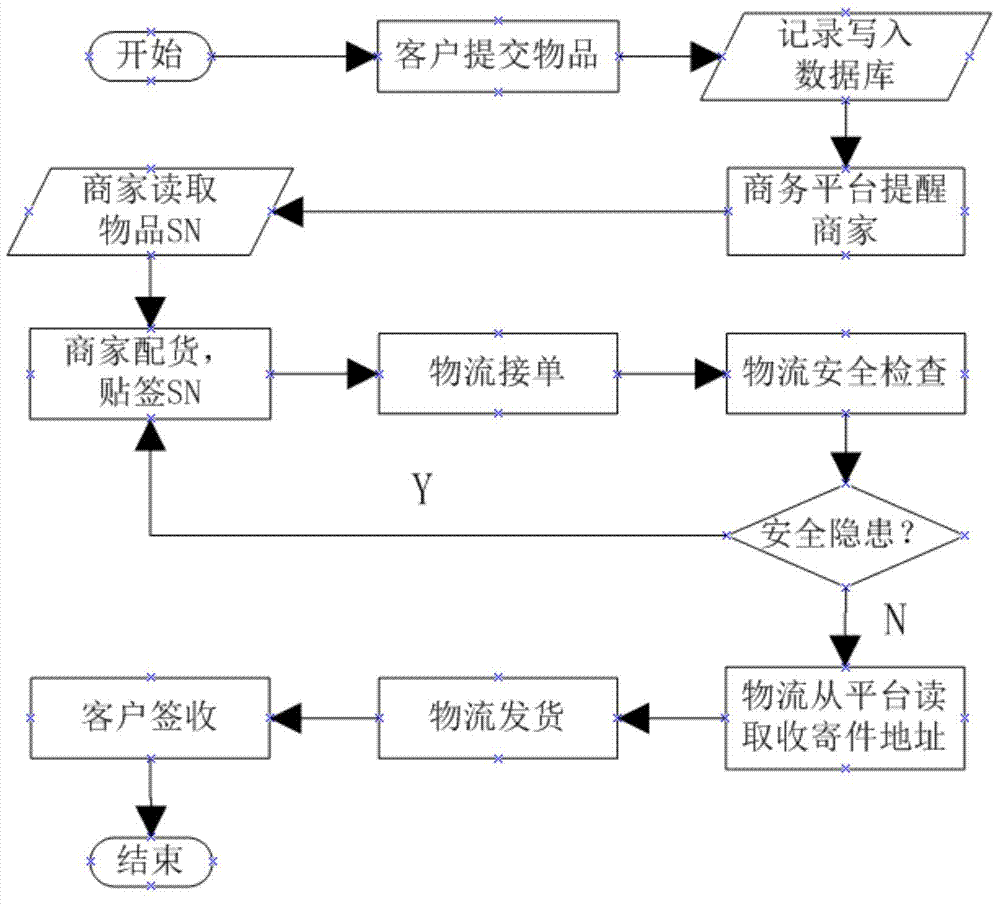
ActiveCN104240121ALoose connectionPrevent leakageBuying/selling/leasing transactionsE-commerceDatabase
The invention provides an anonymous transaction method in e-commerce. The anonymous transaction method in e-commerce is a data storage base as the commercial platform of a trusted fourth party and a core of transaction operation. The anonymous transaction method in e-commerce is capable of storing a sequence number, the individual information of a customer, the merchant information and the article information. As a result, the three particles has the unique common sequence number which can be used as the unique evidence of information communication. A logistics company, as a non-transaction party, does not keep the article information. After the sequence number of an article is scanned, the sequence number and the necessary delivery information of a buyer and a seller are saved by a logistics system to facilitate logistics tracking. The anonymous transaction method in e-commerce has the advantages that the commercial platform of the trusted fourth party is introduced to loosen the necessary connection of a shopping customer and a merchant and change the pattern that collection and delivery addresses are obtained from the merchant in traditional logistics. While the transaction purpose is achieved, the related information of the customer can be effectively prevented from leaking out.
Owner:桂林智慧产业园有限公司
Block chain design method of blind signature based on ECC algorithm
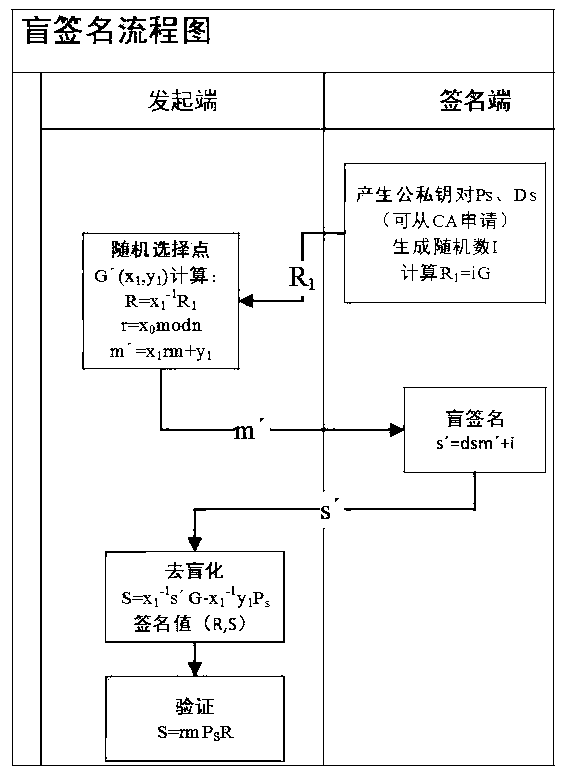
InactiveCN108898031ALeak will notReduce the cost of trustDigital data protectionDigital Signature AlgorithmBlind signature
The invention provides a block chain design method of blind signature based on ECC algorithm, The invention belongs to the cross technical field of cryptography and block chain. In the prior block chain deployment process, the invention realizes blind signature algorithm by using go language, reconstructs the original signature flow, adds blind signature module to block chain code for deployment,and completes blind signature reconstruction of block chain. Blind signature based on digital signature has anti-forgery and anti-repudiation characteristics, and can blind the message, and will not disclose any message content and information to the signer. The signer can not deduce the content of the signature according to the parameters, so it can be applied to the block chain system very well.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Position air conditioner based on metro vehicle depot
PendingCN107327959ASolve the vibrationSolve the noiseSpace heating and ventilation safety systemsLighting and heating apparatusEngineeringRefrigeration
The invention discloses a position air conditioner based on a metro vehicle depot. The position air conditioner based on a metro vehicle depot comprises an air conditioner main machine. The air conditioner main machine comprises a main machine shell and a refrigeration device, wherein casters are arranged at the bottom of the main machine shell, an air port part is arranged on the top of the main machine shell, the air port part comprises a sealing ring, a rotating shell, a ventilation disk and a fixing ring, the opening in the top of the main machine shell is sleeved with the upper portion of the sealing ring, the outer edge of the ventilation disk is connected with the bottom of the rotating shell, the lower portion of the sealing ring is connected with the upper portion of the fixing ring, a whole formed by the ventilation disk and the rotating shell is arranged in the sealing ring and the fixing ring, the rotating shell and the ventilation disk are limited in the vertical direction by the sealing ring and the fixing ring, an air outlet is formed in the surface of the rotating shell, the ventilation disk is connected with a motor, and the motor is arranged in the fixing ring. According to the position air conditioner based on a metro vehicle depot, an air port can rotate by 360 degrees because the air port part is driven by the motor, and further because the position air conditioner naturally has the characteristic of being movable, the problems that effective refrigeration air flow cannot be organized because a metro vehicle depot maintenance shop is limited by the self civil structure and the stream people is decentralized are effectively solved.
Owner:GUANGZHOU METRO DESIGN & RES INST +1
A civil aviation emergency causal relationship analysis method based on a Bayesian network
PendingCN109886577AWeaken dependenciesSpeed up message deliveryResourcesMessage passingUnexpected events
The invention discloses a civil aviation emergency causal relationship analysis method based on a Bayesian network. The method comprises the steps of firstly establishing a civil aviation emergency management field ontology as a Bayesian network model, and dedarizing the Bayesian network to obtain a Markov network; and then initializing the Markov network and iteratively optimizing the Markov network, taking the Markov network optimized in the last iteration as an optimal Markov network, and using the optimal confidence coefficient of each node in the optimal Markov network to evaluate the probability of the causal relationship of the civil aviation emergency. According to the method, the V-shaped structure in the Bayesian network is changed, the message transmission rate in the Markov network is increased in the reasoning process, and the causal relationship calculation complexity in a large-scale network is reduced; in the Markov network reasoning process, a cyclic confidence coefficient propagation algorithm is improved in combination with a differential privacy model, and the leakage of sensitive information during causal relationship reasoning in the civil aviation field is avoided.
Owner:SHAANXI NORMAL UNIV +1
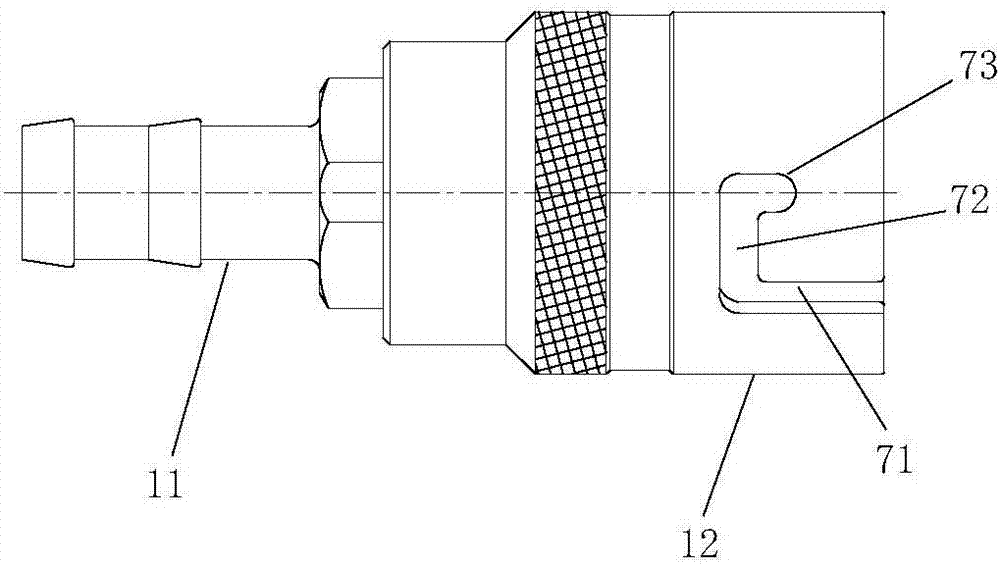
Quick coupling and working method thereof
The invention relates to a quick coupling and a working method thereof. The quick coupling comprises a male connector and a female connector which are connected and matched with each other in a plugged mode. The male connector and the female connector are internally provided with a movably first valve element and a movable second valve element correspondingly, and the first valve element and the second valve element are in sealing fit with annular sealing parts of sleeves correspondingly. The quick coupling is simple in structure. After the male connector and the female connector are plugged together, the second annular sealing part is in sealing fit with a third sleeve of the male connector to effectively avoid leakage. A herringbone guide support is arranged to guarantee that the first valve element cannot get inclined when sliding in the third sleeve of the male connector, and guiding is stable. Meanwhile, the outer edge of the herringbone guide support protrudes out of the edge of a first sealing disk so that a channel suitable for circulation of liquid with pressure can be formed easily after the first sealing disk slides towards the third sleeve of the male connector, and quick circulation of the liquid with pressure is guaranteed.
Owner:丹阳市裕桥精密元件有限公司
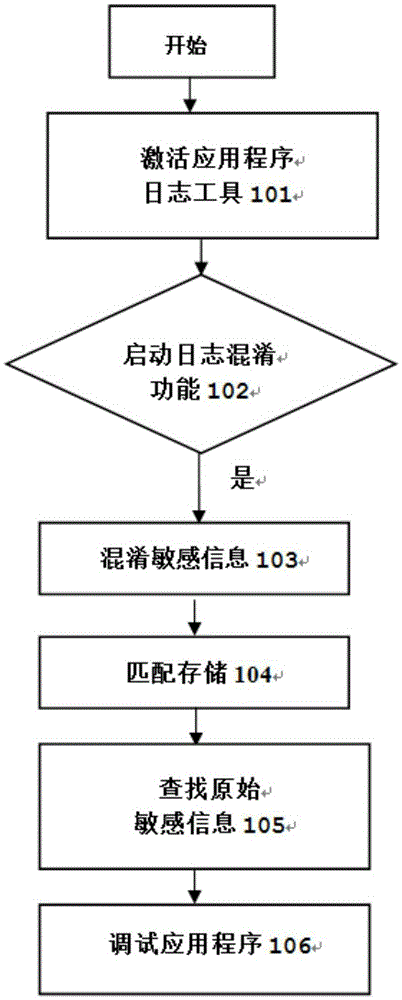
Method and system for preventing sensitive information from leakage
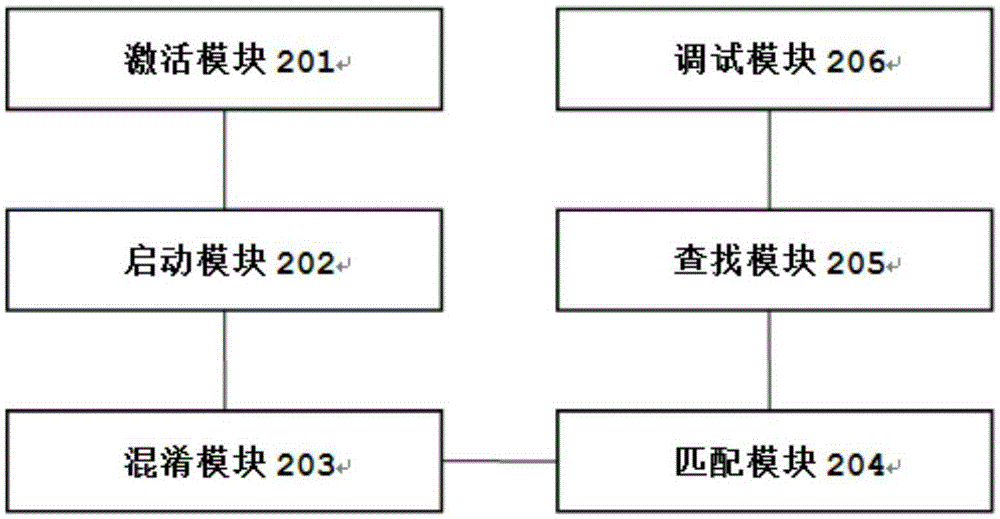
InactiveCN105337988APrevent leakageLeak will notEncryption apparatus with shift registers/memoriesInternet privacyConfusion
The invention relates to a method for preventing sensitive information from leakage. The method comprises the following steps: before operating an application program at a client, enabling a client user to activate a log tool of the application program; after the client activates the log tool of the application program, determining whether a log confusion function of the log tool is started or not by the client; if determining that the log confusion function is started, when operating the application program, confusing original sensitive information in a generated log when the log confusion function generates the log; matching the confused log information with the original sensitive information in the log and storing the original sensitive information to a local dictionary; when the client user determines that the application program has faults according to the confused log information, finding out the original sensitive information from the local dictionary; and debugging the application program according to the original sensitive information. The invention further provides a system for preventing the sensitive information from leakage.
Owner:刘奇
Acid fog collection spraying device
InactiveCN108479367AGood air tightnessImprove work efficiencyDispersed particle separationFog collectionMedicine
The invention discloses an acid fog collection spraying device, and relates to the technical field of collection spraying. The acid fog collection spraying device comprises a collection spraying device body; the collection spraying device body comprises a collection cover, a spraying box and a ventilation pipe; a sealing gasket is fixedly installed at the position of the lower end edge of the collection cover; one end of the ventilation pipe is fixedly connected with one end of the collection cover; the ventilation pipe and the collection cover are integrally formed; and the other end of the ventilation pipe is movably connected with one end of the spraying box. According to the acid fog collection spraying device, on one hand, the spraying box and the ventilation pipe can be used for carrying out acid fog collection by randomly disassembling and changing different specifications of collection devices, and acid fog is prevented from leaking out due to low impermeability when the acid fog is collected by using different specifications of collection covers; and on the other hand, the sealing gasket can guarantee high air impermeability of the collection cover when the acid fog is collected, the acid fog cannot leak, and then a suction machine inside the ventilation pipe can be used for sucking the acid fog into the spraying box more quickly, so that the working efficiency is improved.
Owner:SUQIAN LONGKING ECOTECH
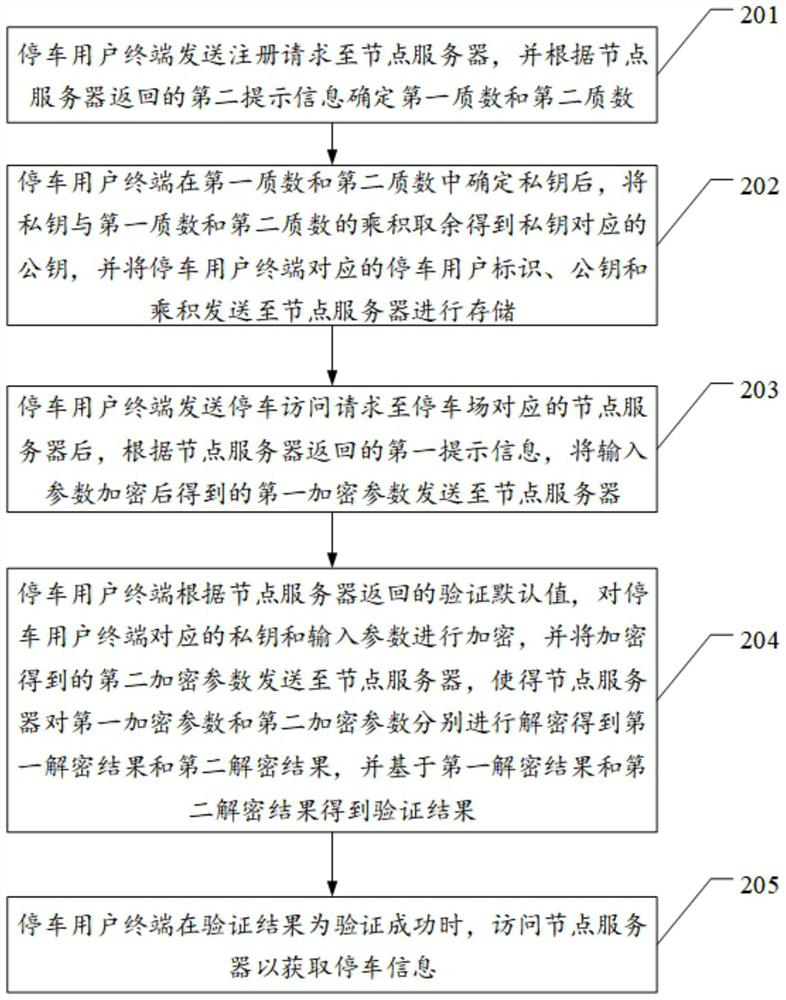
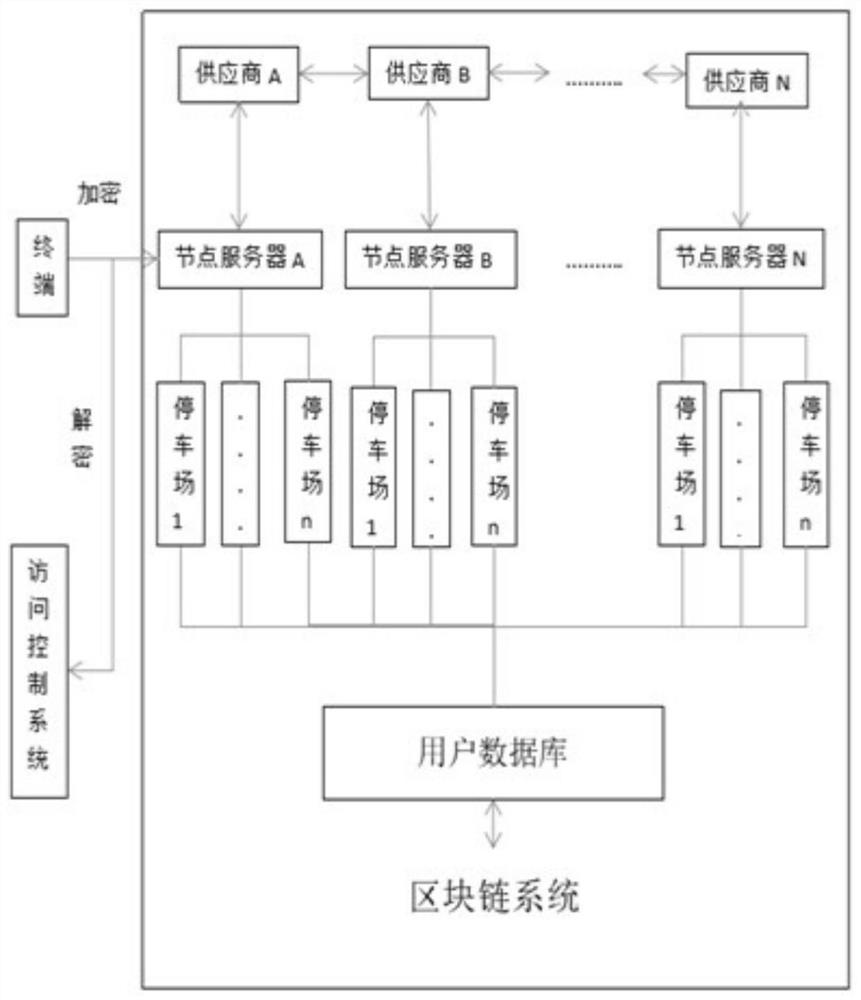
Verification method for parking access, parking user terminal and node server
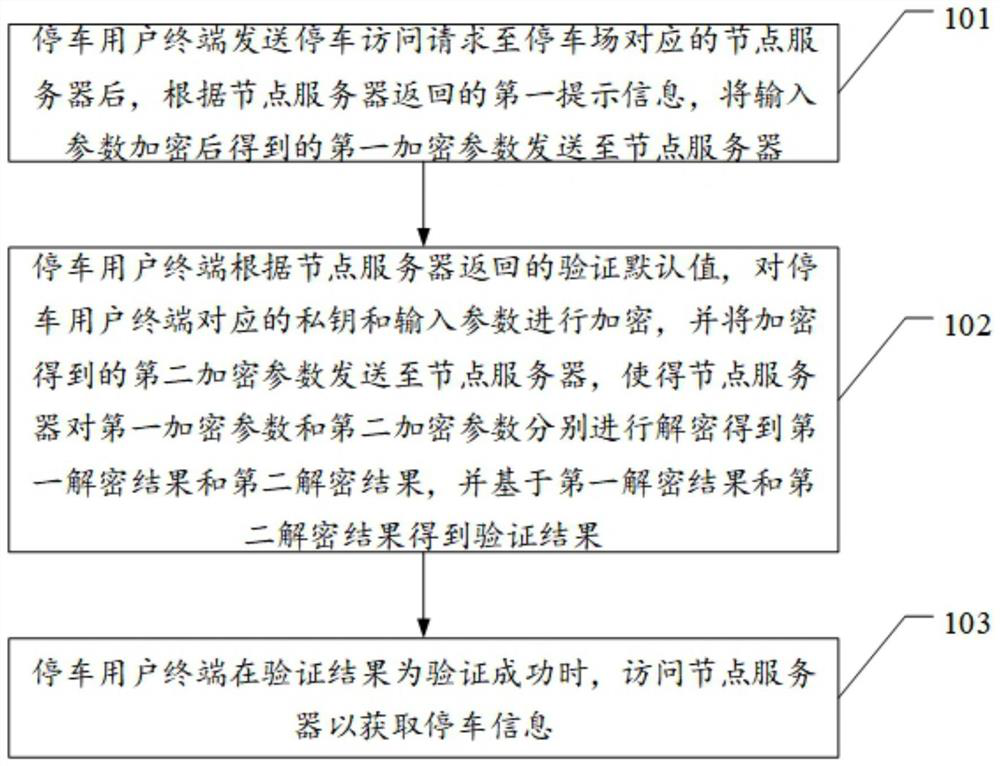
ActiveCN112039921ALeak will notEnsure safetyIndication of parksing free spacesTransmissionEngineeringManagement system
The invention discloses a verification method for parking access, a parking user terminal and a node server, and the method comprises the steps that the parking user terminal transmits a parking access request to the node server, and then transmits a first encryption parameter obtained after the encryption of an input parameter to the node server according to first prompt information returned by the parking user terminal; the parking user terminal encrypts a private key and an input parameter of the parking user terminal according to a verification default value returned by the node server, and sends an obtained second encryption parameter to the node server, so that the node server decrypts the first encryption parameter and the second encryption parameter respectively, and obtains a verification result based on a first decryption result and a second decryption result obtained by decryption; and the parking user terminal accesses the node server to obtain the parking information whenthe verification result shows that the verification succeeds, so that the technical problems that no identity verification is performed on the access users in the existing parking management system, any access user can view the parking user data, and the security is relatively low are solved.
Owner:GUANGDONG ANJUBAO DIGITAL TECH
Authentication method and system using portable terminal
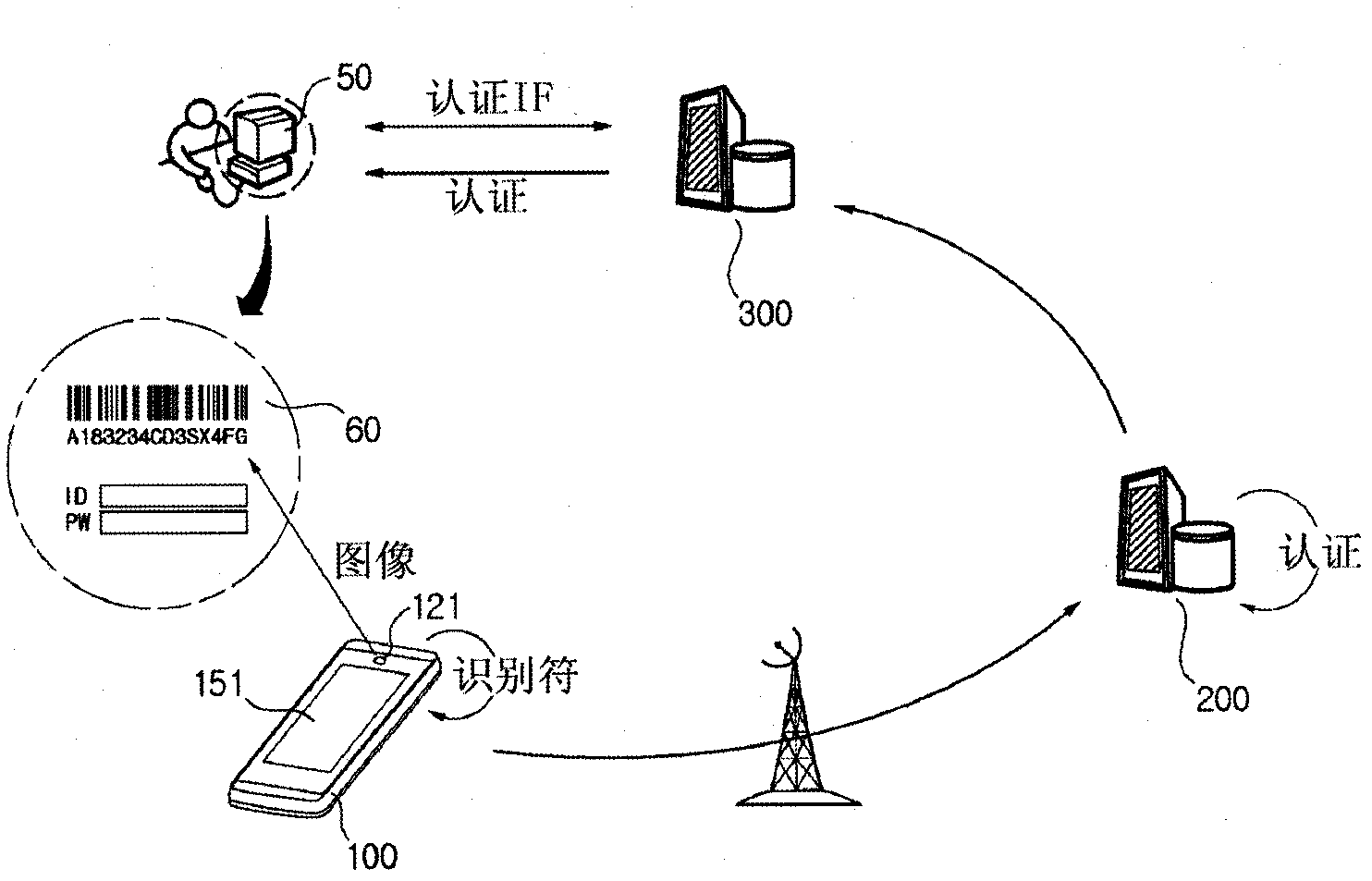
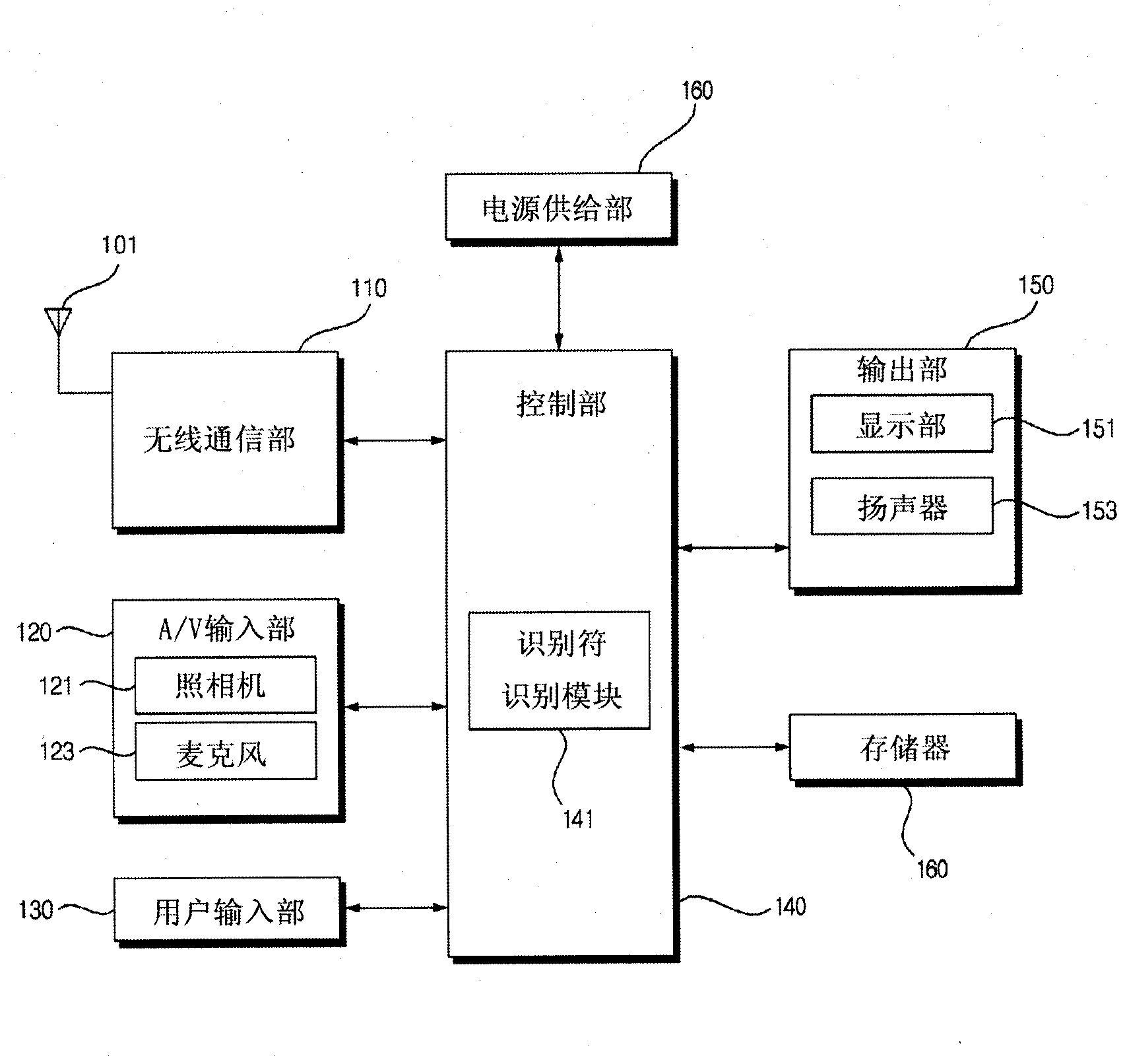
InactiveCN103039098APrevent leakageLeak will notDigital data authenticationTransmissionThe InternetAuthentication information
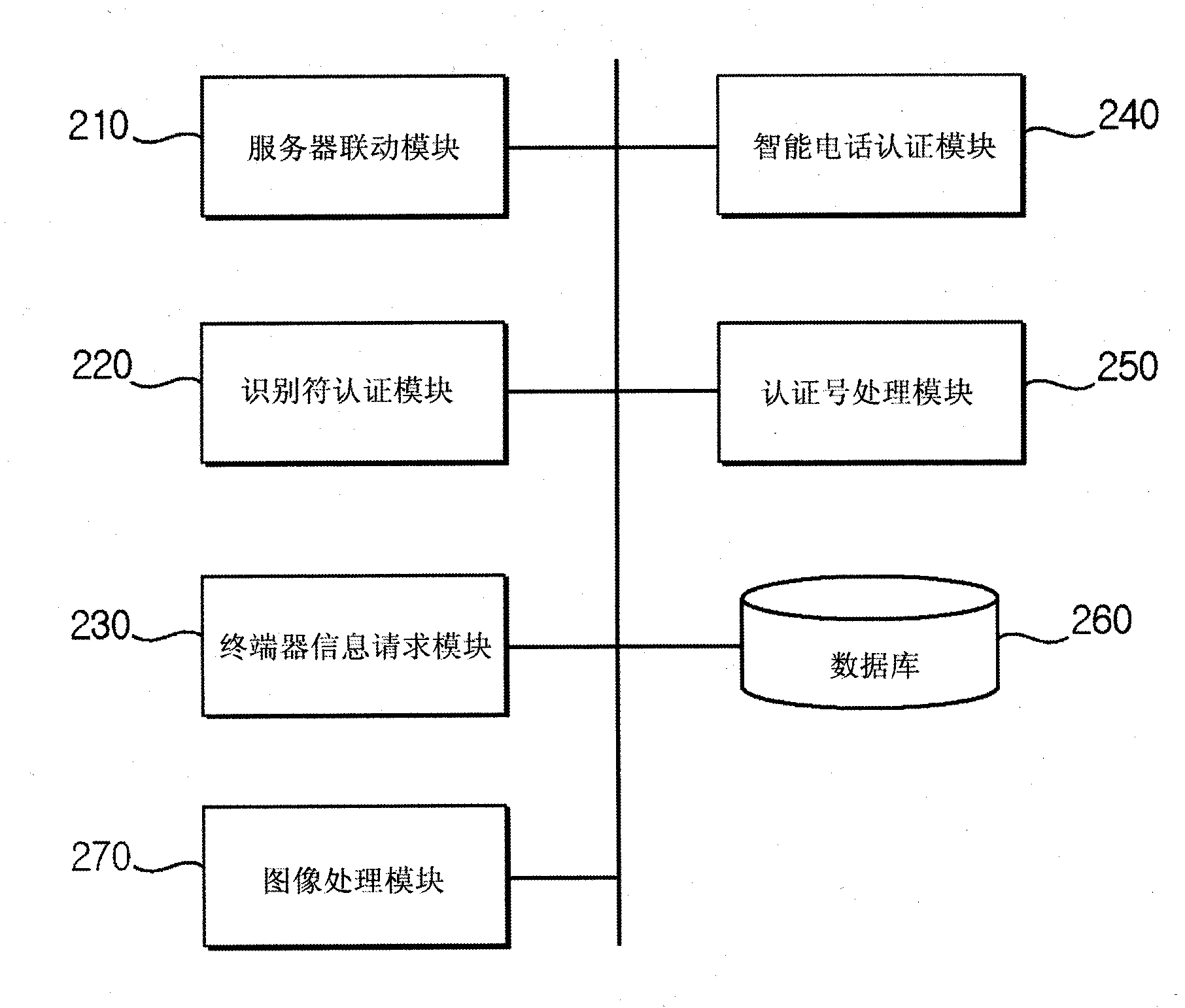
The present invention is to authenticate the user on the basis of an identifier and authentication information which are provided from a portable terminal and service server to a user terminal and displayed. Accordingly, an external invader cannot perform authentication instead of the user unless the external invader collects information required for authentication from all of the portable terminal, the service server, and the user terminal at the same time. The present invention can be used for processing authentication in portal sites, banking facilities including banks, personal blogs, homepages, and various other websites using the Internet.
Owner:株式会社艾克洛芙
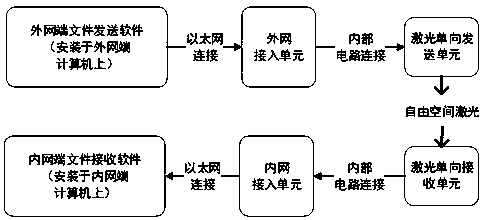
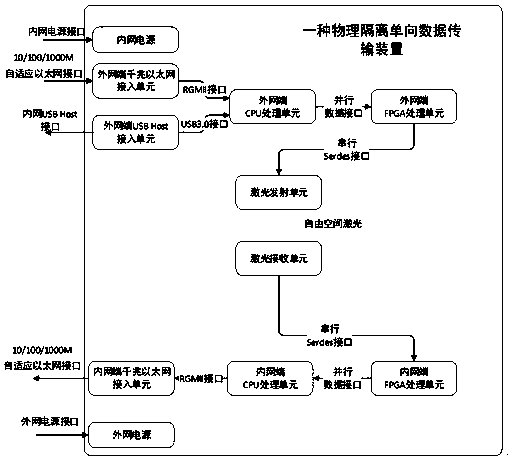
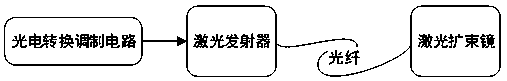
Physical isolation one-way information transmission system
The invention relates to a physical isolation one-way information transmission system, which solves the technical problem that the complete isolation is incompatible with the convenience. The system comprises an internal network access unit; an external network access unit; a laser one-way receiving unit connected to the internal network access unit; a laser one-way transmitting unit connected tothe external network access unit; an external network end file sending software installed on an external network end PC connected to the external network access unit by a network interface; and an internal network end file receiving software installed on an internal network end PC connected to the internal network access unit by the network interface. According to the above technical scheme, the problem is solved. The physical isolation one-way information transmission system can be used in an information transmission application.
Owner:智强通达科技(北京)有限公司
Range hood and gas stove all-in-one machine
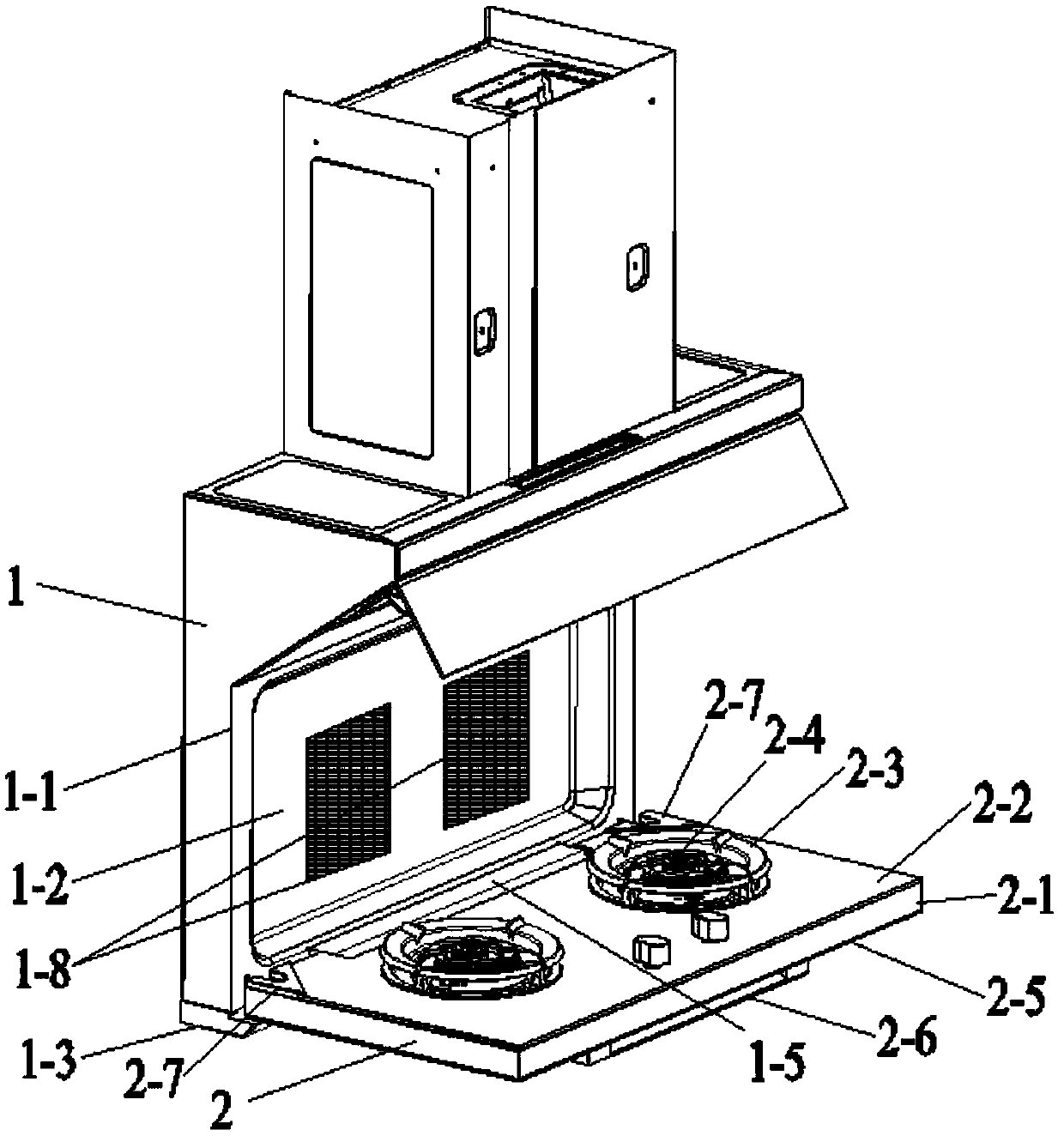
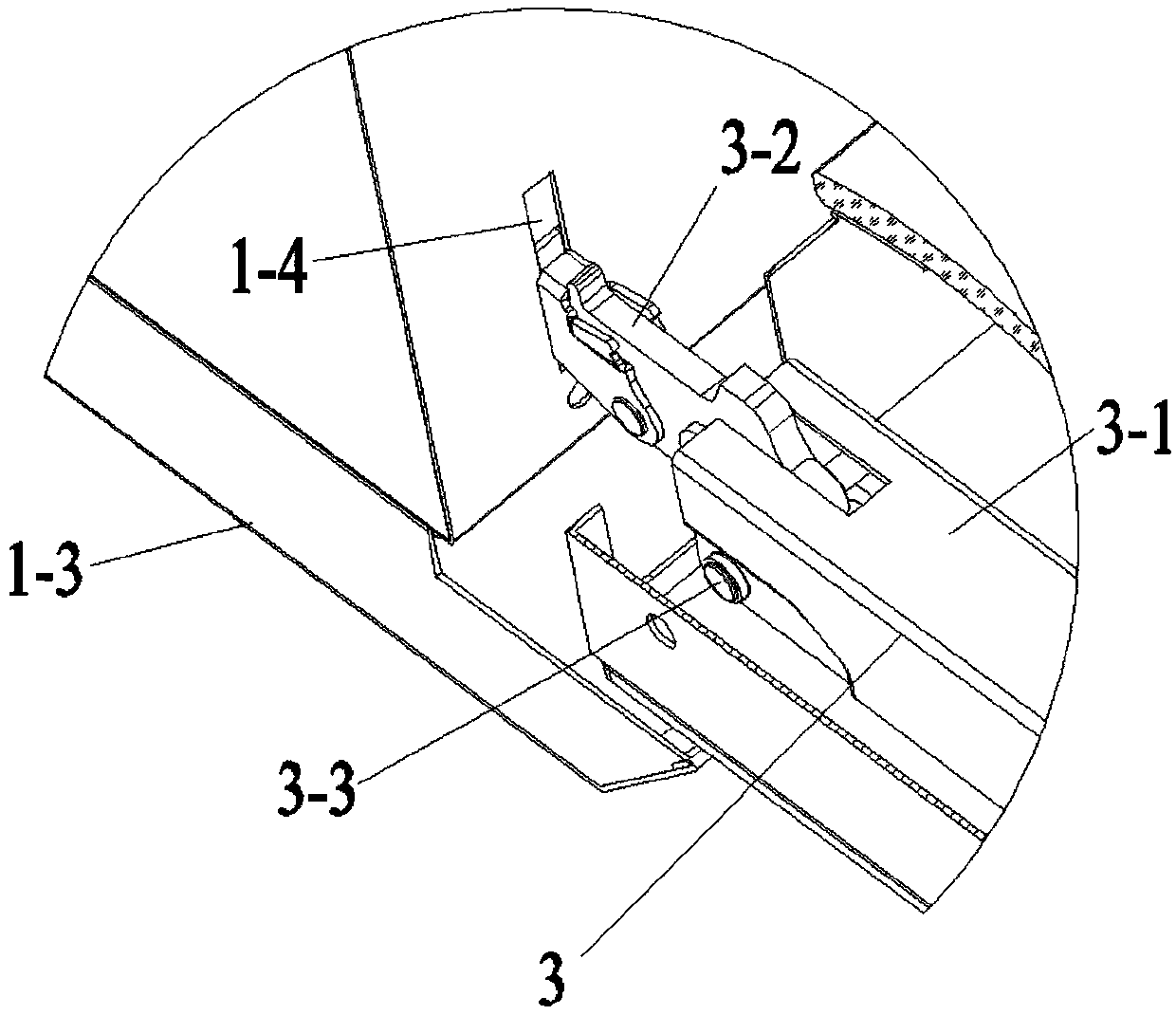
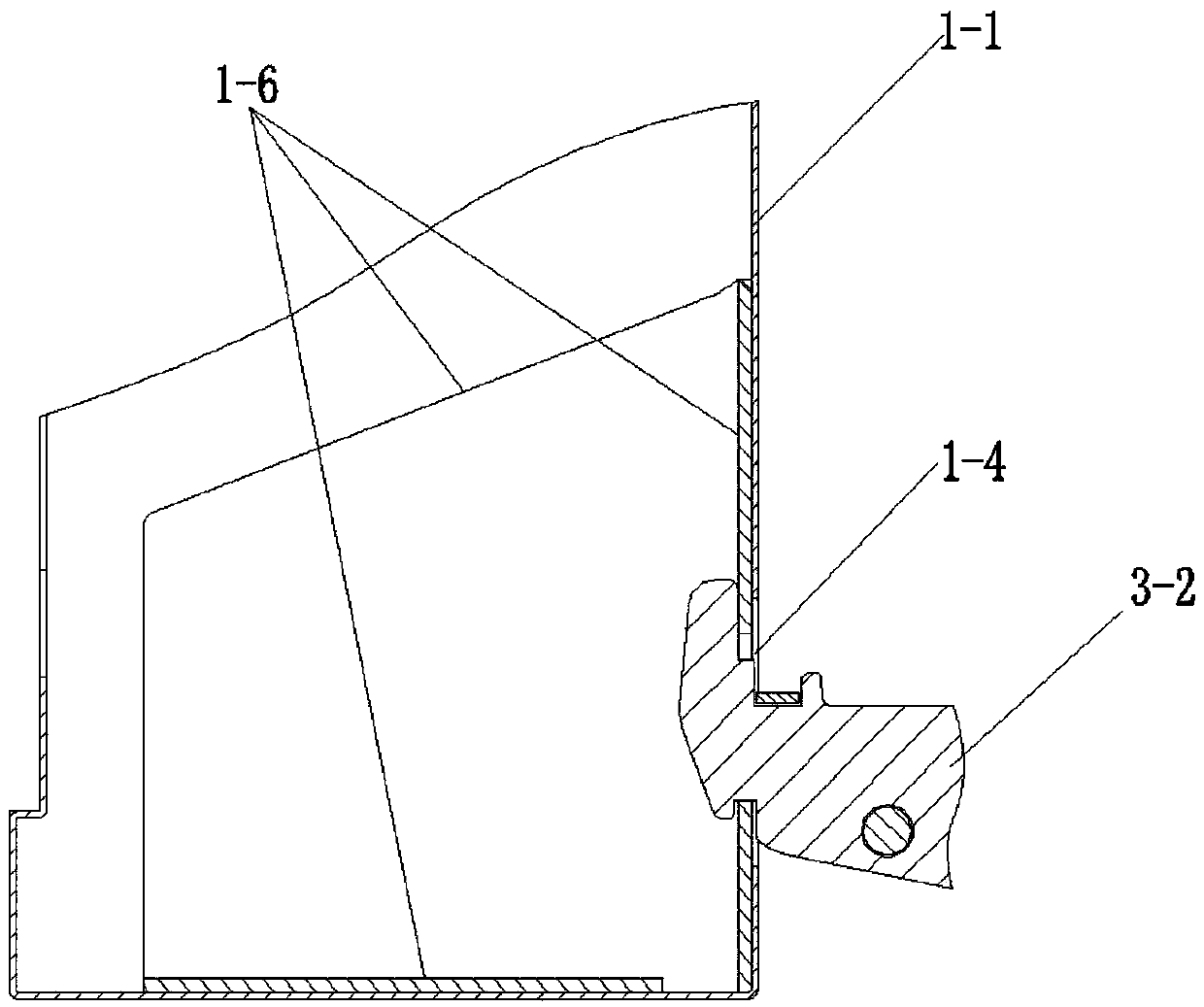
PendingCN110578938AAffect integritySave spaceStoves/ranges foundationsDomestic stoves or rangesCombustorExhaust fumes
The invention discloses a range hood and gas stove all-in-one machine. The range hood and gas stove all-in-one machine includes a range hood and a turnover gas stove, the range hood includes an exhaust fume collecting hood and a vertical panel arranged below the exhaust fume collecting hood, the hearth of the gas stove is hinged to the lower end of the vertical panel, an oil collecting box is arranged below the bottom wall of the vertical panel, and the front side wall, the left side wall and the right side wall of the vertical panel extend downwards to enclose a facade stretch cavity of the exhaust fume collecting hood. According to the range hood and gas stove all-in-one machine, burners and gas pipelines do not need to be arranged in cabinets like the prior art, the space in a kitchen is saved, a cabinet below the gas stove can be used for other purposes, the available space is enlarged, the arrangement of the vertical panel takes advantage of the viscous effect of oil fume, in theprocess of rising of the oil fume, the oil fume is attached to the front wall of the vertical panel to rise upwards, the facade stretch cavity formed by the front wall, the left side wall and the right side wall of the vertical panel and the exhaust fume collecting hood can improve the effect of oil fume collecting, and the oil fume absorption effect is enhanced.
Owner:HANGZHOU ROBAM APPLIANCES CO LTD
Submerged pump with spiral labyrinth seal device
InactiveCN101929469ALeak will notImprove reliabilityPump componentsPump installationsImpellerEngineering
The invention provides a submerged pump with a spiral labyrinth seal device. A right-handed spiral sealing ring is arranged on the back of an impeller and close to a motor shaft; a left-handed spiral sealing ring fixed on a sealing chamber is arranged above the impeller; and the right-handed and left-handed spiral sealing rings form the labyrinth seal device. The submerged pump with the spiral labyrinth seal device can effectively prevent a liquid in the pump from leaking into the sealing chamber, so that the problem that the reliability of the normal running of the submerged pump is affected by the leak liquid is solved.
Owner:JIANGSU GUOQUAN PUMP MFG CO LTD
Process and device for generating power by pressure energy of small natural gas pipeline network
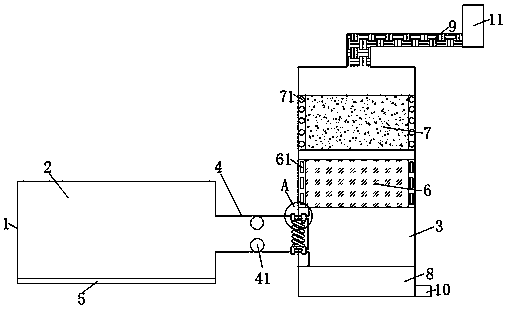
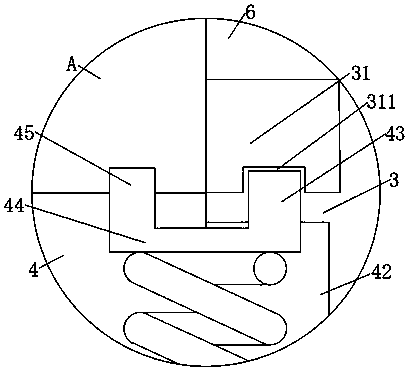
InactiveCN103422899BLeak will notSolve the problem that cannot be explosion-proofSealing arrangements for enginesMachines/enginesGas cylinderEngineering
The invention discloses a process and a device for generating power by pressure energy of a small natural gas pipeline network. A high-pressure pipeline network of the device is connected with a gas inlet of an expansion machine through a pipeline; a gas outlet of the expansion machine is connected with a gas inlet of a temperature balancer through a pipeline; an outlet of the temperature balancer is connected with a low and medium-pressure gas pipeline network through a pipeline; a main shaft of the expansion machine is connected with a gearbox; the gearbox is connected with a power generator; the power generator is connected with a transformer synchronizer; the expansion machine adopts an improved AT15-65 type gas expansion machine; one end of the main shaft is connected with an air cylinder in a totally-closed way; a first seal ring and a second seal ring, which have sealing effects, are arranged between the other end of the main shaft and a wheel drum; a flow guide pipe is arranged in a closed cavity between the two seal rings; the flow guide pipe is connected with an inert gas bottle. The device can be used for continuously and stably providing a 220 V / 380 V stable power supply for an interruptible and closed 1-5 kW low-power user.
Owner:SOUTH CHINA UNIV OF TECH +1
High-protection-level air-cooled lithium battery pack thermal management system and method
PendingCN110707259ALeak will notSo as not to damageSecondary cellsCell component detailsThermodynamicsEngineering
The invention discloses a high-protection-level air-cooled lithium battery pack thermal management system and method. The system comprises one or more layers of batteries and / or battery modules in thebattery pack, a battery pack shell and an external air cooling module, wherein the battery and / or the upper surface and / or the lower surface are / is attached to a micro heat pipe array, the part attached to the surface of the battery and / or the battery module is an evaporation section, at least one end of the micro heat pipe array extends out of the surface of the battery and / or the battery module, and the extending part serves as a condensation section to be attached to a battery pack shell; the battery pack shell surrounds the battery pack and is of a closed structure, and at least the position, corresponding to the condensation section, of the battery pack shell is provided with a heat conduction partition plate; the external air cooling module is tightly attached to the outer surface of the face, provided with the heat conduction partition plate, of the battery pack shell, air cooling fins are arranged in the external air cooling module, and a fan is arranged on the side face of the external air cooling module. The heat dissipation efficiency is high, the risk of liquid pollution is avoided, and the protection level is high.
Owner:赵耀华 +1
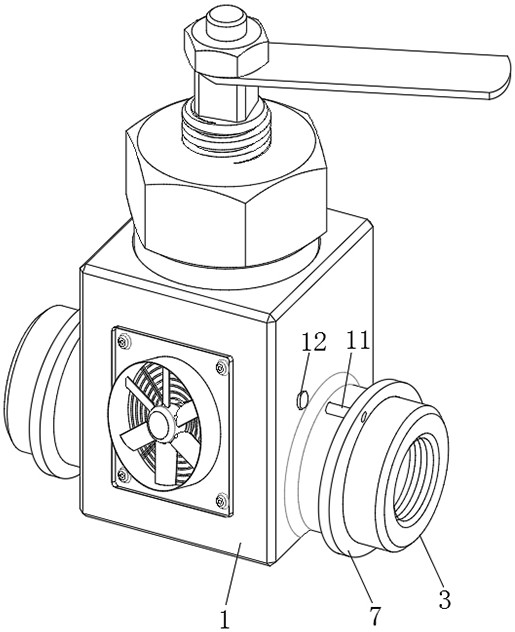
Protective valve of gas pipeline terminal
ActiveCN113431955AEasy to installNot easy to shakeSleeve/socket jointsValve arrangementsStructural engineeringMechanical engineering
The invention relates to the field of valves, and particularly discloses a protective valve of a gas pipeline terminal. The protective valve comprises a valve body and pipeline joints integrally connected to the two ends of the valve body, wherein the outer wall of each pipeline joint is sleeved with an outer ring plate; the end, away from the valve body, of each outer ring plate is connected with a sealing sleeve; a lantern ring is installed at the other end of each sealing sleeve; and a gas leakage alarm is further installed on the outer wall of each sealing sleeve. According to the protective valve, first plugging sleeves and second plugging sleeves are all opened by a pipeline, and the first plugging sleeves and the second plugging sleeves can perform double sealing on the joints of the pipeline joints and a home-entry pipeline or an internal pipeline, so that the joints are not prone to gas leakage; and even if leakage occurs, gas can only stay in the sealing sleeves and cannot drift outwards, it is guaranteed that the gas cannot leak at the installation position of the valve body, and the safety of the valve body in the using process is improved.
Owner:QIDONG YONGAN VALVE CO LTD
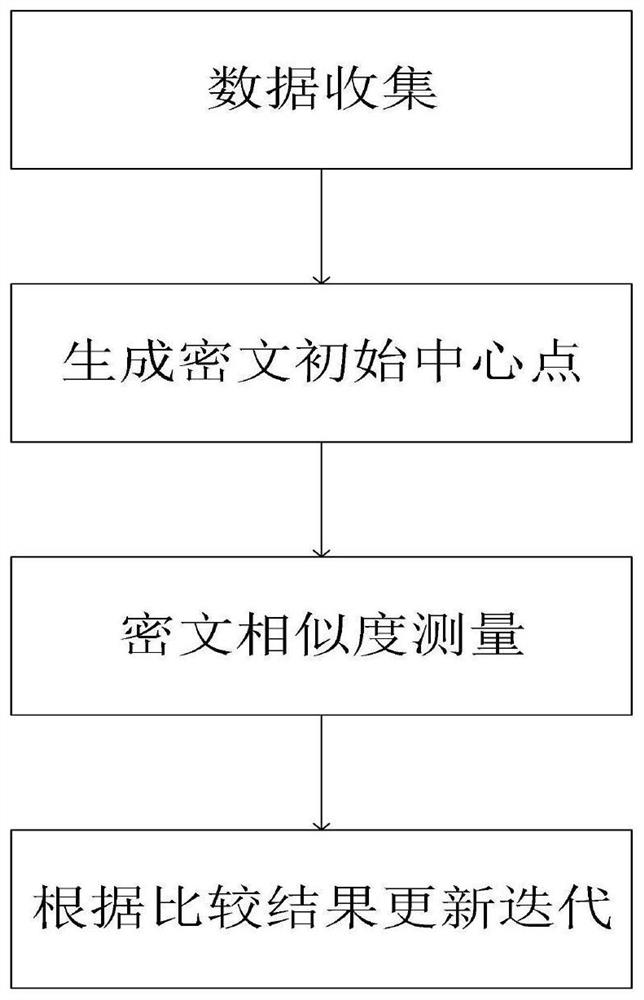
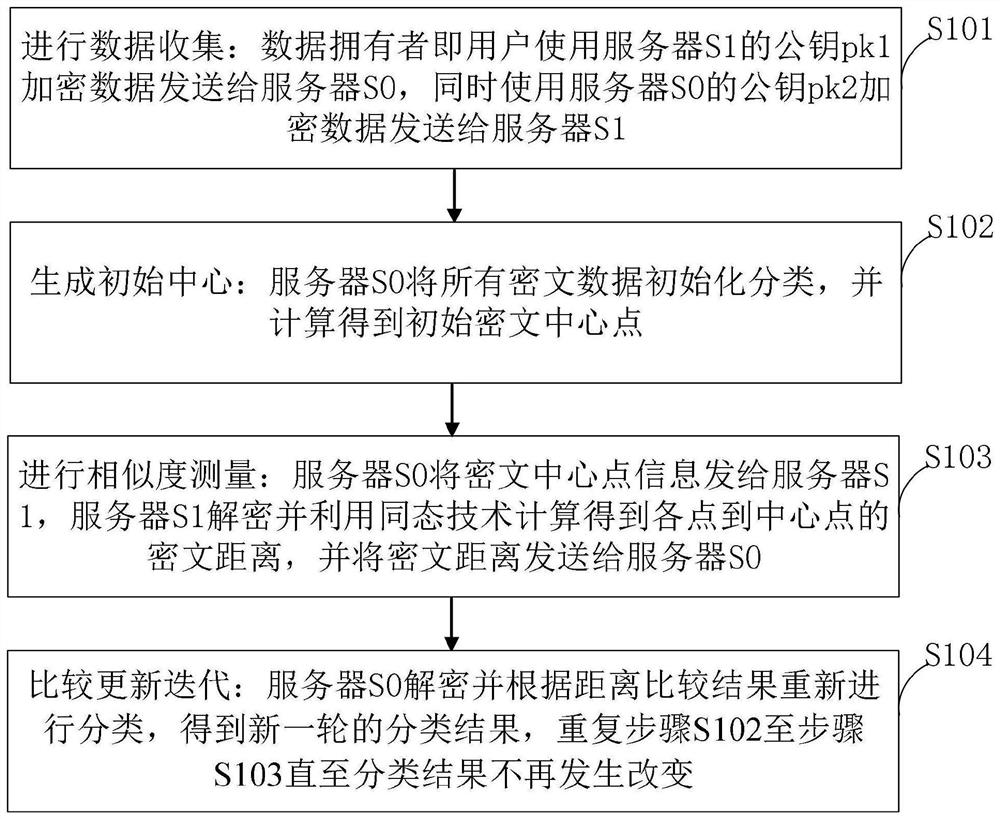
Privacy protection k-means clustering method and device, medium and terminal
PendingCN113626858AProtect private informationSmall calculation cost and time costCharacter and pattern recognitionDigital data protectionPrivacy protectionUser information
The invention belongs to the technical field of information privacy protection, and discloses a privacy protection k-means clustering method and device, a medium and a terminal, and the privacy protection k-means clustering method comprises the steps: collecting and encrypting original data, processing the encrypted data through two servers, classifying the data through a K-means algorithm, and grouping similar data according to distance measurement. The privacy information of the user can be well protected in the whole K-means clustering algorithm process, and the invention is friendly in the two aspects of calculation cost and time. The privacy protection k-means clustering method provided by the invention has the advantages of user friendliness, safety, correctness and effectiveness. The efficient privacy protection k-means clustering method provided by the invention is efficient and has linear complexity, and correctness and efficiency are not affected under the condition that the problem of user information privacy is solved.
Owner:XIDIAN UNIV
An Identity-Based Anonymous Authentication Method and System
ActiveCN107947913BImprove securityLess fairnessKey distribution for secure communicationUser identity/authority verificationSecure communicationInternet privacy
The invention relates to an identity-based anonymous authentication method and system. The method comprises the following steps: a server generates two partial private keys and sends the same to double parties P1 and P2 participating in the authentication respectively, wherein P1 and P2 generate a main authentication code (the formula is described in the specification) and R in an authentication process, and the privacy and reliability of the interactive information between P1 and P2 are ensured by using zero knowledge proof; after the P1 obtains the main authentication code, the P1 generatesa pseudo-address AID, generates a third temporary public key R3, calculates a final authentication code alpha, and sends the authentication information (AID, R, R3, alpha, T) the server, and the server verifies the authentication information and feeds back the authentication information to a user, after the successful completion of three times of handshake, the server can establish secure communication with the user. The identity-based anonymous authentication method and system are suitable for jointly completing identity-based distributed anonymous authentication without exposing the respective partial authentication private keys of the both parties together, the both parties holding the partial private keys must participate in the authentication at the same time, and the complete authentication private key does not need to be restored.
Owner:WUHAN UNIV
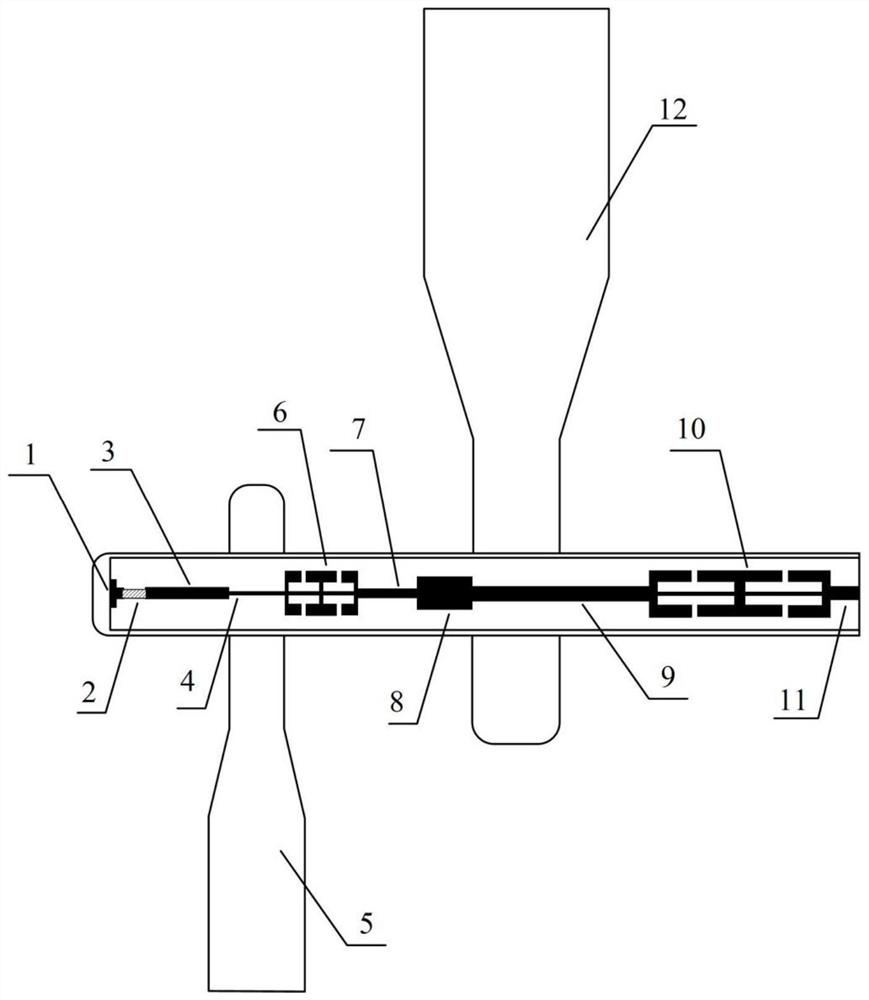
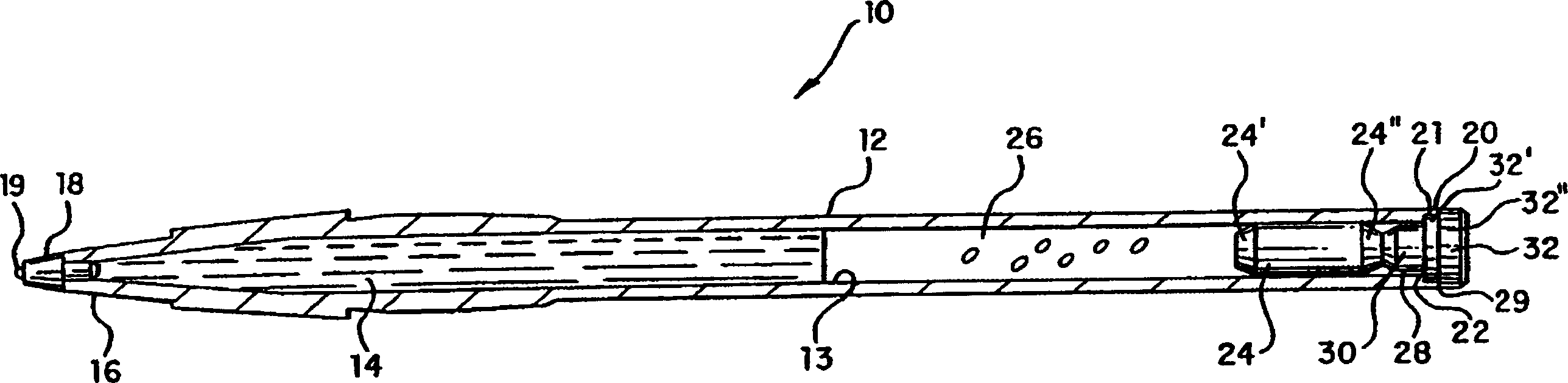
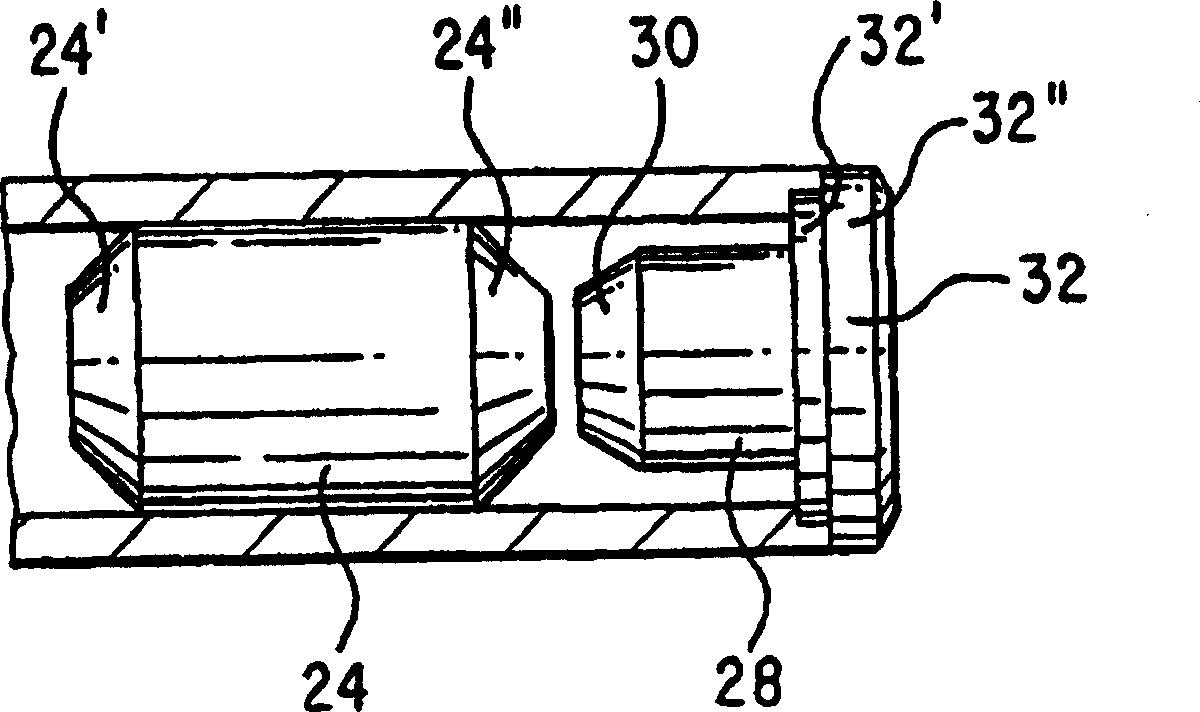
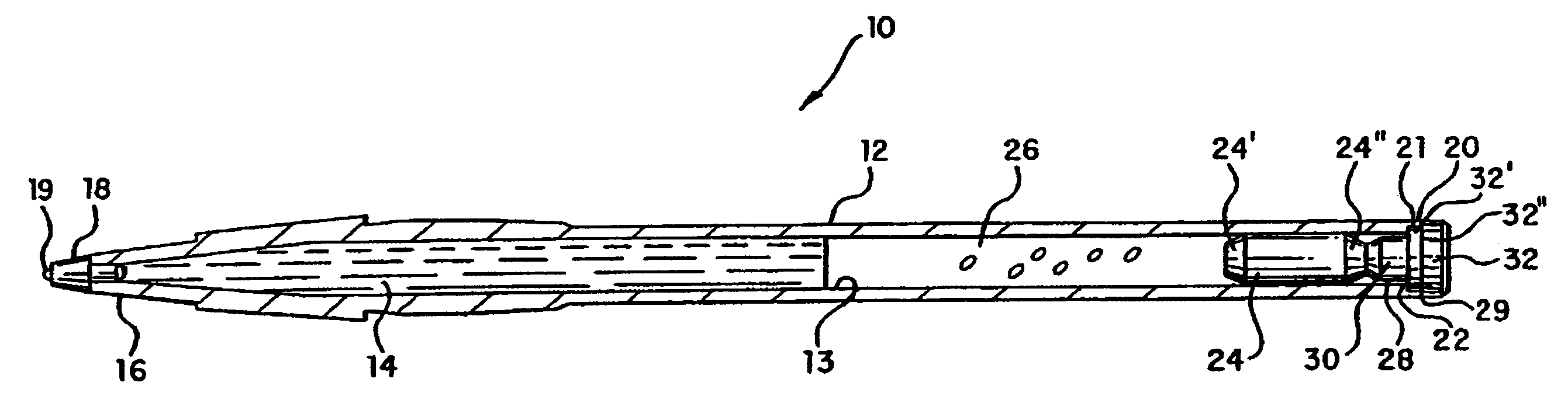
Double seal system for pressurized writing device
InactiveCN1278872CPrevent leakageLeak will notLiquid surface applicatorsBrush bodiesNitrogenEngineering
A writing device (10) generally includes a cylindrical body (12) with uniform thickness, and a part of writing medium, such as ink (14), is filled in the cylindrical body. A writing point (19) is inserted into the first end (16) of the body (12), and a first sealing member (24) is inserted into the second end (20) of the body (12). A first sealing element (24) is in the body (12), proximate to the second end (20). A pressurized gas, such as nitrogen (26), is disposed within the body (12), between the ink (14) and the first sealing member (24). Alternatively, a gas generating means may be provided in the body (12) to continuously generate gas as the ink (14) is consumed, thereby maintaining the pressure therein. A second sealing member (28) is inserted into the second end (20) of the body (12) to provide a double seal gas pressurization system.
Owner:SOC DITE SOC BIC
Insulation system for liquid cargo tanks of independent type b lng ships with splash screen structure
ActiveCN105736903BImprove reliabilityReduce workloadThermal insulationHull bulkheadsInsulation layerMarine engineering
The invention provides an independent B-type LNG ship liquid cargo tank heat insulation system with a splash-proof screen structure. The independent B-type LNG ship liquid cargo tank heat insulation system comprises a splash-proof screen, a bolt mechanism and a heat insulation plate, wherein the splash-proof screen is arranged on a main screen wall in a spaced manner through a supporting mechanism; the bolt mechanism is arranged on the main screen wall; and the heat insulation plate is fixed to the splash-proof screen through the bolt mechanism. The independent B-type LNG ship liquid cargo tank heat insulation system has the beneficial effects that all components are subject to modularization manufacturing and installation, unified standard specifications can be adopted when the components are prefabricated, and the working amount and the cost of manufacturing are reduced; heat insulation plate modules are relatively independent, when some module is damaged, the other modules cannot be influenced, and the reliability of heat insulation layers is improved; in addition, when the damaged module is repaired, only one damaged module needs to be dismounted for local repairing, and convenience is brought to maintenance and repairing; and the heat insulation system is suitable for an independent B-type LNG ship liquid cargo tank, can also be used for other shore-based low-temperature liquid cargo storage tanks or can serve as a heat insulation system of other low-temperature occasions.
Owner:SHANGHAI JIAO TONG UNIV
A water utilization river sludge cleaning device
ActiveCN109914512BPrevent leakageLeak will notSoil-shifting machines/dredgersHydraulic cylinderRiver routing
The invention discloses a water utilization river channel sludge cleaning device, which comprises a fixed seat, a connecting device located on the fixed seat, and a hydraulic adjustment device, and is characterized in that an excavating sealing bucket device is arranged under the fixing The device is equipped with a silt loosening and stirring device, which is connected to the excavating sealing bucket device, and loosens the silt through the connection between the motor and the auger bit, and the hydraulic adjustment device is connected to the excavating sealing bucket device through the hydraulic cylinder and the bucket The connection of the bucket excavates the silt, so that the silt is loaded into the sealed space formed by the two buckets. The invention has the advantages of simple structure and strong practicability.
Owner:宁夏全唐环境建设有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com